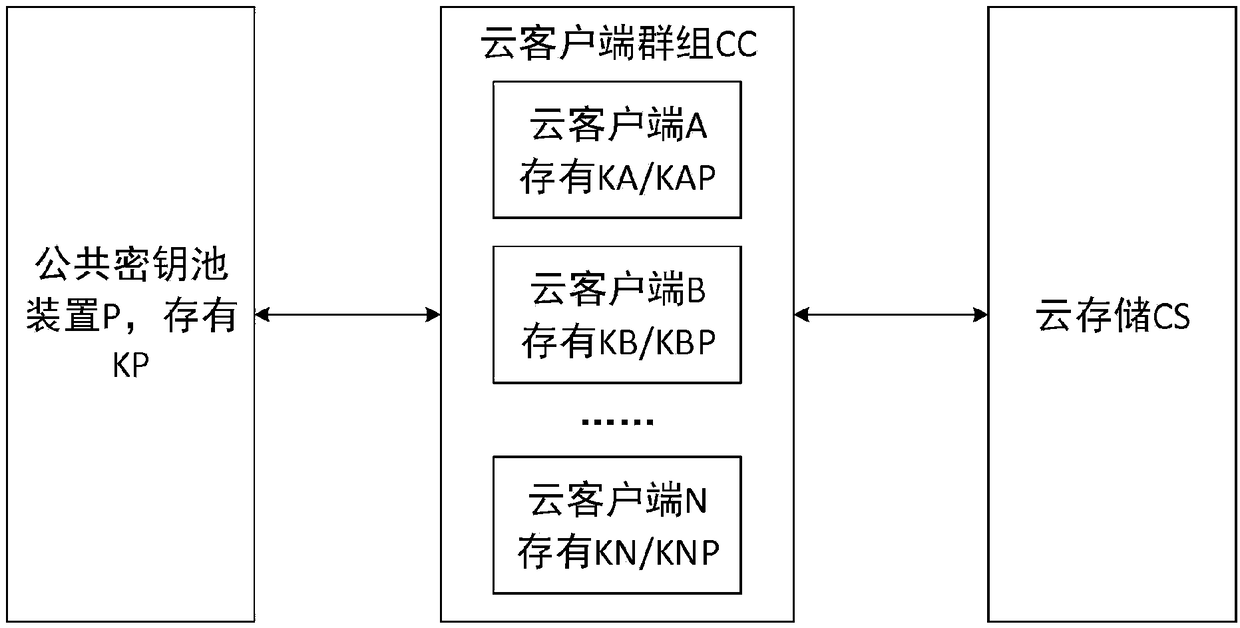
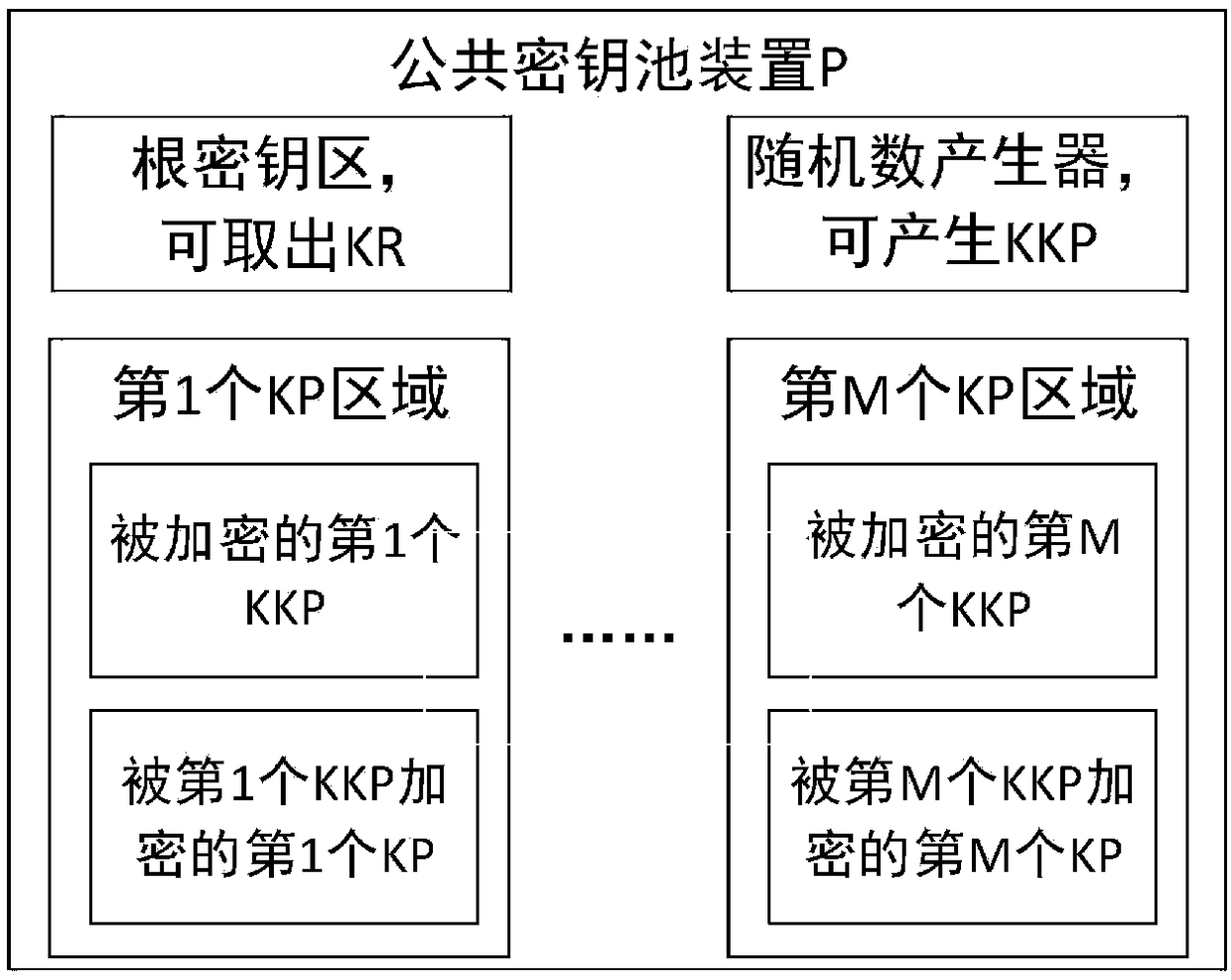
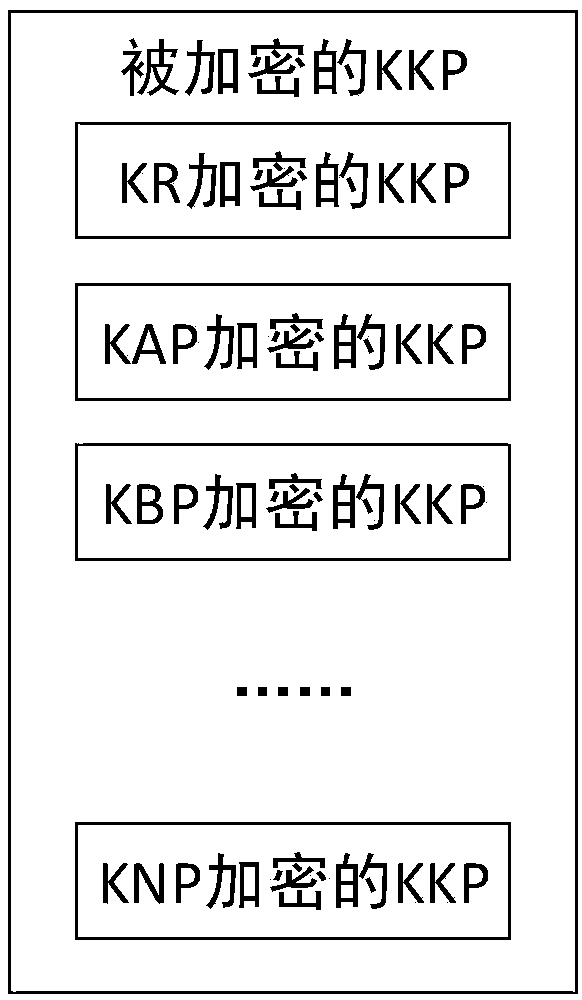
A cloud storage security control method and system based on a public key pool
A technology of security control and key pool, which is applied in the field of cloud storage, can solve problems such as insufficient security for the execution environment of encryption programs on the client side, inability to achieve true randomness of keys, and insufficient security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0066] Figure 5 The timing diagram of the storage method provided by the embodiment of the present invention. Figure 7 It is a flow chart of a storage method provided by the embodiment of the present invention, and the specific steps of a cloud storage security control method based on a public key pool are as follows:
[0067] Step 1.1 The client uploads the Hash value of the data file and each algorithm ID to the server: before uploading the data file, the client first calculates the Hash value of the data file and uploads the Hash value to the server. At the same time, the ID of each algorithm (including the key selection algorithm fp, the primary key generation algorithm fg and the self-selected key generation algorithm ff, the same reason below) is also uploaded. Wherein, the self-selected key generation algorithm ff can be selected unique to the client, or ff0 can be selected. In this embodiment, it is assumed that ff0 is selected, that is, ff(x)=x is selected, which ...
Embodiment 2
[0086] Figure 8 It is a flow chart of a storage method provided in this embodiment. The sequence diagram of the storage method of the present embodiment is consistent with Embodiment 1, and the specific steps of a cloud storage security control method based on a public key pool are as follows:
