Patents
Literature
69results about How to "Prevent snooping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
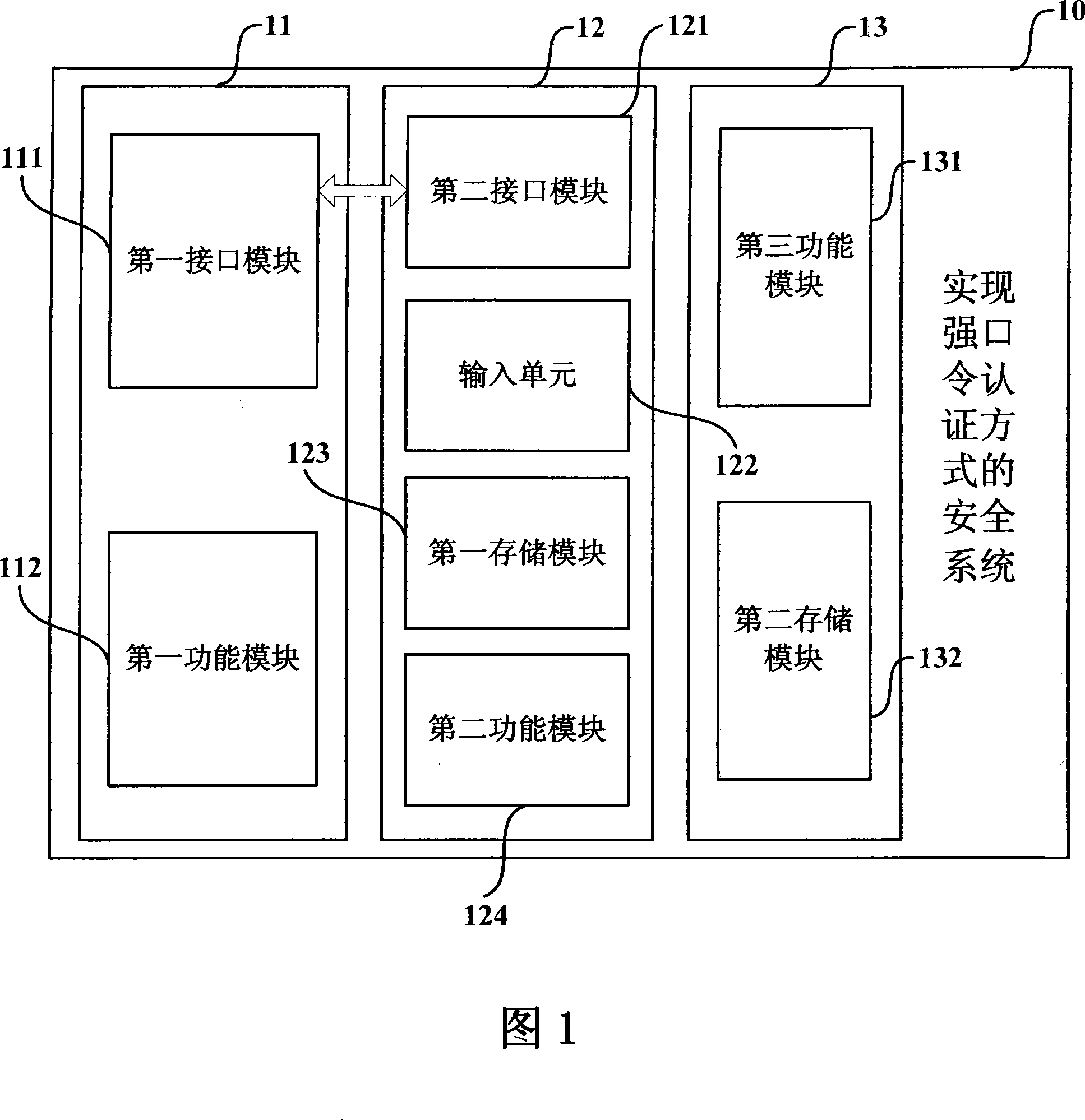
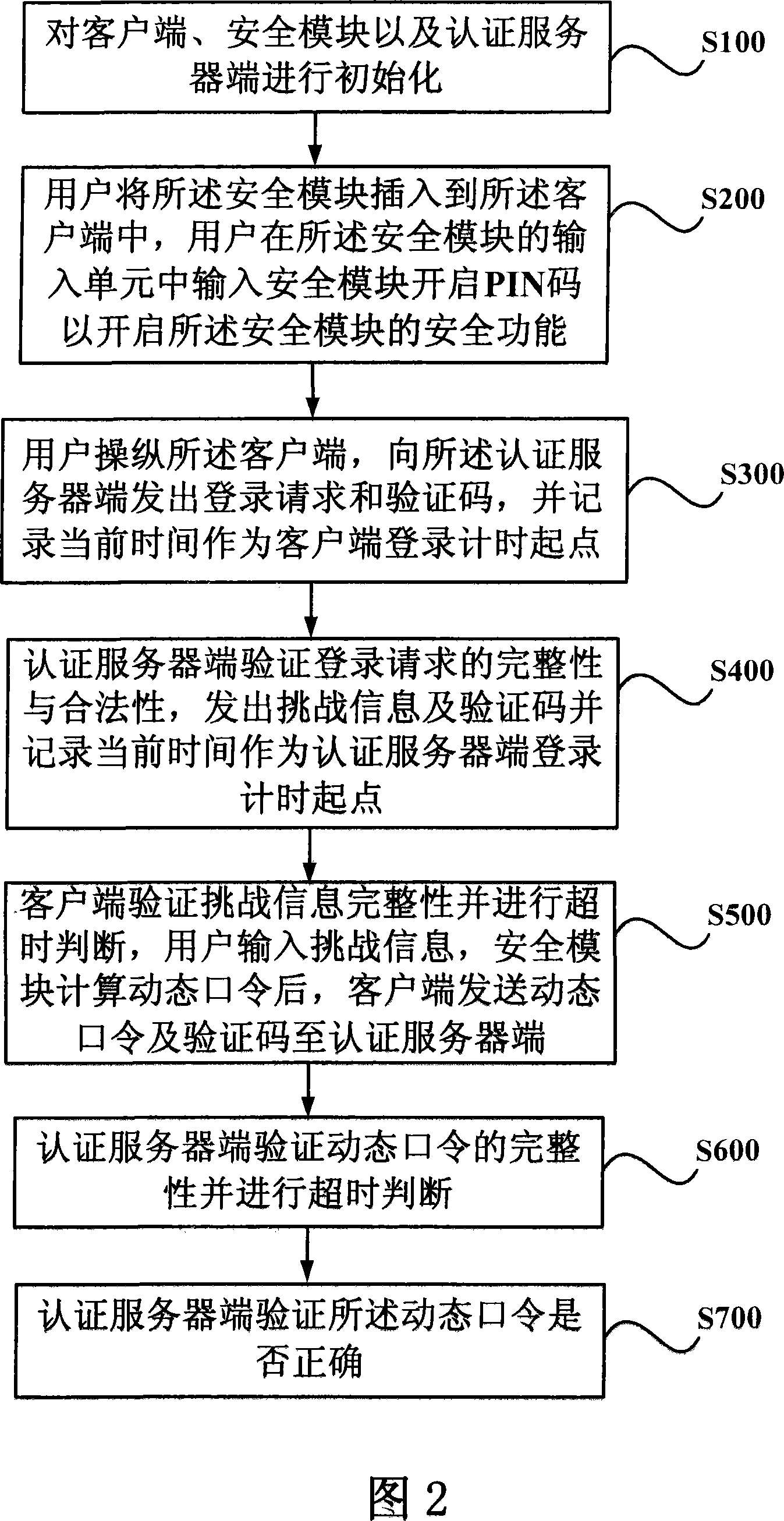
A secure system and method for realizing powerful password authentication mode
ActiveCN101188495APrevent snoopingPrevent eavesdroppingSecuring communicationMan-in-the-middle attackPassword
The invention relates to the field of password authentication and discloses a security system and method that realizes the pattern of strong password authentication so as to resolves such problems in the prior password authentication pattern as the password being easily pried and attacked. The invention uses a security module for password authentication, and imports the user password into the security module instead of a host machine keyboard, adopts the random number with sufficient length as a user password, and the user password is not directly sent onto the network when logging in, and the dynamical information about the transmitted password is once for all, thereby being free from the attacks by various passwords. At the same time, the invention adopts a challenge / reply mechanism and a time synchronization mechanism, and combines the security function property of the security module, helping the method to prevent the counterfeit of a server and the assaults of a middleman apart from the fight against password assaults.
Owner:BEIJING SINOSUN TECH
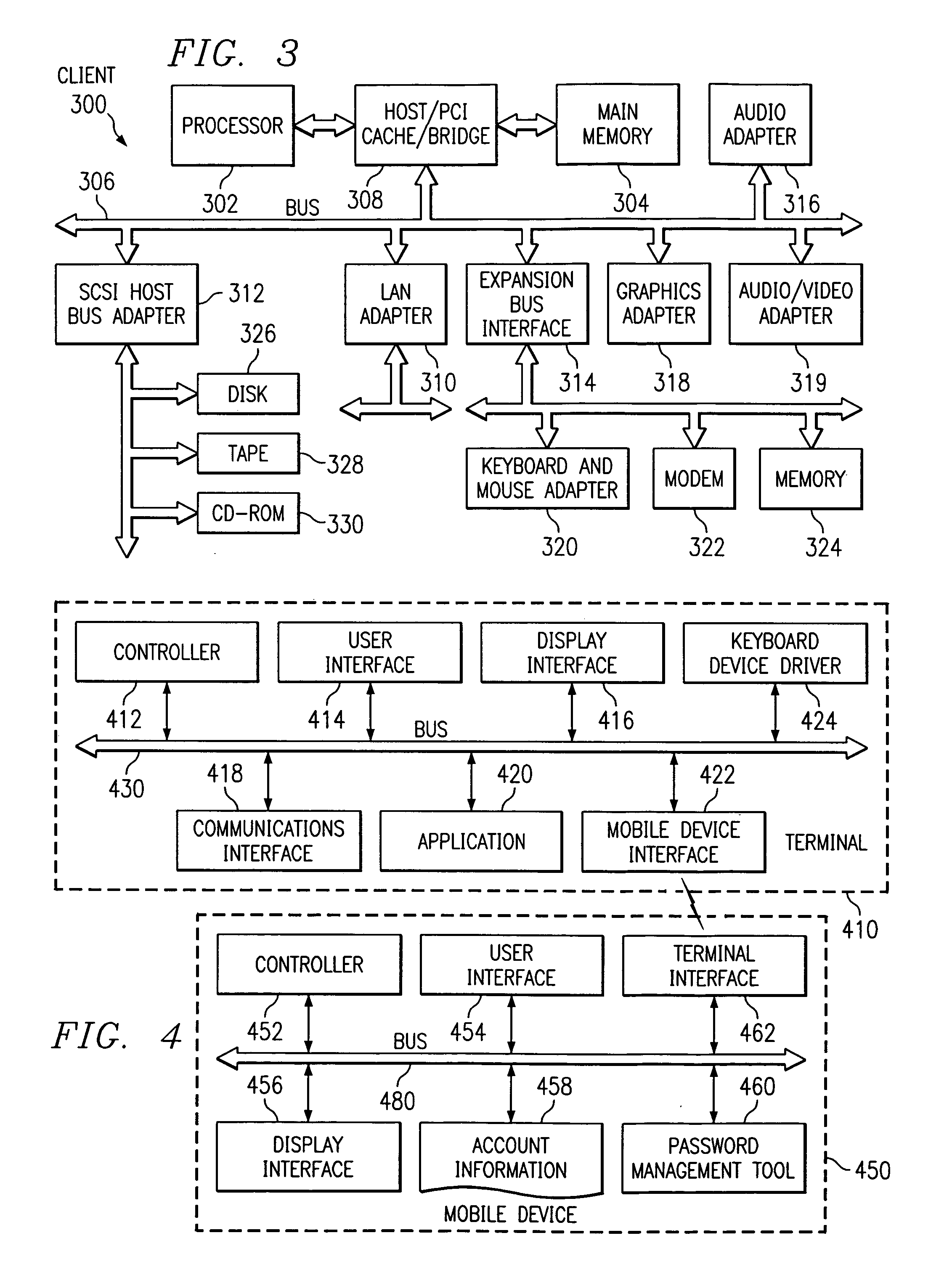
PDA password management tool
InactiveUS7092915B2Prevent snoopPrevent snoopingComplete banking machinesFinancePassword managementCipher
A mechanism is provided for storing user identifications and passwords in a mobile device, such as a personal digital assistant. A modified keyboard device driver may be installed on each platform the user accesses. When the user is prompted for a password from a functioning terminal, the user may select the appropriate account on the mobile device. The mobile device then may send the user identification and password for the account to the terminal. The modified keyboard device driver receives the user identification and password from the mobile device and converts it into keyed text. The accounts with user identifications and passwords may be protected by a password. Thus, the user must only remember the one mobile device password to access a plurality of resources and computer systems. Furthermore, the communications between the mobile device and terminal may be encrypted to prevent snooping.
