Fiber perimeter security intrusion event identification method and apparatus based on integrated characteristics
A technology of optical fiber perimeter security and identification method, which is applied to pattern recognition in signals, character and pattern recognition, computer parts and other directions, can solve the problems of lack of time domain information, affect practicability, and low recognition efficiency, and achieve the characteristics of Vector-reduced, high-accuracy effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
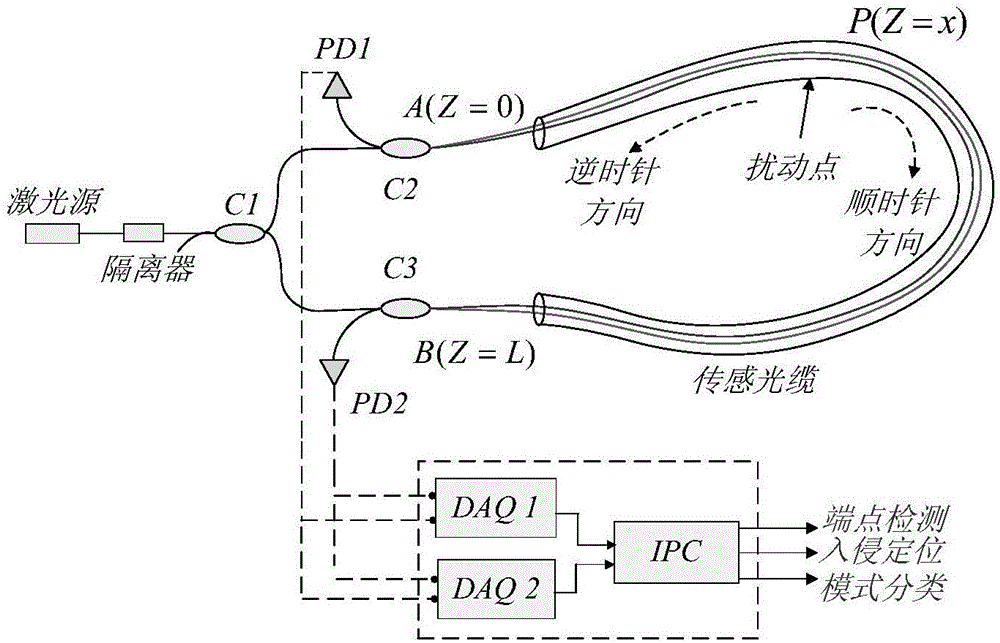
[0047] The embodiment of the present invention takes the dual Mach-Zehnder distributed optical fiber sensing system as the background, and proposes an intrusion event recognition method based on comprehensive features, see figure 1 , the method includes the following steps:
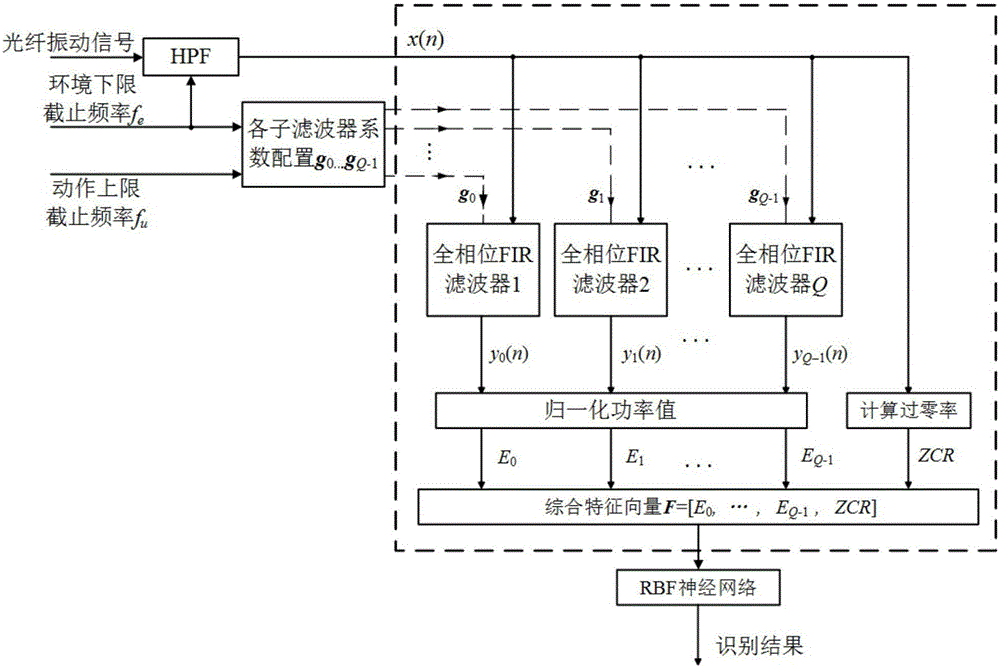
[0048] 101: Perform endpoint detection on the input disturbance signal, and determine the disturbance starting point;
[0049] 102: Feed the signal that determines the starting point of the disturbance into the all-phase filter bank [18][19][20] Each channel of each channel is separated in the frequency domain, and the normalized power value of the output signal of each channel is calculated;
[0050] 103: Synthesize the normalized power value and the time-domain zero-crossing rate (Zero-Crossing Rate, ZCR) of the entire disturbance signal to generate an eigenvector;
[0051]104: Feed feature vectors into radial basis function (RBF) neural network [21][22] Fast and high-precision identification of intr...
Embodiment 2
[0054] The scheme in embodiment 1 is further introduced below in conjunction with specific calculation formulas and examples, see the following description for details:
[0055] The structural principle of the distributed optical fiber sensing system based on the DMZI principle is as follows: figure 1 As shown, point P is the disturbance point, and the length of the sensing optical cable is L. The light emitted by the laser passes through the isolator and is divided into two beams of light by the coupler C1. These two beams of light are injected into the double Mach-Zehnder interferometer composed of C2 and C3. After that, the two beams are clockwise and The counterclockwise direction propagates in the sensing loop and interferes on the opposite coupler (C3 or C2) and outputs to the detectors PD1 and PD2. The detector converts the optical signal into an electrical signal, which is collected by the corresponding high-speed acquisition card (DataAcquisition, DAQ) after DC isola...
Embodiment 3
[0120] Below in conjunction with concrete test, accompanying drawing, and form, the scheme in embodiment 1 and 2 is carried out feasibility verification, see the following description for details:
[0121] The experiment is carried out on a DMZI distributed optical fiber sensing system with a laser source of 1550nm distributed feedback laser and a light intensity of 3.5mV. The total length of the sensing optical cable is 2.25km, and the sampling rate of DAQ1 is f s =10kHz, recording time is 3s. 480 data collections were performed on 4 types of common intrusion events: climbing fences, knocking on optical cables, shaking and stealing shears, and the number of repetitions for each type of intrusion events was 120 times.
[0122] The selection of the feature vector length is mainly due to two considerations: on the one hand, considering the identification of P = 4 types of intrusion events, in order to ensure the accuracy of pattern recognition and classification, the feature ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com