[0087] Step 2.1 The user end uploads the Hash value of the data file and each algorithm ID to the cloud server: before uploading the data file, the user end first calculates the Hash value of the data file, and uploads the Hash value to the cloud server. At the same time, the ID of each algorithm is uploaded. Among them, the self-selected key generation algorithm ff chooses the unique one of the client instead of ff0, that is, chooses ff(x)≠x, which means that the privacy and confidentiality function that only belongs to the individual is used. This file is unique to the user and cannot be used. Participate in ciphertext deduplication.
[0088] Step 2.2 The cloud server saves the H...
Embodiment 3
[0097] Figure 6 The timing diagram of the storage method provided by the embodiment of the present invention. Figure 9 A flow chart of a file reading method provided by an embodiment of the present invention, a cloud storage security control method based on a public key pool, based on the above-mentioned embodiment, the specific steps for the client to read a file are as follows:
[0098] Step 3.1 The client initiates a file read request: the client sends the Hash value of the file to be read and each algorithm ID to the server.
[0099] Step 3.2 The server sends the corresponding information to the client: After receiving the file Hash value and algorithm ID, the server finds the information corresponding to the Hash value and algorithm ID, and sends the ciphertext and personal key to the client.
[0100] Step 3.3 The client obtains the file key: the client uses the private key to decrypt the personal key to obtain a true random number r. Use the public key of P to encryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com