Method to protect software against unauthorized use
An unlicensed, software-based technology, applied in digital data processing components, internal/peripheral computer component protection, instruments, etc., can solve problems, connect hardware conflicts, limit high-value software applications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
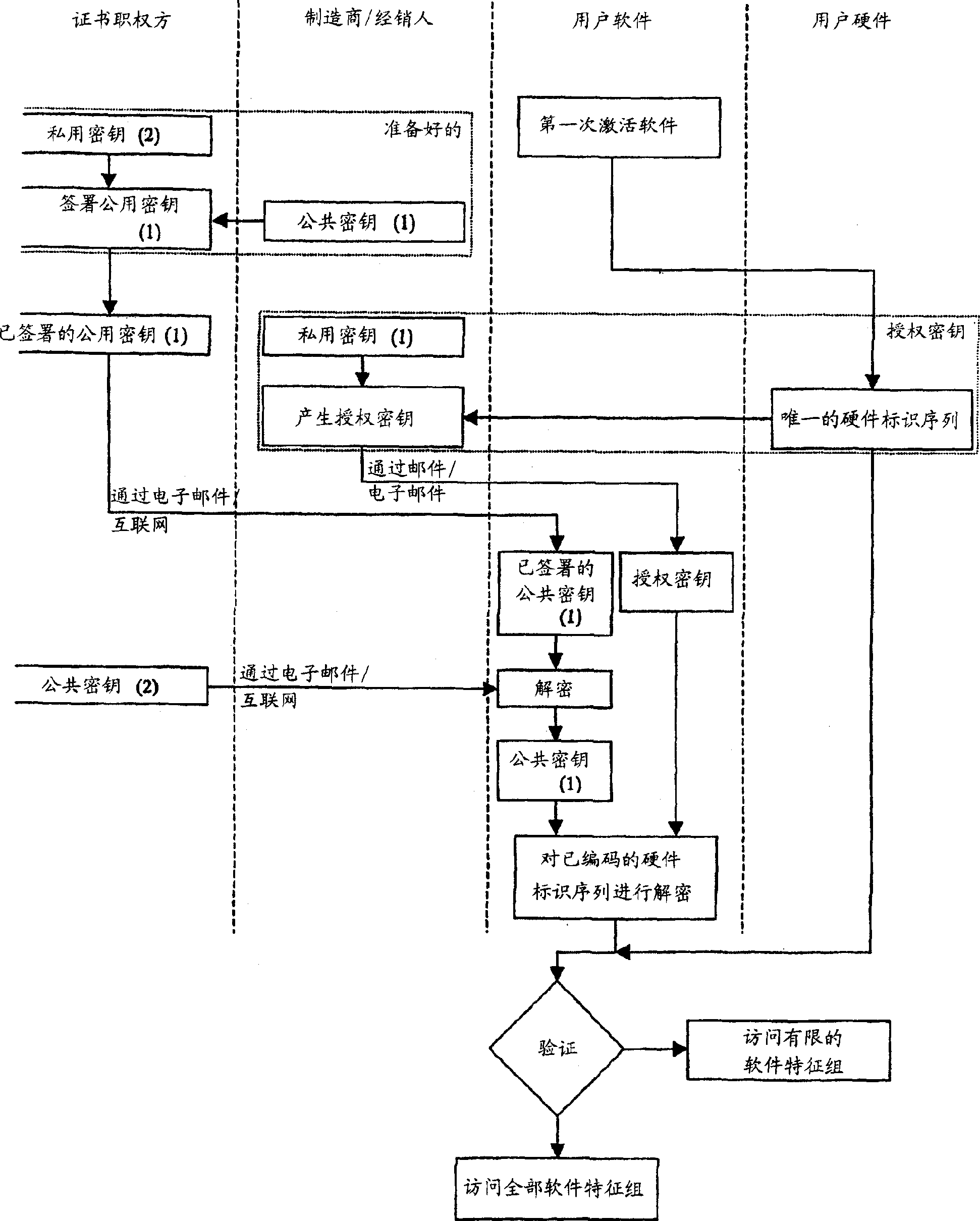
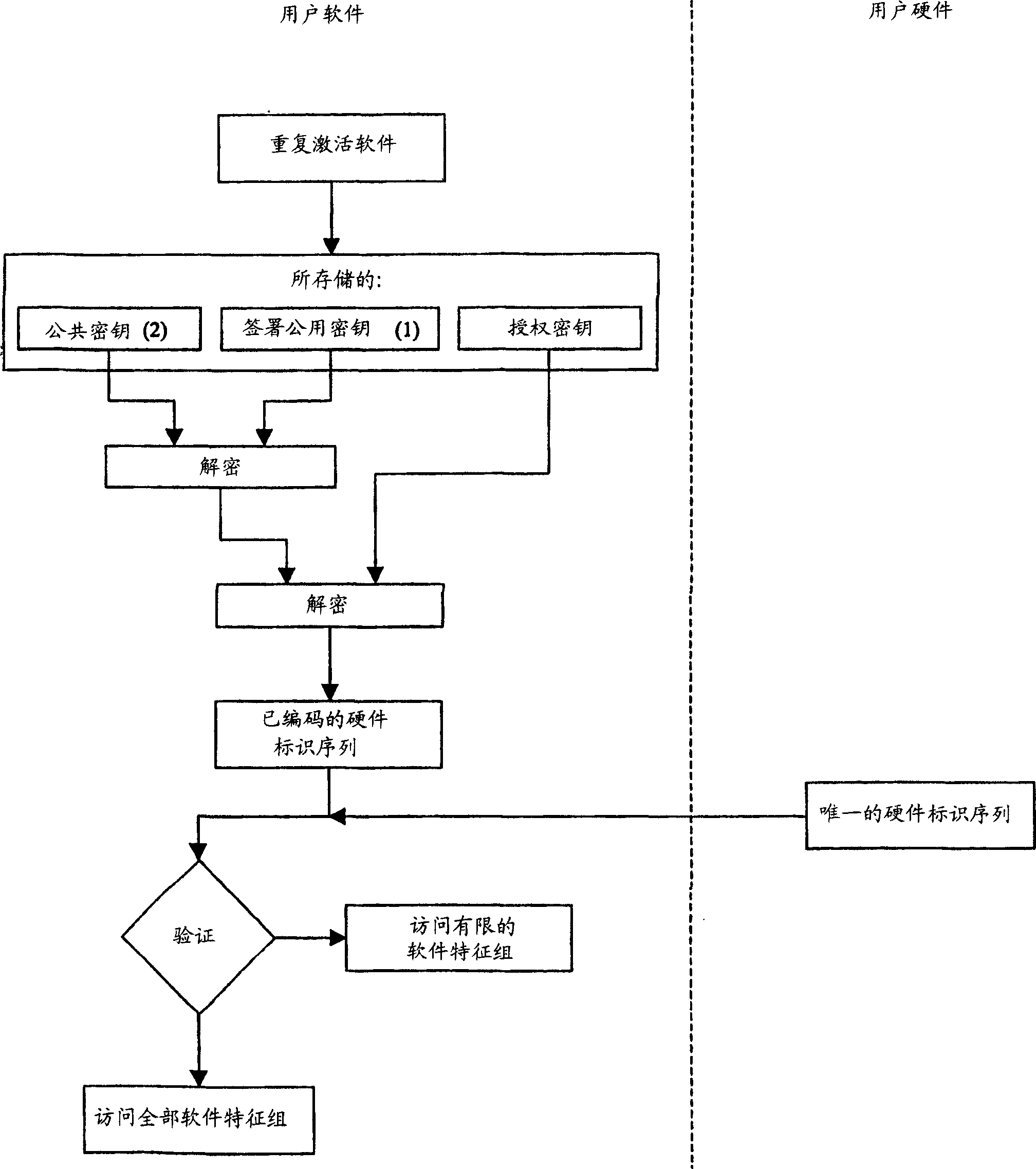
[0043] figure 1 A flowchart is given. The flowchart shows an embodiment of the method according to the invention. The given embodiment applies the aforementioned public key encryption method combining the signed public key and the certificate respectively.
[0044] The following will describe typical exemplary solutions to teach the advantages of software protection methods that prevent unauthorized use. Use the online store of the manufacturer or distributor through the Internet or use the traditional store to purchase hardware equipment and corresponding software. If the purchase is made through Internet contact information, then submit the e-mail address or e-mail address to the seller. Put the hardware equipment and the corresponding software together and send it to the buyer. For example, each hardware identification number can be obtained through the serial number of the hardware product. Link the unique hardware identification number and serial number through the database...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com