Patents
Literature
48results about How to "Improve the security system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
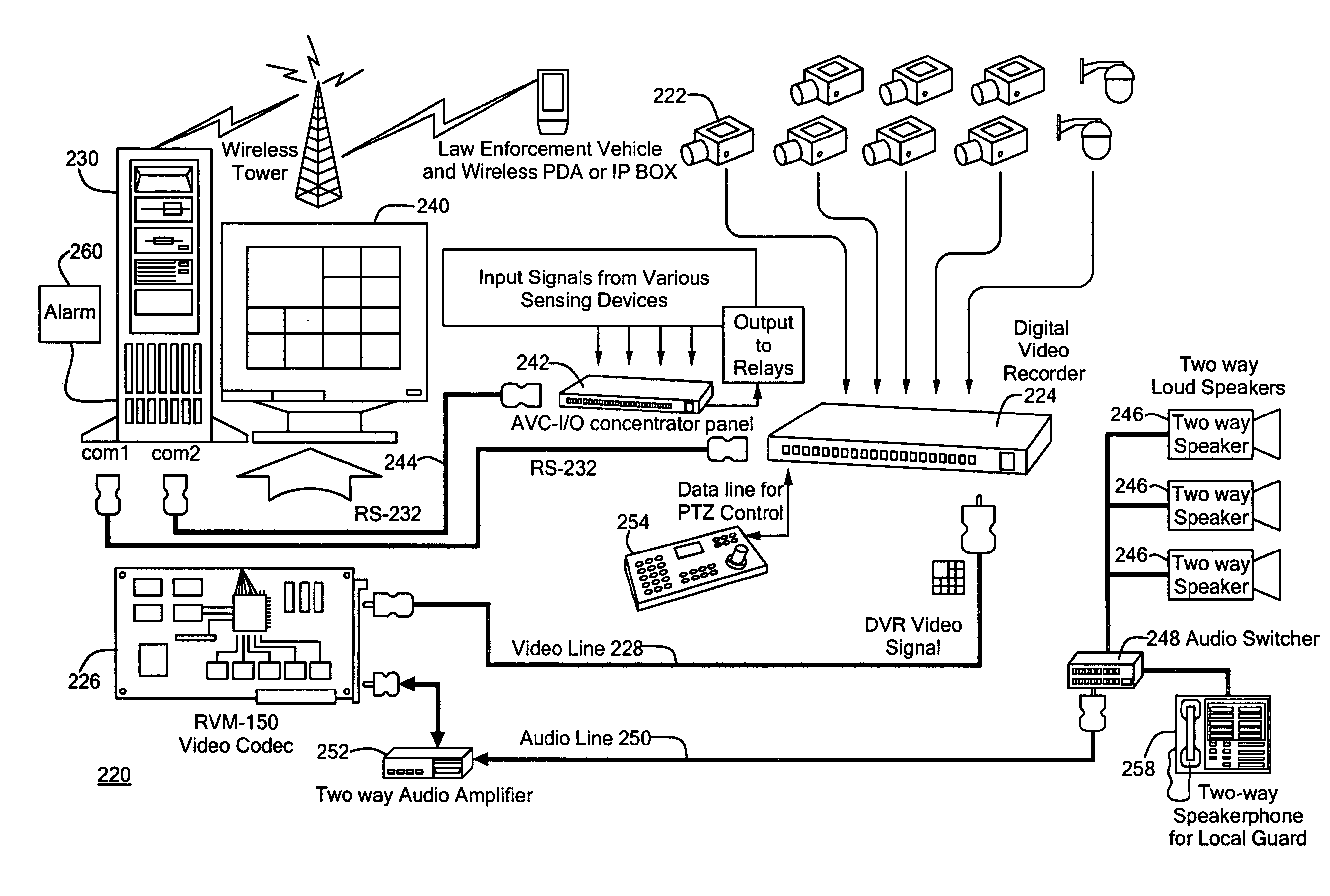
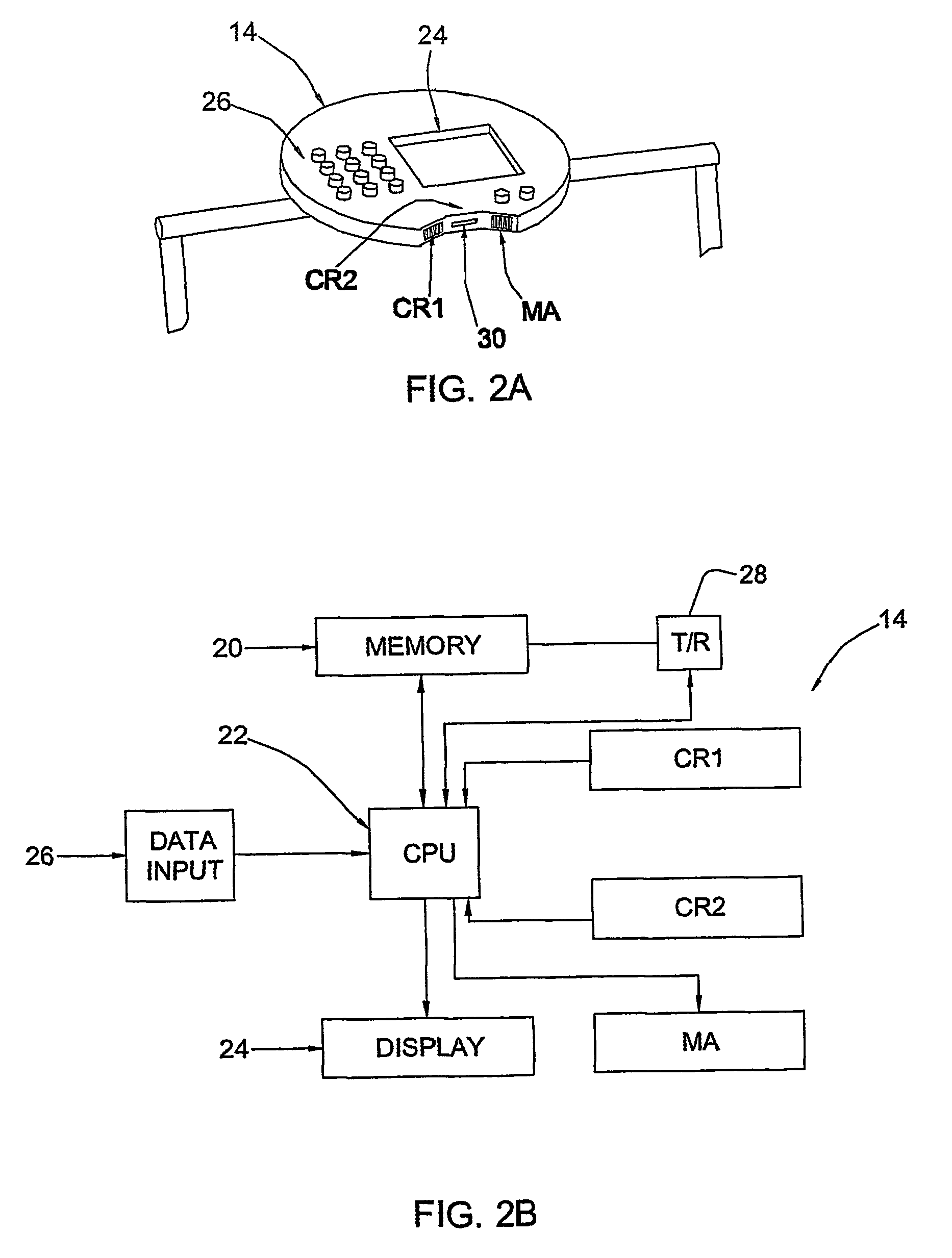
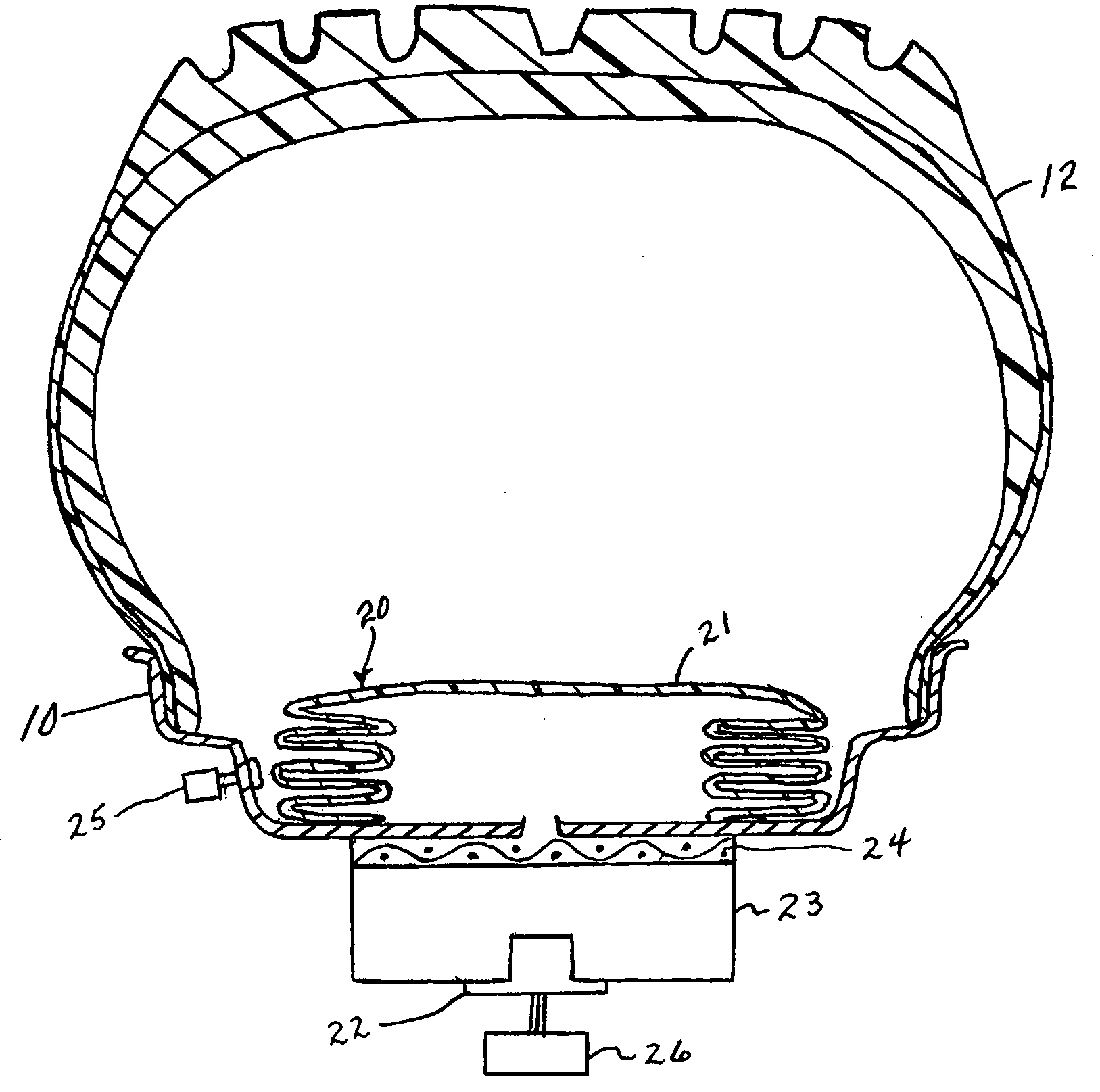
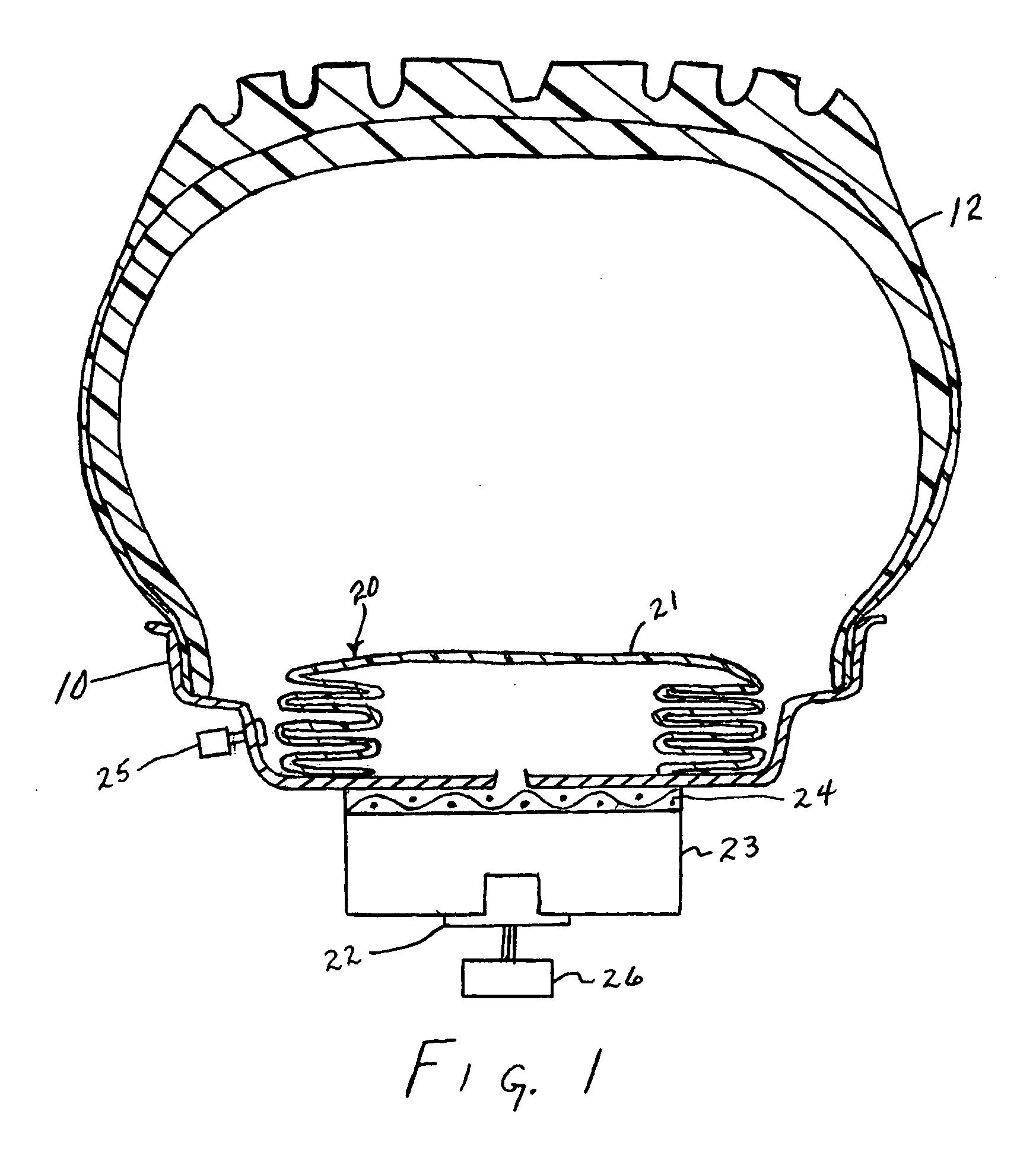
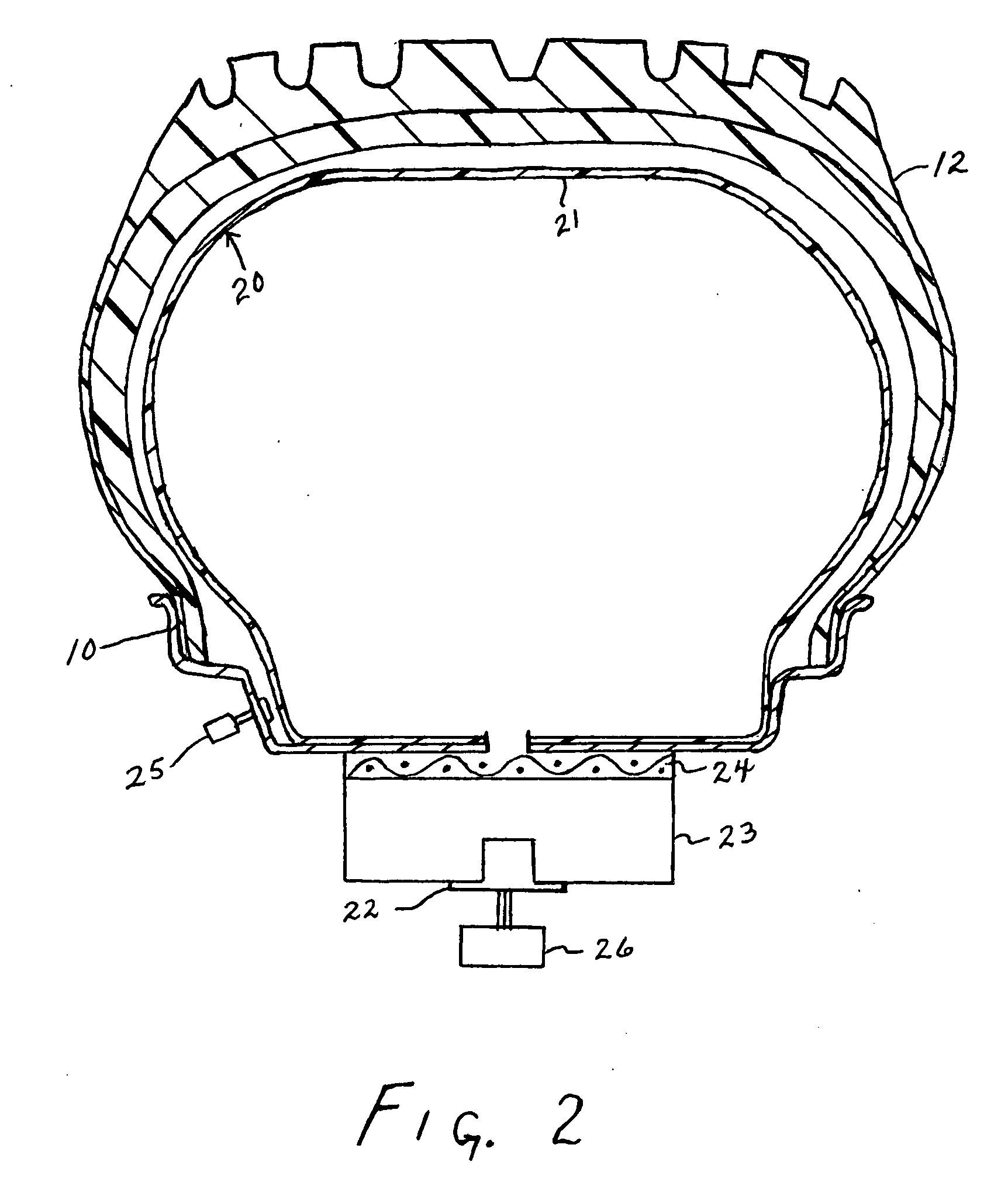
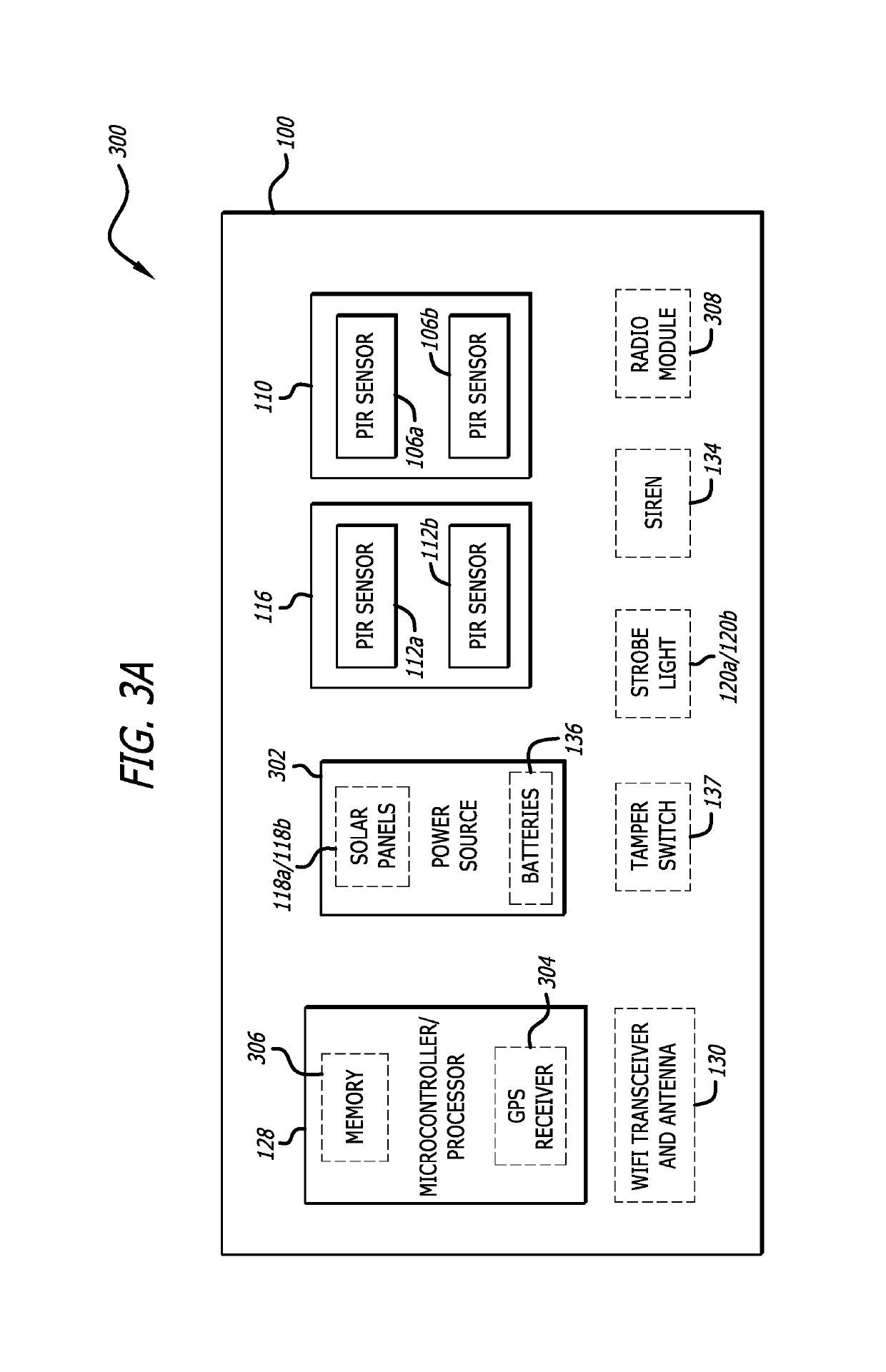
Video monitoring system
InactiveUS20050273831A1Improve service capabilitiesLess costlyColor television with pulse code modulationColor television with bandwidth reductionVideo monitoringSignal routing
A video monitoring system for a plurality of sites. A site security system is located at each site and includes one or more video cameras each outputting a video signal and a processor configured to receive a video signal from each camera, detect predetermined events based on the video signal, generate a video alarm signal upon the detection of an event, transmit the video alarm signal to a central station, and establish a video signal link either with the central station or one of a plurality of satellite stations according to a predetermined protocol upon the transmission of a video alarm signal. A central station includes a router for routing any received video signal to one or more workstations and for routing the video alarm signal to a server configured to associate the video alarm signal with a particular satellite station and to forward the video alarm signal to that satellite station. The satellite station includes a workstation configured to receive the video alarm signal from the central station and to receive the video signal from the site security system.
Owner:VISENTRY
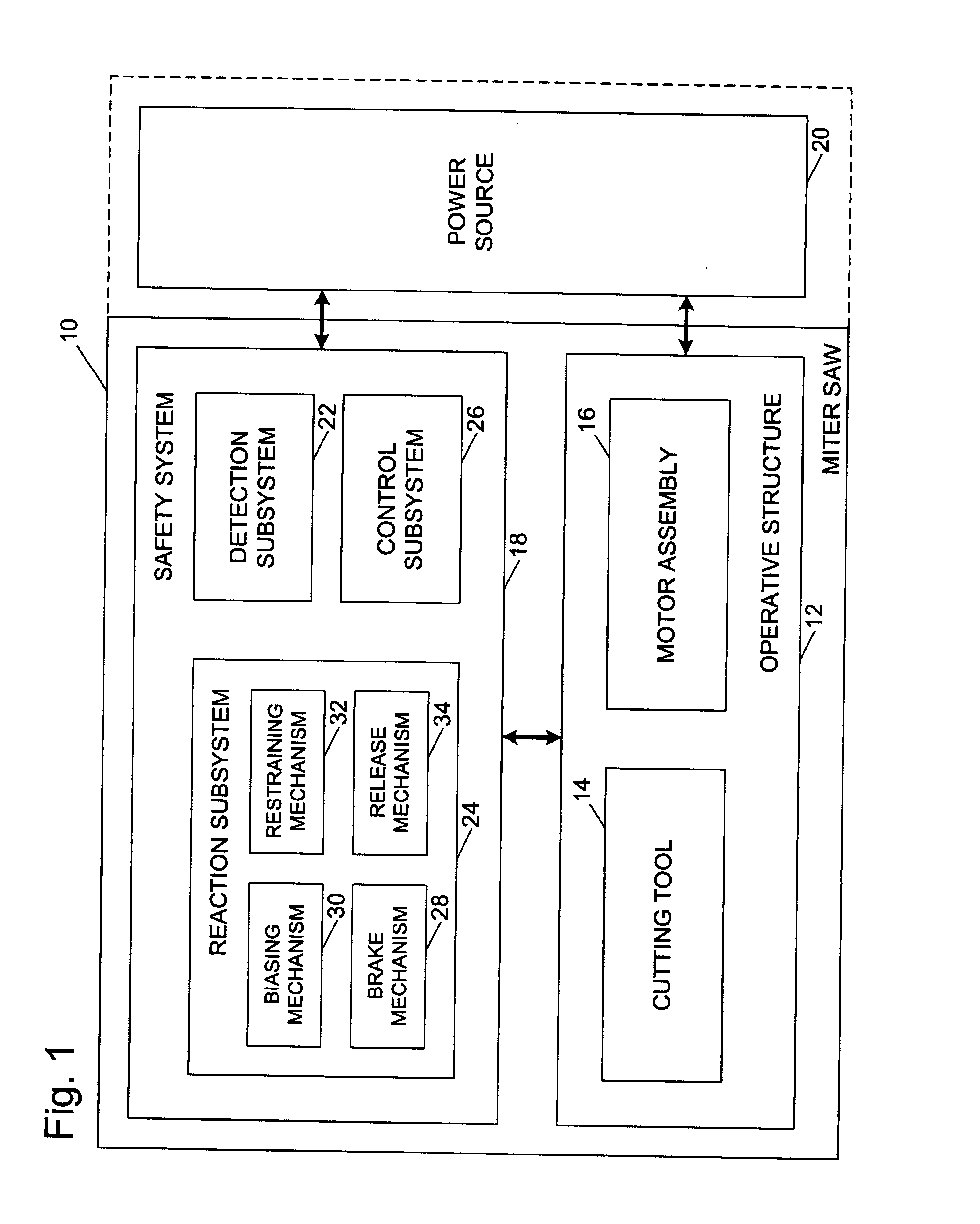
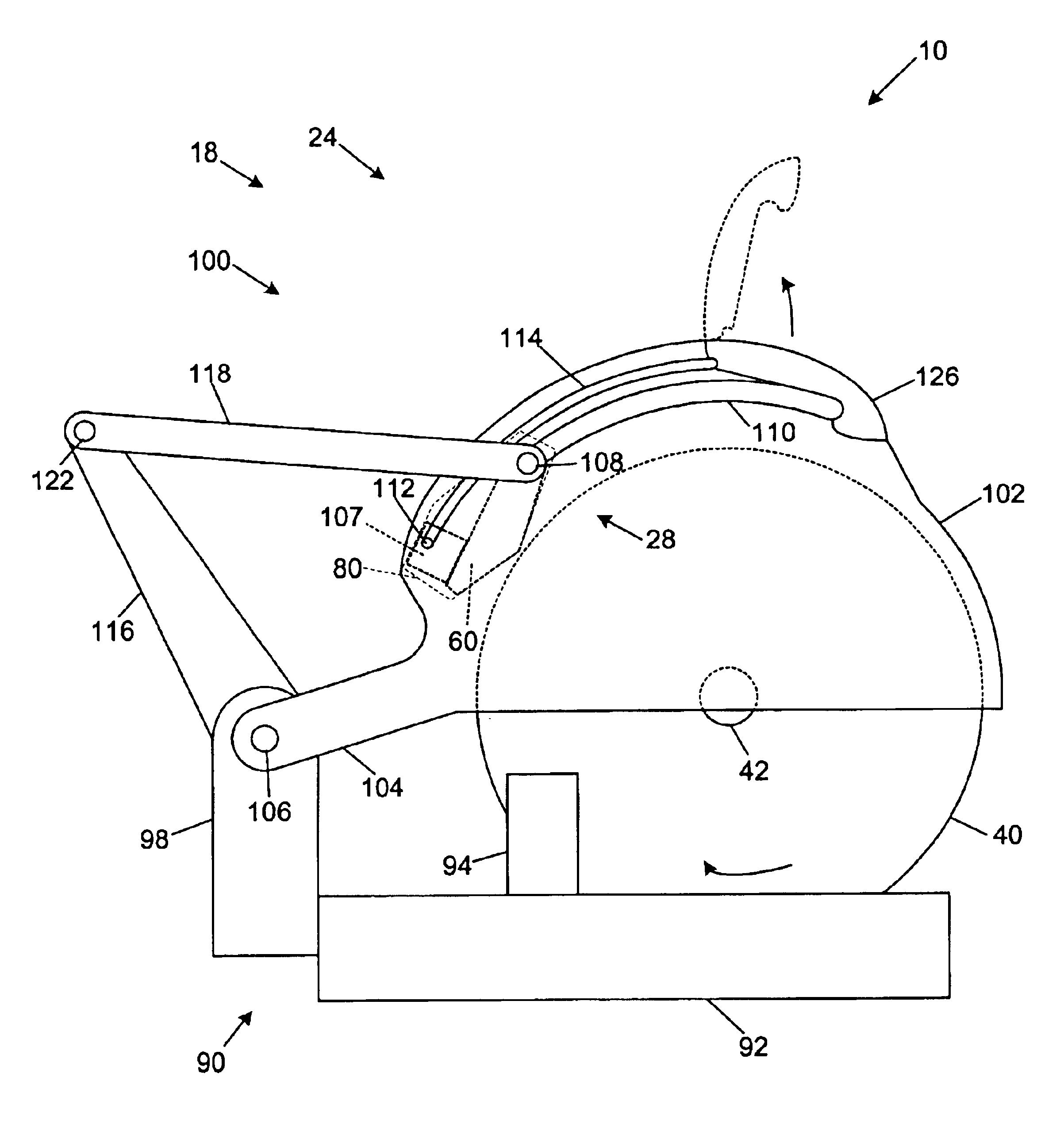
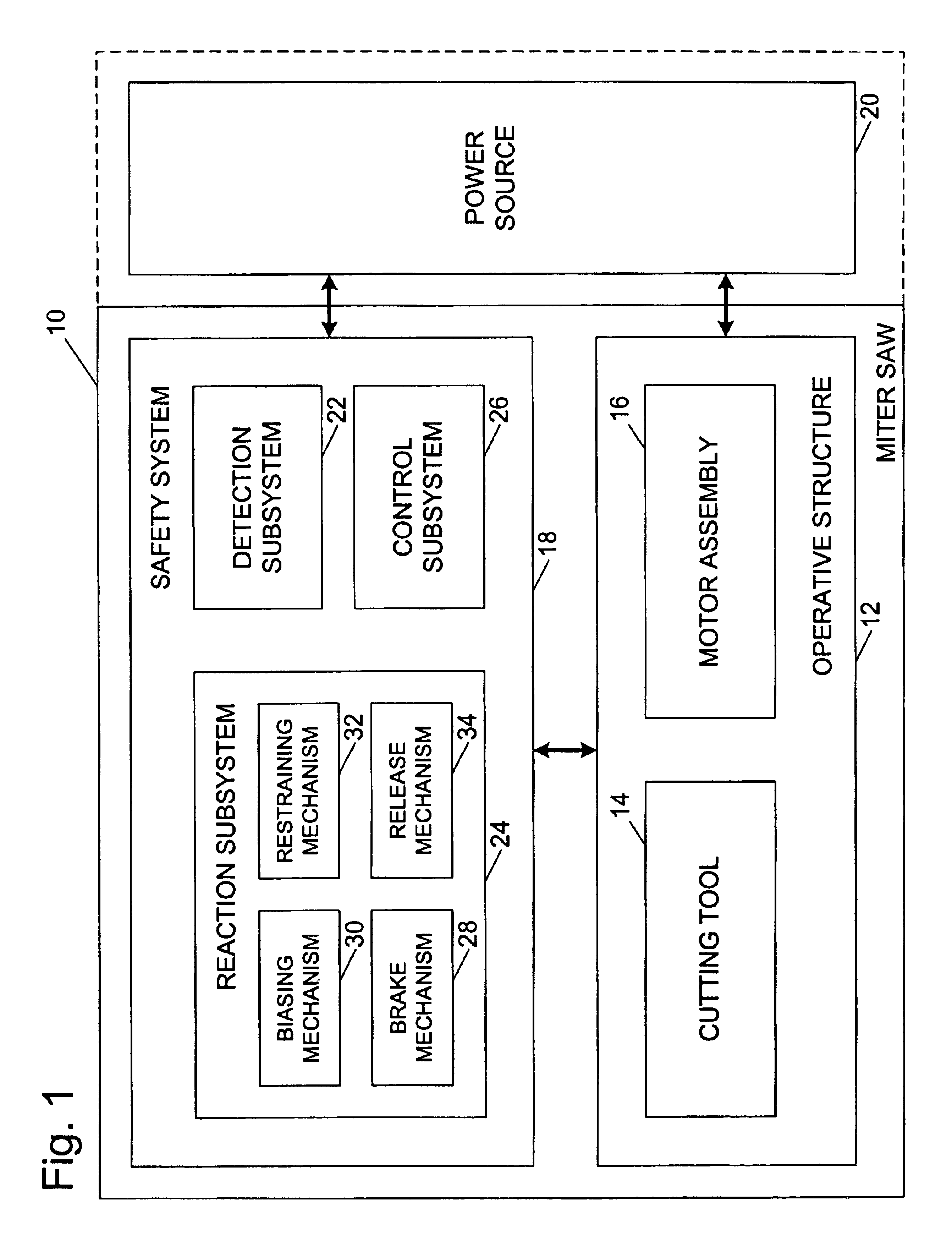
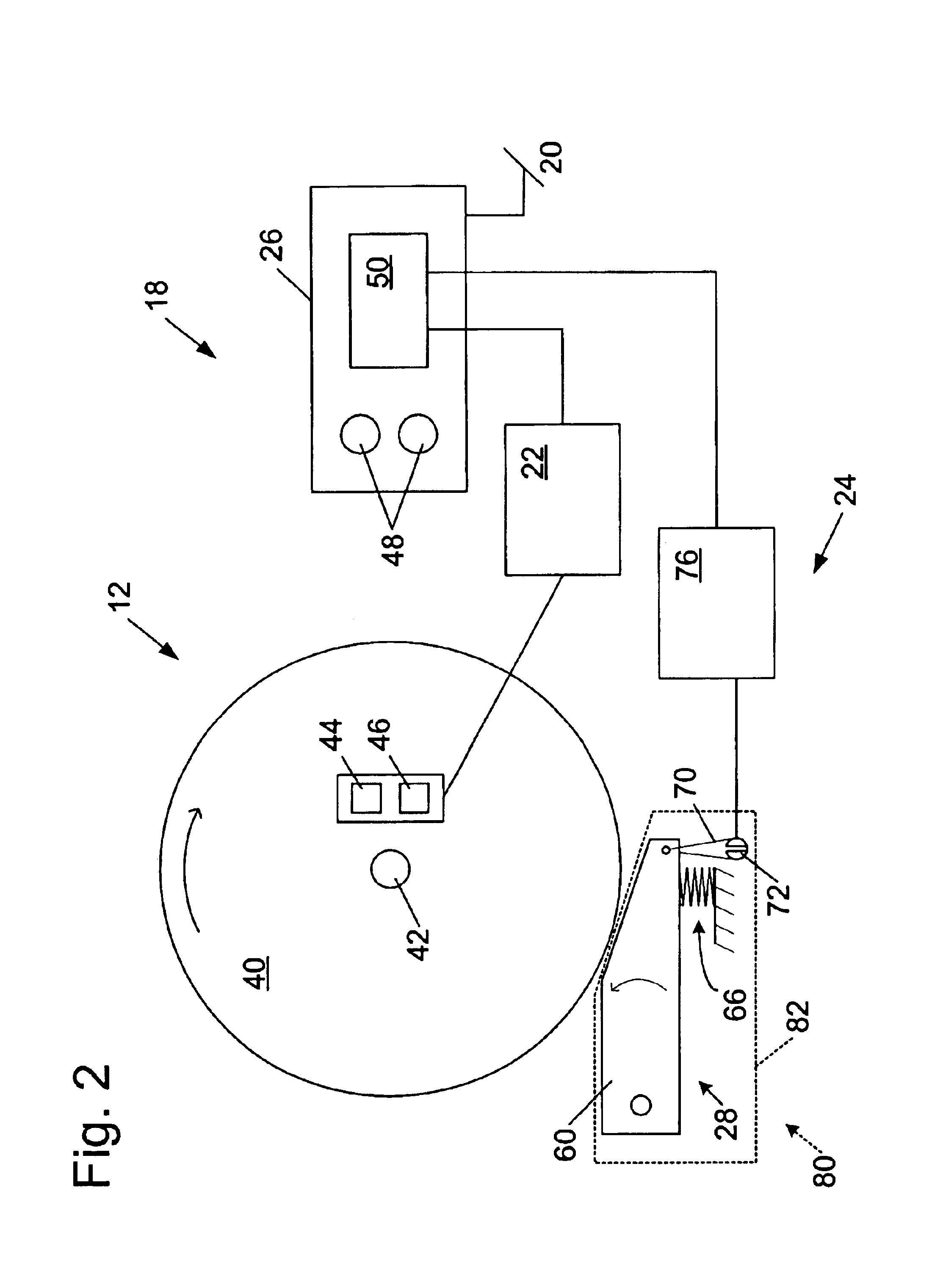
Miter saw with improved safety system
InactiveUS6826988B2Increase opportunitiesLimit and even prevent injuryEmergency protective circuit arrangementsEngineering safety devicesEngineeringWoodworking machine
A woodworking machine is disclosed having a base, a blade, a detection system adapted to detect a dangerous condition between a person and the blade, and a reaction system associated with the detection system to cause a predetermined action to take place upon detection of the dangerous condition. The blade is rotatable, and moves into a cutting zone to cut a workpiece. The predetermined action may be to stop the blade from rotating and / or to stop movement of the blade toward the cutting zone.
