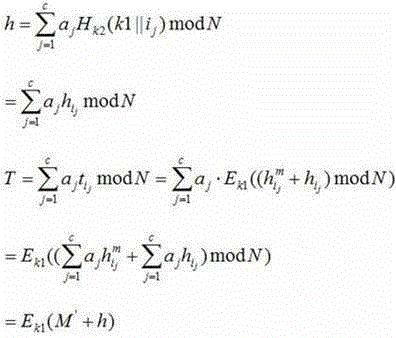Data possession proof scheme
A technology of possession and data owner, applied in the field of information security, it can solve the problems of high computing overhead and extra storage space, and achieve the effect of avoiding exponential operations, improving execution speed and security, and reducing computing overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
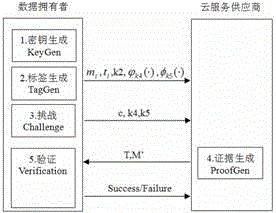
[0061] A data possession certification scheme of the invention will be described in detail below in conjunction with the accompanying drawings.
[0062] A data possession proof scheme, the main symbols used in the present invention are described as follows.
[0063] Owner: data owner.
[0064] CSP: Cloud Service Provider.
[0065] KeyGen: key generation module KeyGen.
[0066] TagGen: Tag generation module.
[0067] Challenge: challenge module.
[0068] ProofGen: Proof generation module.
[0069] Verification: Verification module.
[0070] M: Owner's outsourced data.
[0071] n: The number of data blocks, that is, M is divided into n fixed-size blocks.
[0072] m i : block of data in M, m i ∈M, 1≤i≤n.
[0073] : hash function with key.
[0074] : Data block label.
[0075] : Pseudorandom function under the action of key k.
[0076] : Pseudorandom permutation function under the action of key k.
[0077] : NRTU encryption algorithm.
[0078] Include the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com