Patents
Literature
147results about How to "Update flexible" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
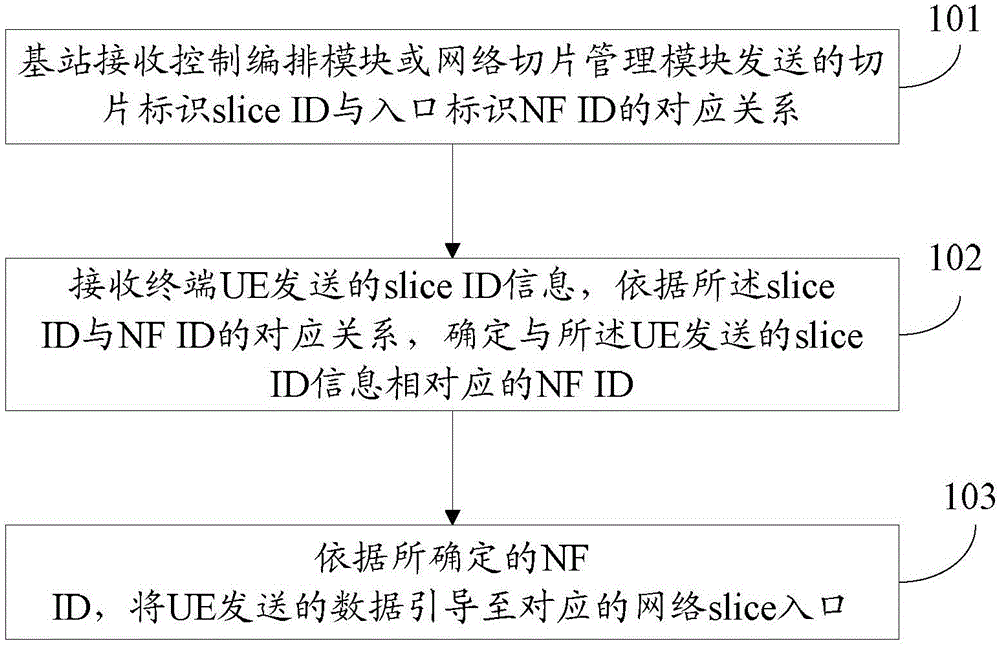
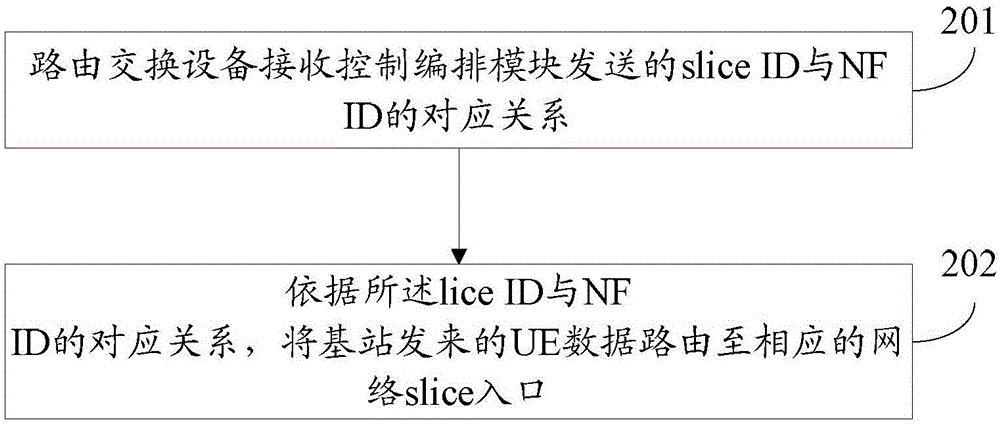
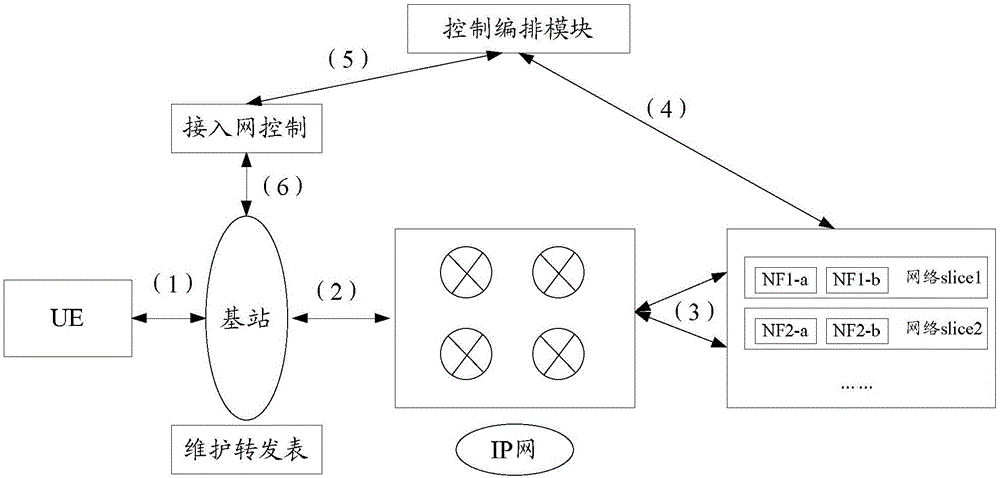
Network slice management and selection method and system, base station and route switching equipment
The invention discloses a network slice management and selection method and system, a base station and route switching equipment. The network slice management and selection method comprises the steps of receiving a corresponding relation, which is sent by a control arrangement module, between slice IDs and NF IDs, or querying a corresponding NF ID according to a slice ID; receiving slice ID information sent by UE (User Equipment), and determining an NF ID corresponding to the slice ID information sent by the UE according to the corresponding relation between the slice IDs and the NF IDs; guiding data sent by the UE to a corresponding slice entry according to the determined NF ID; and performing network slice addition, update and deletion through the control arrangement module.
