Patents
Literature
171 results about "Perimeter Security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
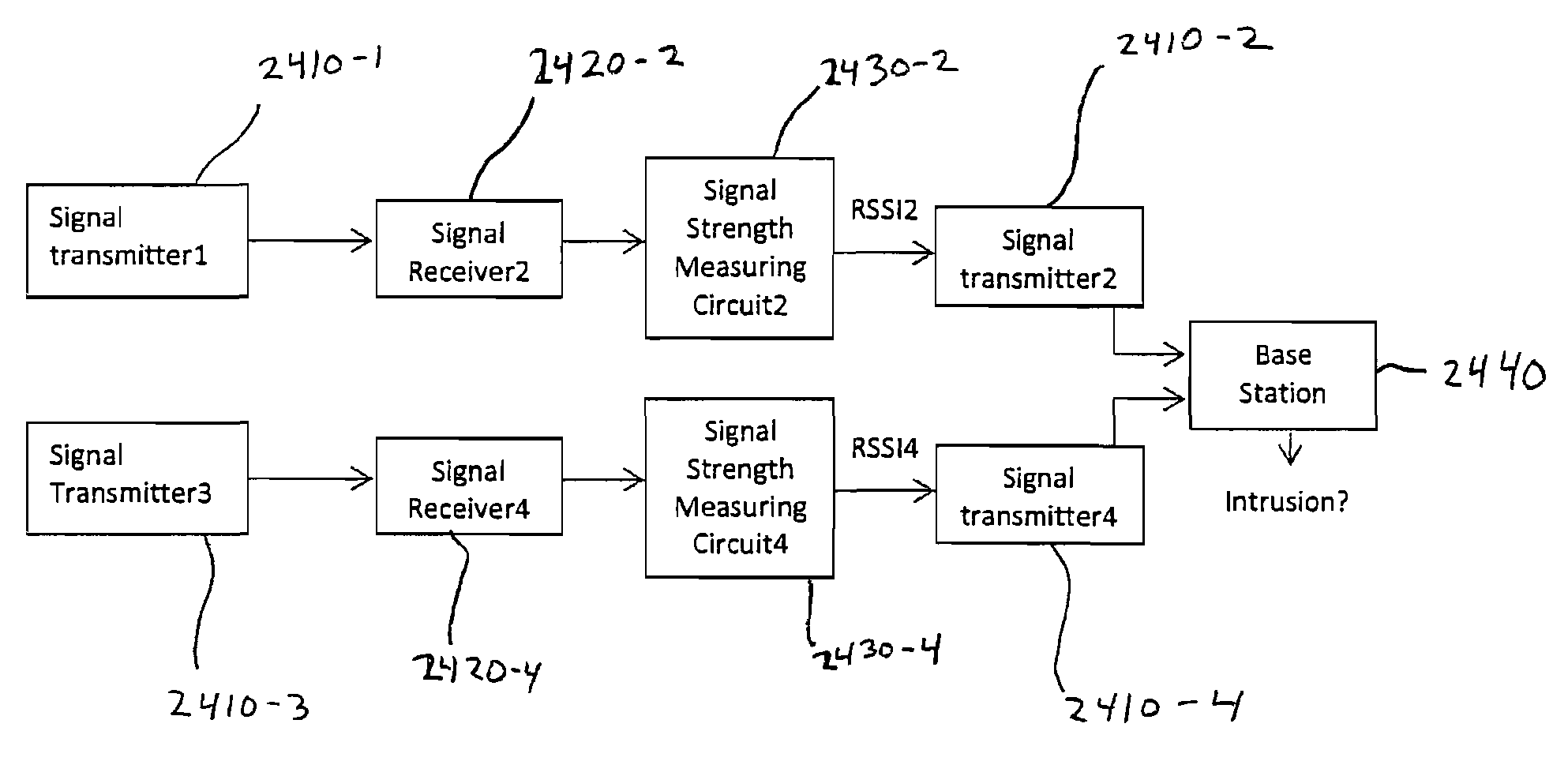
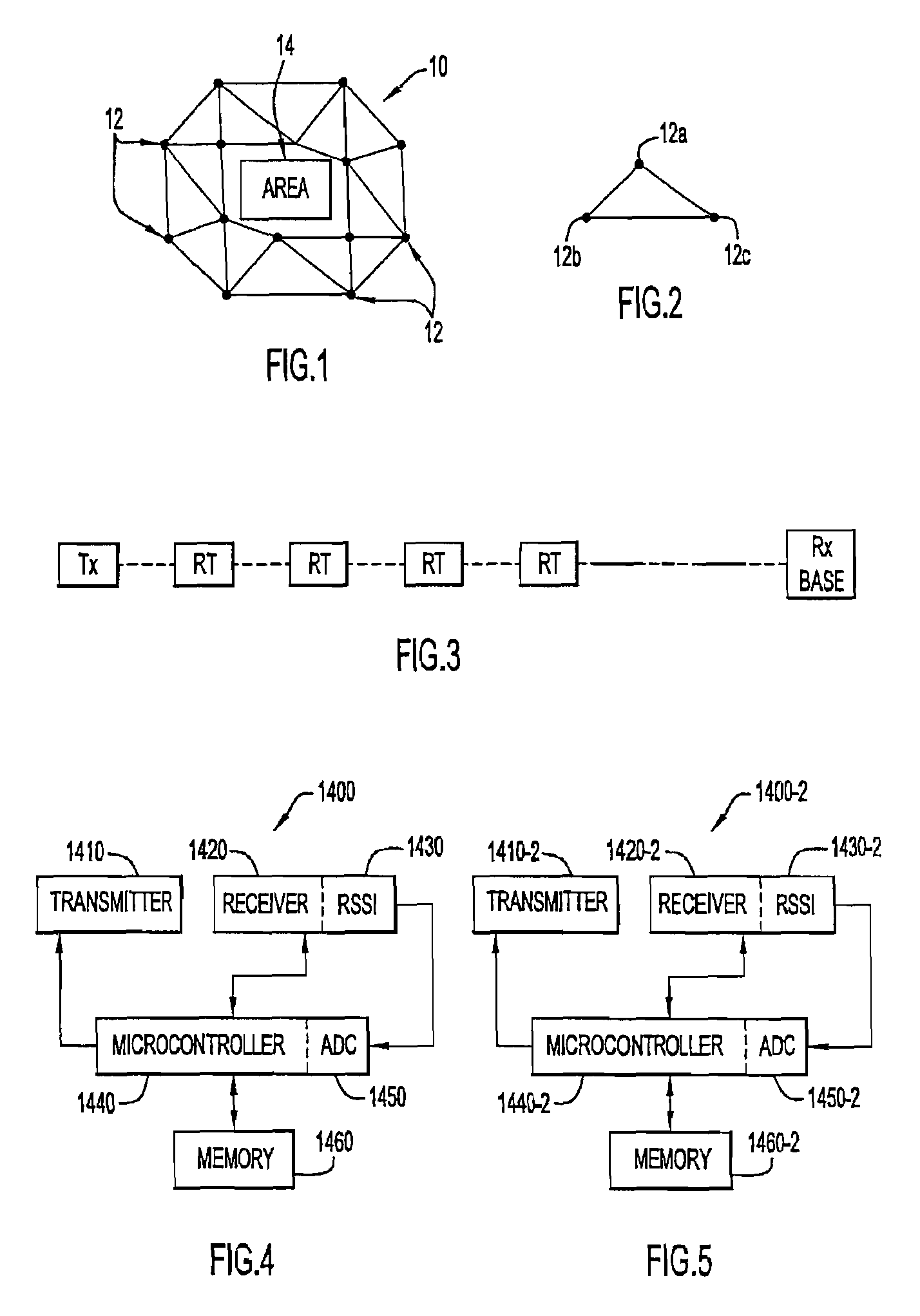
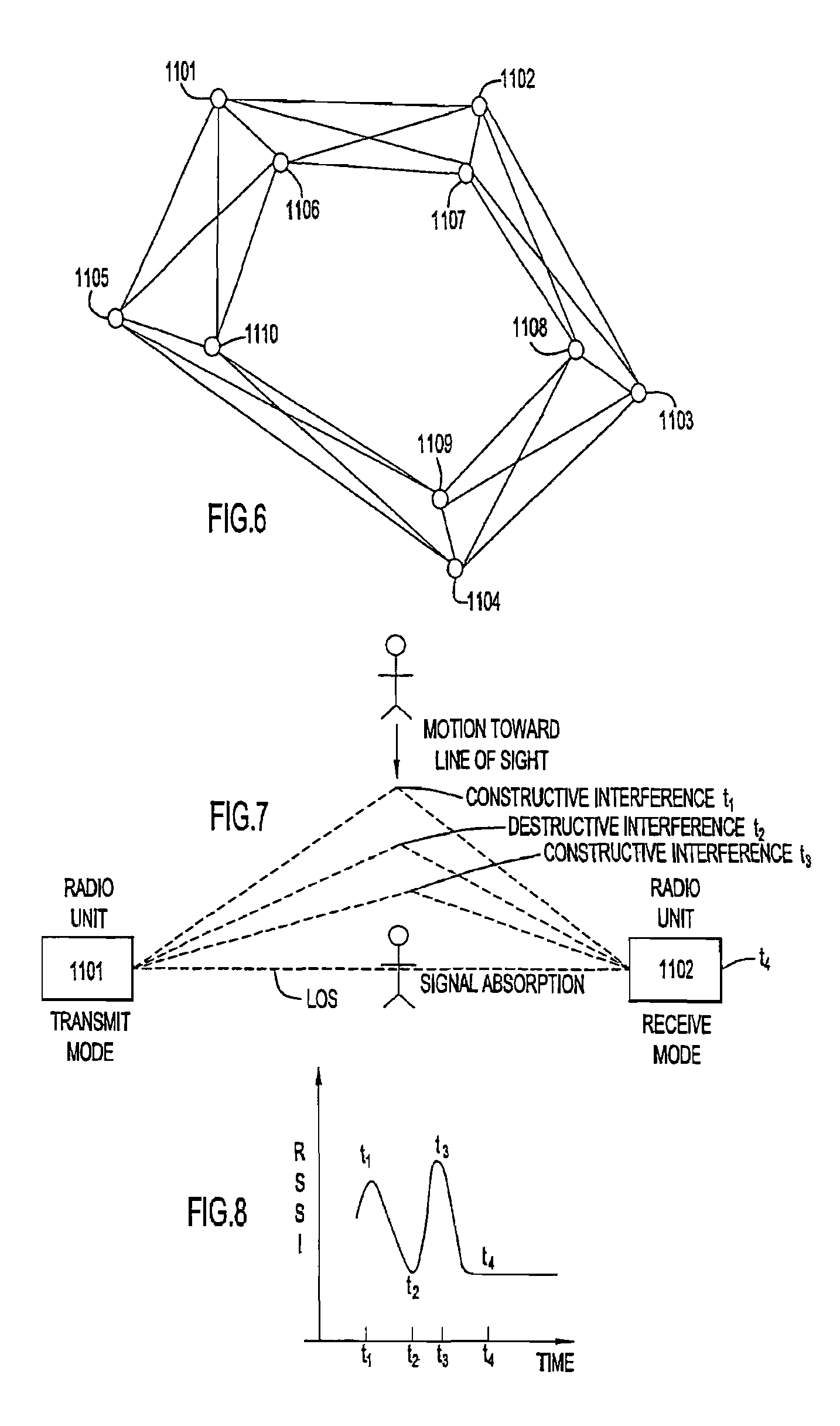
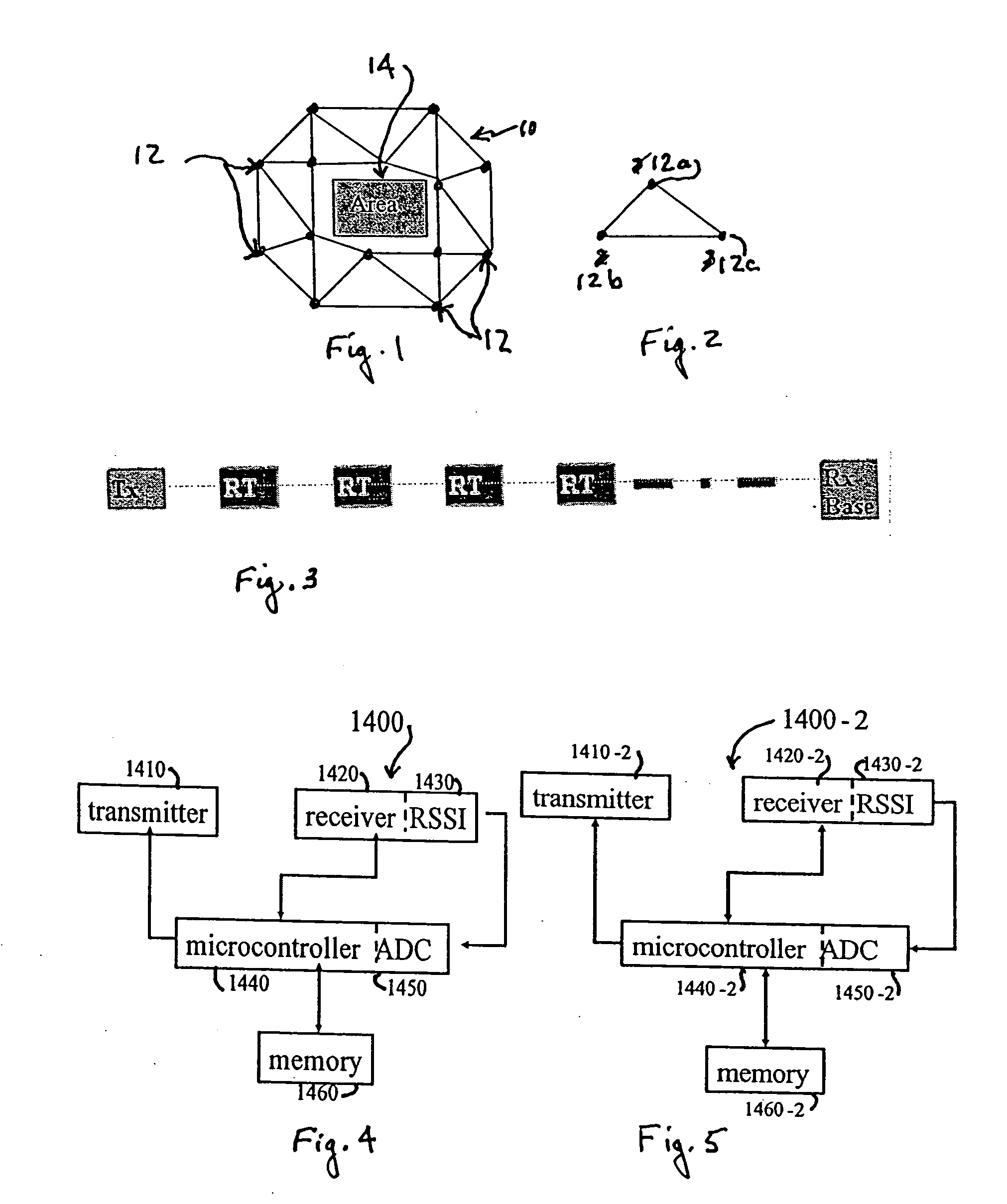
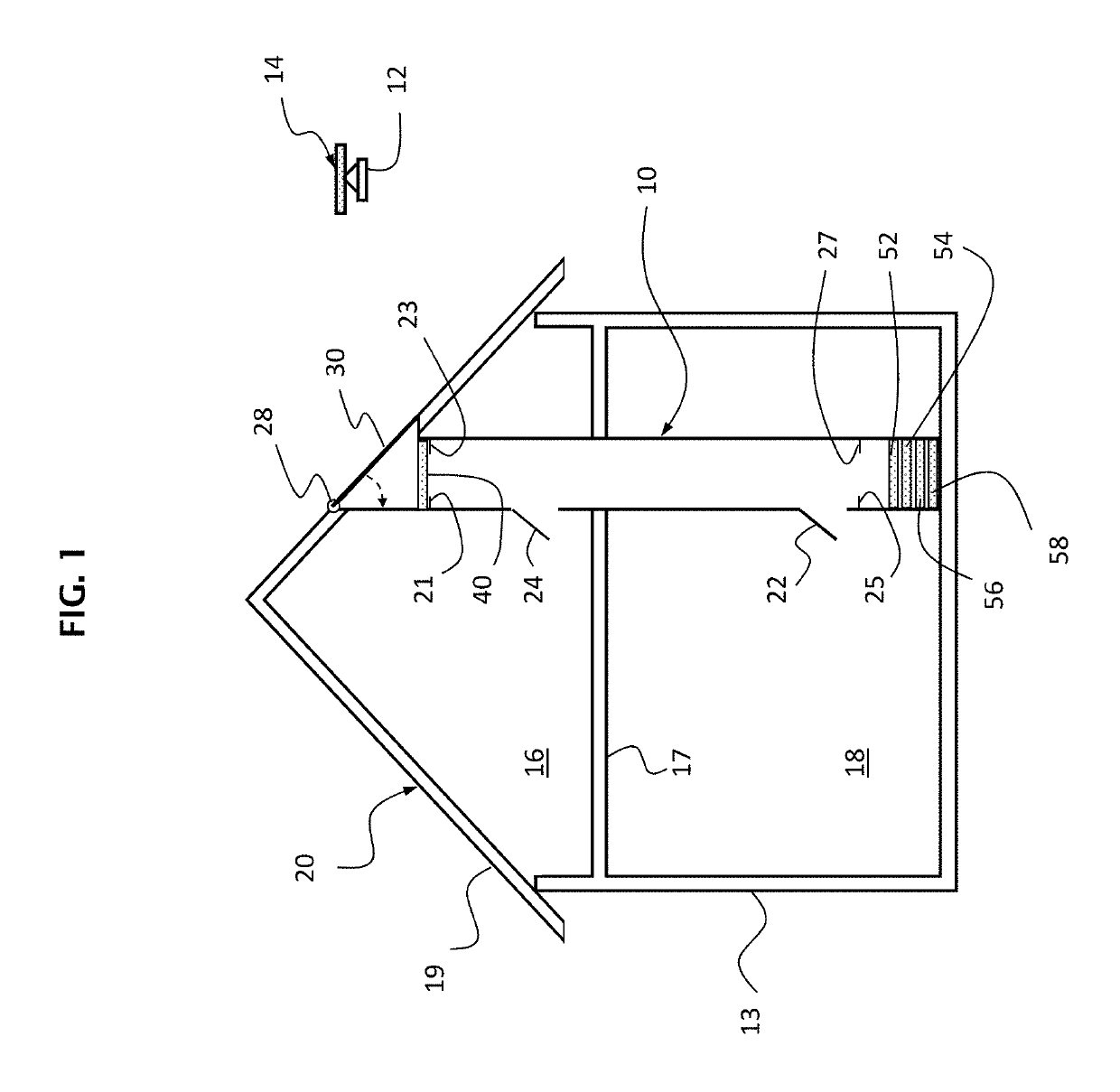
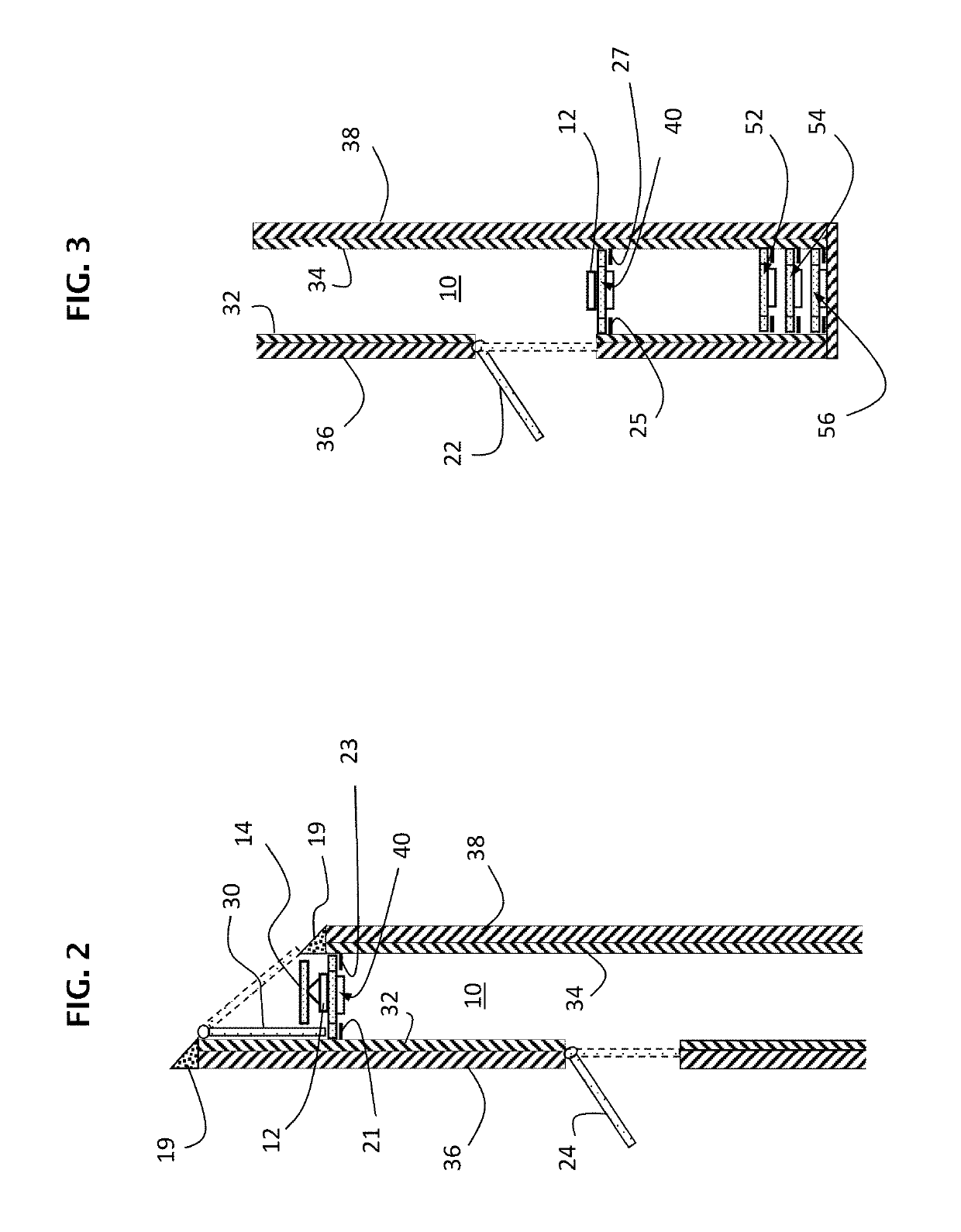
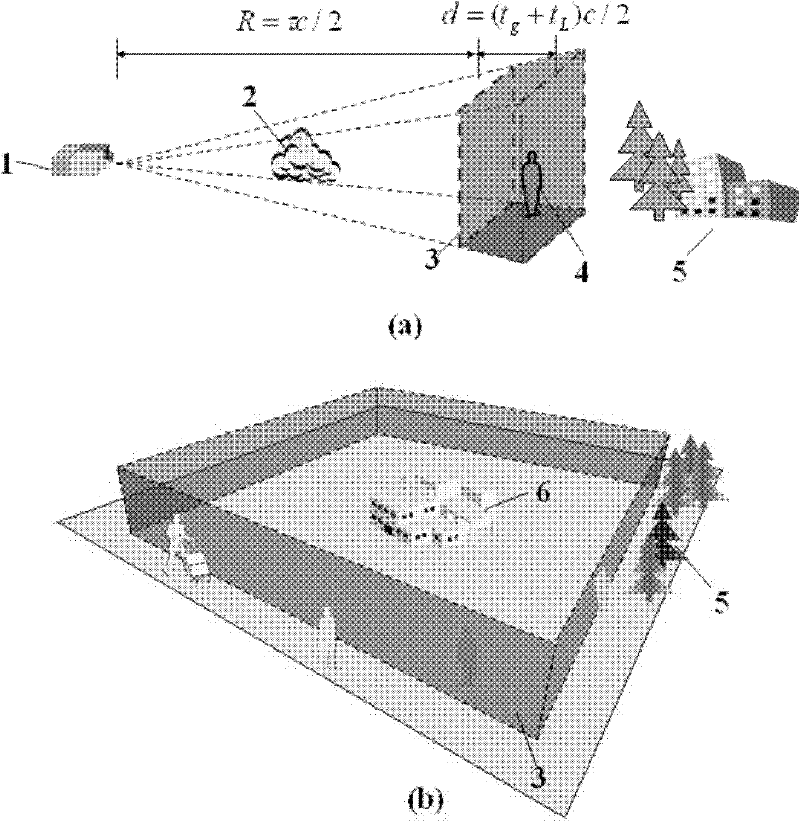
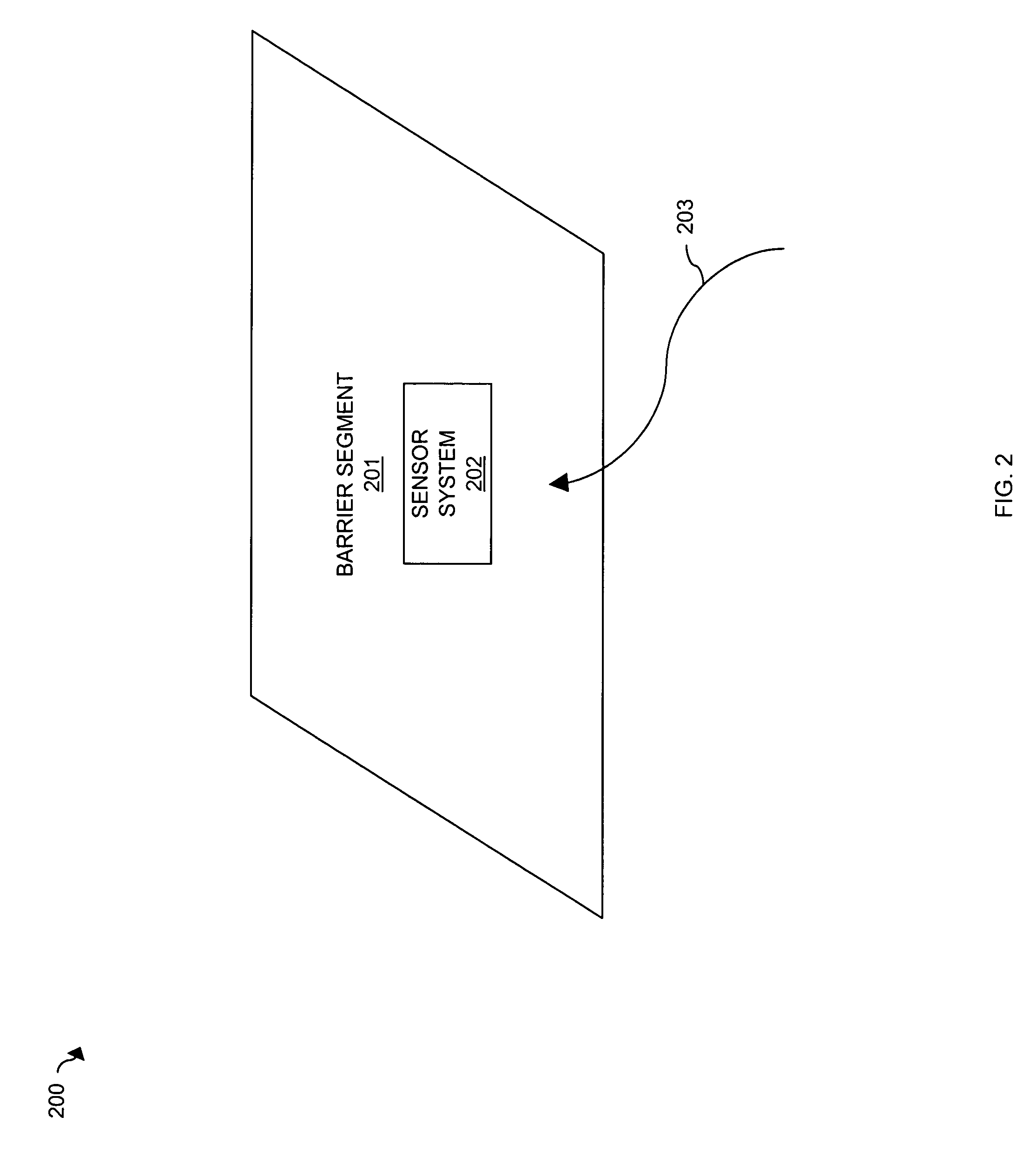
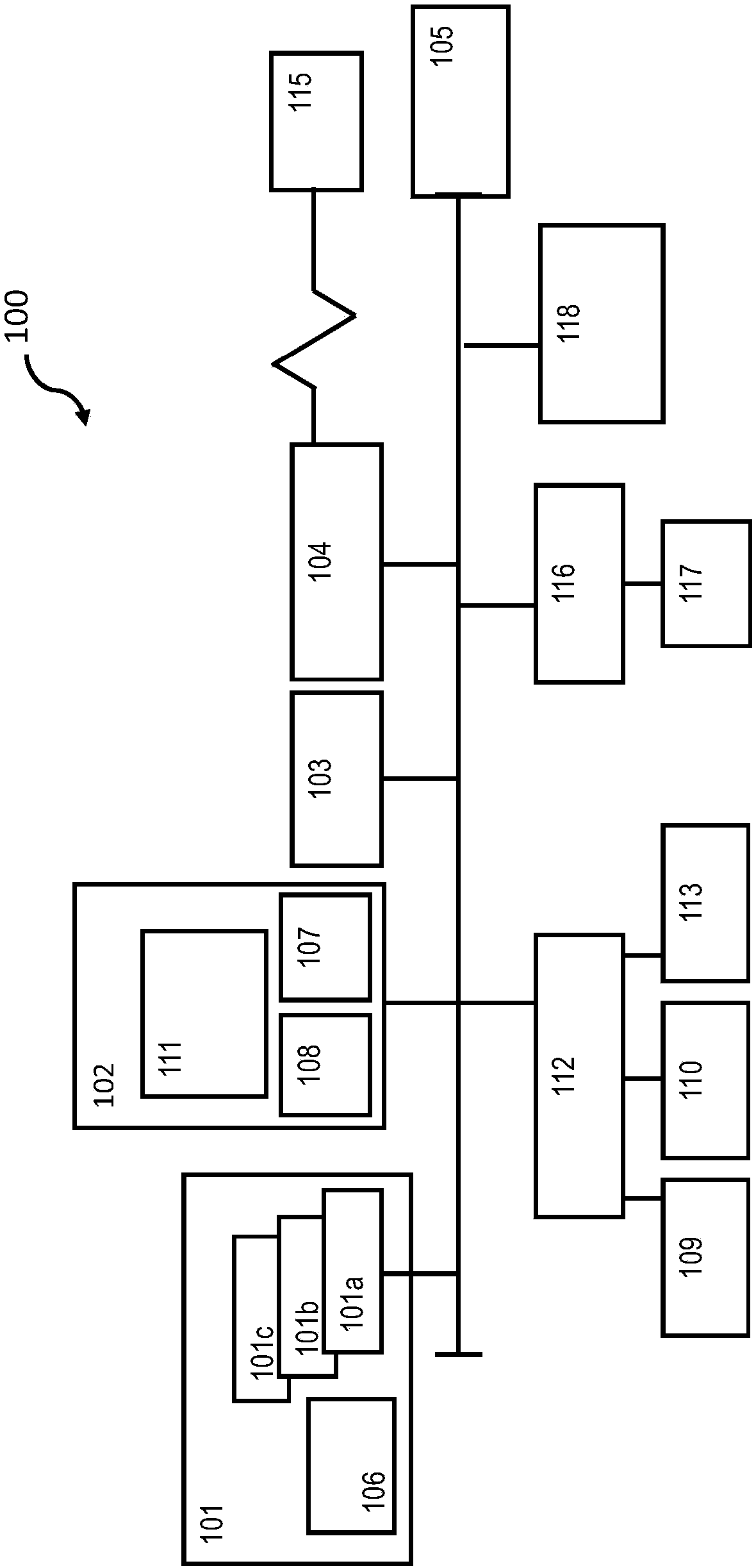
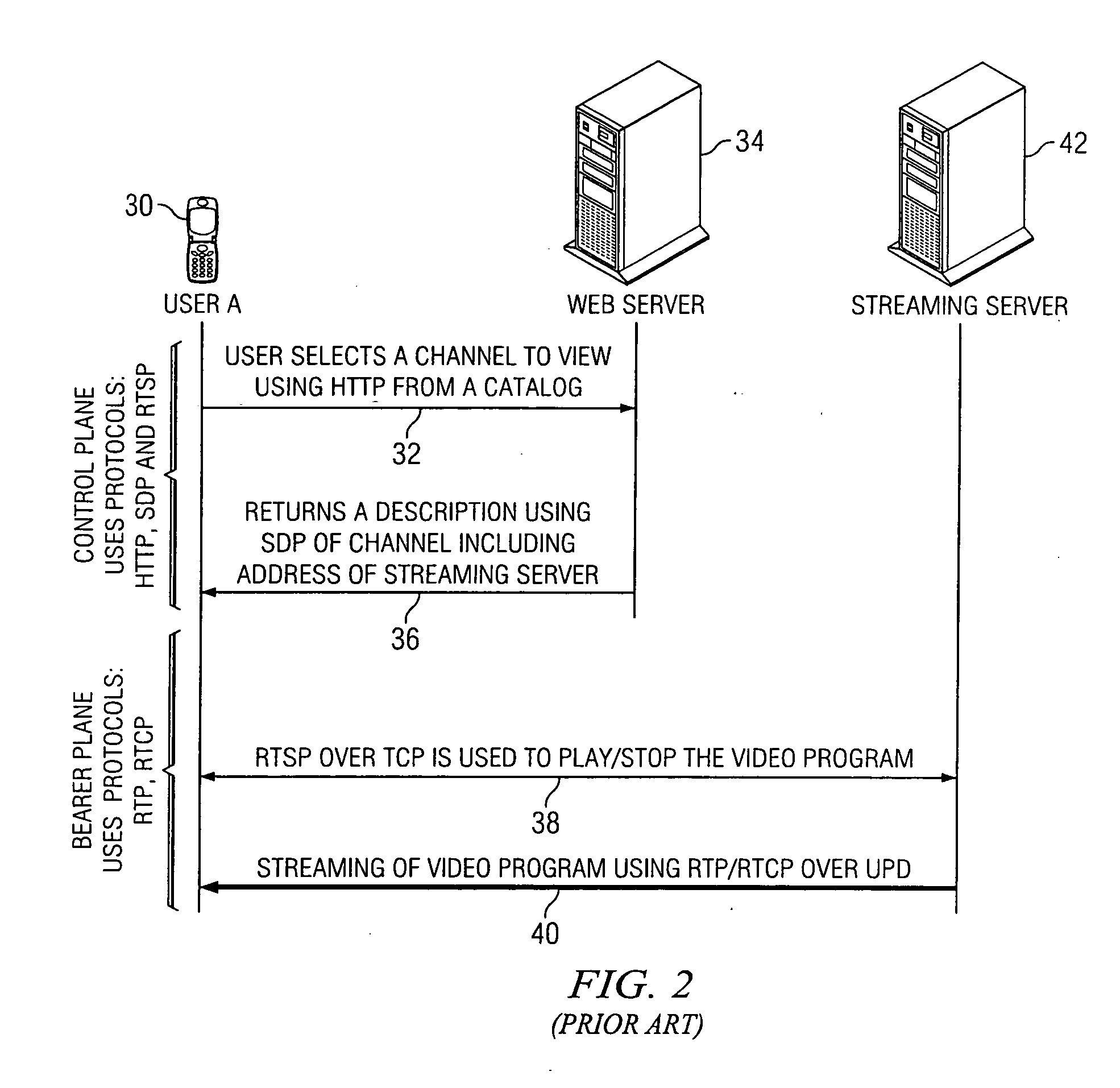
Perimeter security system
ActiveUS8456304B2Burglar alarm electric actuationRadio wave reradiation/reflectionEngineeringSignal strength
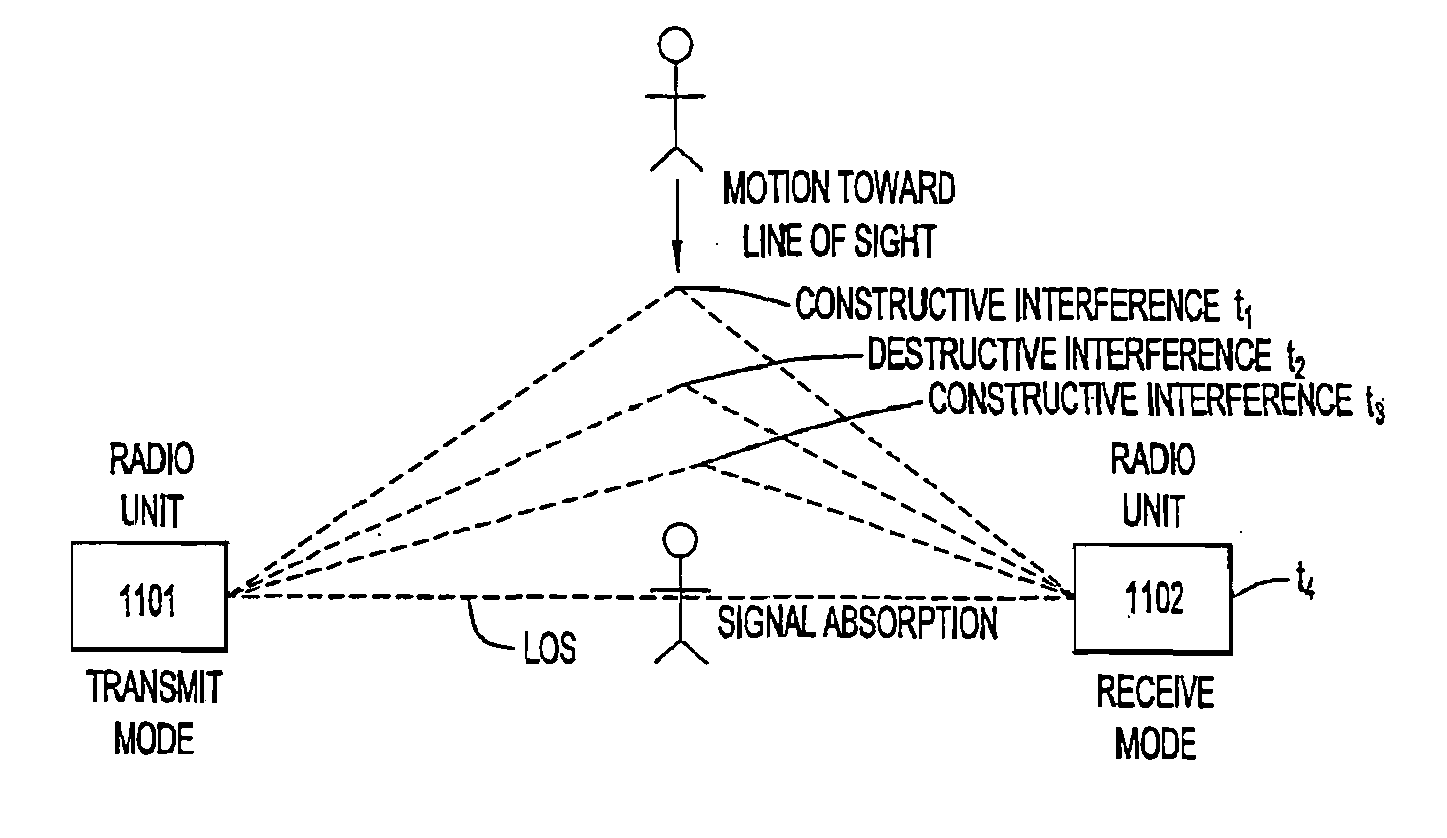
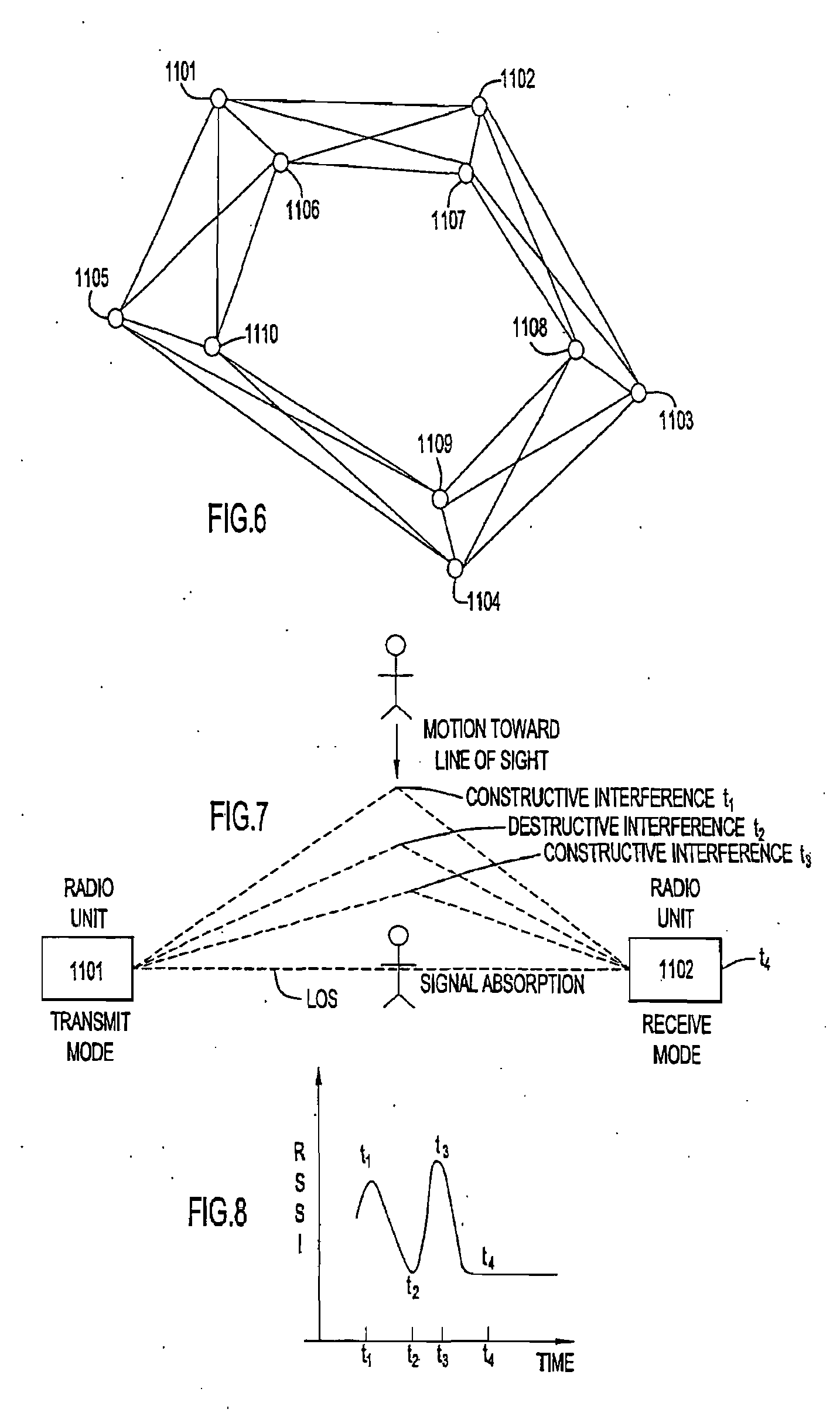
A security system for detecting physical intrusion in a monitored area including a plurality of radio units arranged in a network around the monitored area to determine received signal strength and pass variations thereof through the radio units to a base station.
Owner:INTELLIGENT AUTOMATION LLC
Perimeter security system
InactiveUS20080018464A1Radio wave reradiation/reflectionBurglar alarm short radiation actuationUltimate tensile strengthSecurity system
A security system for detecting physical intrusion in a monitored area including a plurality of radio units arranged in a network around the monitored area to determine received signal strength and pass variations thereof through the radio units to a base station.
Owner:INTELLIGENT AUTOMATION
Method and apparatus using polarisation optical time domain reflectometry for security applications
InactiveUS7173690B2Detection of fluid at leakage pointWave based measurement systemsPolarizerRayleigh backscattering
A preferred apparatus and method is presented in which a distributed fiber optic sensor is used in order to detect a disturbance along its length. A pulse of polarized light is launched into an optical fiber; as the pulse propagates along the optical fiber, it continuously loses a small portion of its energy due to Rayleigh backscatter. The Rayleigh backscattered light is analyzed using a polarization sensitive element such as a fiber polarizer. The dynamics of the time dependence of the polarization analyzed backscattered light is used to ascertain if there has been a disturbance along the length of the optical fiber. This technique can be used for applications in areas such as fiber optic telecommunications, perimeter security, fire detection, and pipelines.
