Secret key and true random number generator and method for generating secret key and true random number
A true random number and key generation technology, applied in key distribution, which can solve the problems of ECC being vulnerable to side-channel attacks, expensive resource overhead, and affecting key security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
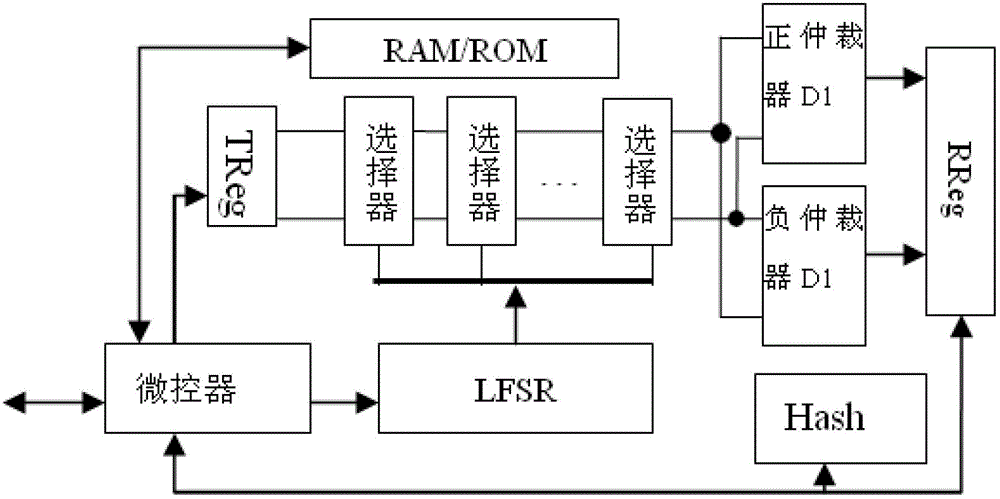
[0059] This embodiment designs based on DAPUF such as figure 1 The shown key and true random number generator (DAPUFKR), including dual arbiter physical unclonable module DAPUF, trigger signal generation register TReg, response acquisition register RReg, microcontroller, shift register LFSR, Hash engine, volatile Memory RAM and non-volatile memory ROM; the dual arbiter physical unclonable module DAPUF is composed of a sensitive circuit and an arbitration circuit, which is used to receive the challenge sent by the LFSR and the rising edge trigger signal sent by the trigger signal generation register, and generate The corresponding positive arbitration response and negative arbitration response are stored in the response acquisition register.
[0060] The trigger signal generating register is composed of two-bit registers, one bit register is connected to the upper input of the first selector of the DAPUF sensitive circuit, and the other bit register is connected to the lower in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com