Owner:CHINA MOBILE COMM GRP CO LTD
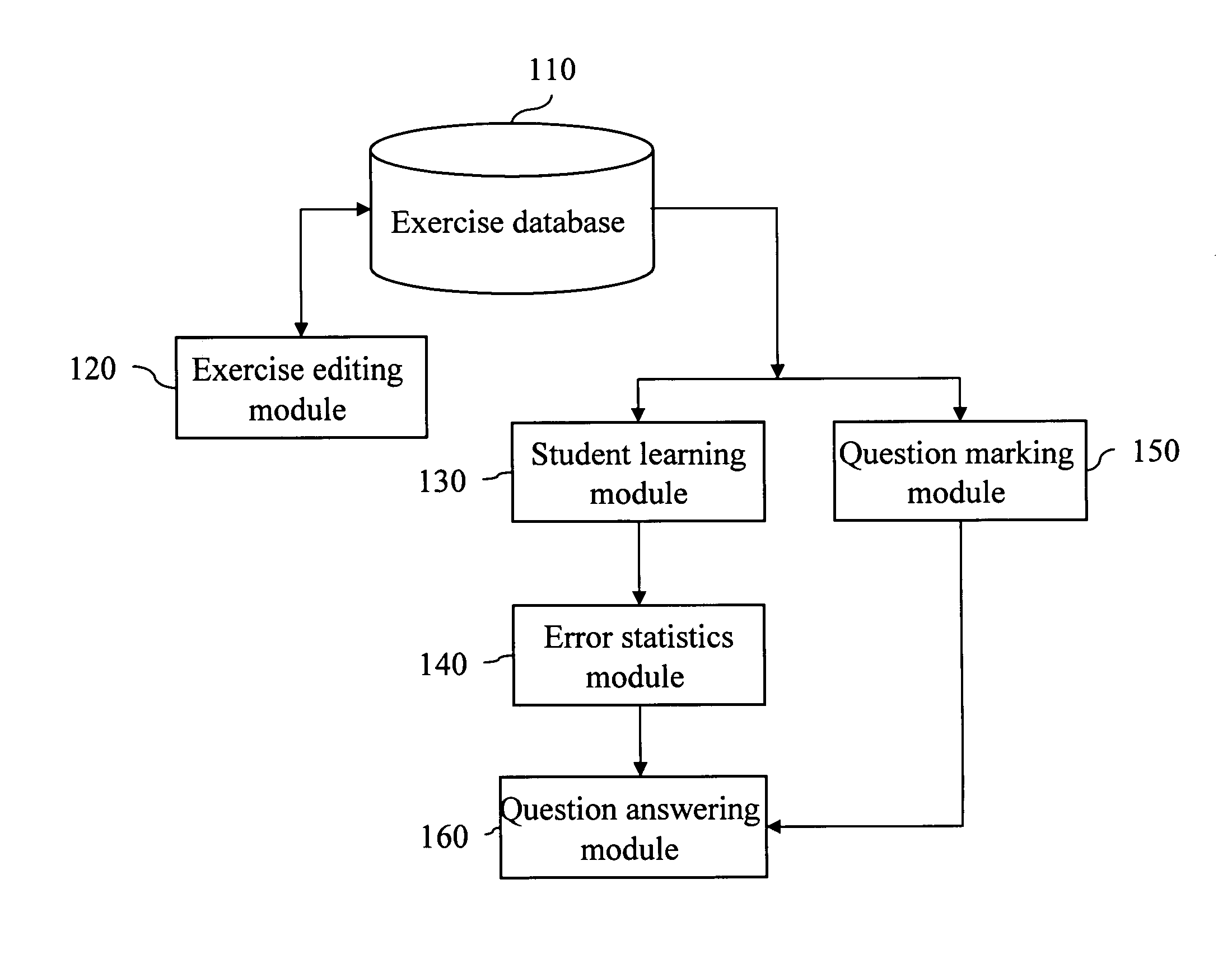
Remote instruction system and method
InactiveUS20060141438A1Update flexibleImprove convenienceElectrical appliancesMechanical appliancesQuestion answerComputer science
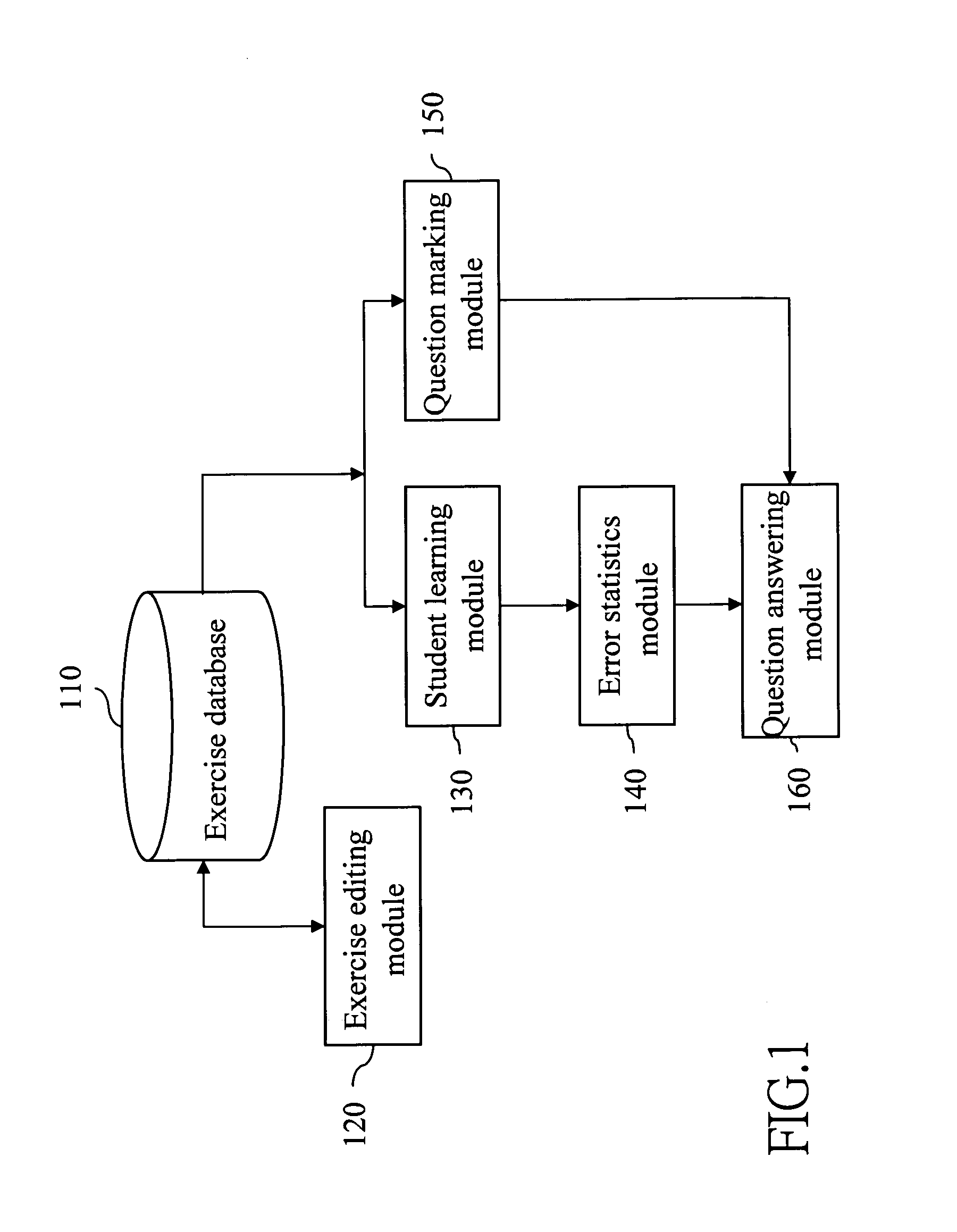
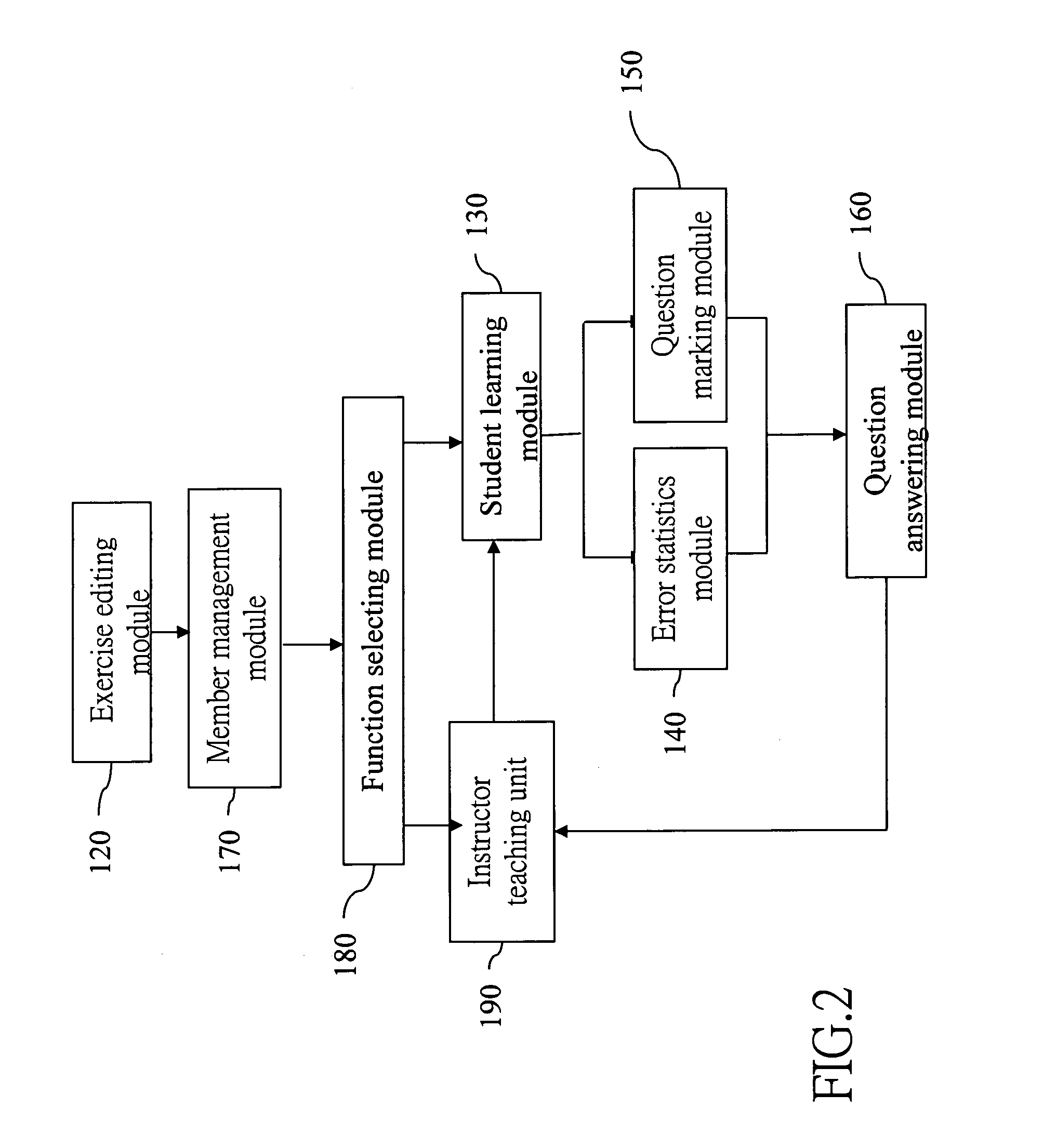
A remote instruction system and method includes an exercise editing module for instructor ends to edit exercises in an exercise database and a student learning module to access the exercises in the exercise database and display the exercises at student ends. Students learn and test based on the exercises. An error statistics module is provided to mark questioned exercises based on statistics results. A question marking module receives the questioned exercises marked by students, and a question answering module is linked to the instructor ends and student ends to implement teaching activities and enable the instructor to teach the questioned exercises and answer student's questions.