Owner:SENSTAR CORP
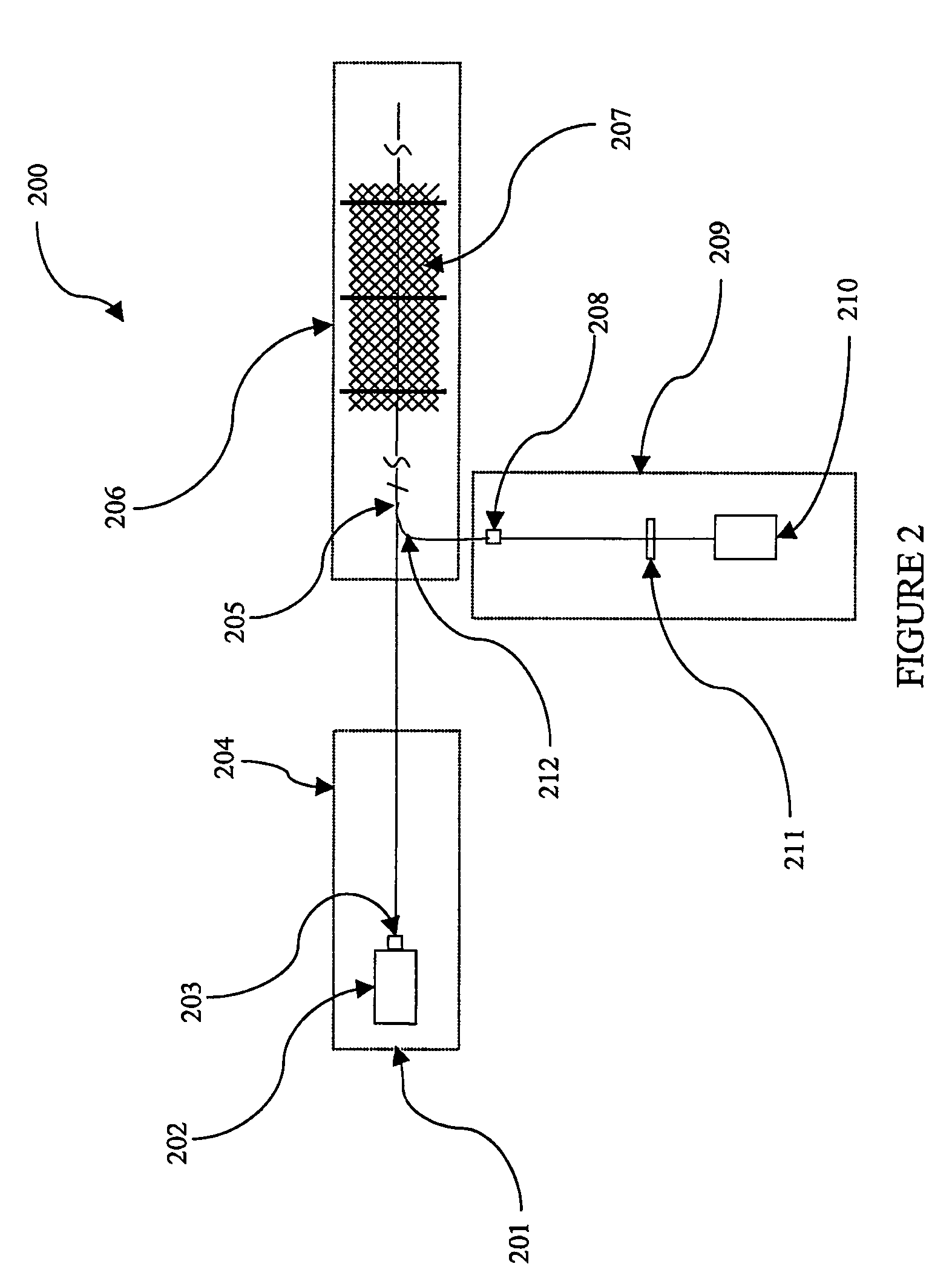
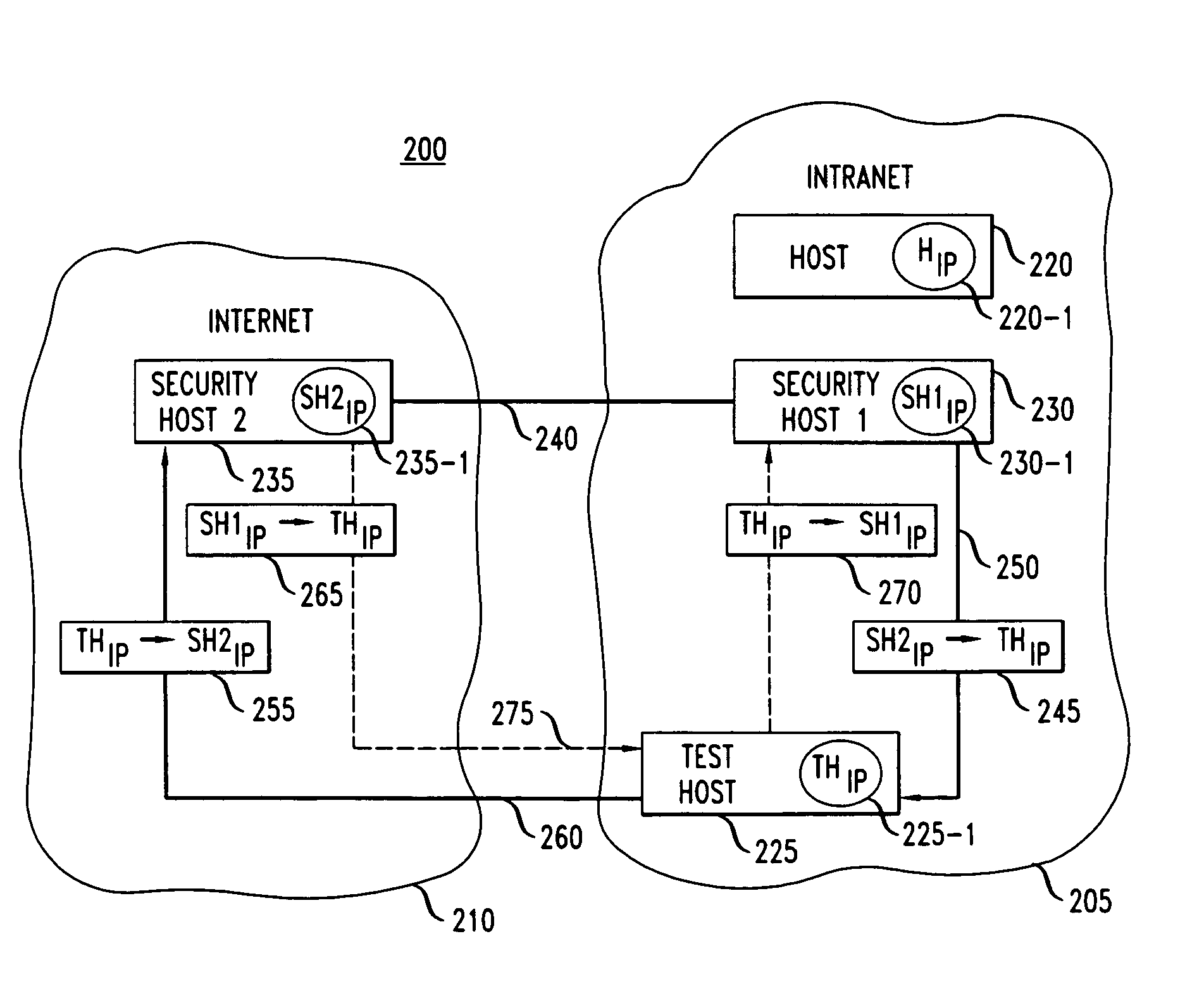
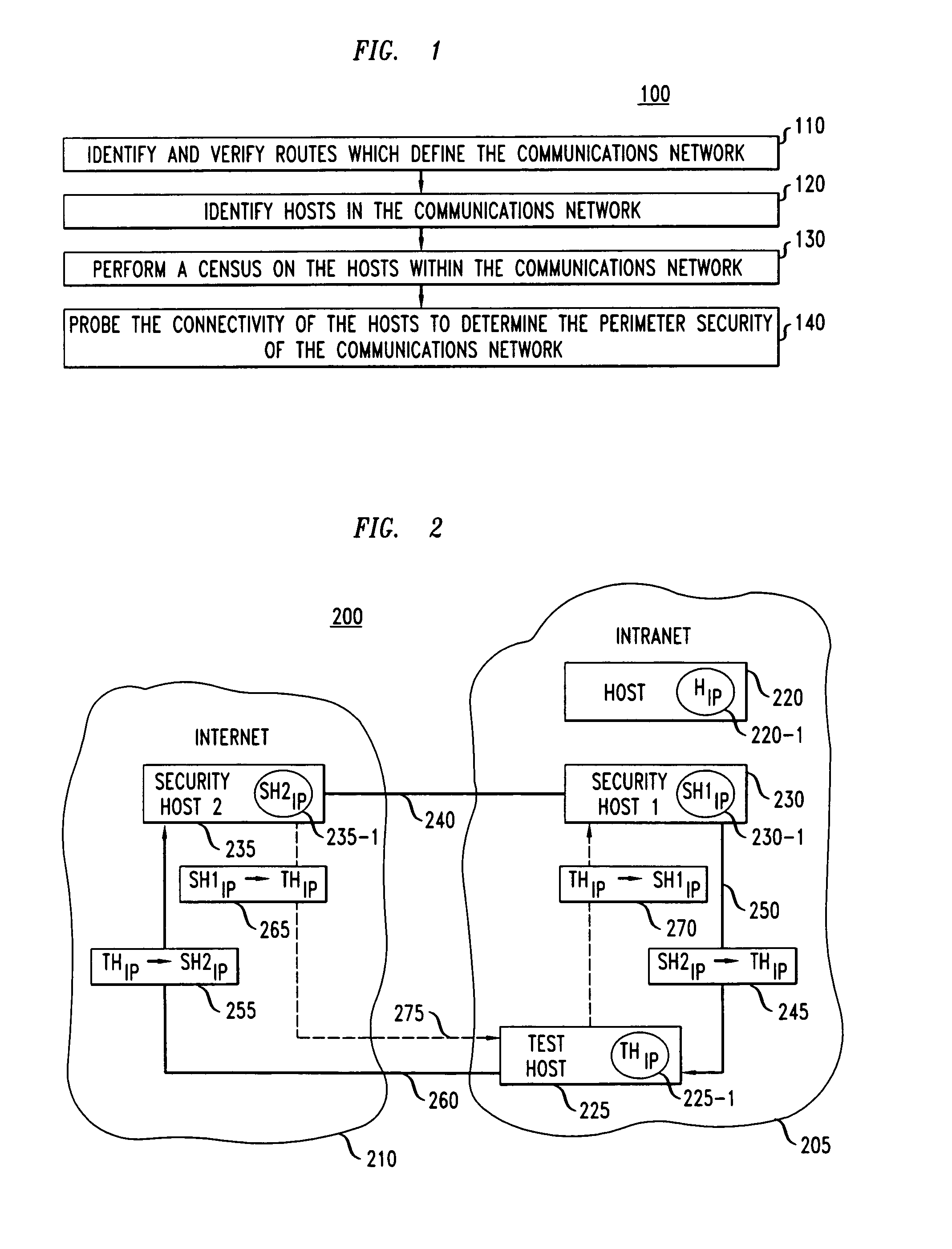
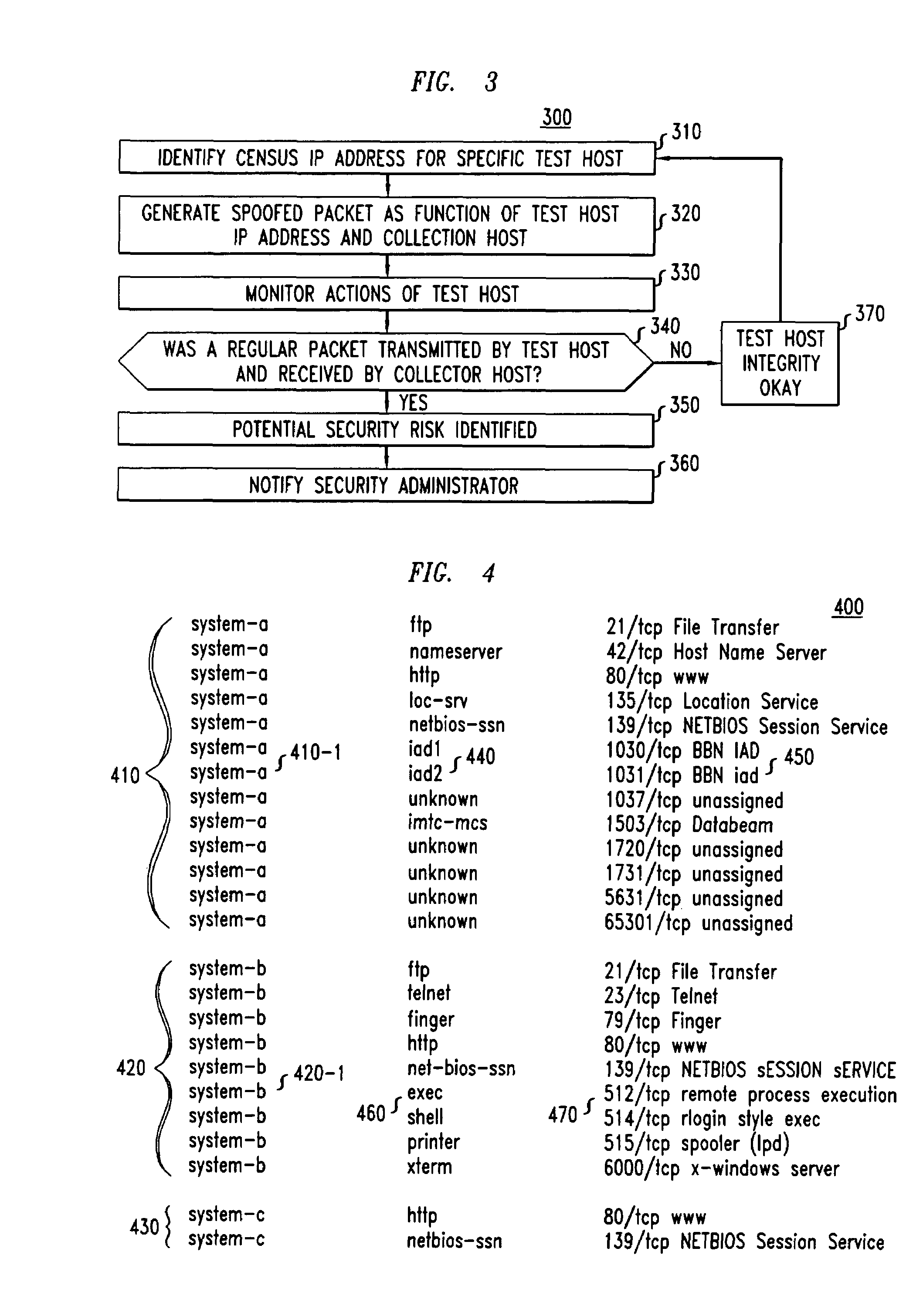
Method and apparatus for host probing
InactiveUS7299489B1Data taking preventionDigital data processing detailsEngineeringDistributed computing
A method and apparatus for analyzing the perimeter security of communications networks. More particularly, information is identified which defines a particular communications network, e.g., an intranet, and identifying the connected hosts thereto. Utilizing such information, a determination is made with respect to identifying the routes that define the network. Utilizing the routing information, the connectivity of the hosts within the network, e.g., an intranet, is probed to ascertain the integrity of the network and thereby identifying potential security risks across the perimeter defense of the network.
Owner:RPX CORP +1
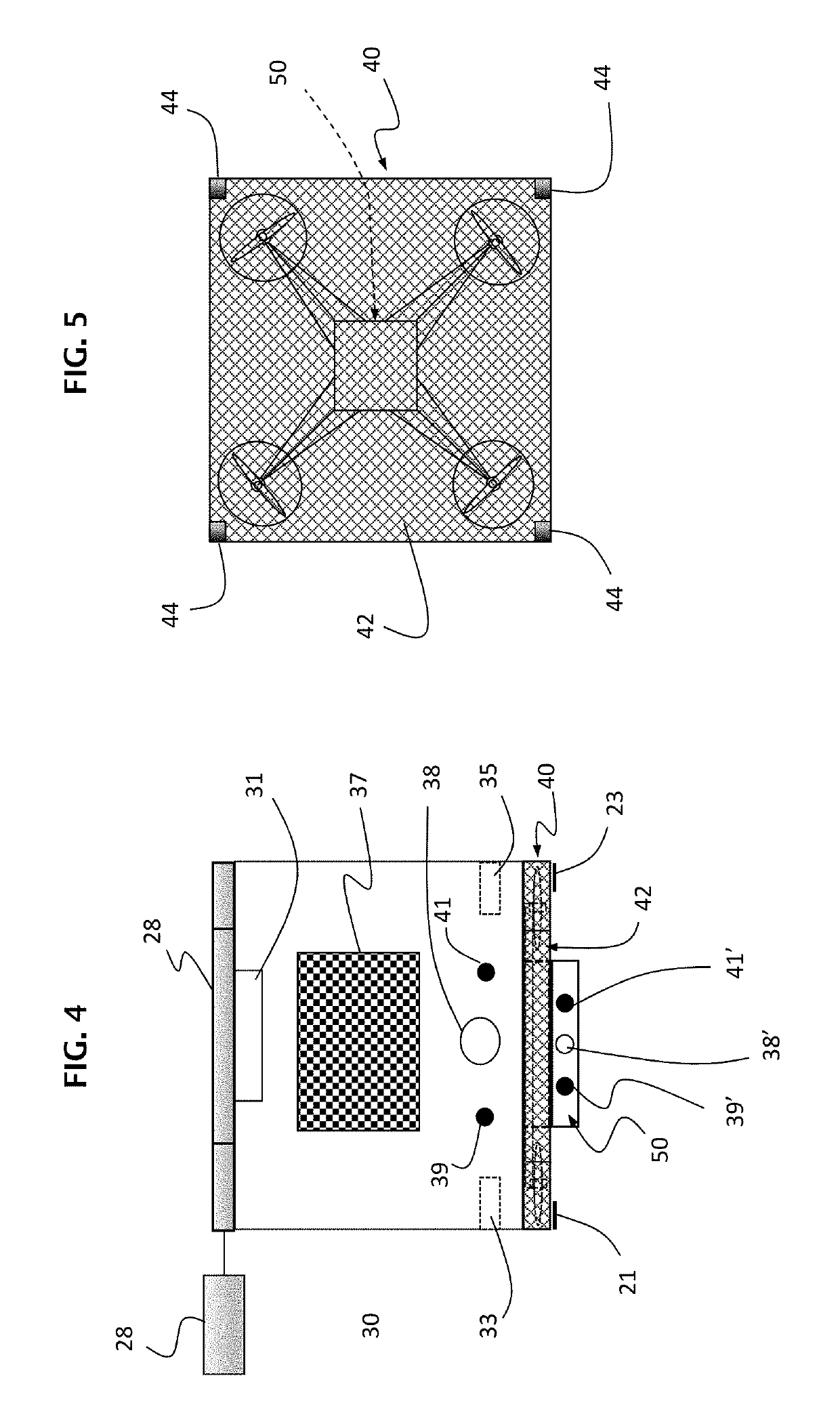
Autonomous drone based package reception and surveillance system
ActiveUS10351261B1Provide securityUnmanned aerial vehiclesCoin-freed apparatus detailsTransceiverWireless transceiver
A system and method for autonomous drone-based package reception and surveillance of the present invention. In accordance with the inventive method, an at least partially enclosed chute is provided with dimensions sufficient to receive packages. A platform is mounted within the chute to receiving the packages. A mechanism is provided to move the platform from a first position within the chute to receive the packages to a second position within the chute to deliver the packages. In the best mode, the platform is a second drone. Multiple drones, equipped with wireless transceivers, cameras, lasers, lights, detectors and even weapons are networked to provide perimeter security. The chute includes a door secured with a wireless latch activated by a system controller. One or more identification symbols, such as QR codes, bar codes, symbols etc. are provided on the door to be read by the airborne delivery vehicle. Nodes are included for charging the airborne delivery vehicle and the site-based drones as well. The deployment of the nodes within the chute is controlled by the site-based drones. An optional scale is provided in the platform for weighing package upon delivery. The system is adapted for operation via a smartphone.
Owner:BRYANT CAROLYN
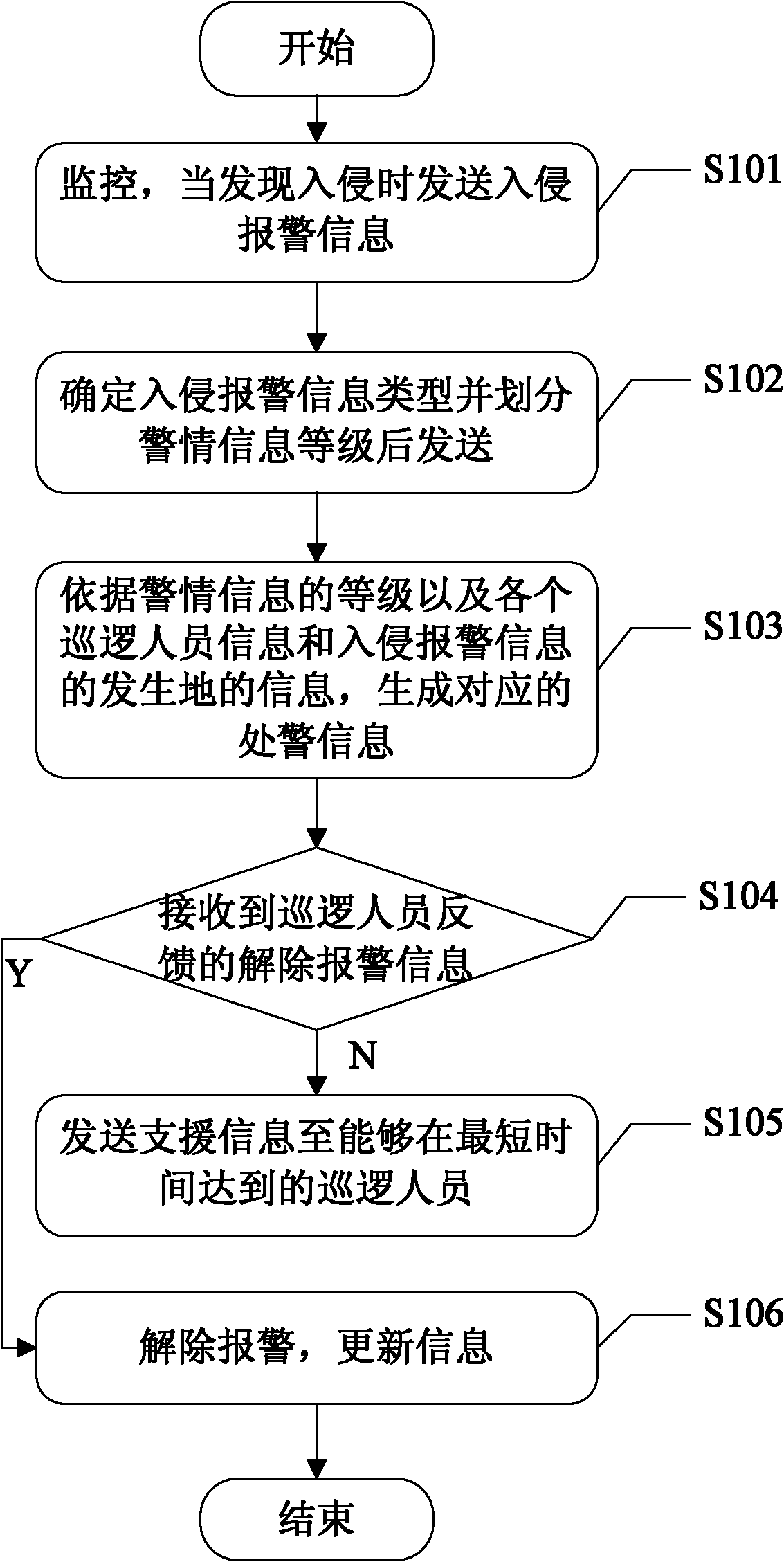
Perimeter security police method and system
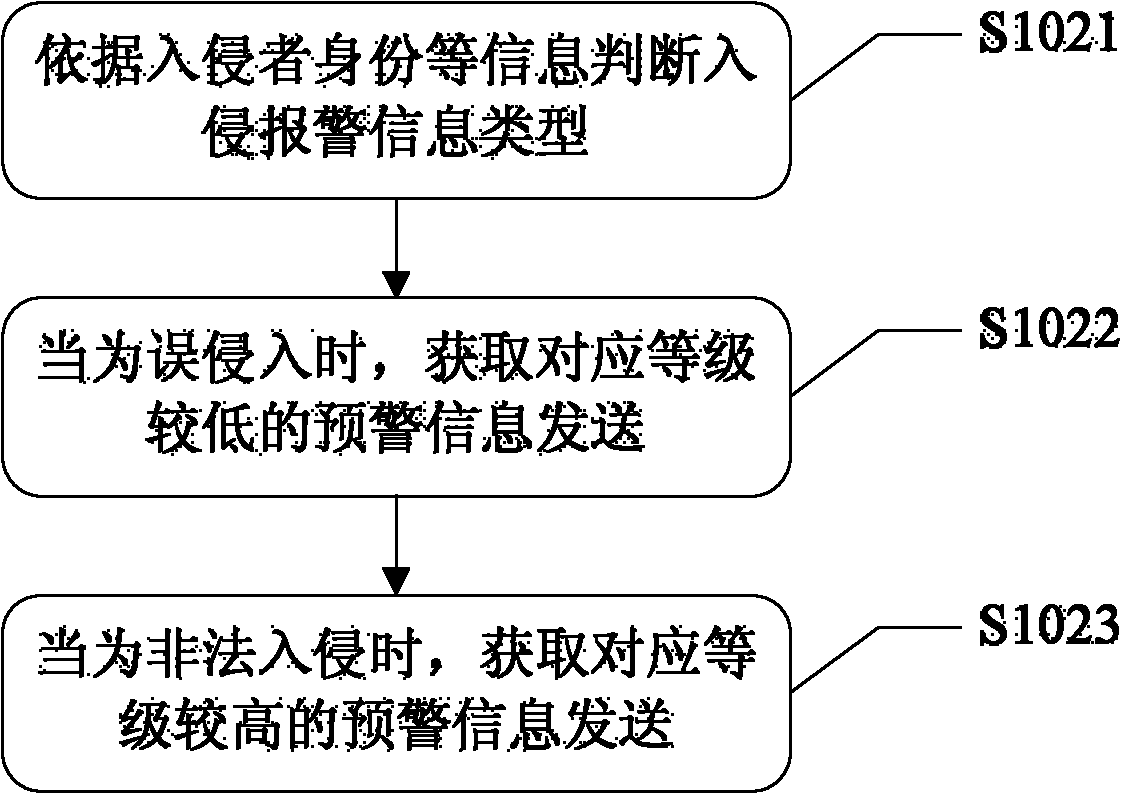
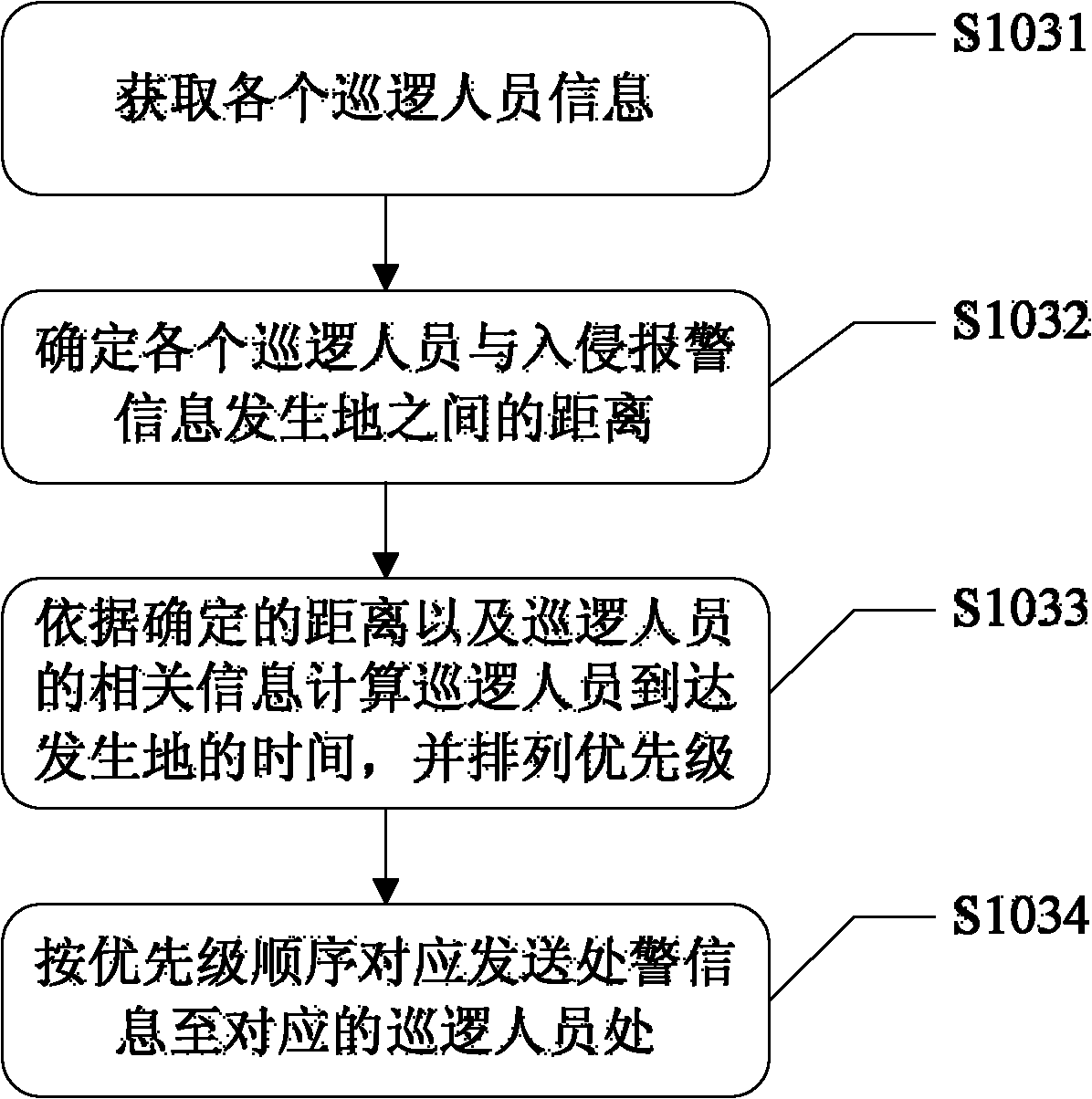
ActiveCN102280011AImprove mobilityIncrease flexibilityBurglar alarmReal-time computingPerimeter Security
The invention discloses a boundary safeguard alarm disposing method and a system therefor. The method comprises the steps as follows: a primary console receives the invasive alarm information within a preset boundary scope sent by a monitoring device, and determines the type of the invasive alarm information and classifies the level of the alarm information; a night watching device generates corresponding alarm disposing information for alarm disposing, according to the level of the alarm information, and the realtimely acquired information of each patrol worker and the address information ofthe occurring place of the invasive alarm information; and when the night watching device receives the alarm canceling information fed back by the patrol workers in the first time period, the alarm is cancelled, and the information of the patrol workers is updated. By realtimely positioning the patrol workers, after alarm disposing needing information is received, the realtime information of the patrol workers is combined with safeguard related information, patrol workers needed for alarm disposing are determined, rapid and accurate linkage monitoring is realized, and the airport safeguard efficiency is improved.