Owner:LINKEDIN
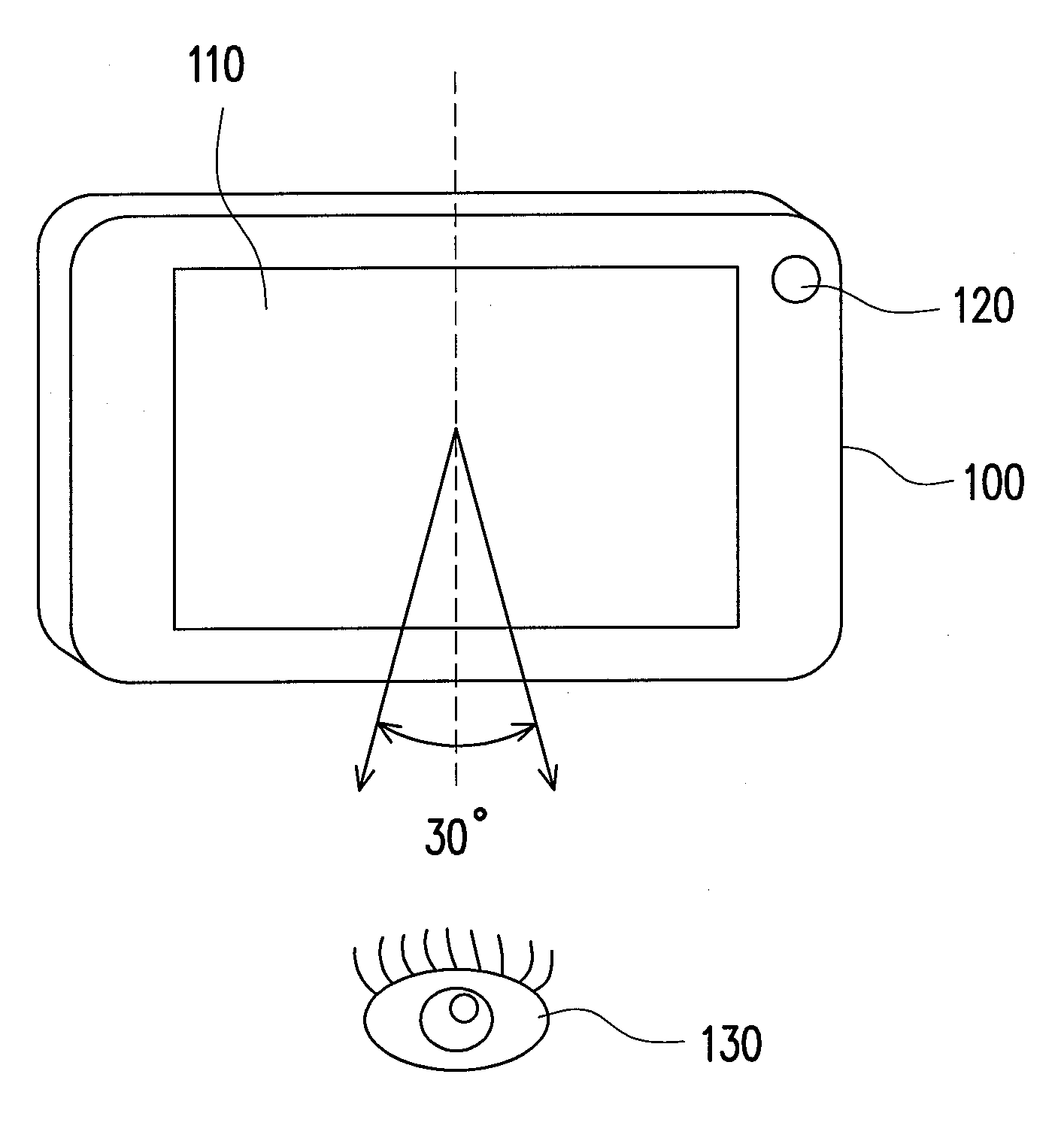
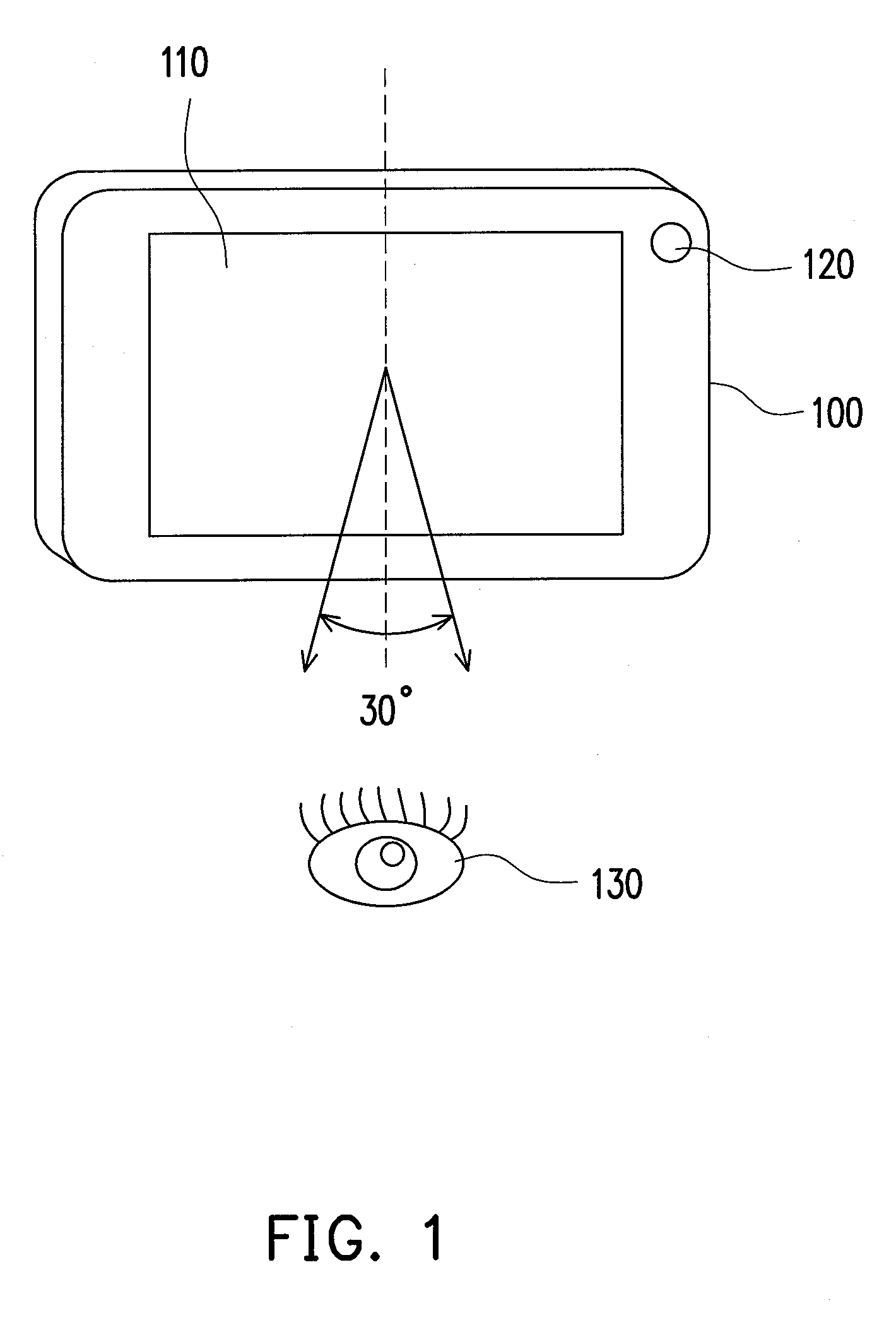
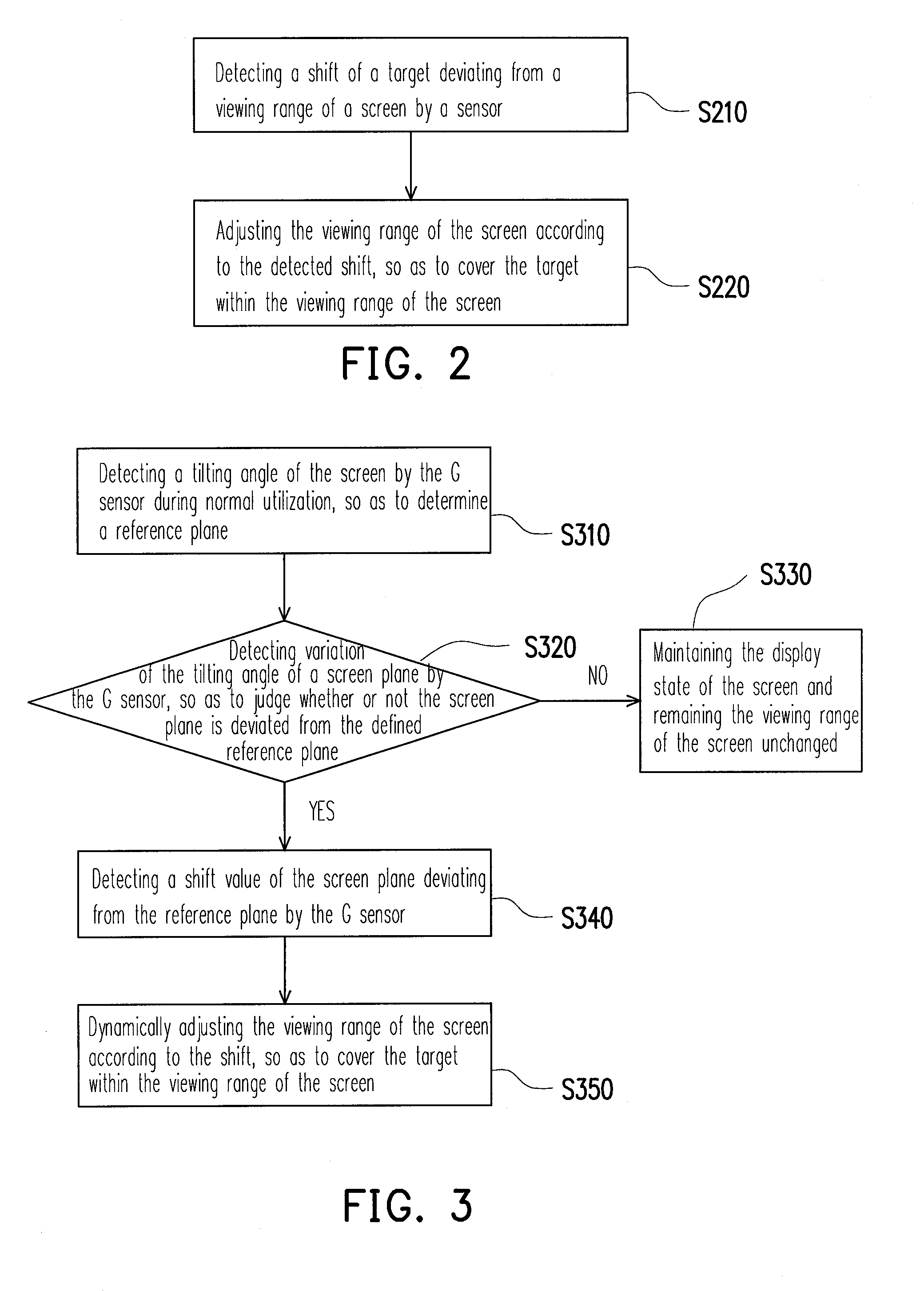
Method and apparatus for dynamically adjusting viewing angle of screen
ActiveUS20090167737A1Improve convenienceAvoid normal displayInput/output for user-computer interactionTelevision system detailsComputer scienceElectronic equipment
Owner:HTC CORP
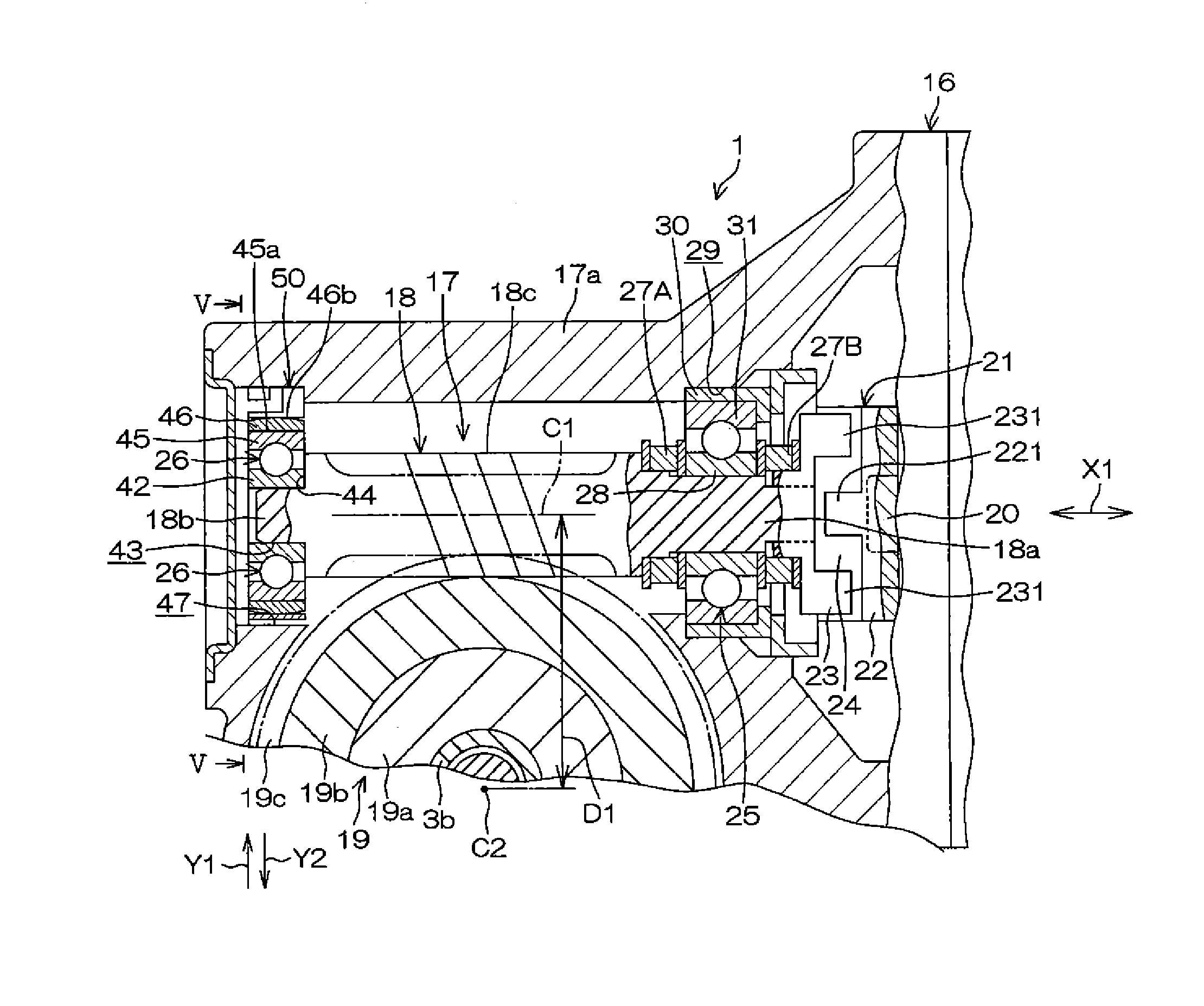
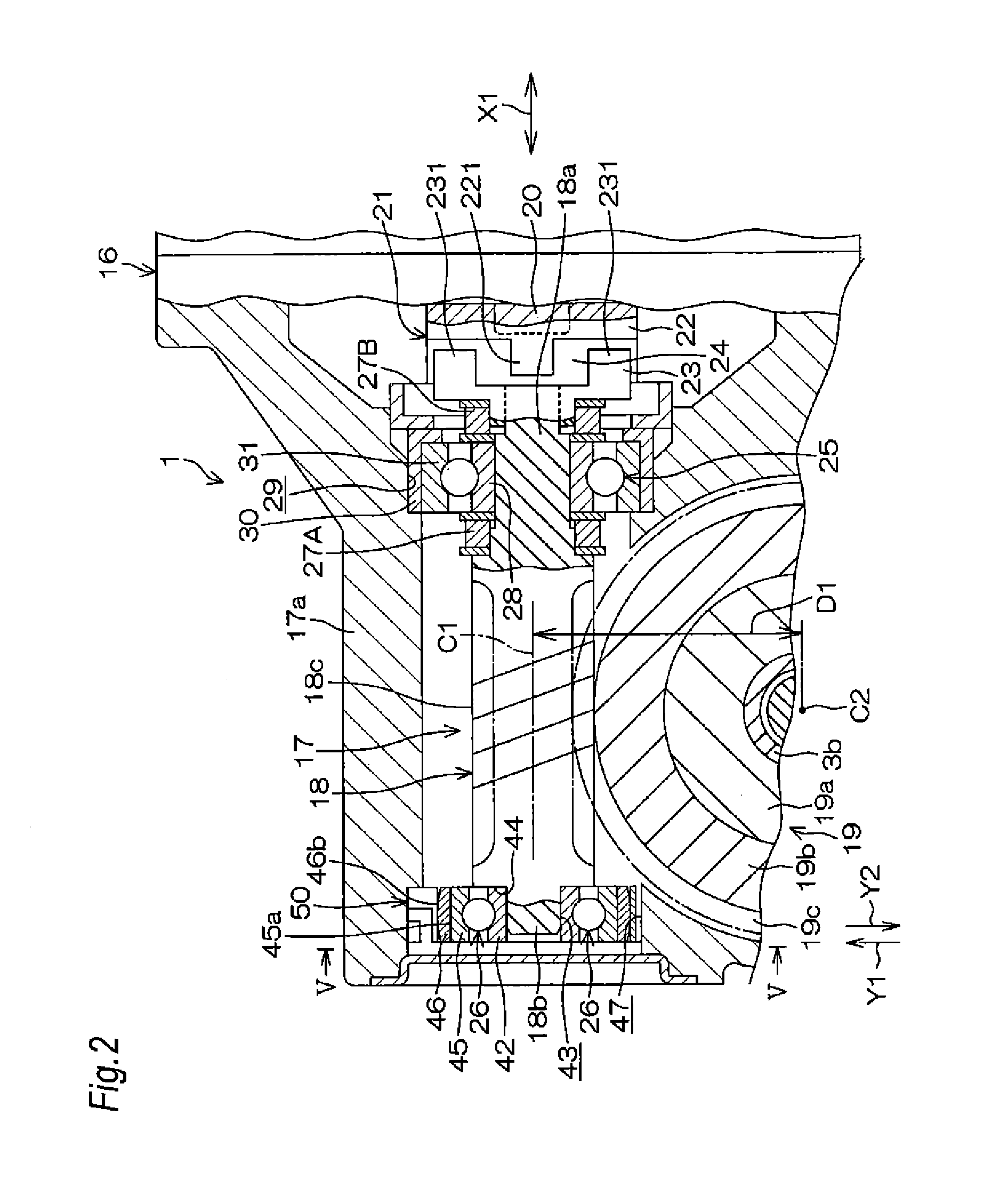
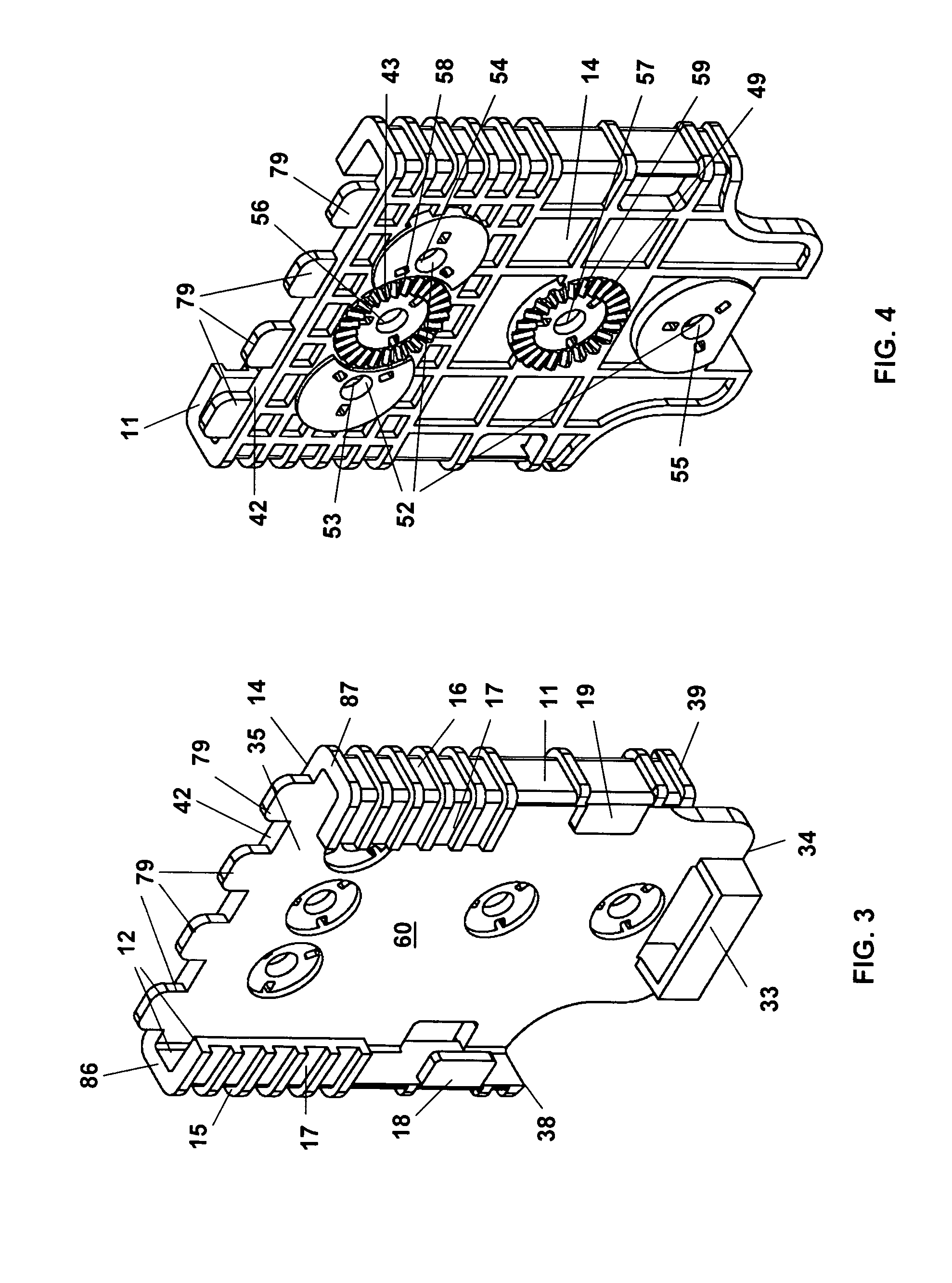
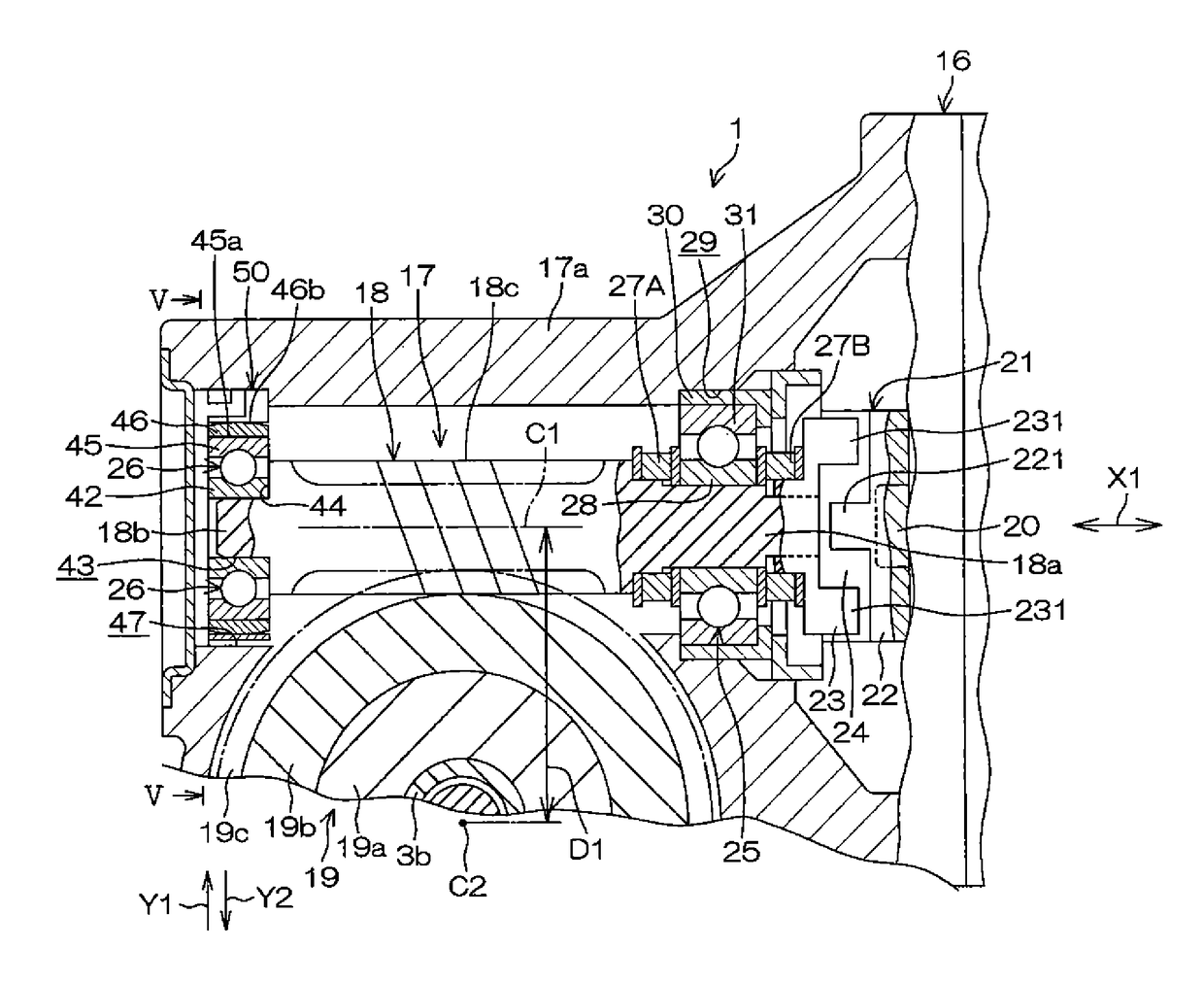
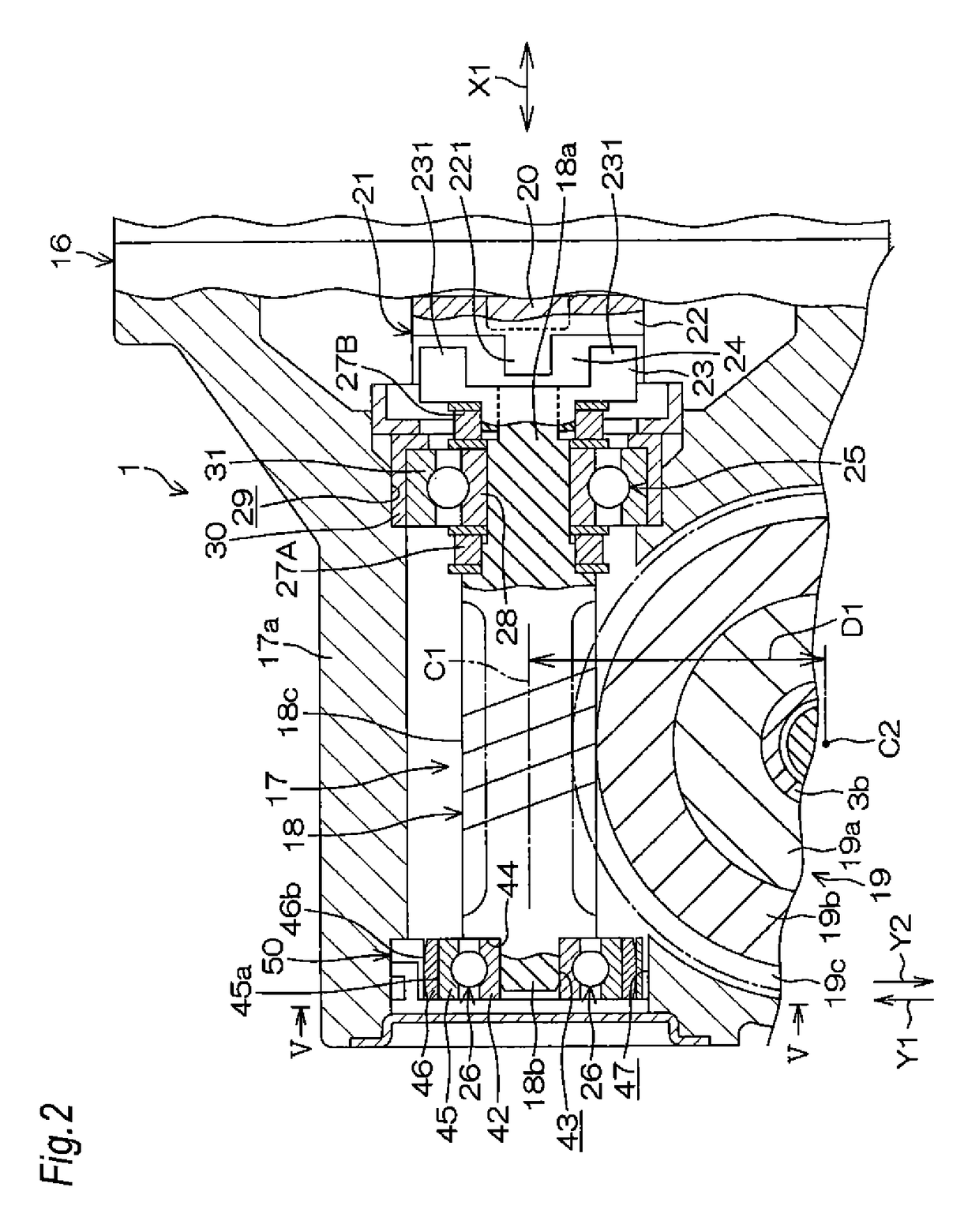
Electric power steering device
InactiveUS20150075899A1Feel goodProcess stabilityBall bearingsMechanical steering gearsElectric power steeringEngineering
An electric power steering device includes a worm which is swingably connected to the rotation shaft of an electric motor through a joint. A first end portion and second end portion of the worm are supported by a first bearing and a second bearing, respectively. A pair of elastic members elastically urge the worm to an axial neutral position. An annular leaf spring which is held by a housing urges the second end portion toward a worm wheel through the second bearing. A synthetic resin member having a sliding contact surface which is in contact with the leaf spring is integrally disposed on the second bearing.
Owner:JTEKT CORP
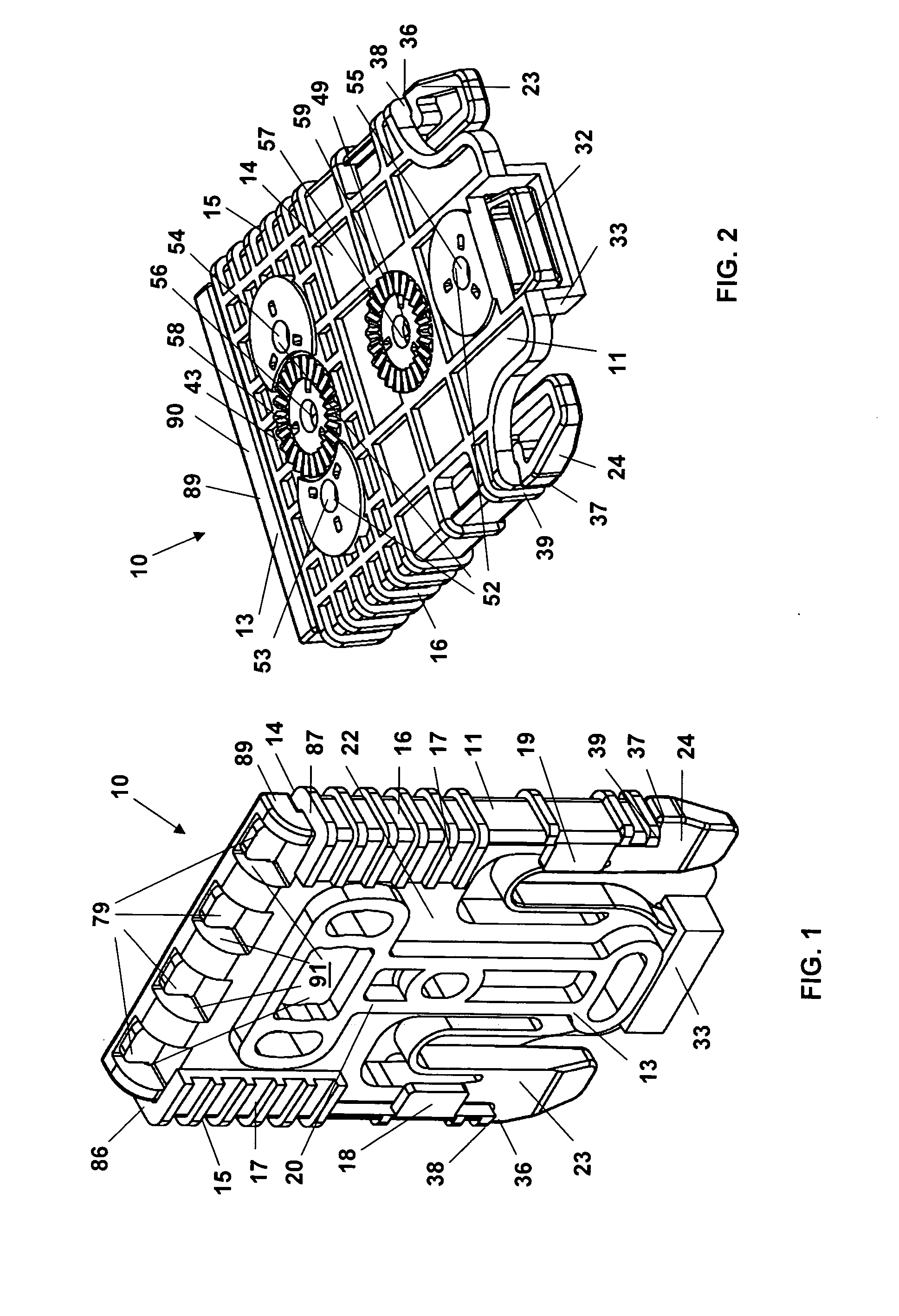
Attachment mount and receiver system for removably attaching articles to garments
ActiveUS20090277936A1Move quicklyWithdrawn quicklySnap fastenersTravelling carriersEngineeringReceiver system
An attachment mount and receiver system for attaching articles to a garment. A receiver has openings for affixing the receiver to a support that is then attached to a compatible garment. The mount has openings for affixing an article thereto. A pair of flexible springs permit connected tines to be compressed inwardly, allowing the mount to be slidingly inserted into the receiver. A barb at the end of each tine engages an end wall of the receiver when the mount is fully seated. Tines are compressed inwardly and the mount is withdrawable. Selective locks can inhibit the tines from being compressed. Resistance to prying the mount away from the receiver is also provided.