Owner:INVENTEC CORP
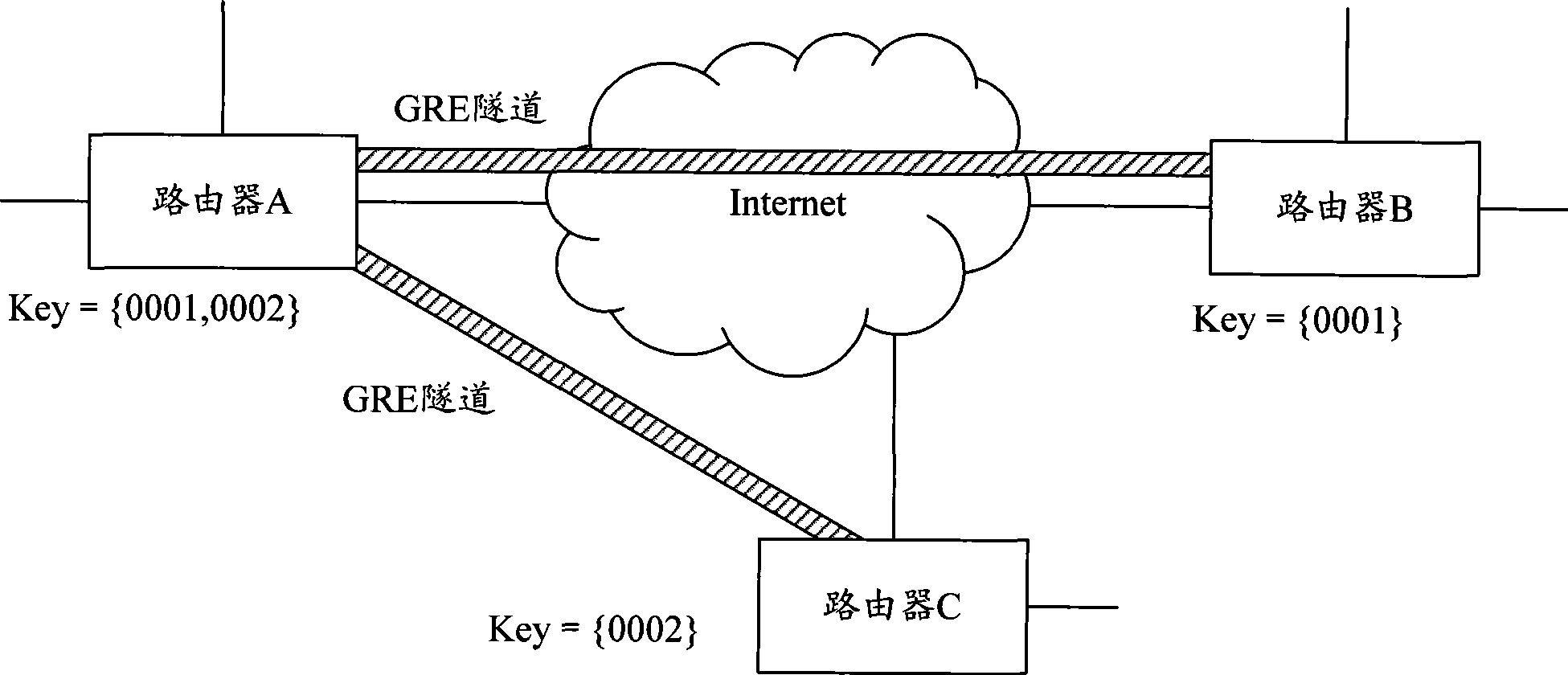
Dynamic establishing method and device for GRE tunnel
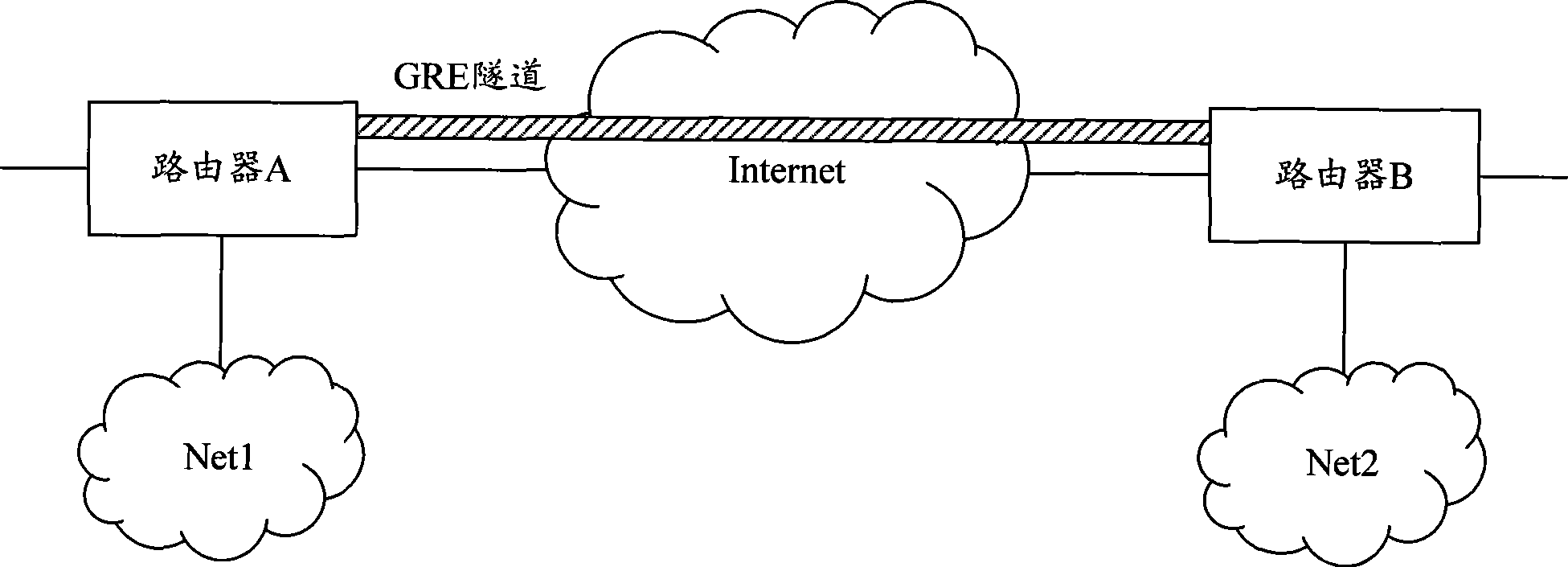
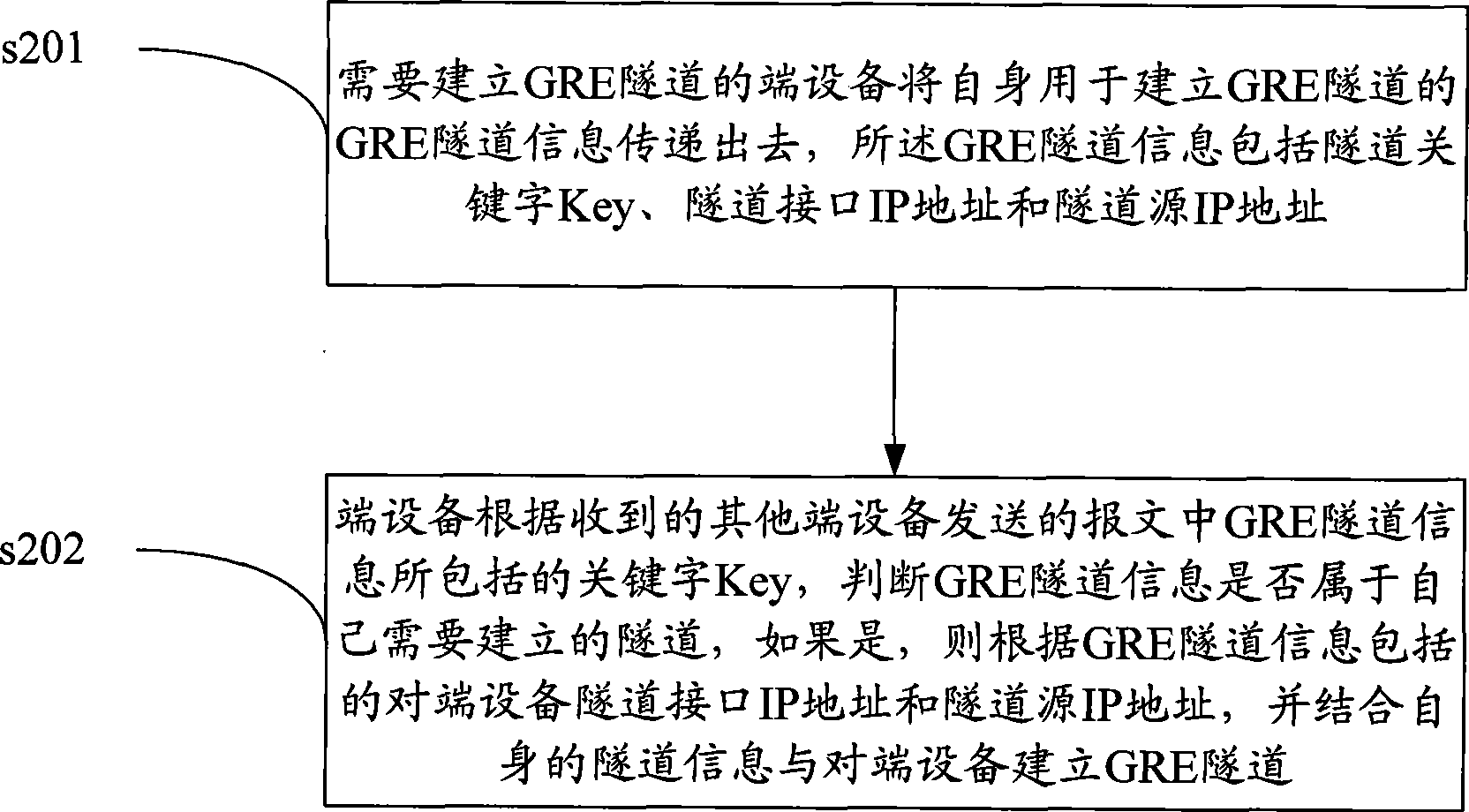
The invention discloses a method and apparatus for dynamically building GRE tunnel. The method comprises the steps that: the end apparatus needing to build GRE tunnel transmitting the GRE tunnel information for itself to build the GRE tunnel; the GRE tunnel information comprising tunnel keyword Key, tunnel interface IP address and tunnel source IP address; the end apparatus judges whether the GRE tunnel information belongs to the tunnel built by itself according to keyword Key comprised in the GRE tunnel information in the message sent by other end apparatuses; if it is, the GRE is built according to the end-to-end apparatus tunnel interface IP address and tunnel source IP address comprised by the GRE tunnel information combining with the tunnel information and the end-to-end apparatus. Using the invention can dynamically build and maintain GRE tunnel and detect and adjust GRE tunnel state in real-time between the apparatuses in two ends of GRE under the condition that the IP address of two ends of GRE tunnel dynamically changes, which makes the building and maintenance of GRE tunnel be more flexible.
