Privacy protection method during data aggregation of wireless sensor network
A wireless sensor and privacy protection technology, applied in the field of privacy protection, can solve problems such as increased calculation consumption, high calculation complexity, and large amount of additional calculation, and achieve the effect of small number of public key digits and fast calculation speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
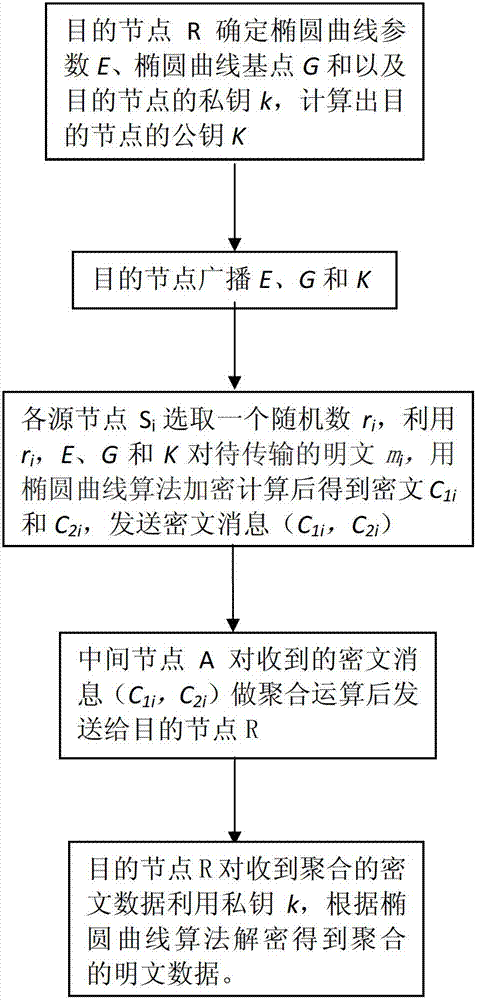
[0027] When realizing additive aggregation privacy protection in the present invention, the steps are as follows:
[0028] (1) First, the destination node R determines the elliptic curve E, the base point G and the private key k, calculates the public key K, and broadcasts the elliptic curve parameters, G and K;
[0029] (2) Each source node S i Encode the plaintext to be transmitted m i to a point M on the elliptic curve E i , choose a random number r i , according to the following formula to calculate C 1i and C 2i , send a message (C 1i , C 2i ); the value of i is greater than 1 but less than the number of source nodes;
[0030] C 1i = r i G
[0031] C 2i = r i K+M
[0032] (3) The intermediate node A receives the message sent by each source node (C 1i , C 2i ), after doing addition operation to get (ΣC 1i , ΣC 2i ), send it to the destination node R;
[0033] (4) Destination node R receives (ΣC 1i , ΣC 2i ) and then use the private key k to calculate th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com