Owner:PREZINE LLC A LIMITED LIABILITY COMPANY OF FLORIDA
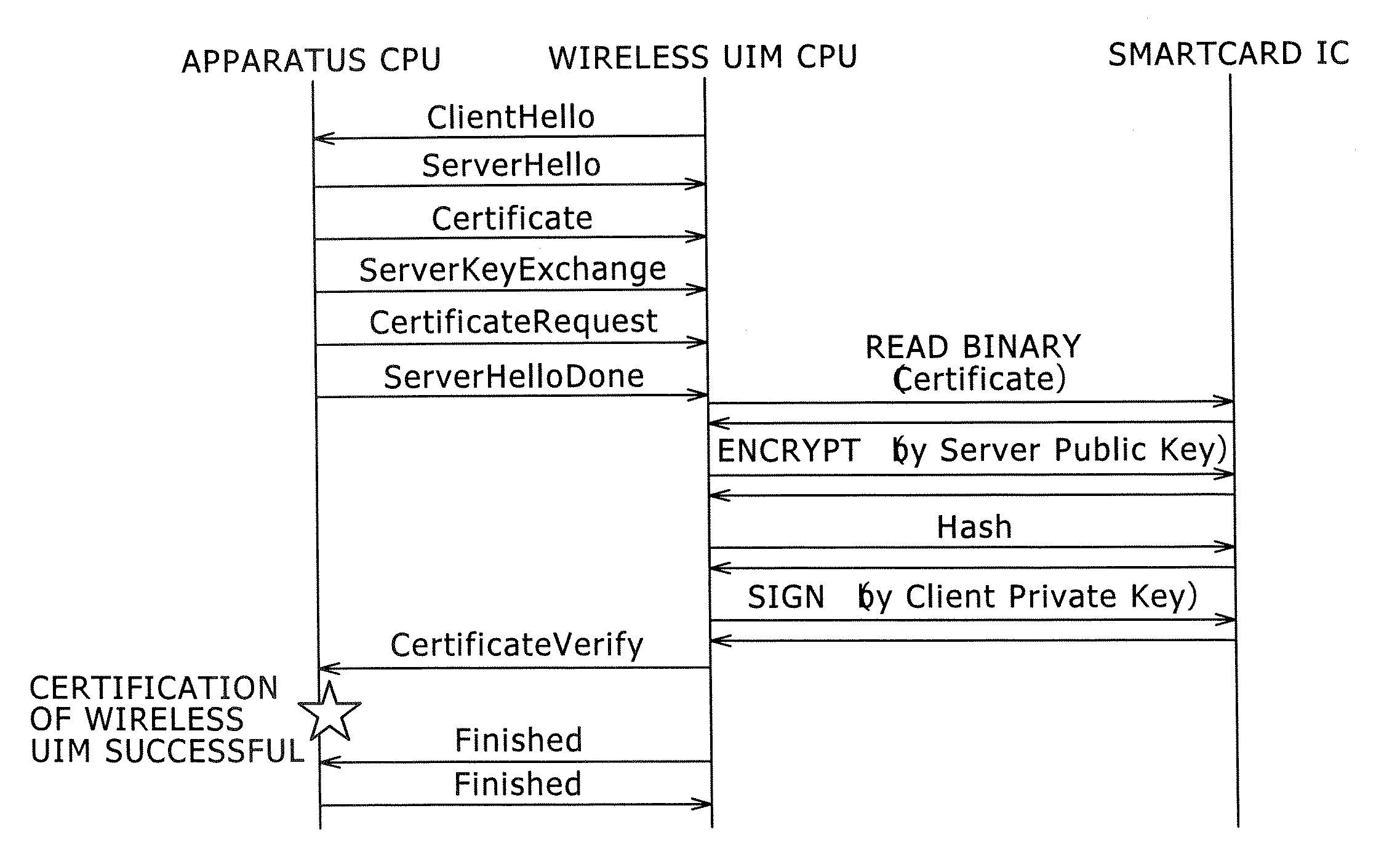
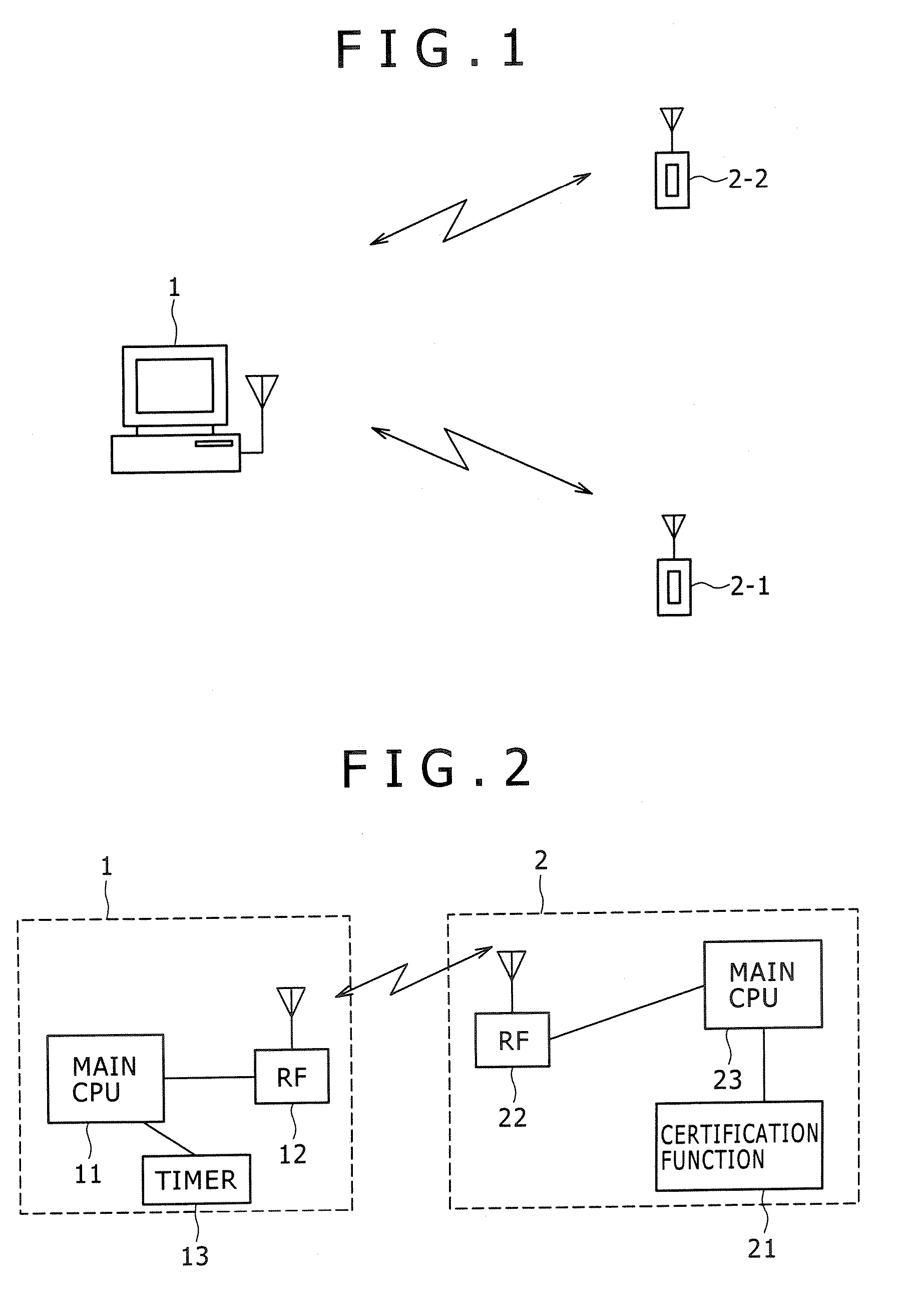
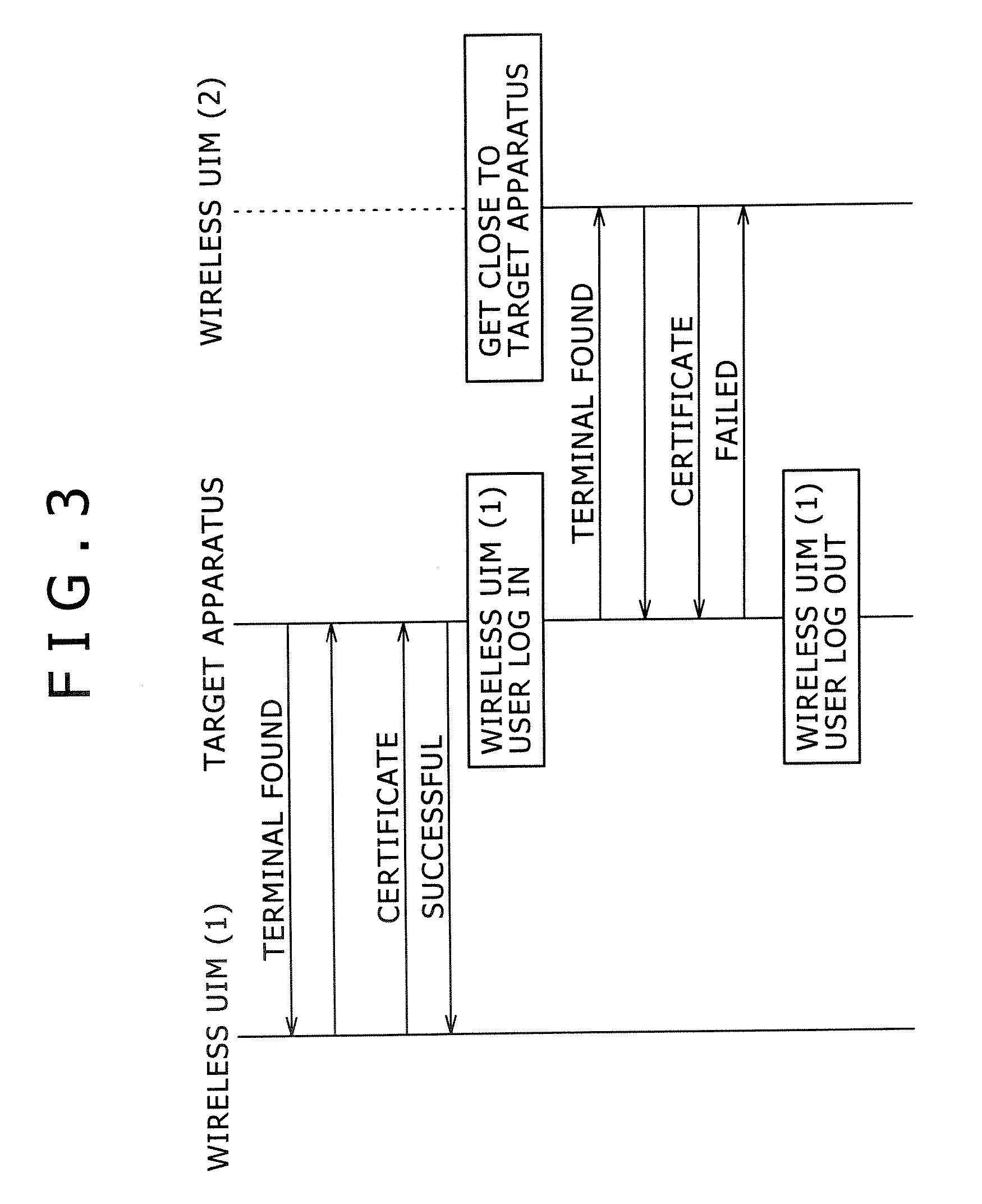
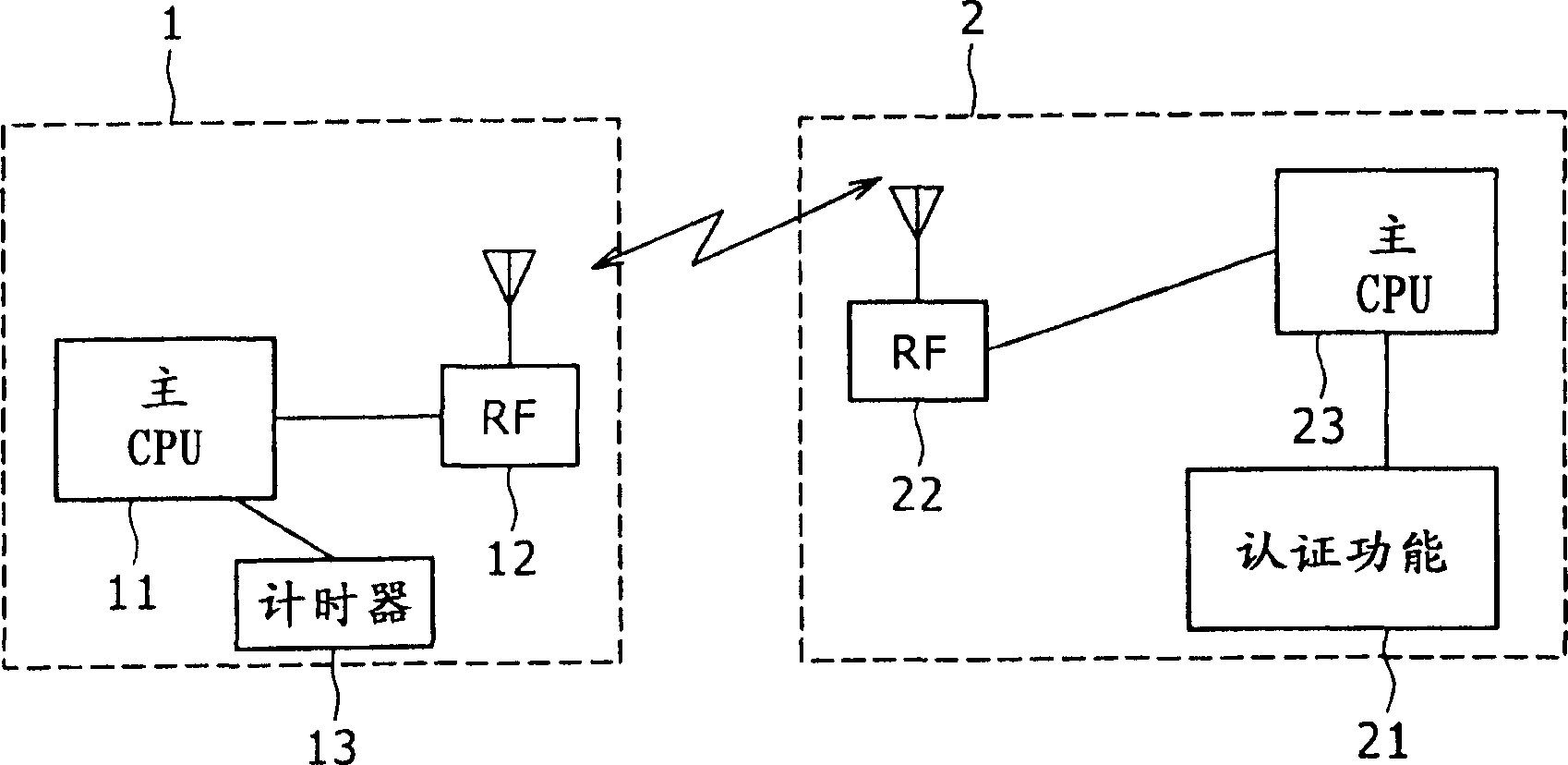
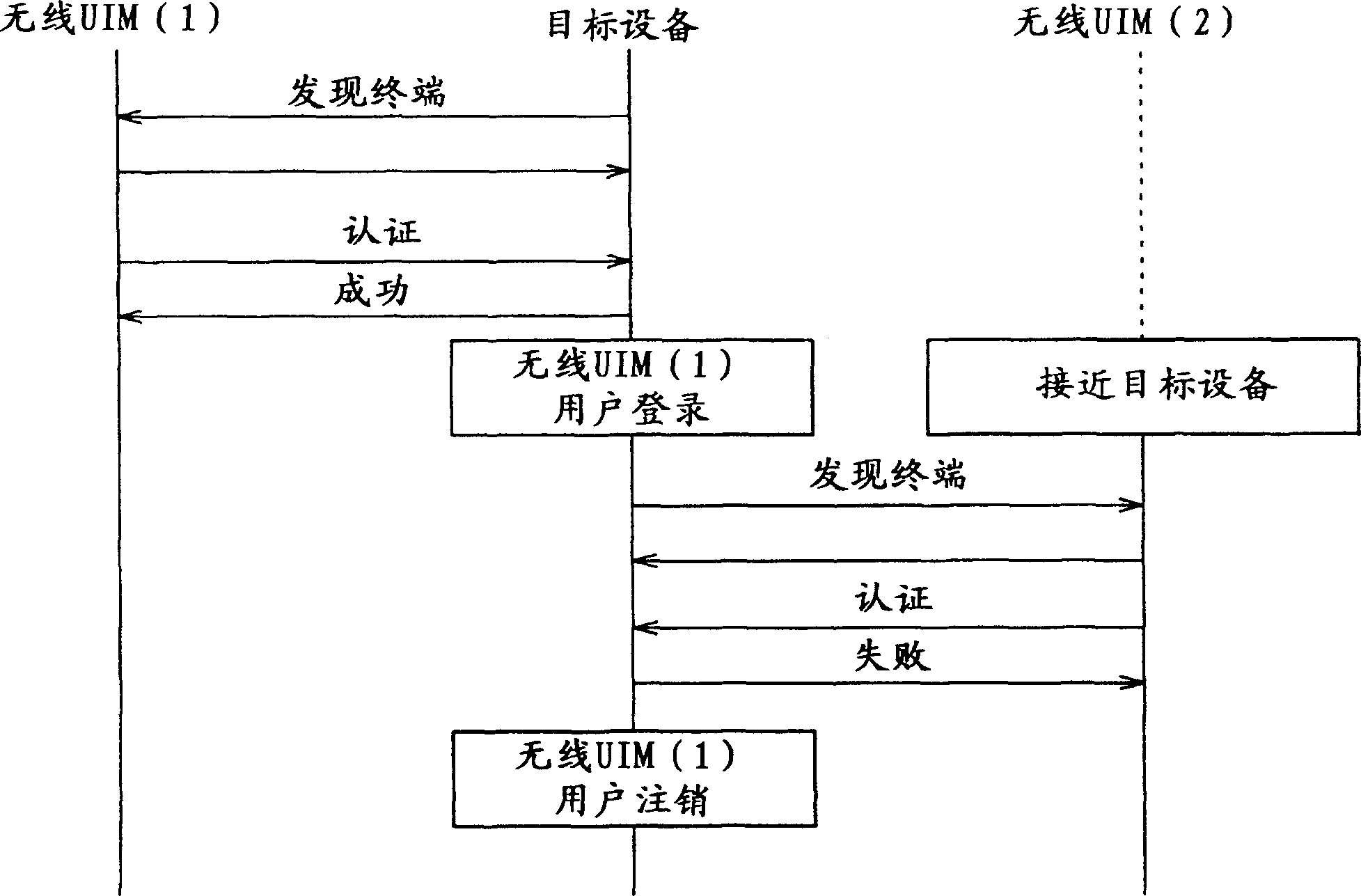
Target apparatus, certification device, and certification method
InactiveUS20070043950A1Improve user friendlinessReduce necessityUser identity/authority verificationDigital data authenticationEngineering
Owner:SONY CORP
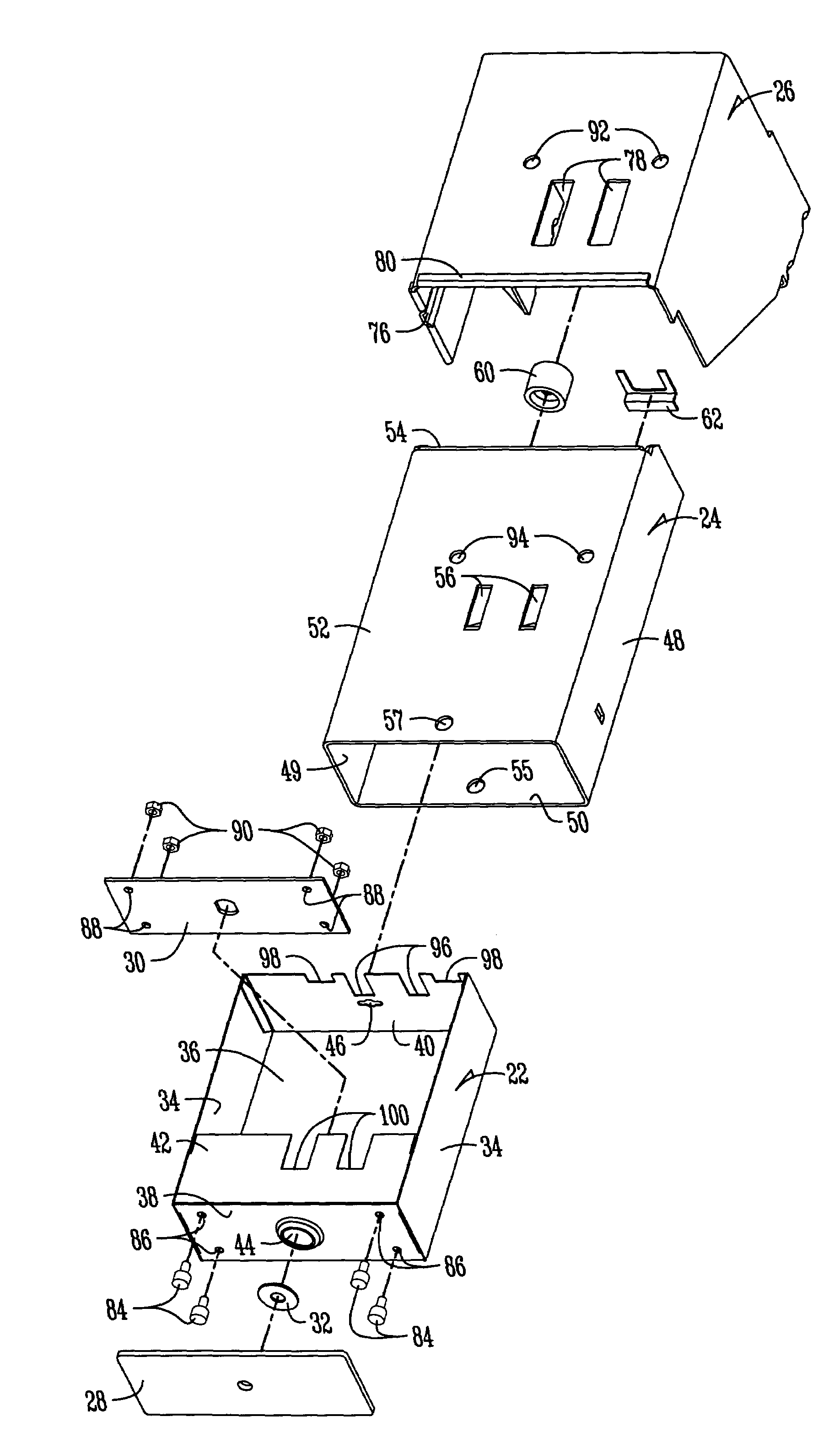
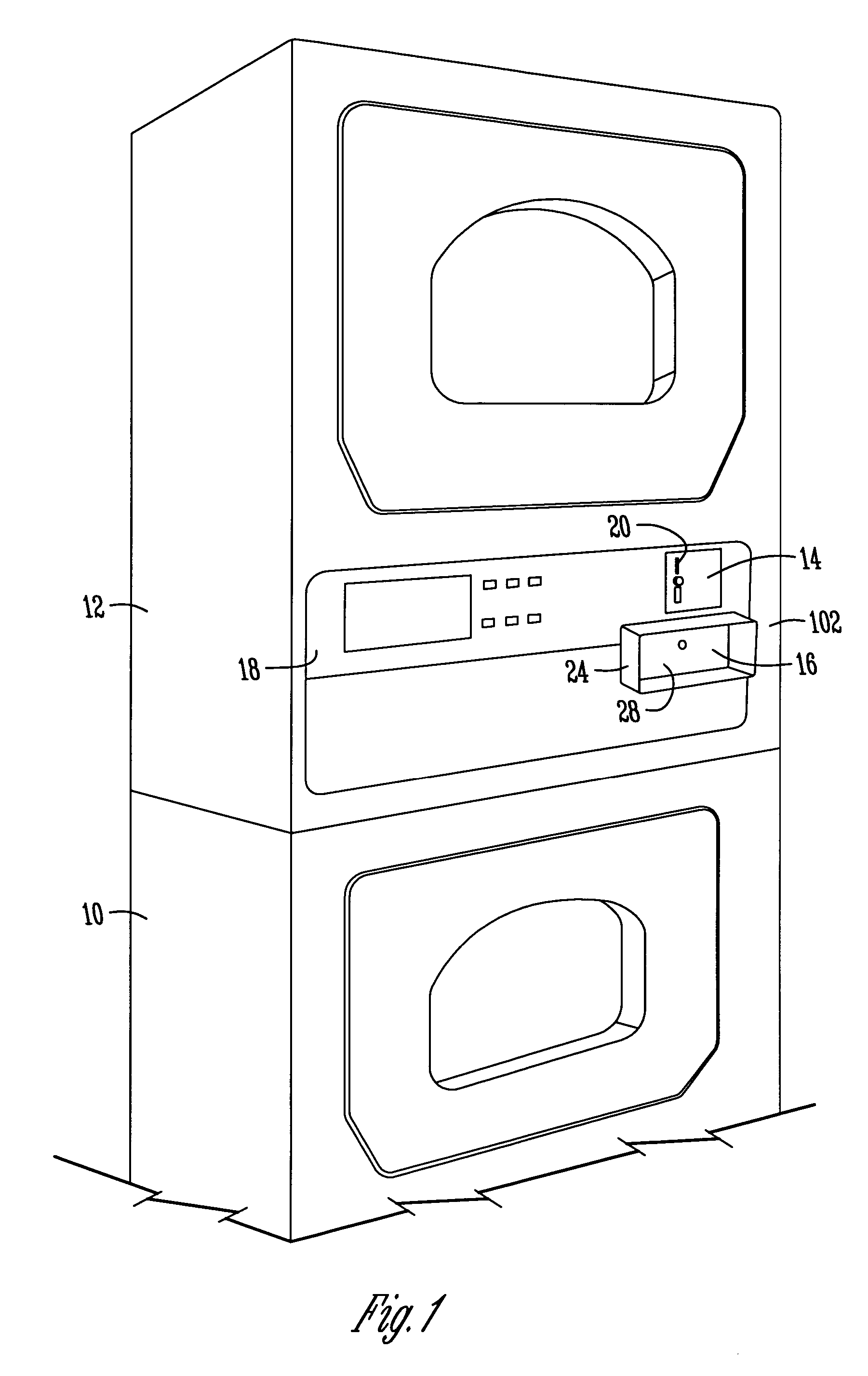
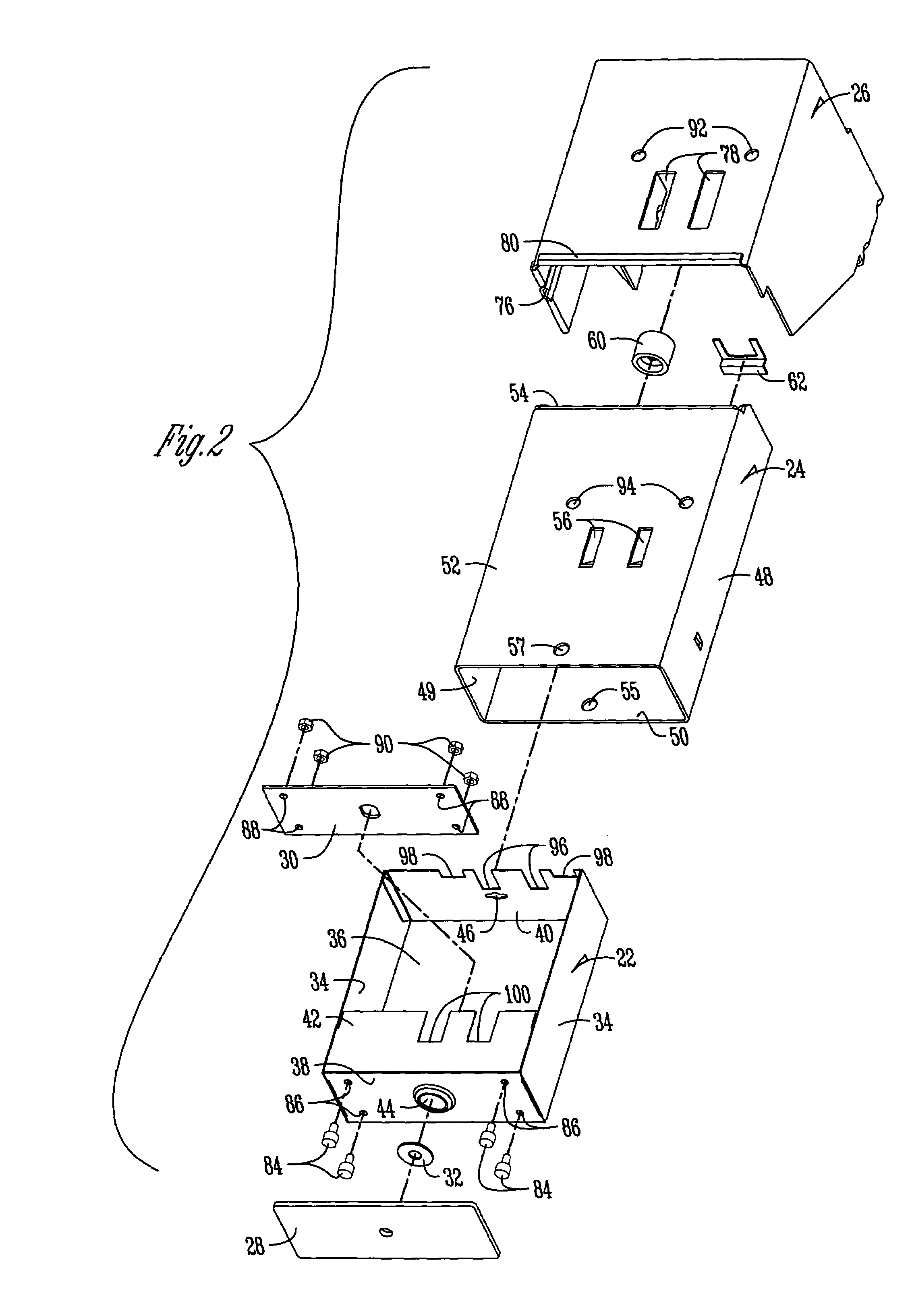
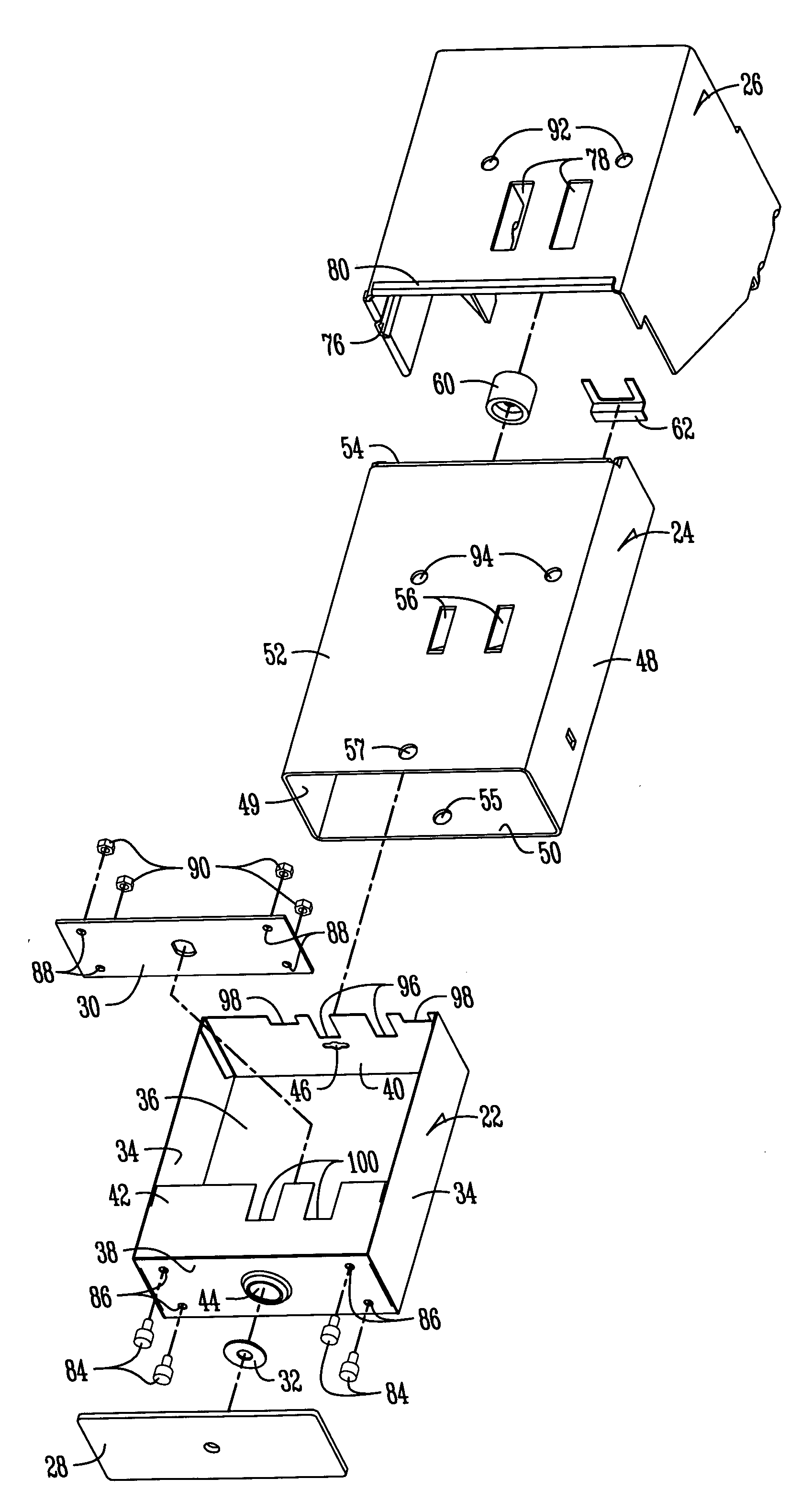
Coin vault for commercial appliances
An improved coin box assembly is provided for a coin operated laundry appliance. The assembly includes a mounting bracket mounted in the cabinet of the appliance, a vault mounted within the mounting bracket, and a coin box mounted within the vault. The mounting bracket and vault provide double-wall protection for the coin box so as to inhibit prying. The assembly further includes external and internal plates sandwiching the front wall of the coin box to prevent cutting of the front wall of the coin box. A freely-spinning washer is mounted between the front plate and the front wall of the coin box to preclude a hole saw from cutting out the lock cylinder of the coin box.