Owner:NEW H3C TECH CO LTD
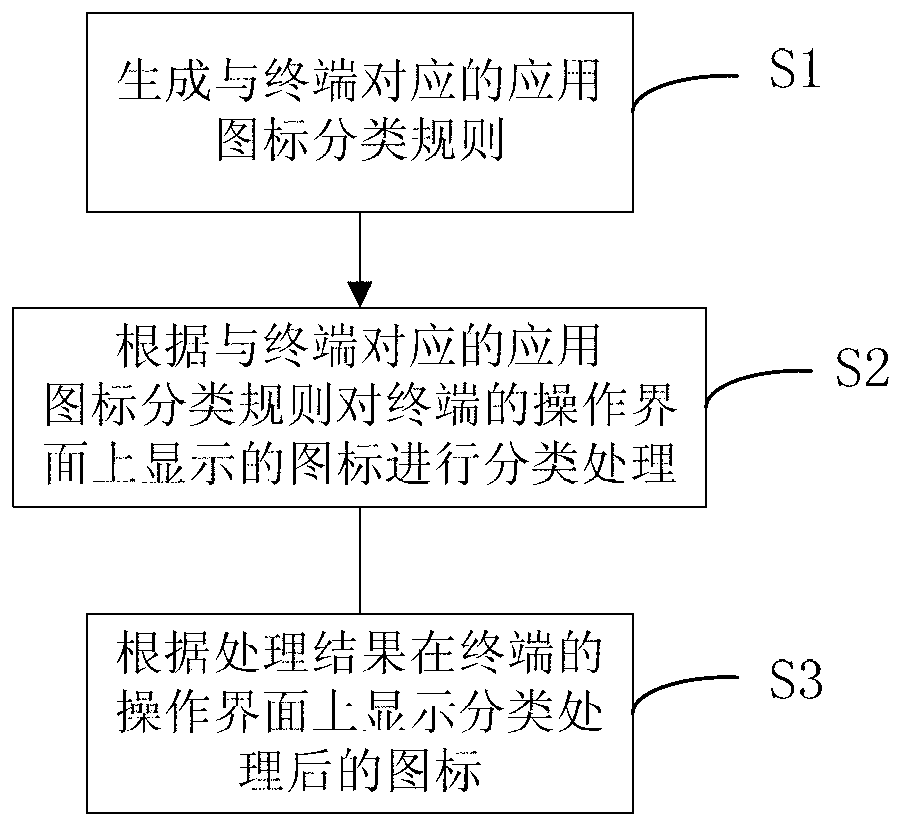
Method and device of classifying icons of terminal operation interface
InactiveCN103164114ASolve operational problemsSolve efficiency problemsInput/output processes for data processingComputer engineeringComputer science
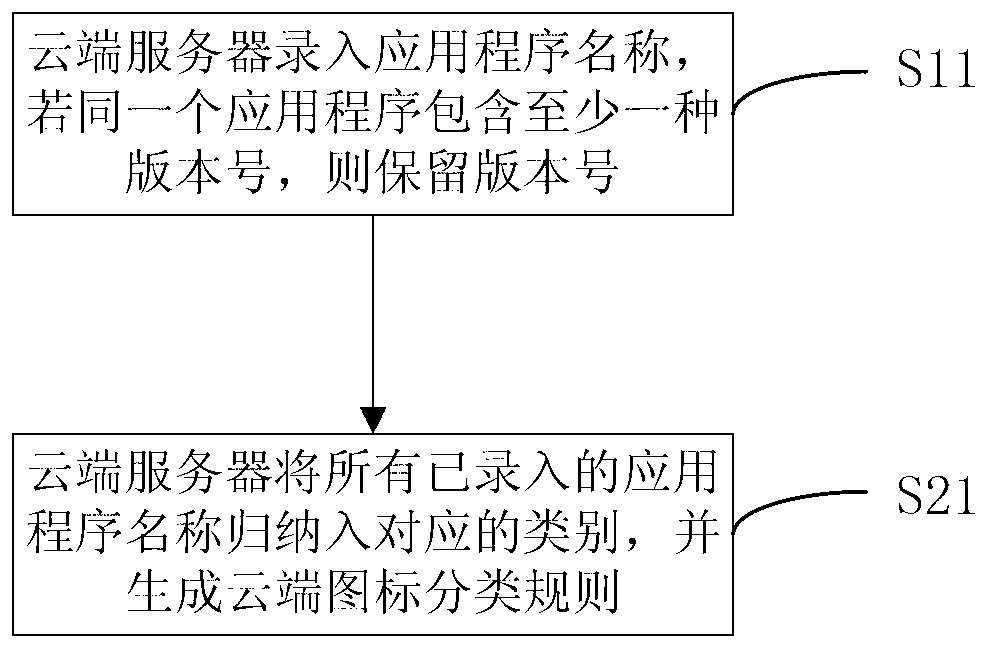
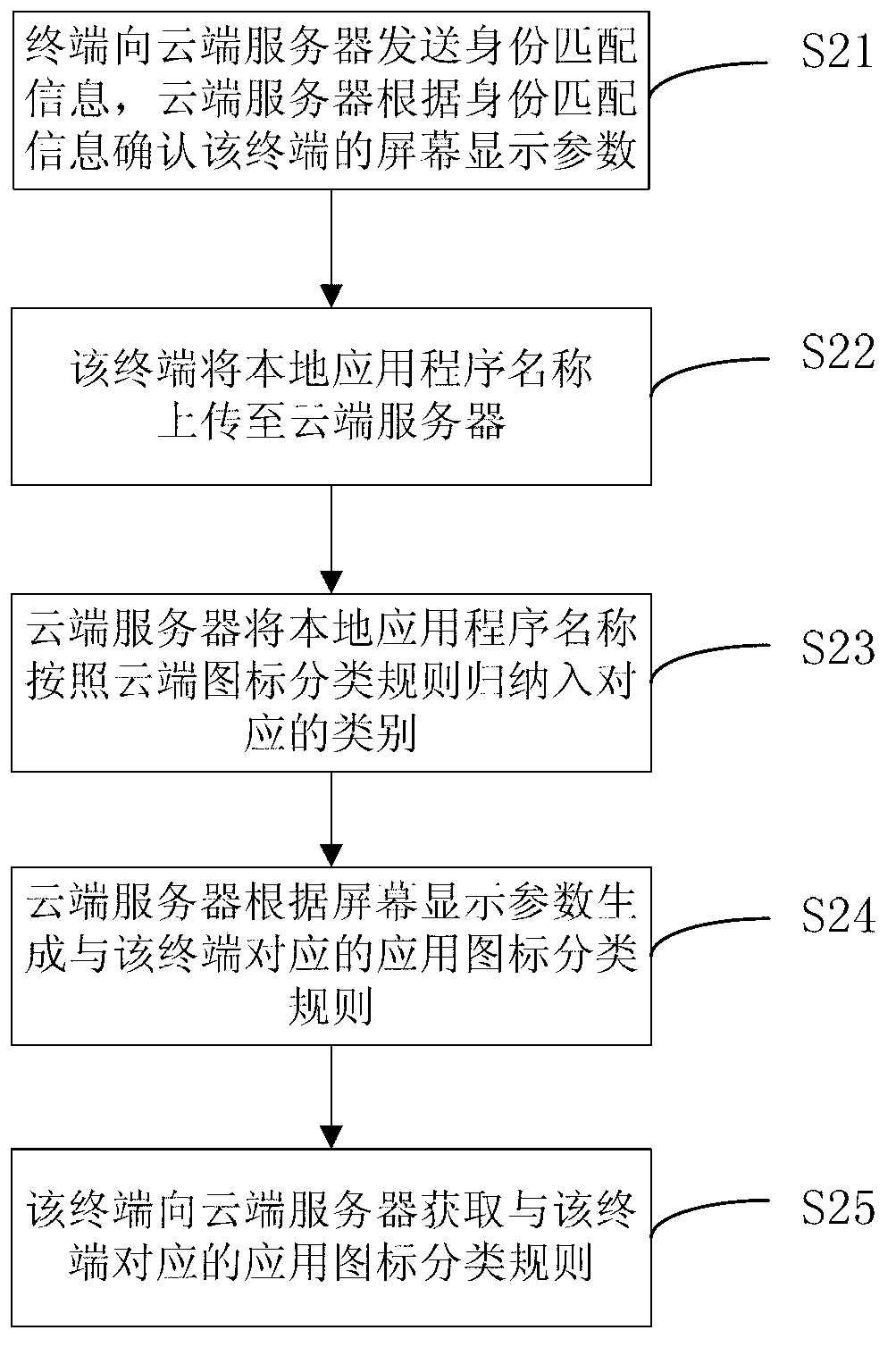
The invention discloses a method of classifying icons of a terminal operation interface. The method comprises the following steps: generating an application icon classifying rule corresponding to the a terminal, carrying out classifying processing on the icons displayed on the operation interface of the terminal according to the application icon classifying rule corresponding to the terminal, and displaying the icons after the classifying processing on the operation interface of the terminal according to a processing result. Due to the fact that a cloud server is used, an input rule can be flexibly and fast updated, and yet a local terminal cannot achieve the updating. In addition, a multi-screen thumbnail provides more classifying displaying modes, and is independent of the limit of a traditional thumbnail. At the same time, the problems that a specific software mode is not visualized in operation and local processing is low in efficiency are solved, and the classifying operation of application icons is enabled to be simple and fast.
