Cloud storage security deduplication method and device based on Merkel hash tree
A Merkle hash and cloud storage technology, applied in the field of cloud storage security deduplication based on Merkle hash tree, can solve ciphertext attacks, proof of file ownership without consideration, and side channels without consideration Attack problems and other issues, to achieve the effect of reducing the number and size
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
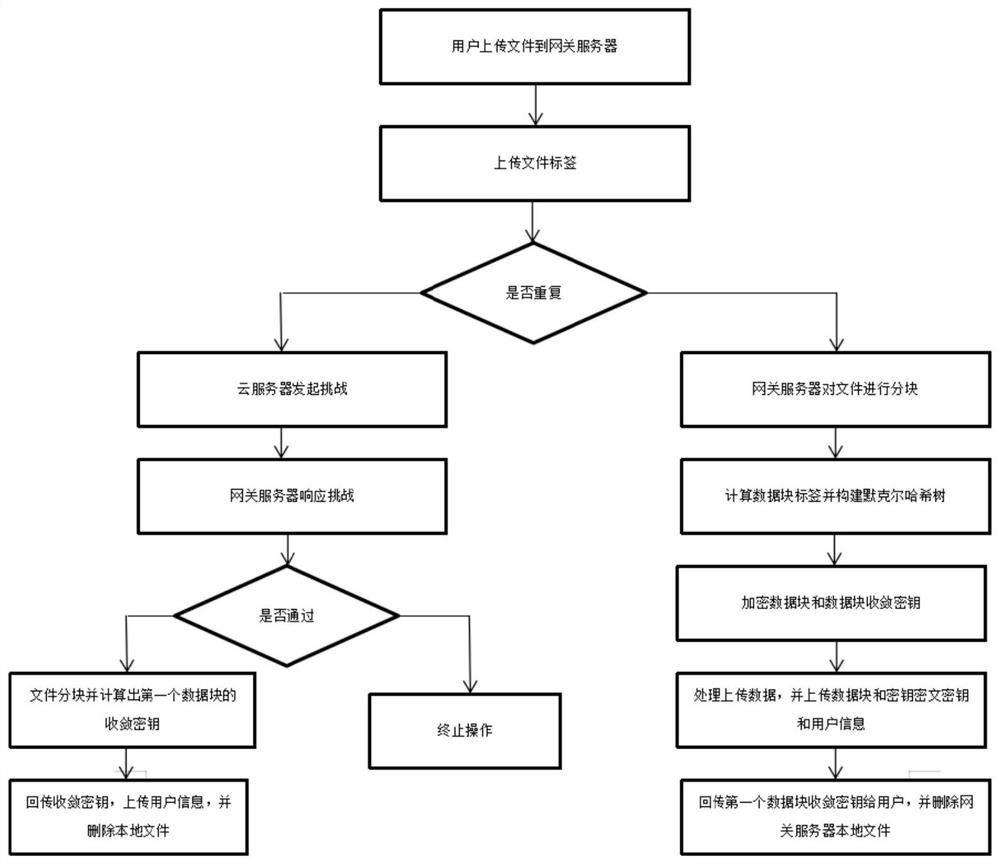
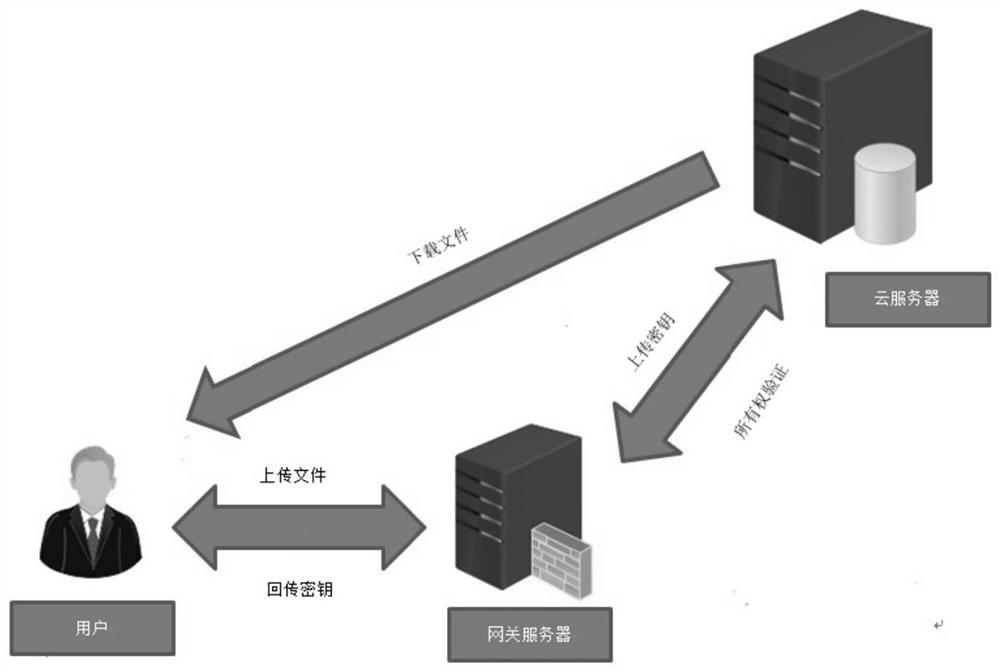
[0047] The embodiment of the present invention provides a cloud storage security deduplication method based on a Merkle hash tree. The system model used in this method includes: users, cloud servers and gateway servers. The system model architecture is shown in the attached figure 1 shown.
