System and method for passive assessment of industrial perimeter security
A technology for network security and security assessment, applied in transmission systems, computer security devices, instruments, etc., can solve the problems of attack vectors and increased risks of malicious penetration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
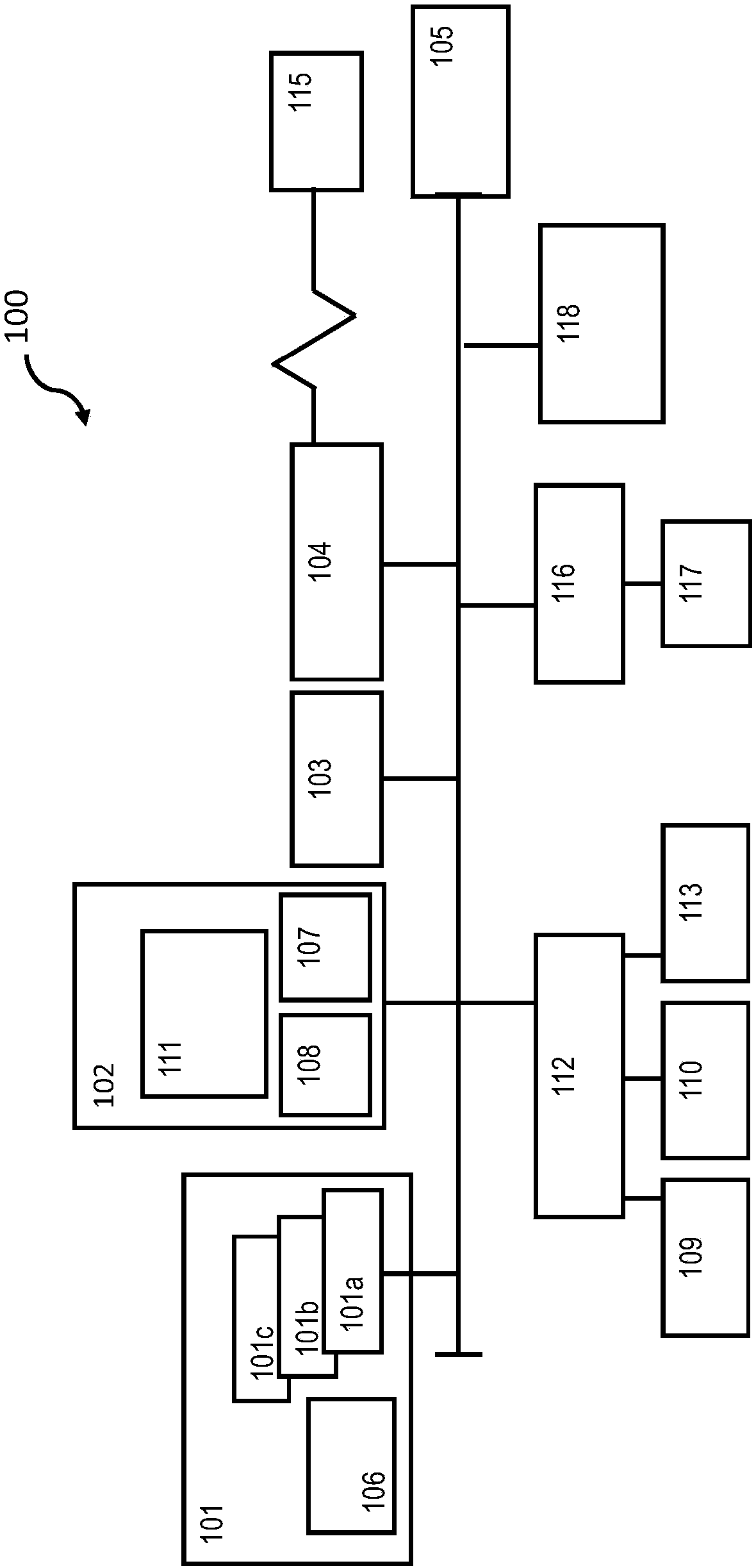
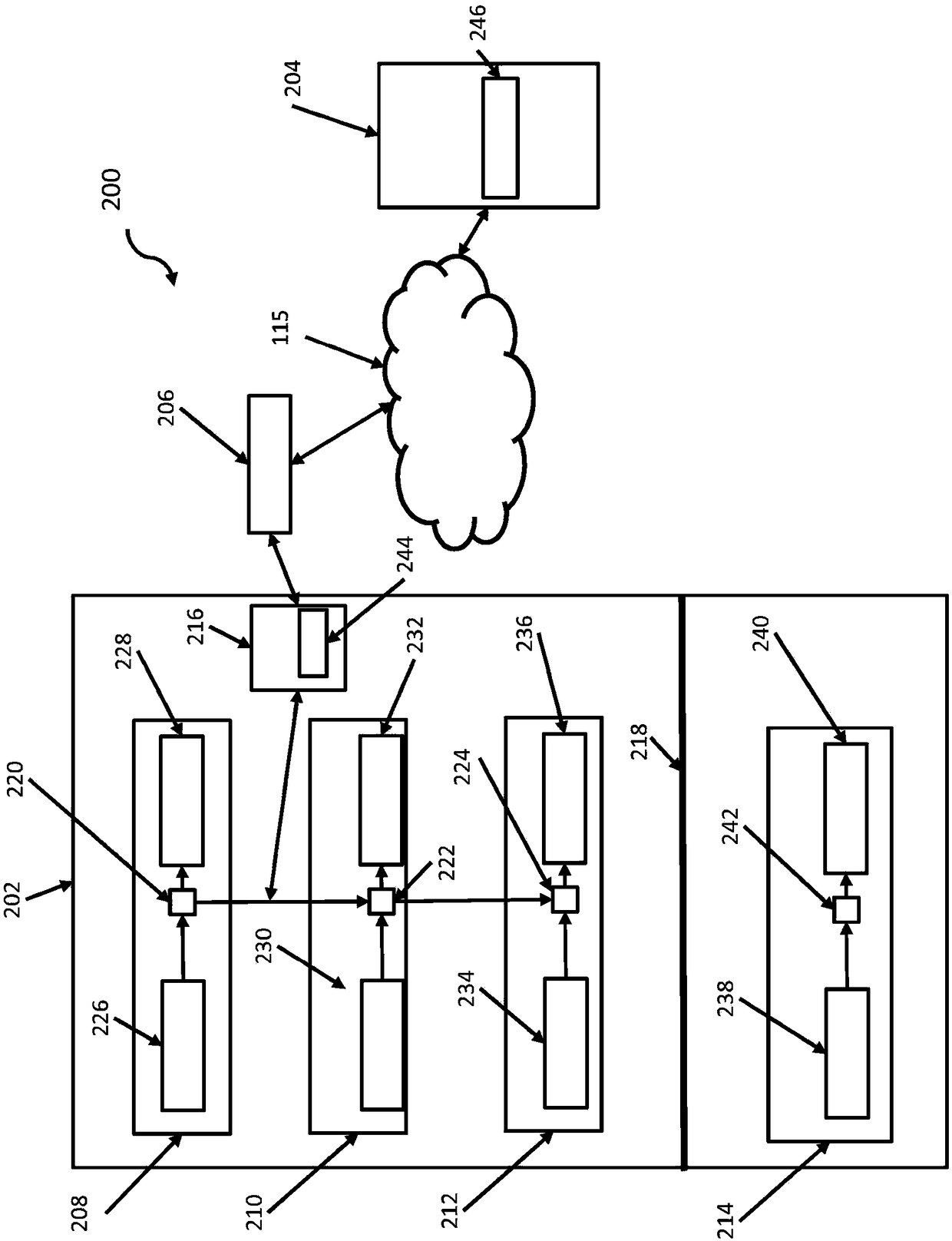
[0019] figure 1 A block diagram of a computer system 100 (hereinafter "computer 100") for practicing the embodiments described herein is shown. The methods described herein can be implemented in hardware, software (eg, firmware), or a combination thereof. In exemplary embodiments, the methods described herein are implemented in hardware and may be part of the microprocessor of a special purpose or general purpose digital computer, such as a personal computer, workstation, minicomputer or mainframe computer. Computer 100 may thus be implemented as a general purpose computer. In another exemplary embodiment, the methods described herein are implemented as part of a mobile device, such as a mobile phone, personal data assistant (PDA), tablet computer, or the like.
[0020] In an exemplary embodiment, in terms of hardware architecture, such as figure 1 As shown, computer 100 includes processor 101 . The computer 100 also includes a memory 102 coupled to the processor 101 and o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com