Owner:DONGGUAN YULONG COMM TECH +1
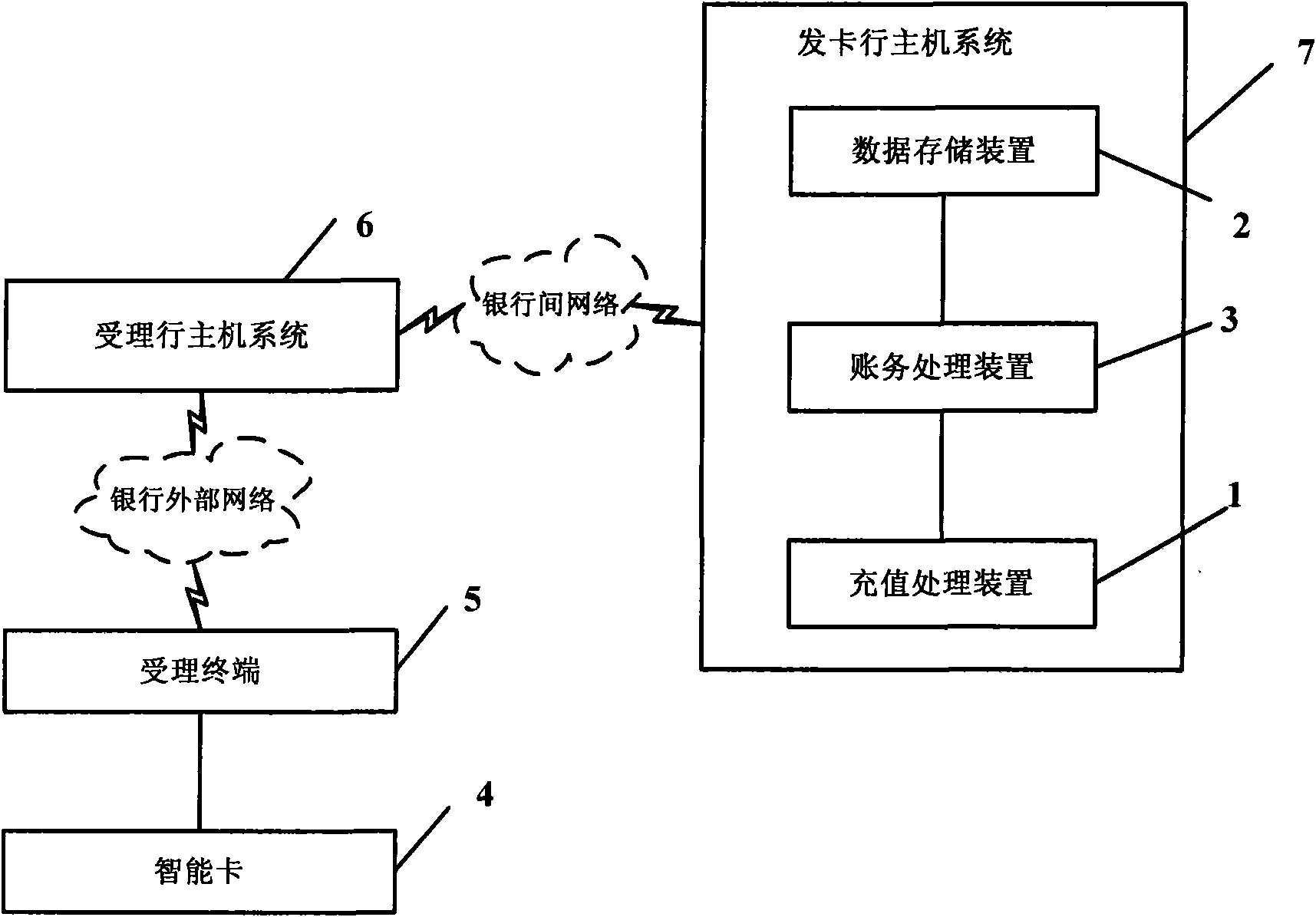
System and method for realizing rapid payment based on bank intelligent card
ActiveCN101923754AGuaranteed to be trueGuaranteed validityComplete banking machinesCoded identity card or credit card actuationIssuing bankComputer terminal
The invention discloses a system for realizing rapid payment based on a bank intelligent card, comprising an issuing bank host system (7), an accepting bank host system (6), an accepting terminal (5) and an intelligent card (4) having the function of rapid and safe payment, wherein the issuing bank host system (7) and the accepting bank host system (6) are connected through an interbank network, the accepting bank host system (6) and the accepting terminal (5) are connected through an external network of a bank, and the accepting terminal (5) and the intelligent card (4) are connected in a contact or noncontact type. The invention simultaneously discloses a method for realizing rapid payment based on the bank intelligent card. The invention overcomes the defects