Owner:峰润技术无锡有限公司
Deflection sensing system
The system incorporates wire deflection, taut wire detection for perimeter security applications. Generally, the system of the invention provides intrusion detection by an internal mechanism. The internal mechanism can detect wire deflection in any direction. In turn, given a sufficient amount of wire deflection, a security system is signaled. However, the force required to sufficiently deflect the wires is high enough so as to minimize nuisance alarms. The internal mechanism is generally held within a structure so that it is protected from tampering. As such, the internal mechanism is also kept separate from the wire array so that it is protected from attempts by an intruder to isolate the wire array.
Owner:ZAREBA SECURITY
Method for detecting moving target based on millimeter wave radar and video data fusion
InactiveCN109920185ASolve urgent problems that cannot be displayed visuallyImprove accuracyBurglar alarmRadio wave reradiation/reflectionCombined useComputer vision
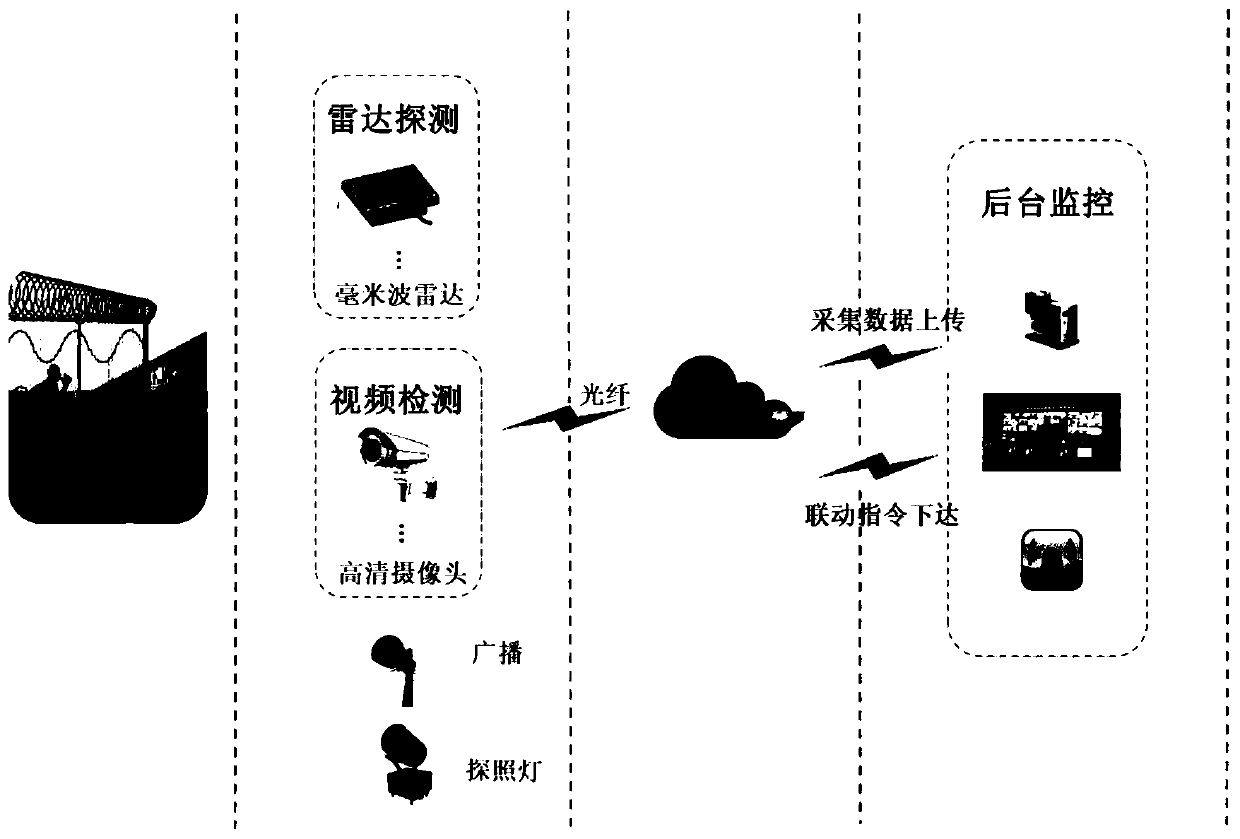
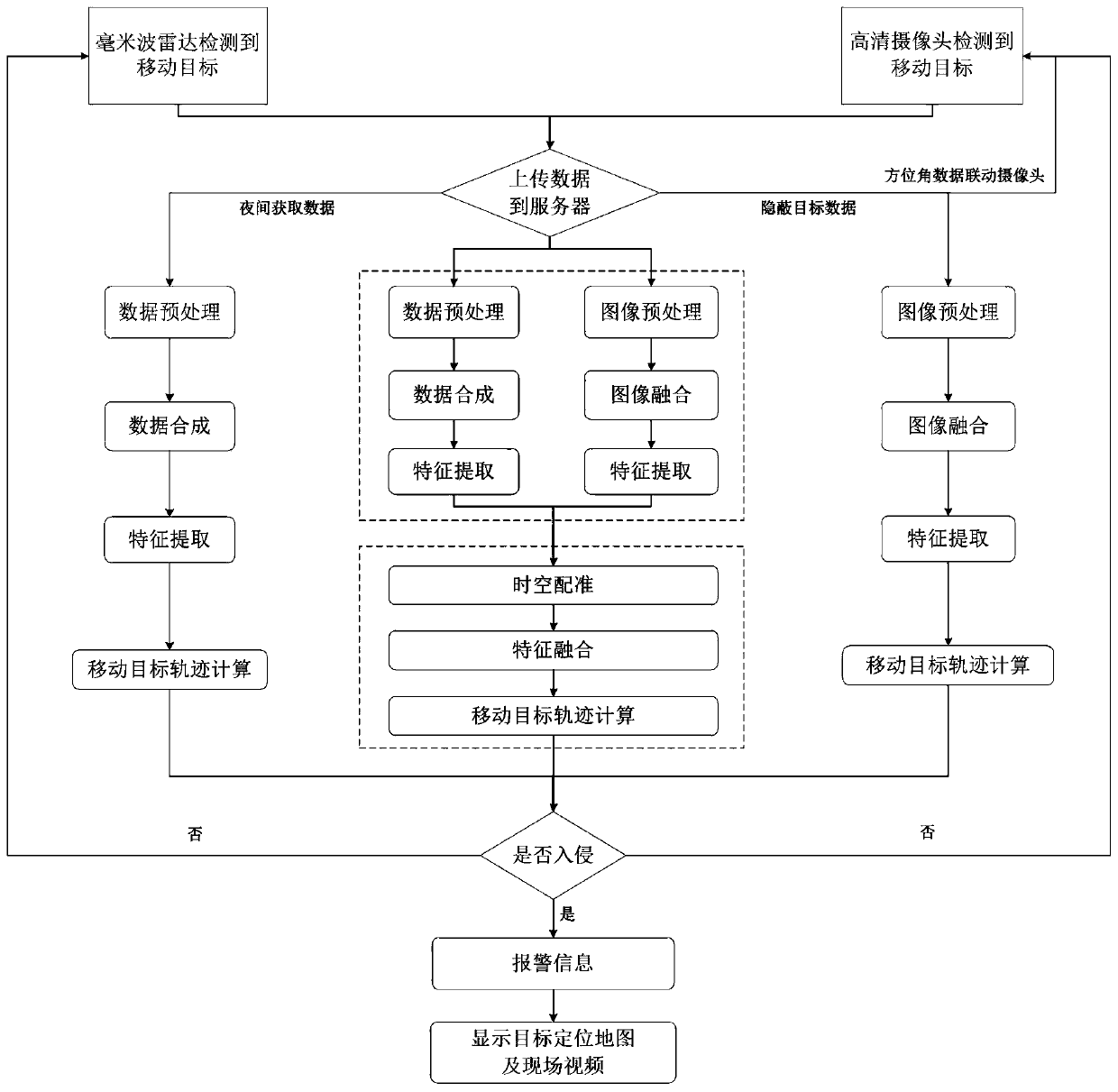
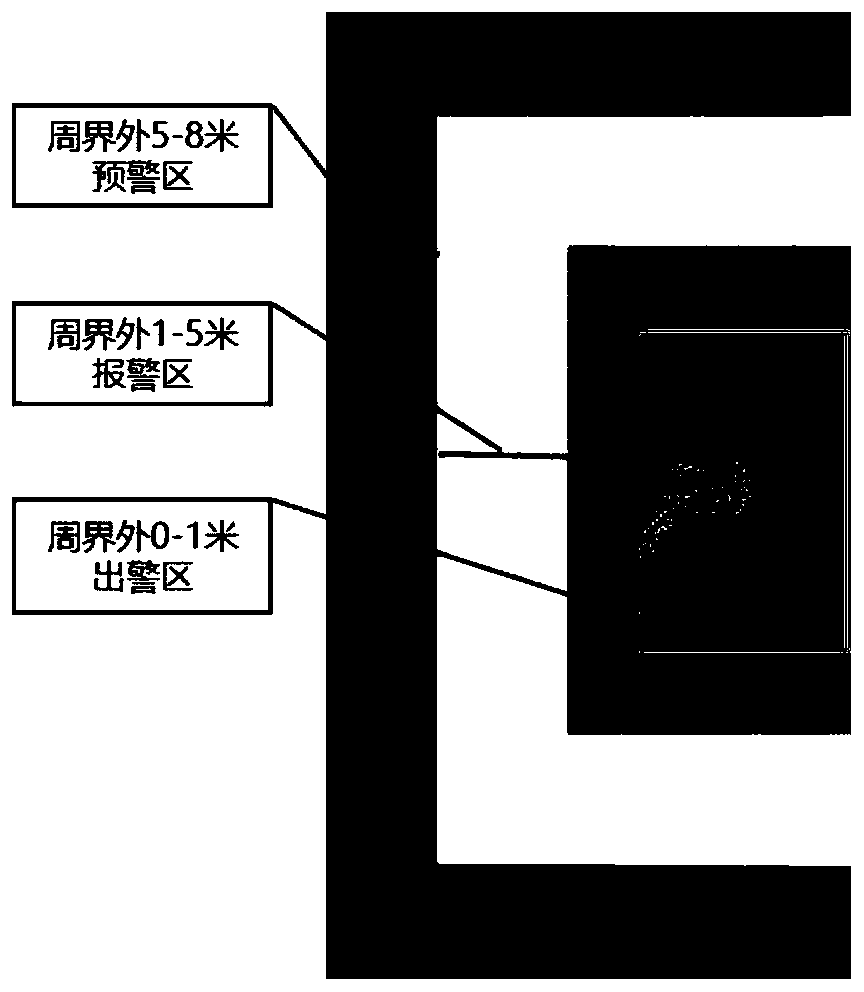
The invention discloses a method for detecting a moving target based on millimeter wave radar and video data fusion, which comprises steps of performing all-weather perimeter intruded target detectionby using a high-definition camera and a millimeter wave radar, and uploading the data acquired by the high-definition camera and the millimeter wave radar to a server in real time; then performing deep recognition based on an algorithm to detect an intruded target. By combining the millimeter wave radar and the high-definition camera, the method solves the problem that an existing perimeter security protection system has a low target recognition rate and poor adaptability to special environment, has high target detection accuracy and reliability, adapts to special environments such as cloud,rain and snow, reduces deployment and maintenance cost, and more importantly, solve the urgent problem that a current tracking target cannot be visualized.
Owner:ZHONGKE JIUDU BEIJING SPATIAL INFORMATION TECH
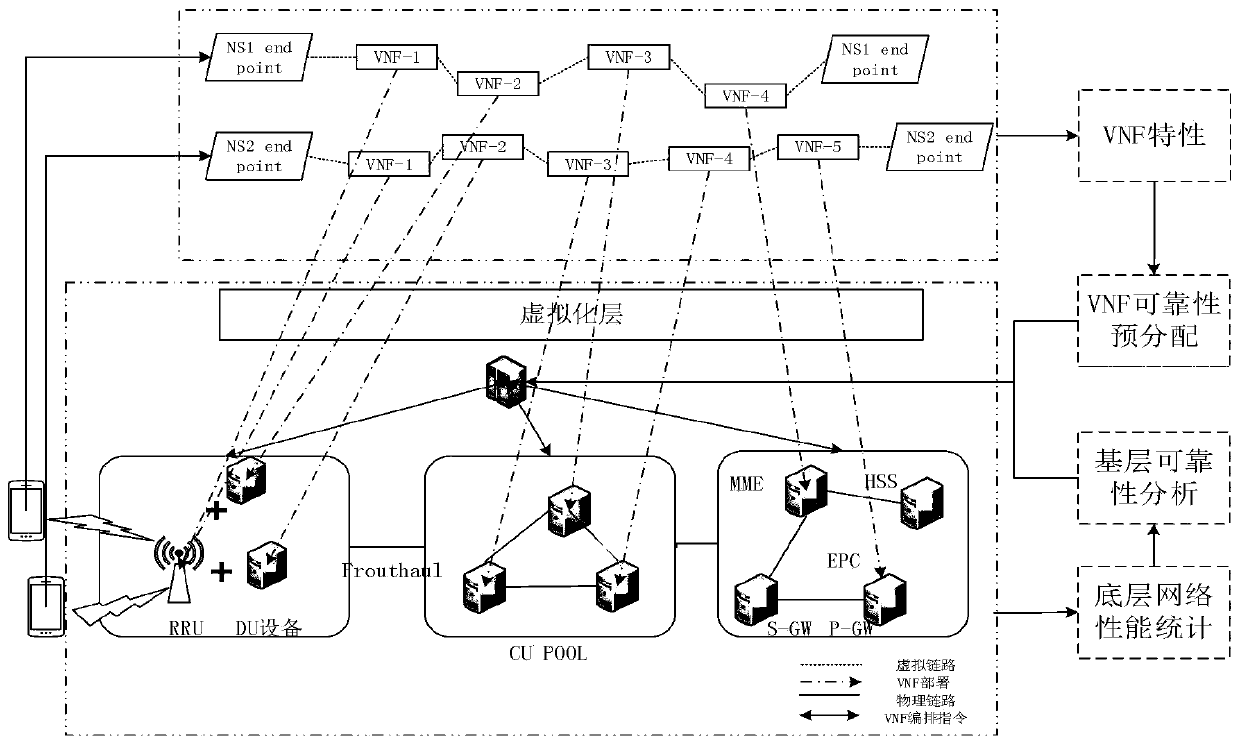
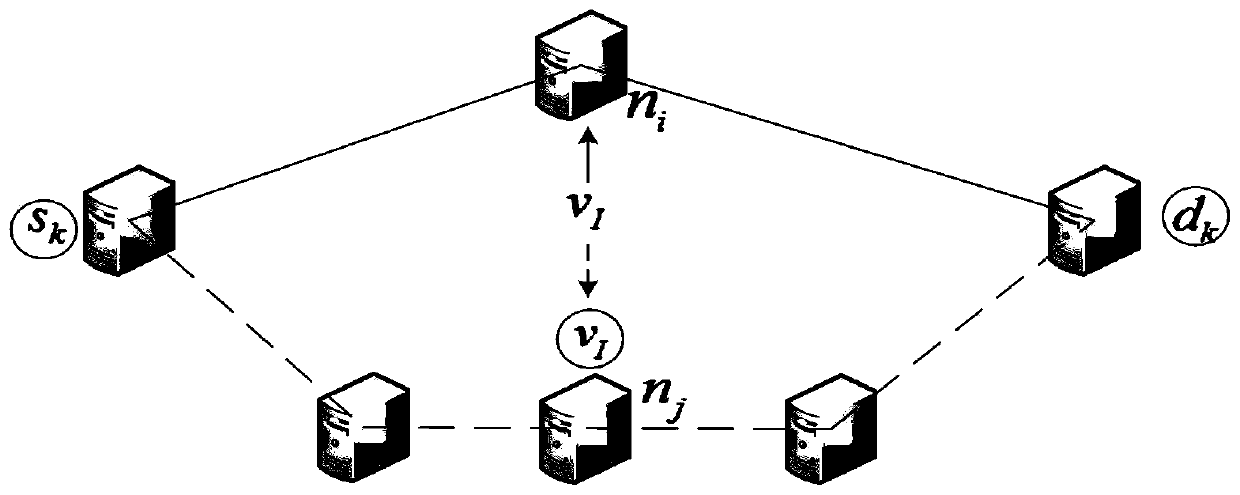
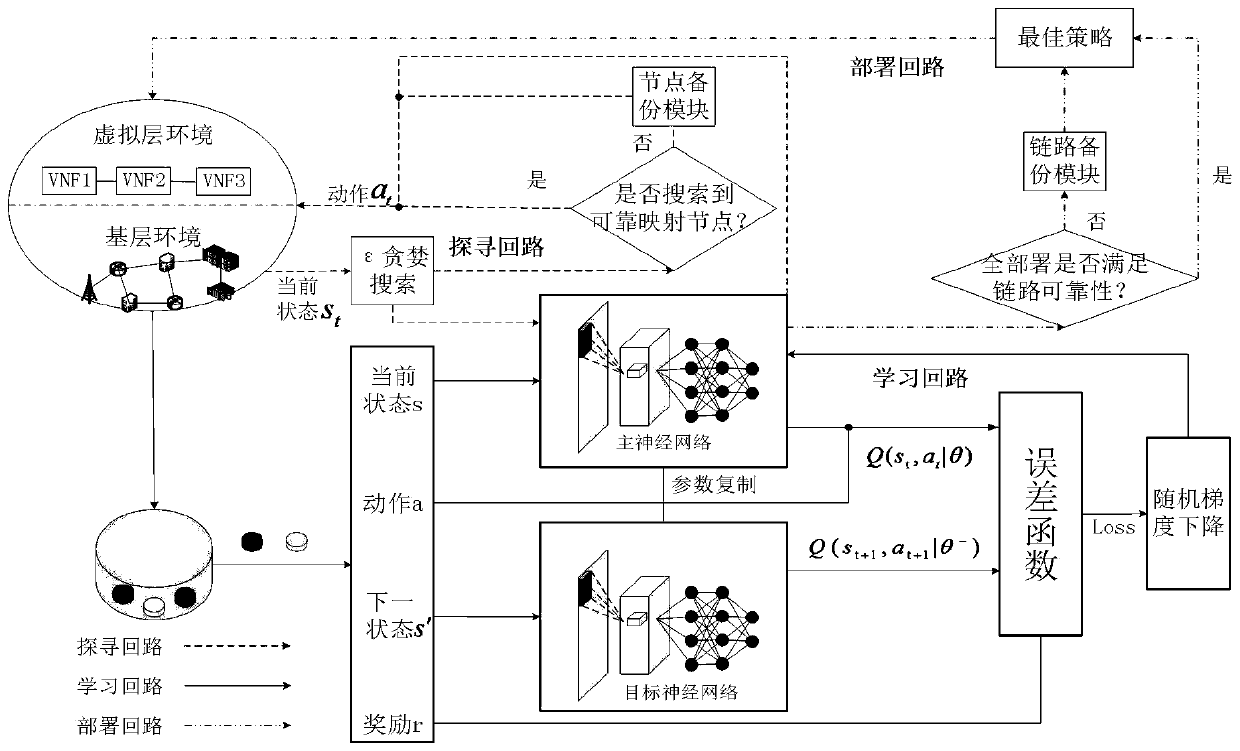
Service function chain reliable deployment method based on deep reinforcement learning
ActiveCN111147307AReduce consumption costImprove recovery rateError preventionData switching networksDependabilityReinforcement learning
The invention relates to a service function chain reliable deployment method based on deep reinforcement learning, and belongs to the technical field of communication. The method comprises the following steps: S1, obtaining a reliability value based on the reliability measurement mode of the equipment use degree and the peripheral safety coefficient; S2, preliminarily determining a reliability demand of each virtual network function through the functional characteristics and the topological characteristics; S3, obtaining the deployable length of the link reliability requirement meeting the virtual link reliability requirement; S4, searching an optimal mapping scheme suitable for the virtual network environment and the base environment by using deep reinforcement learning based on each reliability demand; and S5, if the VNF reliability cannot be satisfied in the mapping process, using an importance-based node backup method, and if the link deployment result does not satisfy the link reliability, using a link backup importance-based link backup method. The method can effectively deal with basic faults on the basis of ensuring reliability requirements, reduces the number of failure SFC, and ensures load balance to make the whole virtual network more stable and reliable.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
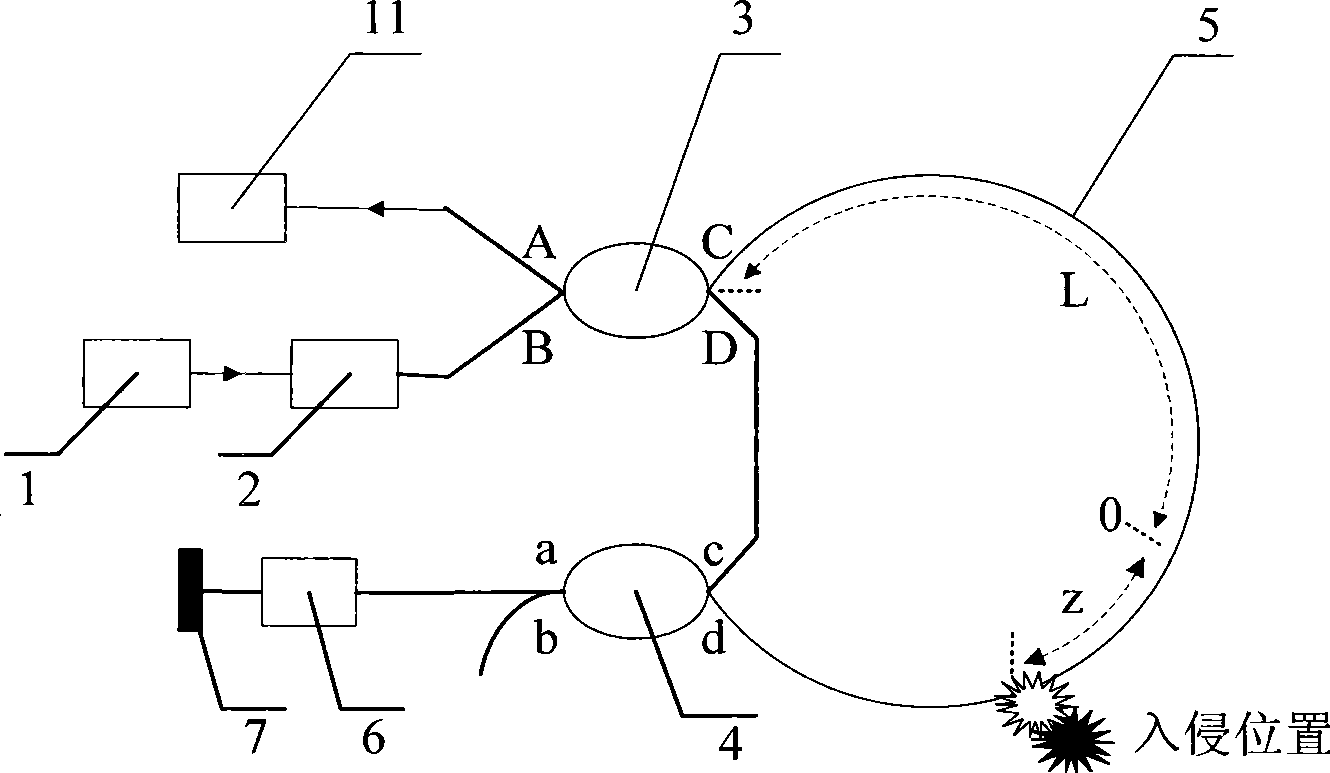
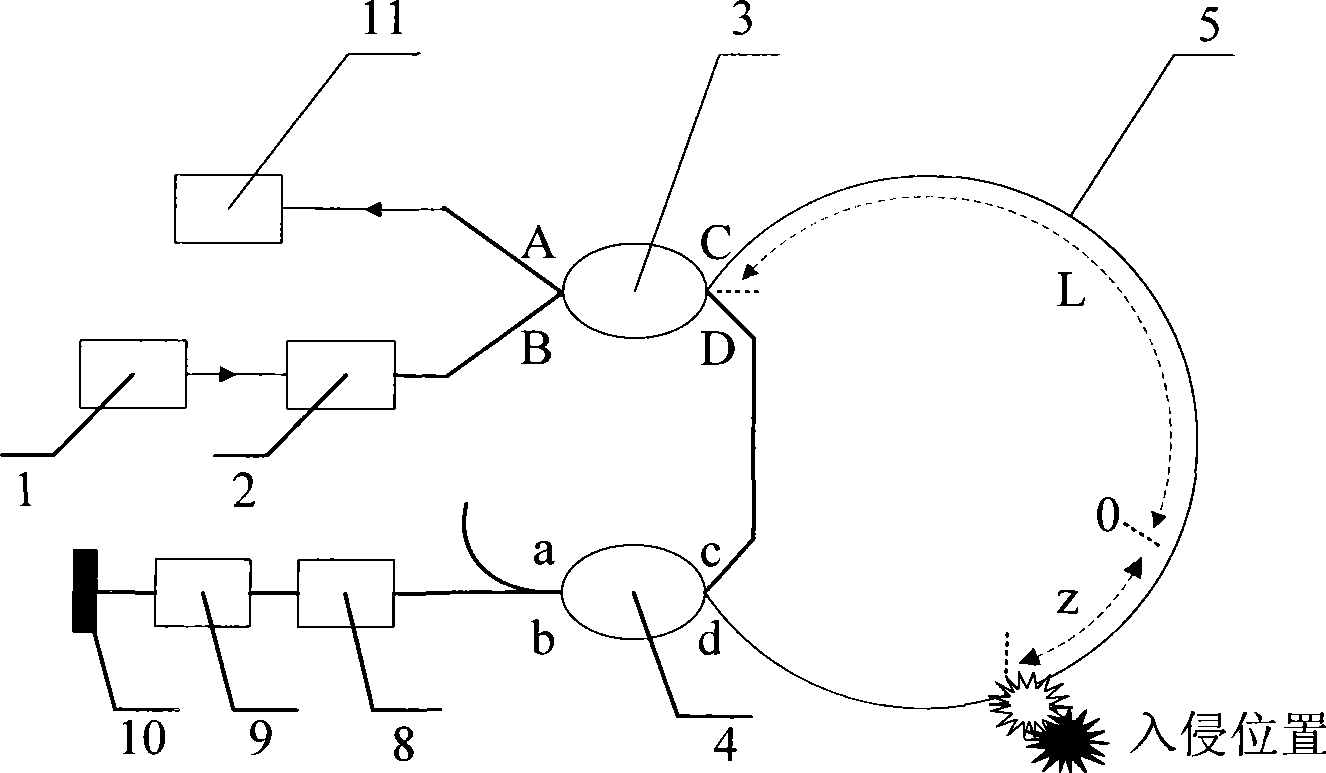
Safety monitoring system and method for circumference
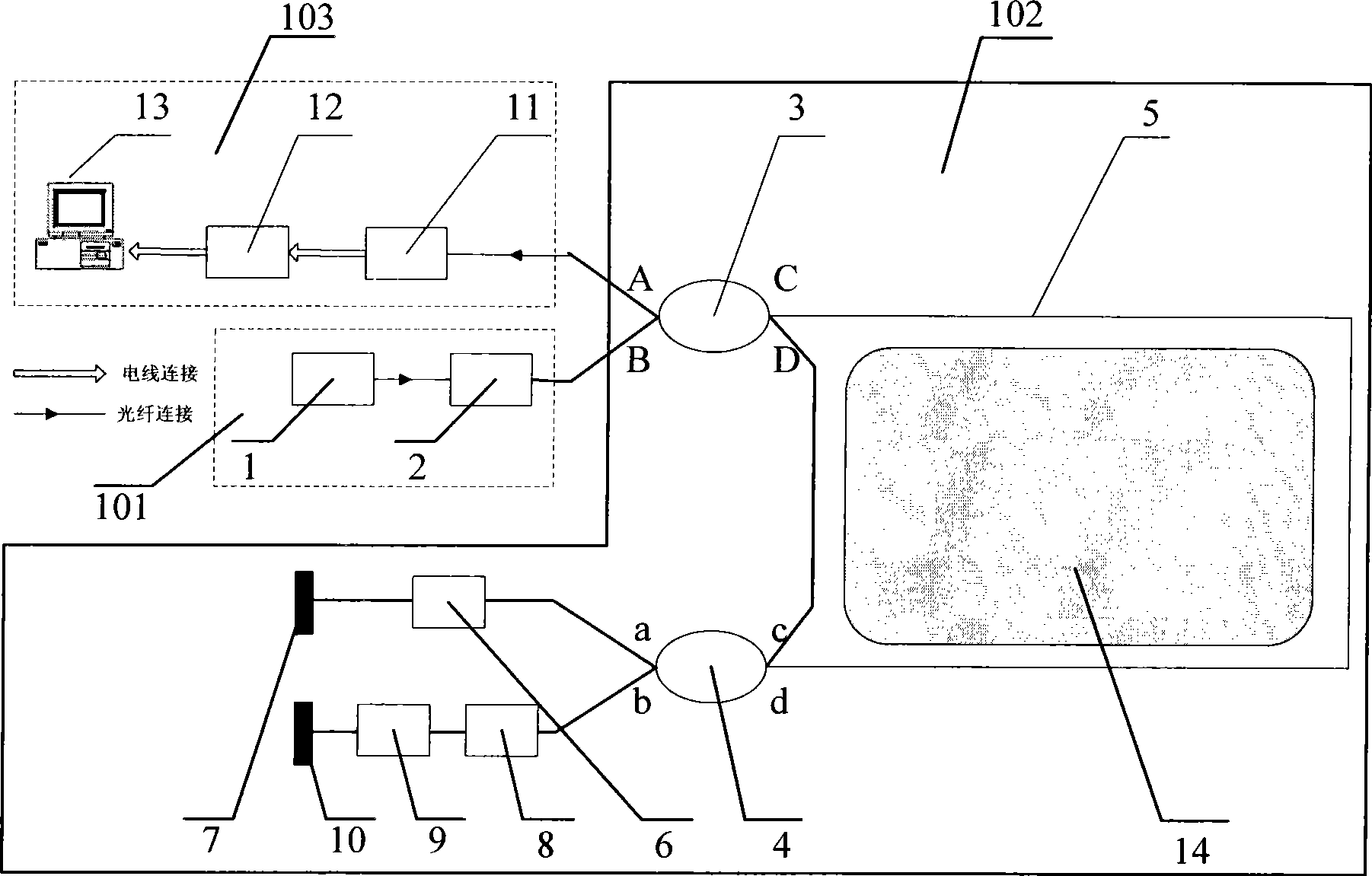
InactiveCN101465052AHigh sensitivityLow costNon-electrical signal transmission systemsOptical apparatus testingBeam splitterData acquisition
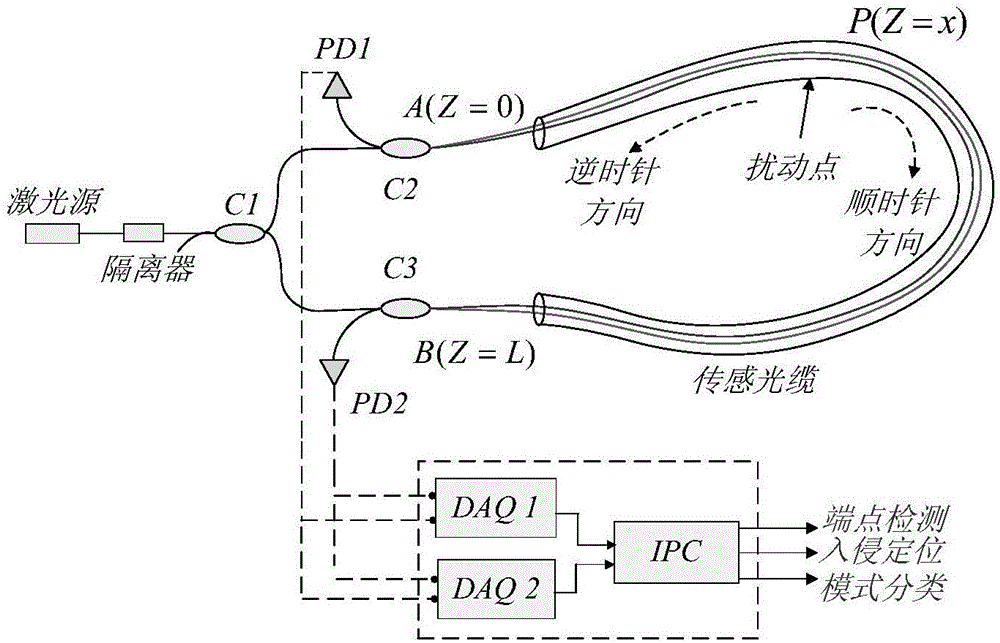
The invention discloses a perimeter security monitoring system. A light source, an optical isolator and a port B of a beam splitter 3 are connected through an optical fiber in sequence, the beam splitter 3 is connected with a beam splitter 4 through a sensing optical fiber, the port a of the beam splitter 4 is connected with a reflecting mirror through a phase modulator, the port b of the beam splitter 4 is connected with a delay winding through the phase modulator, and the delay winding is connected with the reflecting mirror. When the sensing optical fiber vibrates along the line, the two paths of interference optical signals carried with the same vibration information reach an photoelectric detector from the port A of the beam splitter 3, the analog signal is transformed into a digital signal through a data acquisition unit, the digital signal is transmitted to a computer, and the positioning of a vibration source is obtained by a formula, i.e. z is equal to LD*phi s(t) / phi M-Z (t). The invention can monitor the perimeter vibration conditions at real time, has very high sensitivity and positioning accuracy and reliably runs.