Owner:SAWSTOP HLDG LLC
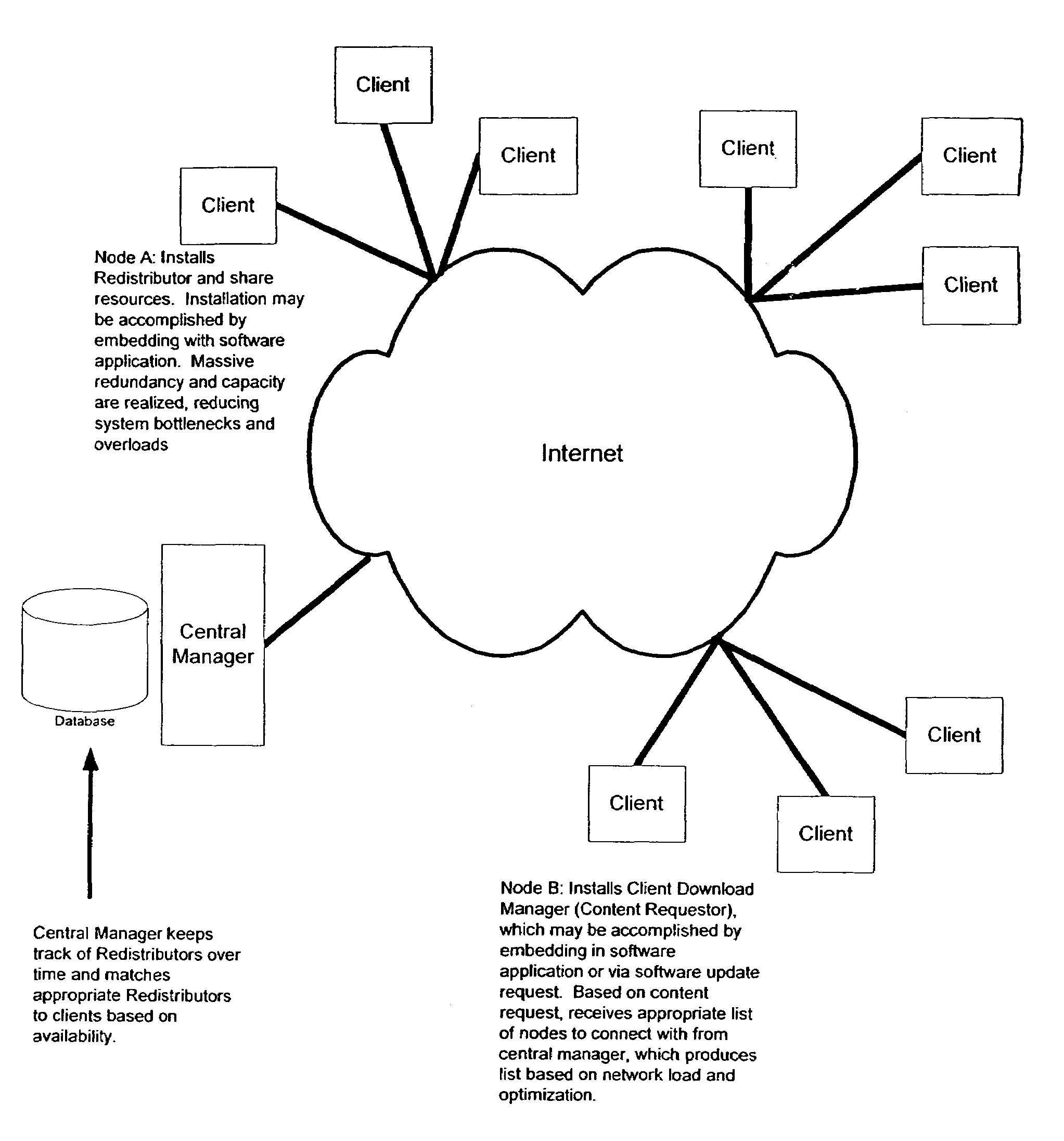
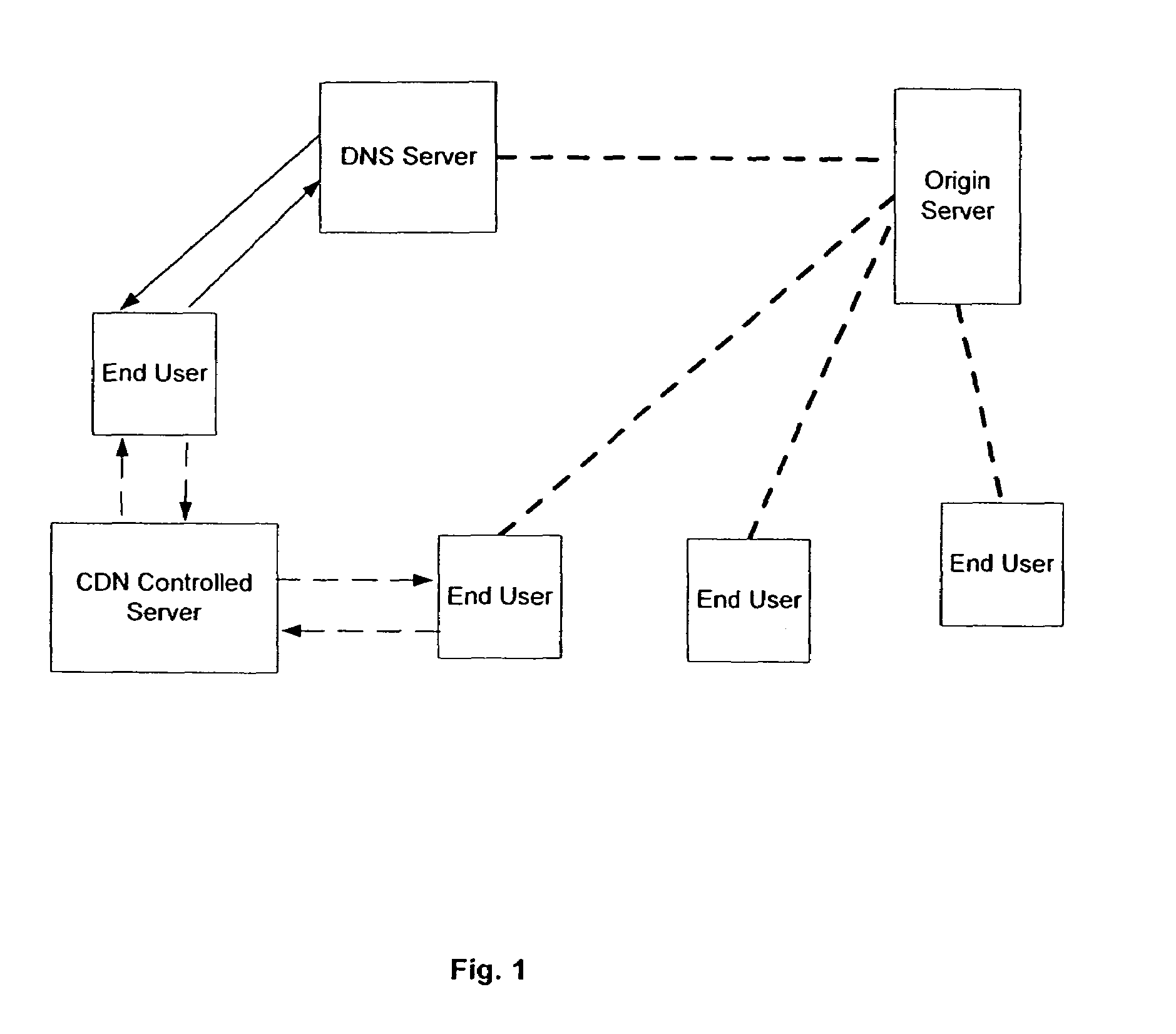
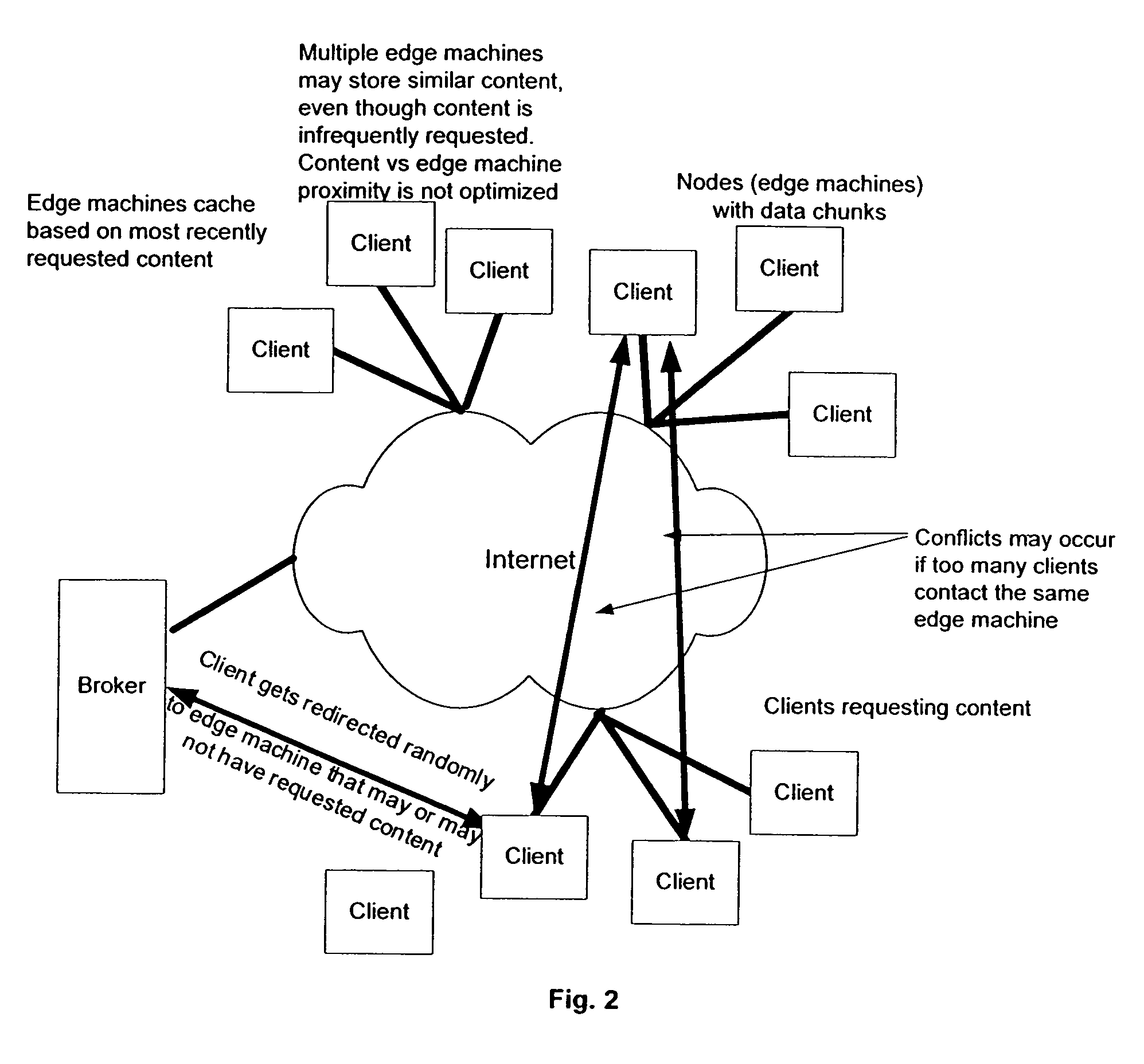
Intelligent virtual content distribution network system and method
InactiveUS7653689B1Low costCost efficientMultiple digital computer combinationsTransmissionContent distributionClient-side
A method and system of use of a Content Distribution Network (CDN), wherein server functionality and client functionality are unbundled. Client software, which governs the accesses and request of the information from the CDN (i.e., server) is provided by a “thin” client architecture. The thin client software is capable of running on an as needed basis, therefore not allocating significant portions of available memory, except when being accessed. The server functionality retains the bulk of the software functionality to manage locally stored content, process content requests, and forward the requested data to content requesters running the client software.
Owner:ABACAST +2
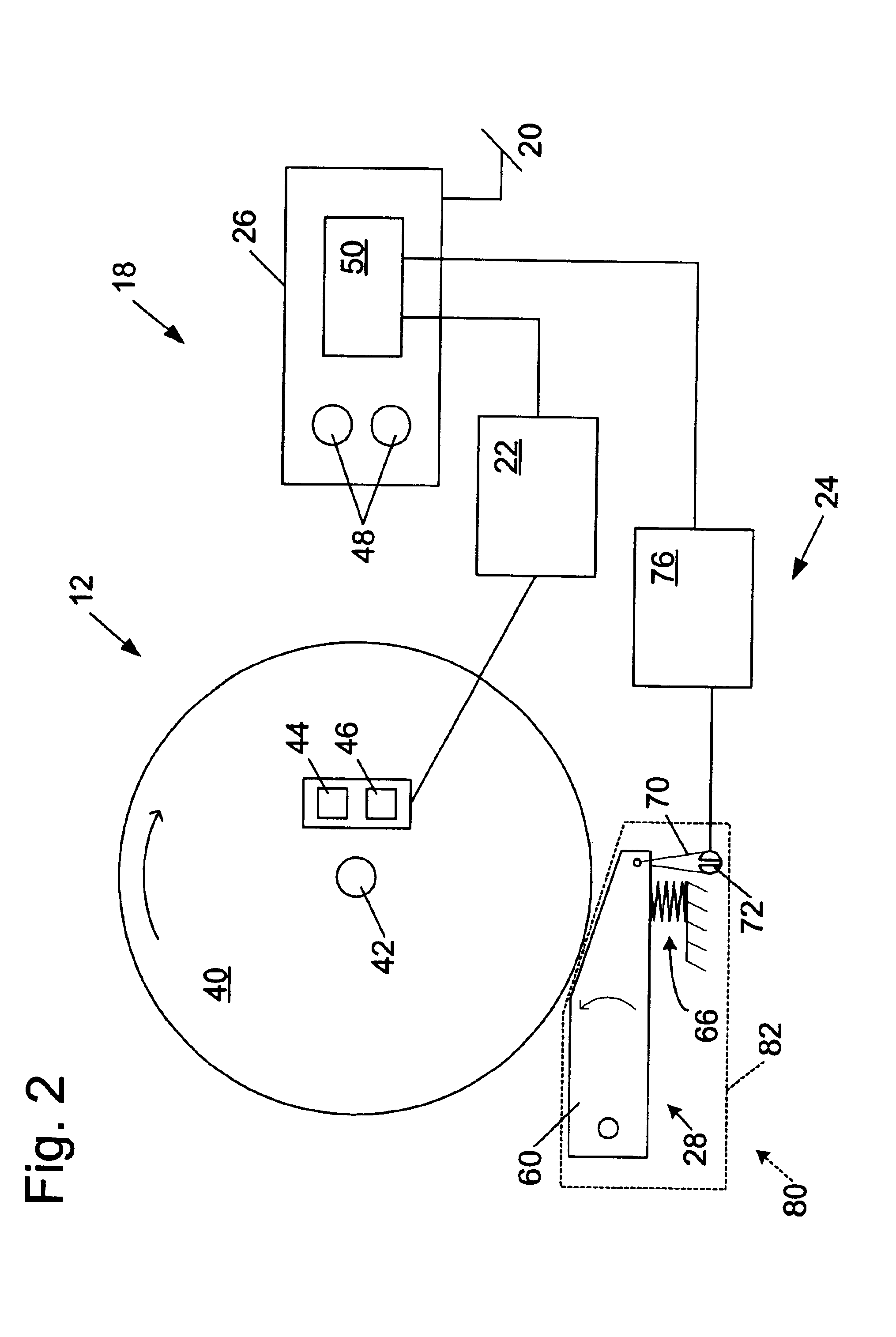
Miter saw with improved safety system
InactiveUS6945148B2Increase opportunitiesLimit and even prevent injuryOther plywood/veneer working apparatusMechanically actuated brakesEngineeringMechanical engineering
A miter saw is disclosed having a base, a blade supported by the base, a detection system adapted to detect a dangerous condition between a person and the blade, and a reaction system associated with the detection system to cause a predetermined action to take place upon detection of the dangerous condition. The blade is rotatable, and moves into a cutting zone to cut a workpiece. The predetermined action may be to stop the blade from rotating, to create an impulse against movement of the blade into the cutting zone, or to cause the blade to move away from the cutting zone.
Owner:SAWSTOP HLDG LLC
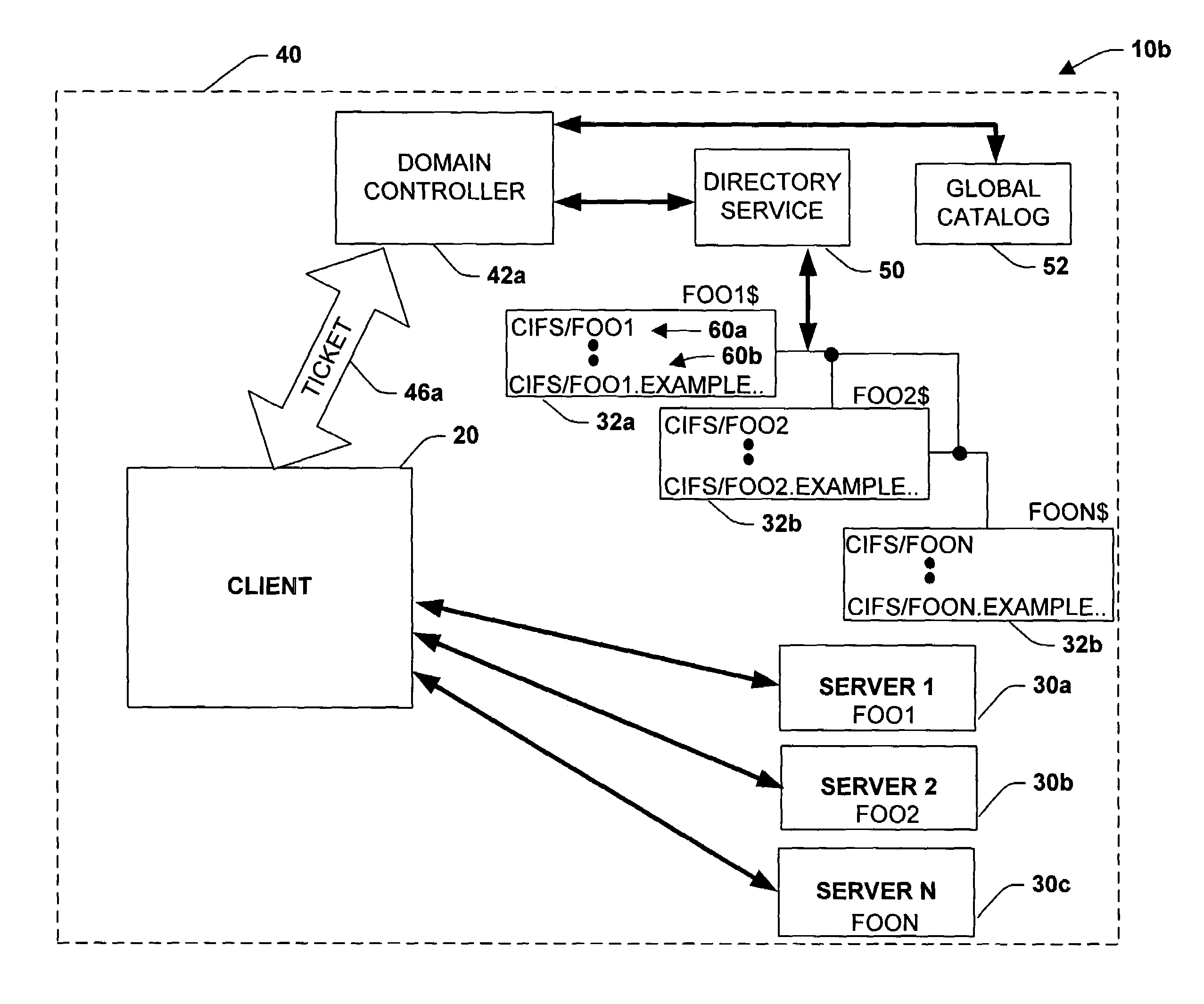
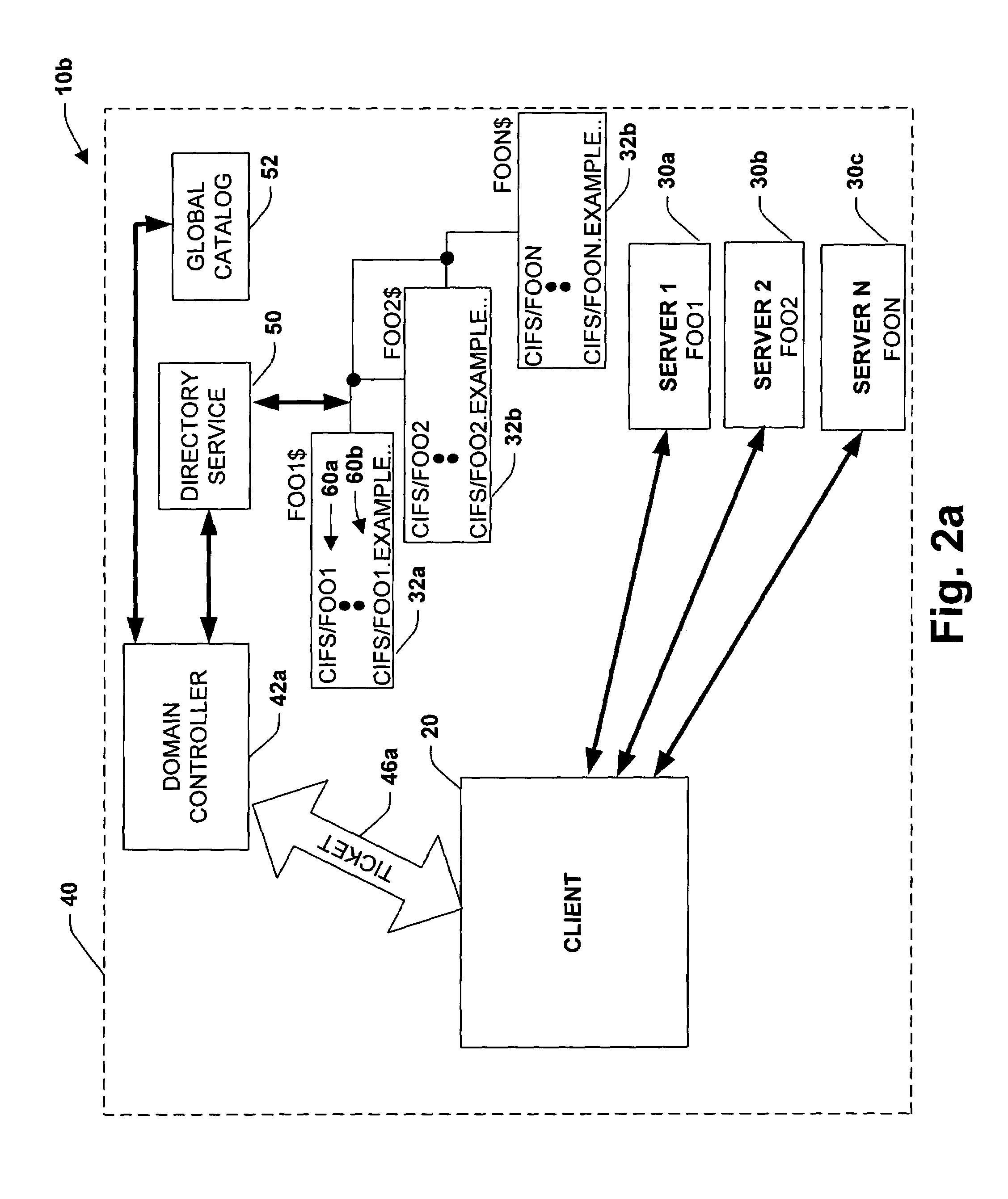
System and method for managing and authenticating services via service principal names
InactiveUS7308709B1Reduce administrative burdenConvenient registrationDigital data processing detailsMultiple digital computer combinationsAuthenticationComputer science
A methododology is provided for facilitating authentication of a service. The methodology includes making a request to a first party for authentication of a service, the request including a first alias. A list of aliases associated with the service is then searched enabling a second party making the request to access the service if a match is found between the first alias and at least one alias of the list of aliases.
Owner:MICROSOFT TECH LICENSING LLC
Authentication method using multi-factor eye gaze
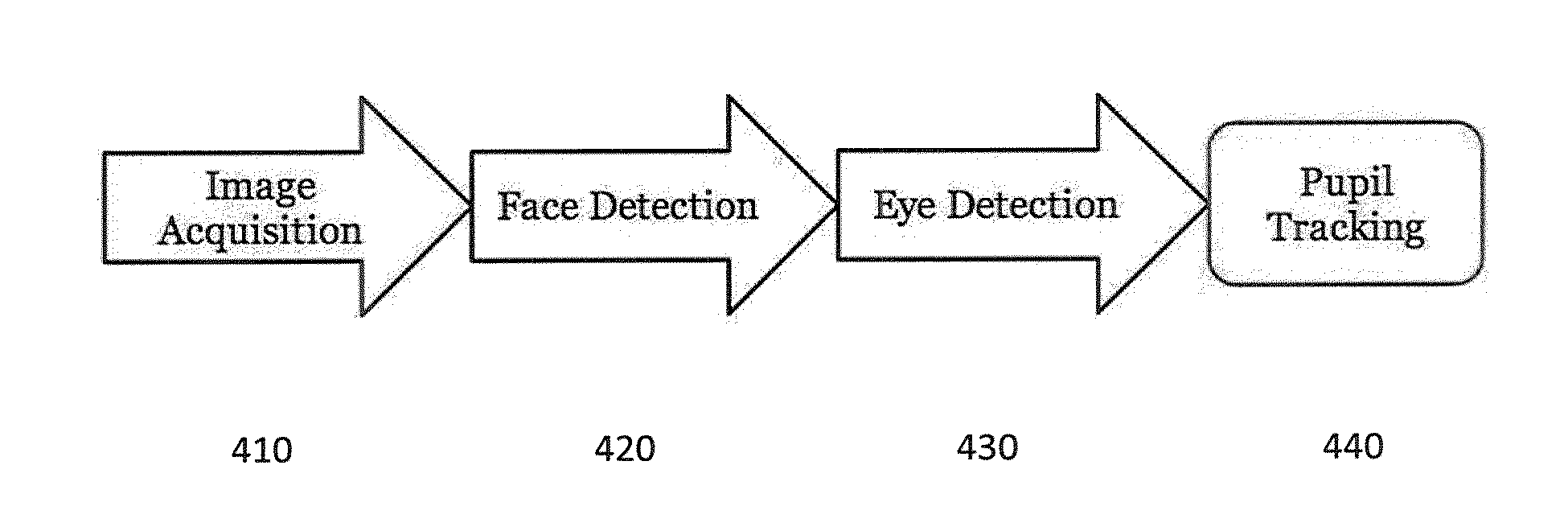
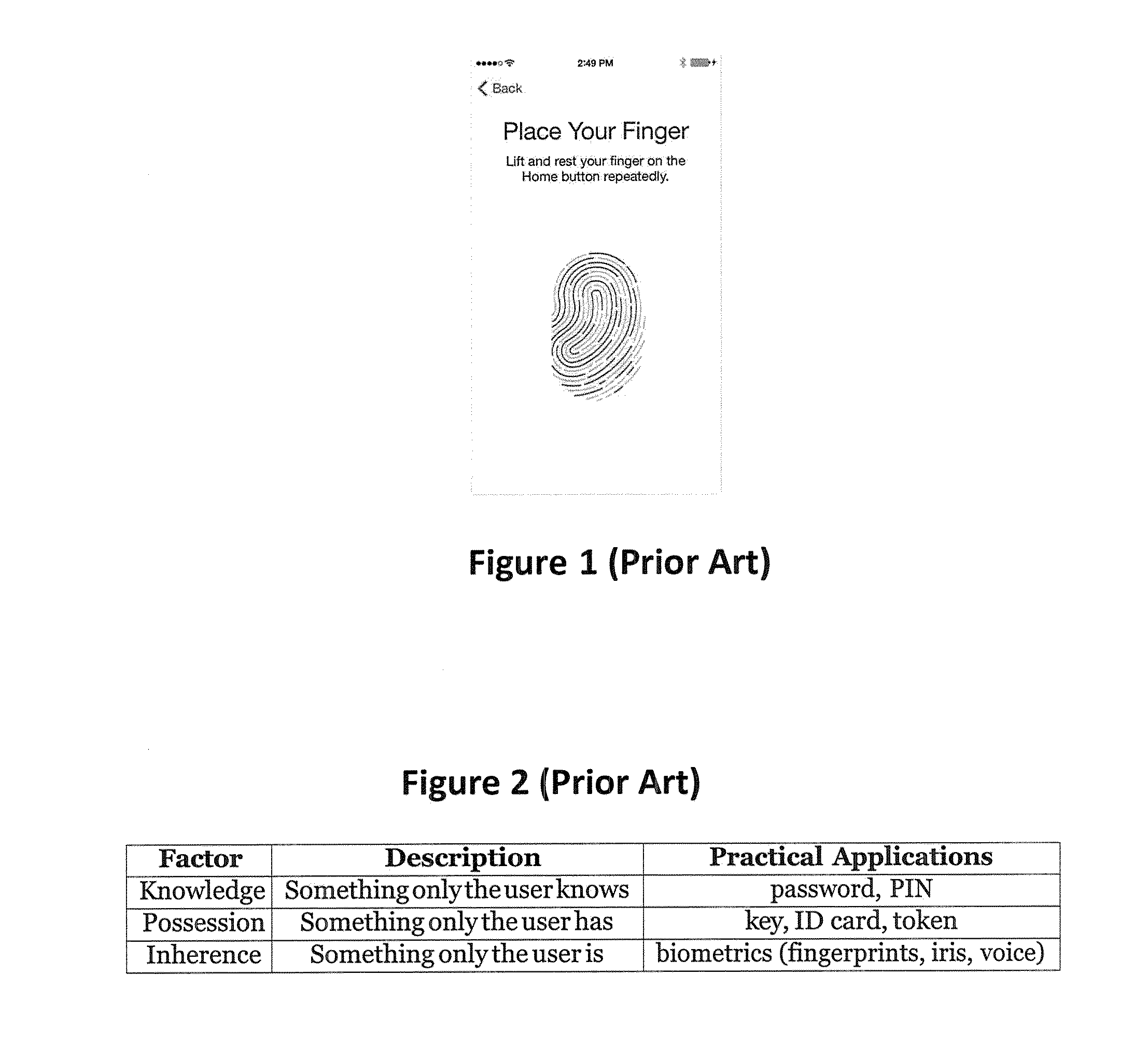
InactiveUS20150302252A1Improve the security systemImprove availabilityImage analysisAcquiring/recognising eyesPasswordPupil
A method for rapid and robust one-step multi-factor authentication of a user is presented, employing multi-factor eye gaze. The mobile environment presents challenges that render the conventional password model obsolete. The primary goal is to offer an authentication method that competitively replaces the password, while offering improved security and usability. This method and apparatus combine the smooth operation of biometric authentication with the protection of knowledge based authentication to robustly authenticate a user and secure information on a mobile device in a manner that is easily used and requires no external hardware. This method demonstrates a solution comprised of a pupil segmentation algorithm, gaze estimation, and an innovative application that allows a user to authenticate oneself using gaze as the interaction medium and biometrics to authenticate an individual's facial structure.
