Cloud storage security realization method based on data encryption and access control
A data encryption and access control technology, applied in the field of cloud computing applications, can solve security threats, data security issues, difficult data security and other issues, to achieve the effect of protecting security and avoiding mutual access to data intentionally or unintentionally
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
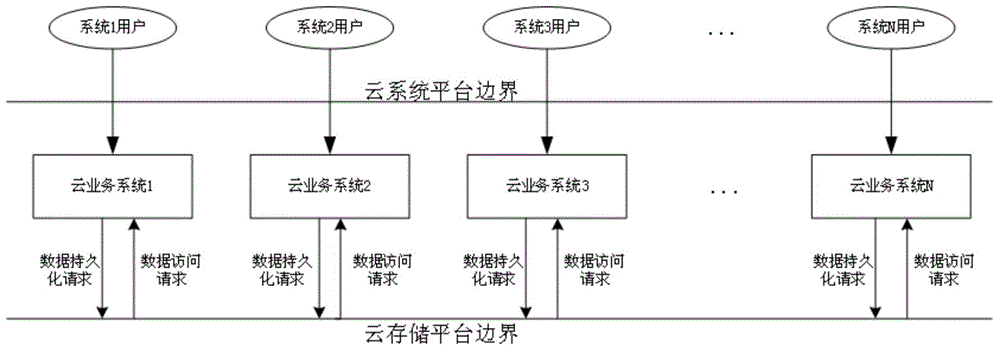
[0020] The security system mainly consists of three parts: system users, cloud business system and cloud storage platform. System architecture such as figure 1 . System users are deployed on PCs or mobile devices; the cloud business system accepts user data input; the cloud storage platform implements centralized data storage and is deployed on clusters, and the data storage entrance of the cloud storage platform is equipped with data encryption software modules and data access control software The module is installed at the data access entrance of the cloud storage platform.
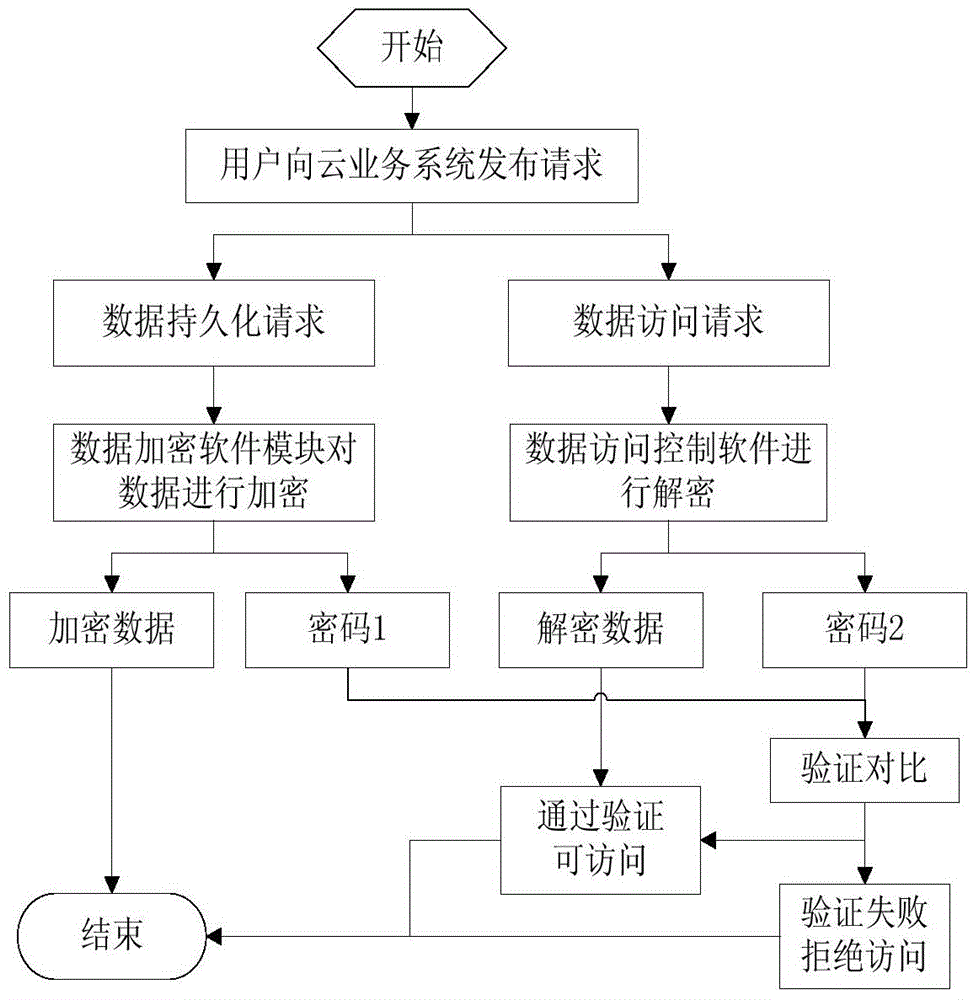
[0021] The realization of data access mutual exclusion consists of two parts: data encryption and data access control.
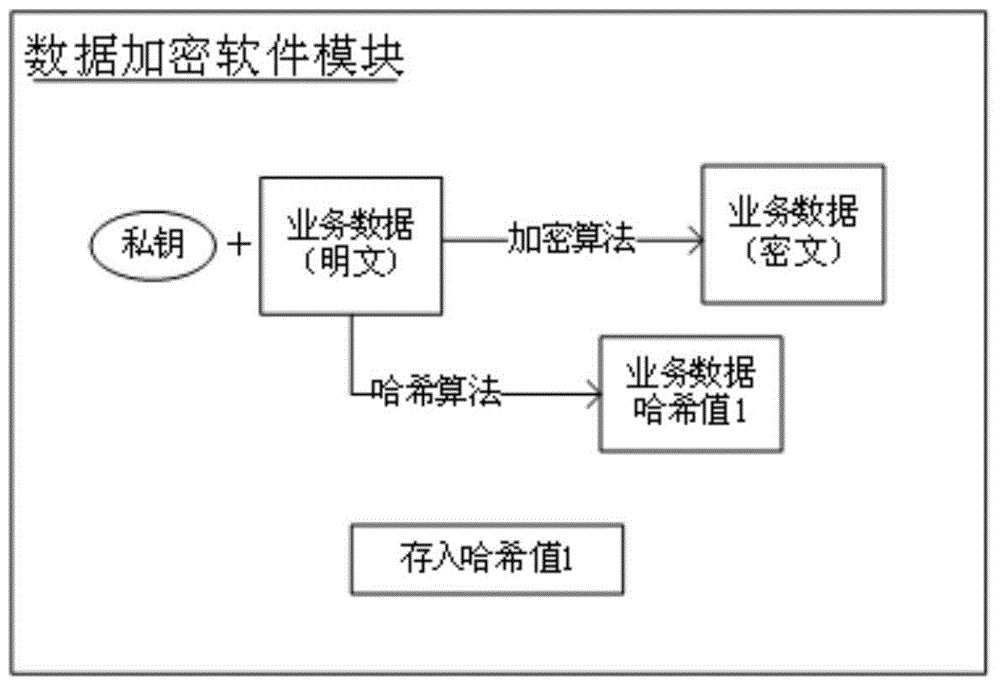
[0022] Implementation of data encryption
[0023] When the business system receives the data input by the user or the user modifies or deletes the busine...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com