Method and system for generating safety key bound with device
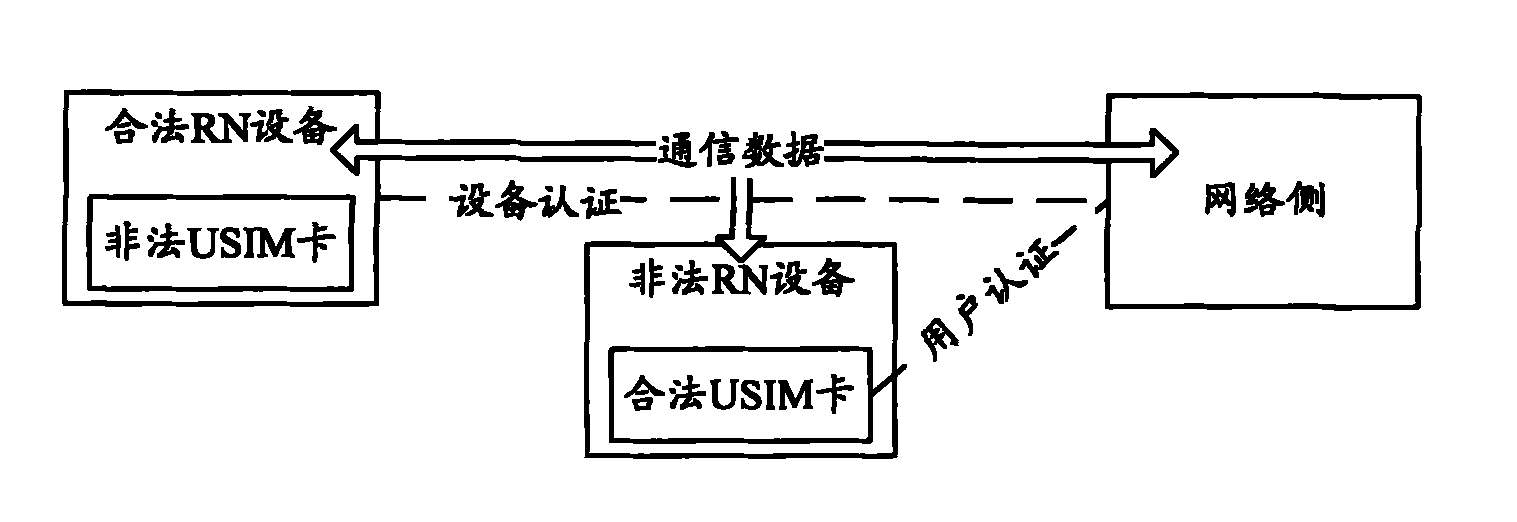
A security key and device technology, applied in the field of security authentication, can solve the problems of not being able to guarantee the security of RN and network communication data, and not being able to realize user authentication and device binding of RN, so as to prevent eavesdropping and tampering and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
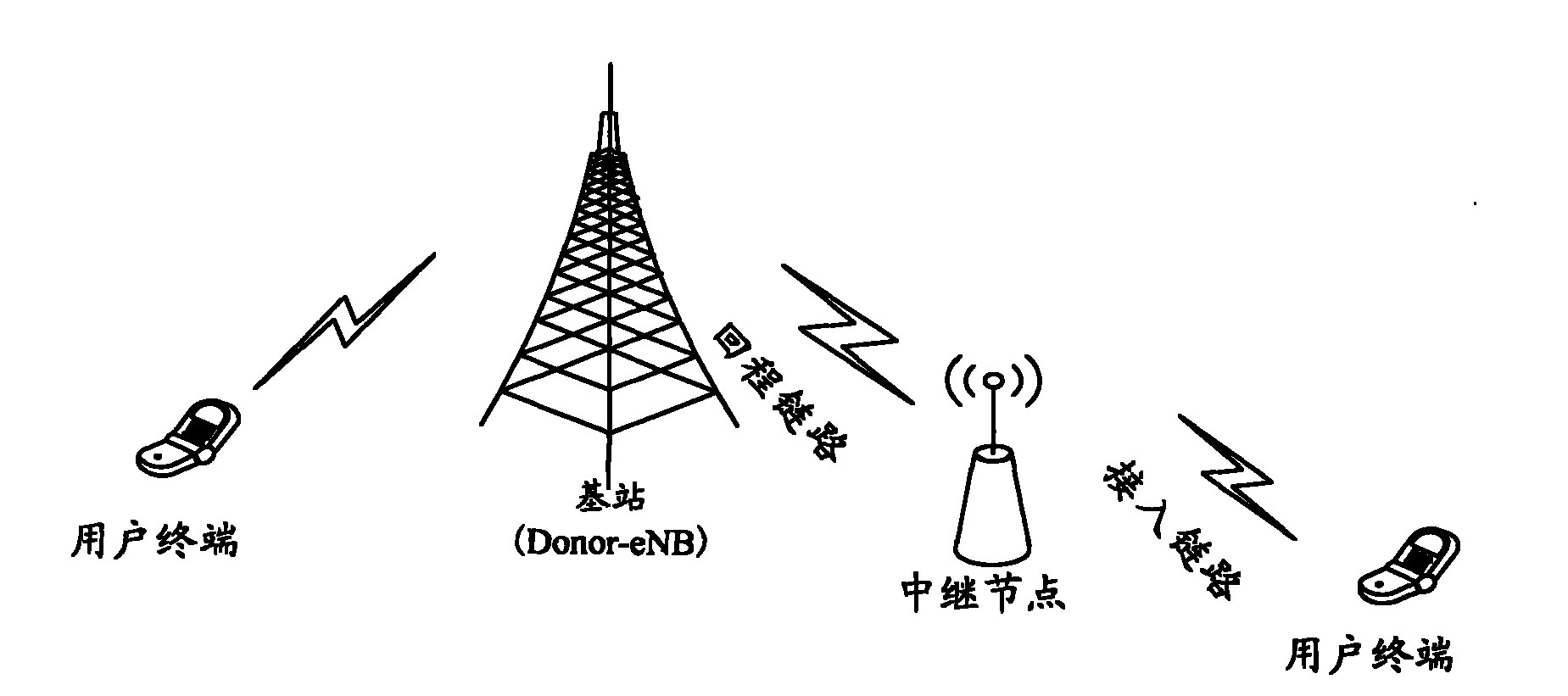
[0042] Figure 4 A flowchart of a method for generating a security key bound to a device for the present invention, such as Figure 4 shown, including the following steps:
[0043] Step 400: The network side agrees with the RN on user security keys and device-related security parameters.