Owner:HERRERA LUCAS A
Method and system for purchasing items
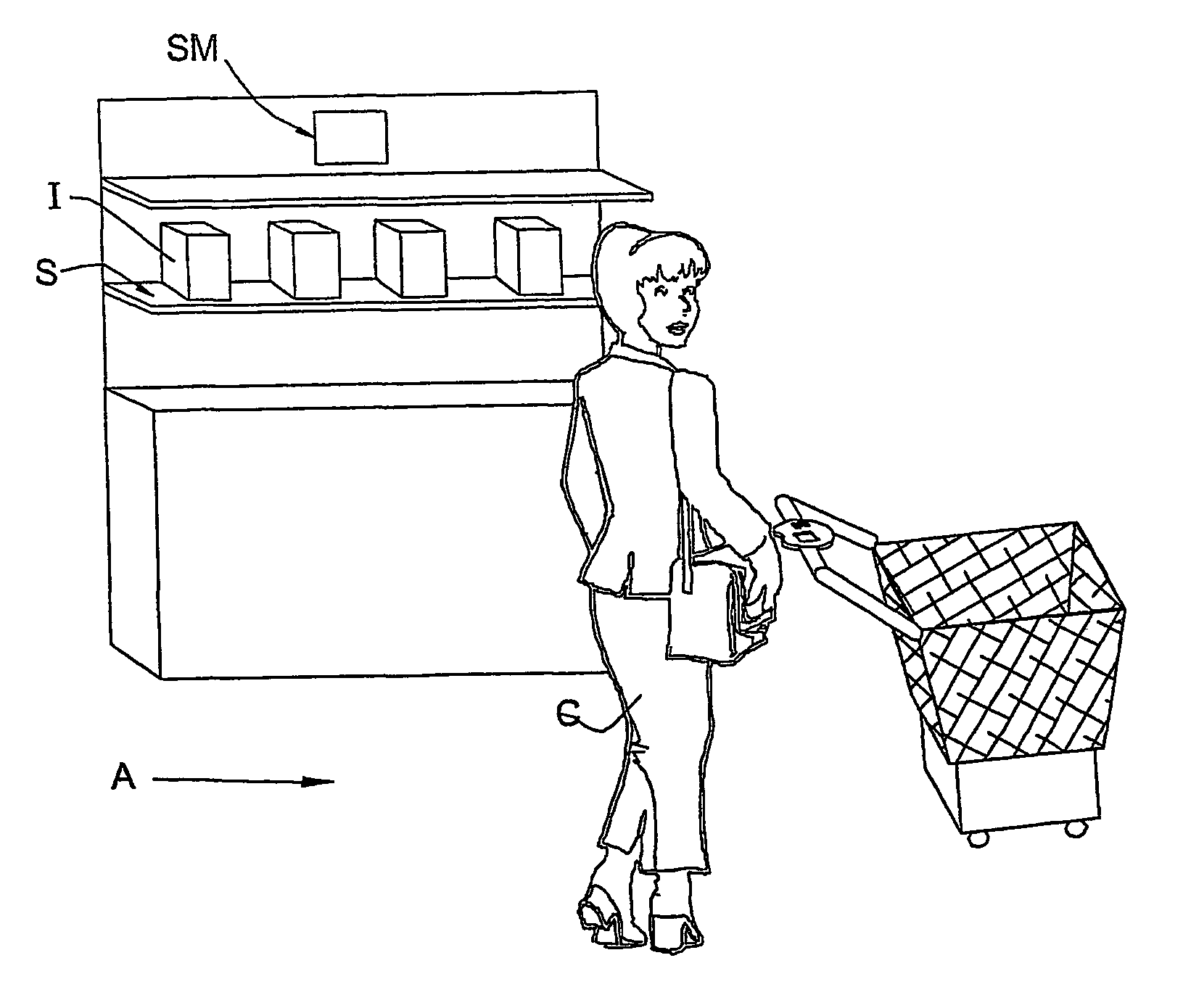
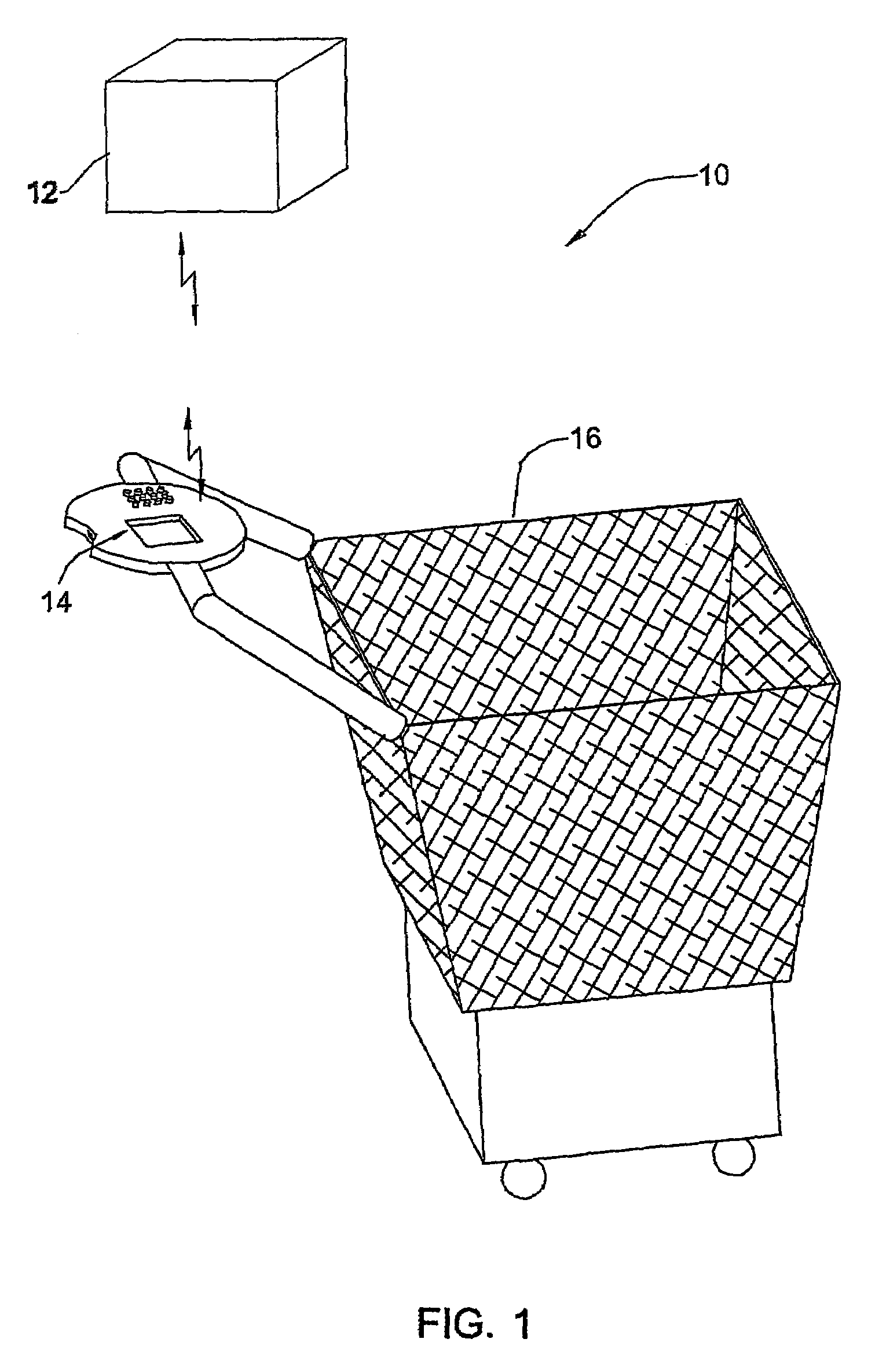
InactiveUS7044369B2Improve the security systemAdd featureCredit registering devices actuationCash registersPurchasingCustomer information
A customer station for use in an items' purchasing system in a supermarket or other retail store is presented. The customer station has an identification assembly, a control unit, a data presentation unit for presenting to the customer information related to selected items, and a deactivator. The identification assembly is operable to identify a nature of an item of customer's interest, and generate data indicative of information related to the item of interest to be presented to the customer. The control unit has a processing system responsive to the generated data indicative of the information related to the item to generate data indicative of the entire sum to be paid by the customer which is to be presented to the customer. The deactivator is operable to deactivate a security tag attached to the item. The entire customer station or at least the identification assembly and the data presentation unit are incorporated in a unit mountable on a supermarket trolley.
Owner:BUYPASS SYST 1999
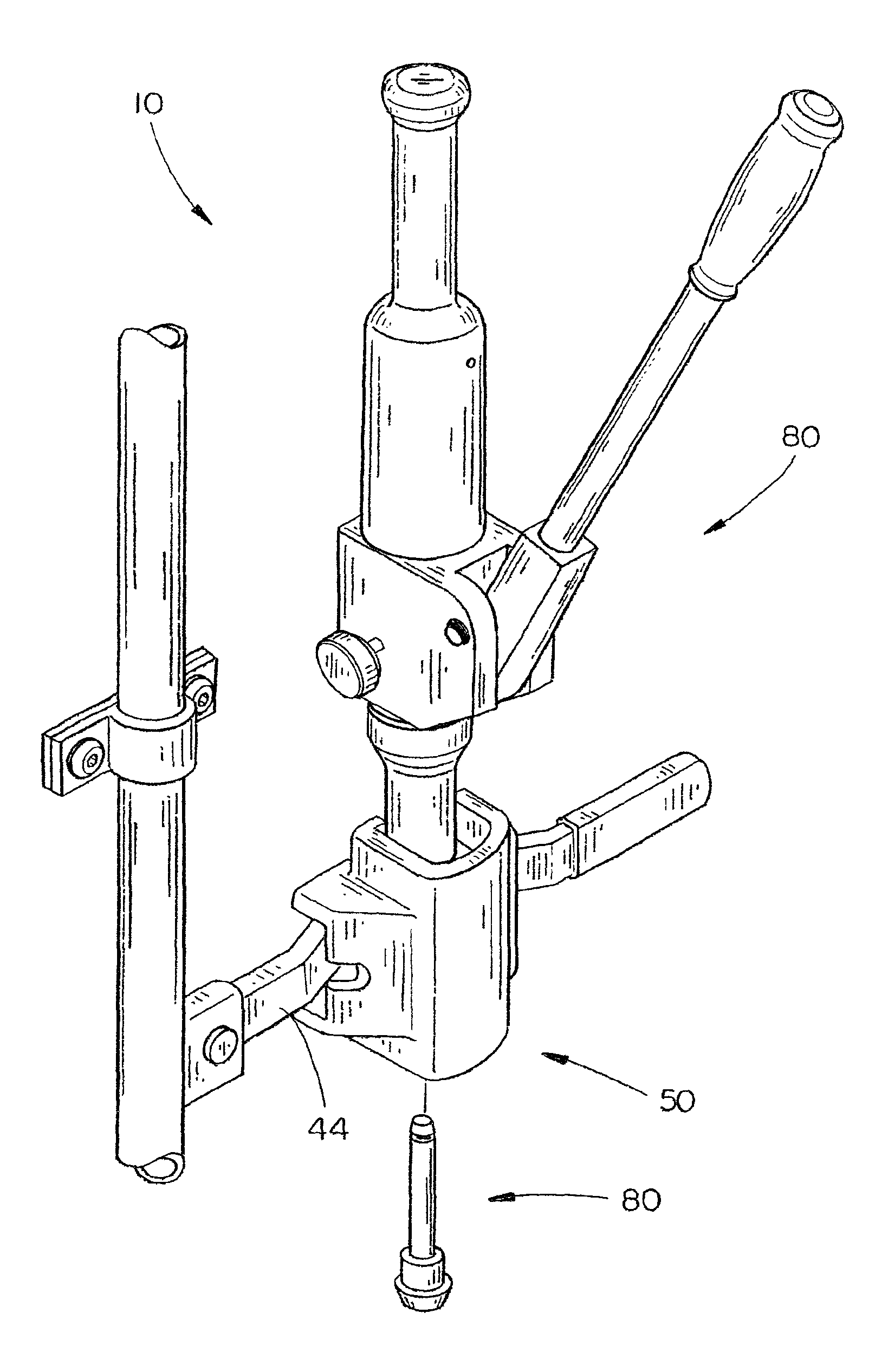
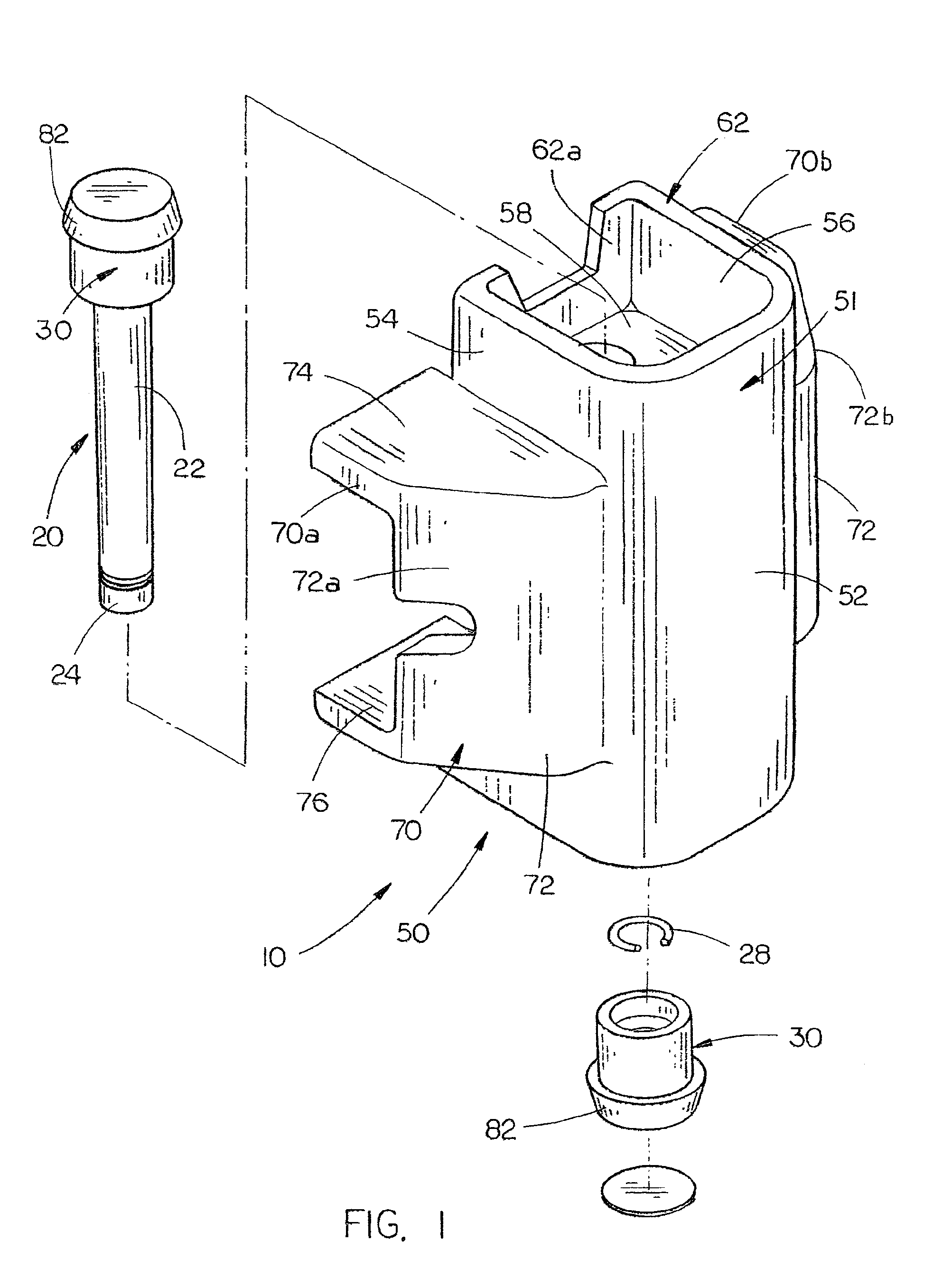
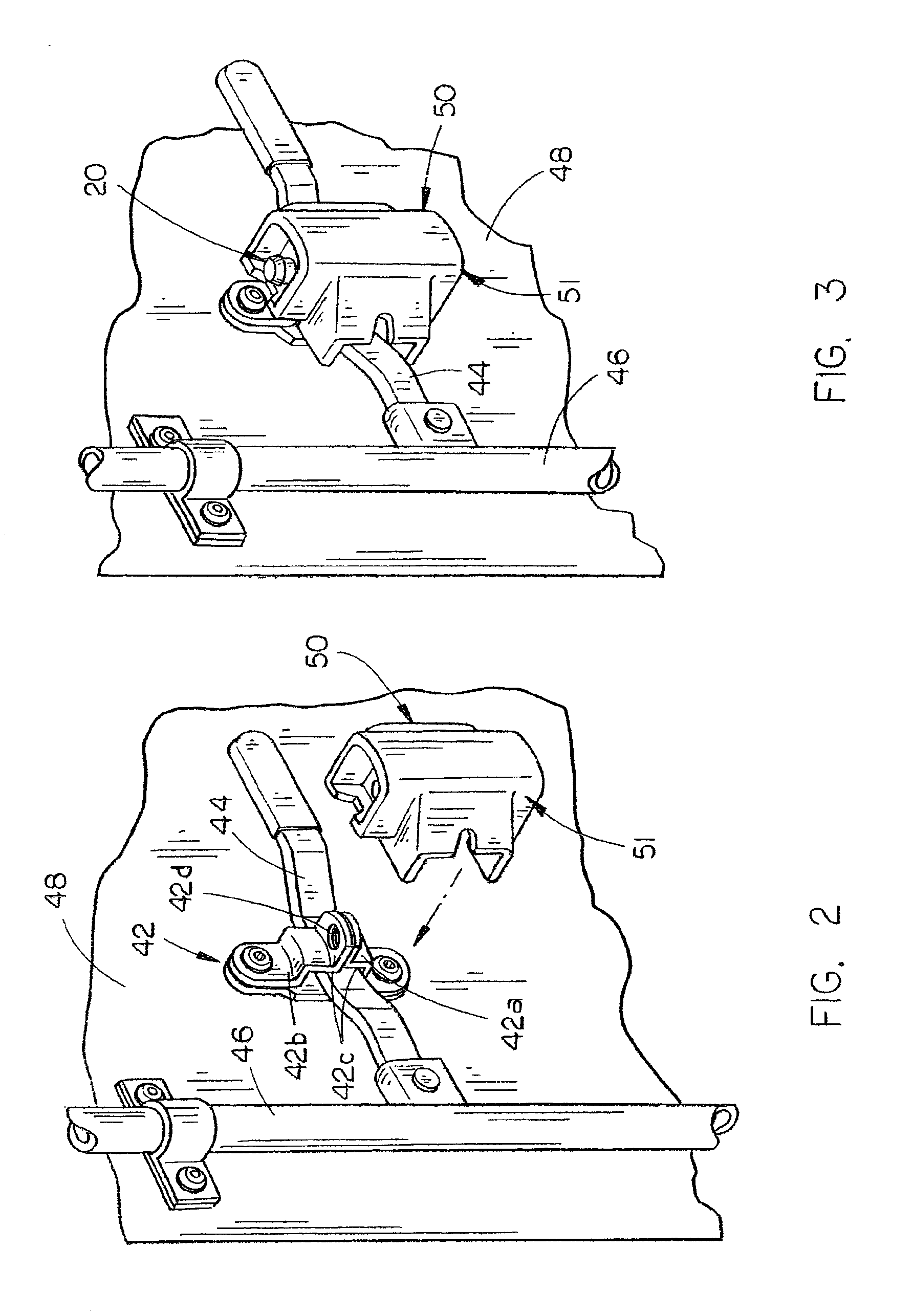
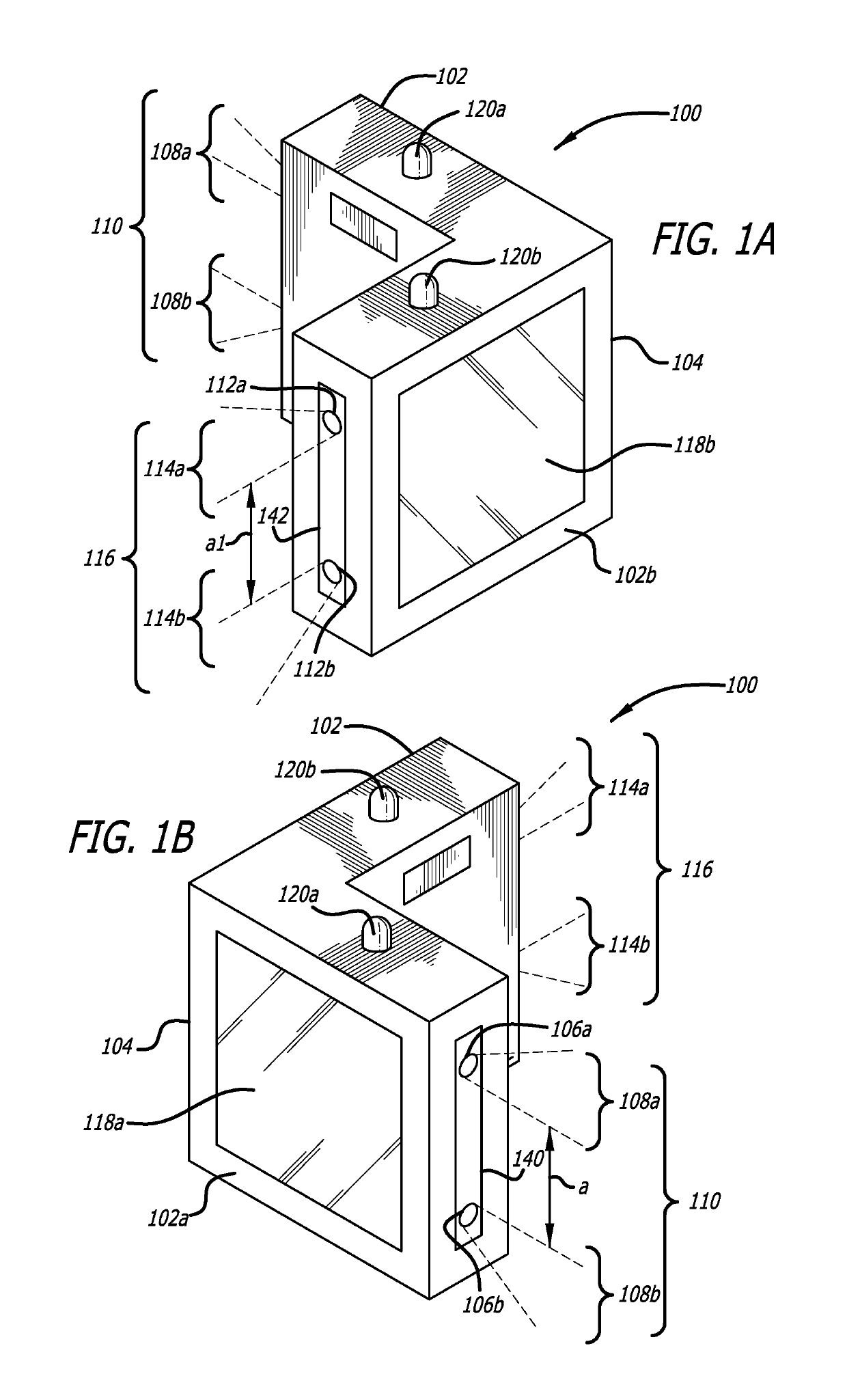
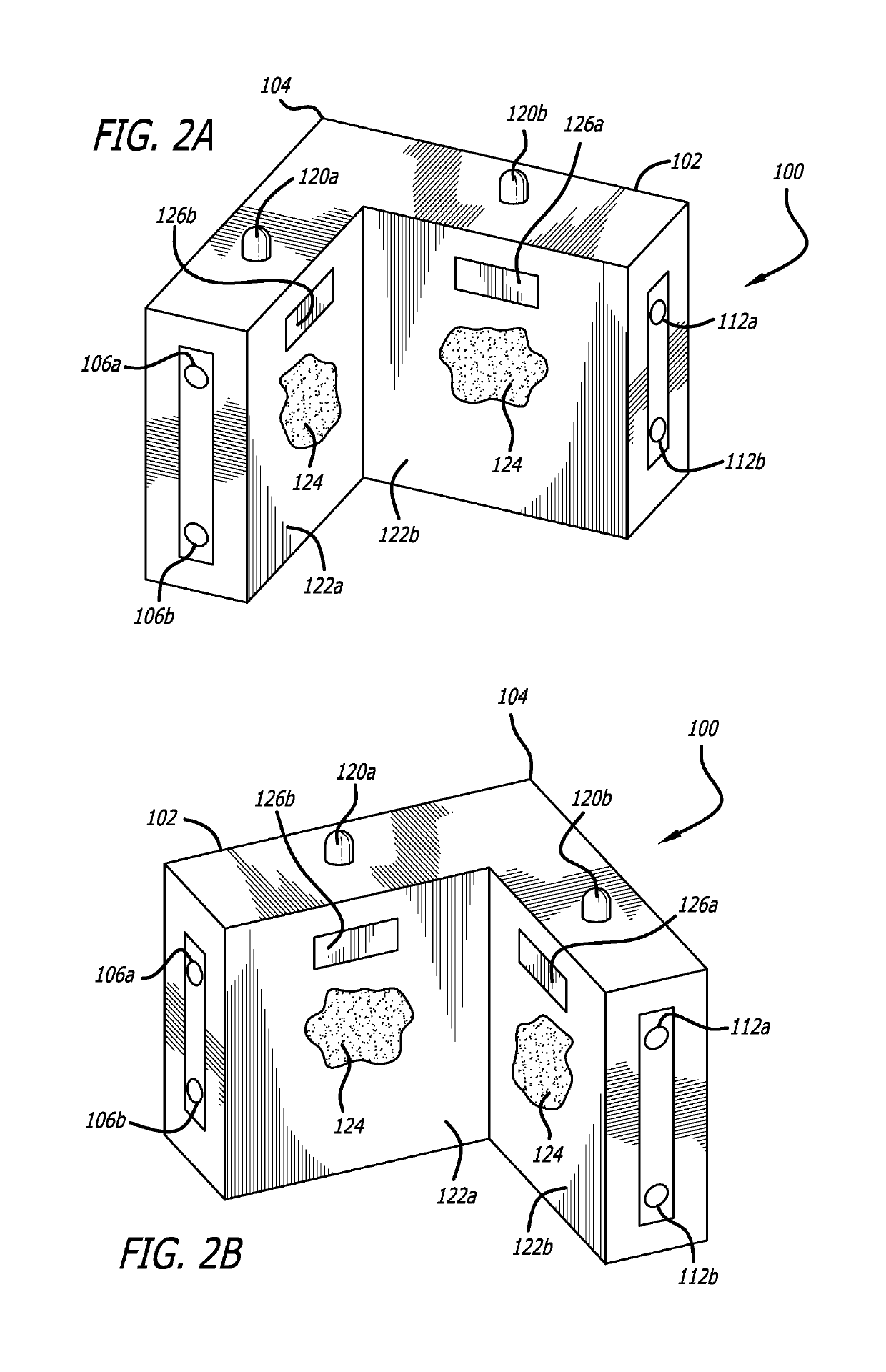
Security cover system for cargo container latch
InactiveUS6846024B1Improve the security systemSimple and economical to manufactureVehicle locksWing fastenersHydraulic pumpCovering system
A security system for a shipping container includes a cover and seal pin, and a special removal tool for removing the pin from the cover. The cover includes a vertical channel with top and bottom plates mounted therein to form a rearwardly opening box. A pair of vertically aligned apertures in the top and bottom plates are aligned with apertures in ears of a hasp on the shipping container, and receive the seal pin to secure the cover to the container. A seal pin includes an elongated shaft with annular grooves in the upper and lower ends. A pair of end caps each includes an annular groove on their interior surfaces that correspond with the shaft grooves to retain a locking ring within the pair of aligned grooves, when the caps are snapped on the ends of the shaft. The locking rings prevent removal of the caps, once snapped into place on the shaft. A removal tool includes a hydraulic pump with a punch secured to a piston of the pump. A punch housing has a gripping structure on the lower end that will grip a seal pin end cap, while the punch is driven through the end cap to push the shaft free of the end cap and release the seal pin.