at the aspects of the payment speed, the communication cost and the safety risk of the traditional bank card during payment and has the advantages of rapid transaction, high safety and convenient implementation.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
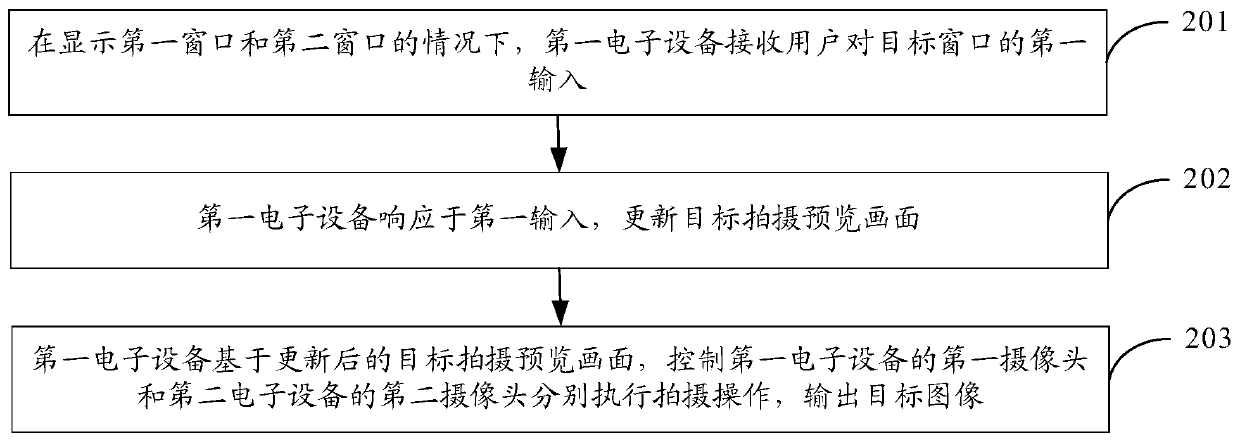
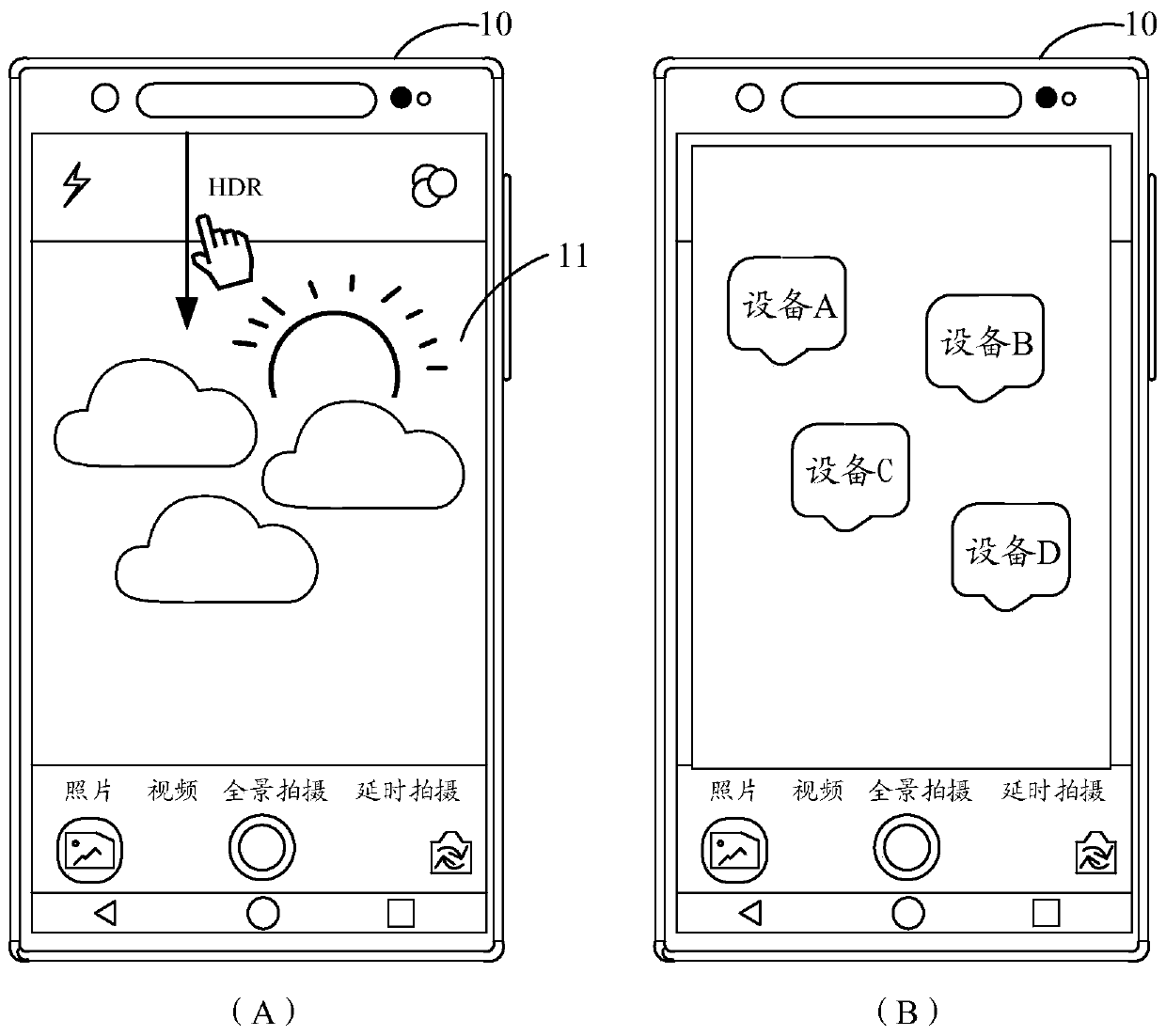
Shooting method and electronic equipment
PendingCN111083379AInput flexibleUpdate flexibleTelevision system detailsColor television detailsImage synthesisEngineering
An embodiment of the invention discloses a shooting method and electronic equipment, relates to the technical field of communication, and can solve the problem that an image shot by the electronic equipment is single. The method comprises the steps that under the condition that a first window and a second window are displayed, first input of a user to a target window is received, the first windowis used for indicating a first shooting preview picture of first electronic equipment, the second window is used for indicating a second shooting preview picture of