Owner:MAYTAG
Method and apparatus for protecting user privacy
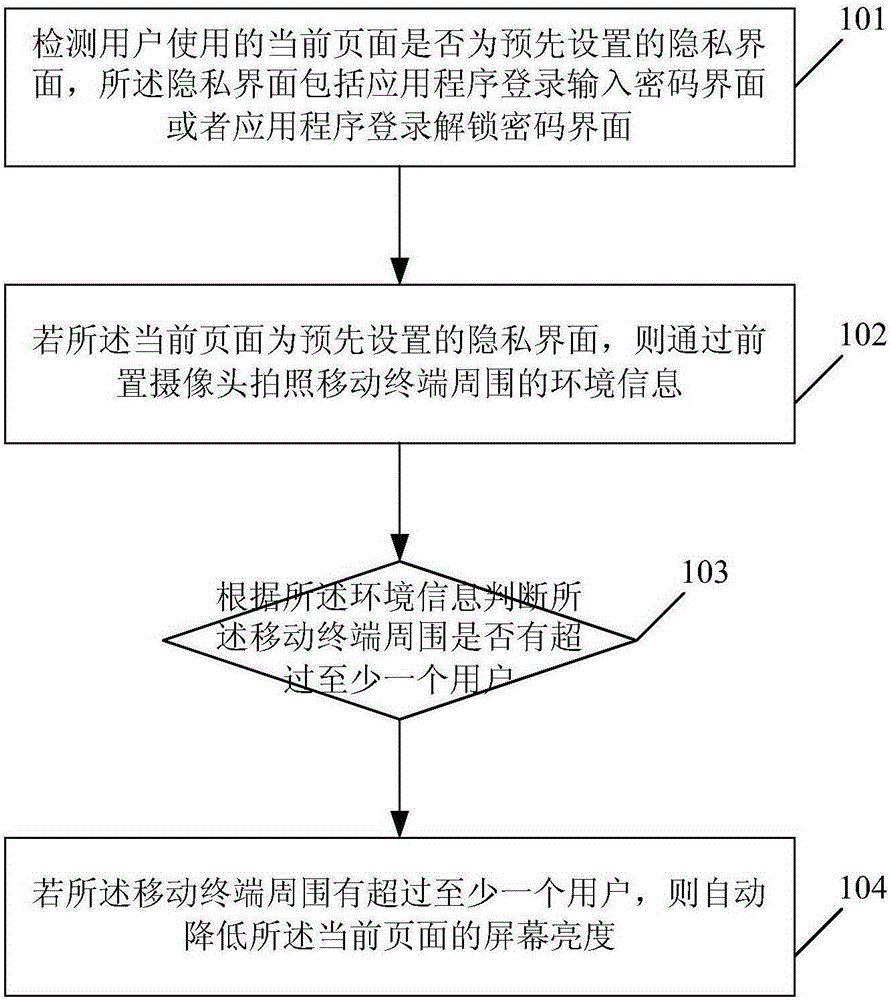
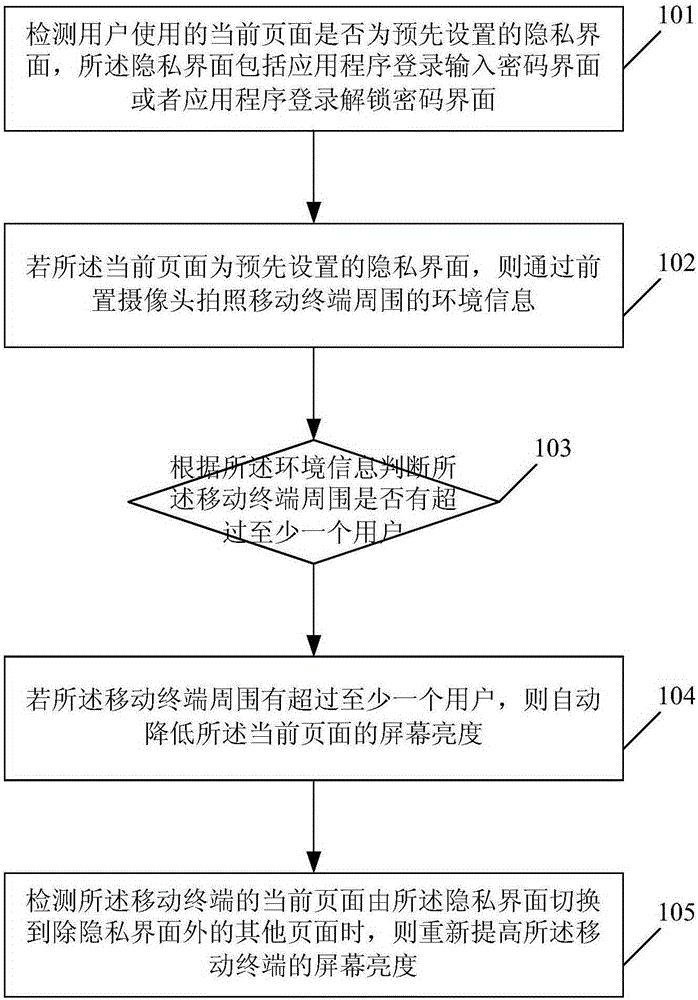
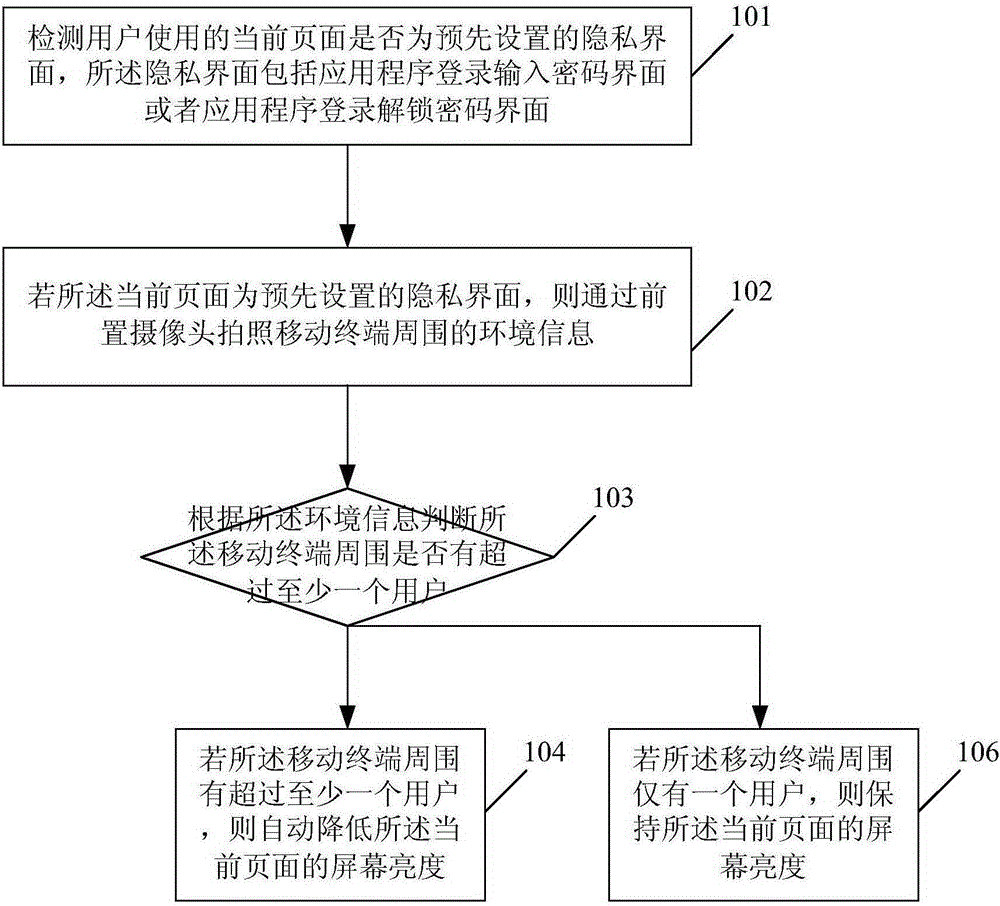
ActiveCN105260682AProtect privacy and property securityReduce brightnessInternal/peripheral component protectionInternet privacyPassword
Embodiments of the present invention disclose a method and an apparatus for protecting user privacy. The method comprises: detecting whether a current page used by a user is a preset privacy interface, wherein the privacy interface comprises an application login password input interface or an application login password unlocking interface; if the current page is the preset privacy interface, photographing environmental information around a mobile terminal by a front camera; according to the environmental information, determining whether more than at least one user is around the mobile terminal; and if more than at least one user is around the mobile terminal, automatically lowering screen brightness of the current page. According to the method and the apparatus provided by the present invention, whether a display interface of a smart device used by the user is the login password input interface or the password unlocking interface is recognized, and the brightness of a display screen is reduced, thereby preventing user password security from being spied by personnel around, protecting user privacy and property security, and improving security in use of the smart device.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Target apparatus, certification device, and certification method
InactiveCN1917423APrevent snoopingPrevent leakageUser identity/authority verificationDigital data protectionEngineering
Owner:SONY CORP
Coin vault for commercial appliances
An improved coin box assembly is provided for a coin operated laundry appliance. The assembly includes a mounting bracket mounted in the cabinet of the appliance, a vault mounted within the mounting bracket, and a coin box mounted within the vault. The mounting bracket and vault provide double-wall protection for the coin box so as to inhibit prying. The assembly further includes external and internal plates sandwiching the front wall of the coin box to prevent cutting of the front wall of the coin box. A freely-spinning washer is mounted between the front plate and the front wall of the coin box to preclude a hole saw from cutting out the lock cylinder of the coin box.
Owner:MAYTAG
Keyboard input encryption method and mobile terminal thereof
InactiveCN102880305AImprove encryption securityPrevent snoopingInternal/peripheral component protectionInput/output processes for data processingTerminal equipmentProcessing element
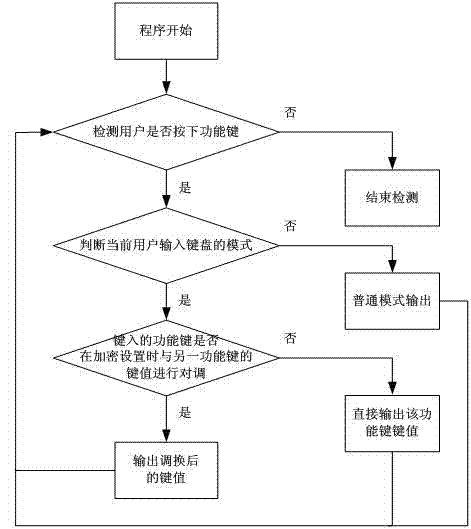
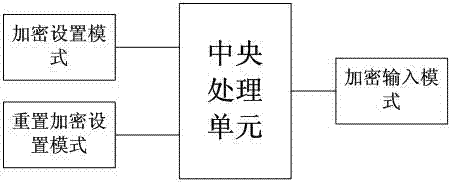
The invention discloses a keyboard input encryption method and terminal equipment thereof. The mobile terminal comprises an encryption setting module, a resetting encryption setting module, an encryption input module and a central processing unit. The method comprises the following steps of: (a) detecting whether a user presses a functional key, and if the user presses the functional key, executing the next step, otherwise, ending the detection; (b) judging a mode of the current user input keyboard by a system, if the mode is a common mode, directly outputting a typed functional key value through a keyboard, and if the mode is an encryption input mode, executing the next step; (c) judging whether the typed functional key value is exchanged with a key value of another functional key during encryption, if so, executing the next step, otherwise, directly outputting the functional key value; and (d) outputting the exchanged key value, and returning to the step (a). Aiming at a situation that a user uses mobile phone application to input sensitive information under a complicated environment, the encryption security of an input method is realized; a phenomenon that sensitive information acquired by the user is pried is avoided; fund loss of the user is prevented; and therefore, the user can securely execute relevant operation with a mobile phone, and the security of the mobile phone is also improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Terminal and method for safely utilizing same
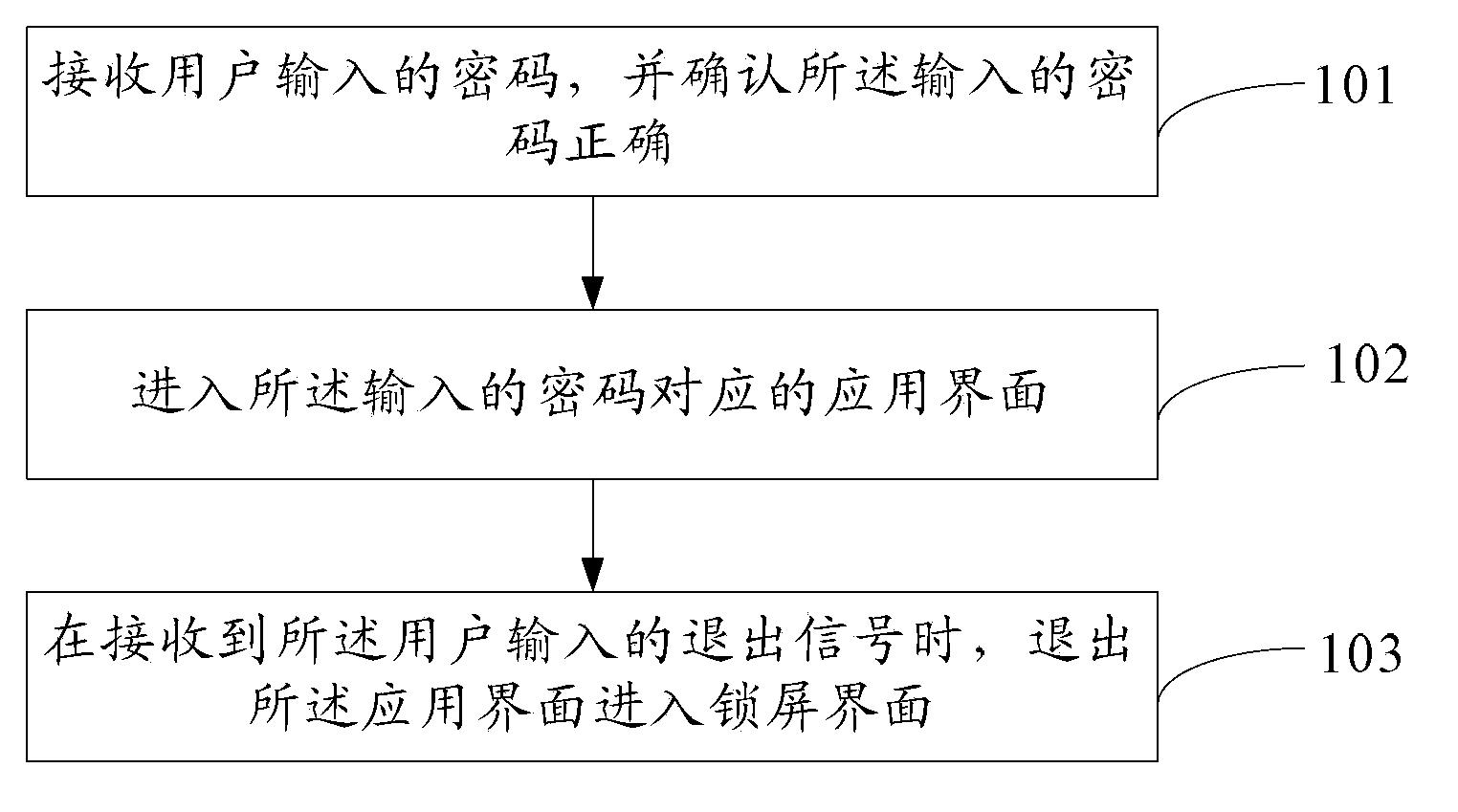
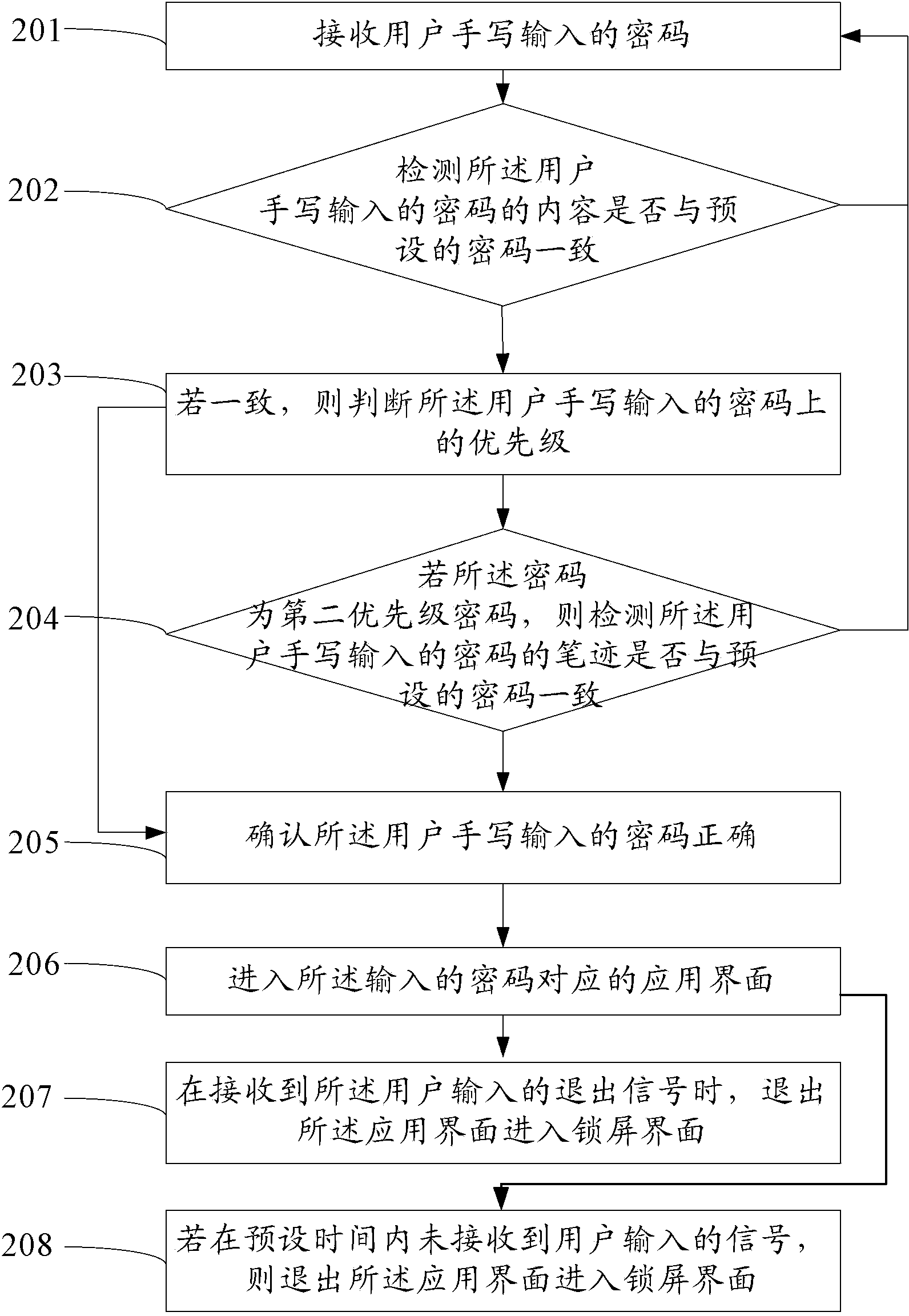
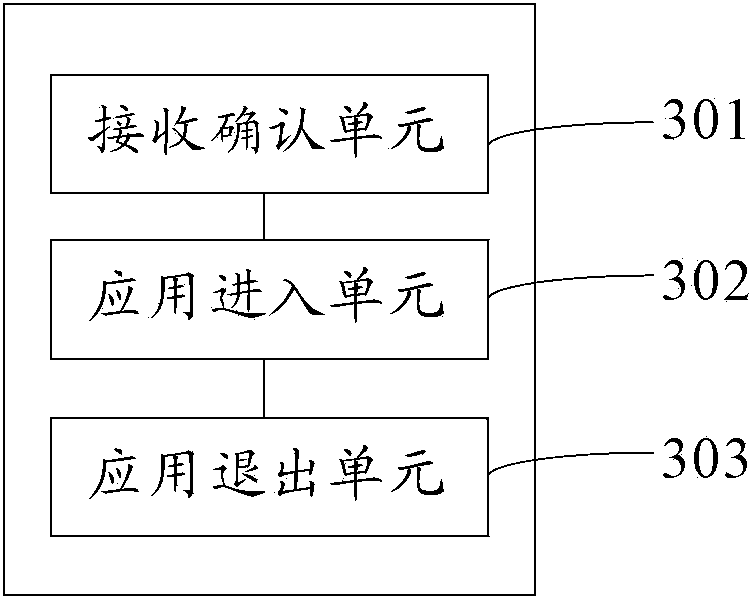
ActiveCN103886232ASafe to usePrevent snooping of user informationDigital data authenticationPasswordComputer science
An embodiment of the invention provides a terminal and a method for safely utilizing the same, and relates to the technical field of mobile terminals. The method includes receiving a password inputted by a user and confirming the correctness of the inputted password; entering an application interface corresponding to the inputted password; withdrawing from the application interface when a withdrawal signal inputted by the user is received, and entering a screen lock interface. The terminal and the method have the advantages that other people can be prevented from snooping information stored in the terminal of the user, and accordingly the information is safe.