Owner:SECURUS ENTERPRISES
Apparatus and method using optical speckle
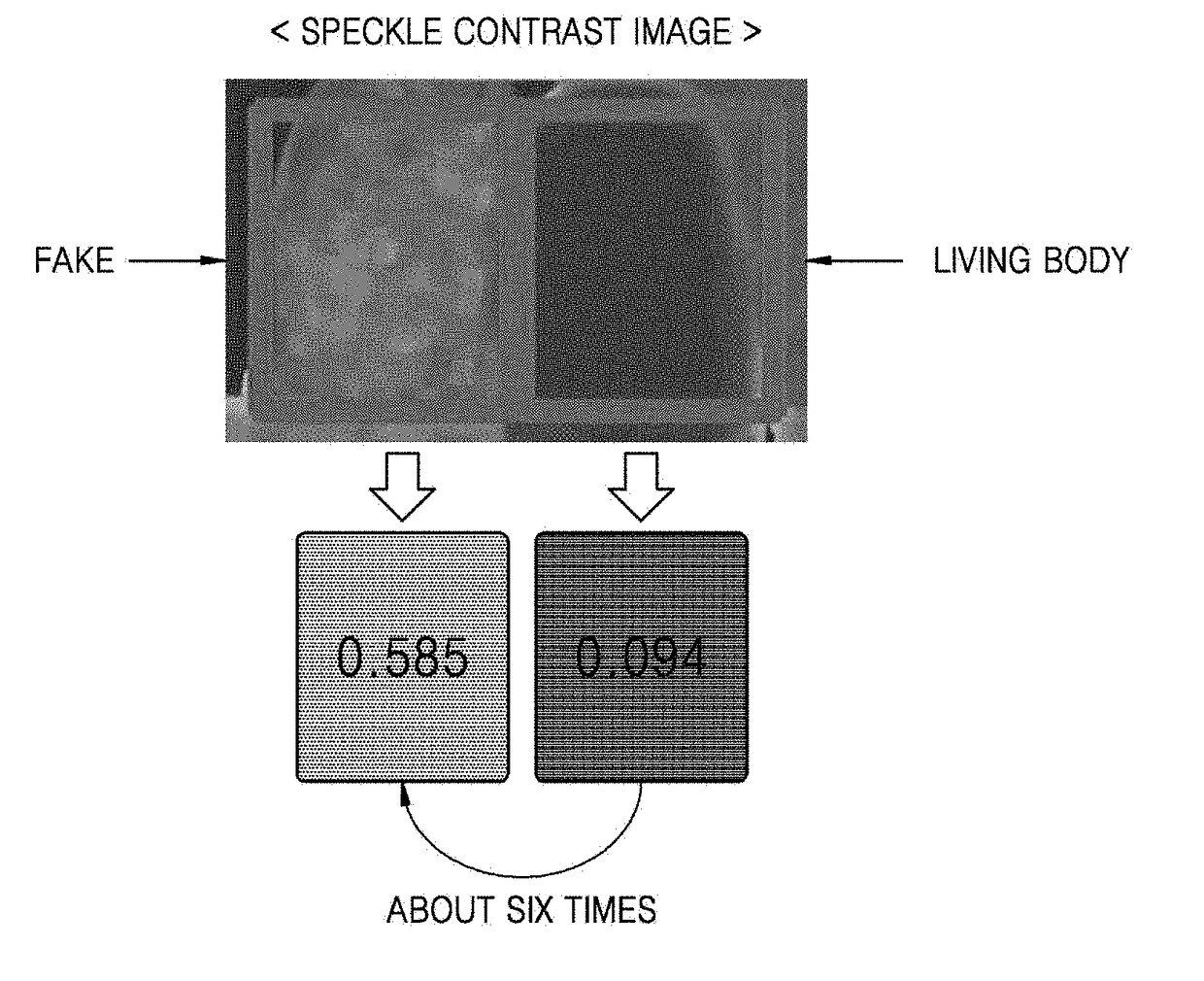
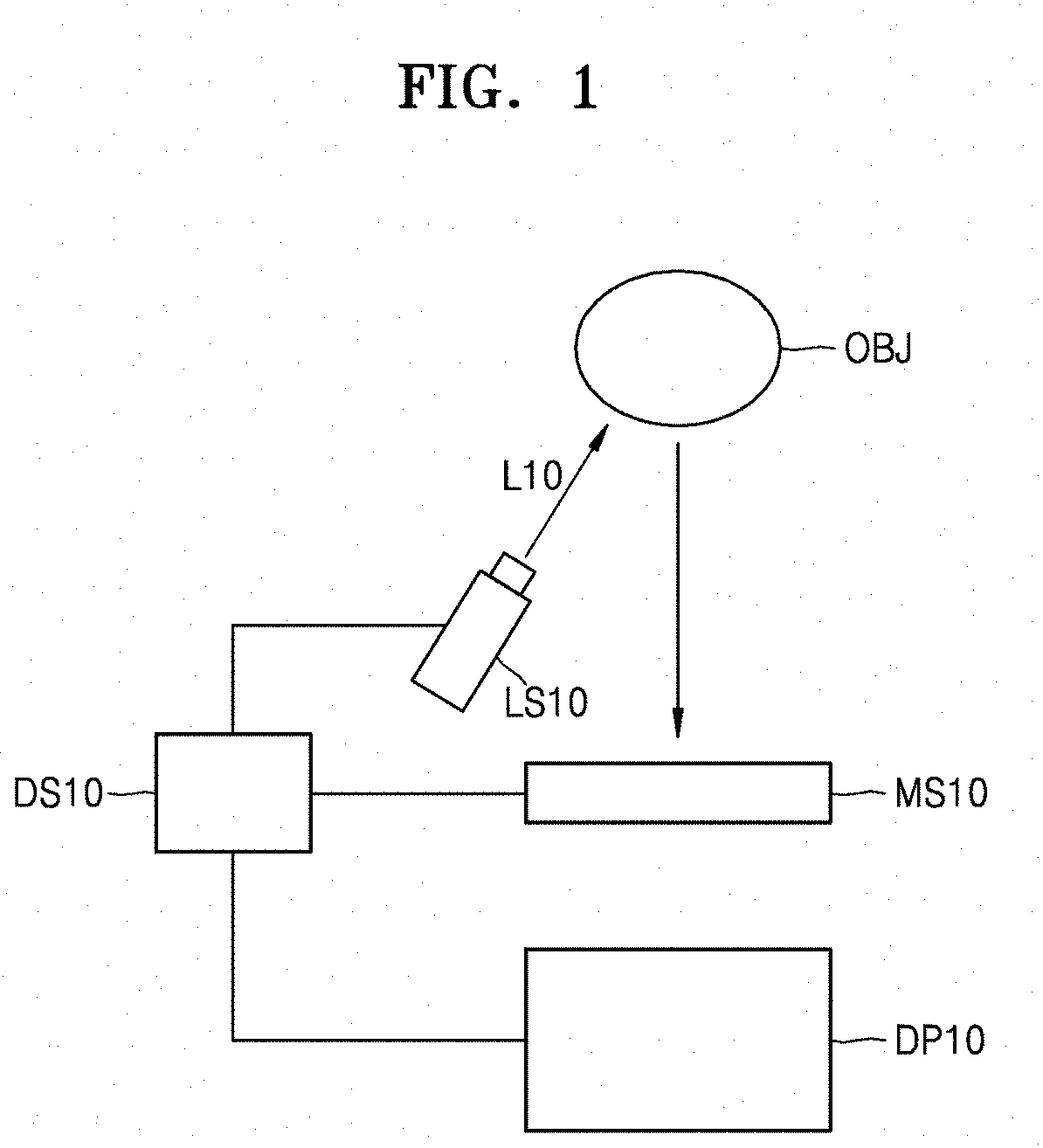
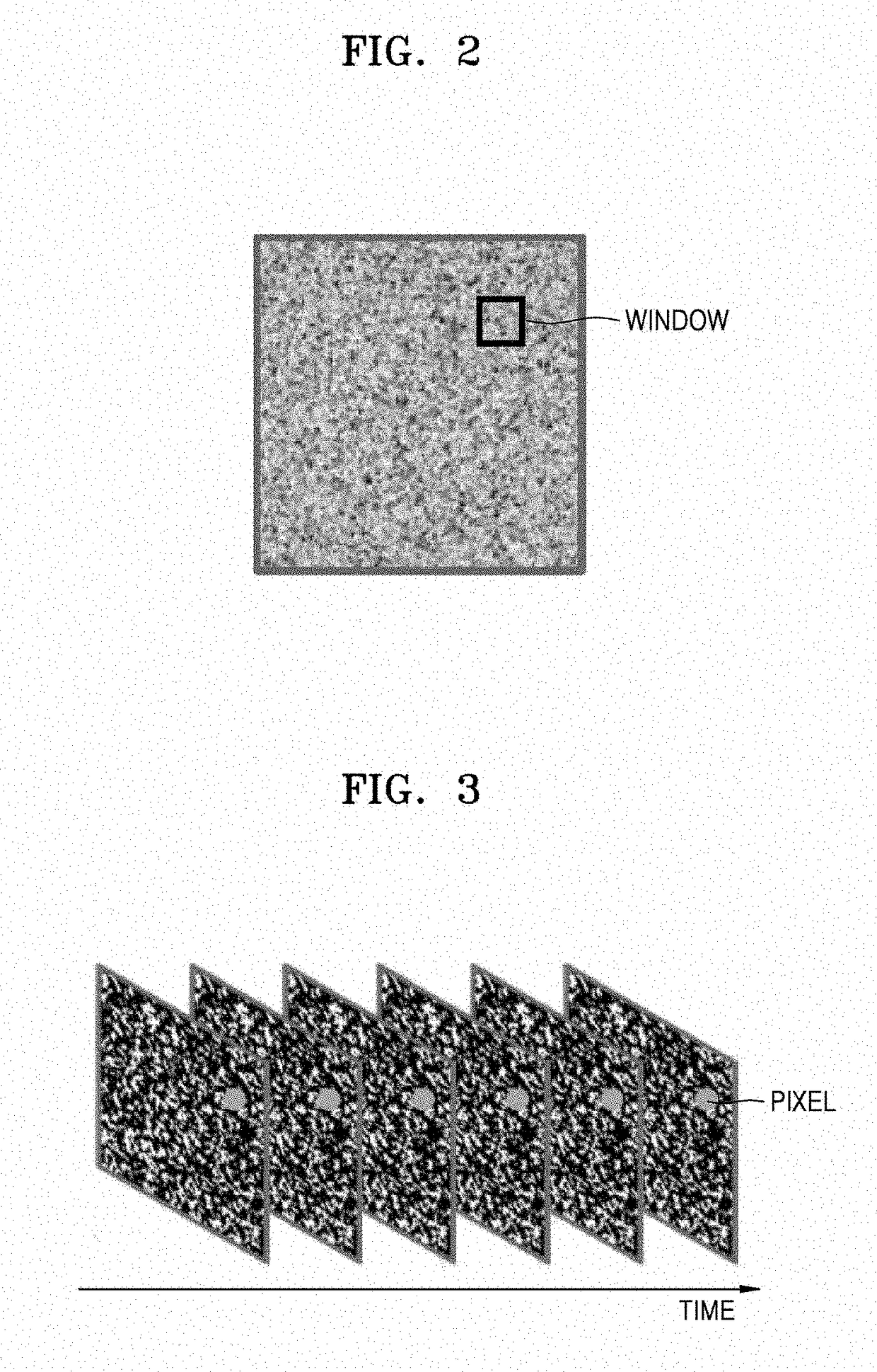
ActiveUS20180060639A1Improve reliabilityImprove the security systemLaser detailsMaterial analysis by optical meansSpeckle patternLiving body
Provided are apparatuses and methods using an optical speckle. An apparatus may include a light source configured to emit coherent light to an object and an imaging device configured to photograph a speckle pattern generated on the object by the coherent light. The apparatus may also include a processor having a function of determining whether the object is a living body or a non-living body by measuring a contrast of the speckle pattern. The processor may be configured to determine whether the object is a living body or not by comparing the contrast of the speckle pattern with a threshold contrast or a reference contrast previously registered by a user. The apparatus may be used by being applied to a fingerprint recognition system.
Owner:SAMSUNG ELECTRONICS CO LTD +1
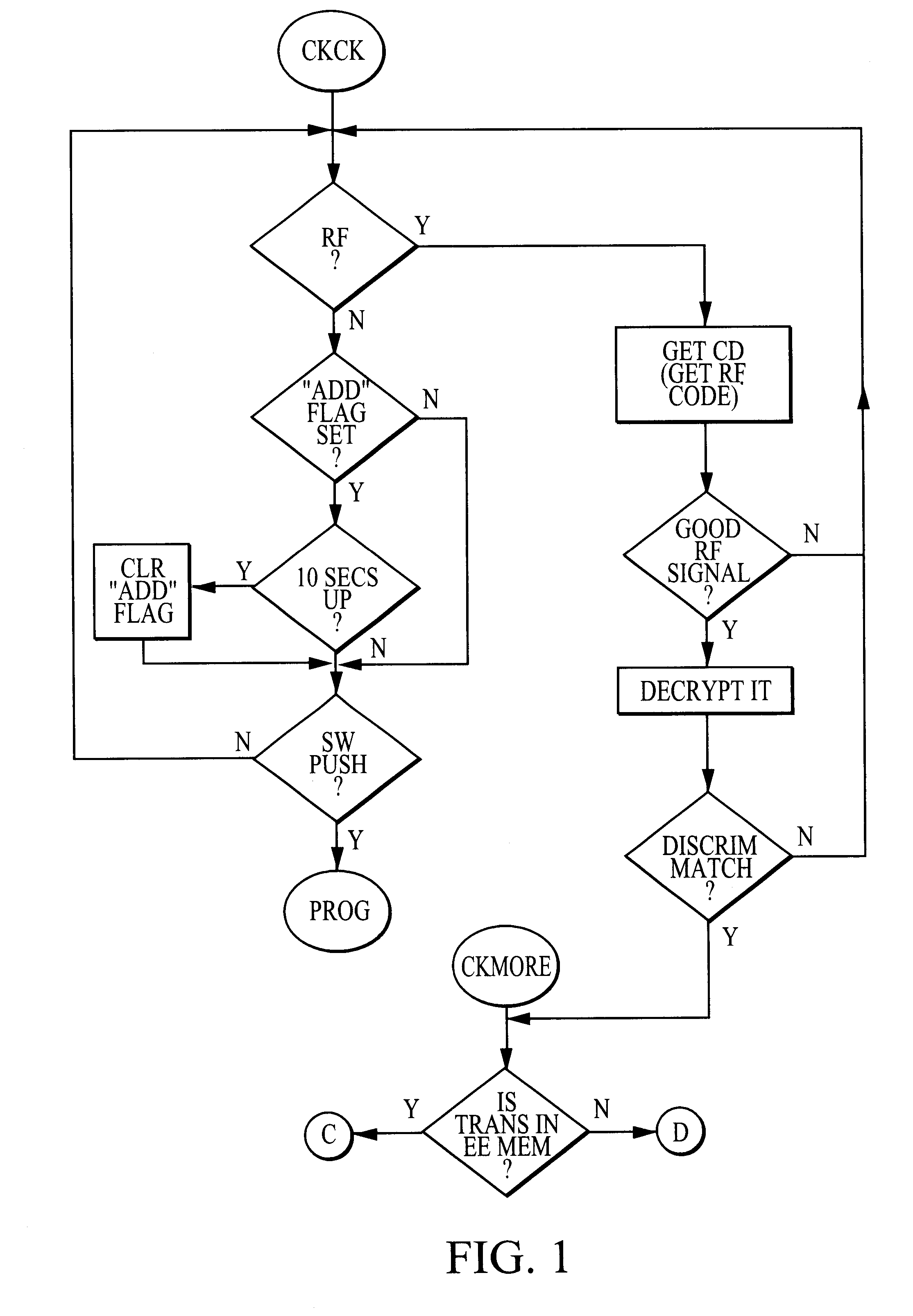
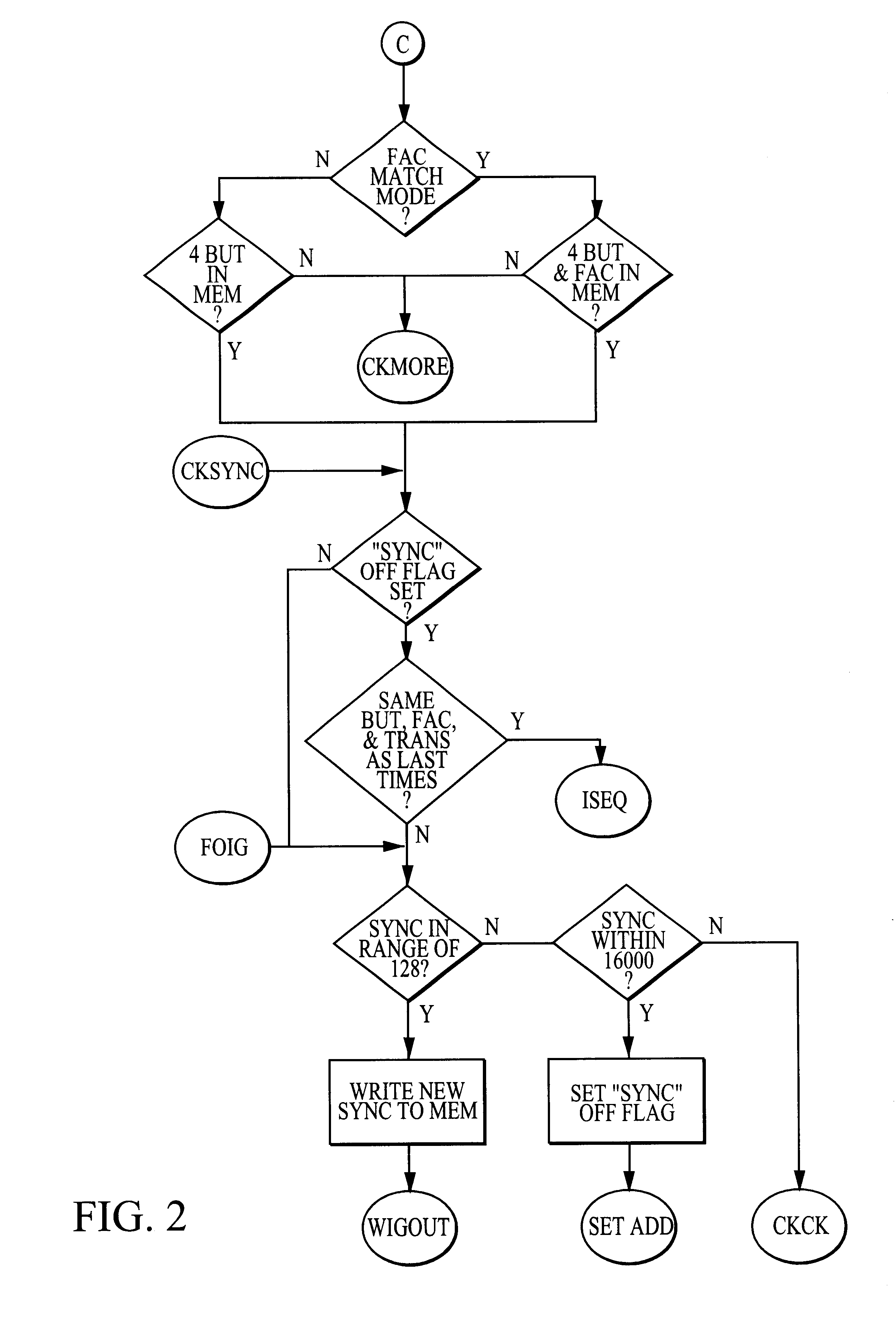
Method and apparatus for radio frequency security system with automatic learning
InactiveUS6856237B1Improve the security systemImprove securityElectric signal transmission systemsMultiple keys/algorithms usageElectronic securityRadio frequency
A security system for control access of multiple users to a selected area combines rotating electronic security code or equivalent technology with an automatic self-learning receiver. The first transmitter is “learned” by the receiver manually, but subsequent transmitters are learned without the need for actuating the conventional “manual learn” mode of the receiver. Instead, by simply sending the transmit signal twice within a fixed time period, users of the subsequent transmitters use “self-learning” circuitry (interposed between conventional transmitter and receiver technology) in a way that is relatively transparent to the user. Other aspects of conventional systems are provided, such as separate control via computer or otherwise of an authorized list of uniquely-identified transmitters. In alternative embodiments, even the first transmitter / controller can be programmed into the receiver (such as at the time of manufacturing or installing the system).
Owner:DOORKING
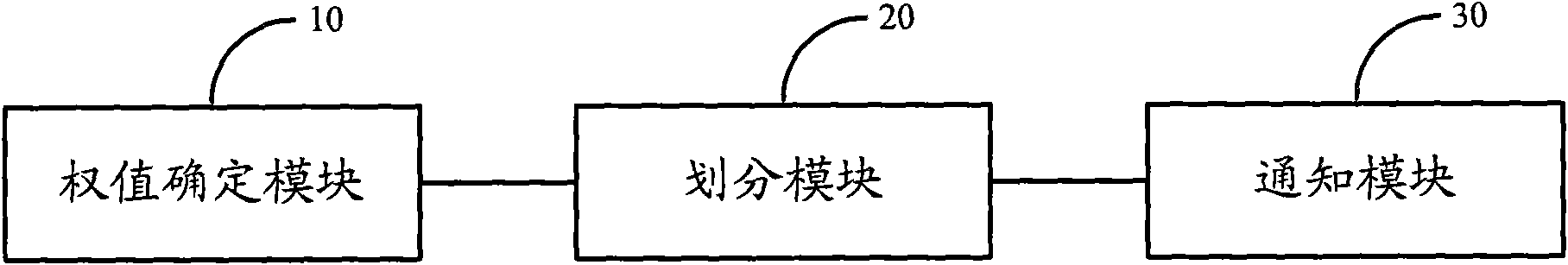
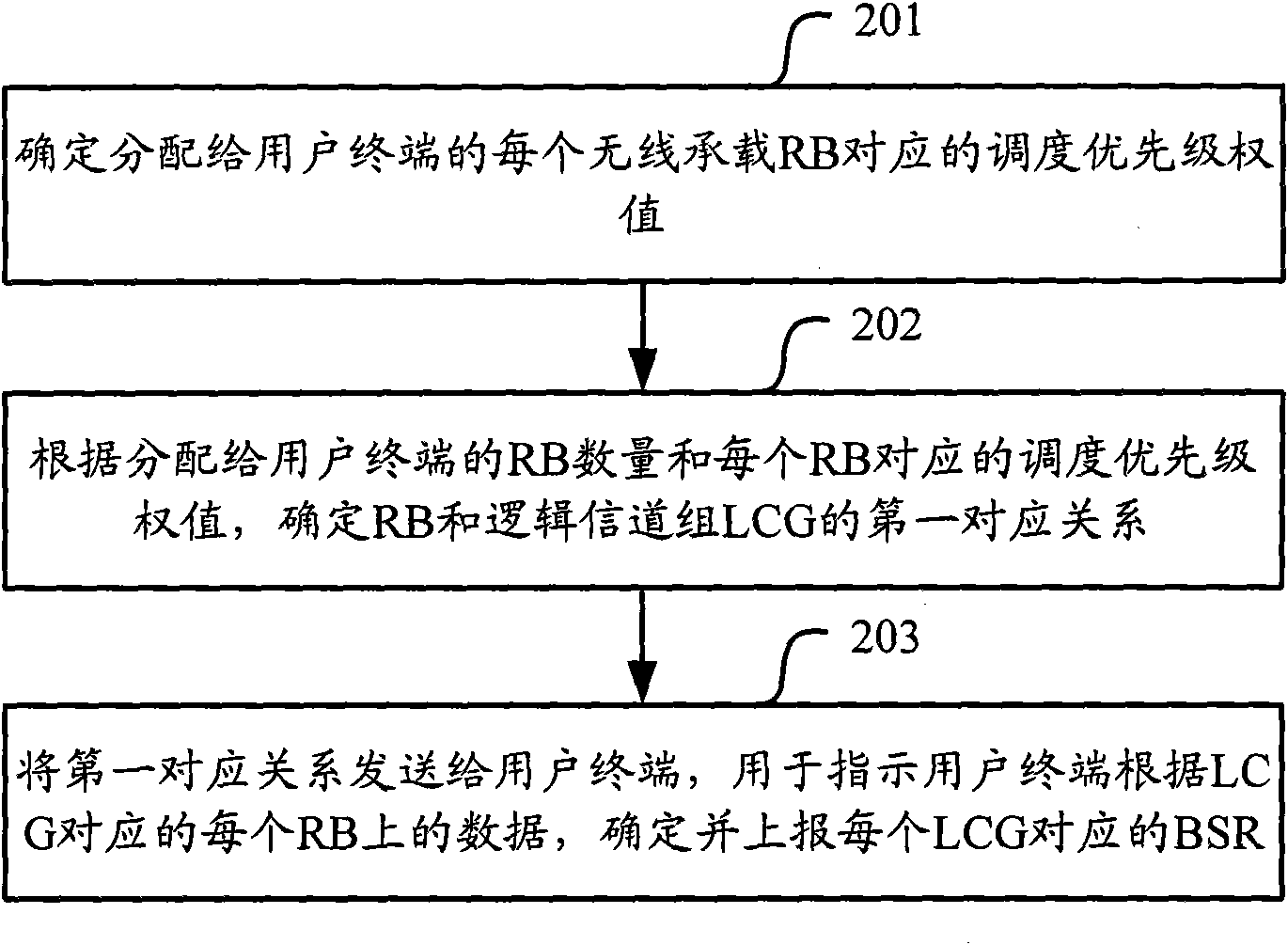
Method and device for reporting BSR (Buffer Status Report)
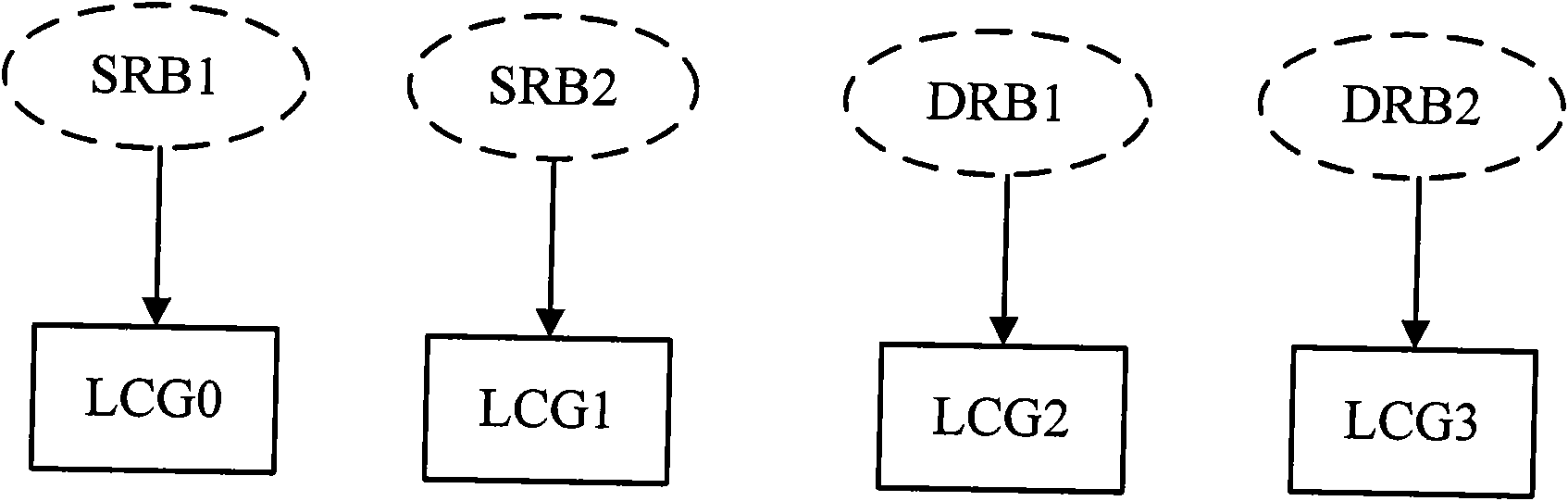
ActiveCN102065552AHigh precisionImprove the security systemWireless communicationFirst relationshipQuality of service
The embodiment of the invention relates to radio communication technology, particularly a method and device for reporting BSR (Buffer Status Report). The method provided by the invention comprises the following steps: determining a scheduling priority weight allocated to a user terminal corresponding to each RB (Radio Bearer); determining a first relationship between the RBs and an LCG (Logical Channel Group) according to the quantity of the RBs allocated to the user terminal and the scheduling priority weight corresponding to each RB; and transmitting the first relationship to the user terminal to indicate the data of the user terminal on each RB corresponding to the LCG, and determining and reporting the BSR corresponding to each LCG. The method provided by the invention can help the base station to enhance the adjustment precision of scheduling priority of the user terminal, and improve the support system of QoS (Quality of Service).
Owner:DATANG MOBILE COMM EQUIP CO LTD
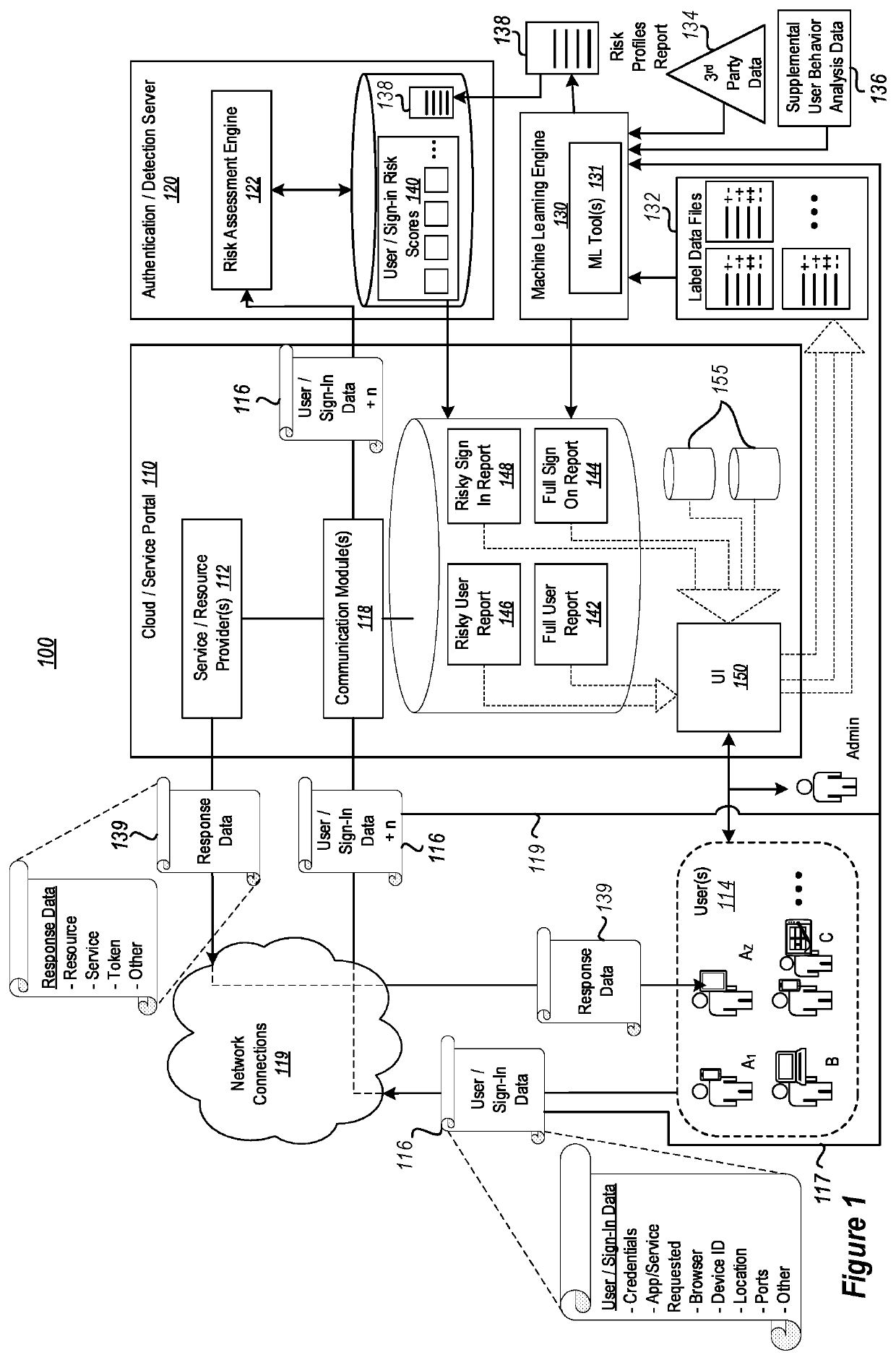
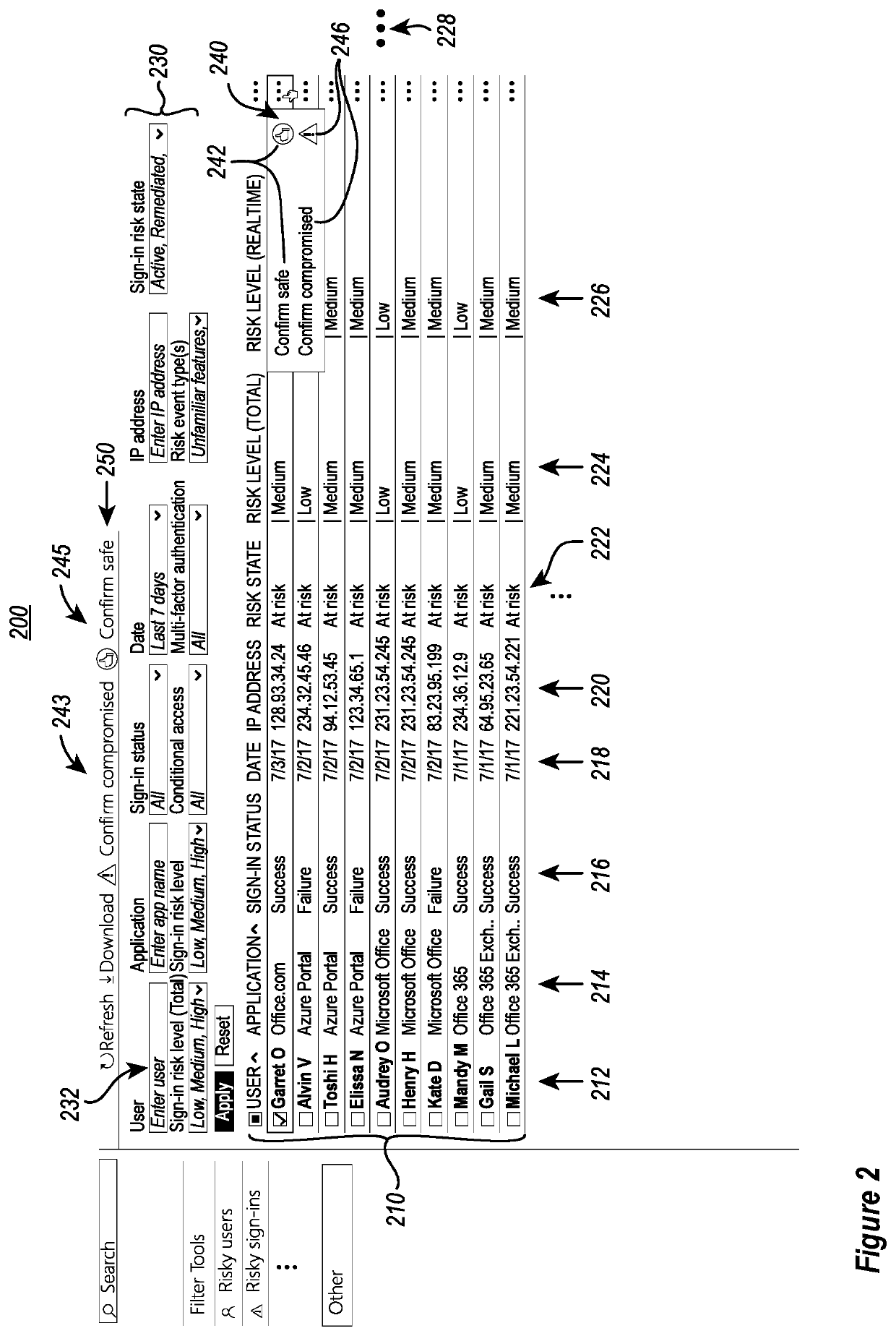
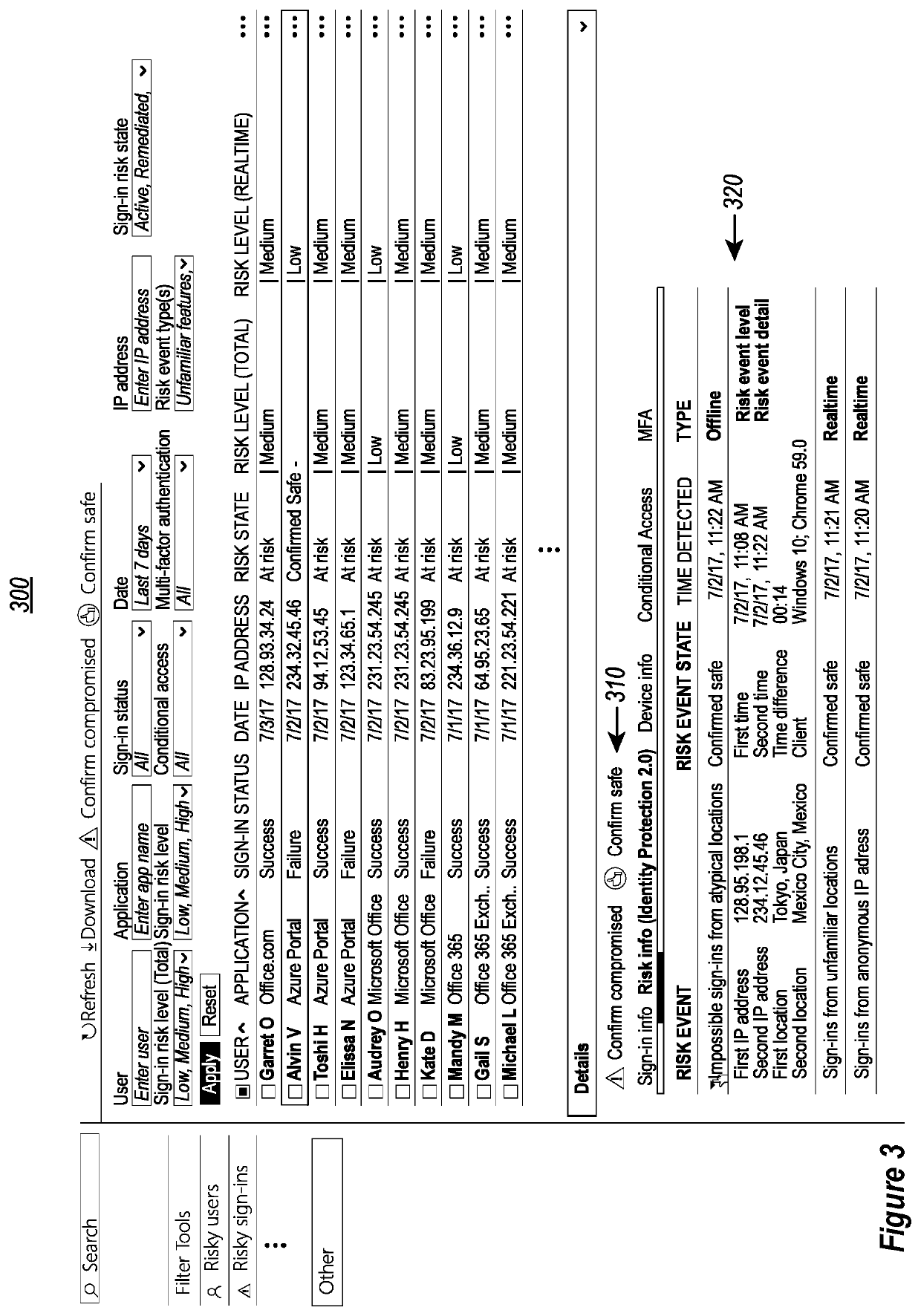
Crowdsourced, self-learning security system through smart feedback loops
ActiveUS20200089887A1Increase heightIncrease training dataEnsemble learningKernel methodsFeedback loopUser input
Systems are provided for utilizing crowdsourcing and machine learning to improve computer system security processes associated with user risk profiles and sign-in profiles. Risk profiles of known users and logged sign-ins are confirmed by user input as either safe or compromised. This input is used as crowdsourced feedback to generate label data for training / refining machine learning algorithms used to generate corresponding risky profile reports. The risky profile reports are used to provide updated assessments and initial assessments of known users and logged sign-ins, as well as newly discovered users and new sign-in attempts, respectively. These assessments are further confirmed or modified to further update the machine learning and risky profile reports.
