Face image biological key generating method
A biological key and positive face technology, applied in the field of information security, can solve the problems of no face biological key technology, no face feature information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
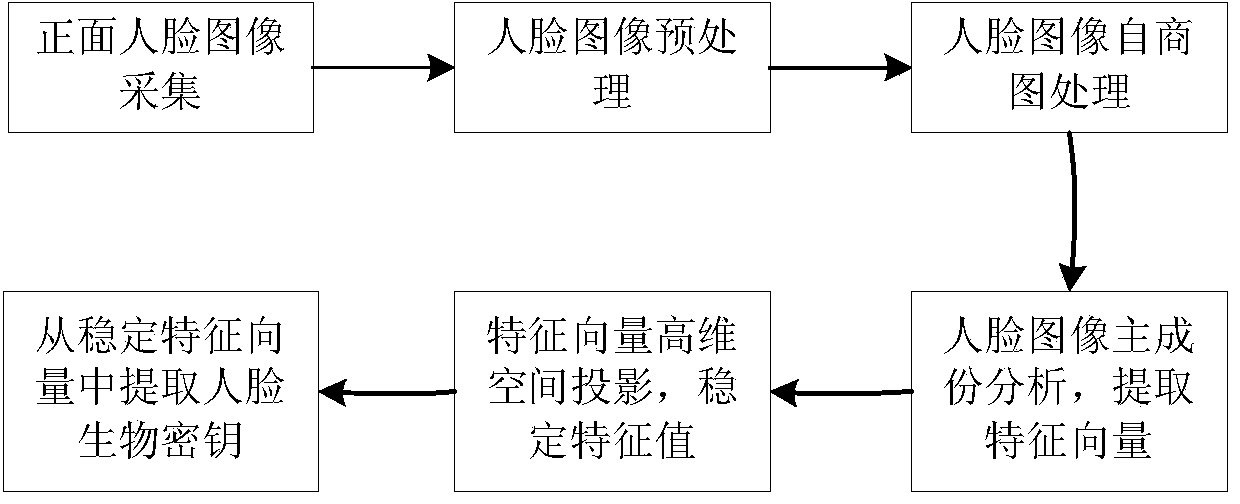
[0027] The present invention will be further described below in conjunction with accompanying drawing.
[0028] The current face recognition technology cannot correctly identify faces with multiple poses and complex lighting conditions. The preconditions for extracting the human face biological key in the present invention are a frontal face, sufficient illumination, and no multi-light source and multi-angle irradiation. Under this premise, face recognition has a high accuracy rate. After a series of stabilization processes, the biological key can be extracted from it. The extraction process of the face biometric key is as follows: figure 1 shown.
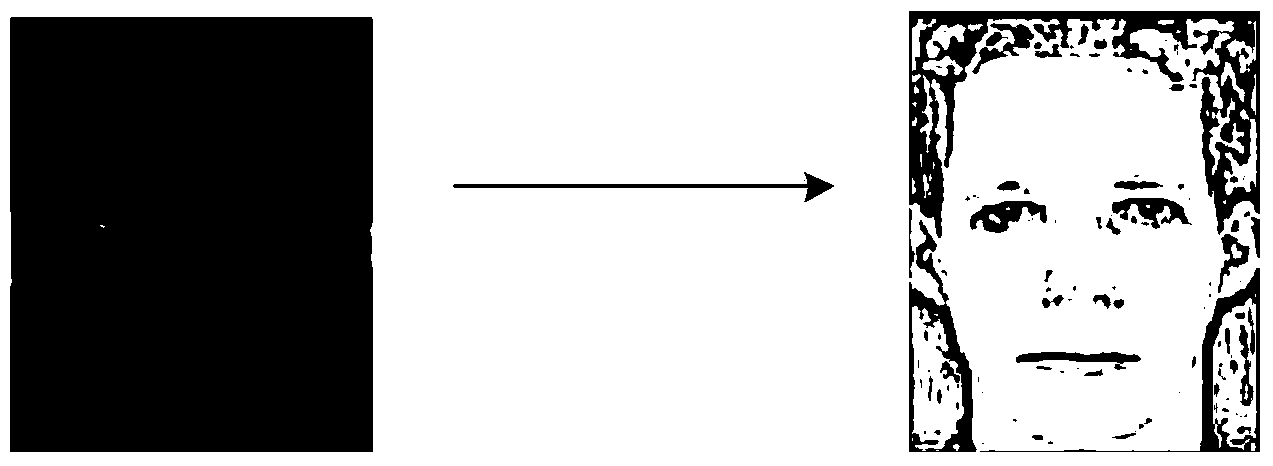
[0029] Illumination conditions have a great influence on the existing face recognition effect, and it is necessary to eliminate the influence of illumination first. The present invention uses the self-quotient graph method to eliminate the influence of illumination, and the effect is as follows figure 2 shown.
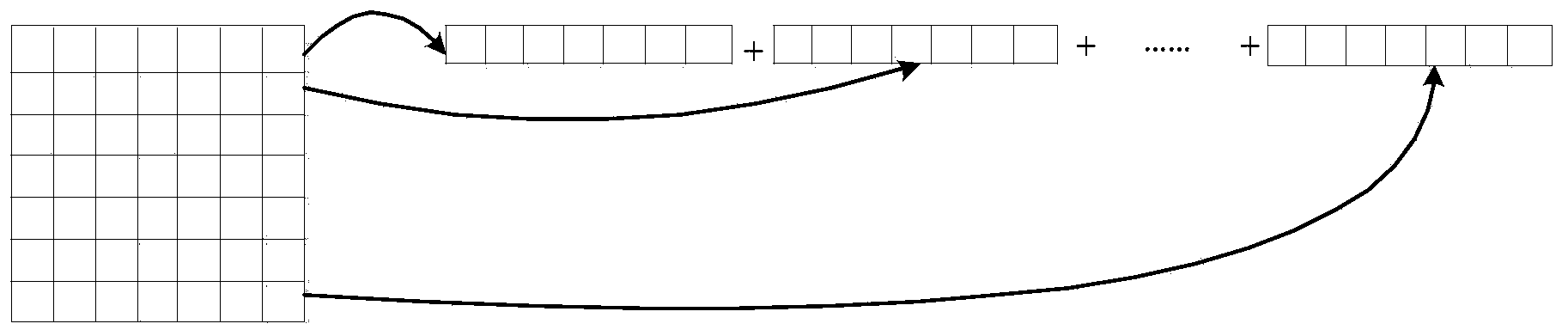
[0030] The fa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com