Owner:LENOVO (BEIJING) CO LTD
Window structure body
InactiveCN104662248AMake sure to look outPrevent snoopingMechanical apparatusMirrorsOptoelectronicsGlass sheet
Owner:MIRAI KIKAKU
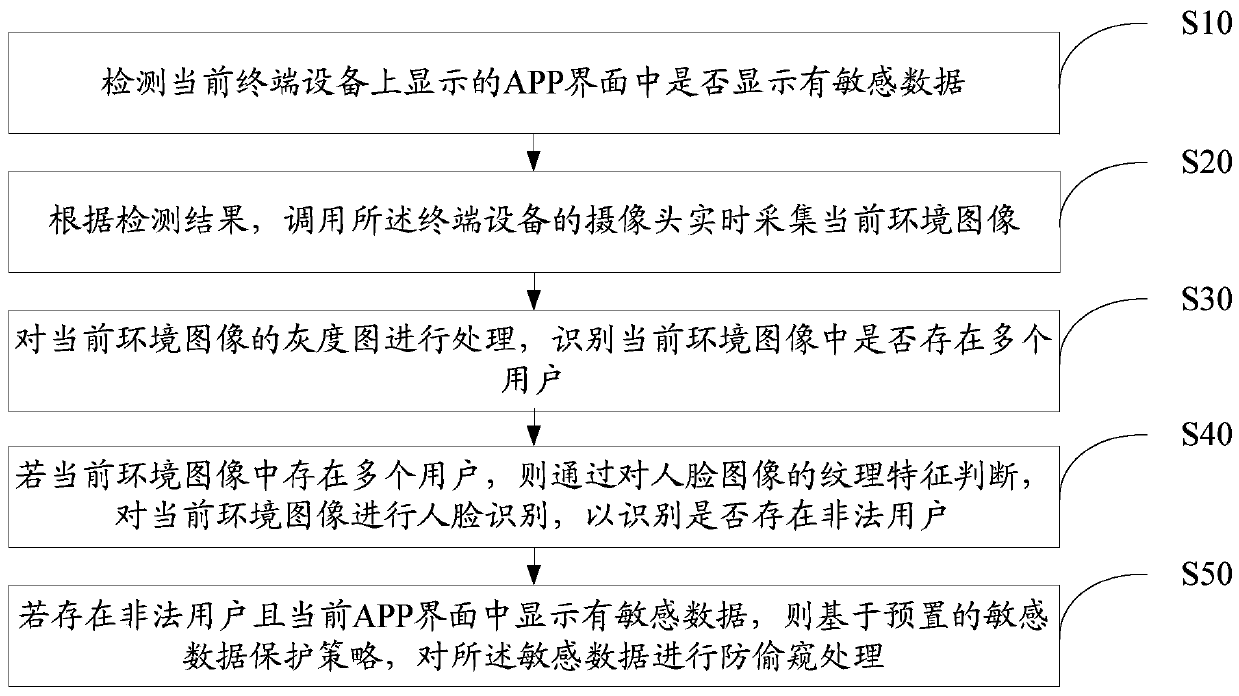
Sensitive data anti-peeping processing method and device, equipment and storage medium
PendingCN110135262ARealize automatic protectionImprove user experienceCharacter and pattern recognitionInternal/peripheral component protectionData displayPattern recognition
The invention relates to the technical field of artificial intelligence, and discloses a sensitive data anti-peeping processing method, which comprises the following steps: detecting whether sensitivedata is displayed in an APP interface displayed on current terminal equipment; if yes, calling a camera of the terminal device to collect a current environment image in real time; processing the grayscale image of the current environment image, and identifying whether a plurality of users exist in the current environment image or not; if a plurality of users exist in the current environment image, performing face recognition on the current environment image by judging the texture features of the face image so as to recognize whether illegal users exist or not; and if an illegal user exists and sensitive data is displayed in the current APP interface, performing anti-peeping processing on the sensitive data based on a sensitive data protection strategy. The invention further discloses a sensitive data anti-peeping processing device and equipment and a computer readable storage medium. An illegal user can be prevented from peeping sensitive information of others, and then the security of sensitive data display of the user is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Multi-role application method and device for terminal, readable storage medium of computer and terminal
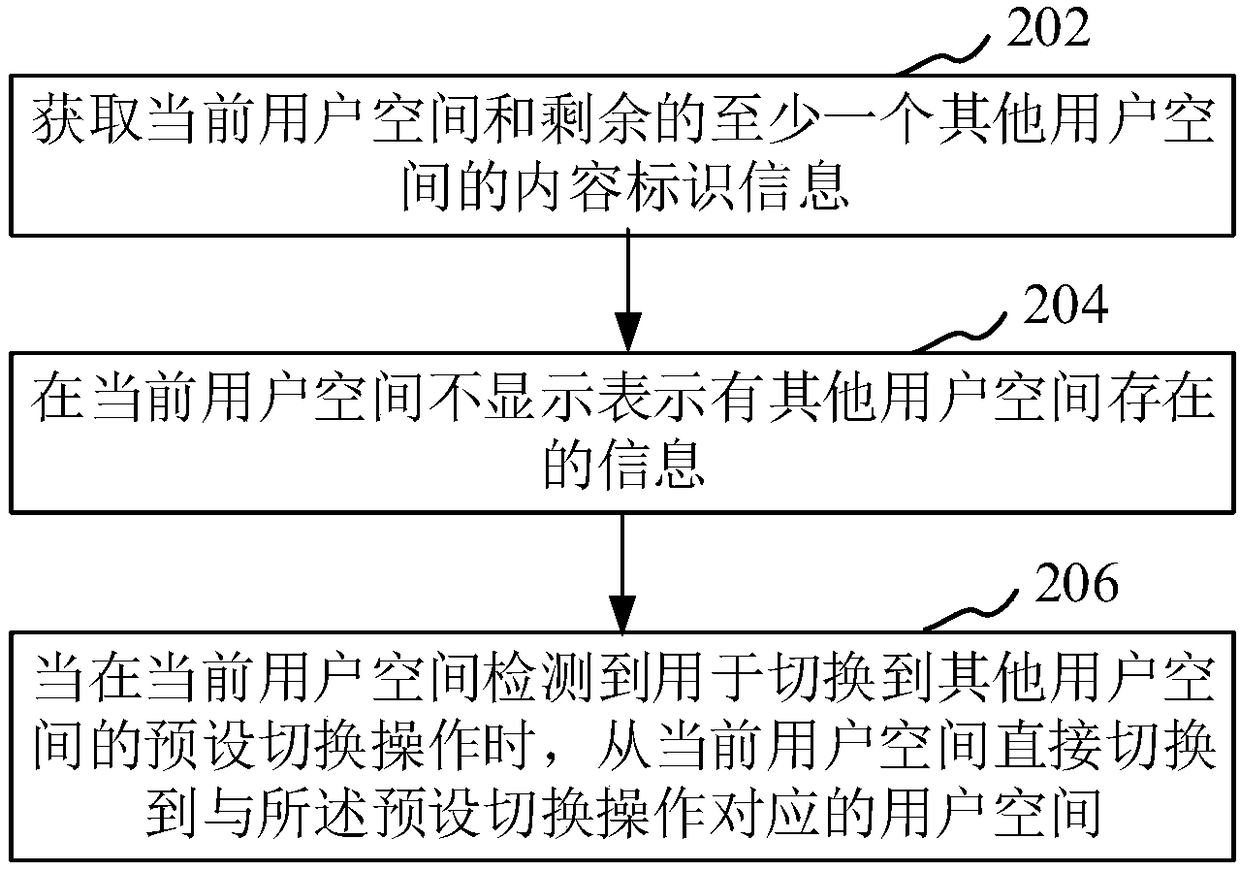
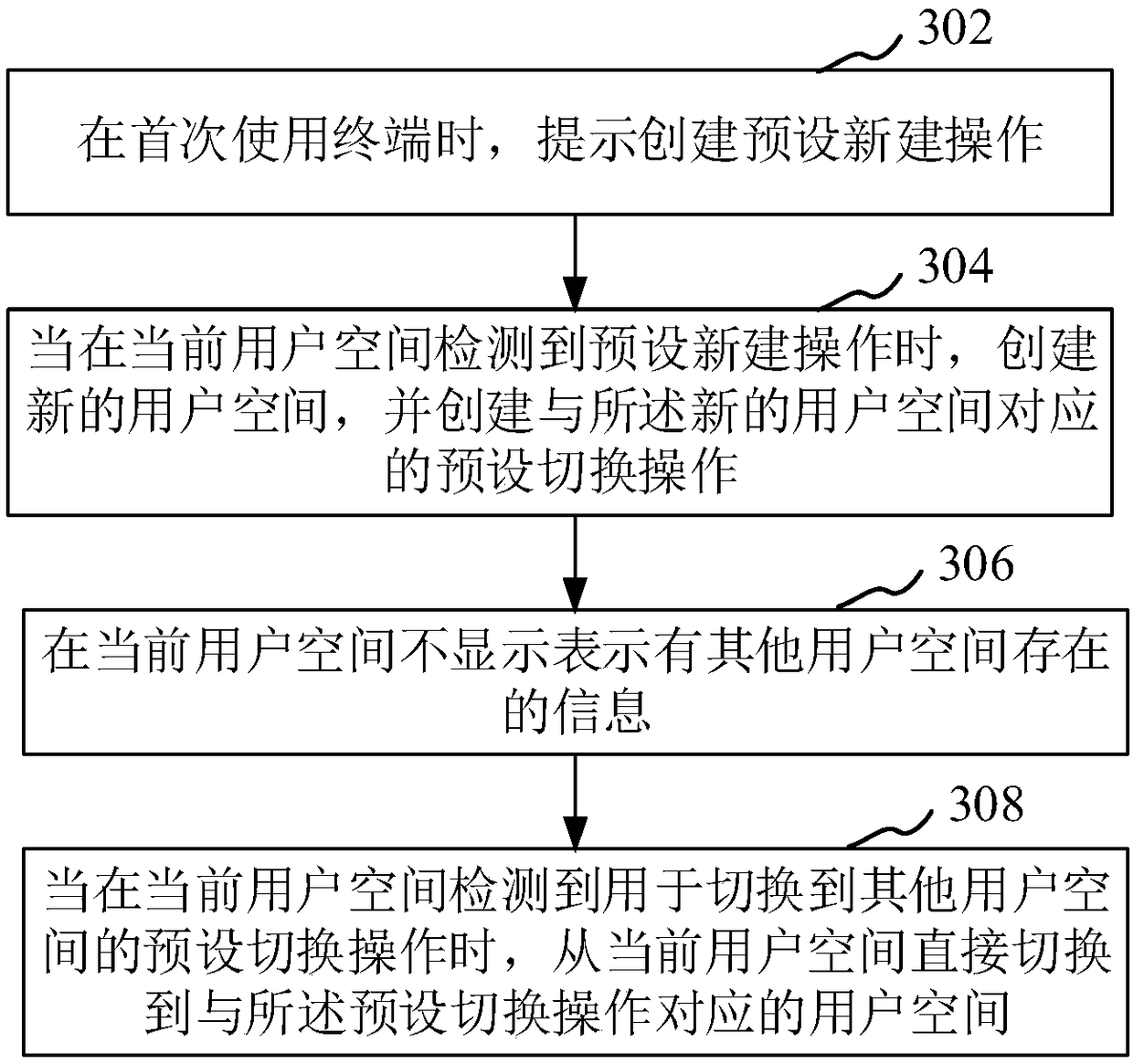
InactiveCN108537058AAvoid embarrassmentMeet the needs of useDigital data protectionDigital data authenticationCurrent userUser space
The application relates to a multi-role application method and device for a terminal, a readable storage medium of a computer and the terminal. The method comprises the following steps: not displayinginformation expressing the presence of other user spaces in a current user space; and directly switching from the current user space to a user space corresponding to pre-set switch operation when thecurrent user space detects pre-set switch operation used for switching other user spaces in the current user space. By not displaying the presence of other user spaces in the current user space, a user that has no idea about what happens does not know the presence of other user spaces, thereby avoiding snooping of other user spaces. Additionally, a current user does not feel embarrassed when other people know configuration of other user spaces. By performing pre-set switch operation, user spaces can be switched, thereby meeting the application demand of multi-role spaces.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
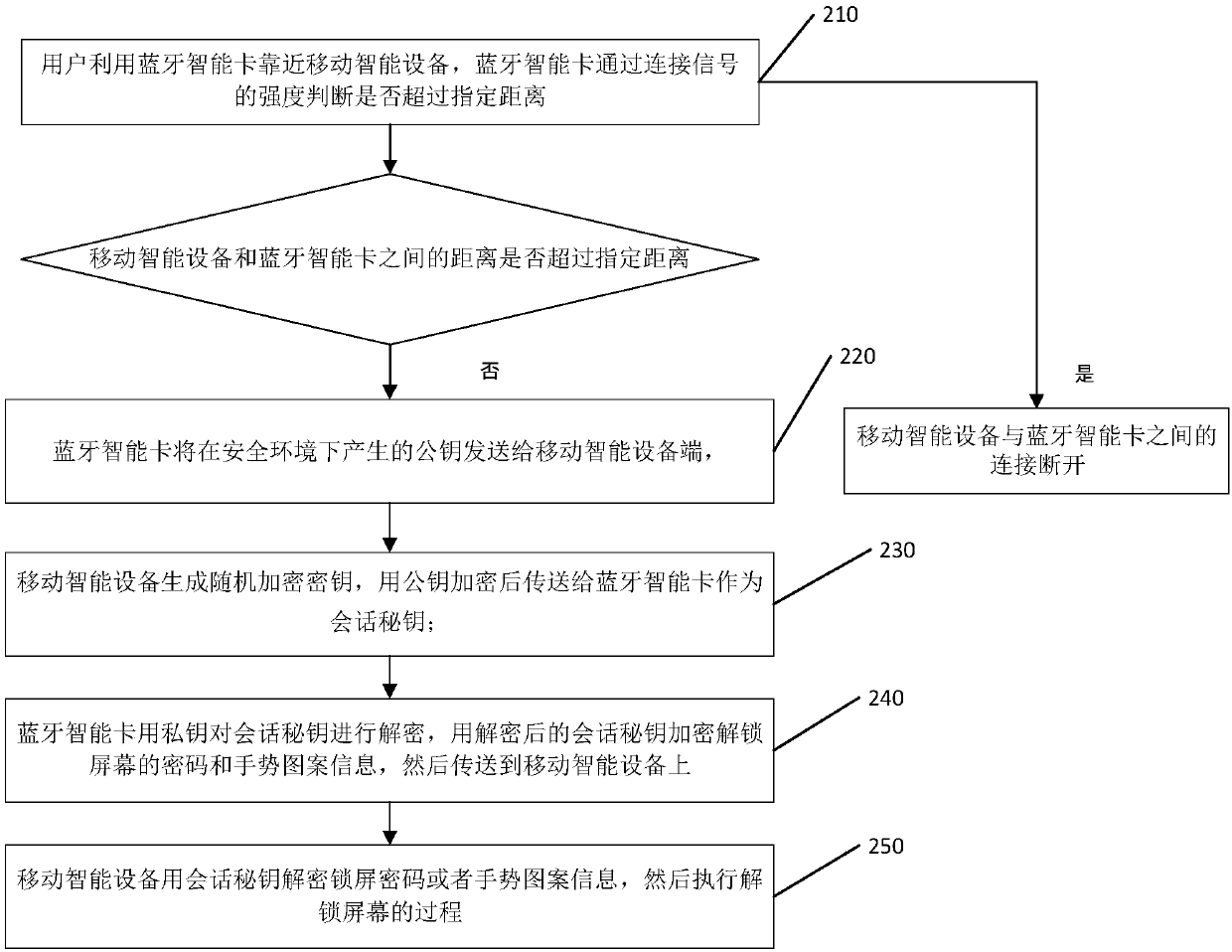
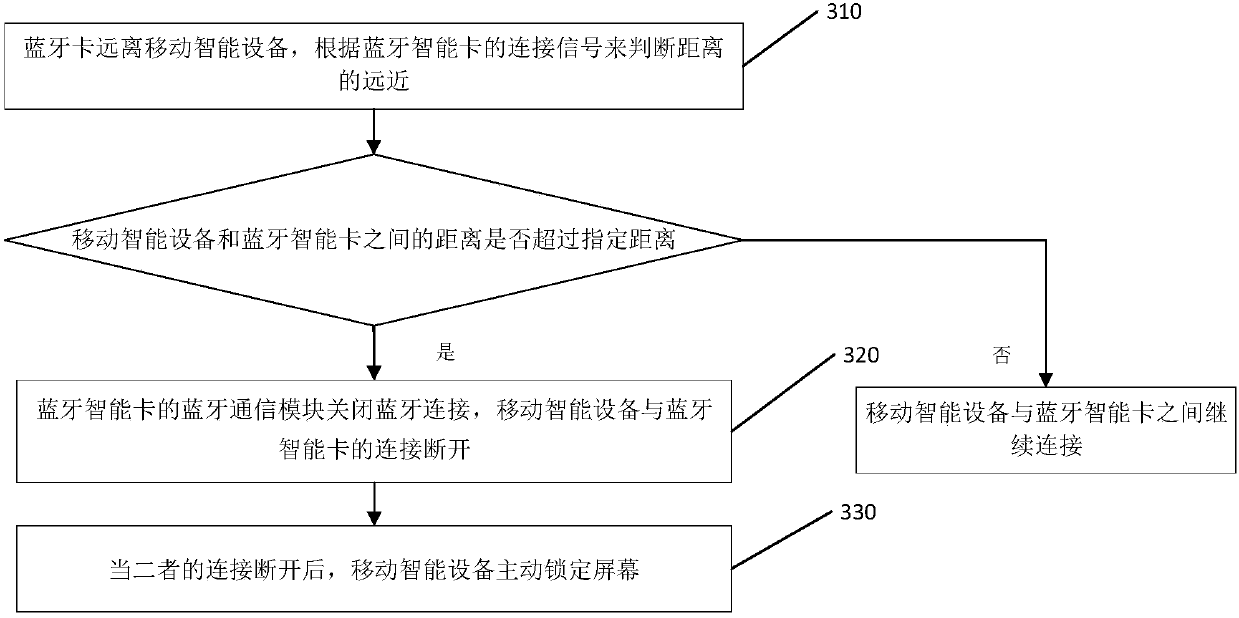
Method for unlocking and locking mobile intelligent equipment and Bluetooth intelligent card
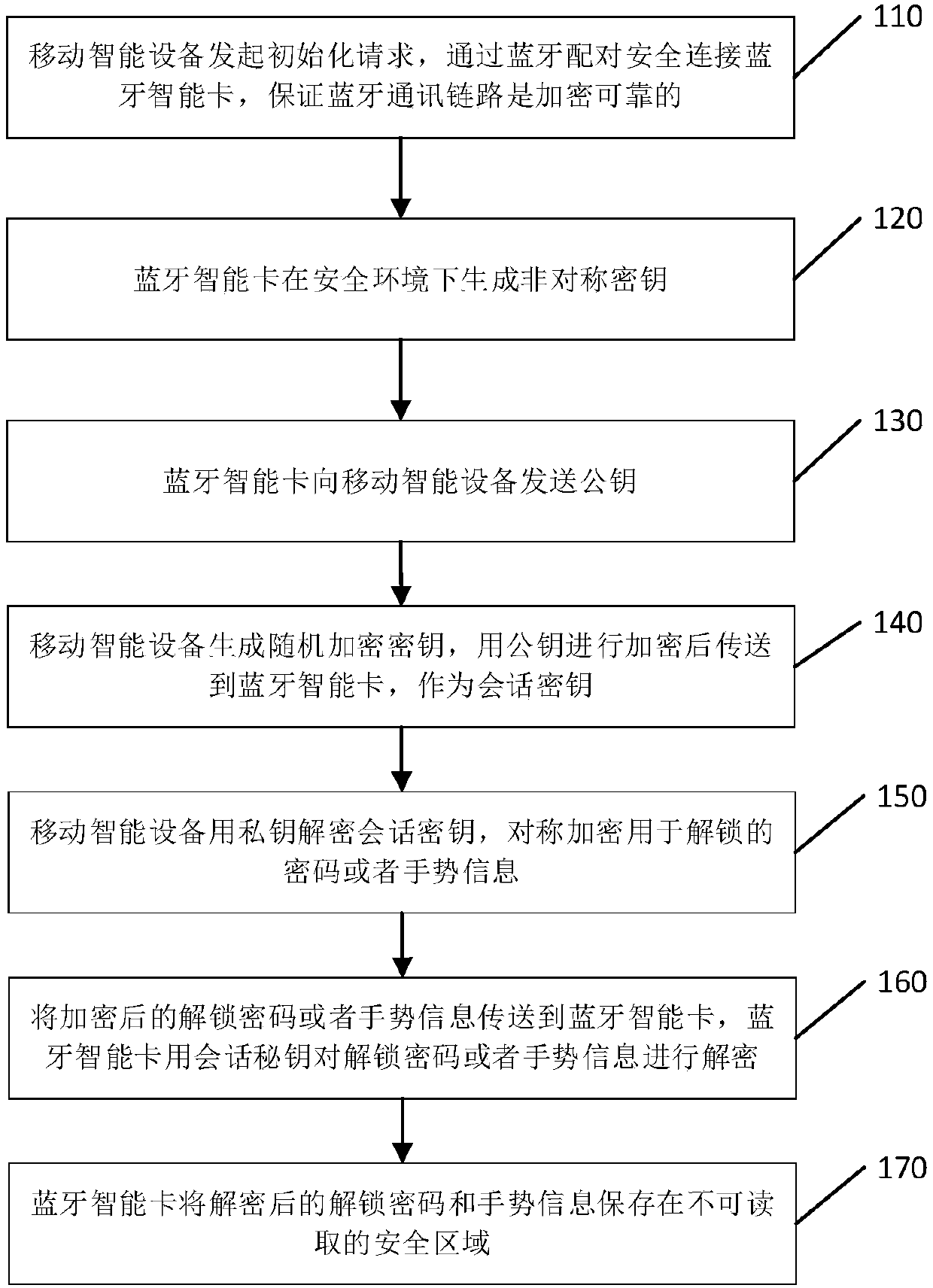
InactiveCN107690030AImprove experiencePrevent snoopingNear-field transmissionSubstation equipmentSmallerThanSmart card
The application discloses a method for unlocking and locking mobile intelligent equipment by utilizing a Bluetooth intelligent card and a Bluetooth intelligent card. The method comprises the steps that: the Bluetooth intelligent card is close to the mobile intelligent equipment and determines whether a distance between the Bluetooth intelligent card and the mobile intelligent equipment is smallerthan a specified distance according to intensity of a received signal; if the distance between the Bluetooth intelligent card and the mobile intelligent equipment is smaller than the specified distance, the Bluetooth intelligent card generates an asymmetrical secret key in a safe environment and sends a public key to the mobile intelligent equipment; the Bluetooth intelligent card receives a random encrypted secret key which is transmitted by the mobile intelligent equipment and encrypted by the public key and the random encrypted secret key is used as a first session secret key; and the Bluetooth intelligent card decrypts the first session secret key by a private key, carries out encryption on unlocking information by the decrypted first session secret key, and transmits the decrypted unlocking information to the mobile intelligent equipment, so that the mobile intelligent equipment executes unlocking of a screen by utilizing the decrypted unlocking information. According to the application, as long as the mobile intelligent equipment is close to the Bluetooth intelligent card, unlocking and locking of the screen can be automatically implemented.
Owner:HENGBAO
Attachment mount and receiver system for removably attaching articles to garments
An attachment mount and receiver system for attaching articles to a garment. A receiver has openings for affixing the receiver to a support that is then attached to a compatible garment. The mount has openings for affixing an article thereto. A pair of flexible springs permit connected tines to be compressed inwardly, allowing the mount to be slidingly inserted into the receiver. A barb at the end of each tine engages an end wall of the receiver when the mount is fully seated. Tines are compressed inwardly and the mount is withdrawable. Selective locks can inhibit the tines from being compressed. Resistance to prying the mount away from the receiver is also provided.
Owner:PREZINE LLC A LIMITED LIABILITY COMPANY OF FLORIDA
Electric power steering device
InactiveUS9638307B2Prevent the leaf spring from impedingFeel goodGearboxesBall bearingsElectric power steeringEngineering
An electric power steering device includes a worm which is swingably connected to the rotation shaft of an electric motor through a joint. A first end portion and second end portion of the worm are supported by a first bearing and a second bearing, respectively. A pair of elastic members elastically urge the worm to an axial neutral position. An annular leaf spring which is held by a housing urges the second end portion toward a worm wheel through the second bearing. A synthetic resin member having a sliding contact surface which is in contact with the leaf spring is integrally disposed on the second bearing.