[0048] Cloud server: An entity that provides outsourced data services for users. When users upload duplicate data files, the cloud server will securely deduplicate the file data to reduce storage costs and save user upload bandwidth.
[0049] User: In order to save local storage space, the data is outsourced and stored in the cloud server, and the entity that can access the data at any time.
[0050] Gateway server: upload files for the user agent, verify file ownership, authorize the user on behalf of the cloud server, and confuse file upload traffic.
[0051] Such as figure 2 As shown, the cloud storage security deduplication method based on the Merkle hash tree provided by this embod...
Embodiment 2
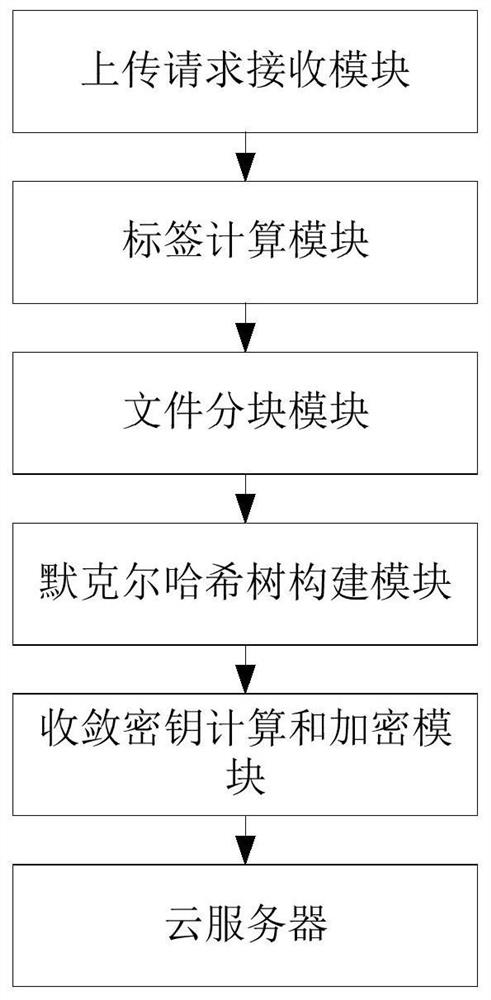
[0078] Such as image 3 As shown, a cloud storage security deduplication device based on Merkle hash tree, the device is a gateway server, including:
[0079] Upload request receiving module: used to receive the request sent by the user to upload the file to the cloud server;
[0080] Label calculation module: used to calculate the label T of the file that the user needs to upload, and upload the label T to the cloud server, and the cloud server determines whether the uploaded label already exists;
[0081]File block module: used to block the file to be uploaded into n data blocks {Bi} (1≤i≤n) when the tag does not exist in the cloud server;
[0082] Merkle hash tree construction module: used to calculate the label {ti} (1≤i≤n) of n data blocks, and use the label of the data block to construct the Merkle hash tree, that is, the data block The label is used as the leaf node of the Merkle hash tree to build a complete Merkle hash tree;
[0083] Convergent key calculation and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com