Owner:SUZHOU GUANGLAN INFORMATION TECH
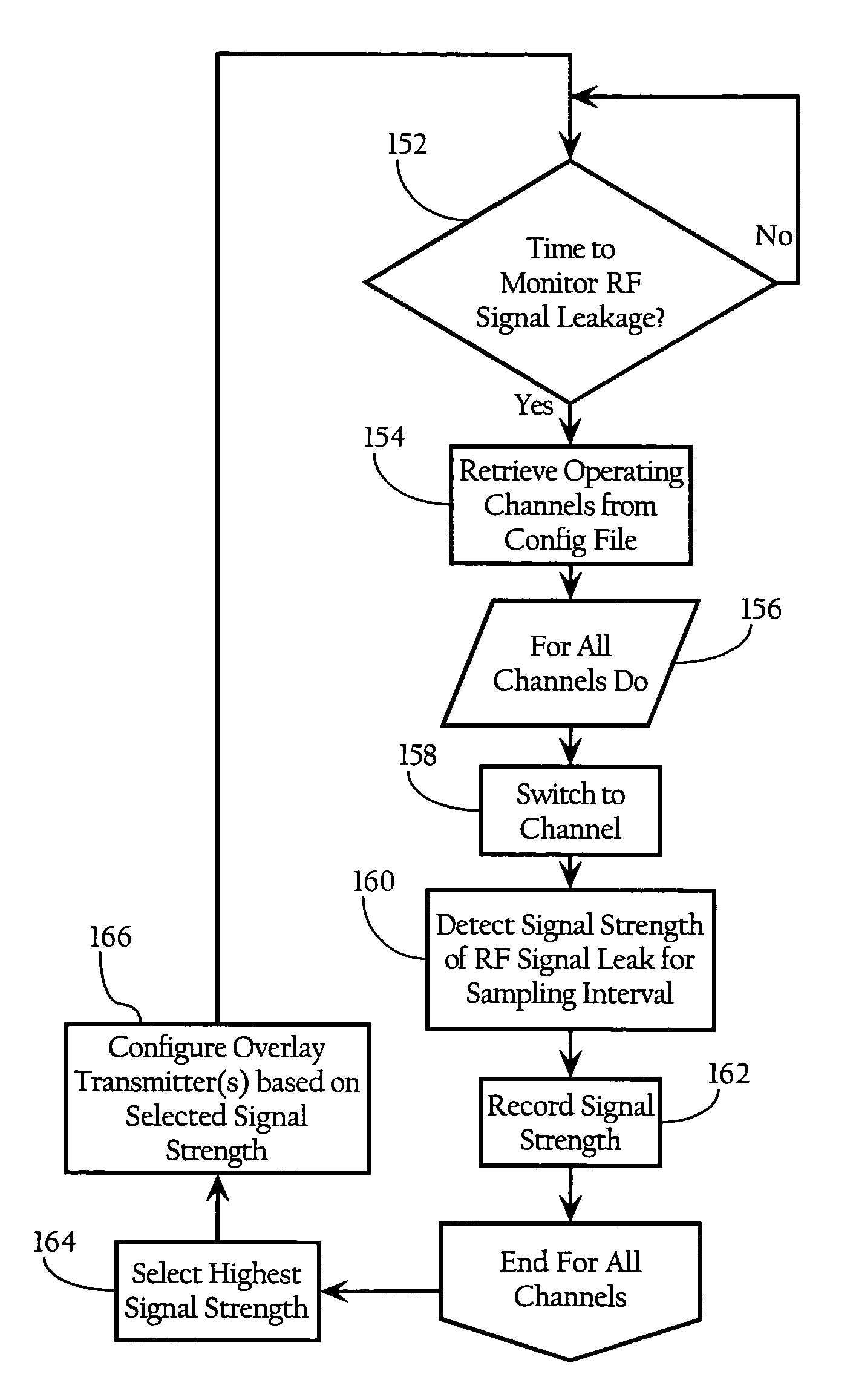
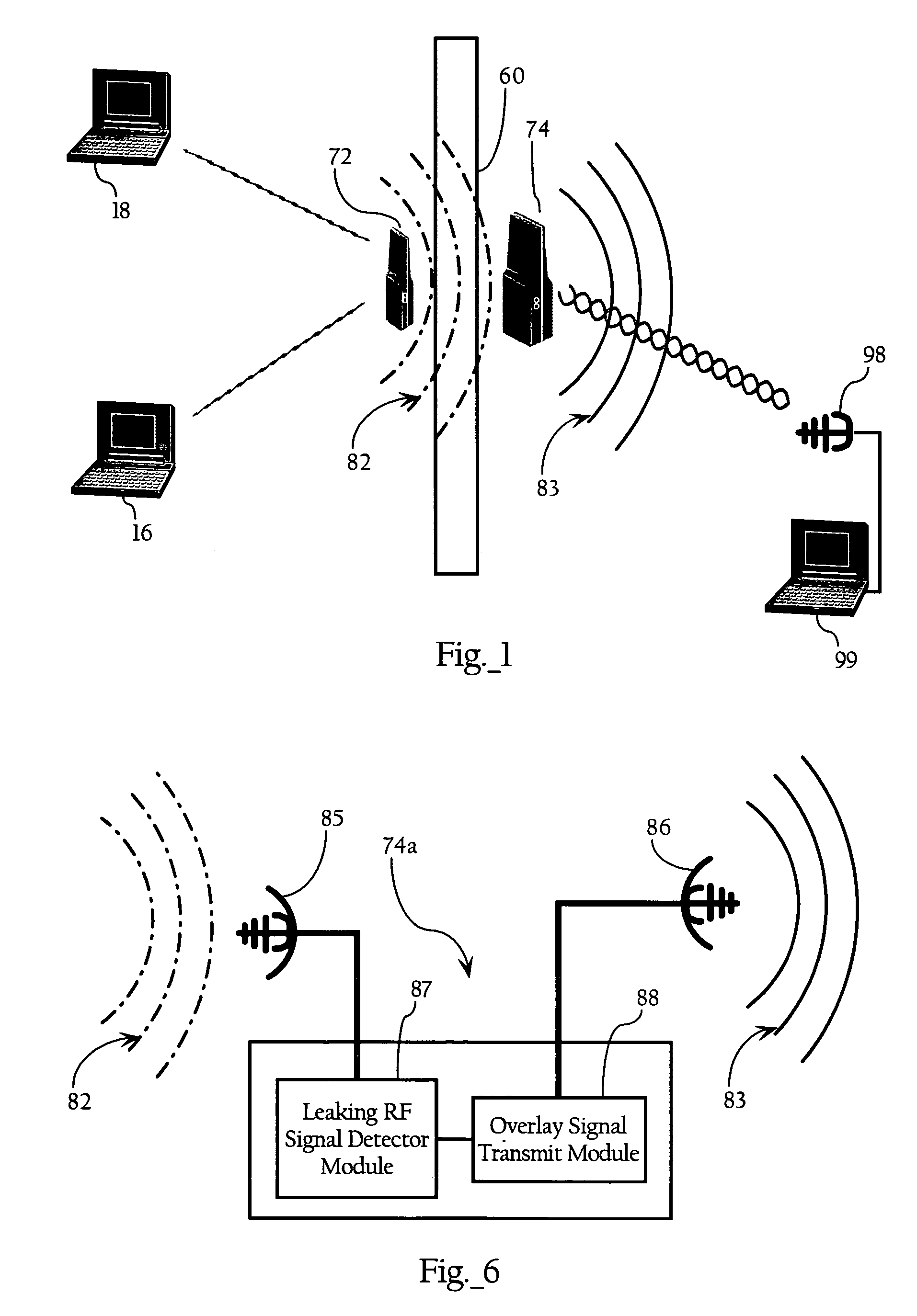
Wireless network perimeter security system using overlaying radio frequency signals
ActiveUS7251457B1Prevents and disrupts meaningful accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPhysical spaceRadio frequency signal
Methods, apparatuses and systems directed to securing a wireless network environment from eavesdropping and other unauthorized activities. One implementation prevents or disrupts meaningful access to information contained in WLAN RF signals that escape from a given physical space during operation of the wireless network. One implementation utilizes overlay RF signals transmitted on one or more operating channels of the WLAN to overpower or mask the internal RF signals escaping from a defined security line or perimeter. One implementation monitors the RF energy escaping to dynamically adjust the power of the overlay signal as required. Implementations of the invention can secure the outer perimeter of an office within a building, or even the outer perimeter of an entire building.
Owner:CISCO TECH INC
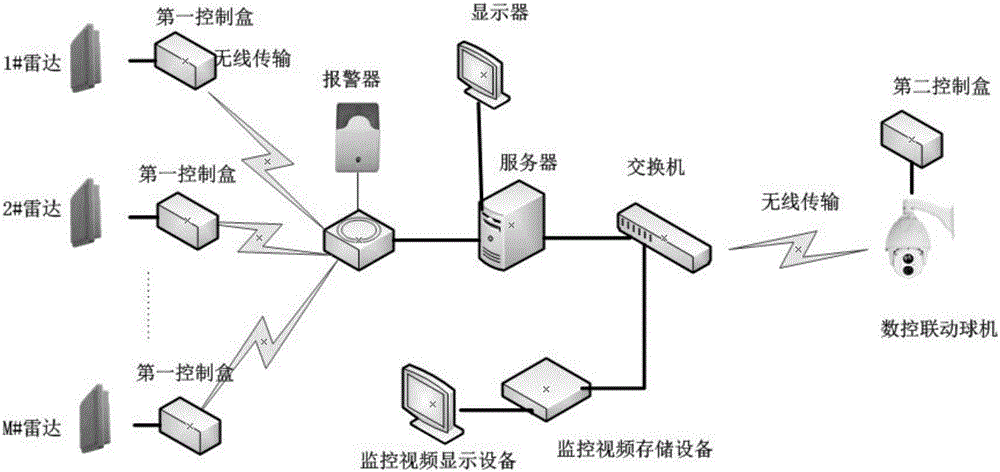
Portable radar perimeter security and protection system
InactiveCN106657921ARemind in timeEstablish an intelligent identification and filtering mechanismClosed circuit television systemsBurglar alarm electric actuationNumerical controlDisplay device
The invention provides a portable radar perimeter security and protection system. The portable radar perimeter security and protection system comprises radars, first control boxes, a numerical control linkage dome camera, a second control box, a server, a displayer of the server, a switch, a monitoring video display device and an alarm device. The server, the numerical control linkage dome camera, the wireless equipment, the radars, the monitoring video display device and the alarm device are connected by the wireless network. The server is equipped with the portable perimeter security and protection system software; the core of the software is the control of 3D linkage of the radars and the numerical control linkage dome camera; the algorithm adopted by the linkage control is presetting the space coordinates of the left, center and right 3 points of the radars and the numerical control linkage dome camera, and the input data is the target location detected by the radars, and the calculating result which is calculated according to trigonometric function is the PTZ 3D coordinate of the numerical control linkage dome camera. The first control boxes are used for supplying power to the radars, and the second control box is used for supplying power to the numerical control linkage dome camera. The switch provides the connection ports for a plurality of cables, used for connecting the server, the monitoring video display device, and the numerical control linkage dome camera; and the switch adopts star topology and realizes the data exchange among the devices in the network.
Owner:秦皇岛博微智能科技有限公司
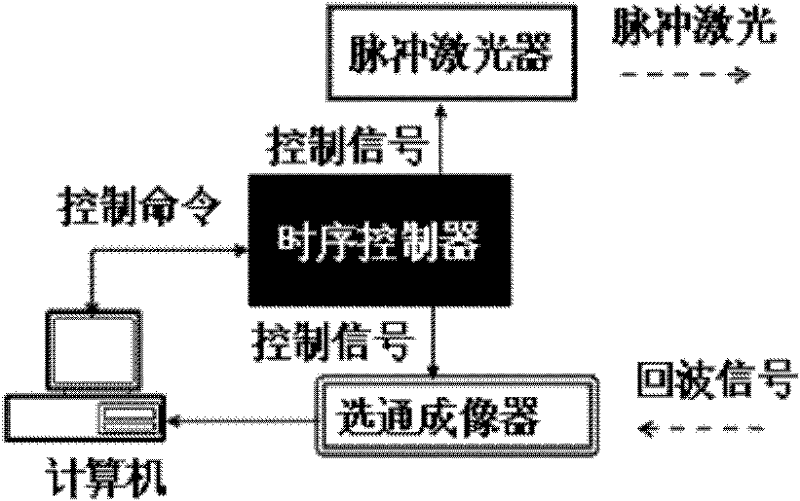
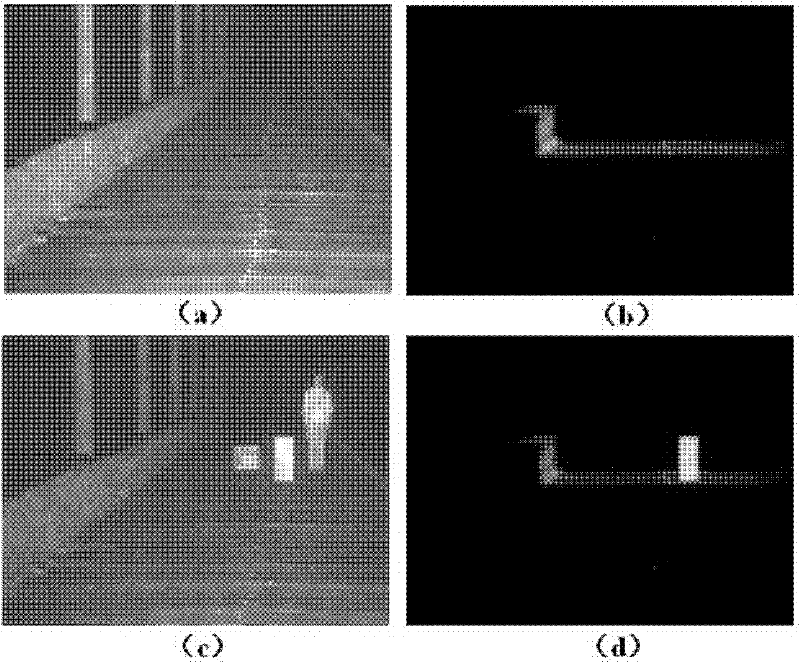
Photon fence system for perimeter security monitoring at night
The invention discloses a photon fence system for monitoring on security protection of perimeter at night. The system comprises: a pulsing laser, which is used for emitting a laser pulse to carry out illumination on an object; a gated imaging device, which is used for controlling exposure time by a pulse width of a gated pulse; a time schedule controller, which is used for controlling time delay between the gated pulse and the laser pulse; and a computer, which is used for carry out controlling, image processing and displaying on the pulsing laser, the gated imaging device and the time schedule controller. According to the system provided in the invention, a pulsing laser is utilized as a light source and a gated imaging device is employed as a detector; time delay between a gated pulse and a laser pulse is controlled so as to establish a photon fence in space, wherein the photon fence is invisible for human eyes; therefore, when an invading object passed through the photon fence, image information of the invading object is collected and background outside the photon fence and a non-invading object are removed by filtering, so that non-background extraction on the invading object is realized.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
Distributed perimeter security threat confirmation
ActiveUS7450006B1Improve scalabilityImprove efficiencyProgramme controlElectric signal transmission systemsInternet privacyHandling system
A sensor system for monitoring a perimeter for a plurality of events comprises a signal sensor configured to receive an event signal for an event of the plurality of events, a processing system configured to process the event signal to determine if the event is a threat, confirm that the event is a threat in response to determining that the event is a threat, and generate a threat message identifying the event in response to confirming the threat, and an interface system configured to transmit the threat message.