Owner:JTEKT CORP
Angle-adjustable multifunctional computer display
PendingCN114020101APlay a protective rolePrevent snoopingMachine framesDigital data processing detailsComputer hardwareComputer graphics (images)
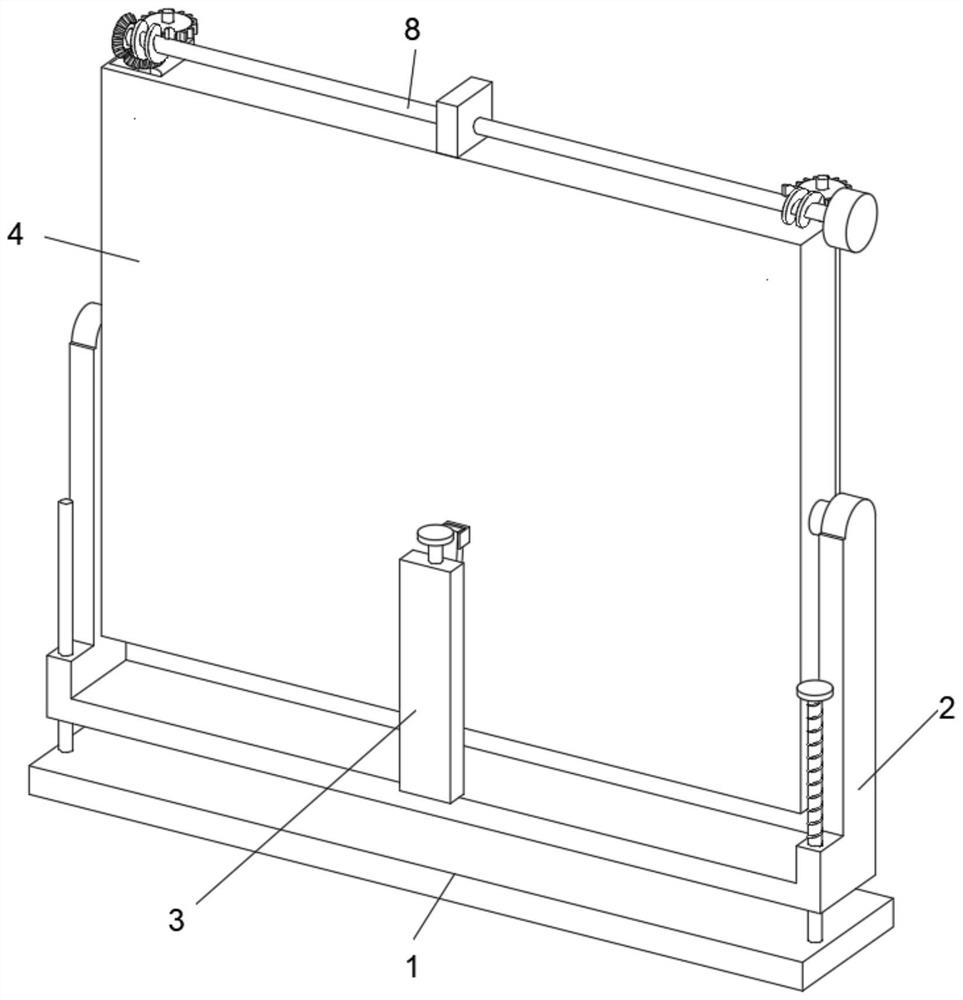
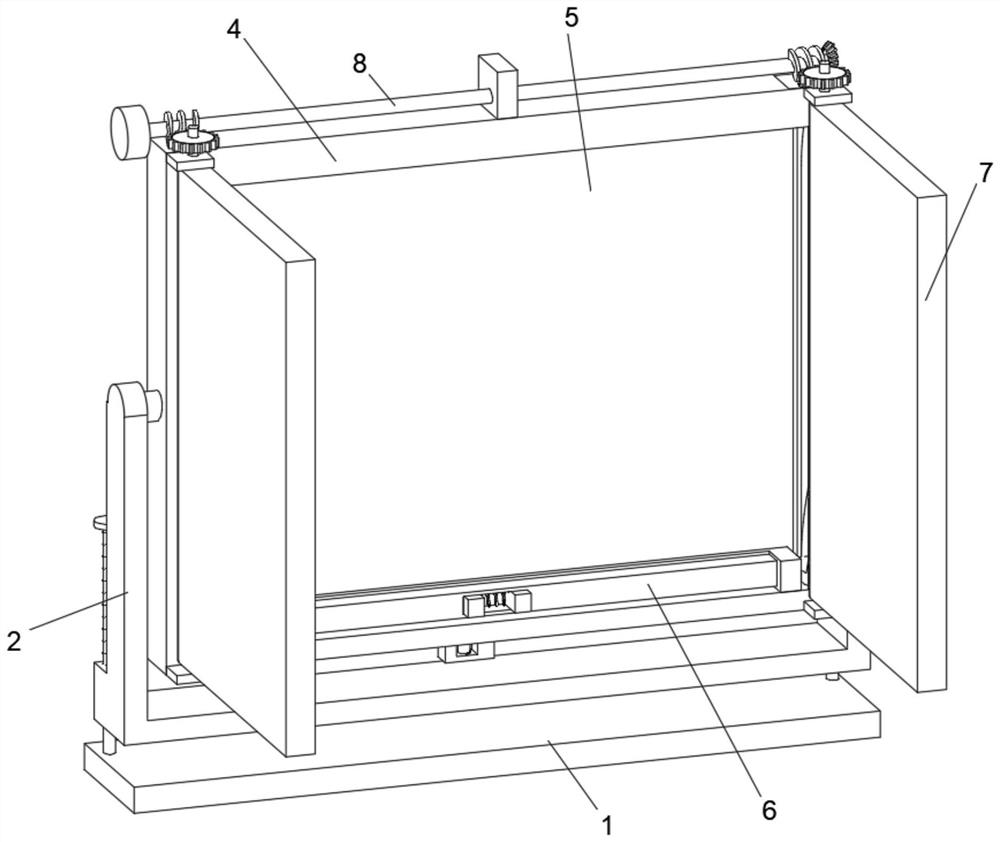
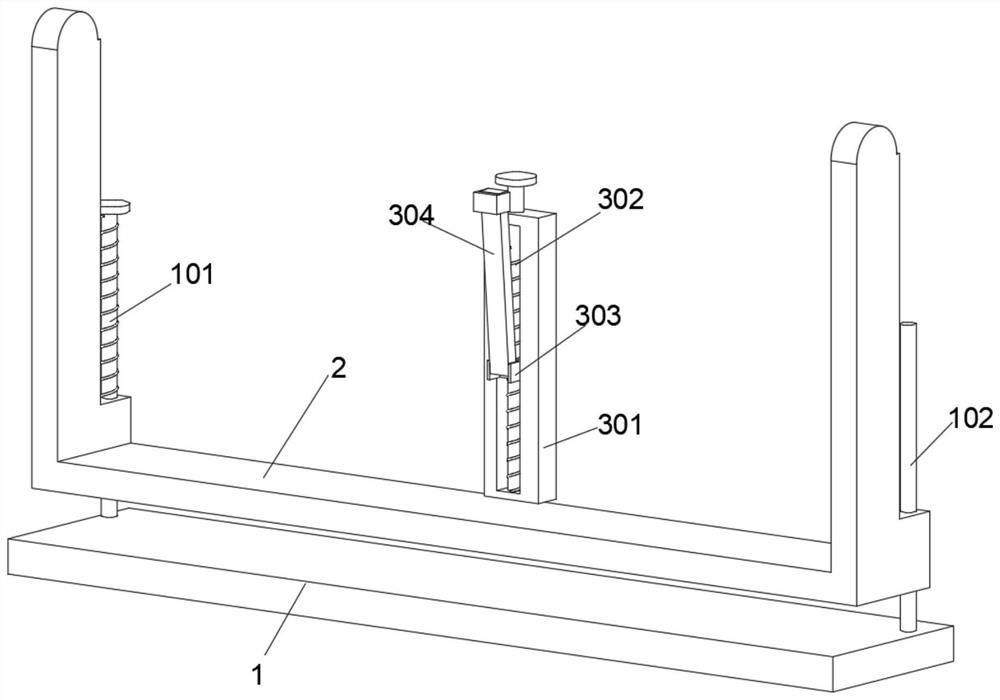
The invention discloses an angle-adjustable multifunctional computer display, and belongs to the technical field of computers. An angle-adjustable multifunctional computer display comprises a base, a fixing frame is arranged above the base, an adjusting assembly is connected to the top face of the rear side of the fixing frame, a mounting plate is arranged above the fixing frame, a display screen is mounted on the inner wall of the front side of the mounting plate, a cleaning assembly is arranged on the front side of the lower end of the mounting plate, and two privacy plates are arranged on the front wall of the mounting plate in a bilateral symmetry mode. By arranging the privacy plate, when the display screen is transported, the display screen can be protected inside, other objects are prevented from colliding with the privacy plate, the display screen is effectively protected, meanwhile, when the privacy plate is used, the two sides of the display screen can be shielded, the display content is prevented from being easily snooped by others during use, and the privacy of the device is greatly improved.
Owner:温学勤
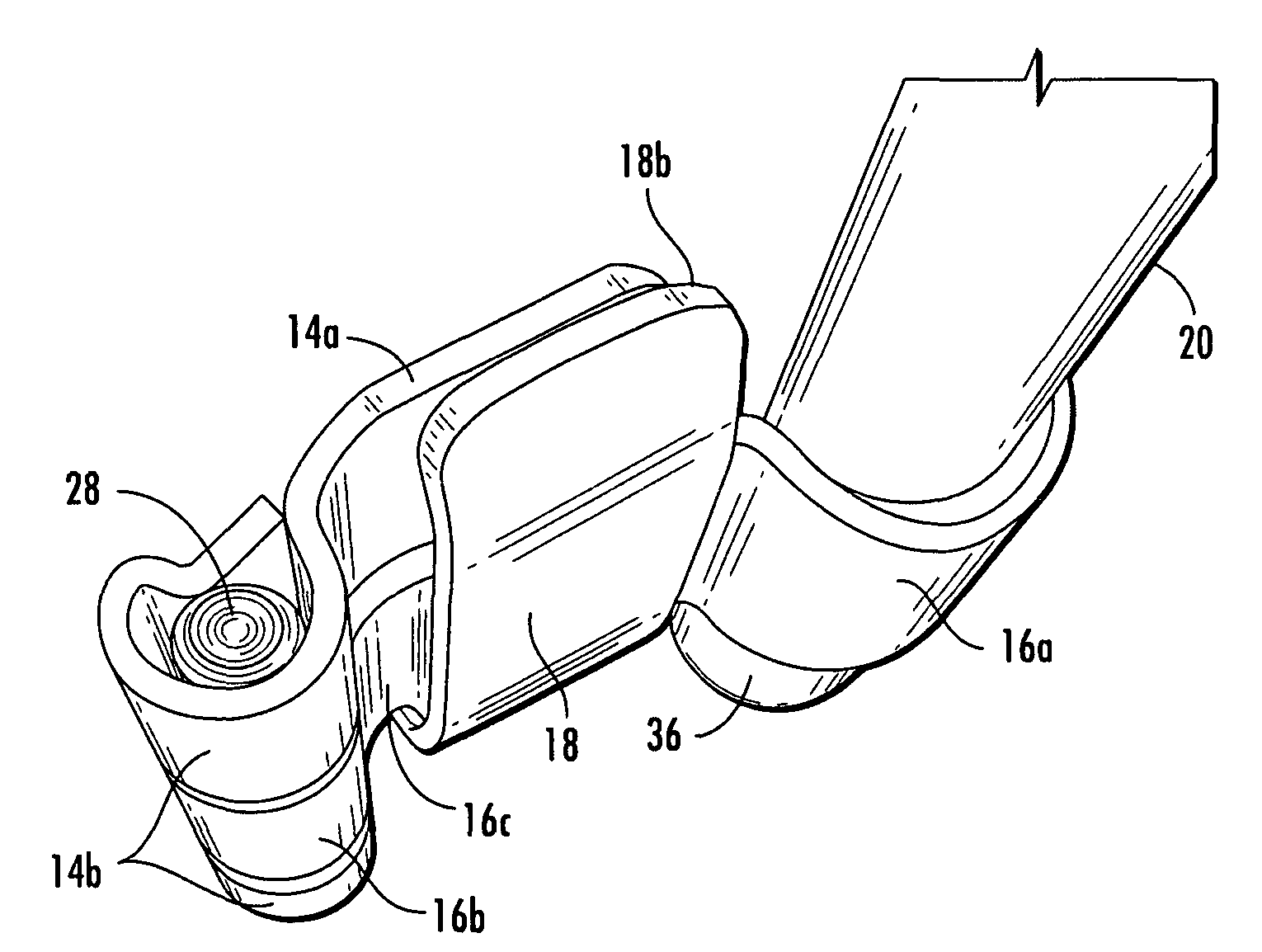
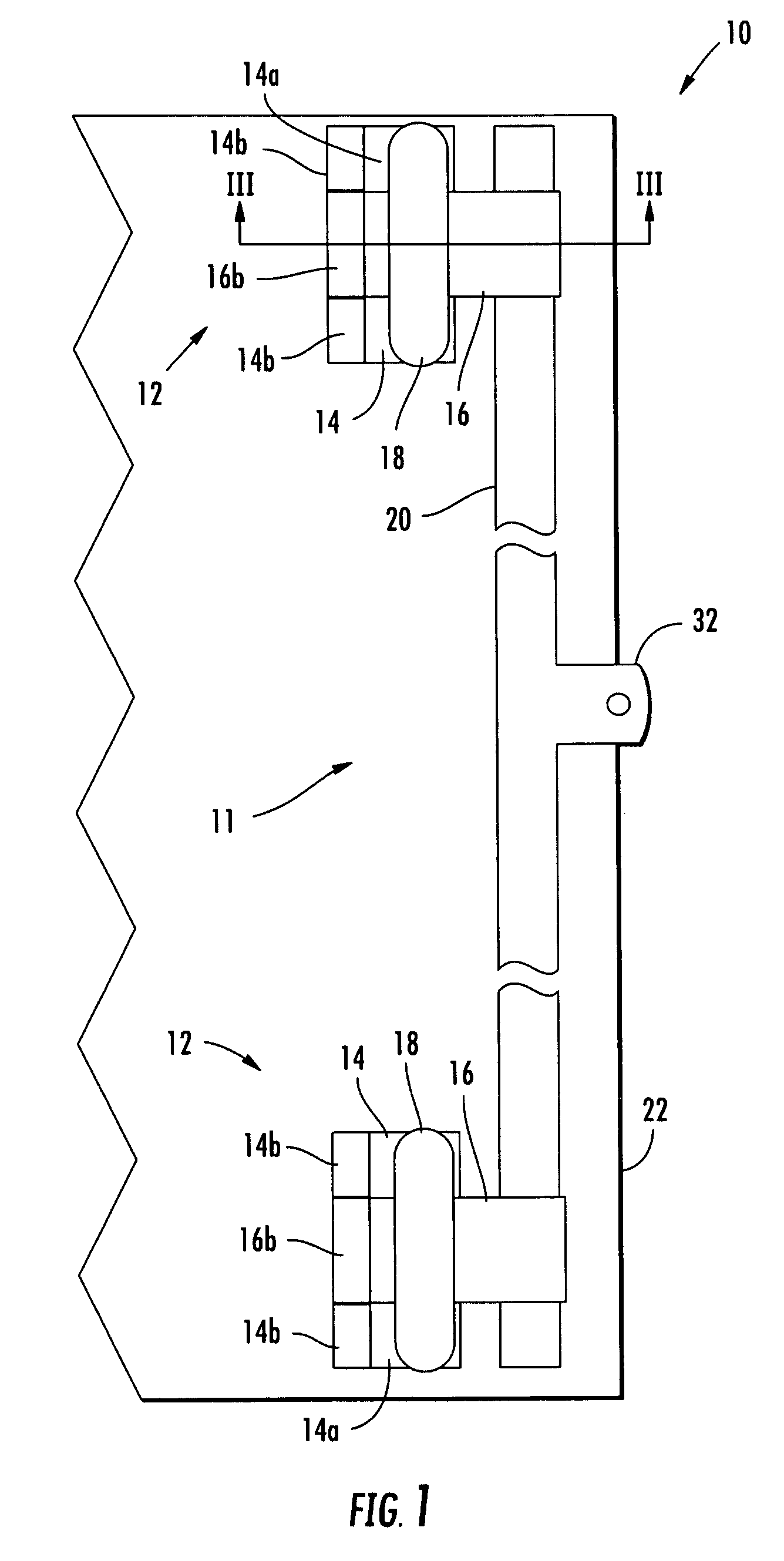
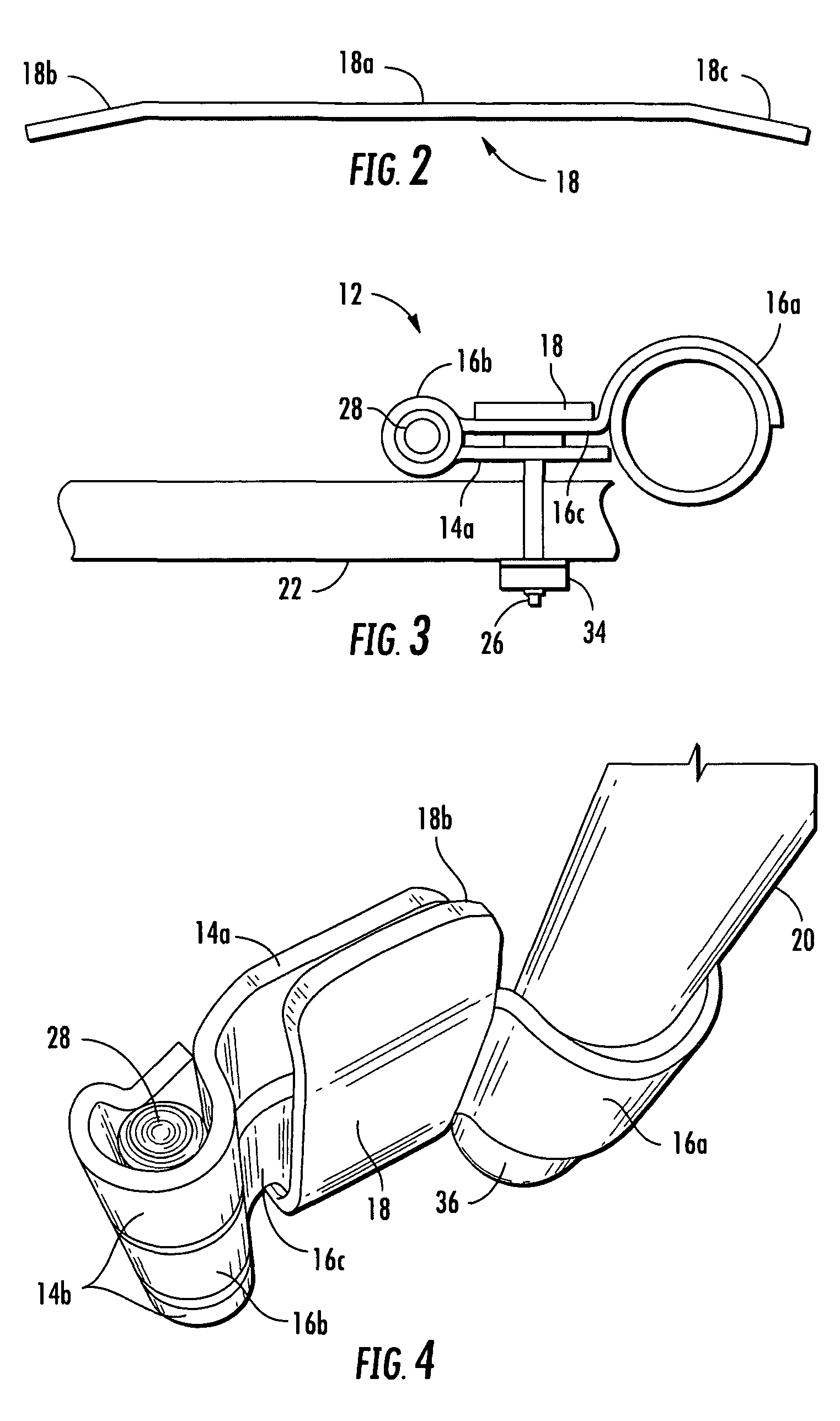
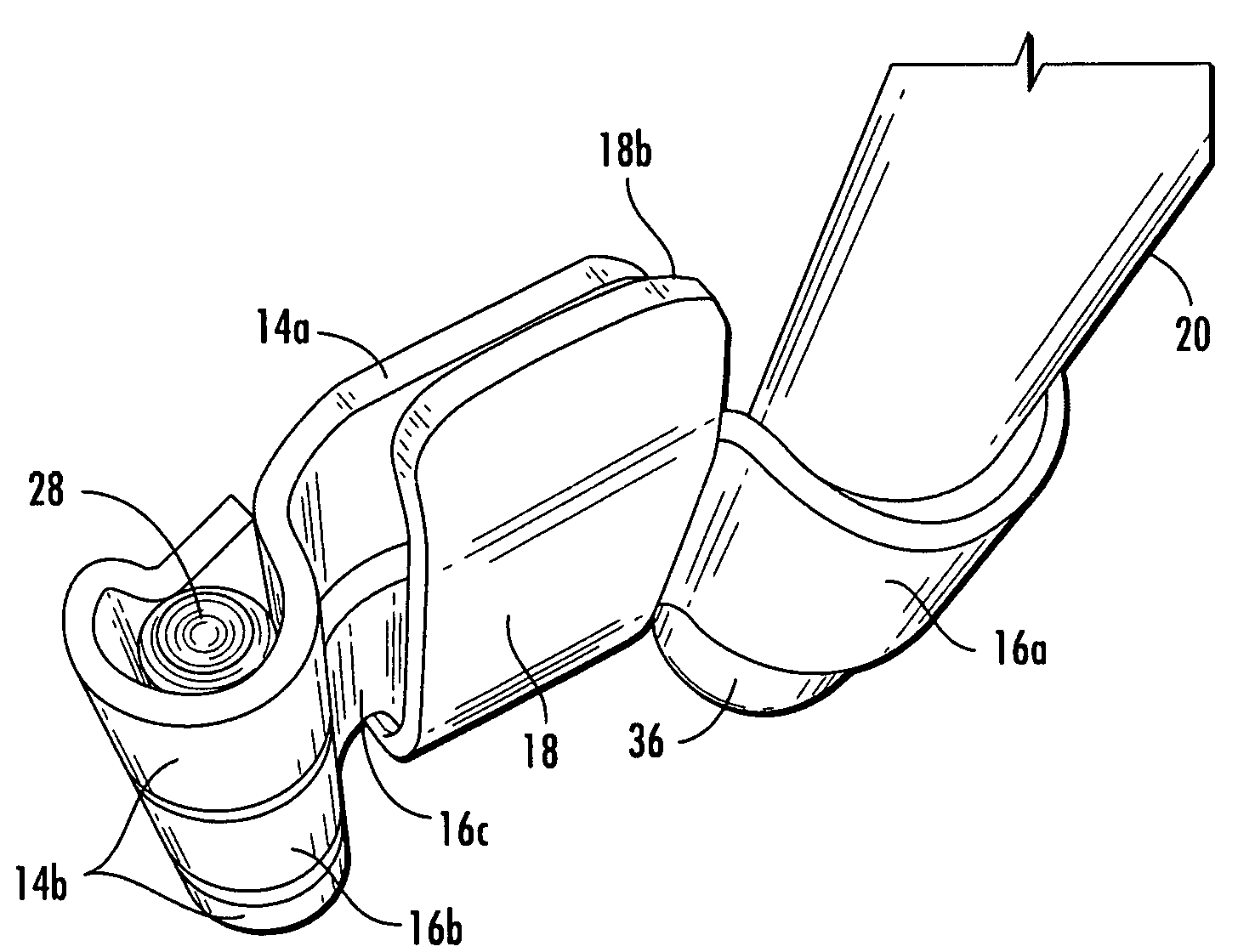
Tamper resistant hinge
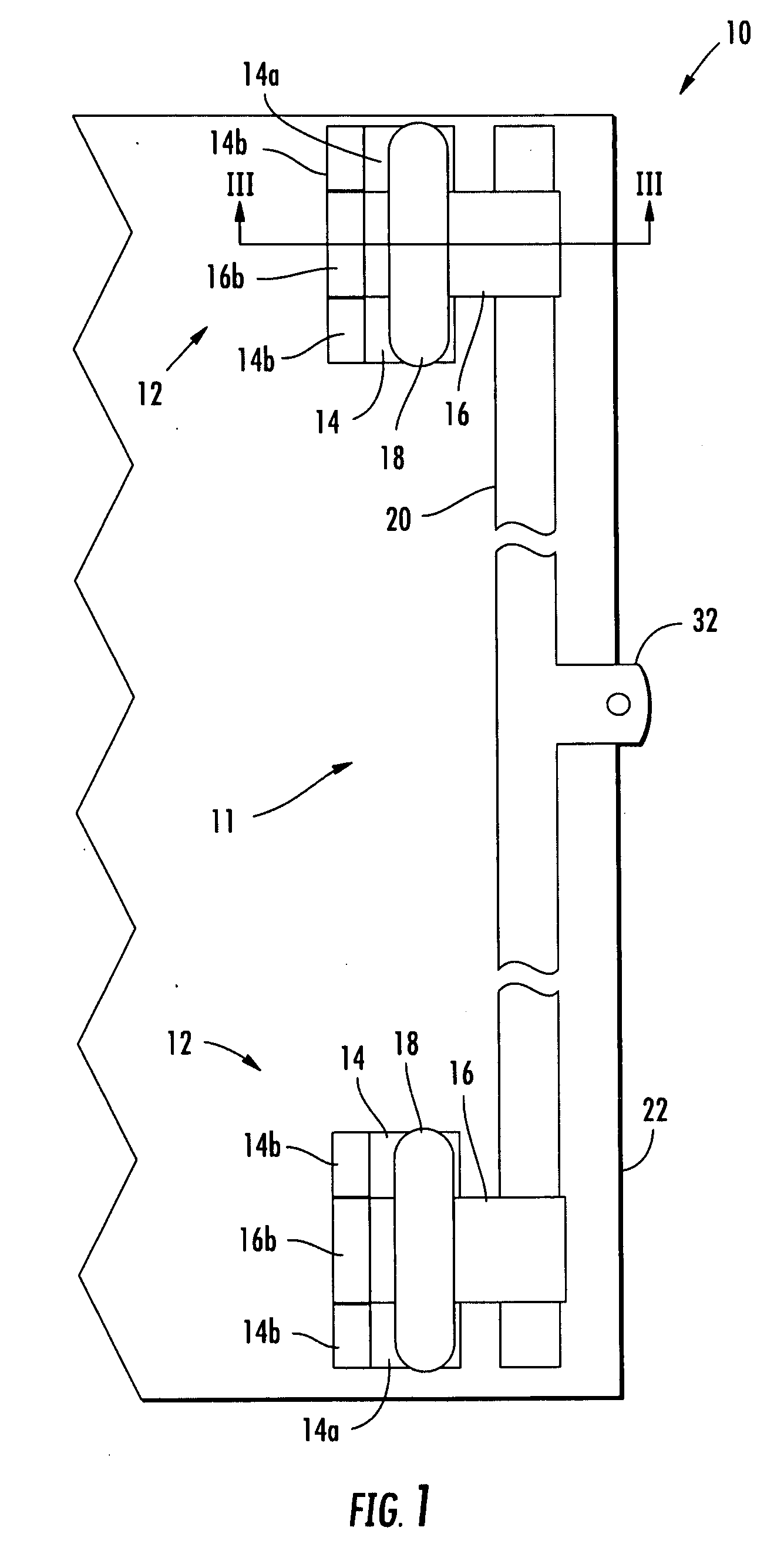
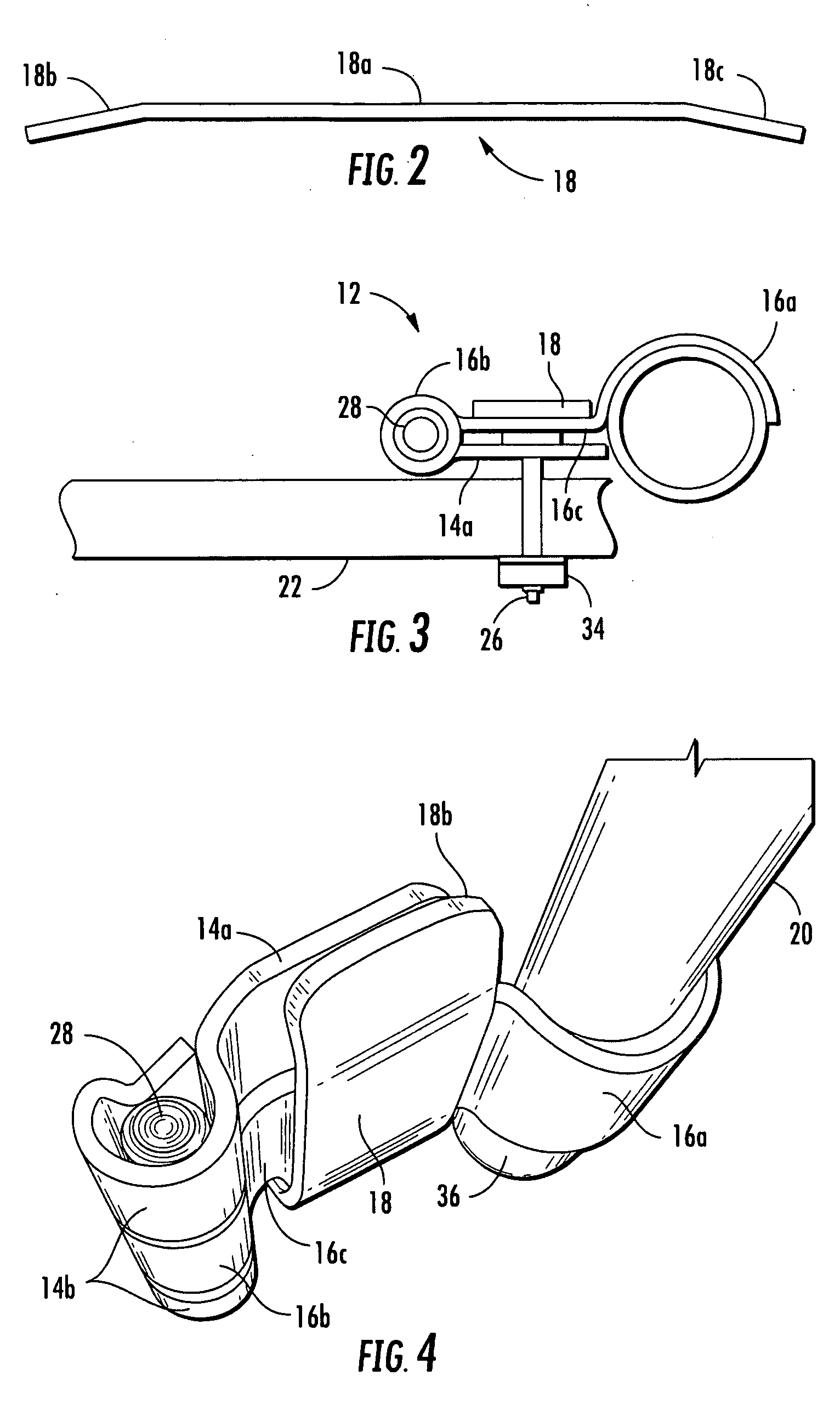
ActiveUS8146205B2Improve securityAvoid accessVehicle locksWing accessoriesTamper resistanceEngineering
A hinge assembly incorporates an anti-tamper member that is selectively positionable to protect fasteners holding the hinge assembly to a mounting surface such as an access door. The hinge assembly may be incorporated into a bar lock assembly to provide additional tamper resistance for a shipping container, for example, to limit or prevent unauthorized access to the container.