Owner:MICROSOFT TECH LICENSING LLC
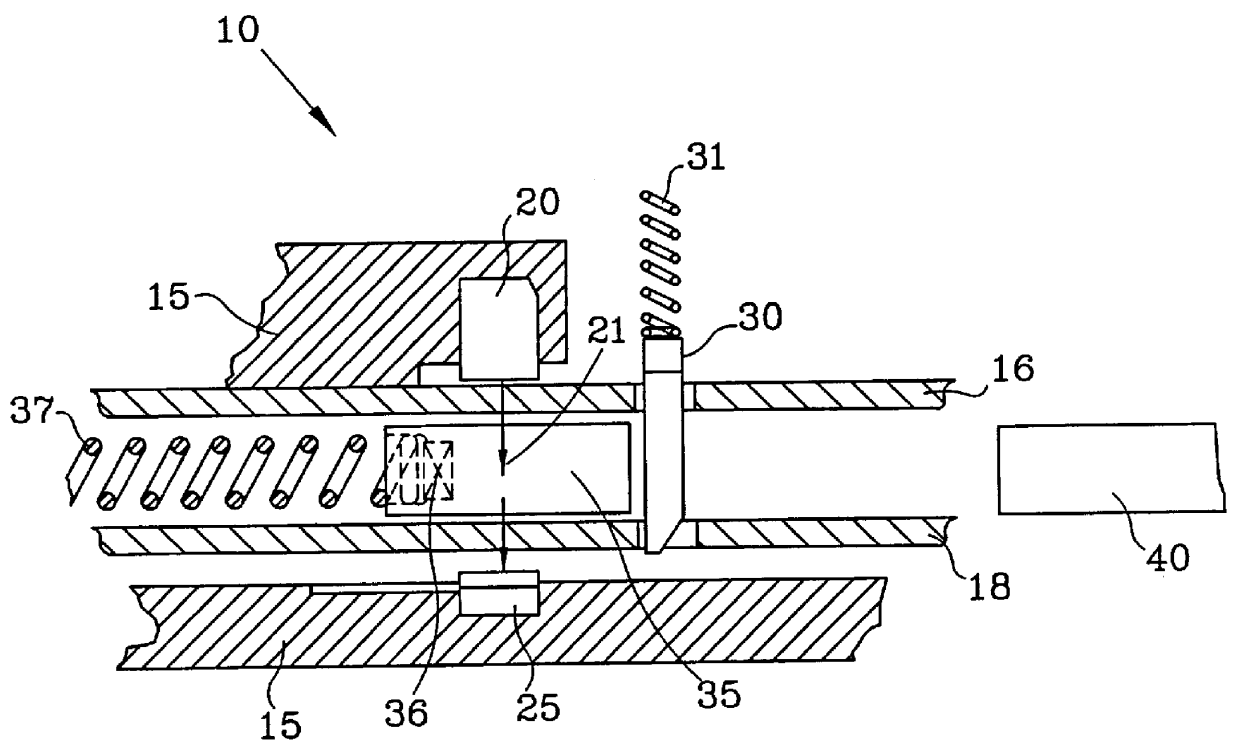
Integrated tire rim airbag system
InactiveUS20050109439A1Improve safety systemImprove the security systemTyre measurementsTyre-inflating valvesFiberAirbag
An airbag system secured to the tire rim inside a tire. The airbag is normally in a collapsed state close to the rim. The airbag is inflated with pressurized gas in the event of a tire failure. The inflated bag generally conforms to the inner walls of the tire to support the weight of the vehicle and enable the vehicle to be safely stopped. The bag has wear surfaces composed of durable material such as nylon or Kevlar fibers.
Owner:DROEGEMUELLER DAVID S
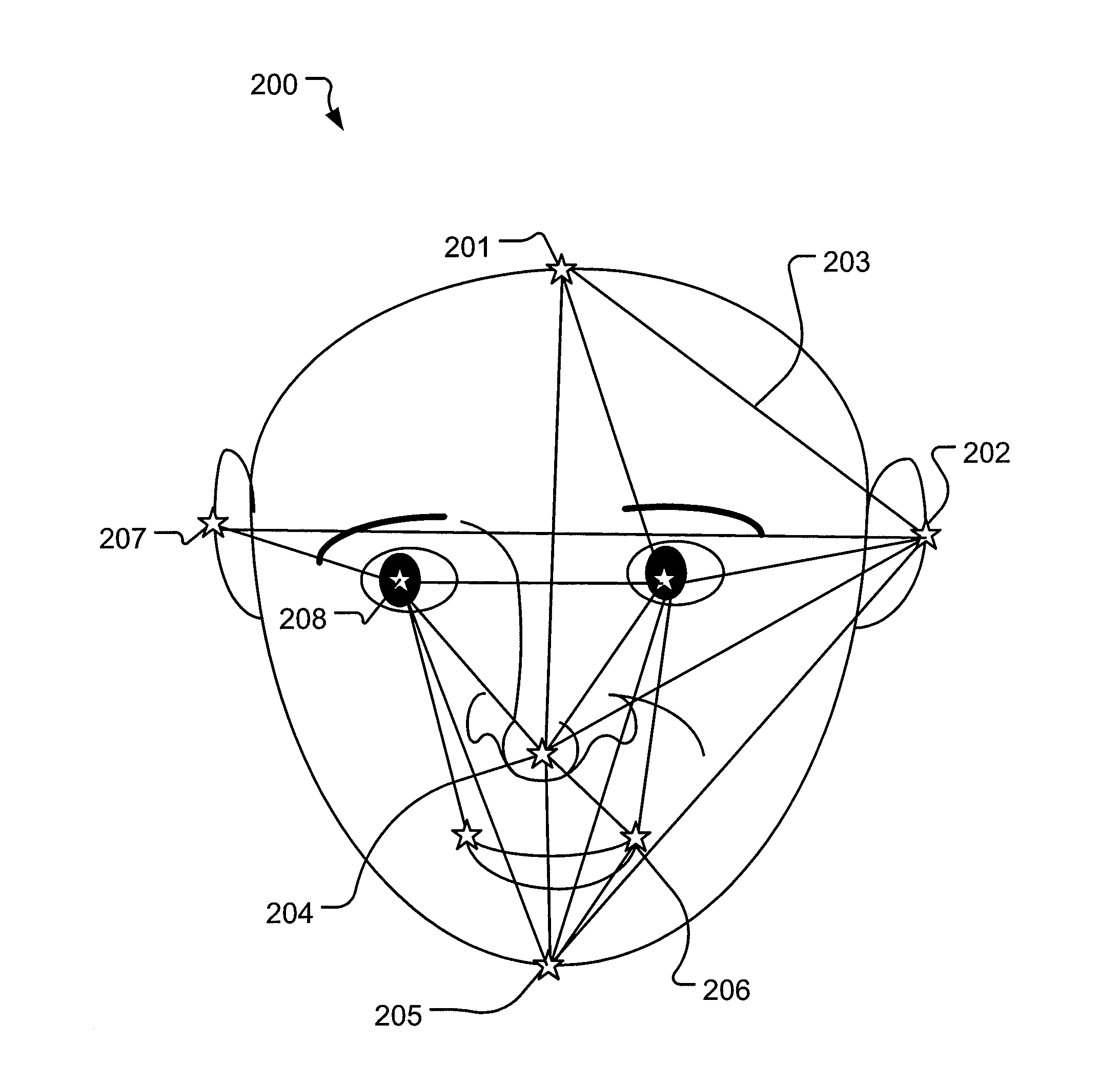
Security by z-face detection
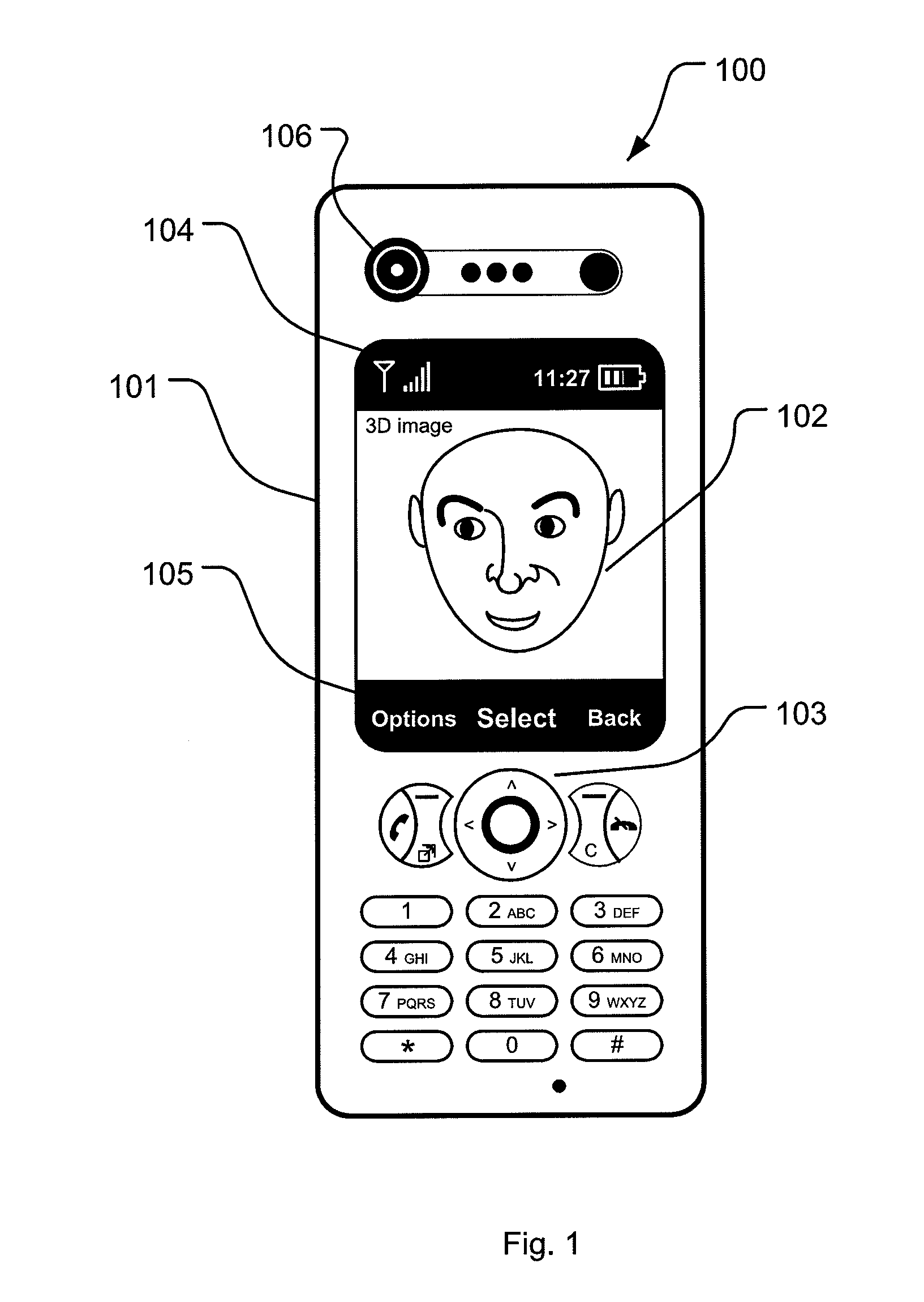
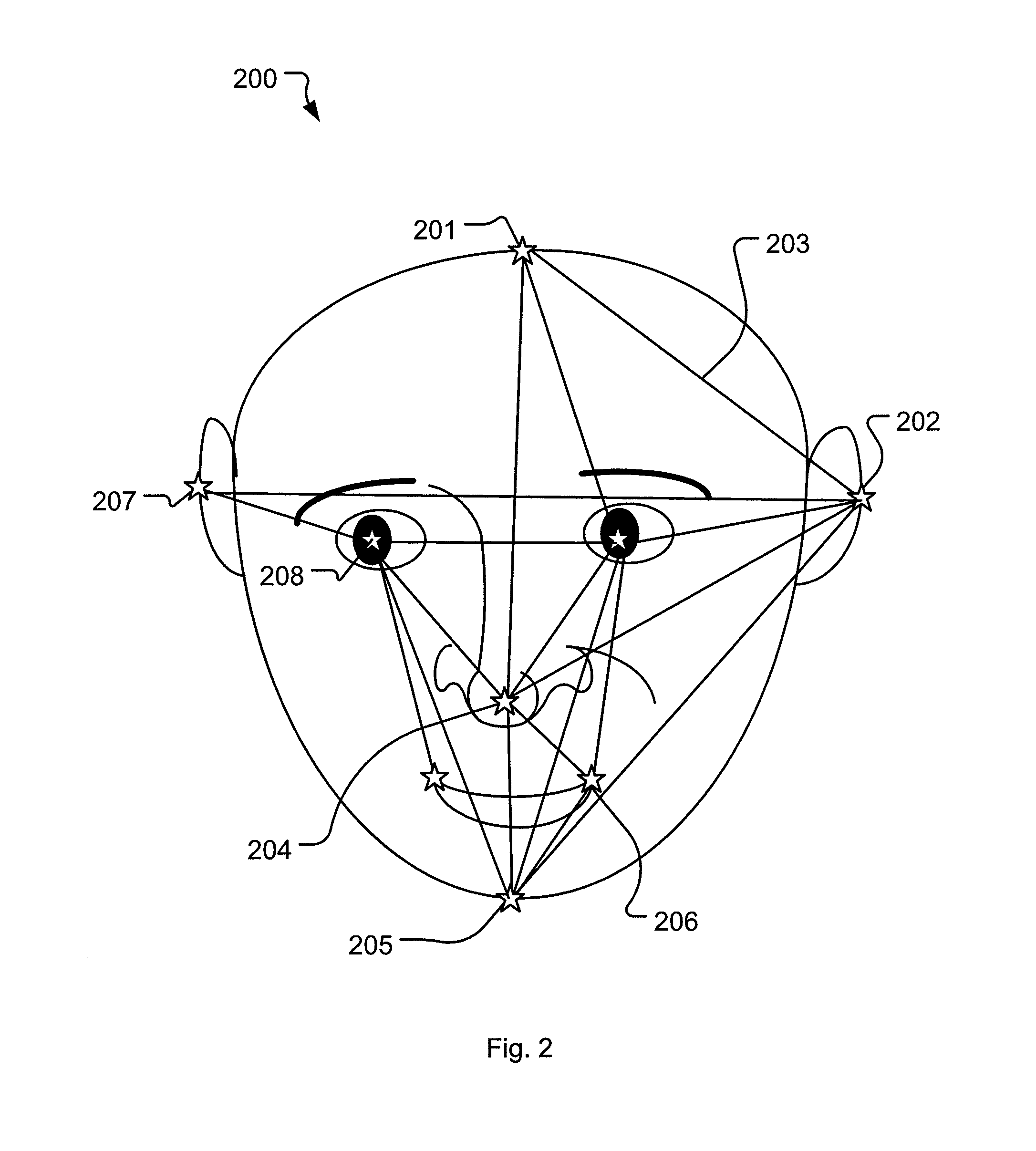
InactiveUS20130322708A1Improve the security systemMitigate, alleviate, or eliminate one orCharacter and pattern recognitionFace detection3d image
A method for identifying a person using a mobile communication device, having a camera unit adapted for recording three-dimensional (3D) images, by recording a 3D image of the person's face using the camera unit, performing face recognition on the 2D image data in the recorded 3D image to determine at least two facial points on the 3D image the of person's face, determining a first distance between the at least two facial points in the 2D image data, determining a second distance between the at least two facial points using the depth data of the recorded 3D image, determining a third distance between the at least two facial points using the first distance and the second distance, and identifying the person by comparing the determined third distance to stored distances in a database, wherein each of the stored distances are associated with a person.
Owner:SONY MOBILE COMM AB +1
Safety restraint buckle three-state tongue sensor
InactiveUS6082481AImprove the security systemSnap fastenersPedestrian/occupant safety arrangementHall elementEngineering
A safety restraint buckle apparatus and method wherein a Hall element is mounted with respect to a housing and a magnet is mounted with respect to the housing, at a distance from the Hall element. A latch is movably mounted between a latched position and an unlatched position. A tongue is movable between an engaged position within the housing and a disengaged position. In the engaged position of the tongue, the latch is in the latched position. An ejector with a pole piece or a pole member is movably mounted between a loaded position and an unloaded position. When the ejector is in the unloaded position, the Hall element operates in a high magnetic state. When the ejector is in the loaded position and the tongue is in the engaged position, the Hall element operates in a low magnetic state because the magnetic flux density is shunted through the tongue. When the latch is in the latched position and the tongue is in the disengaged position with the ejector thus held in an intermediate position, the Hall element operates in a mid magnetic state, between the low magnetic state and the high magnetic state, to indicate a false positive latch condition of the safety restraint buckle apparatus.
Owner:HONEYWELL INC
Universal cellular circuit board
InactiveUS20060199614A1Improve the security systemNeed for manySpectrum investigationSubstation equipmentService provisionDigital security
A system and apparatus that allows cell phone users to control the roaming features of their service from one telecommunication network (i.e., cellular service provider) to another at the device level, independently of a particular primary network. More specifically, it intends to perform primary functions using the principles of (SoC) design, allowing an array of third party smart cards to share the motherboard of the universal cellular circuit, thus, allowing for ease of switching service providers by simply pushing a button on the apparatus. In addition, this device is equipped with a digital security diagnostic port (DSDP), allowing the scanning of the physical layer of the cellular circuit for unwanted / unexpected chips and other digital security breaches. For the cause of unprecedented efforts to accelerate the design, production, implementation, and distribution of new technologies (SoC design, ESL design, Robotics . . . ), this invention addresses a future threat to human-computer interactions (HCI) and public safety.
Owner:INFOSENSE TECH & RES
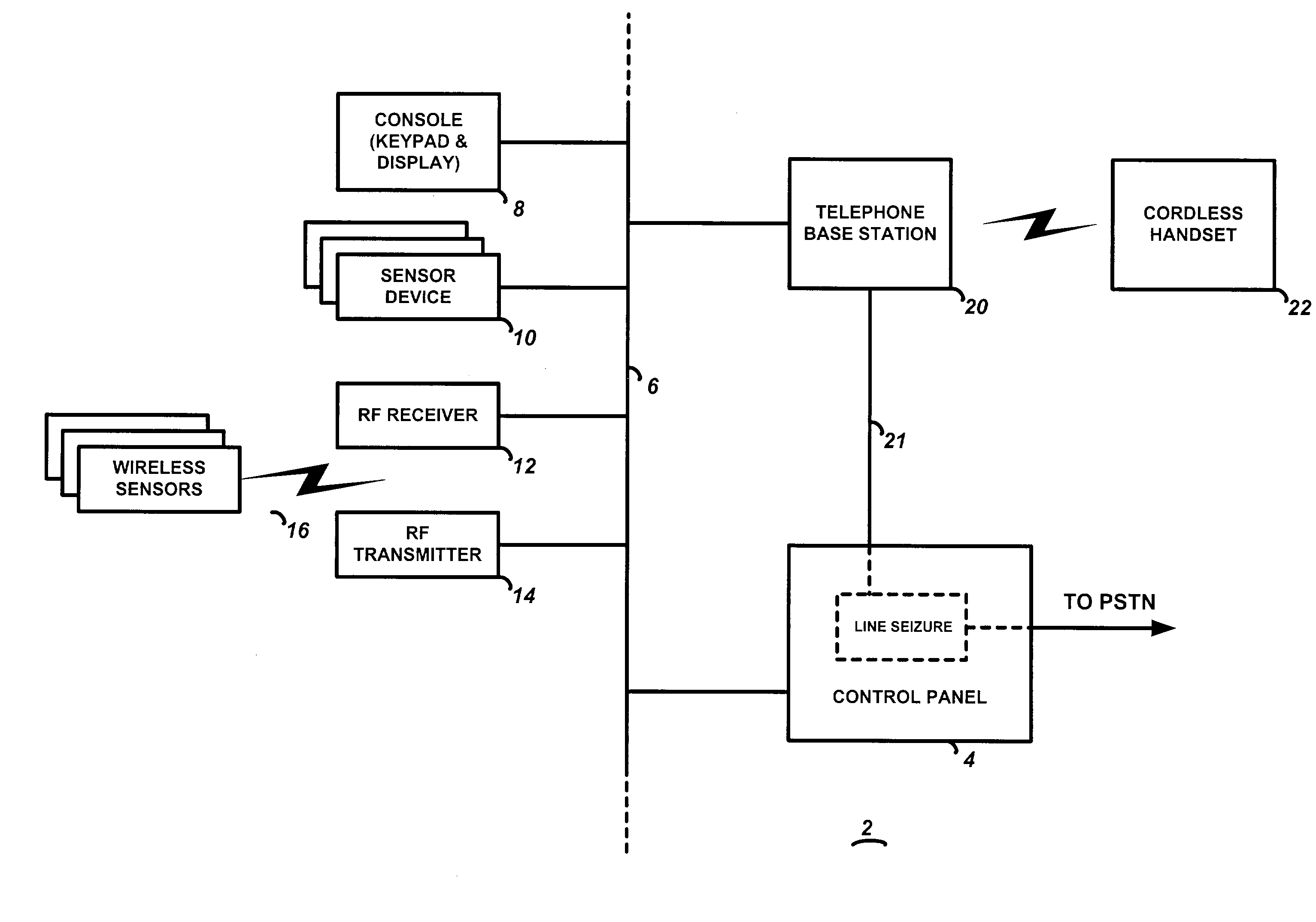
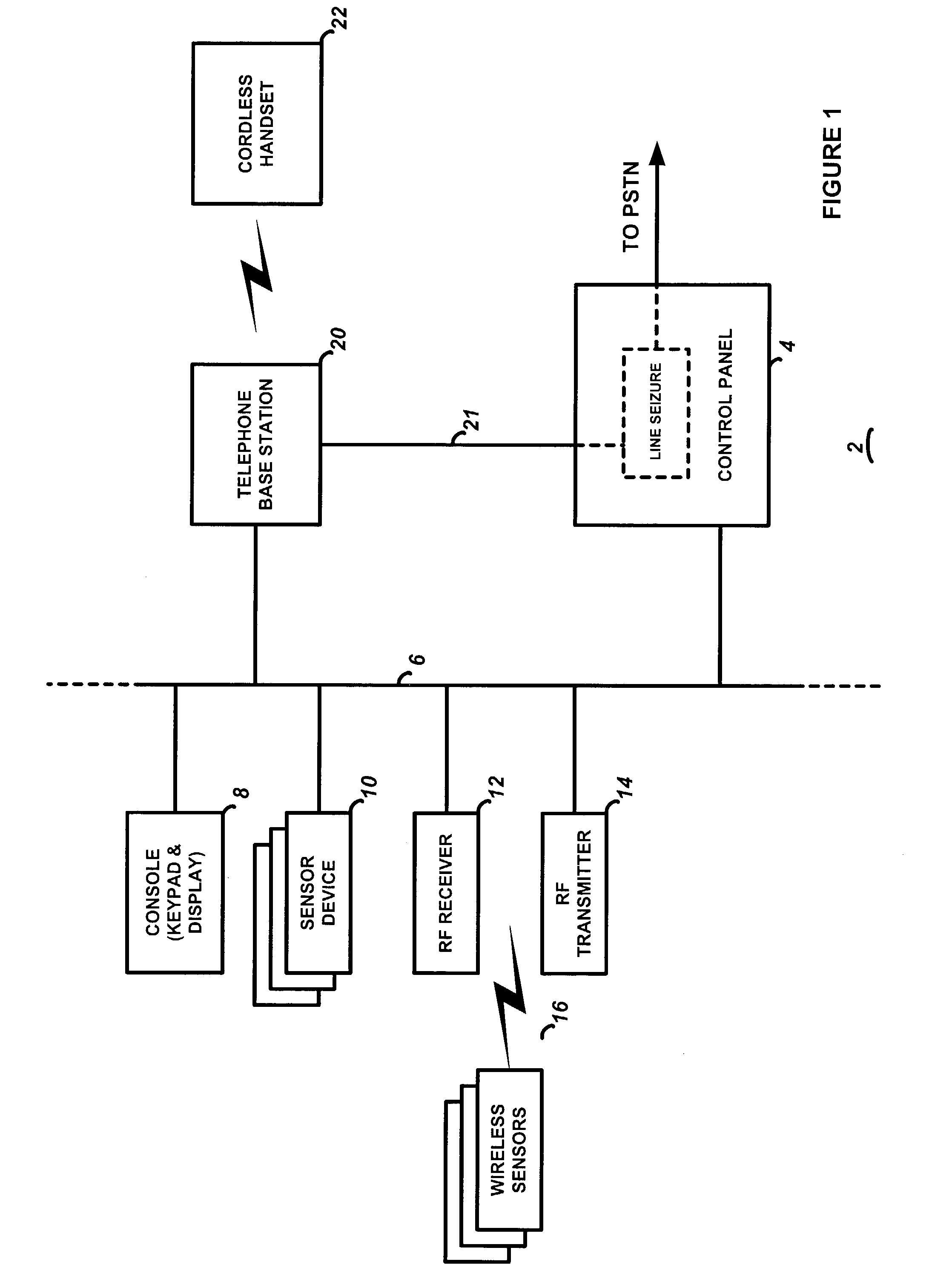
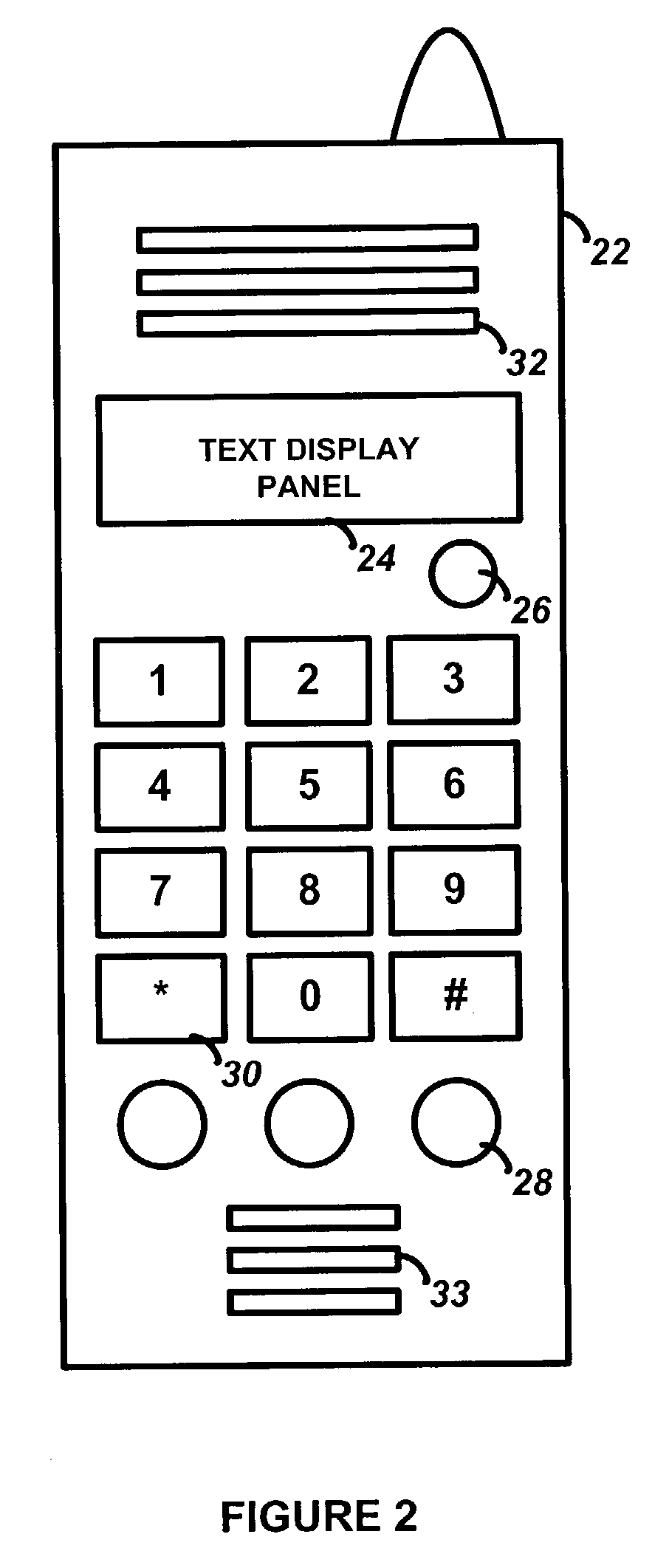
Security system with telephone controller
InactiveUS7096001B2Improve securityEasy to optimizeElectric signal transmission systemsDigital data processing detailsHandoff controlTelephone network
A combination telephone set (such as a cordless phone) and security system control device that has a first interface means for interfacing the control device with a security system bus, a second interface means for interfacing the control device with a telephone network such as the PSTN, and a user interface means with an input means for providing user control information to the control device, the input means including means for a user to switch the control device between a telephone mode and a security system mode, an output means for providing status data to a user regarding operation of the control device, and adapted to enable a user to communicate over the telephone network when the security device is in the telephone mode. Processing means controls operation of the control device, and is adapted to switch between a telephone mode and a security system mode on receipt of a user command from the input means. When in the telephone mode, the processing means sends and receives telephony information between the user interface means and the second interface means; when in the security system mode, the processing means sends and receives security system information between the user interface means and the first interface means.