Owner:ALLISON SYST
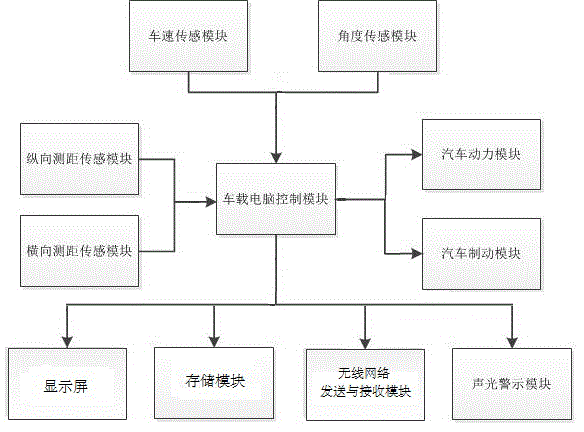
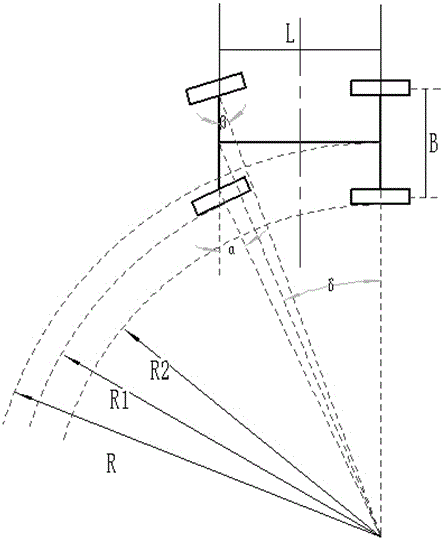
Vehicle turning safety assisting system
ActiveCN104960466APredict collisionPre-judging its likelihoodAcoustic signal devicesAutomatic initiationsAcousto-opticsElectric vehicle
The invention relates to a vehicle turning safety assisting system. The vehicle turning safety assisting system comprises a vehicle-mounted computer control module, and an angle sensing module connected, a longitudinal distance measurement sensing module connected, a vehicle speed sensing module, a vehicle power module, a vehicle braking module, and an acousto-optic warning module which are connected with the vehicle-mounted computer control module; after acquiring the turning state of a vehicle and the information of conditions surrounding the vehicle, the vehicle-mounted computer control module predicts the running route of the vehicle and the information of passers-by or objects, which are the closest from the vehicle, through calculation, so as to judge whether the vehicle can collide with the passers-by or other objects and the degree of danger or not; if a collision danger is discovered, the vehicle-mounted computer control module automatically takes safety measures, such as cutting off vehicle power, and starting emergent band-type brake immediately, and sends acousto-optic warning signals to drivers and the passers-by so as to guarantee the safe of people, the vehicle and the surroundings. The vehicle turning safety assisting system can be mounted on any vehicle using an internal combustion engine as power, and can also be applied to various electric vehicles and various engineering machinery; therefore, the vehicle turning safety assisting system is extensive in application prospect, good in timeliness, easy to realize, low in mounting cost, and easy to popularize.
Owner:FUZHOU UNIV
System and method for passive assessment of industrial perimeter security
A computer-implemented method for assessing and managing network security for a network includes retrieving topology data and network traffic data with a processor, where the topology data is indicative of a topology of the network. The method may further include retrieving network flow data from a plurality of network data collectors via the processor, generating an attack tree based on the topology data and the network flow data via the processor, updating a customer model database with the attack tree and the topology data, and outputting a security assessment based on the attack tree and the topology data.
Owner:SIEMENS AG
Phase sensitive optical time-domain reflectometer (phi-OTDR) sensing signal noise separation and signal extraction method
InactiveCN103196465AEasy to detectSuppress background noiseMitigation of undesired influencesElectromagnetic transmissionTime-domain reflectometerMultiscale decomposition
The invention discloses a phase sensitive optical time-domain reflectometer (phi-OTDR) sensing signal noise separation and signal extraction method, a longitudinal time sequence signal of each point of a phi-OTDR space is used as a processing object, multi-scale decomposition is performed for the time sequence signal by utilization of wavelet transforming, component signals in each scale are analyzed and reorganized in a selective mode, undulate background noise, acoustic waves and other time-varying interference signals are separated, real disturbance invasion signals are extracted, not only can undulate background noise be restrained, but also influences from other complicated time-varying interference noise are avoided, an invasion detection accuracy rate can be effectively improved, a system false alarm rate is reduced, detection performance of an invasion detection system based on a phi-OTDR in an actual complicated noise environment is improved, and significant application requirements in perimeter security, long-distance pipeline safety, large structure health monitoring and the like for a country can be met.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Distributed optical fiber vibration sensing method and system based on pulse coding external modulation
ActiveCN104034409ALittle external interferenceEasy to installSubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansVibration detectionDigital signal
The invention discloses a distributed optical fiber vibration sensing method and system based on pulse coding external modulation. The method comprises the steps that a reverse echo curve obtained by continuous k times of optical pulse emitting is selected, an average time and interval parameters are preset, and a plurality of average curves are acquired; the standardized average curves are combined to form a two-dimensional signal matrix Y, a range matrix is selected to calculate a local range, the vibration strength of a sensing optical fiber is evaluated according to all elements in a range matrix to acquire a vibration space position, the data at the ith point in each echo curve after decoding delay are extracted to obtain time domain sampling signals of vibration. The system comprises a photoelectric detector which forms electrical signals and a signal collecting and regulating device which is used for conducting amplification and analog-digital conversion to achieve digital signals, the digital signals are transmitted into a computer to achieve decoding, time delay, positioning and extraction time domain processing, and the vibration condition along the line of distributed sensors. The distributed optical fiber vibration sensing method and system based on pulse coding external modulation meet the demand for various vibration detection and monitoring application, and is particularly suitable for long-distance pipeline monitoring and perimeter security.
Owner:天津精仪精测科技有限公司
Perimeter security system
ActiveUS20120319844A1Burglar alarm electric actuationRadio wave reradiation/reflectionEngineeringUltimate tensile strength
A security system for detecting physical intrusion in a monitored area including a plurality of radio units arranged in a network around the monitored area to determine received signal strength and pass variations thereof through the radio units to a base station.
Owner:INTELLIGENT AUTOMATION LLC
Fiber perimeter security intrusion event identification method and apparatus based on integrated characteristics
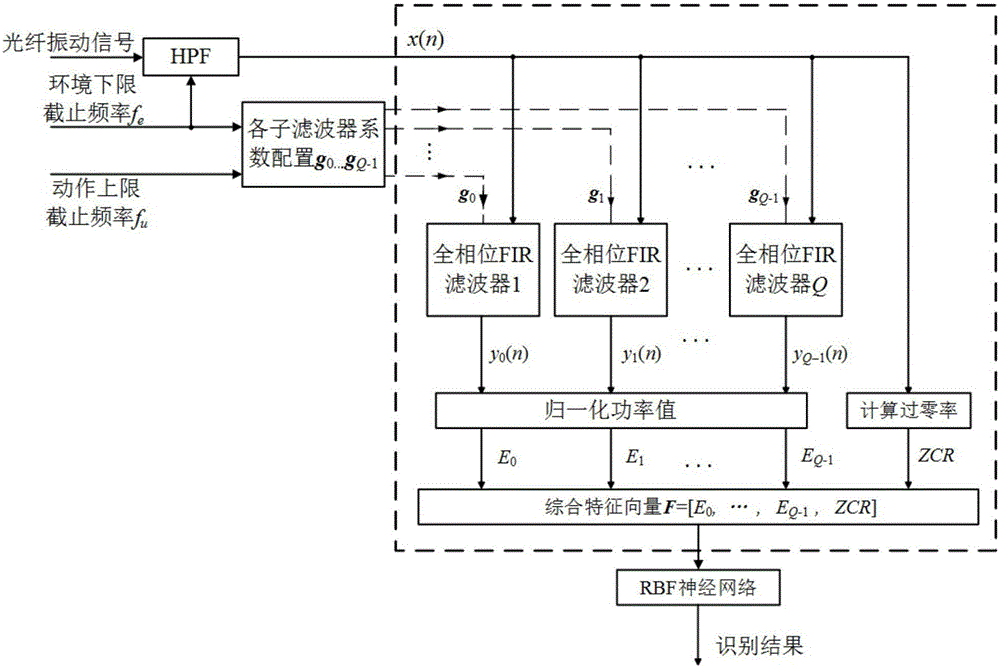
InactiveCN107180521AImprove accuracyHigh precisionInput/output to record carriersCharacter and pattern recognitionFiberPhase filter
The invention discloses a fiber perimeter security intrusion event identification method and apparatus based on integrated characteristics. The fiber perimeter security intrusion event identification method based on integrated characteristics includes the steps: feeding the signal disturbing the start point in each channel of an all-phase filter bank each channel to perform frequency domain separation processing, calculating the normalization power value of the output signal of each channel, wherein the plurality of normalization power values are output in parallel; integrating the normalization power values and the time domain zero-crossing rate of the whole section of disturbance signals to generate a characteristic vector, wherein the characteristic vector contains two aspects of information: the time domain and the frequency domain; and feeding the characteristic vector in a radial primary function neural network to realize intrusion motion quick high precision identification. The fiber perimeter security intrusion event identification apparatus based on integrated characteristics includes an analog-to-digital converter and a DSP (Digital Signal Processor) device. The fiber perimeter security intrusion event identification method and apparatus based on integrated characteristics can accurately distinguish four types of intrusion events. Besides, compared with a current high precision intrusion event identification classifier, the DMZI (dual Mach-Zehnder interferometer) intrusion motion identifier has great advantages of work efficiency.
Owner:TIANJIN UNIV
Method for identifying and detecting disturbance signals of phase-sensitive optical time domain reflectometer
InactiveCN103226028AEasy to detectEasy to identifyMeasurement devicesBiological neural network modelsMultiscale decompositionDecomposition