Owner:IMPERIAL STAMPING CORP
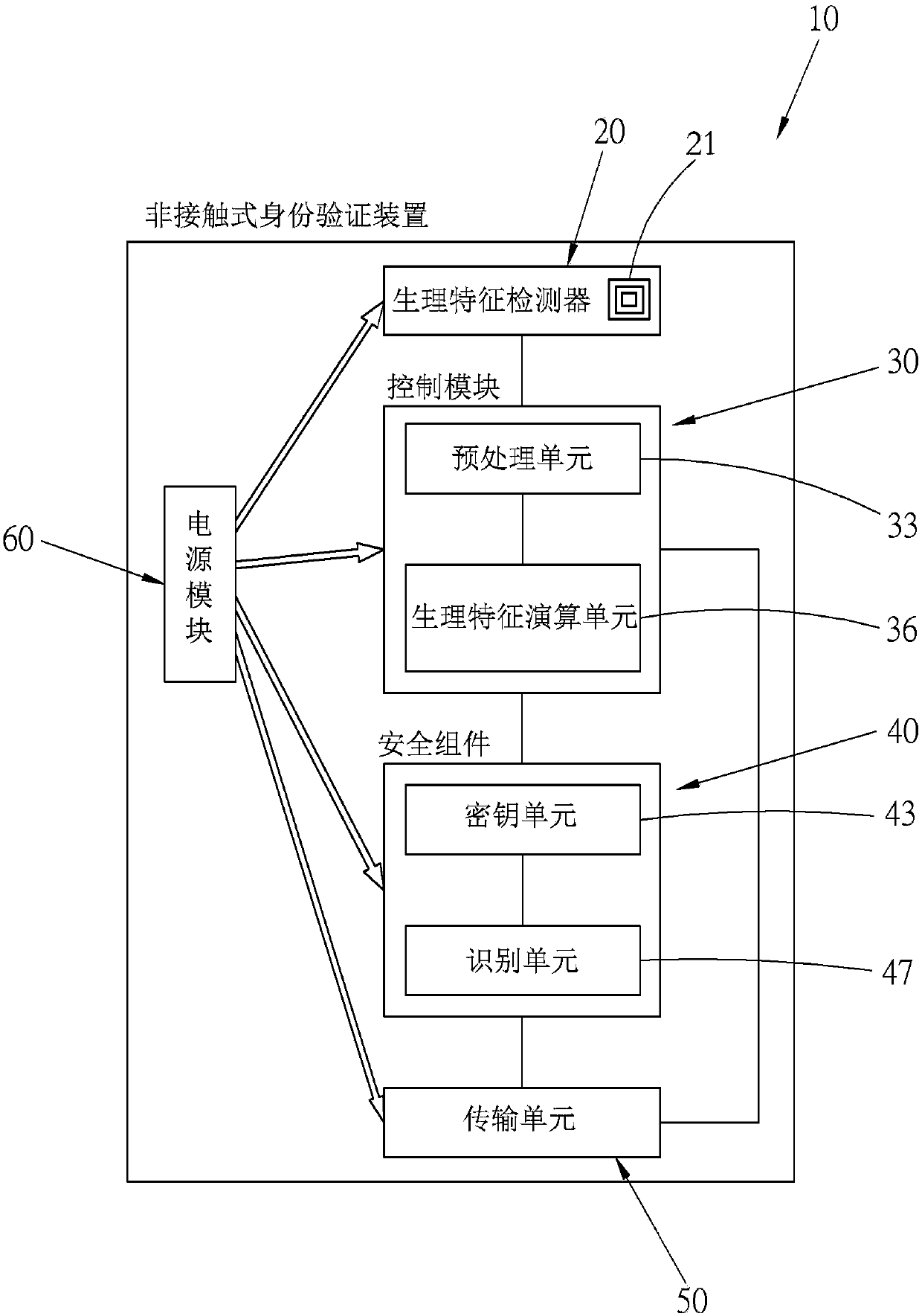
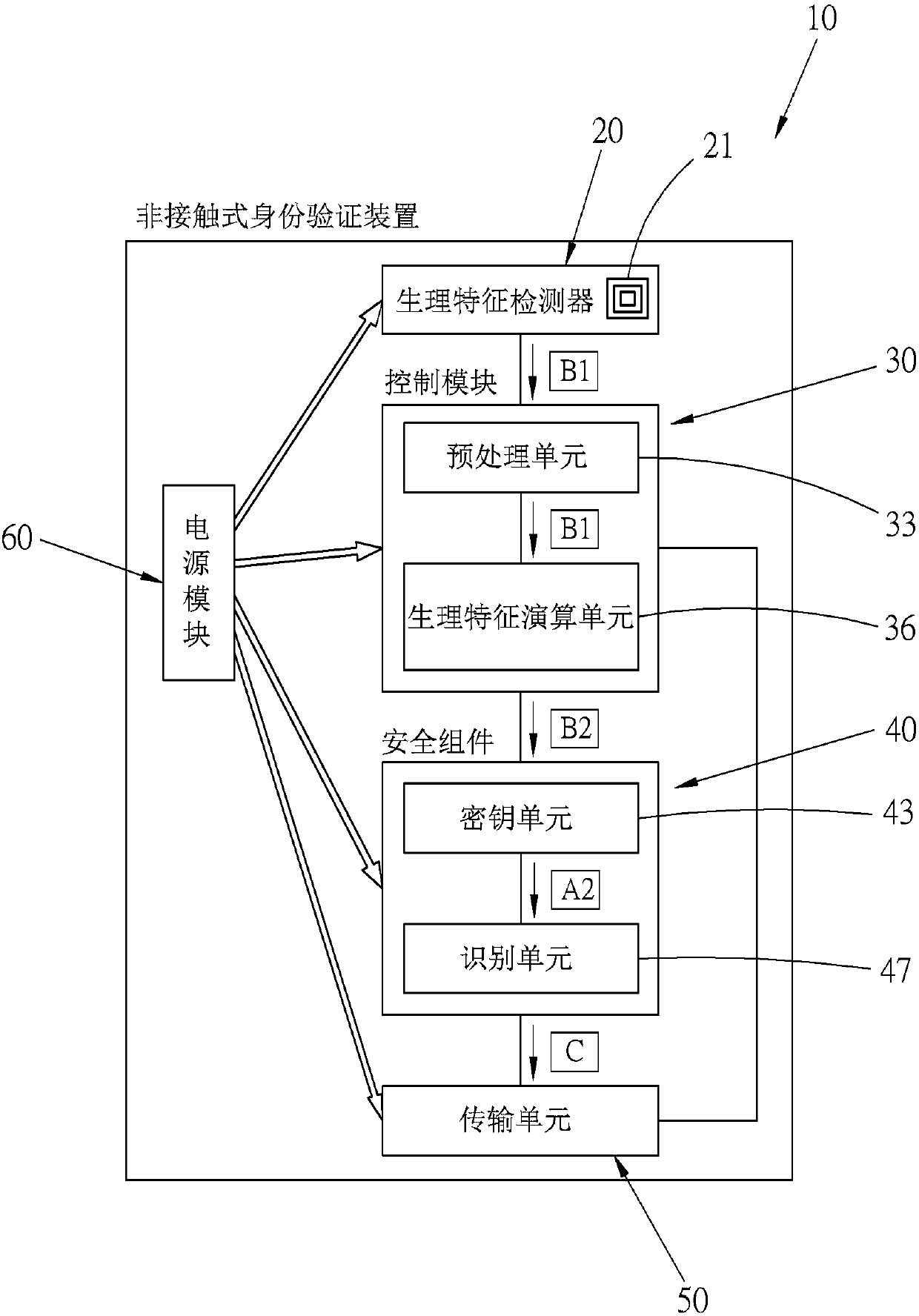
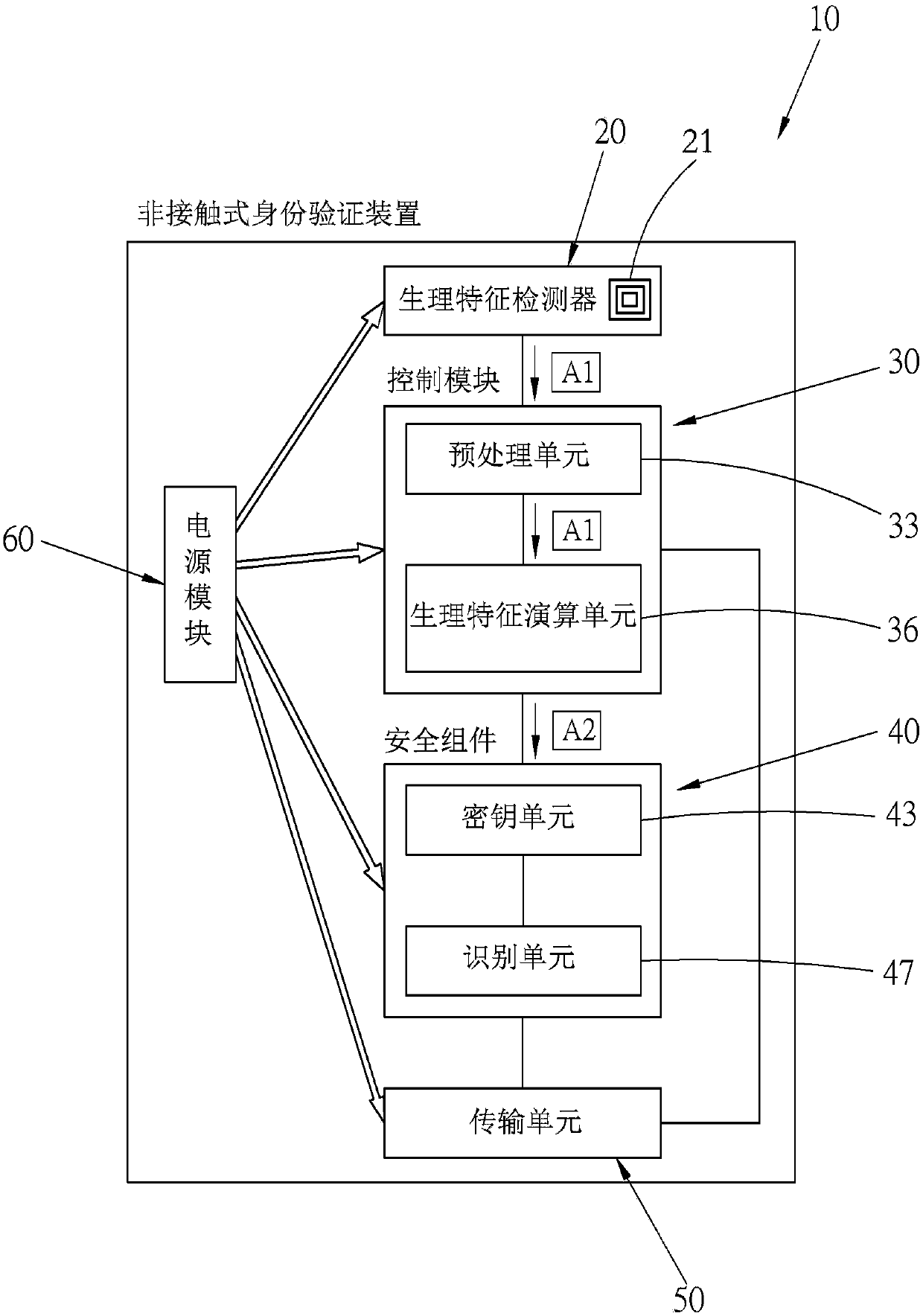
Non-contact identity verification device and system, and method thereof
InactiveCN107623669AStay safeProtection of personal biological informationDigital data authenticationIndividual entry/exit registersComputer moduleComputer science
The present invention relates to a non-contact identity verification device and system, and a method thereof, comprising: a physiological characteristic detector for detecting a physiological characteristic of a human body and generating at least one piece of physiological characteristic verification information; a control module for converting the physiological characteristic verification information into at least one physiological characteristic verification value; a key unit for encrypting and storing at least one physiological characteristic check value; an identification unit for comparing the physiological characteristic verification value with the decrypted physiological characteristic check value, and generating a comparison information; and a transmission unit capable of transmitting the comparison information to the outside. Through a verification technology of the present invention, a user can be verified rapidly and conveniently, recognition stability is very high, and personal data of the user can be adequately protected.
Owner:李殿基 +1
Multifunctional touch display self-service terminal
PendingCN114202855AImprove securityGood face recognitionComplete banking machinesApparatus for meter-controlled dispensingUSBRolling chassis
The invention discloses a multifunctional touch display self-service terminal, relates to the technical field of self-service terminals, and aims to solve the problems that a chassis is mostly of an anti-slip fixed structure, so that the self-service terminal is very good in fixity, but the self-service terminal is difficult to carry, the self-service terminal cannot be flexibly carried as required, and the self-service terminal is inconvenient to carry. And the use effect of the self-service terminal is not good indirectly. The self-service terminal comprises a self-service terminal main body, a processing device is arranged in the self-service terminal main body, a touch display screen, a camera, a card slot and a USB interface are arranged on the self-service terminal main body, four moving wheels are arranged below the self-service terminal main body, and the four moving wheels are arranged at four corners of the self-service terminal main body. Buffering pieces are arranged between the four moving wheels and the self-service terminal body, the two ends of each buffering piece are connected with the corresponding moving wheel and the self-service terminal body to form an integrated structure, a fixing base is arranged outside the self-service terminal body, and electric telescopic rods are arranged on the two sides of the self-service terminal body.
Owner:深圳市中福信息科技有限公司
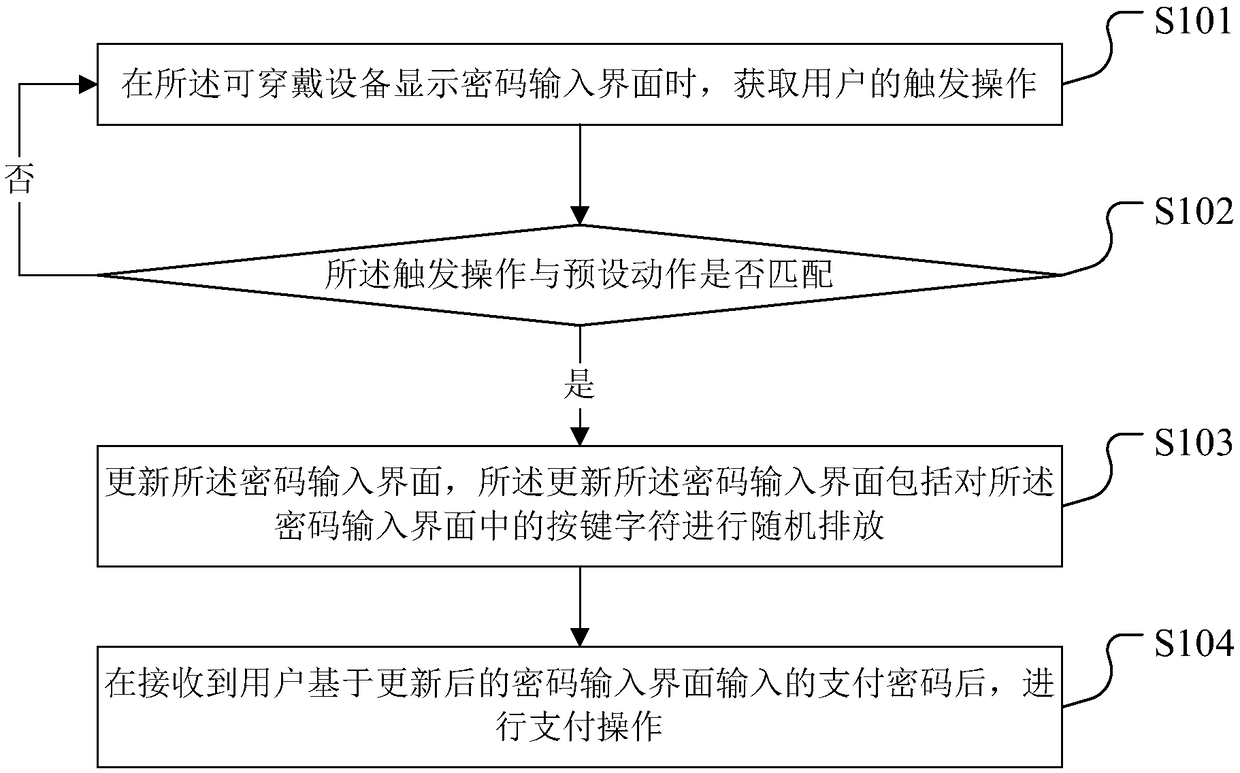
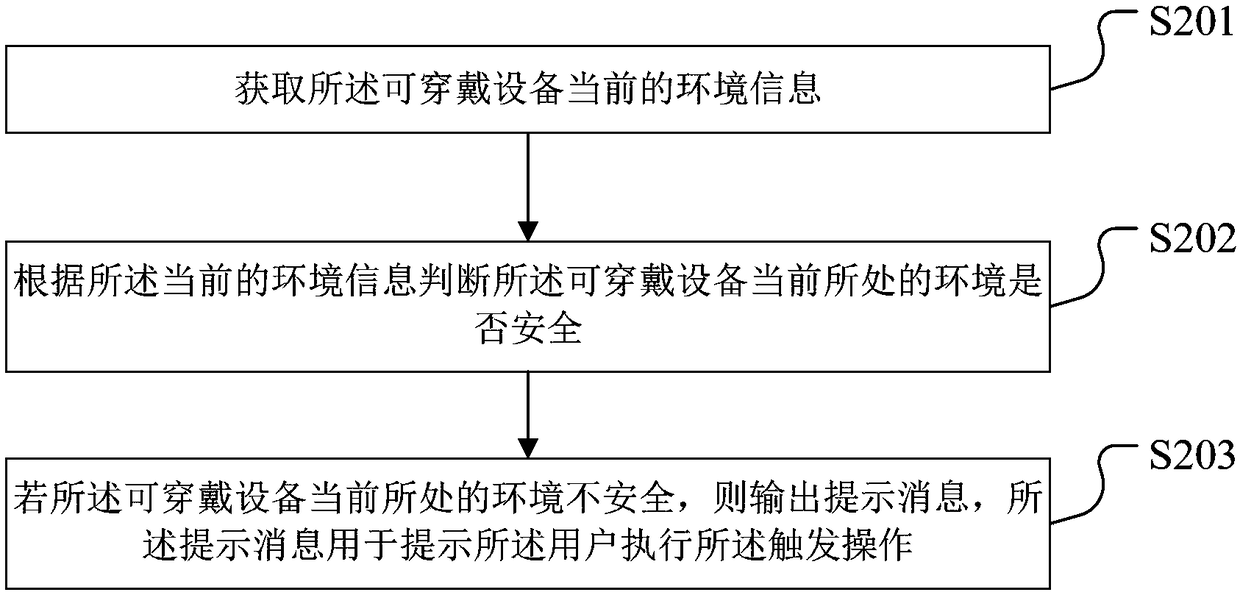
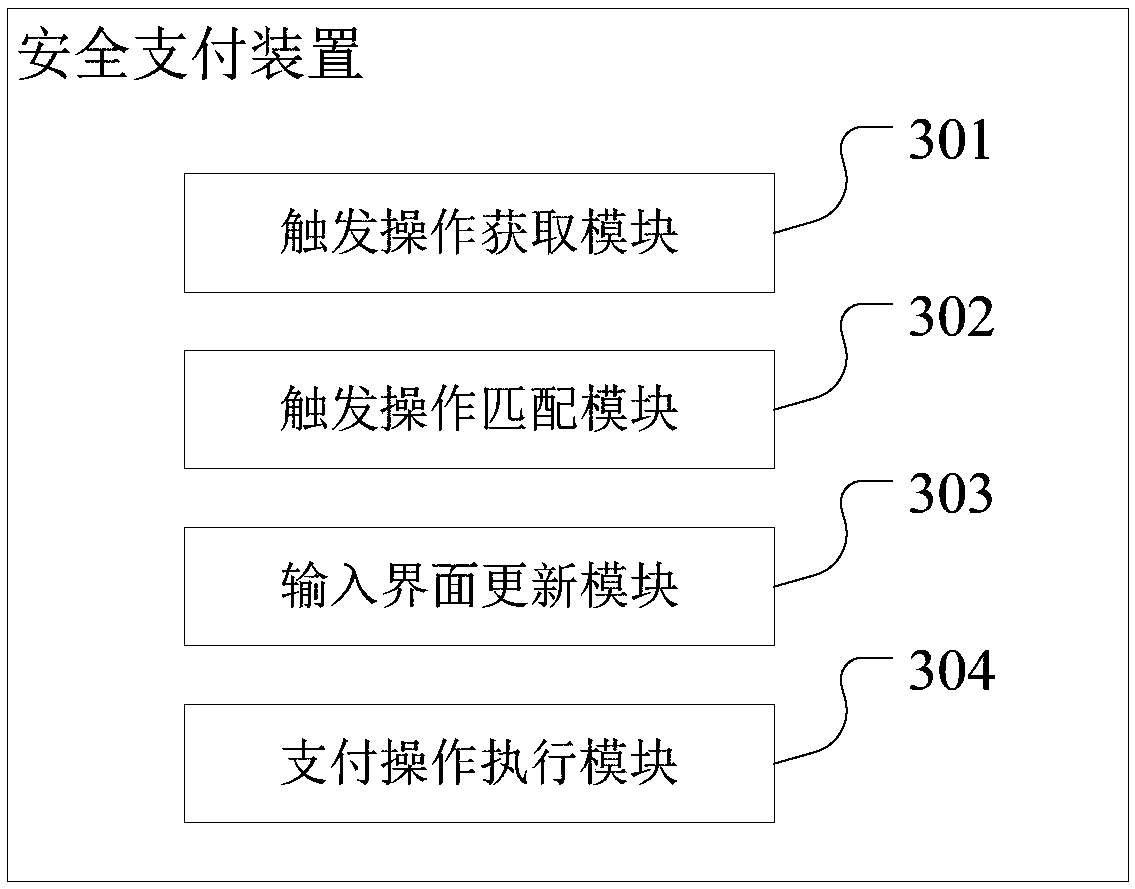
Safe payment method, device, wearable device and storage medium
InactiveCN109272322APrevent snoopingPreventer derivationInternal/peripheral component protectionProtocol authorisationPaymentPassword
The invention discloses a safe payment method, which is applied to wearable equipment. The safe payment method comprises the following steps: when the wearable equipment displays a password input interface, obtaining a trigger operation of a user;judging whether the triggering operation is matched with a preset action; if the triggering operation matches with the preset action, updating the password input interface, wherein the updating the password input interface comprises randomly arranging key characters in the password input interface; after receiving the payment password input by the user based on the updated password input interface, carrying out the payment operation so that when the surrounding environment is insecure, the user can complete the input of the payment password through the updated password input interface, so as to prevent others from snooping or deriving the payment password, avoid the disclosure of the payment password, ensure the security of the payment password input by the user in the wearable device, and ensure the security of funds. The invention also provides a safe payment device, a wearable device and a storage medium.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Dustproof display
InactiveCN105373192ASave effortCompact structureDigital data processing detailsInternal/peripheral component protectionSoftware engineeringDisplay device
Owner:CHONGQING CHENGSHUO TECH
Anti-peeping intelligent security door suitable for smart home system
ActiveCN108019128AImprove securityImprove practicalityBurglary protectionPeep-holesVertical tubePeephole
The invention refers to an anti-peeping intelligent security door suitable for a smart home system. The anti-peeping intelligent security door includes a door plate, a peephole, a keyhole and a handle. The door plate is provided with an anti-peeping mechanism, a lifting mechanism and two observing mechanisms. The lifting mechanism includes a driving assembly, a first pedal and two following assemblies. The following assemblies include bevel gears, screws, bearings and sliding blocks. The observing mechanisms include first vertical tubes, transverse pipes, second vertical pipes and third vertical pipes. Baffle blocks the peephole by the anti-peeping mechanism so that some unlawful people cannot peep into the room. Firstly, the exterior is roughly observed by the observing mechanisms when someone is in the outdoor; the baffle of the anti-peeping mechanism is raised after the basic situation is confirmed, so that the indoor occupants are capable of conveniently observing the external situation clearly; beside, the height of the first pedal is increased by the lifting mechanism, people with short stature are capable of conveniently using the peephole, and the practicability of securitydoor is enhanced.