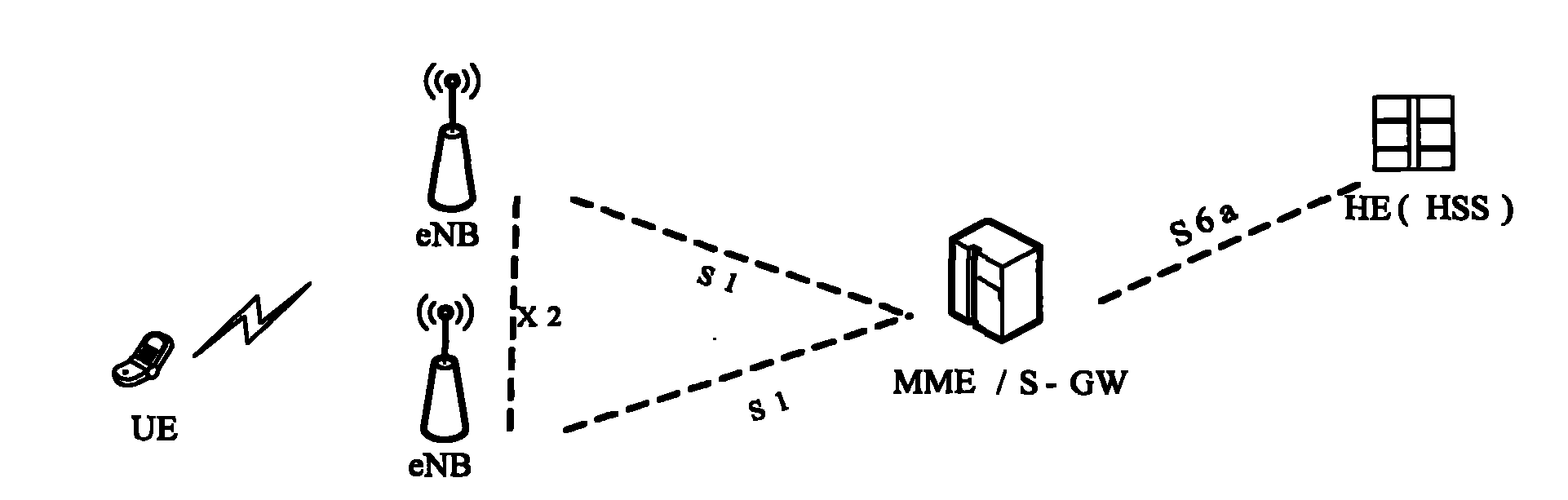
[0044] In this step, the method for agreeing on the user security key between the network side and the RN can adopt the existing EPSAKA process, and the specific implementation will not be repeated here. In this case, the network side refers to the MME. Among them, the user security key includes: the intermediate key K agreed in the EPS AKA process ASME ; or, by the intermediate key K ASME Derived other keys, such as the base station key K eNB or NH value.
[0045] In this step, the method for the network side and the RN to negotiate device-related security parameters includes:
[0046] The network side initiates an authentication process to the RN, and during the authentication proce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com