The invention discloses a method for identifying and detecting disturbance signals of a phase-sensitive optical time domain reflectometer. The method mainly aims at improving detection and intelligent identification ability of the phase-sensitive optical time domain reflectometer to external disturbance, and reducing a misstatement rate and a false alarm rate of a system in a practical complicated noise environment. The method comprises the steps that longitudinal time sequence signals of various spatial points serve as processing objects; fractal characteristics of the longitudinal time sequence signals are extracted for disturbance detection and positioning; multi-scale decomposition is conducted on the time sequence signals by wavelet transformation; the energy characteristics of detail signal components under different scales are extracted by utilizing distribution differences of the different-type disturbance signals of time-varying interference signals such as fluctuating background noises and sound waves, real intrusion signals and the like on a multi-scale time frequency shaft; multi-scale time frequency distribution characteristic vectors of the signals are formed; and specific attributes of the disturbance signals are identified and classified by combining a back-propagation (BP) neural network identification method. The method is applicable to application fields of perimeter security and protection, long-distance pipeline security, large-scale structure health monitoring and the like.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Warning method for campus based on face recognition
InactiveCN109727352AImprove securityReduce work stressRegistering/indicating time of eventsData processing applicationsSecurity systemDigitization
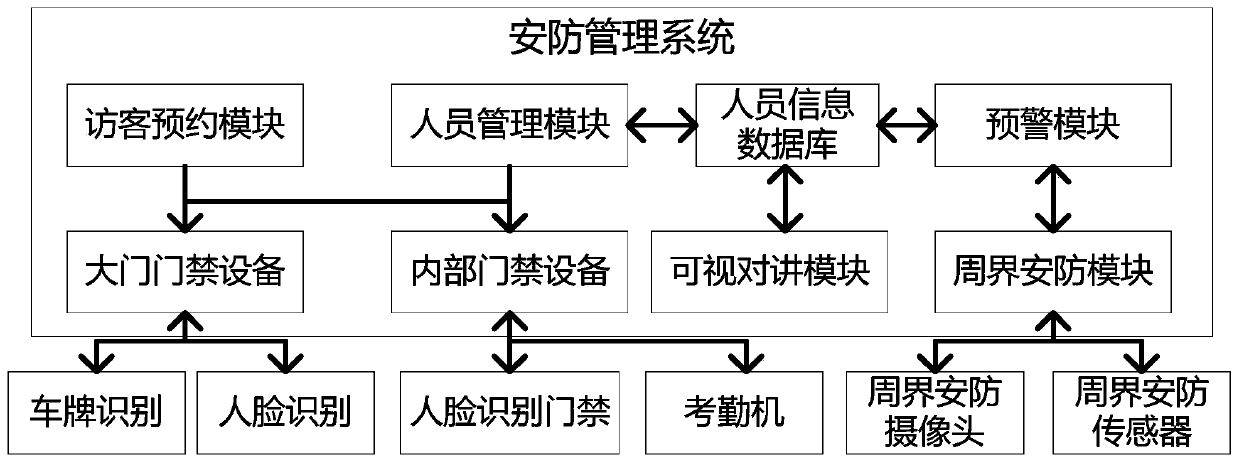
The invention relates to the field of Internet of Things and intelligent security, and specifically discloses a warning method for a campus based on face recognition. The method comprises a personnelmanagement module, a warning module, a visitor reservation module, a perimeter security module, and a visual intercom module. The personnel management module is used for managing access authority andmonitoring personnel access. The warning module is used for pushing warning information to parents and teaching staffs. The visitor reservation module is used for temporary visitors to apply for access authorization. The perimeter security module is used for monitoring and recording a perimeter alarm device and sending out a warning signal. The visual intercom module for communication between security personnel and the teaching staffs and information query. According to the warning method for the campus based on face recognition, a smart camera with face recognition and license plate recognition is combined with a perimeter security device and attendance system to form a complete set of digital security system for the campus, so that the security system for the campus can further realize comprehensive intelligent and automated supervision, the pressure on the security personnel is reduced, and the security level of the campus is improved.
Owner:广东粤众互联信息技术有限公司
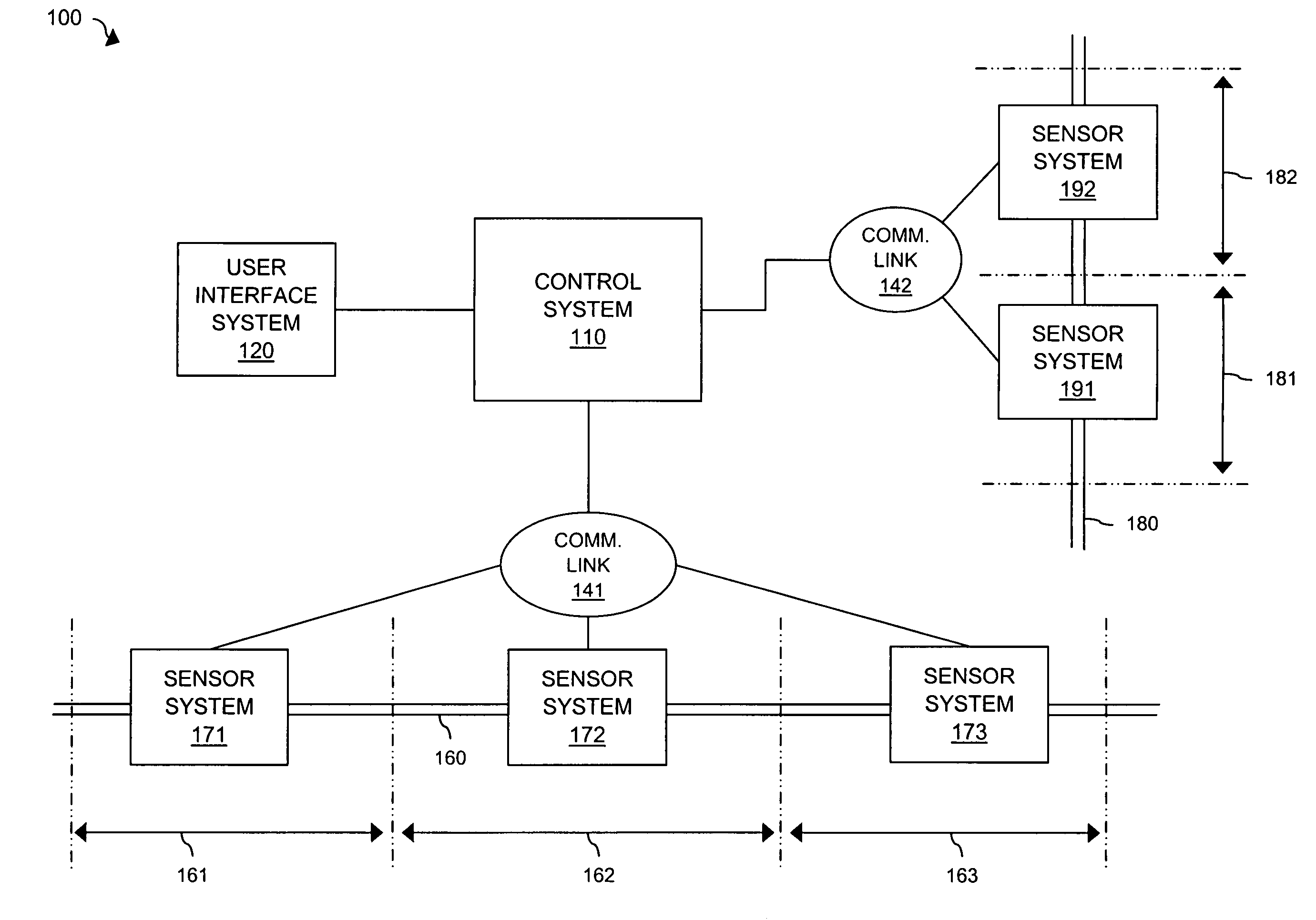
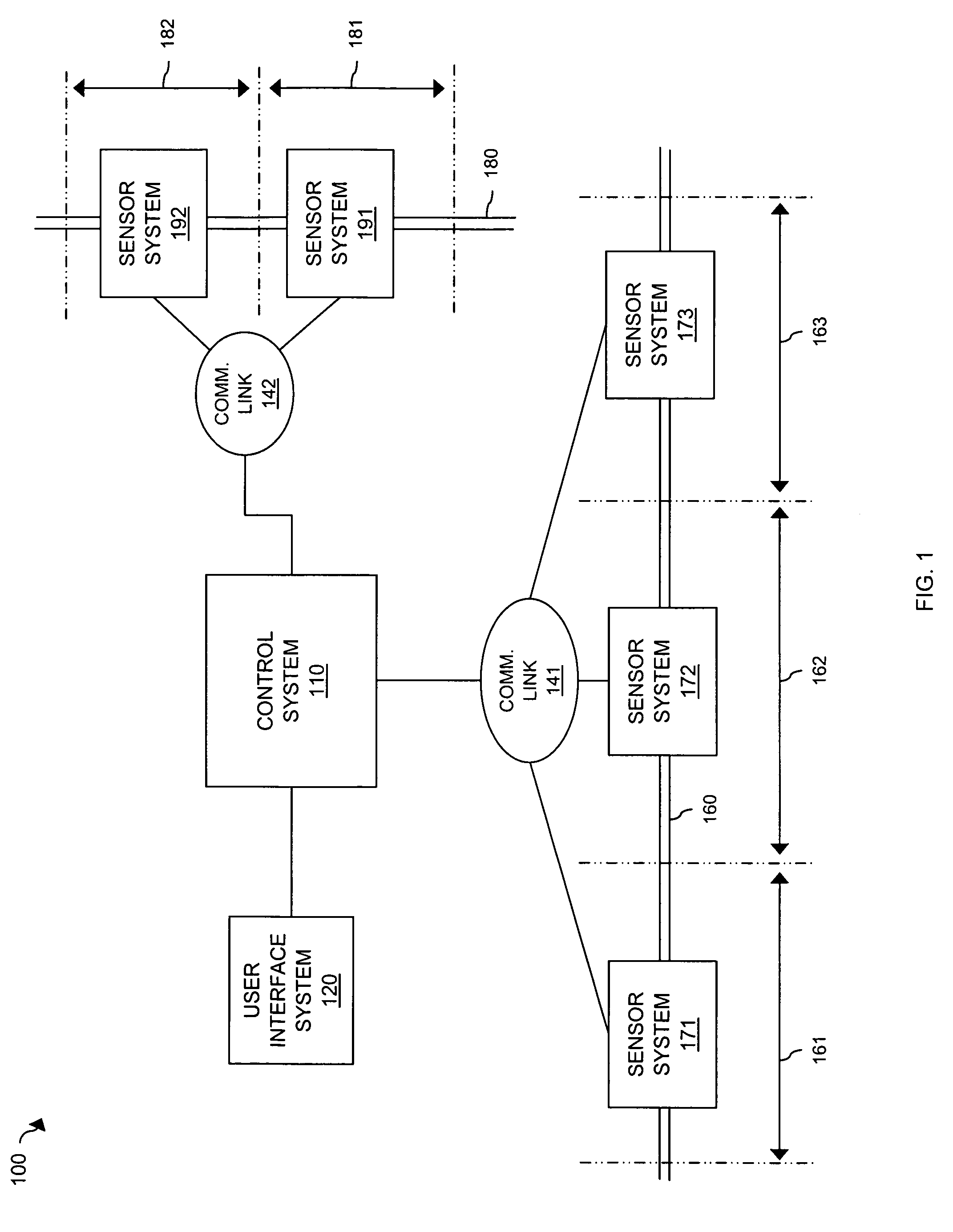
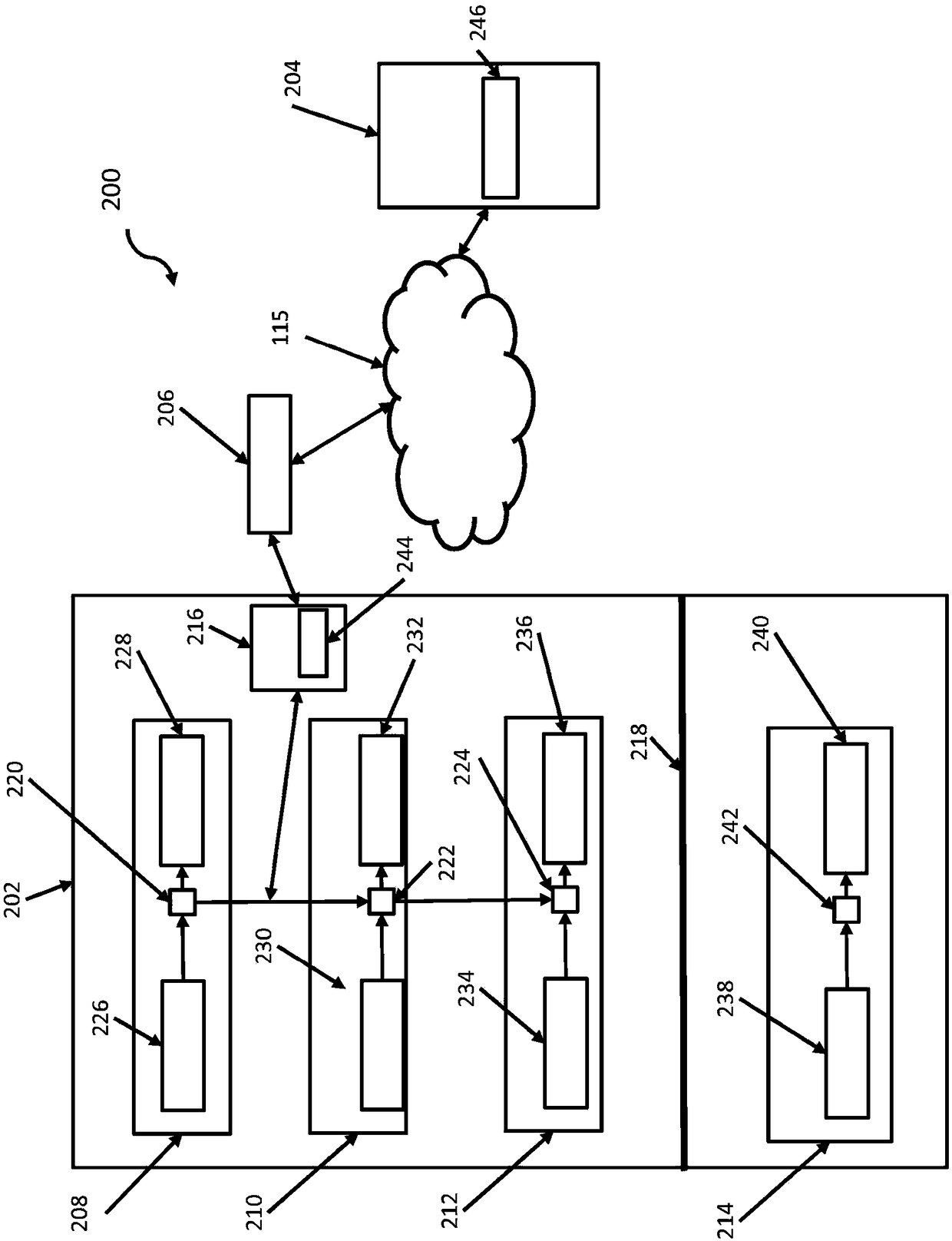
State-full perimeter security for data networks
ActiveUS7886349B2Data switching by path configurationMultiple digital computer combinationsTelecommunicationsData Web
Owner:U S CELLULAR
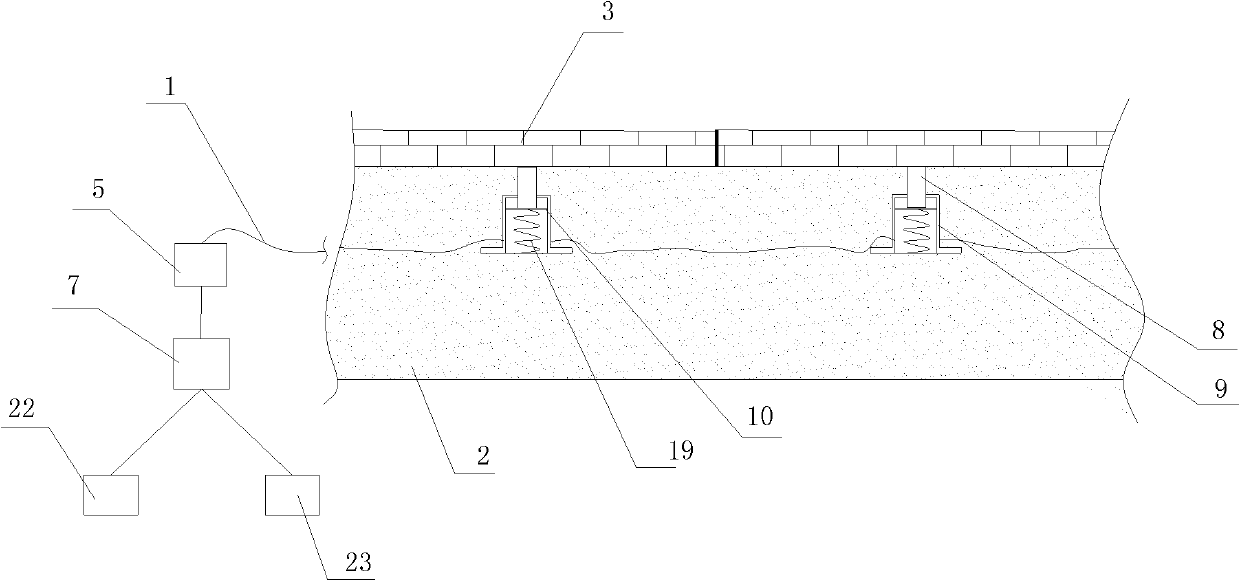
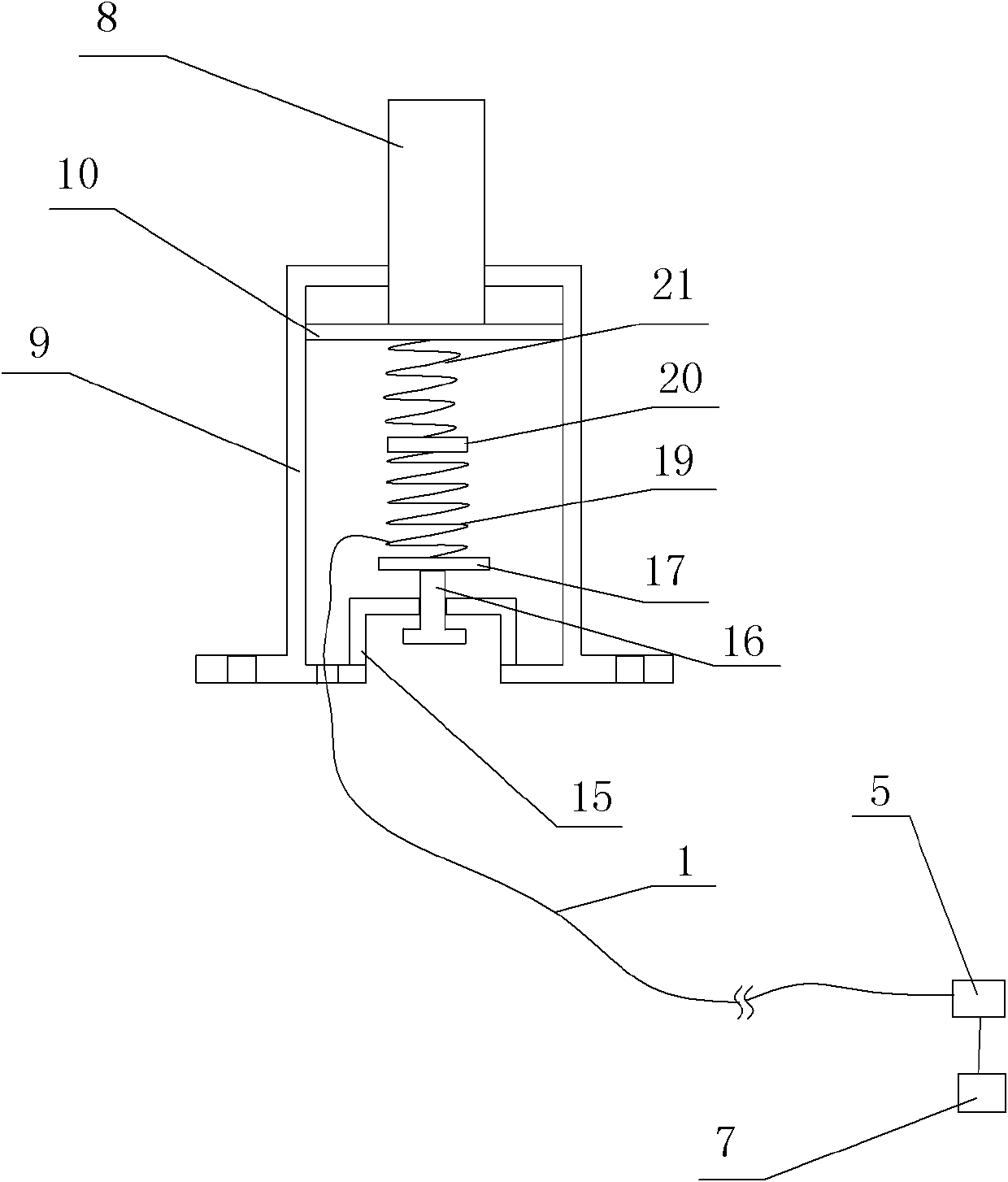
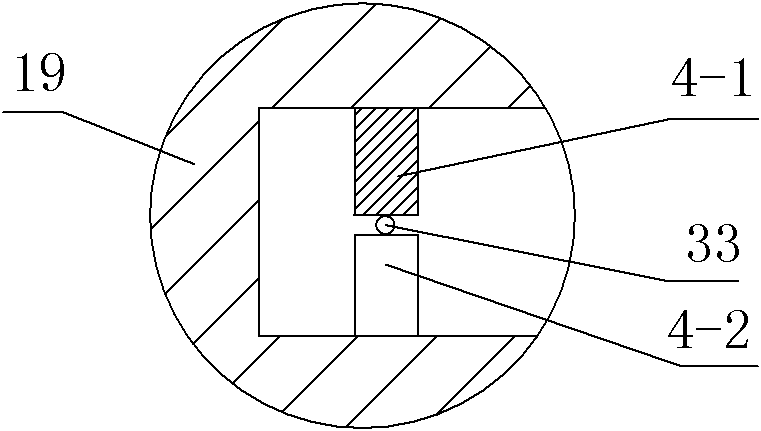
Pressure-sensitive type fiber sensing device for perimeter security protection
InactiveCN102568134ASimple structureEasy to processOptical detectionConverting sensor output opticallyFiberStructural engineering
The invention discloses a pressure-sensitive type fiber sensing device for perimeter security protection. The device comprises at least a fiber bending sensing element which is arranged under a pavement flat plate and is buried in a soil layer. Each fiber bending sensing element comprises a signal fiber. At least one end of an optical cable is connected with a test unit. The test unit is connected with a processing unit. The processing unit is connected with alarm equipment and a camera. The fiber bending sensing element comprises a guide rod and a housing which is in sliding fit with the guide rod. The guide rod is in contact connection with one end of a curved support. The other end of the curved support is fixed on an inner wall of the housing. When extraneous force generates displacement to the pavement flat plate, displacement of the pavement flat plate further enables bending curvature of the signal fiber to change, an optical signal transmitted in the signal fiber changes with the above change, the change of the optical signal can be monitored through the test unit and is transmitted to the processing unit, and the processing unit starts the alarm equipment and the camera. According to the device, an intrusion behavior of an intruder can be effectively monitored.
Owner:XIAN JINHE OPTICAL TECH
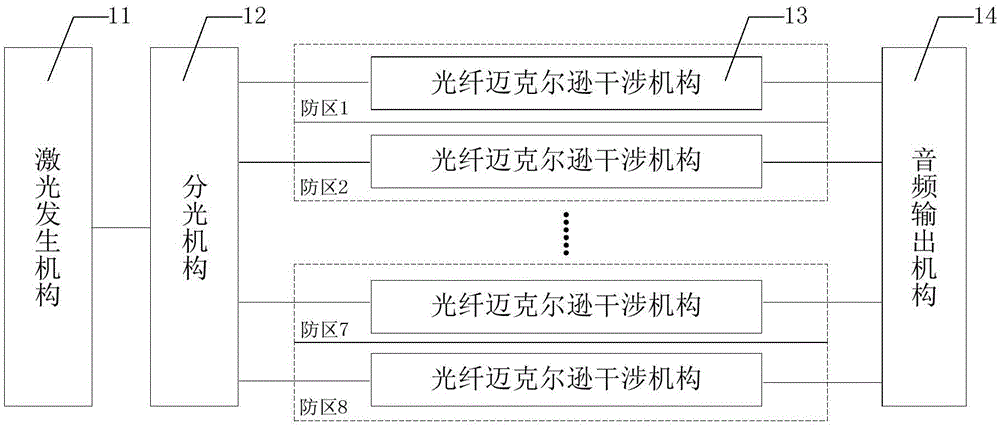
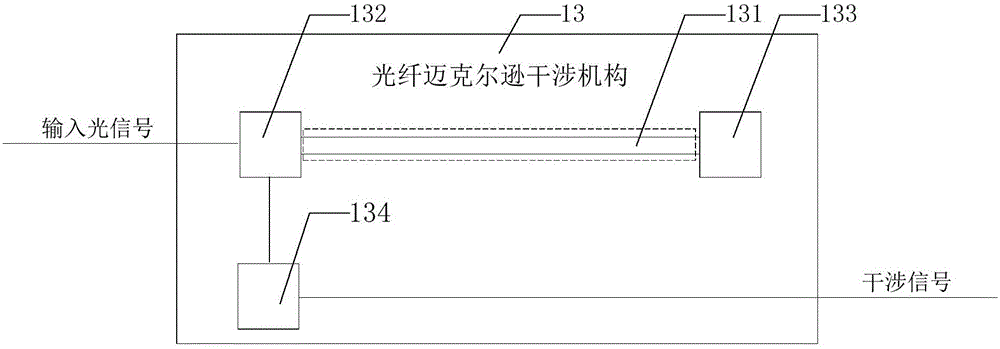
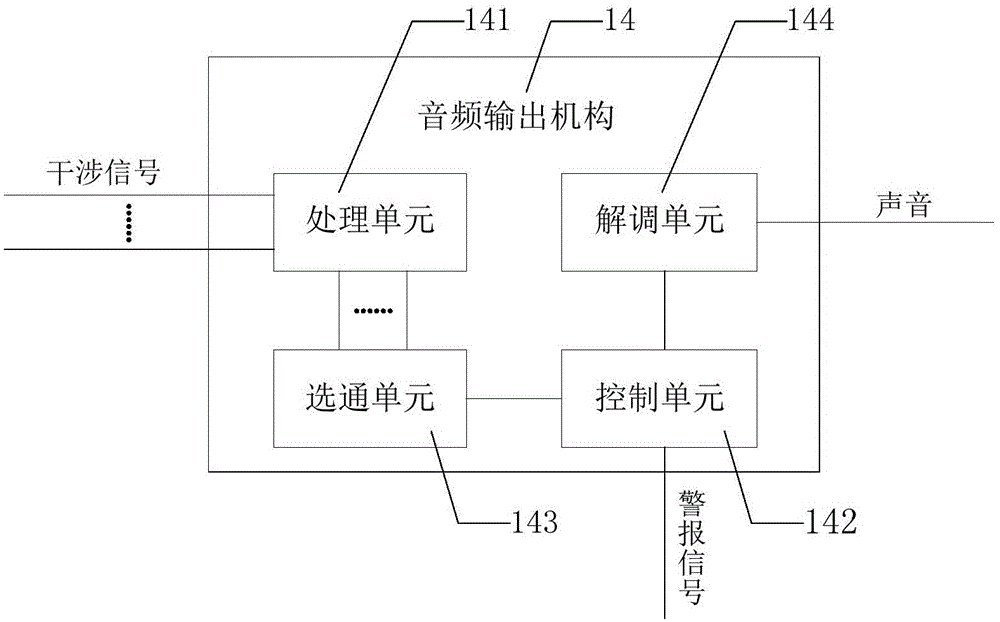
Distributed optical fiber perimeter security-monitoring system, sound reduction system and method
ActiveCN105096490AAvoid interferenceImprove discriminationSubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansMonitoring systemEngineering
The present disclosure provides a distributed optical fiber perimeter security-monitoring system, a sound reduction system and a method. The sound reduction system is applied to the distributed optical fiber perimeter security-monitoring system for monitoring a plurality of defense regions. The sound reduction system comprises a laser generation mechanism used for providing a laser signal; a light splitting mechanism used for splitting laser signals into multiple paths of input optical signals; a plurality of optical fiber Michelson interference mechanisms arranged in the plurality of defense regions correspondingly; and an audio output mechanism used for receiving each of all interference signals. Each optical fiber Michelson interference mechanism is configured to receive an input optical signal and output an interference signal in response to the peripheral sound pressure. When the audio output mechanism receives an alarm signal from any one defense region, the audio output mechanism outputs a sound signal obtained through reducing the interference signal in the corresponding defense region. The system of the invention facilitates people to further confirm and judge the occurrence of abnormal events, such as intrusion activities.
Owner:NUCTECH CO LTD
State-full perimeter security for data networks
ActiveUS20070157301A1Data switching by path configurationMultiple digital computer combinationsComputer networkPerimeter Security
The described embodiments include a system for controlling communications between a first network and a second network including a plurality of in-line security devices, the in-line security devices being configured to manage communication between the first network and the second network, and including a state server connected to the plurality of in-line security devices, the state server being configured to receive state information about the state of the connections established by a first one of the in-line security devices and to communicate the state information to at least a second one of said in-line security devices. In one embodiment, the in-line security devices are firewalls. In another embodiment, state server communicates the state information received from the first one of the firewall devices and communicates the state information to every other one of the plurality of firewall devices. The described embodiments also include a method for controlling communications between a first network and a second network including providing a plurality of in-line security devices, establishing communication between the first network and the second network via the in-line security devices, providing a state server connected to the plurality of in-line security devices, transmitting state information from a first one of the the in-line security devices about the state of the connections established by the a first one of the in-line security devices, and communicating the state information from the state server to at least a second one of said in-line security devices.
Owner:U S CELLULAR
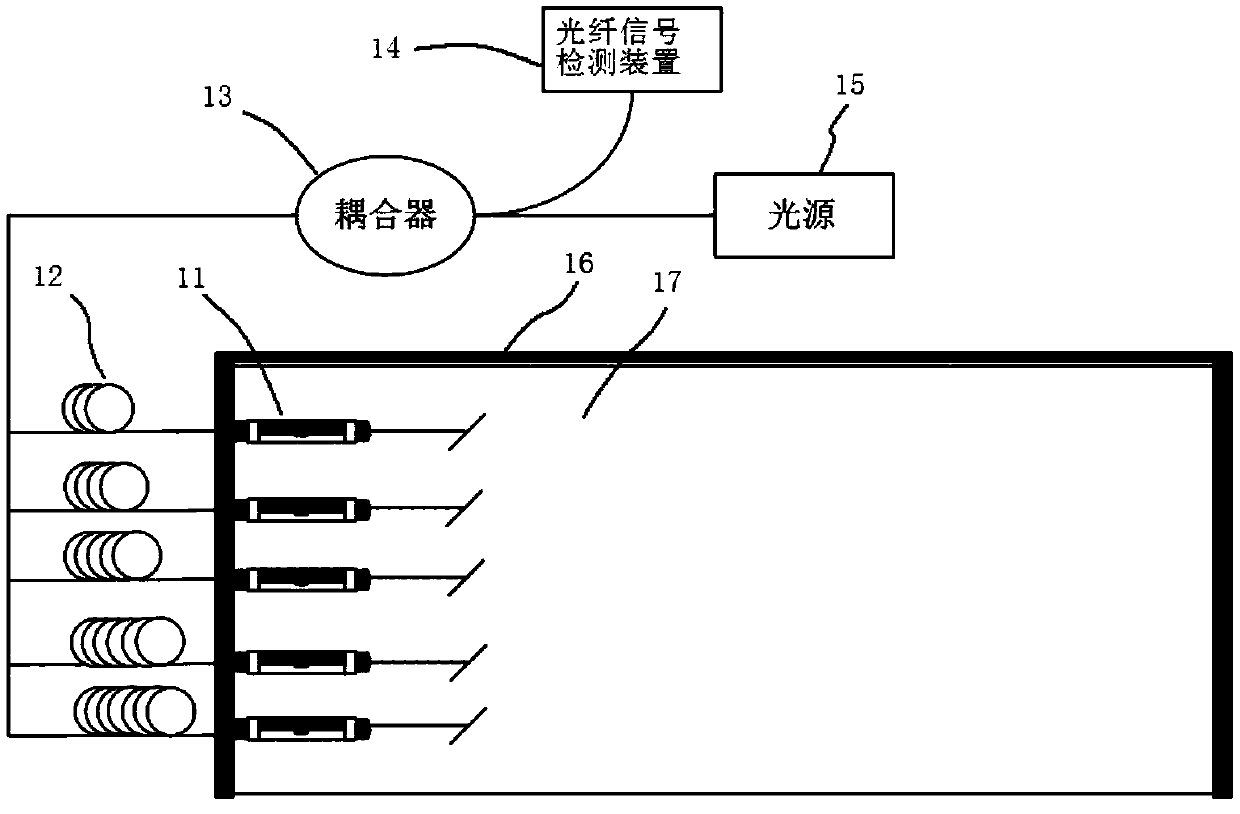
Perimeter security protection system
InactiveCN107862821ATimely detectionTimely processingBurglar alarm by disturbance/breaking stretched cords/wiresElectromagnetic interferenceCommunicating Junction
The invention discloses a perimeter security protection system which comprises an invasion signal sensing detection unit and a signal processing unit. The perimeter security protection system is characterized in that the invasion signal sensing detection unit comprises multiple optical fiber sensors distributed around a protection area, the optical fiber sensors are jointly connected on a couplerthrough optical fiber, and a light source and an optical fiber detection device are connected on the coupler; the signal processing unit comprises a signal analysis processing module and used for processing optical fiber signals received from the invasion signal sensing detection unit and judging whether the optical fiber signals belong invasion signals or not. The perimeter security protection system adopts optical fiber sensor technology to detect invasion signals, thereby being capable of timely and efficiently detecting invasion events; the optical fiber sensors have good characteristics being free of electromagnetic interference, thereby being accurate and stable in detecting the invasion events.