Owner:ADEMCO INC
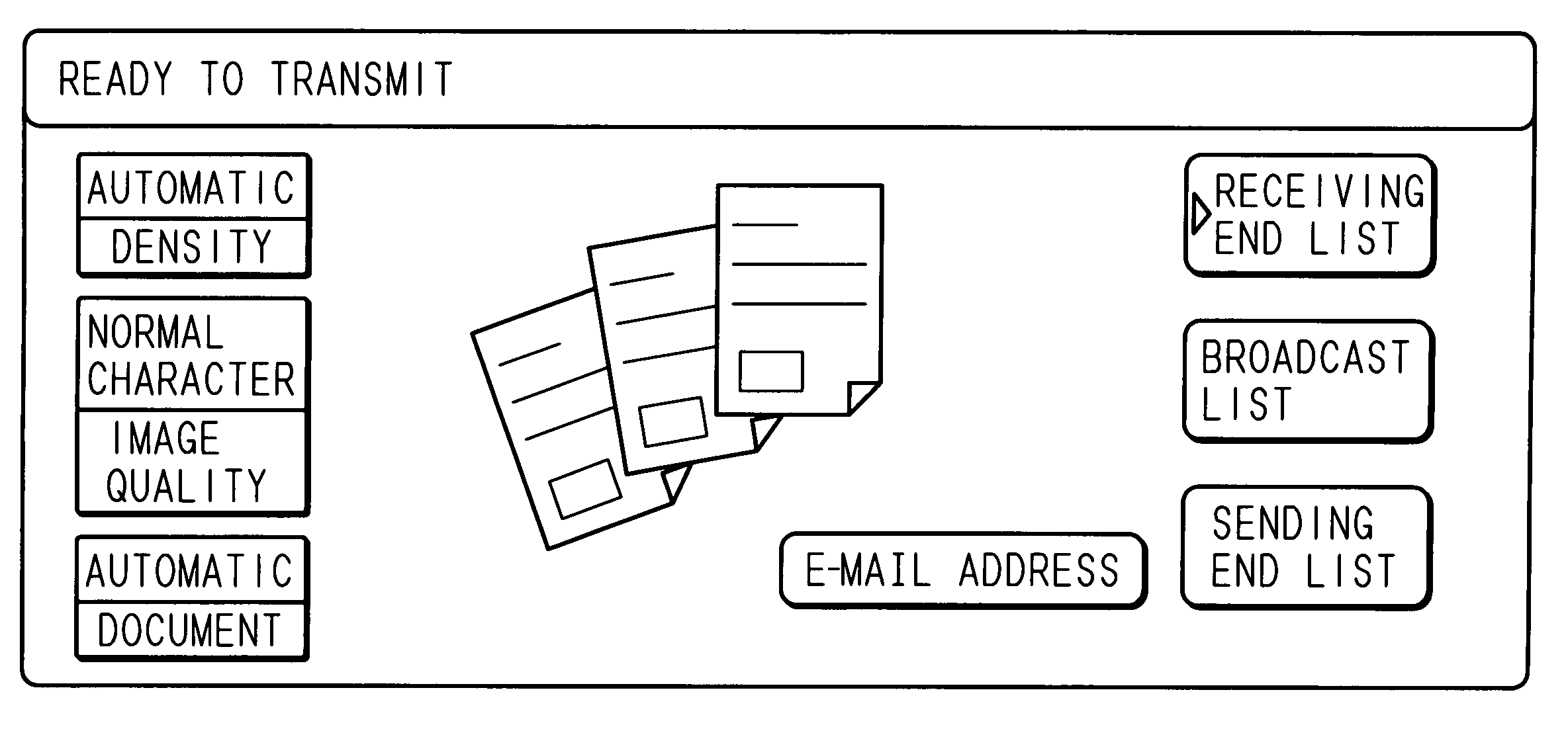
Data transmission device
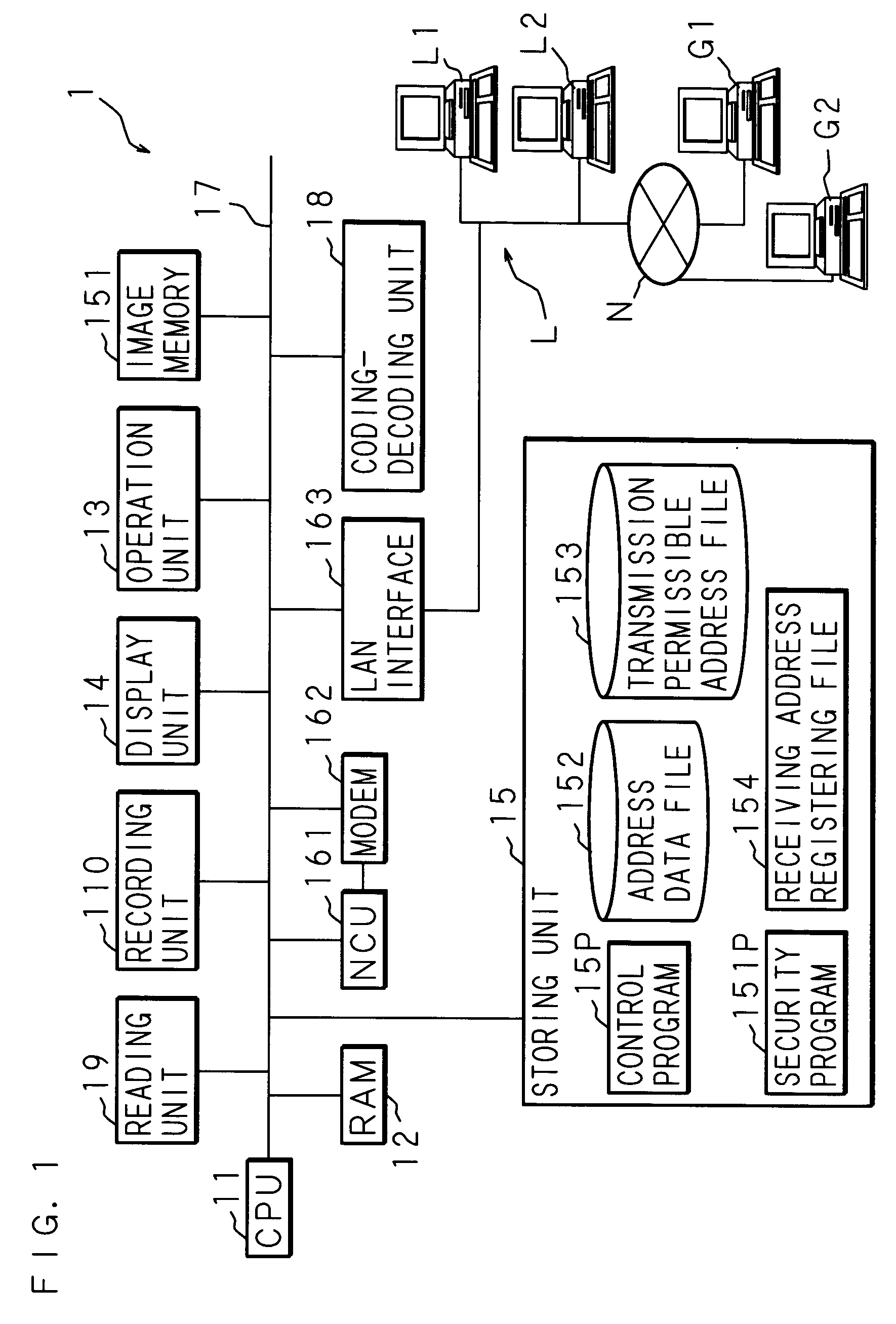
InactiveUS20060253536A1Improve the security systemAvoid spreadingMultiple digital computer combinationsPictoral communicationEmail addressThe Internet
Among unique addresses that are receiving ends of data, such as e-mail addresses, a partial address that is in common with a plurality of addresses is registered in a storing unit. For example, of an e-mail address containing a user name and a domain, the domain is used as the partial address. Thus, a data transmitting apparatus, such as an Internet facsimile apparatus, restricts data transmission for image data and the like only to addresses containing the partial address registered in the storing unit. In other words, data is transmitted only to addresses that have the same domain.
Owner:SHARP KK
Corner security detection device
ActiveUS10242561B1Easy to optimizeReduces false alarm triggerRadiation pyrometryElectric transmission signalling systemsAlert systemComputer security
A security detection device and system for reducing false triggers is provided. The security detection device is a corner mount devices that may be mounted on the outside corners of building and structures. The security detection device may further communicate via a communications data network with other security detection devices to a community server to create a shared community alarm system.
Owner:OUTSMART TECH INC
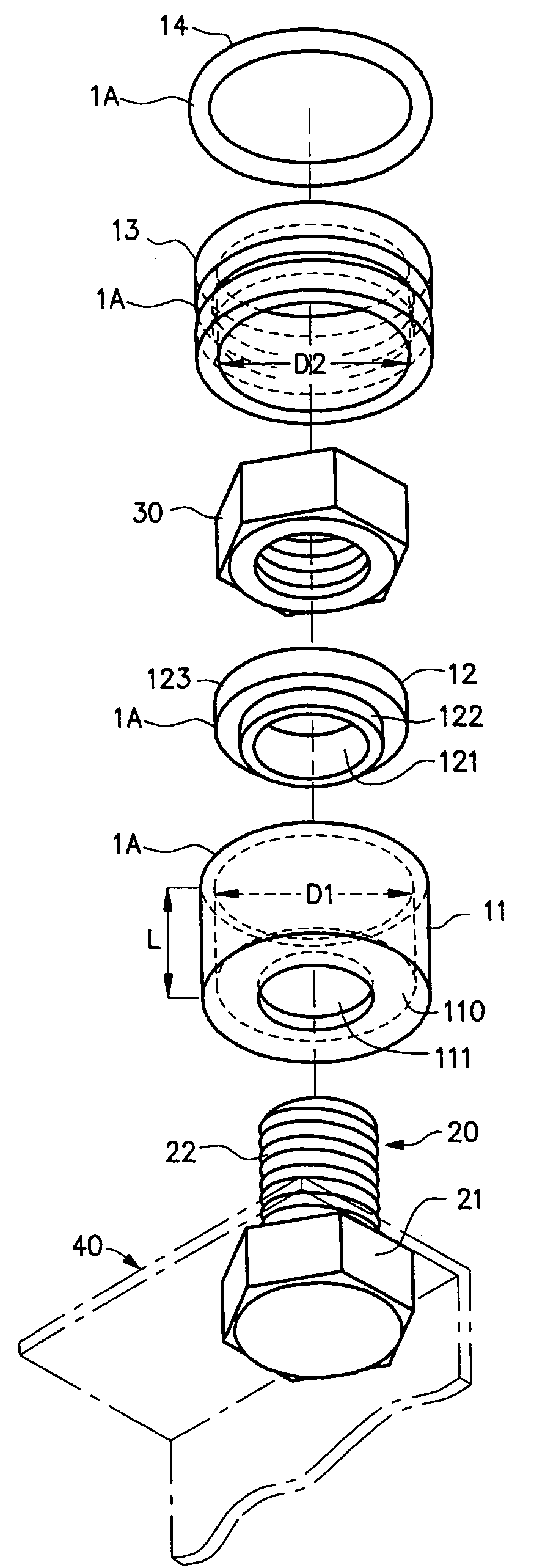
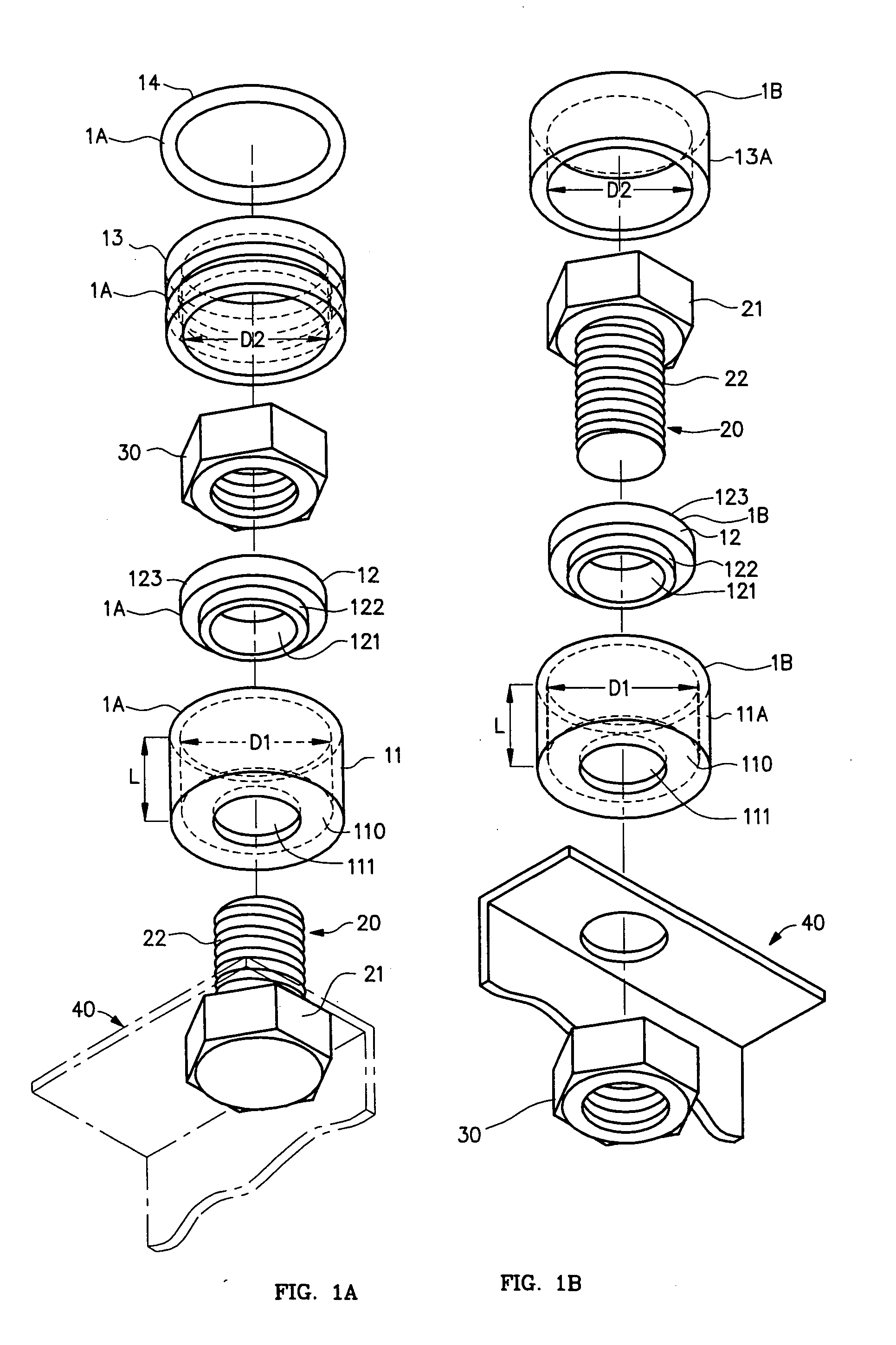
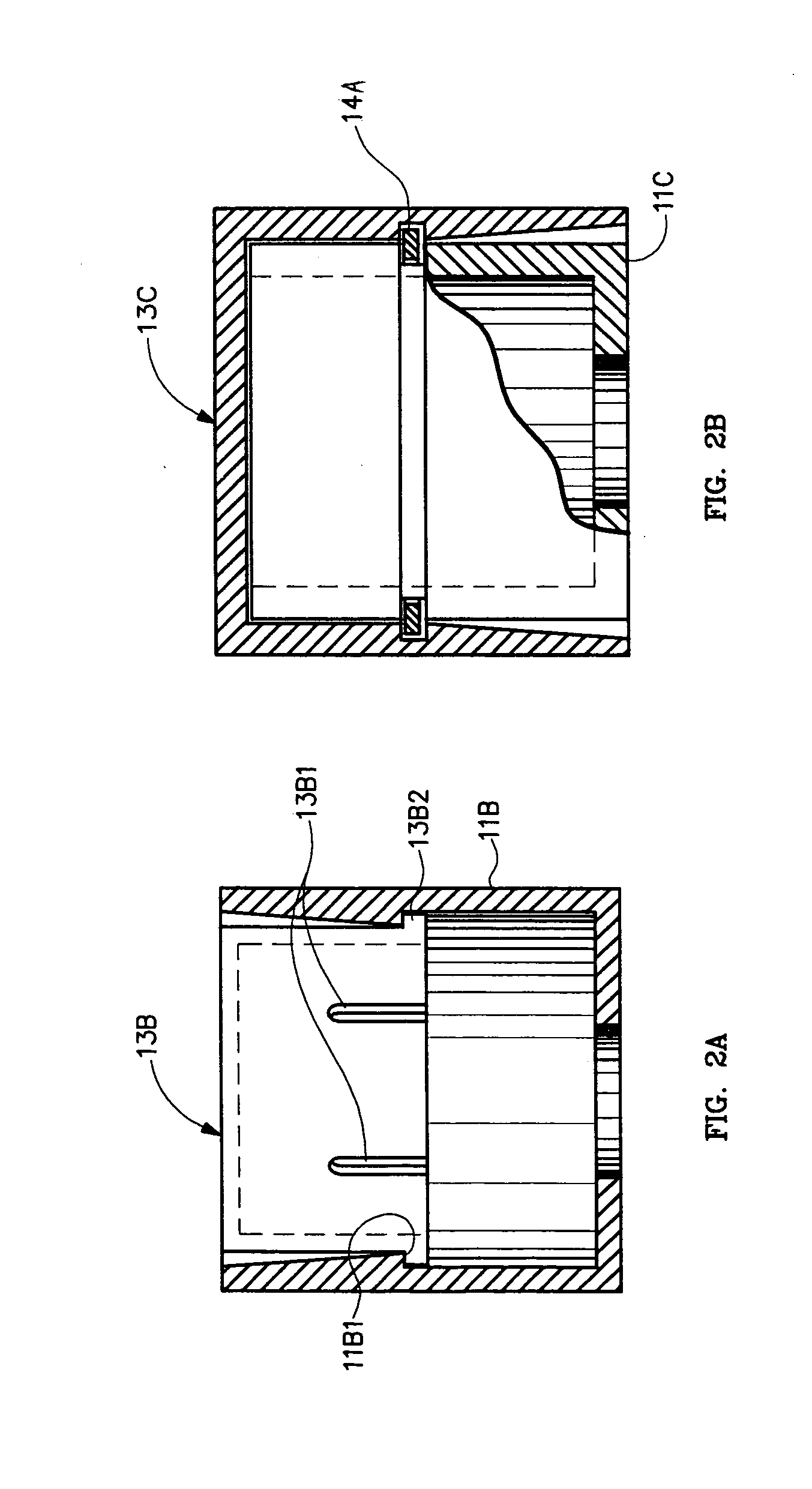
Tamper-proof nut or bolt head security cover
In a security cover, or system, for a fastener both (1) a step washer, and (2) a hollow cylinder rotating to the contained step washer, are affixed to a surface by a nut, or by a bolt head, that is to be protected from tampering. A (3) hollow cap fits loosely over the bolt head or nut, and is either (A) compressively forced upon the step washer, the cap being within cylinder that is then rotatable relative to the cap, step washer and nut or bolt head; or else (B) compressively forced into the hollow of the cylinder, therein to rotate together with the cylinder relative to the step washer and nut or bolt head. The (3) hollow cap may also be fit compressively over, as opposed to within, the cylinder. No matter to which component the cap fits compressively, and whether mounted to the interior or exterior of the cylinder, the outermost structure—normally the cylinder—(A) rotates freely to the bolt head or nut contained therein, (B) is, by action of the lock washer, highly resistant to becoming compressed so as to gain purchase on the enclosed bolt head or nut for malicious loosening and tampering, and (C) is, by its compression fit, highly resistant to removal. An optional (4) ring can be fit between the cap and the cylinder and into complimentary circumferential grooves on each. The rotating incompressible cover in three, or in four, parts provides permanent, unremovable, security to a bolt head, or a nut, from tampering.
Owner:DILLENBERGER ERIC JOHN
Security system for printed material
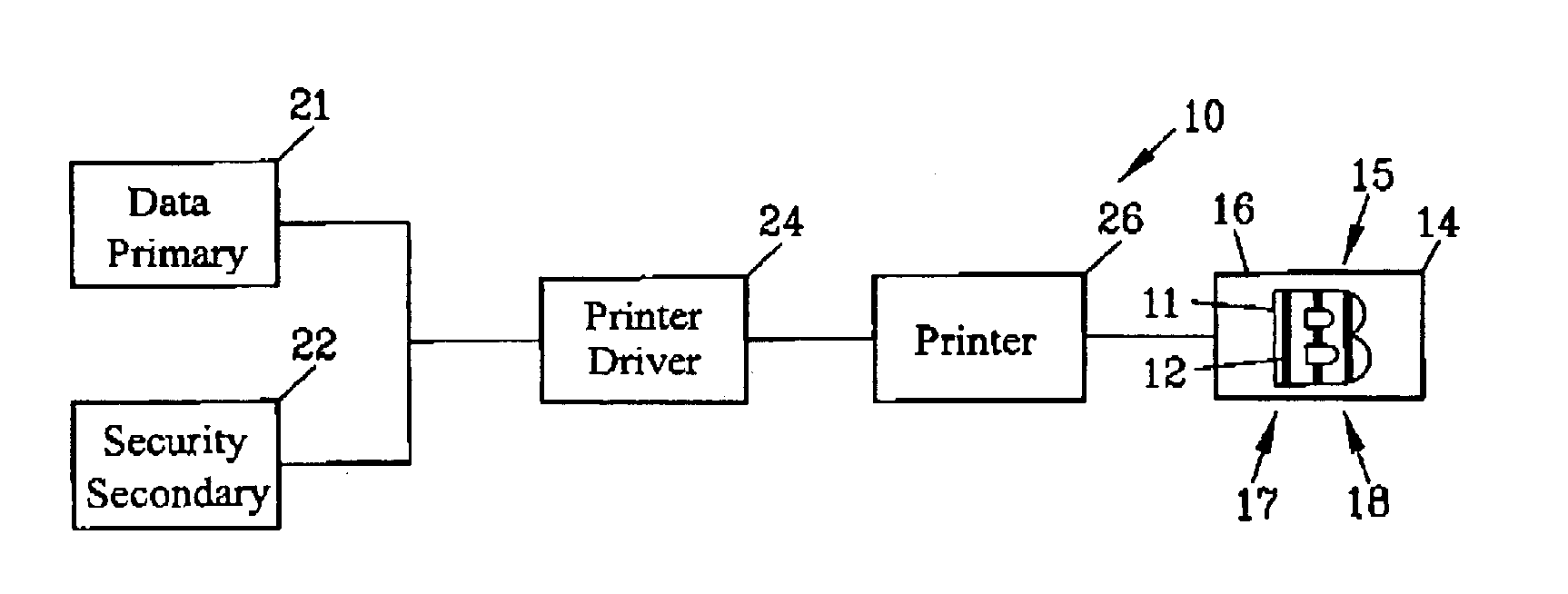
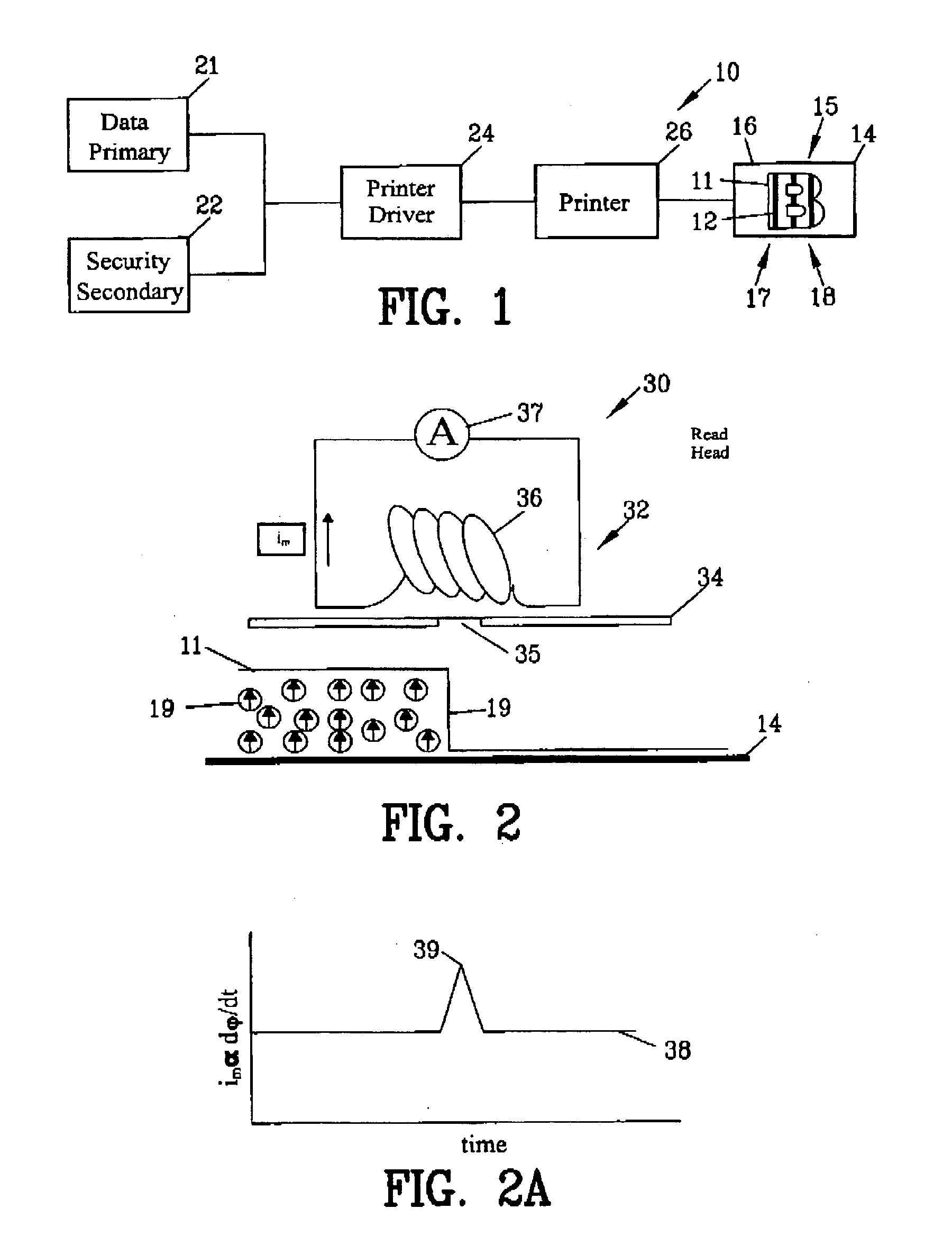
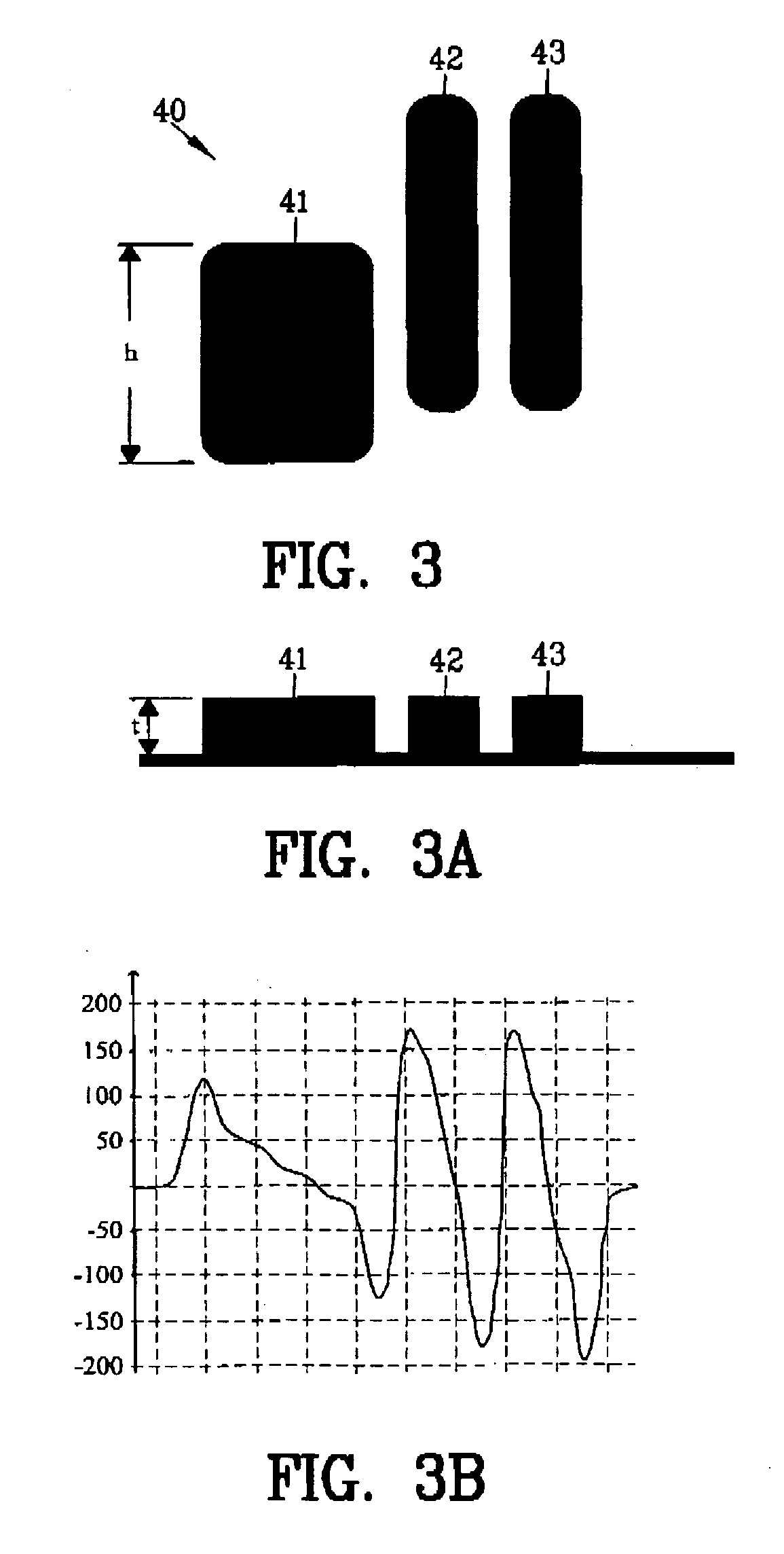
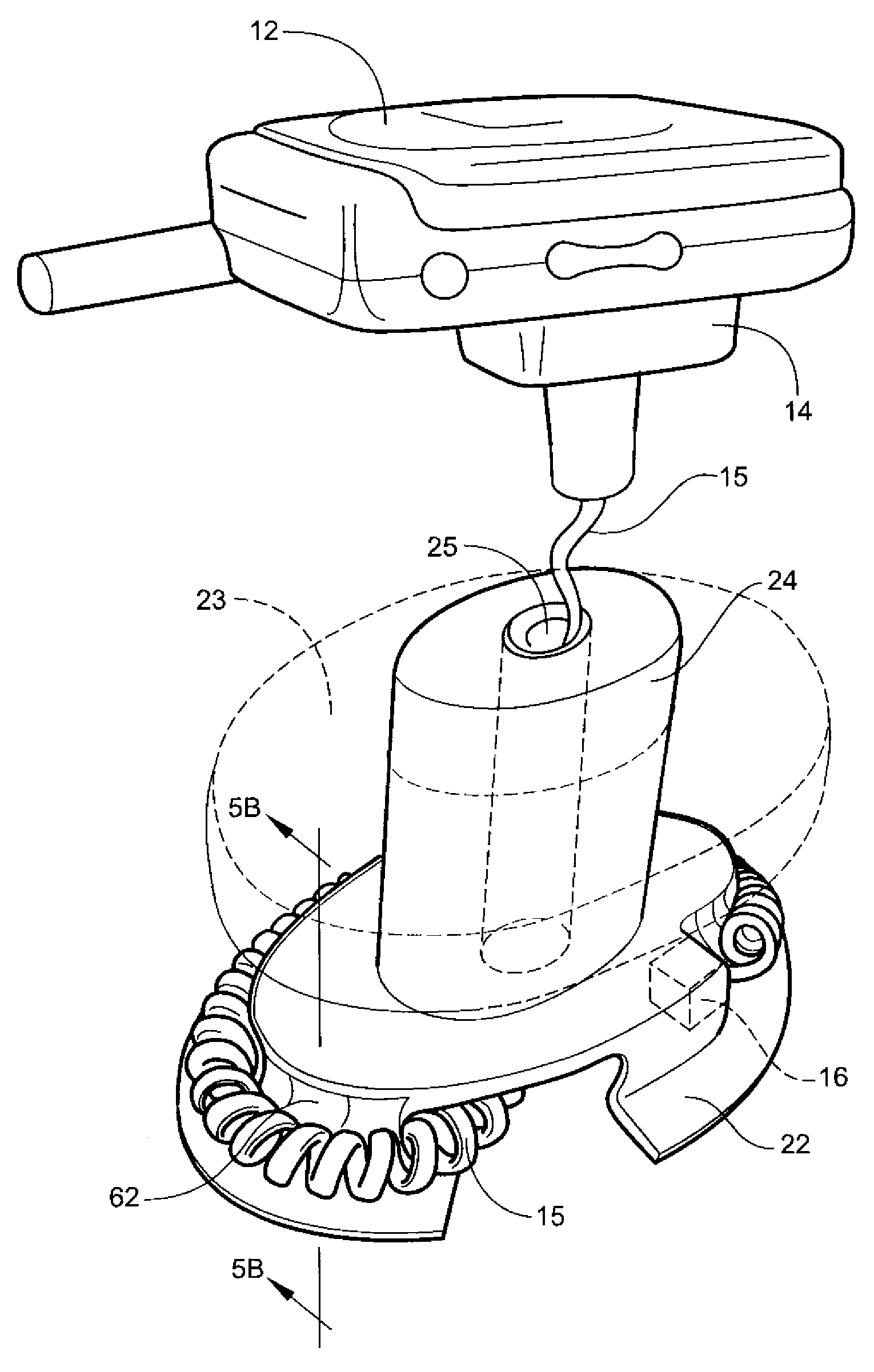
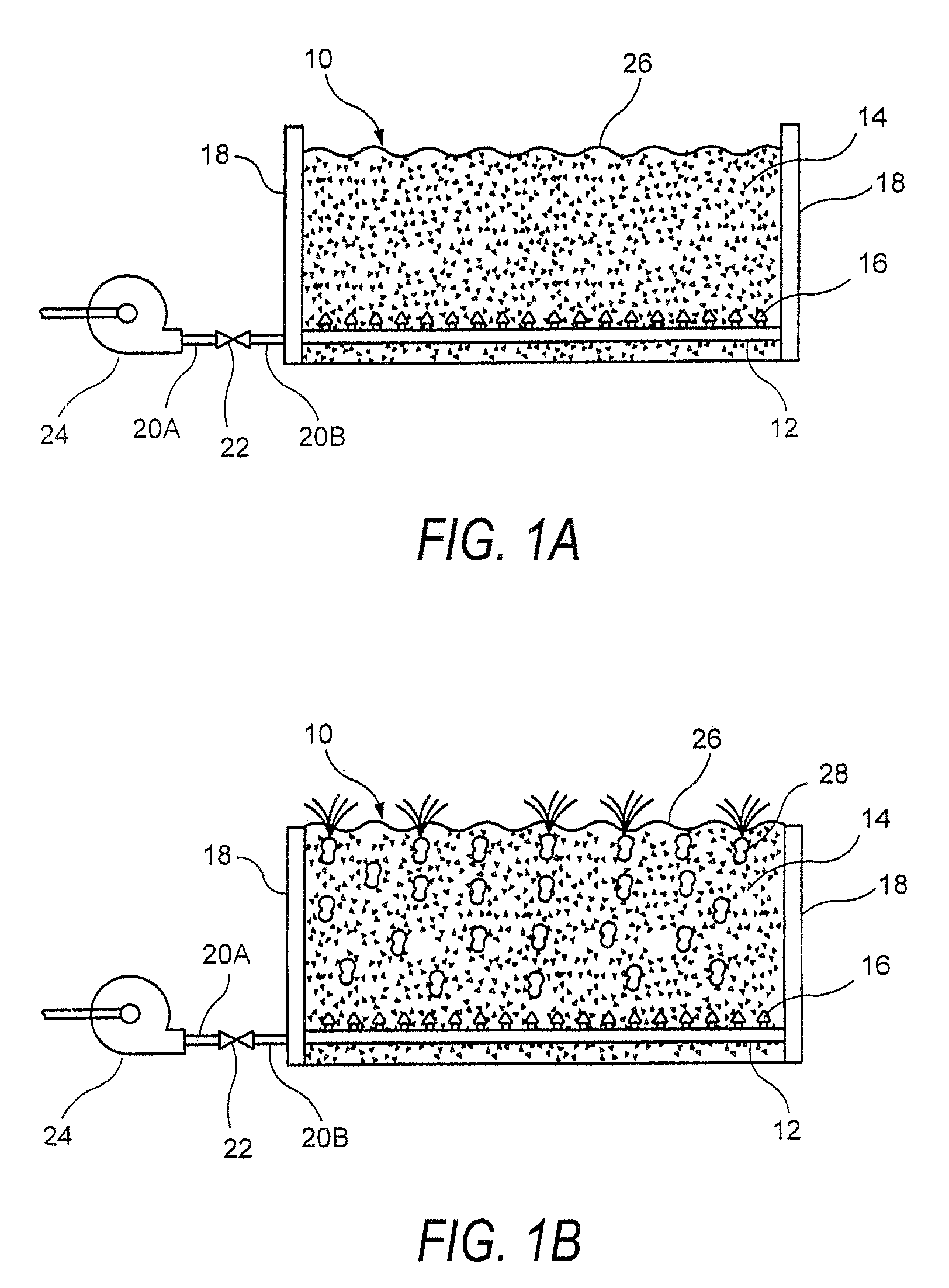
InactiveUS20110096368A1Improve the security systemProvide securityPattern printingVisual presentation using printersOptical propertyEngineering
An improved security system is disclosed for material printed on a substrate comprising a primary marking printed on the substrate for conveying information. A secondary marking provides security to the primary marking. The secondary marking may include a variation in optical properties, a variation in magnetic properties or a variation in both in optical properties and magnetic properties of the primary marking. A method is disclosed comprising printing a primary and a secondary marking on a substrate with the primary marking conveying information and with the secondary marking providing security to the primary marking.