Owner:上海合宝建筑装饰工程有限公司
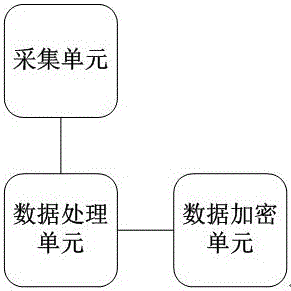
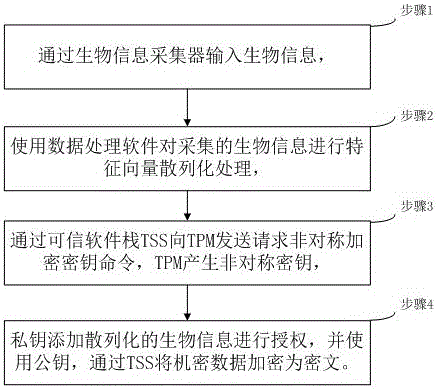
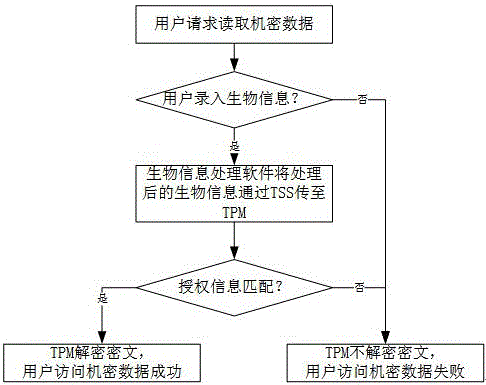
Method for confidential data encryption based on biological information authorization
InactiveCN106682531APrevent snoopingKey distribution for secure communicationDigital data protectionFeature vectorInternet privacy
The invention discloses a method for confidential data encryption based on biological information authorization and relates to the field of safe data access. According to the invention, biological information data is collected; the biological information data is treated by characteristics vector hash processing; TPM is used to generate a pair of asymmetric secrete keys; hashed biological information is added to a private key for authorization; a public key is used; and TSS is used to encrypt the confidential data into a ciphertext. According to the invention, reliability of a TPM hardware chip and counterfeit resistance of the biological information are combined, so the confidential data becomes safer.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
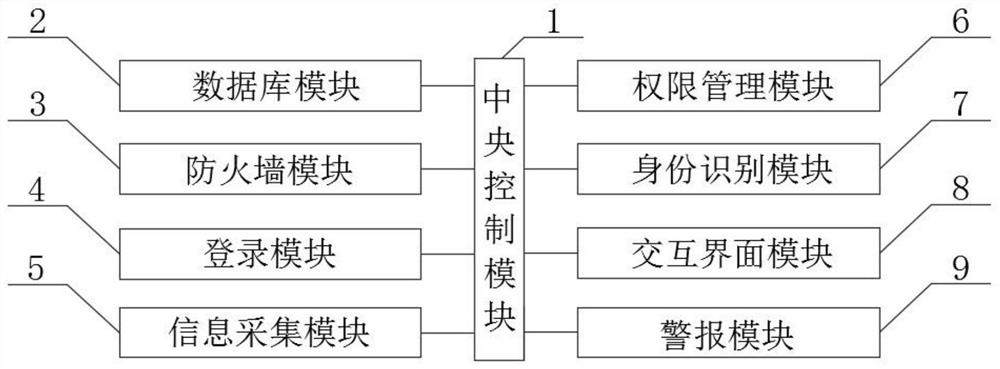
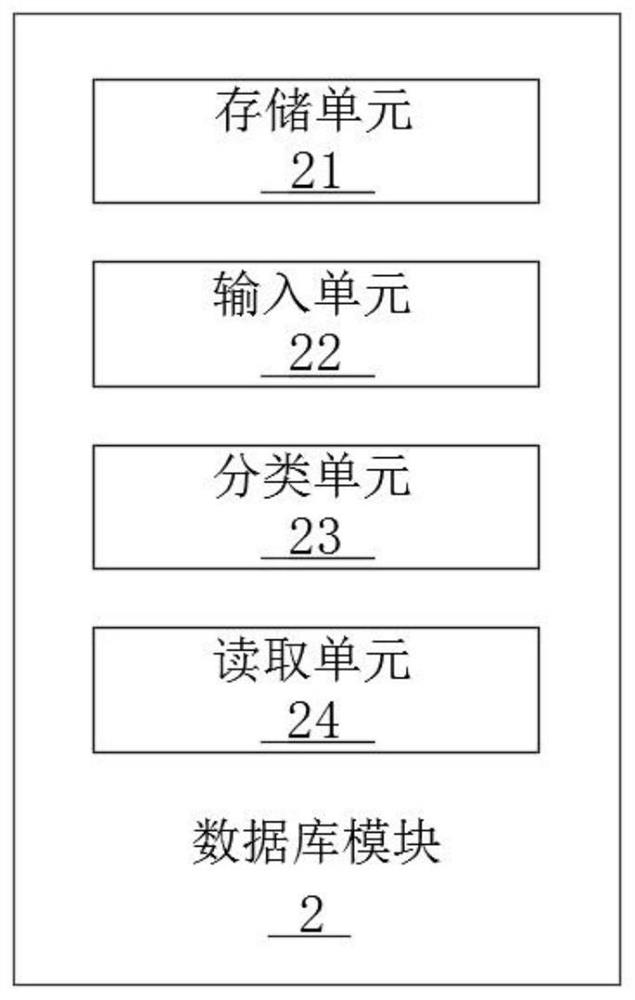
Enterprise information security management system
ActiveCN113094678ARich ways to seek cooperationDeter illegal entryDigital data protectionDigital data authenticationIdentity recognitionSafety management systems
The invention discloses an enterprise information security management system, which comprises a firewall module, a central control module, a database module, a login module, an authority management module and an identity recognition module; in use, illegal invasion of hackers and viruses can be prevented through a firewall, and modes for seeking cooperation among enterprises are enriched, so that potential cooperative clients can seek cooperation intentions and complete cooperation negotiation through the enterprise information security management system; access permissions conforming to identities of different visitors can be provided for the different visitors, and pertinence of enterprise information security management is improved; in addition, the user who completes registration and login can be prevented and stopped from snooping enterprise confidential information.
Owner:合肥天源迪科信息技术有限公司
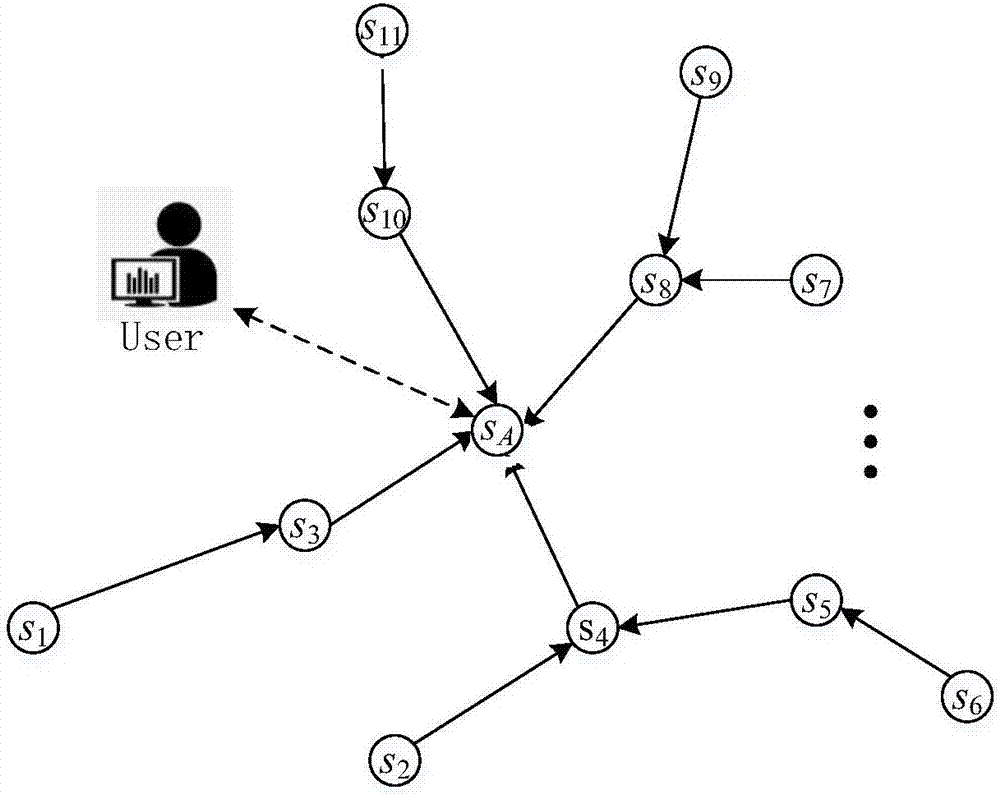
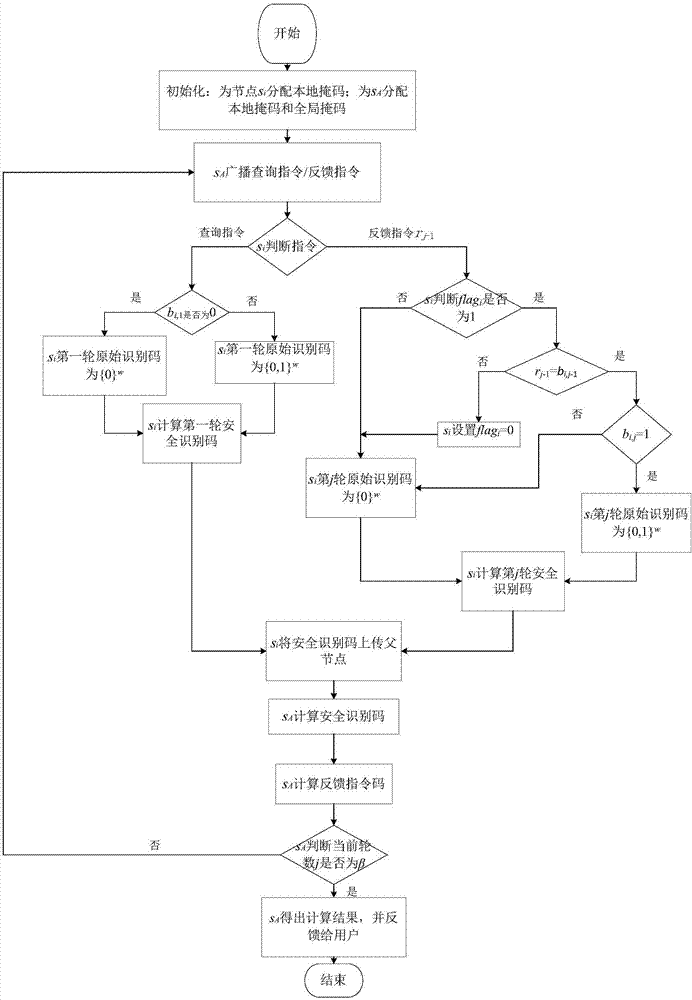
Privacy protection MAX / MIN query method for WSNs leased environment
ActiveCN107277806APrevent snoopingThere is no energy bottleneck problemNetwork topologiesData switching networksData queryPrivacy protection
The invention discloses a privacy protection MAX / MIN query method for WSNs leased environment, including two steps of mask allocation and query processing. The mask allocation initializes the data query protocol by assigning a local mask to each sensor node to ensure data privacy during the querying process. The query processing includes query instruction broadcasting, multiple rounds of collaborative computation of the sensor nodes and the proxy nodes, and the query result obtainment and feeding back of the three processing procedures to the user by the proxy nodes. The protocol flow of the method is simple and easy to implement; the security is high and the privacy security of the perceived data is effectively ensured; and the communication cost is low during the execution of the query processing, which is favorable for improving the utilization ratio of network resources and prolonging the life cycle of the network.
Owner:NANJING UNIV OF POSTS & TELECOMM
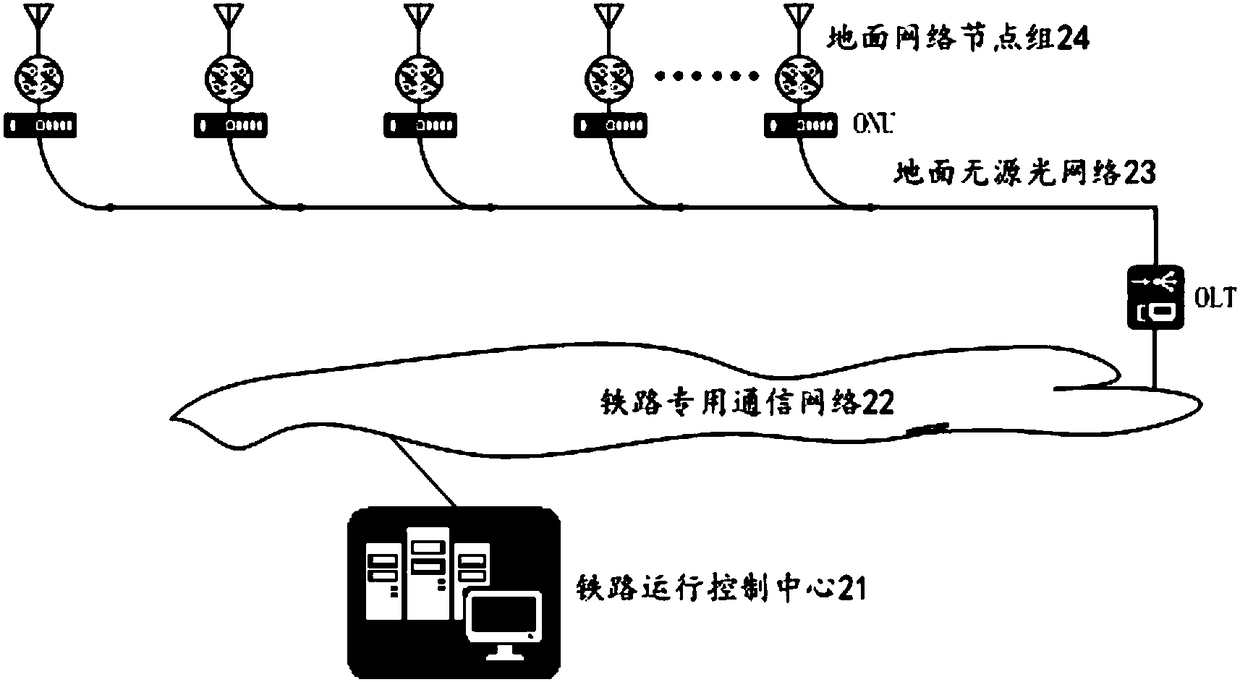
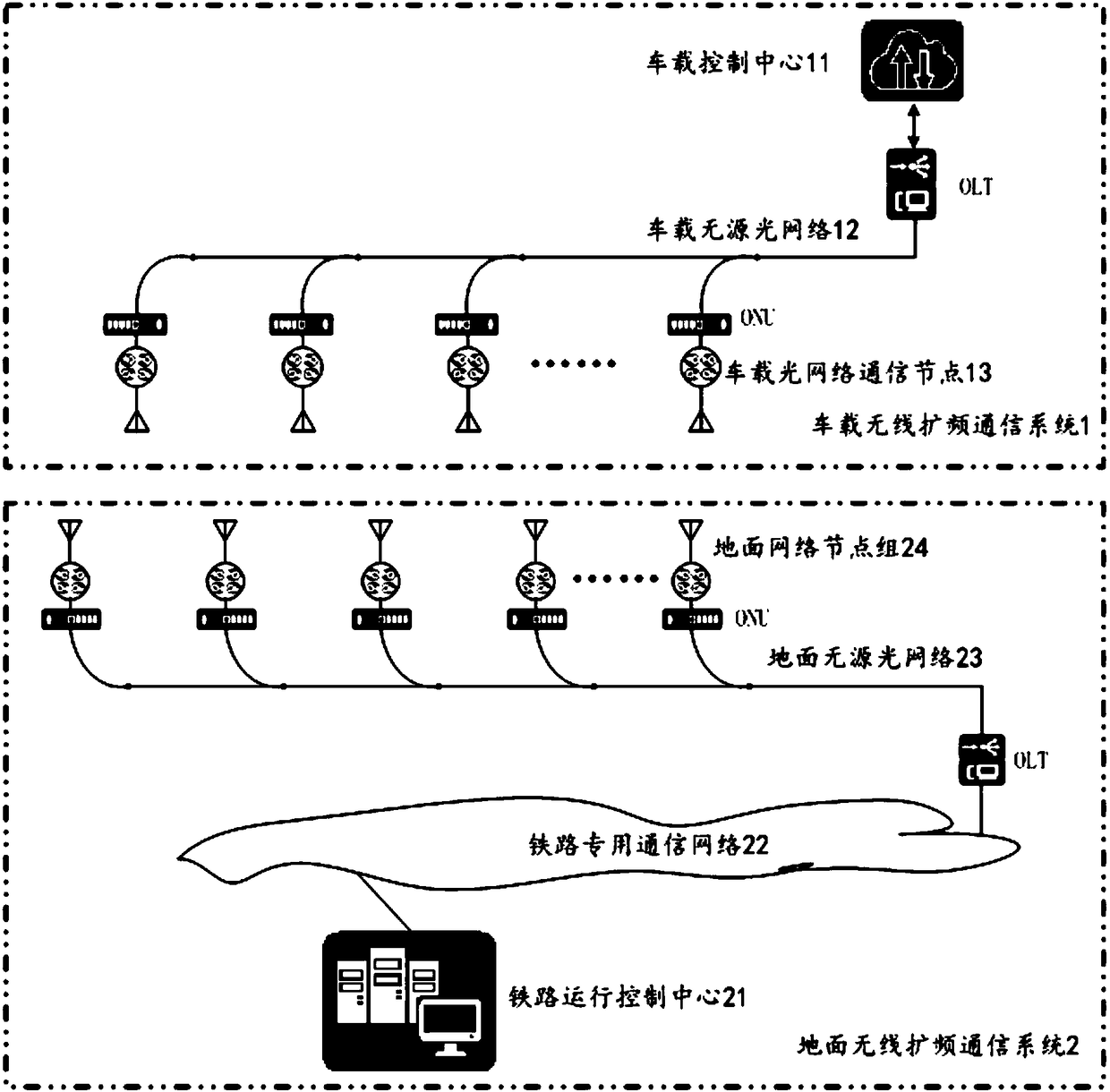
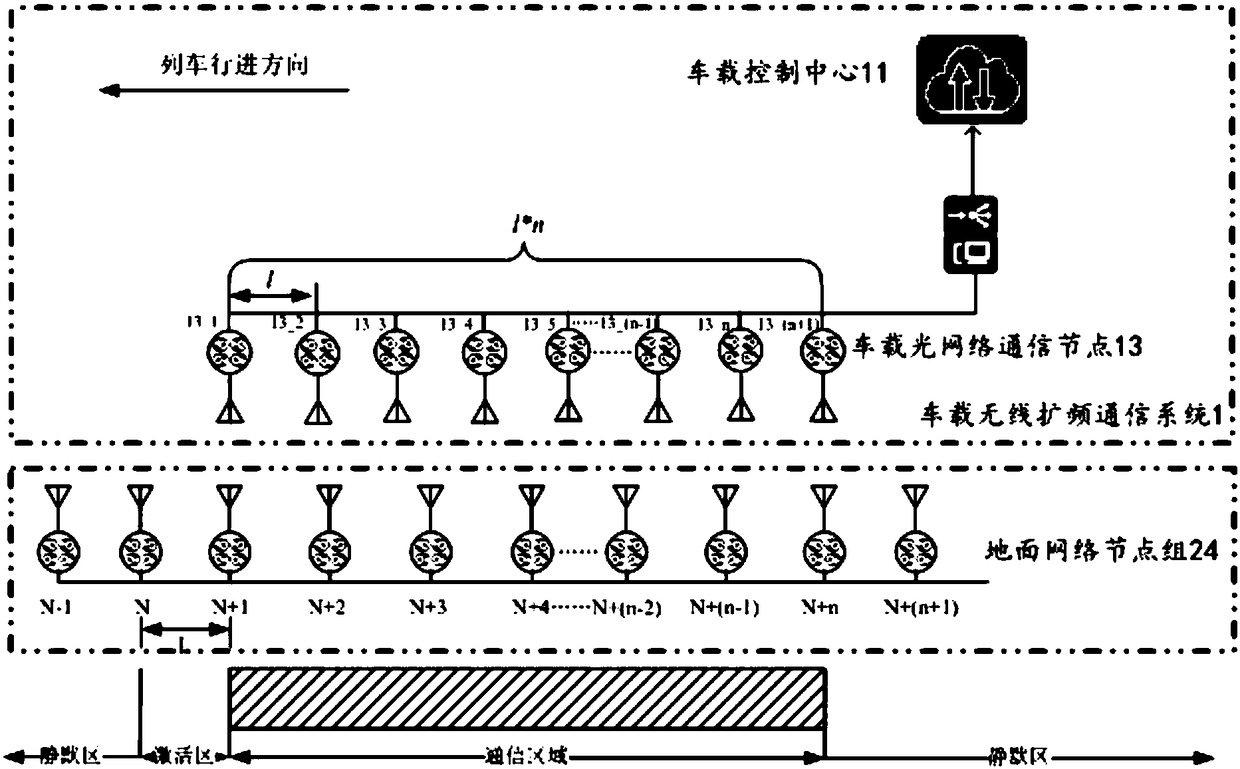
Ground wireless spread spectrum communication system for railway
PendingCN108418603APrevent intrusionPrevent snoopingMultiplex system selection arrangementsParticular environment based servicesNetwork communicationWireless
The embodiment of the invention relates to a ground wireless spread spectrum communication system for a railway. Each ground network node accesses a ground passive optical network through an ONU, andthen accesses a railway operation control center through an OLT and a railway dedicated communication network; a first ground network node group receives a first activation command issued by the railway operation control center through the railway dedicated communication network and the ground passive optical network, switches from a turn-off state to a monitoring state, and monitors the behaviorthat an onboard optical network communication node of a train transmits a first wireless spread spectrum communication signal; when the first wireless spread spectrum communication signal is monitored, a second wireless spread spectrum communication signal is transmitted; and the first wireless spread spectrum communication signal, authentication information of the ground network node group and azone code are transmitted to the railway operation control center to generate a second activation command, and the second activation command is issued to a second ground network node group that is arranged adjacent to the first ground network node group along the traveling direction of the train.
Owner:BEIJING PHOENIX HUITONG TECH CO LTD
Tamper resistant hinge
ActiveUS20090260185A1Improve securityAvoid accessVehicle locksWing accessoriesTamper resistanceEngineering
A hinge assembly incorporates an anti-tamper member that is selectively positionable to protect fasteners holding the hinge assembly to a mounting surface such as an access door. The hinge assembly may be incorporated into a bar lock assembly to provide additional tamper resistance for a shipping container, for example, to limit or prevent unauthorized access to the container.
Owner:IMPERIAL STAMPING CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com