Owner:SHANGHAI NORMAL UNIVERSITY
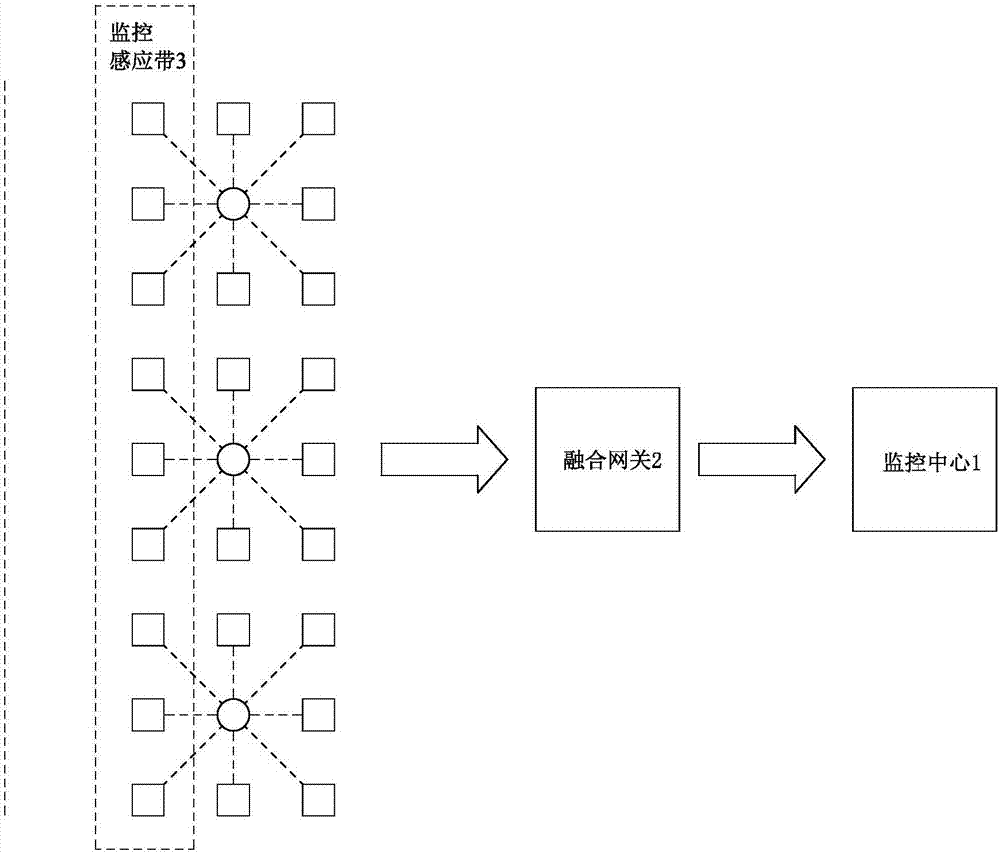
Wide-range perimeter security monitoring method and system
ActiveCN107277443AReduce transmission delayImprove communication reliabilityClosed circuit television systemsTransmissionEvent typeInformation analysis
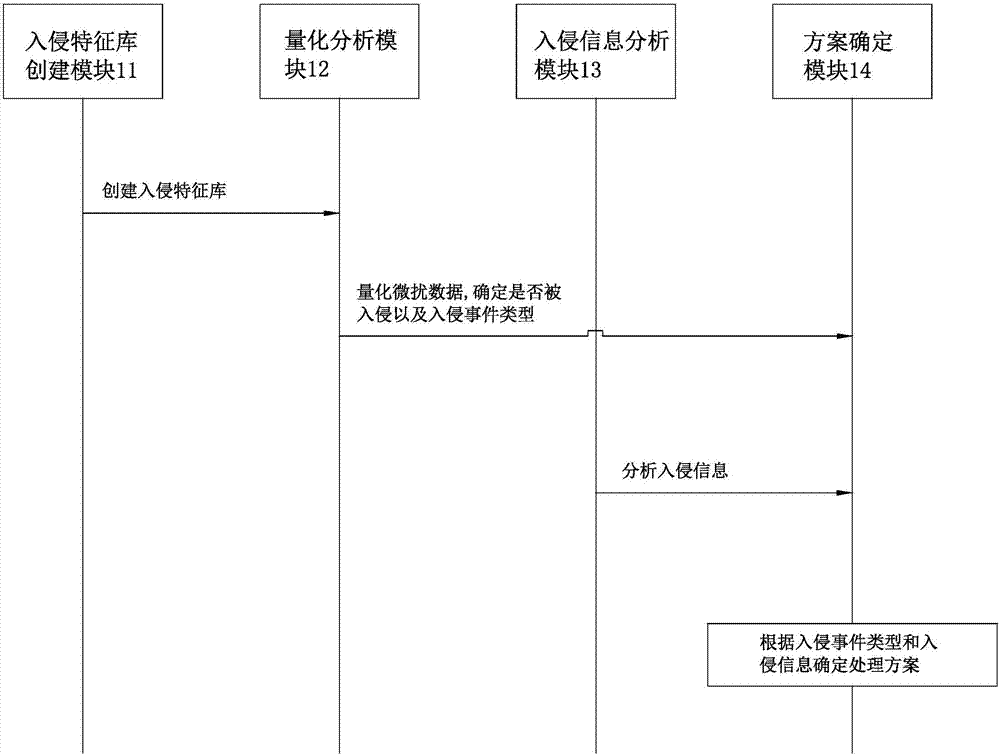
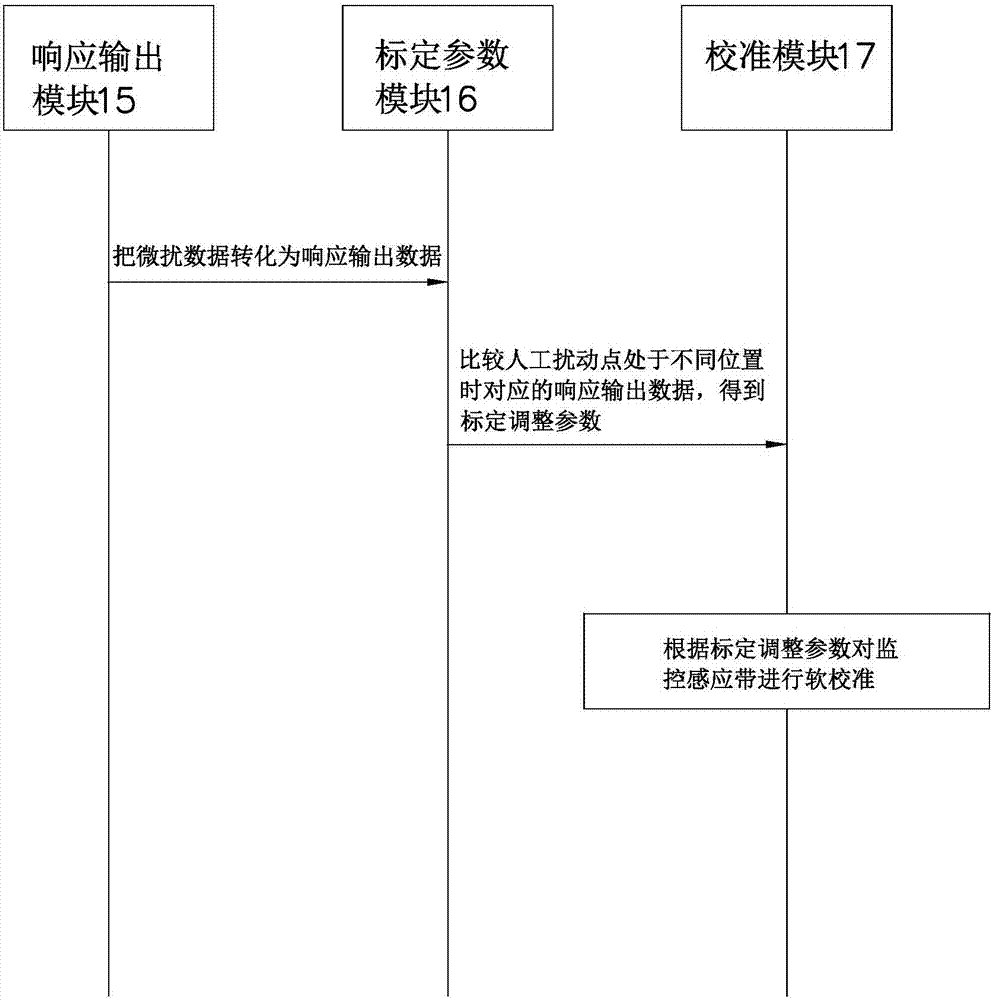
The invention relates to a wide-range perimeter security monitoring method and system. The method comprises the following steps: creating an intrusion feature library; acquiring perturbation data at the boundary of a monitored area; quantifying the perturbation data and obtaining a quantized amplitude, comparing the quantized amplitude with an intrusion data feature, and determining whether the monitored area is intruded and determining a corresponding intrusion event type; analyzing intrusion information of an intruder according to the perturbation data; and determining a processing scheme according to the intrusion event type and the intrusion information. The system comprises a monitoring induction band and a monitoring center; and the monitoring center comprises an intrusion feature library creation module, a quantification analysis module, an intrusion information analysis module and a scheme determination module. The perturbation data are acquired and processed through the above method and system, then whether the monitored area is invaded, the invasion event type and the intrusion information can be determined, so that the security of the monitored area can be ensured, thus the wide-range perimeter security monitoring method and the system provided by the invention have the advantages of being high in accuracy, good in monitoring effect and low in operation and maintenance cost and so on, and are especially suitable for wide-range security monitoring of border lines, etc..
Owner:SHENZHEN SHENGLU IOT COMM TECH CO LTD
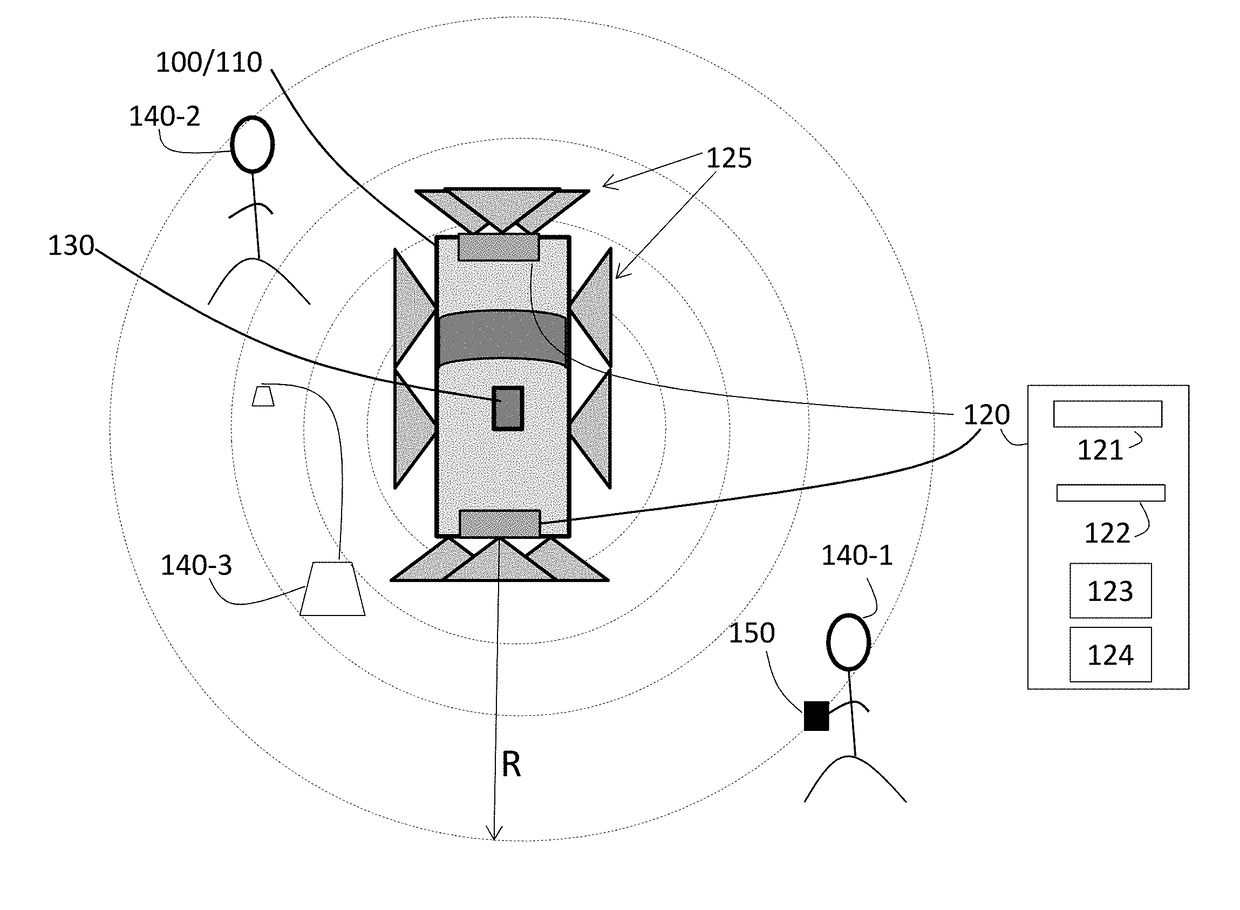
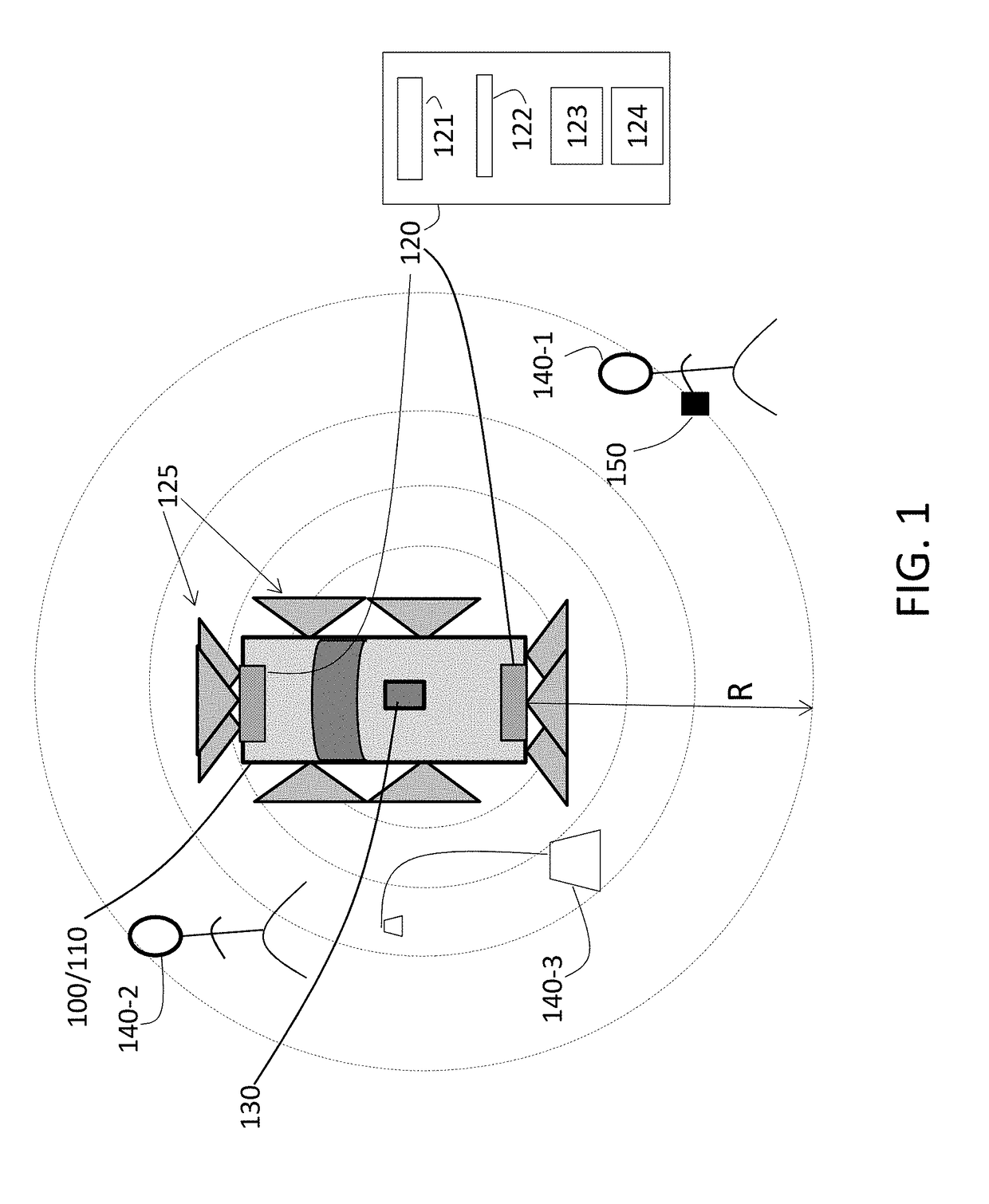
Radar-based vehicle perimeter security and control
A method and system perform perimeter security and control of a vehicle. The system includes a radar system arranged in the vehicle, a maximum range of the radar system being less than 100 meters, and a communication unit to communicate with the radar system. The system also includes a control system of the vehicle to control the platform based on the radar system. The control system dynamically controls each door of the vehicle according to a location of the communication unit relative to the platform.
Owner:GM GLOBAL TECH OPERATIONS LLC
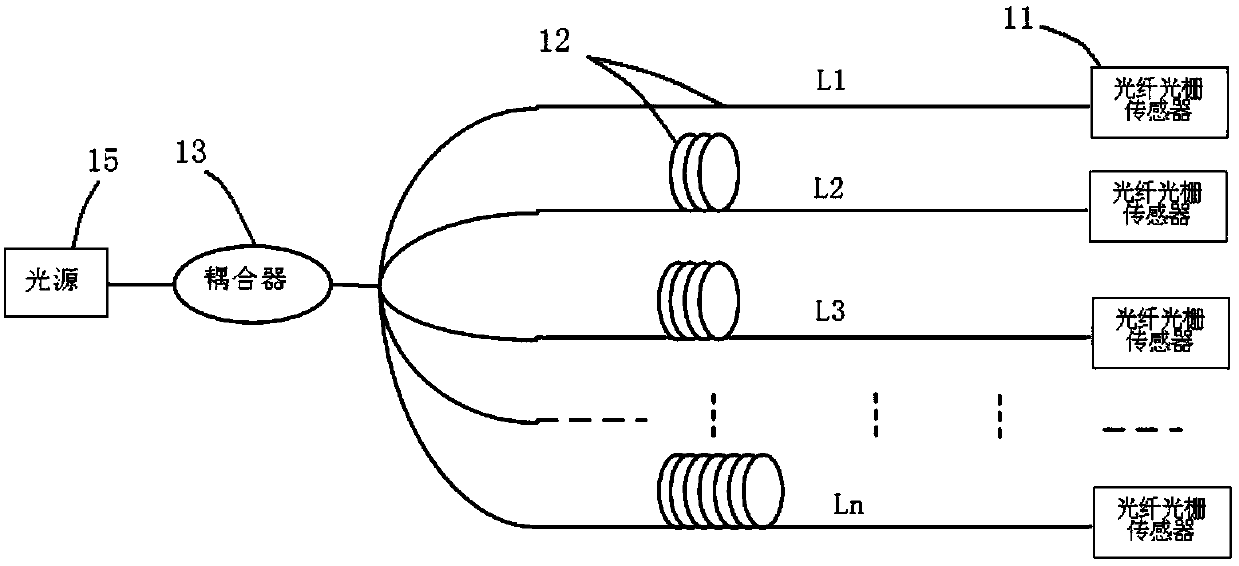
Fiber grating perimeter security and protection system and method by combination with strain information
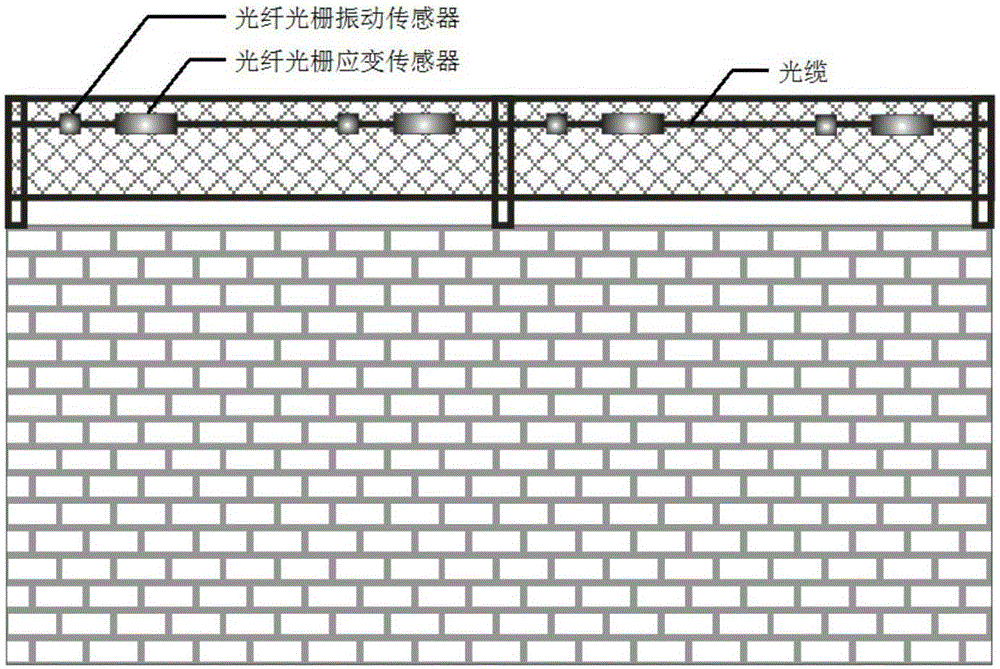
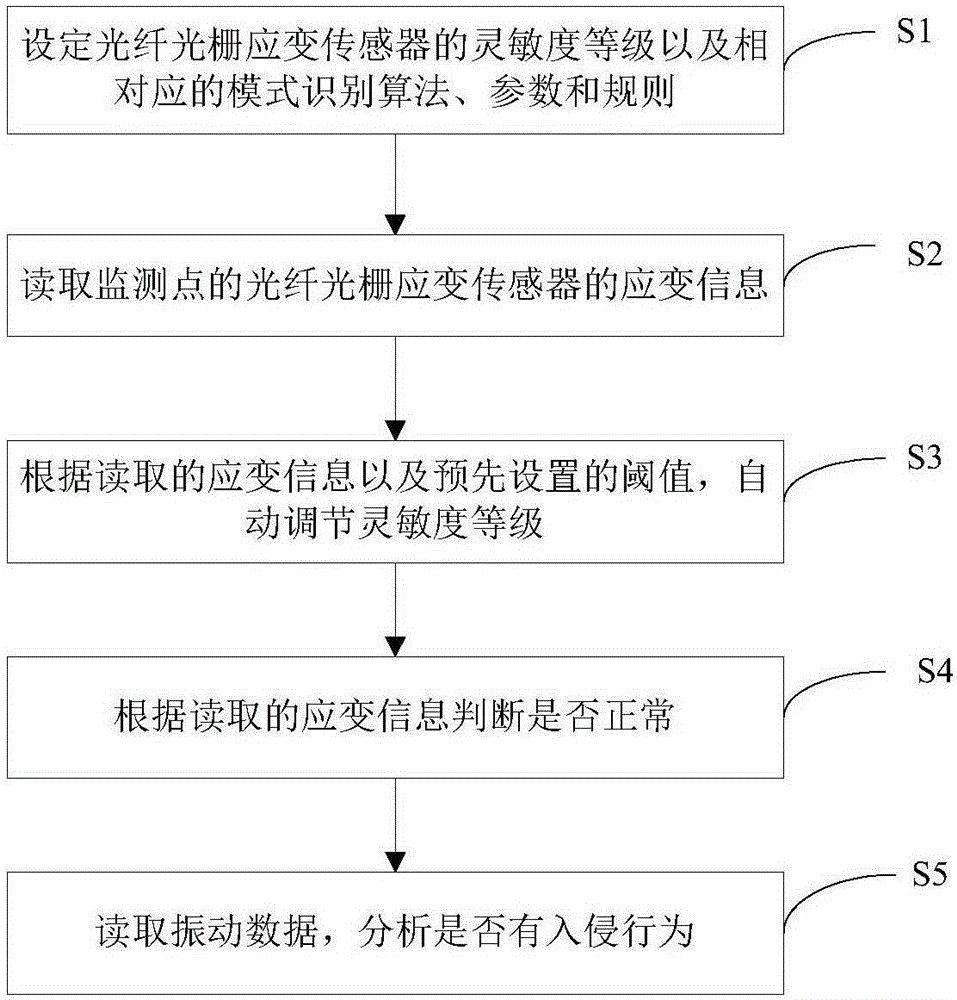
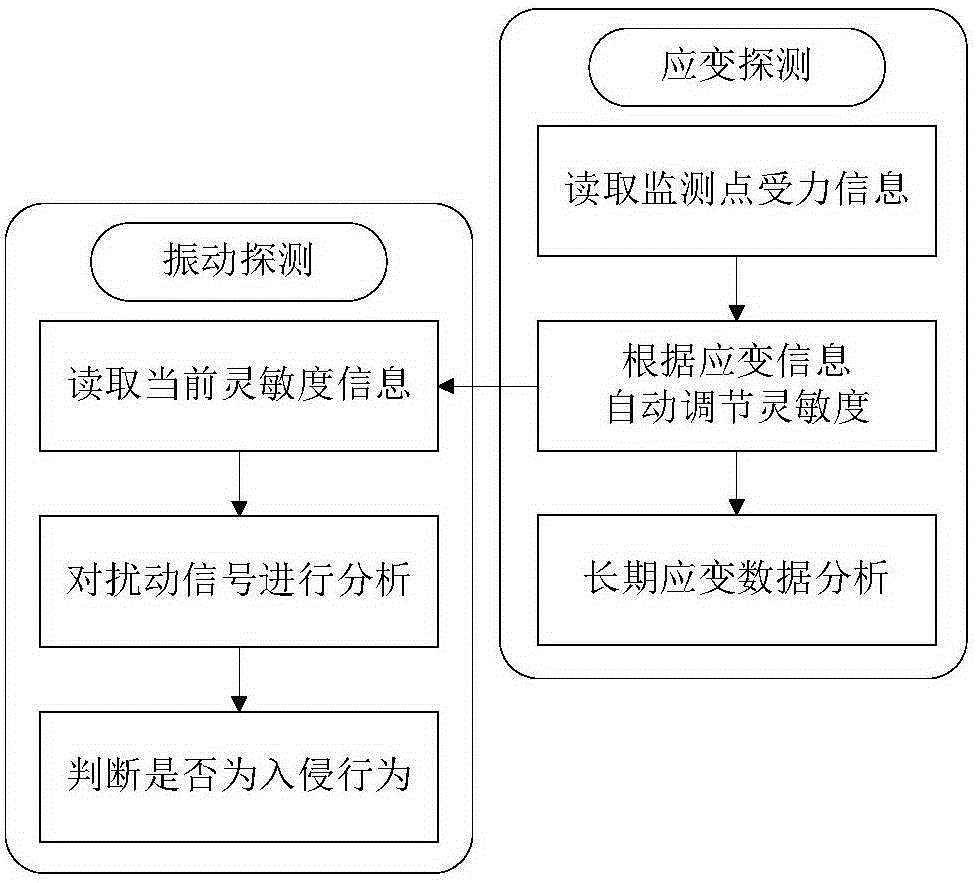
ActiveCN105243772AField passive and flexibleFlexible layoutBurglar alarm by disturbance/breaking stretched cords/wiresFiberFiber gratings
The invention discloses a fiber grating perimeter security and protection system and method by combination with strain information. The system comprises a detection cable and a strain monitoring unit. A plurality of groups of sensors are connected in series to the detection cable; and each sensor group contains at least one fibber grating strain sensor and a fiber grating vibration sensor. The strain monitoring unit is connected with the fibber grating strain sensors of all sensor groups; and strain information of the fibber grating strain sensors is read at predetermined time intervals According to the invention, the fibber grating strain sensors and the fiber grating vibration sensors are integrated into one same cable without repeated installation, thereby reducing the construction load. The strain information is used as a basis for self adjustment of the vibration sensing system, thereby effectively eliminating an adverse effect on the system due to an aging phenomenon of a rail (wall) and thus guaranteeing long-term stability and effectiveness of the vibration monitoring and alarming system.
Owner:WUHAN WUTOS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com