Owner:MAHER JAMES
Display stand including means for dispensing and collecting helical cable
InactiveUS8181929B2Avoid accidental removalStop theftStands/trestlesKitchen equipmentHelical scanDisplay device
A display stand for displaying an article of merchandise includes a base defining an outer periphery and means for dispensing and collecting a helical cable attached to the article of merchandise. The means for dispensing and collecting supports and guides the helical cable along the outer periphery of the base between a retracted length and an extracted length. The dispensing and collecting means may include at least one wheel disposed on the outer periphery of the base. The dispensing and collecting means may include at least one roller disposed on the outer periphery of the base. The dispensing and collecting means may include a low-friction surface disposed on the outer periphery of the base. The dispensing and collecting means may include a scalloped surface disposed on the outer periphery of the base. The display stand may further include a collection tube for delivering the helical cable to the article.
Owner:INVUE SECURITY PROD INC
Removal tool
InactiveUS7117712B1Improve the security systemSimple and economical to manufactureVehicle locksPadlocksHydraulic pumpEngineering
A security system for a shipping container includes a cover and seal pin, and a special removal tool for removing the pin from the cover. The cover includes a vertical channel with top and bottom plates mounted therein to form a rearwardly opening box. A pair of vertically aligned apertures in the top and bottom plates are aligned with apertures in ears of a hasp on the shipping container, and receive the seal pin to secure the cover to the container. A seal pin includes an elongated shaft with annular grooves in the upper and lower ends. A pair of end caps each includes an annular groove on their interior surfaces that correspond with the shaft grooves to retain a locking ring within the pair of aligned grooves, when the caps are snapped on the ends of the shaft. The locking rings prevent removal of the caps, once snapped into place on the shaft. A removal tool includes a hydraulic pump with a punch secured to a piston of the pump. A punch housing has a gripping structure on the lower end that will grip a seal pin end cap, while the punch is driven through the end cap to push the shaft free of the end cap and release the seal pin.
Owner:SECURUS ENTERPRISES
Electronic system with a multiple access protocol and method of multiple access
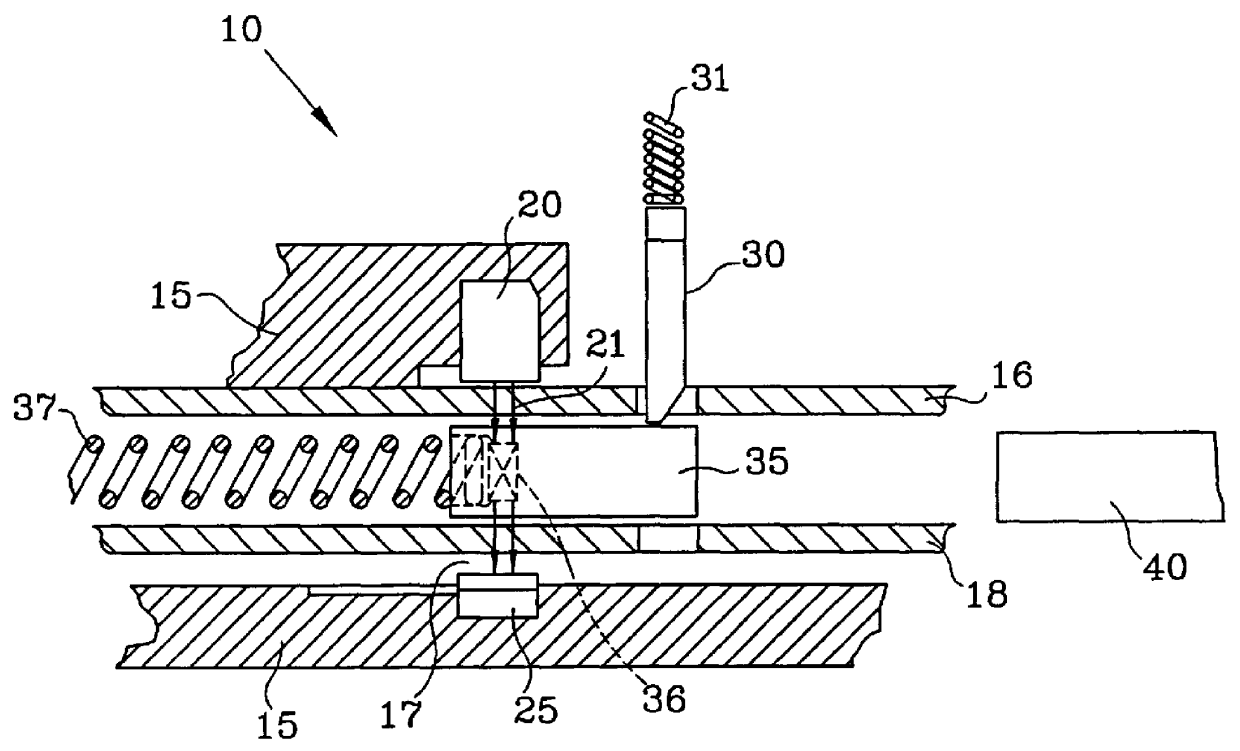
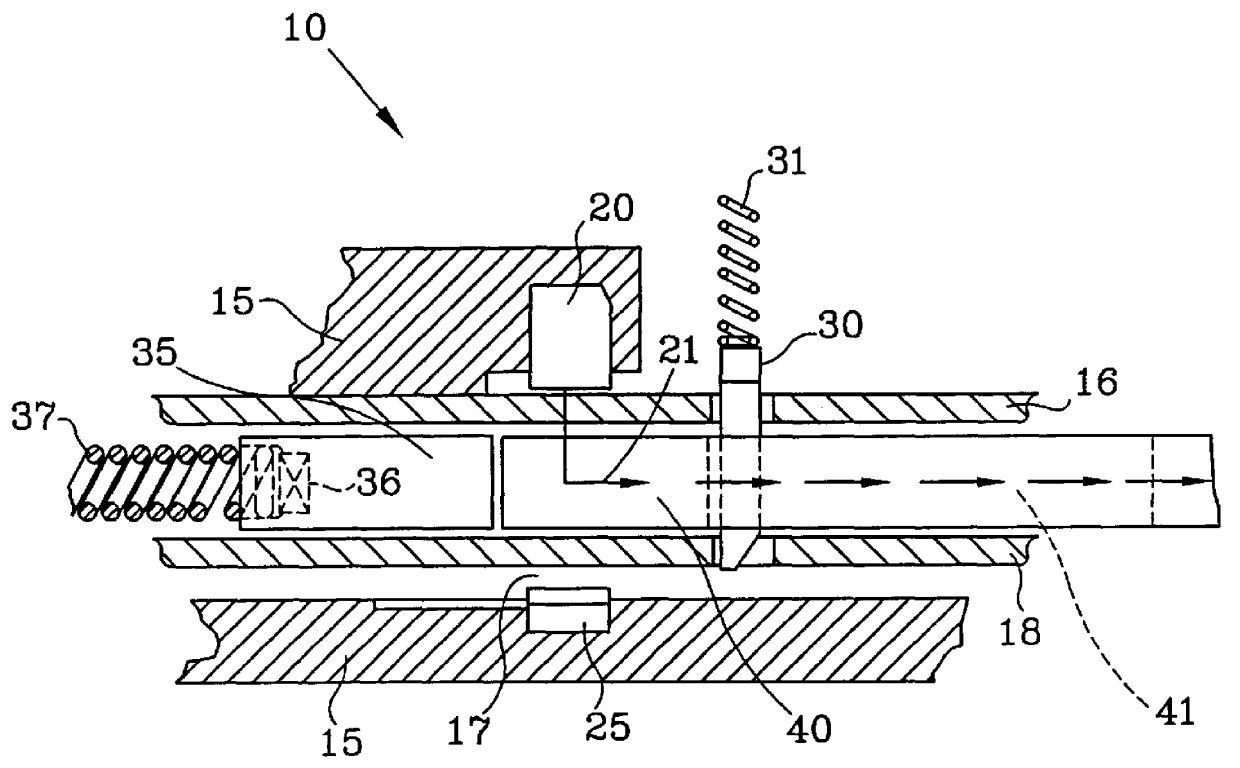
InactiveUS7019636B2Reduce disadvantagesImprove the security systemElectric testing/monitoringLoop networksAccess methodElectronic systems
The electronic system, especially a security system, includes a number of different units that access a network according to a multiple access protocol, which is designed to minimize collisions between frames while reducing bandwidth requirements. The units may monitor different spatial regions according to several different criteria. Respective units that monitor according to correspondingly different criteria in a given spatial region may be assembled into one group and units that monitor different spatial regions but according to the same criterion may be assembled into another group. Each of the units of the one group are provided access to the network in one concurrent time slot, while the units of the other group are provided access to the network in a different concurrent time slot.
Owner:ROBERT BOSCH GMBH
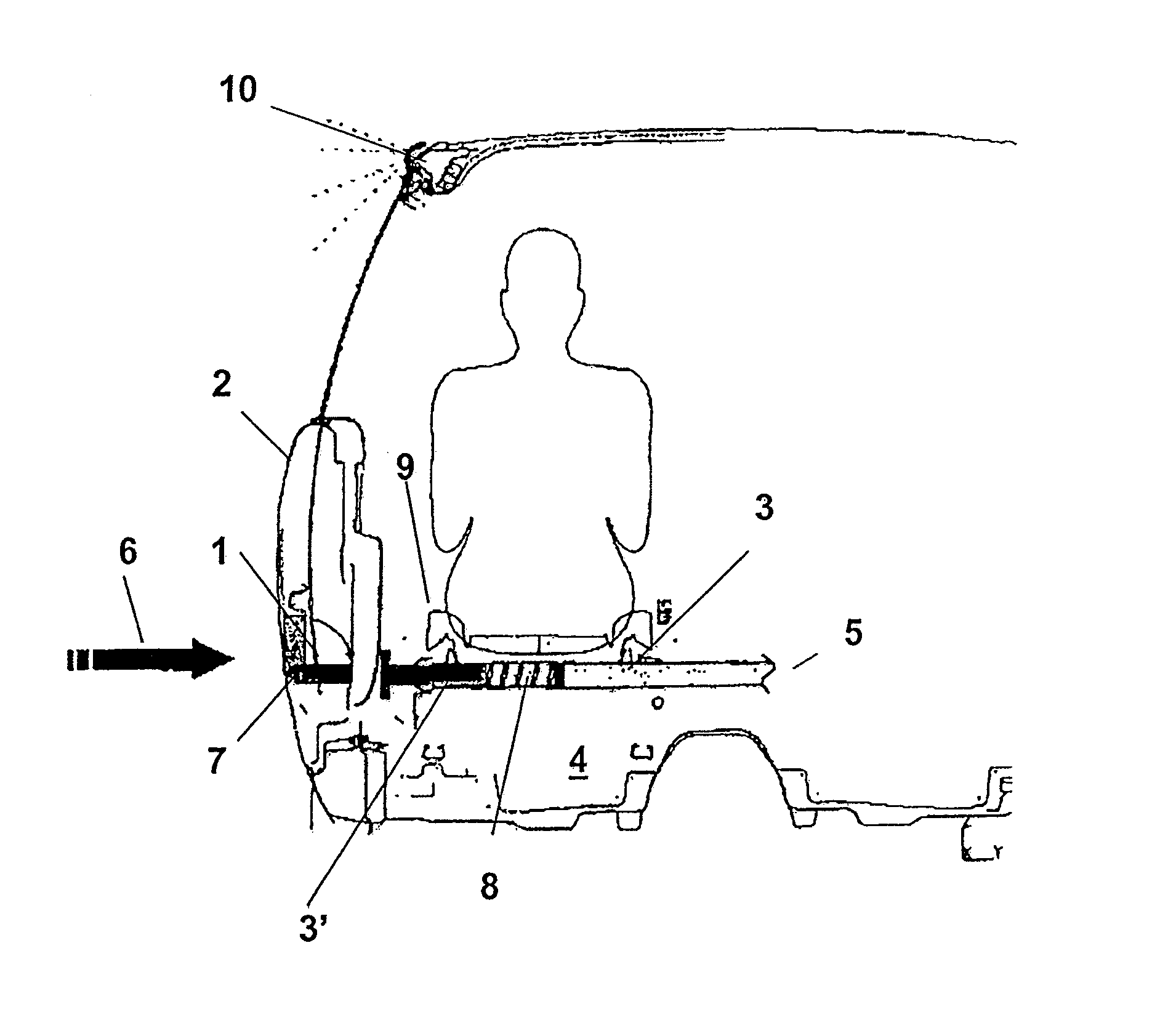
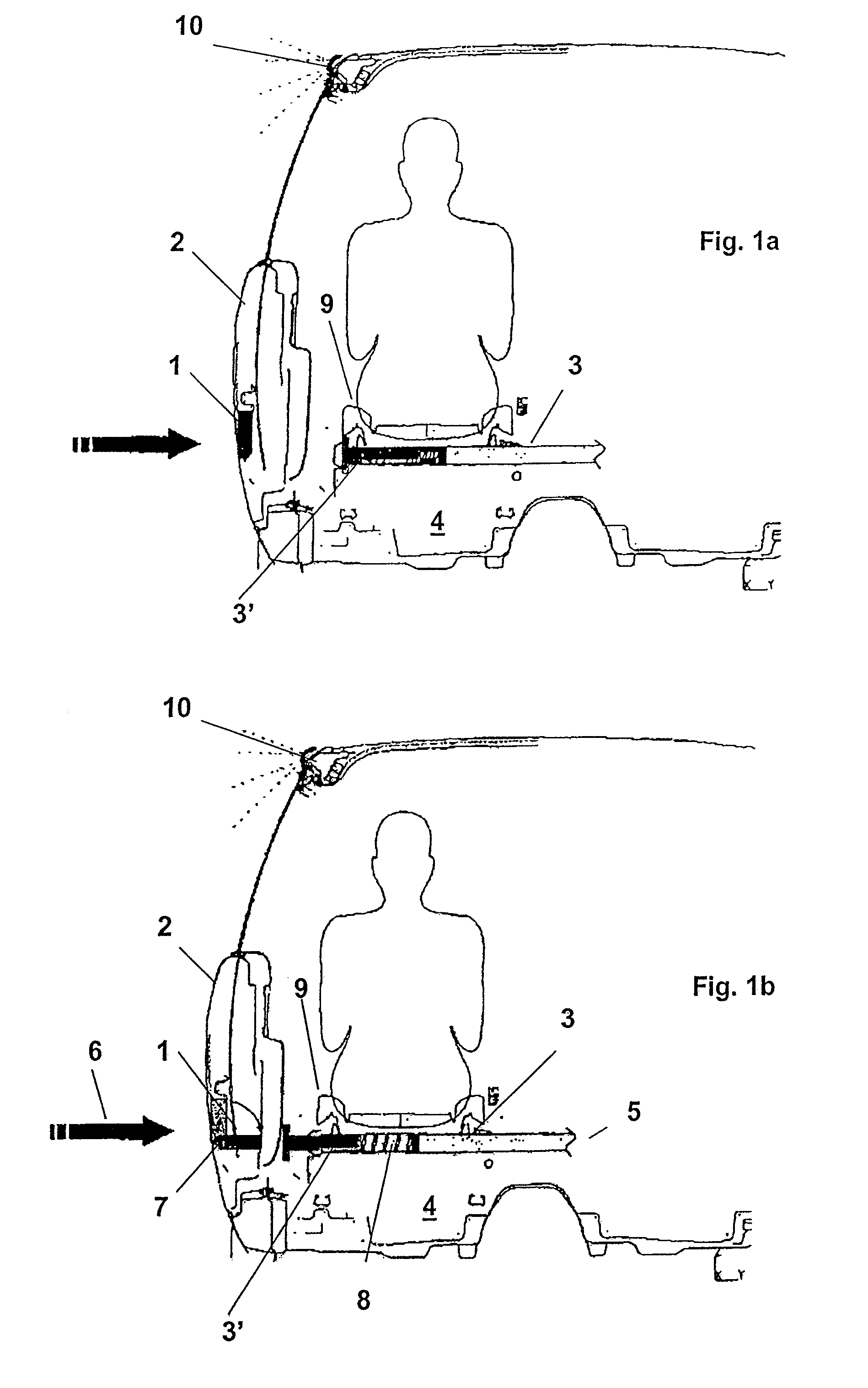
Device for a motor vehicle for protecting vehicle occupants when there is an impact of energy directed at a motor vehicle door due to a collision
InactiveUS8061763B2Improve protectionImproved occupant protectionPedestrian/occupant safety arrangementDashboardsMobile vehicleEnergy absorption
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
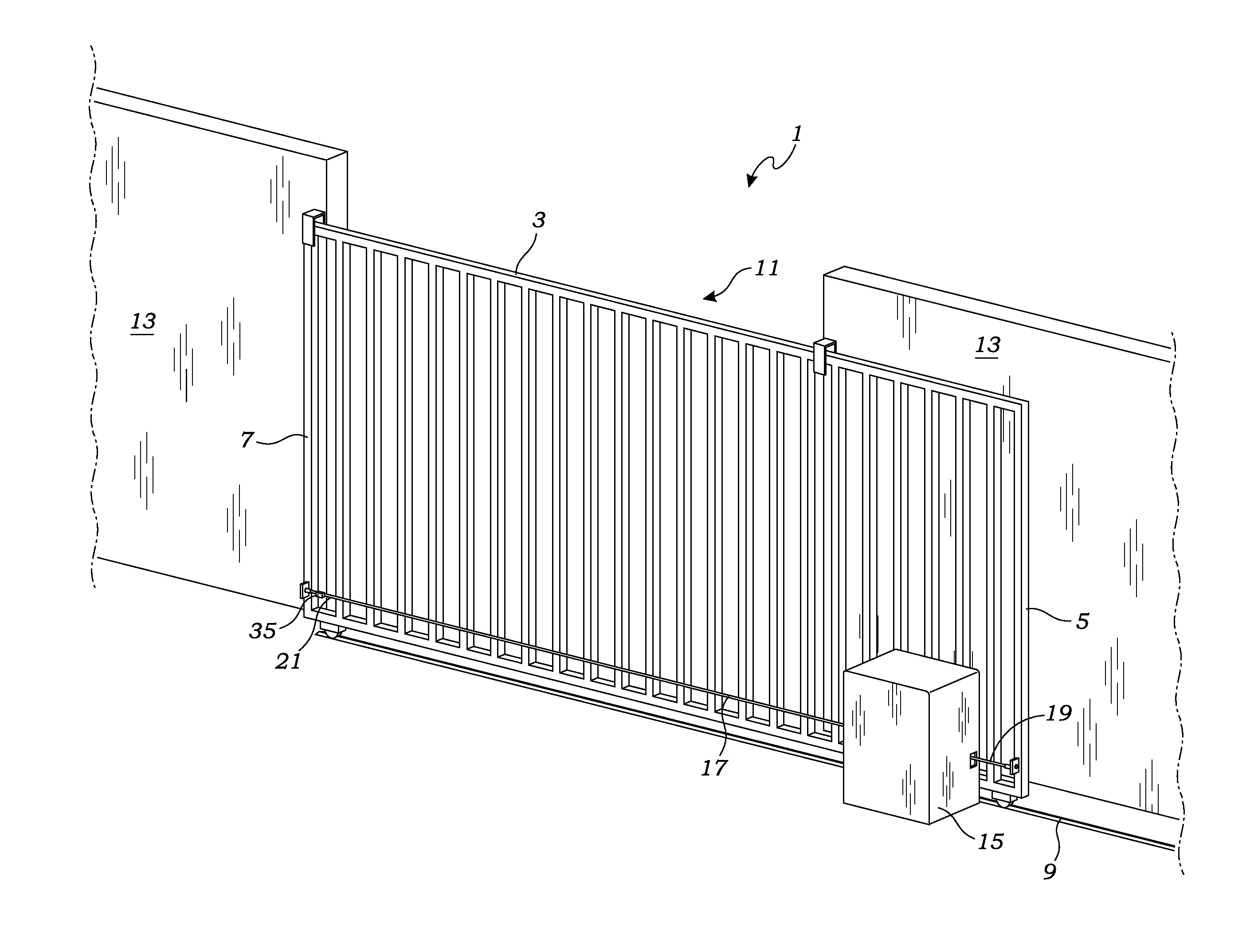
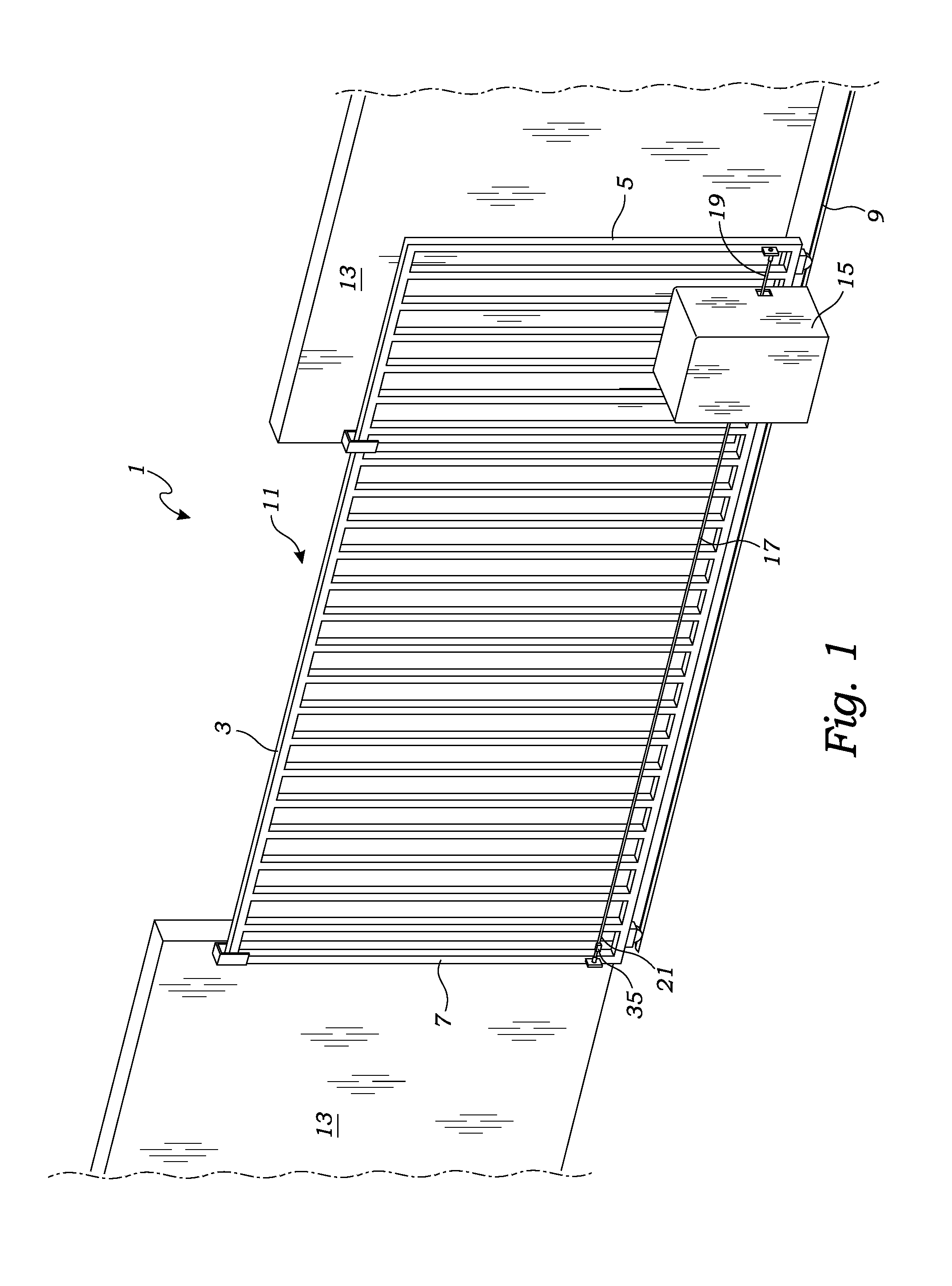
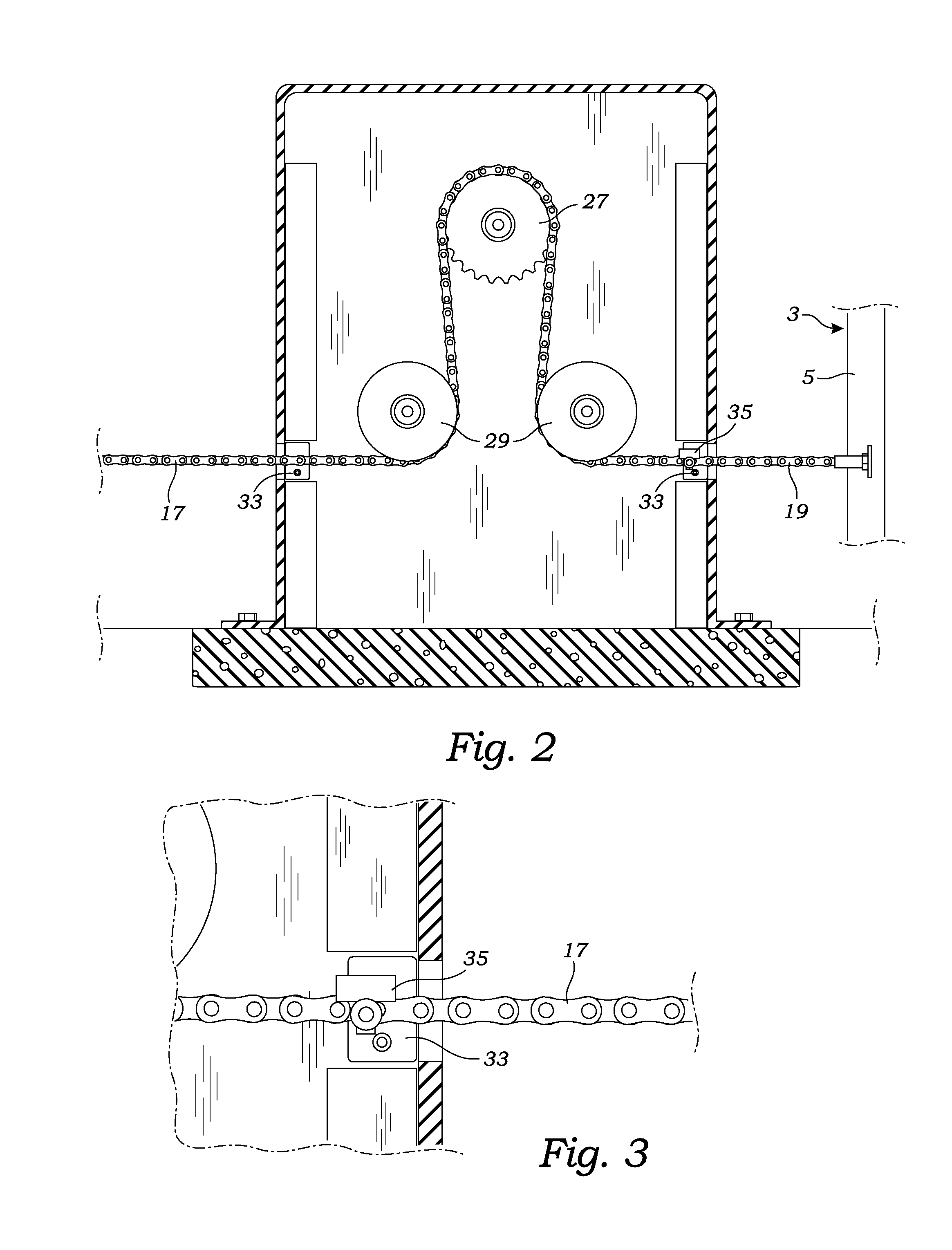
Chain driven gate and security system
ActiveUS9406207B2Easy to slideReduce frictionBurglar alarm by openingGates/doorsSprocketSecurity system
A chain driven gate and security system is provided. The system includes a gate which is opened and closed by a gate operator. The gate operator includes a chain and a motor having a rotatable sprocket for engaging the links of a chain. The gate and security system includes a sensor for detecting whether the chain has been severed, an alarm for producing a visible or audible alert, and a processor connected to the motor, sensor and alarm. The processor activates an alarm in the event that the processor indicates that the gates should be closed, but that the chain has been severed.
Owner:PARSADAYAN ALEX
Fluidized bed technology for security enhancement
InactiveUS7405654B2Prevent crashReduce usageAir-treatment apparatus arrangementsBurglar alarmThird partyFluidized bed
An improved system and methods for increasing security at sensitive locations from unwanted third parties through the use of fluidized granular solids.
Owner:PROCEDYNE
Facility for parking and recharging electrical vehicles
InactiveUS20140321952A1Improve the security systemMore separatedCharging stationsElectric vehicle charging technologyElectricityElectric cars
Facility for parking and recharging electrical vehicles. It comprises platforms (1) where electrical vehicles (2) are parked and / or kept connected to the electricity supply, means for keeping (3) said platforms horizontal in all the positions of the facility and access for vehicles to the inside of facility (14).
Owner:URBAN RESILIENCE
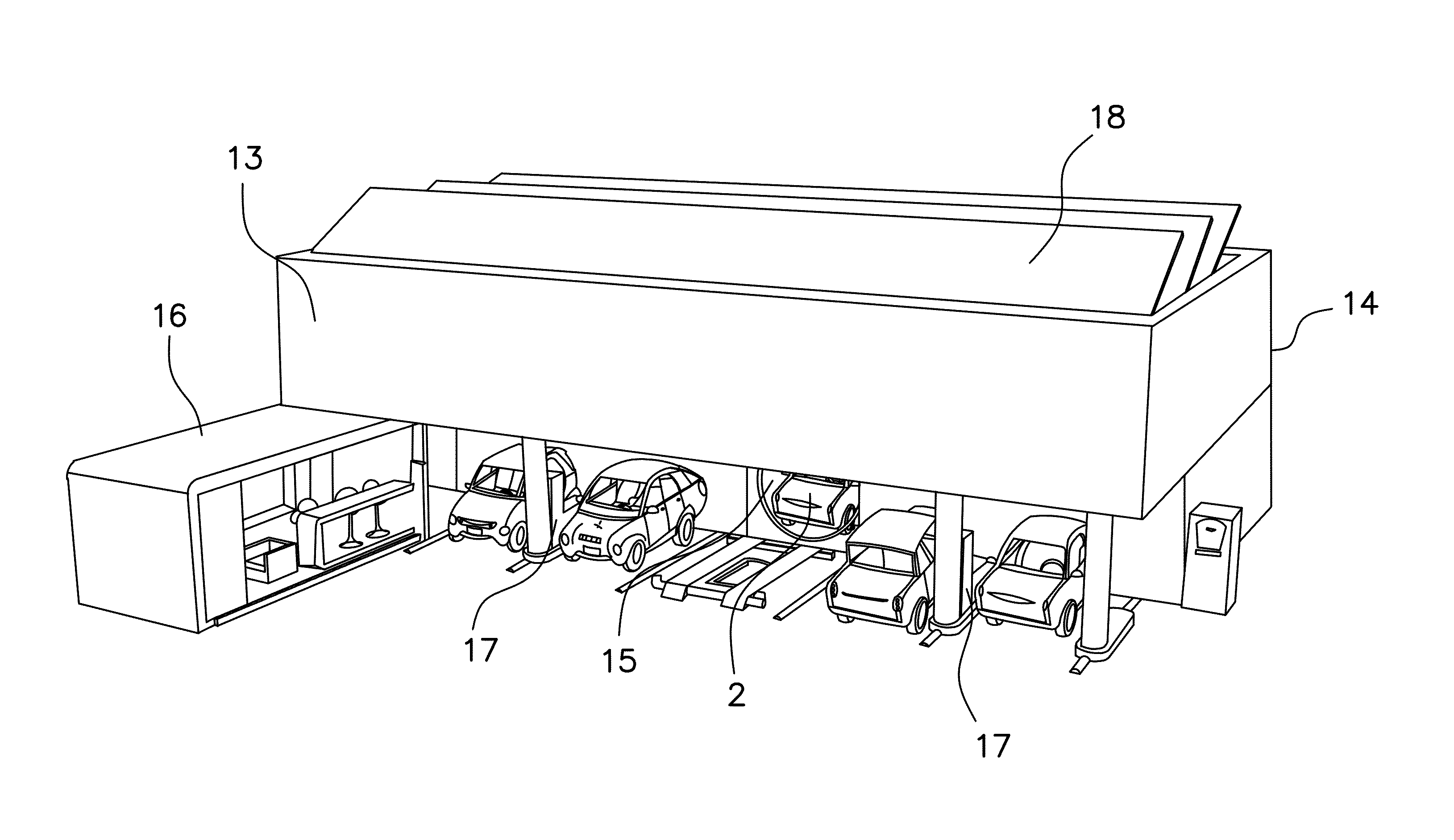
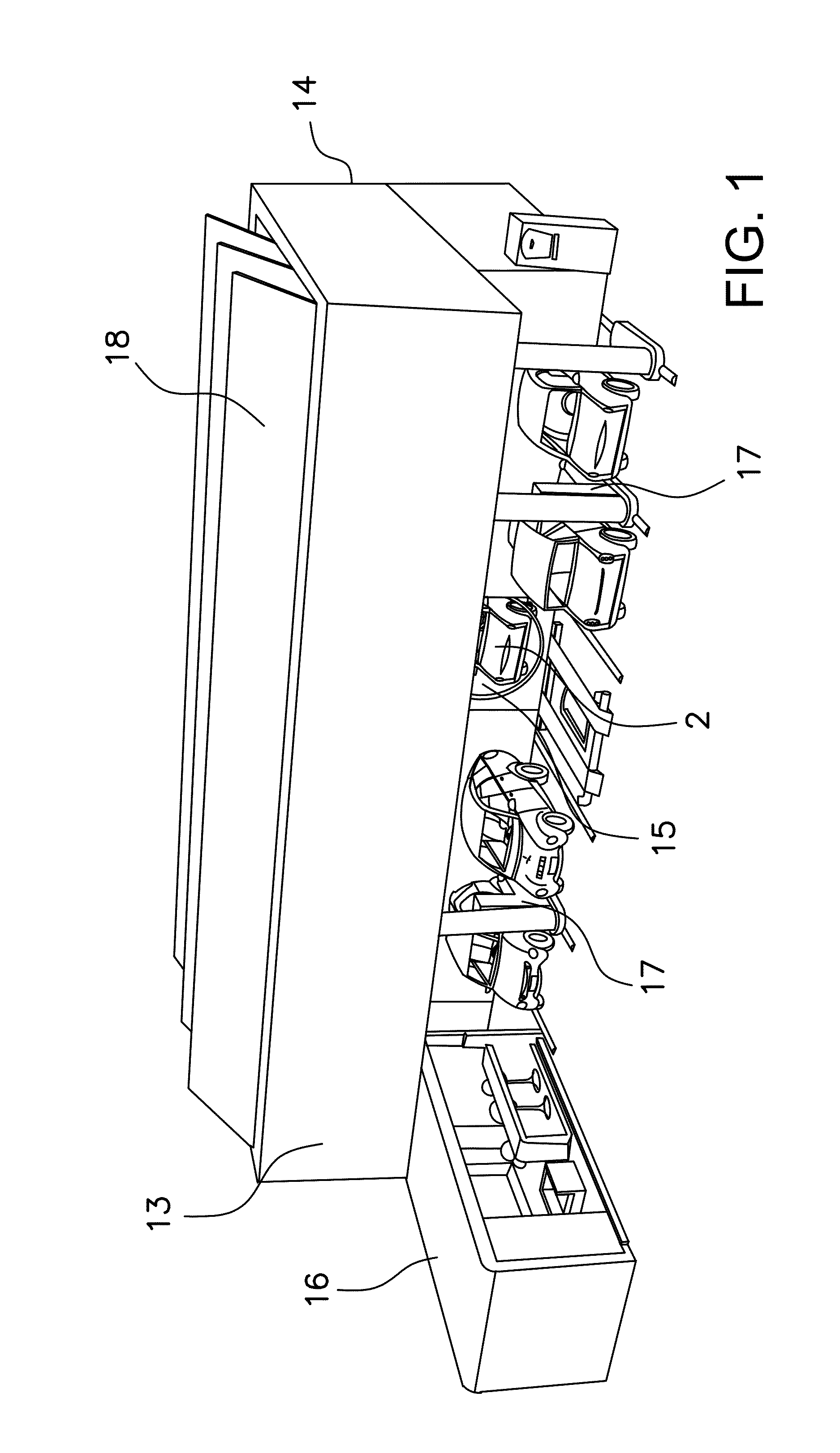
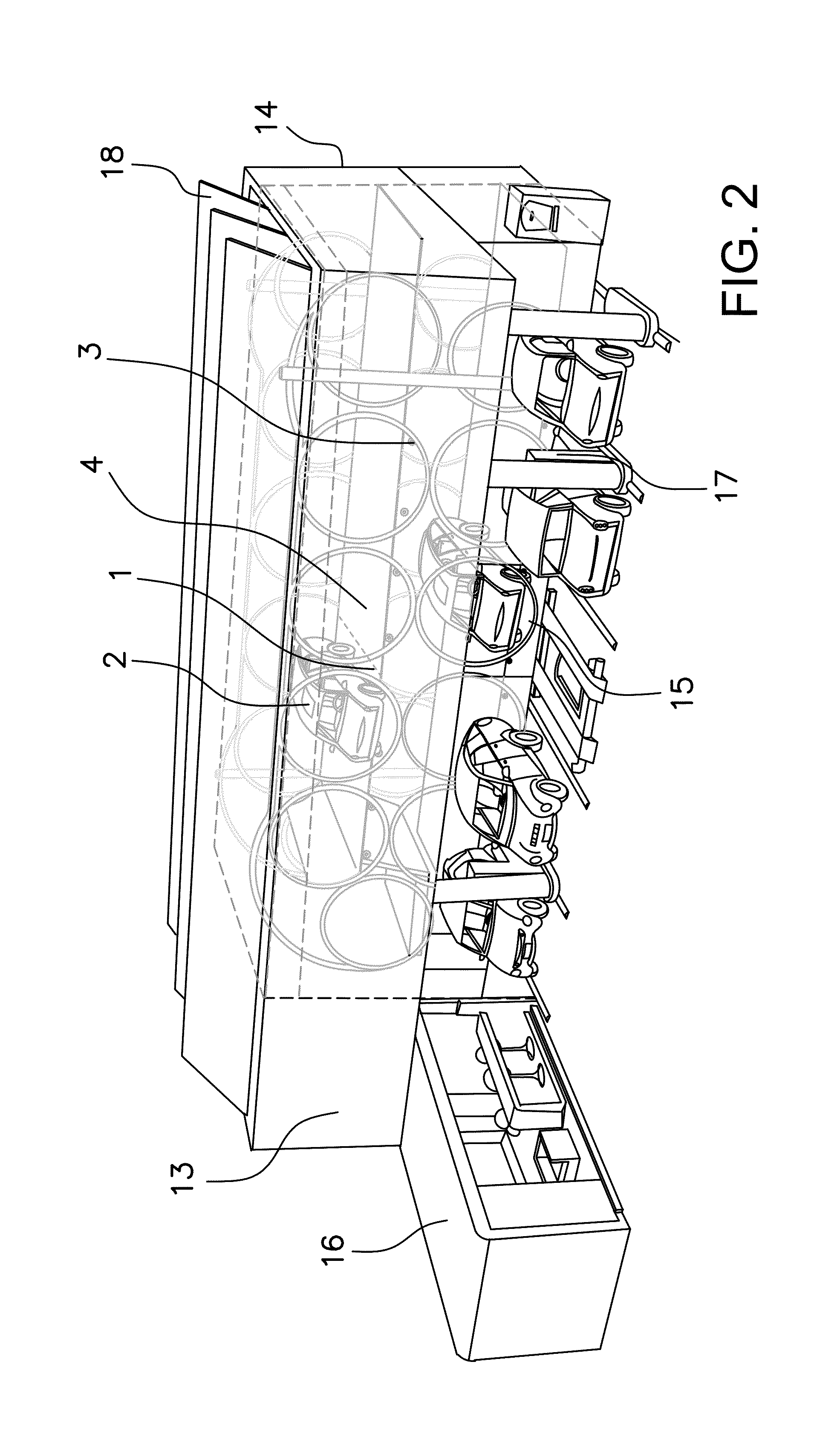
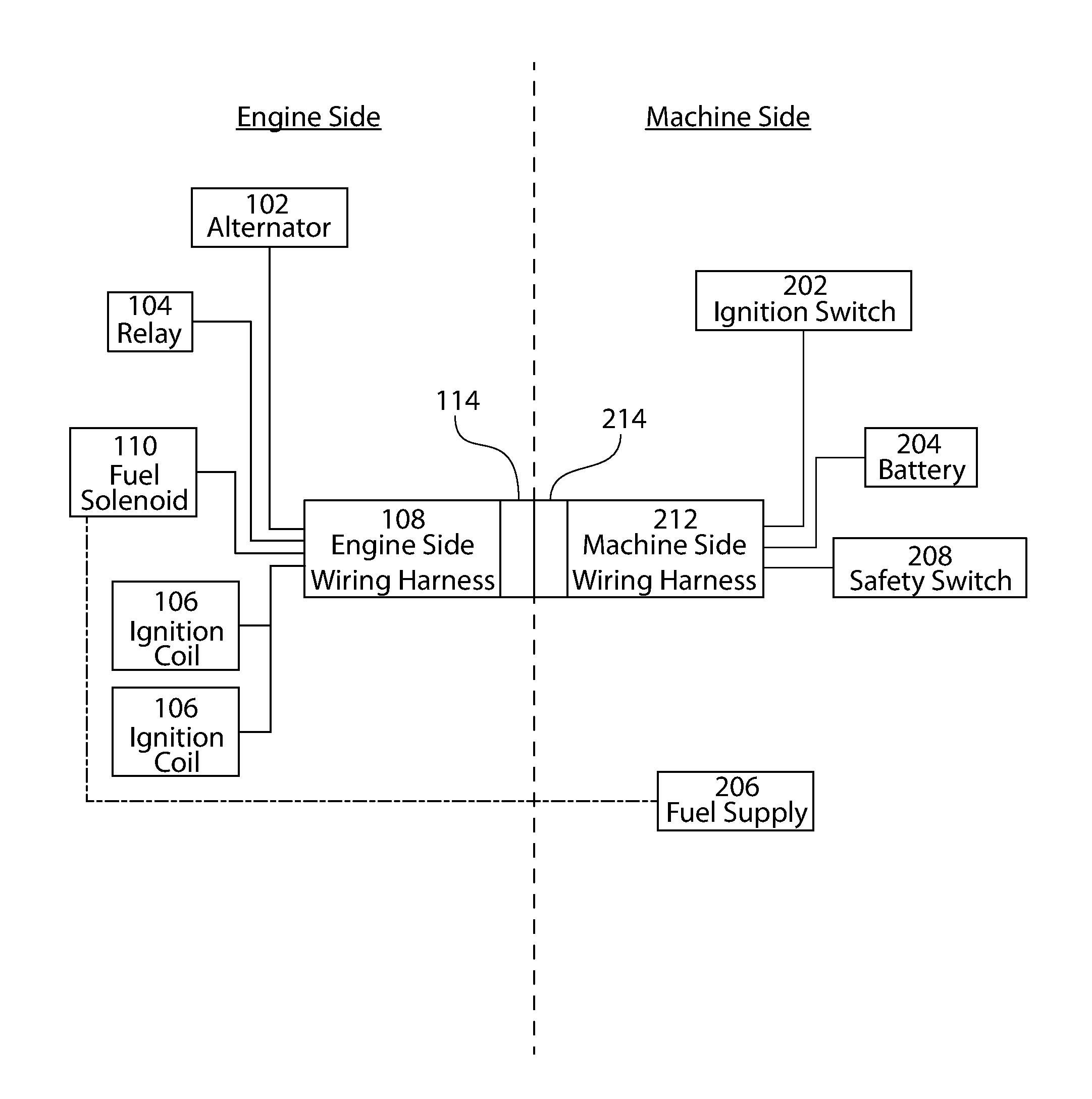
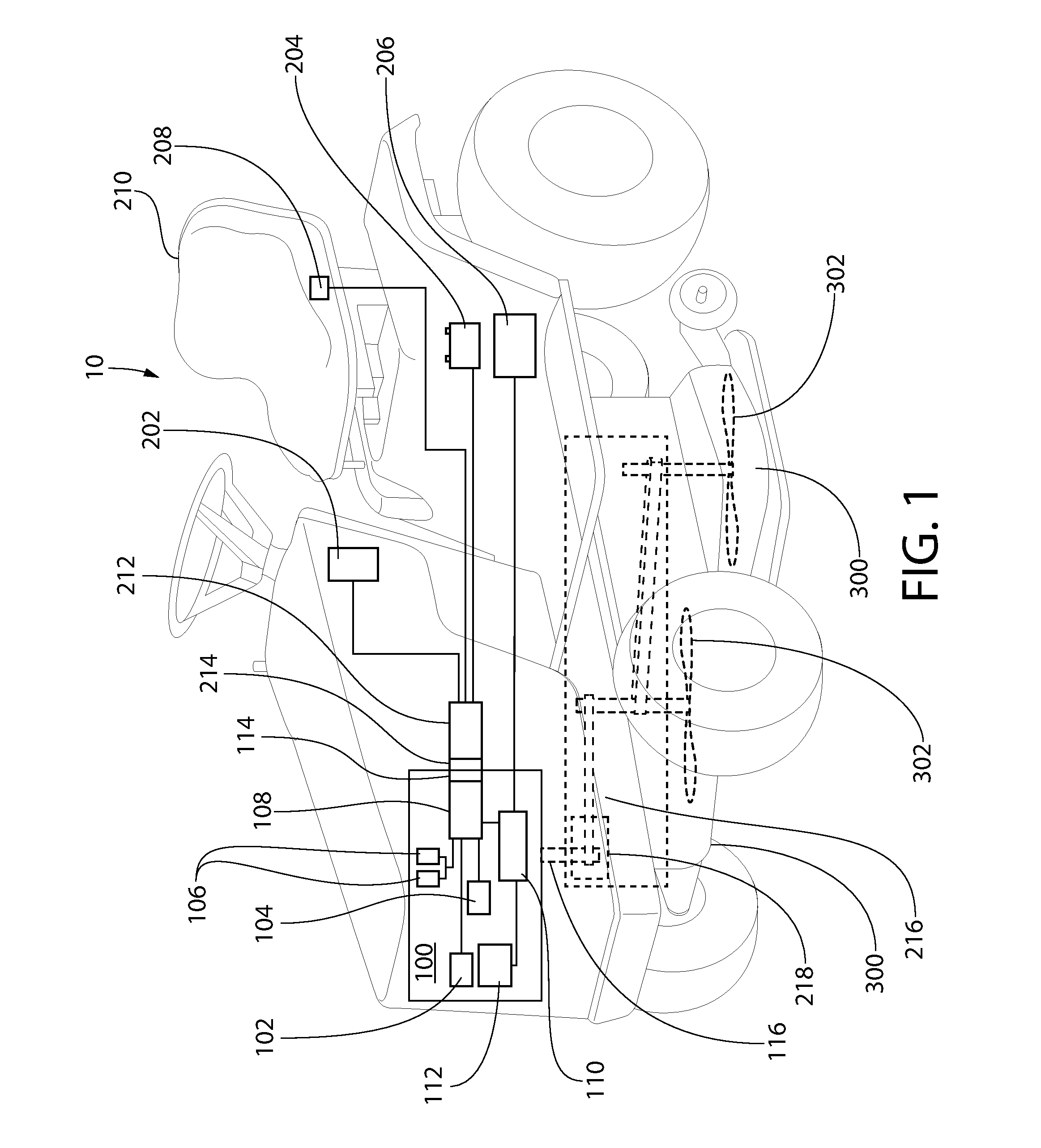
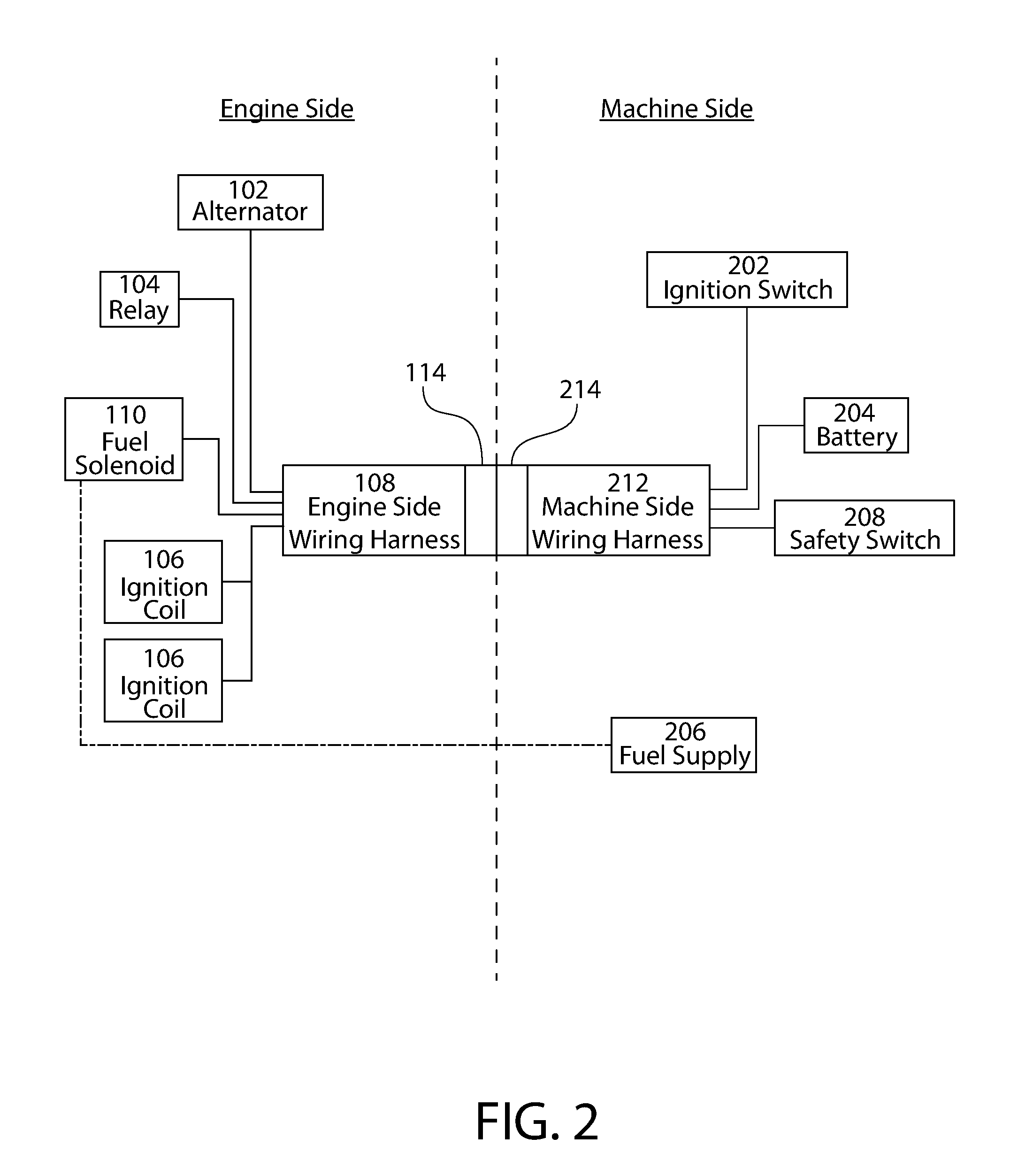
Safety system for engine shutdown, and engines and equipment incorporating the same
ActiveUS20160252024A1Reduce downtimeIncrease inertiaElectrical controlMowersBrake torqueIgnition coil
A safety system for engine powered machinery having a fuel cut functionality to promote more rapid shutdown of the rotating parts of the engine powered machinery. In one aspect, the system is implemented as a wiring harness disposed exclusively on the engine which simultaneously disables one or more ignition coils and prevents a fuel-air mixer from supplying a mixture of air and fuel to the engine upon activation of a safety switch. In alternate aspects, the system further comprises a stator brake which is activated by the safety switch to provide additional braking torque on the engine. These features bring the machinery to a rapid halt, further enhancing safety.
Owner:KOHLER CO
Door handle module
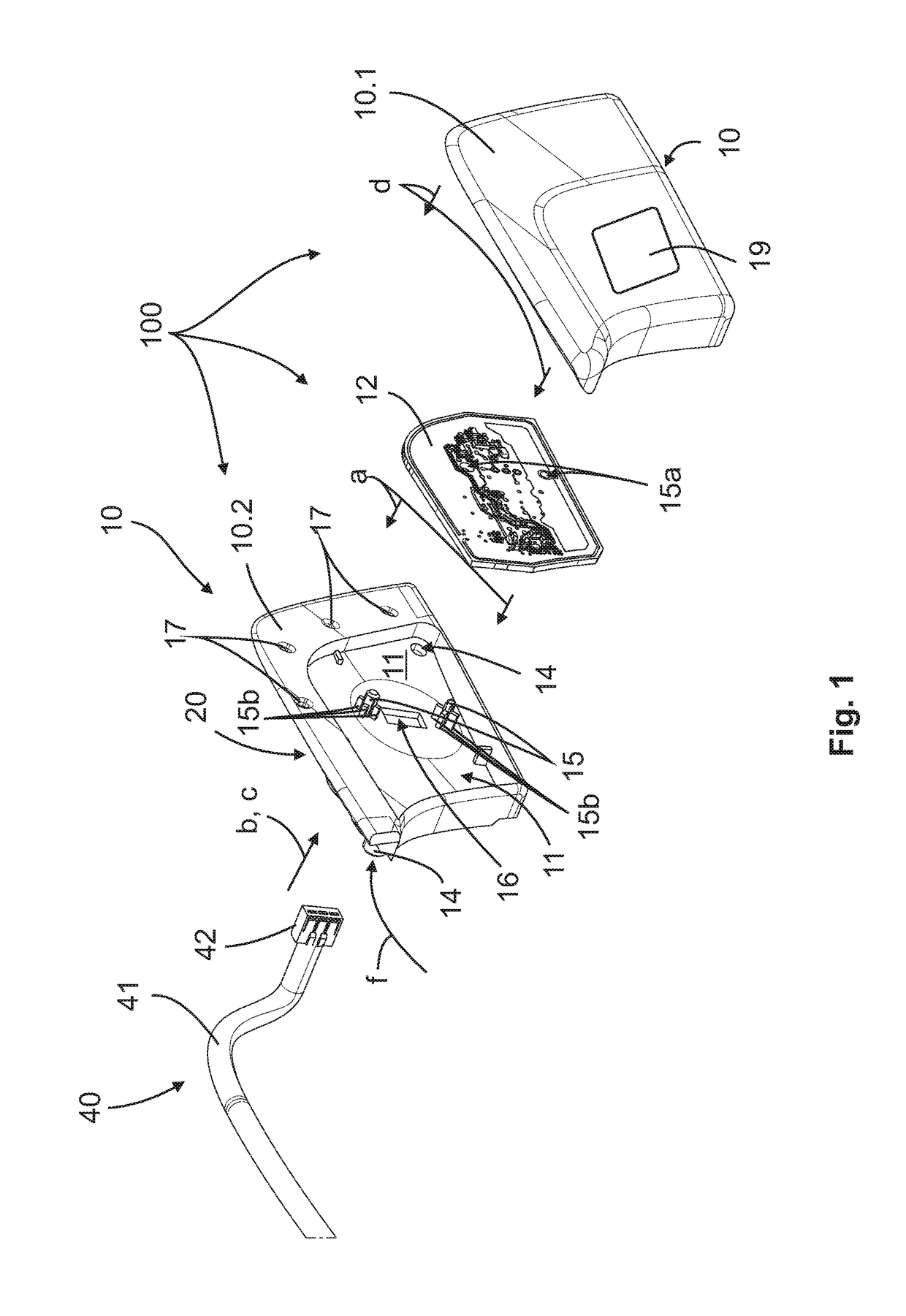
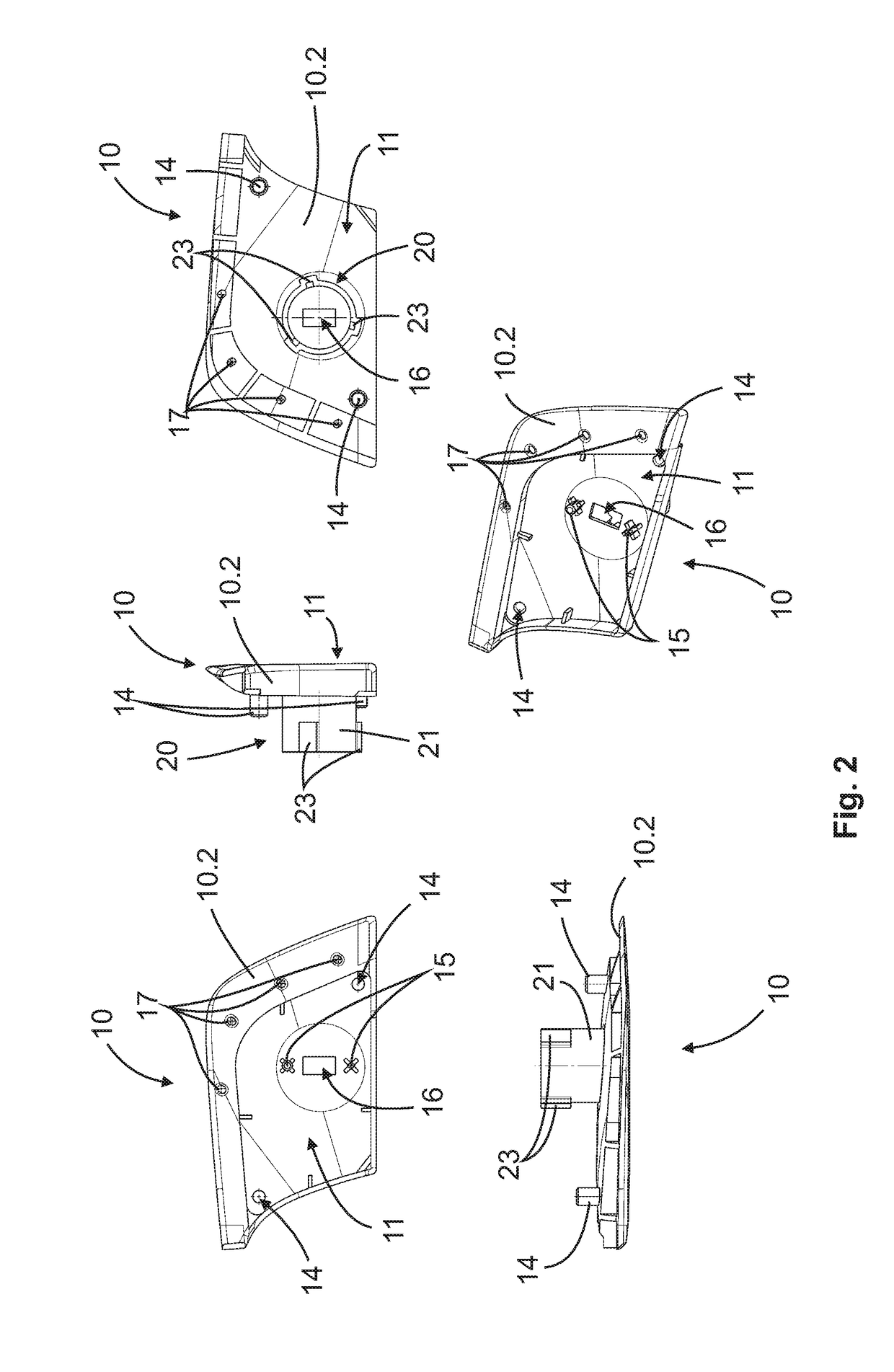
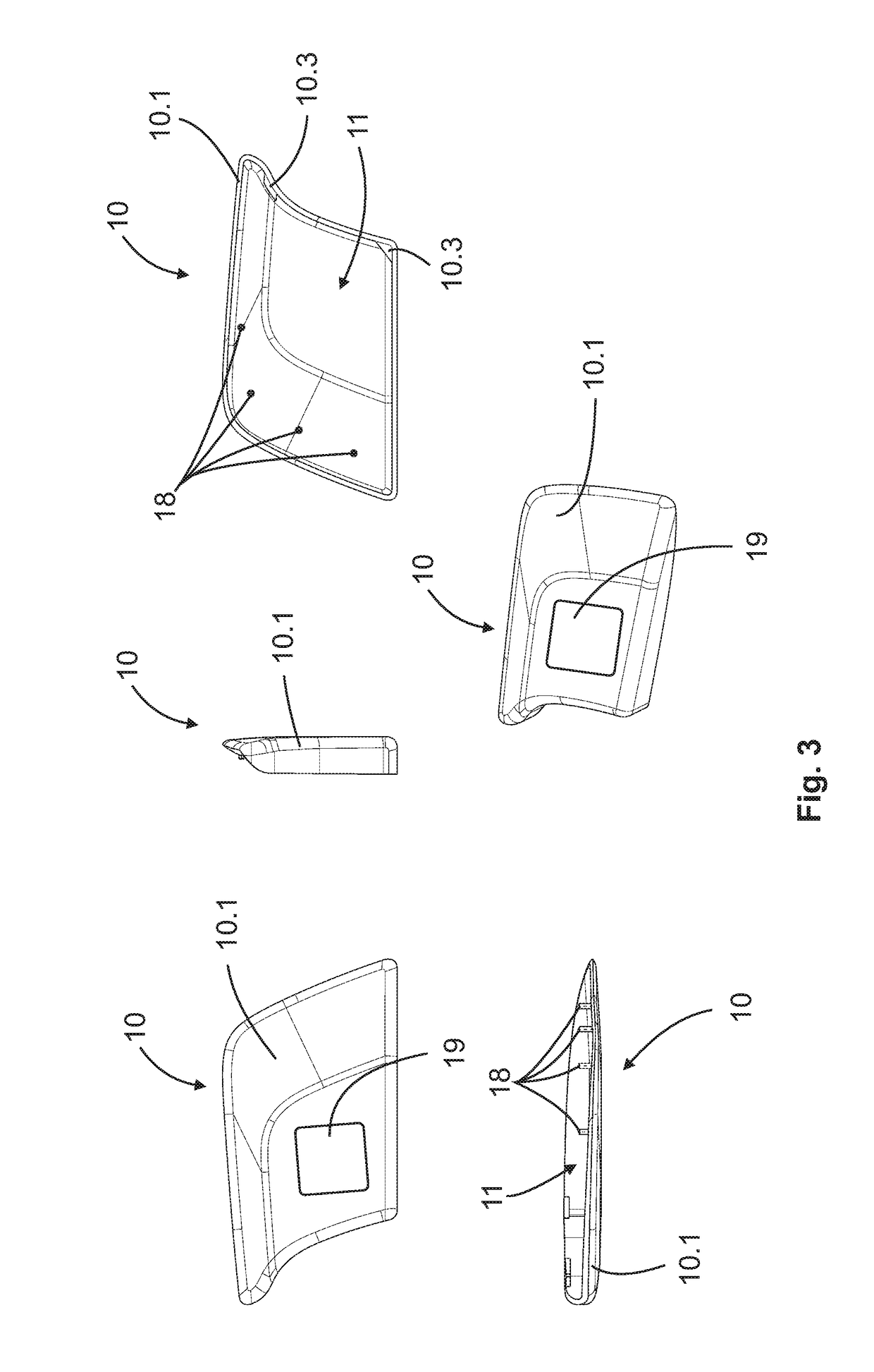
ActiveUS20190040660A1Reliably protected against weather influenceReliably mechanical impactAnti-theft devicesElectrical locking circuitsEngineeringCommercial vehicle
The invention relates to a door handle module (100) for a handle device (202) of a moveable part (201) of a vehicle (200), in particular a commercial vehicle, comprising: a housing (10), in which a receptacle (11) is formed, in which an electronics unit (12) for controlling a security system (203) of the vehicle (200) is arranged, wherein the electronics unit (12) comprises at least one communication element (12a, 12b) for the exchange of data with the vehicle-external communication unit (50).
Owner:HUF HULSBECK & FURST GMBH & CO KG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com