second electronic equipment, and the target window comprises the first window and / or the second window; a target shooting preview image is updated in response to the first input, the target shooting preview image comprising a first shooting preview image and / or a second shooting preview image; a first camera of the first electronic equipment and a second camera of the second electronic equipment are controlled to execute shooting operation respectively based on the updated target shooting preview picture, and a target image is output, wherein the target image is an image obtained by synthesizing an image corresponding to the first shooting preview image and an image corresponding to the second shooting preview image.
Owner:VIVO MOBILE COMM HANGZHOU CO LTD
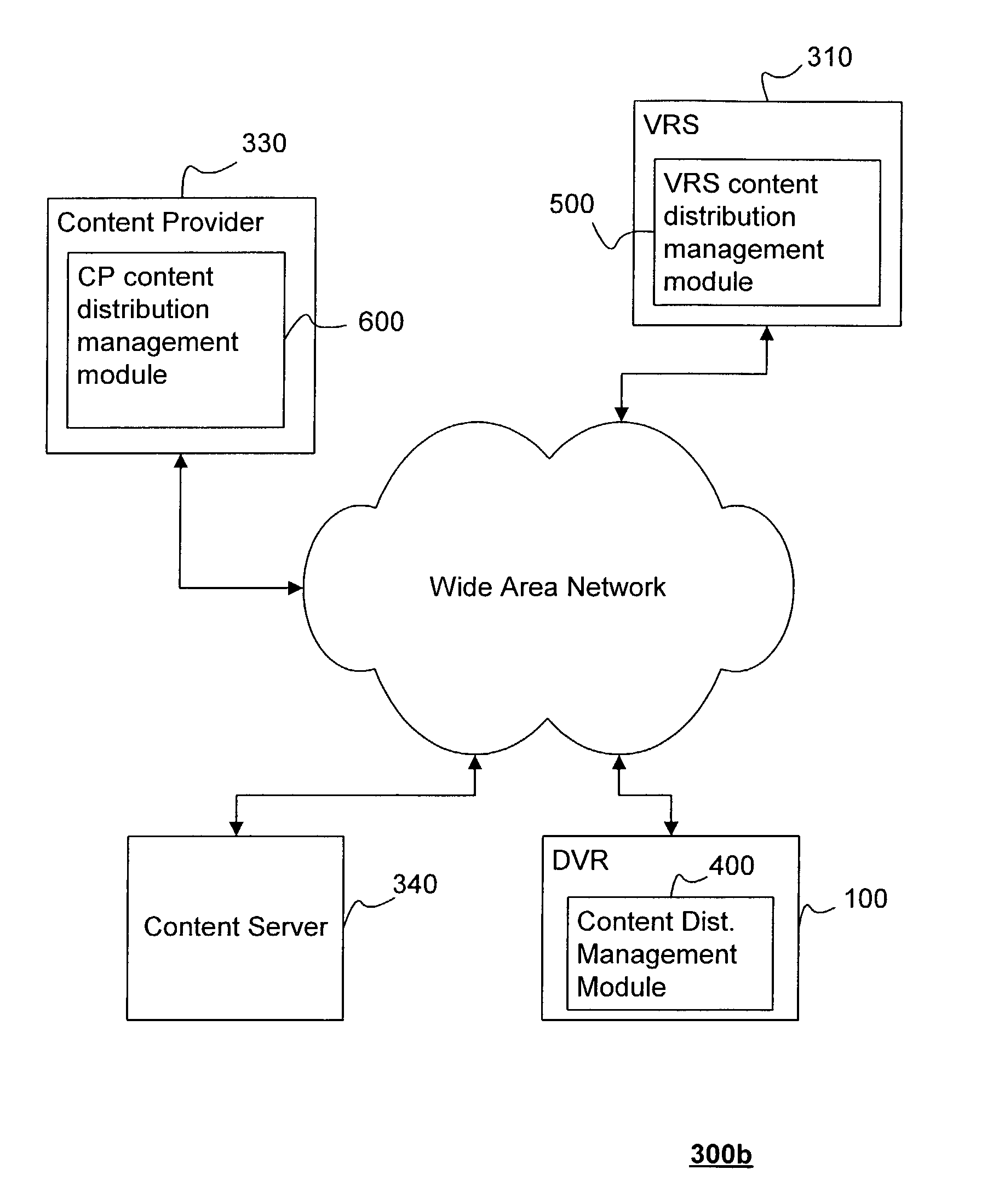
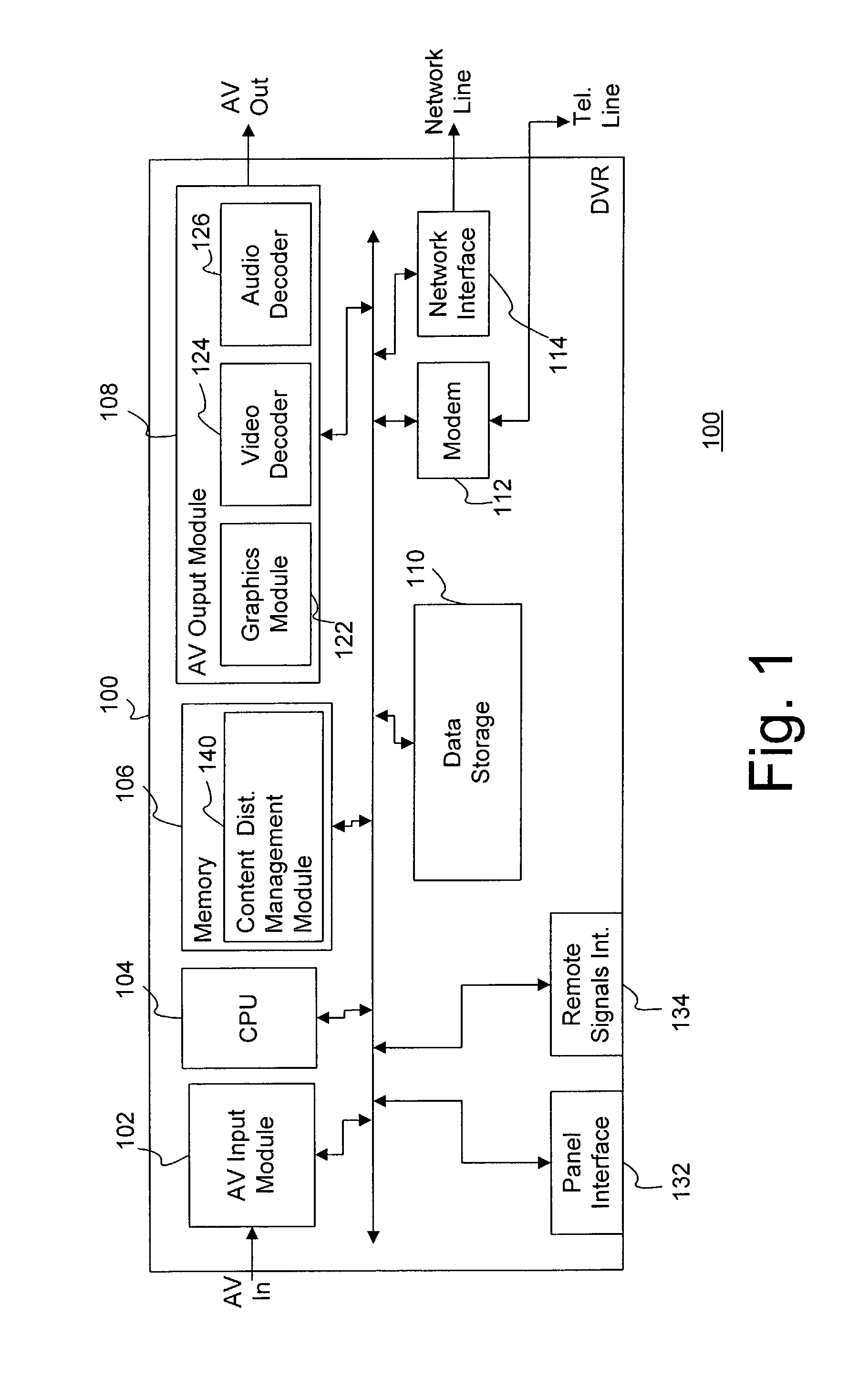
Network video unit
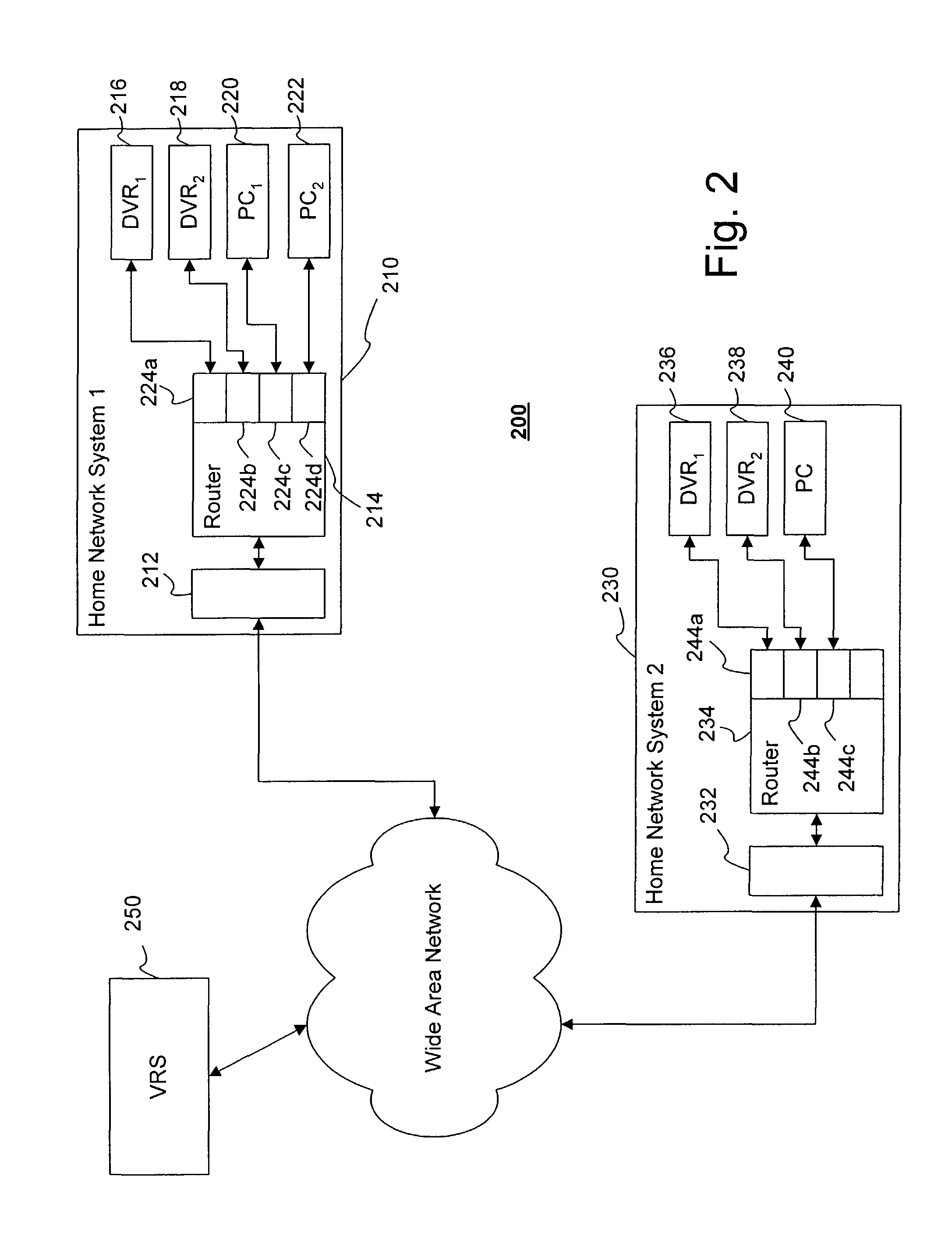
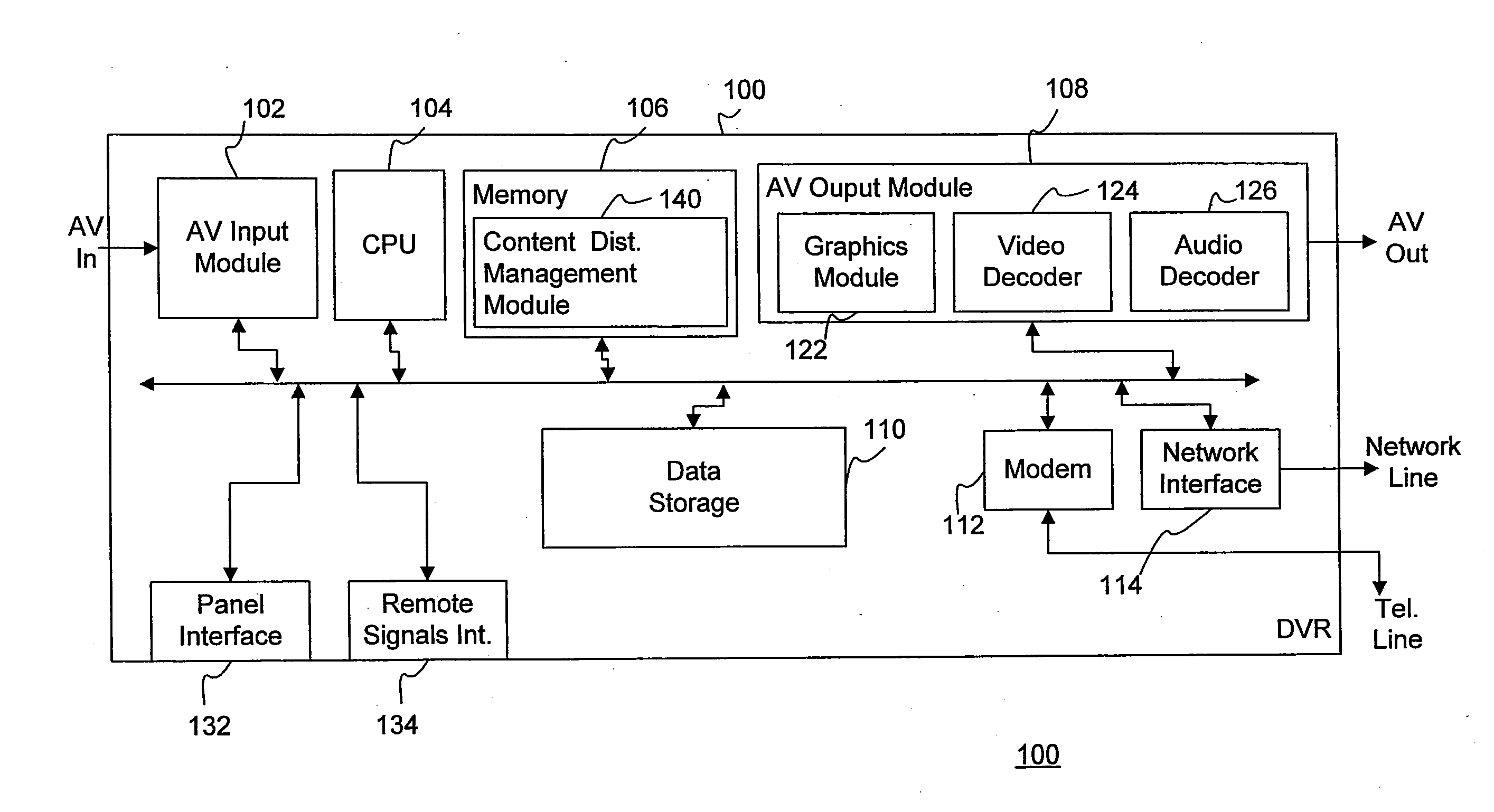
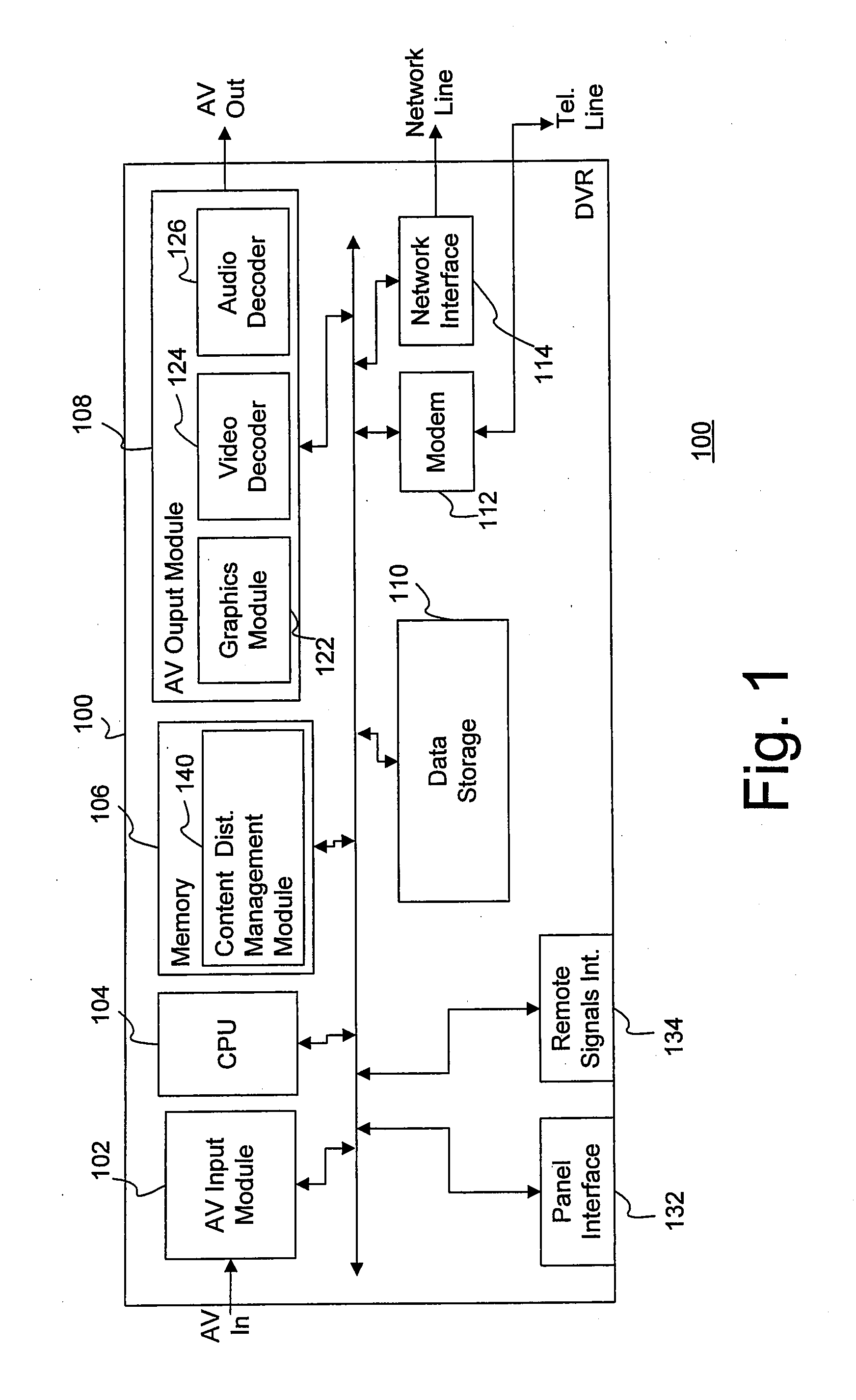
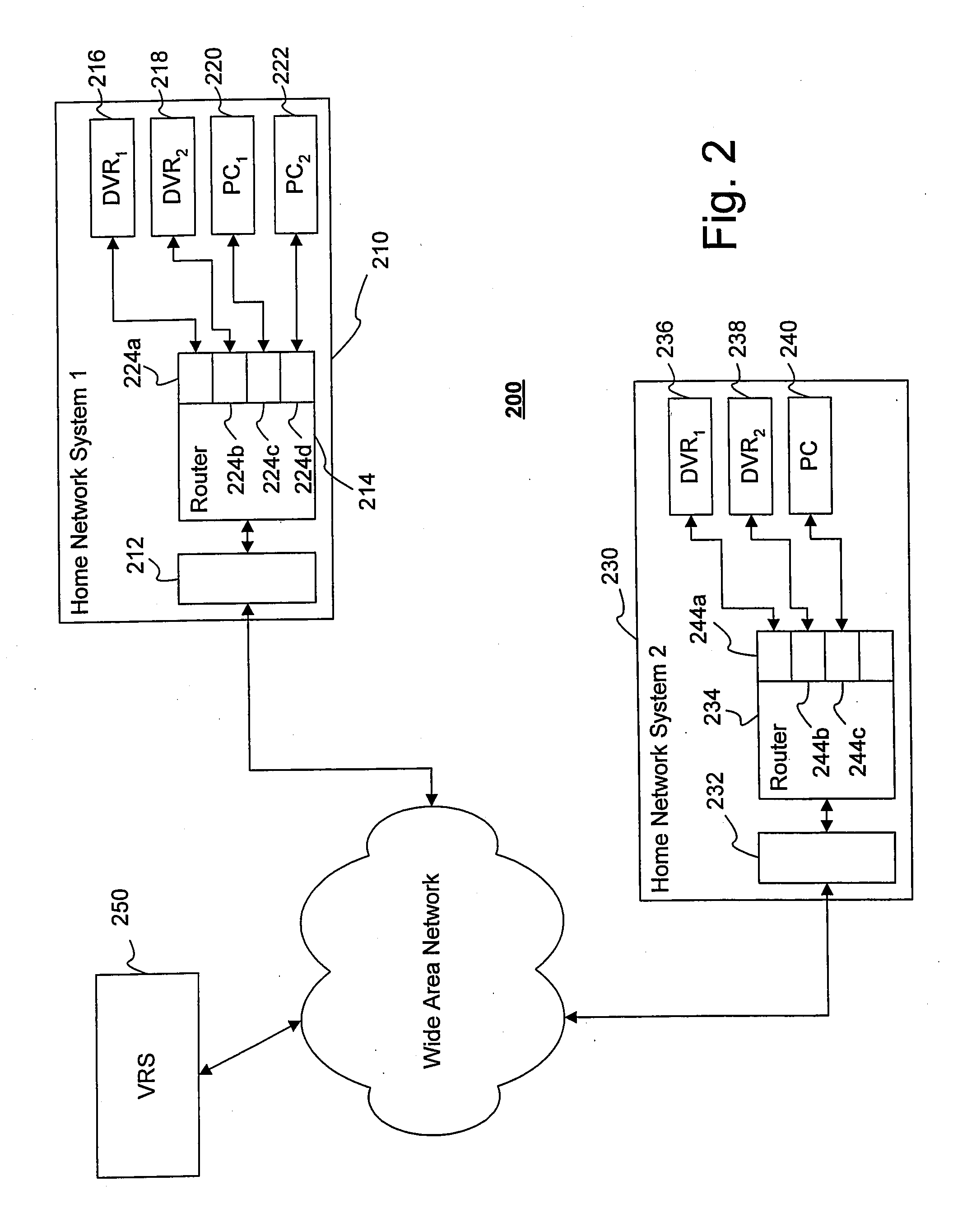
ActiveUS8875198B1Update flexibleEfficient organizationTwo-way working systemsTransmissionWeb siteDigital video
Providing content to content receiving devices, such as digital video recorders, connected to a computer network through a content provider is described. According to one aspect, a server maintains a database correlating contact information to content receiving devices in its network. A user navigates to a web site of the content provider and selects a piece of content, which prompts the content provider to query the server for the contact information, and then transmit a request to download the piece of content to the content receiving device. The request can be a set of content identification information that automatically populates a content guide at the receiving device with an entry corresponding to the requested piece of content. This entry allows the user to confirm, interrupt, resume and cancel a download of the content as desired.
Owner:DIRECTV LLC
Method for realizing adaptive signaling in distributed control collaborative optical networks
ActiveCN101605278ASolve resource congestionFlexible updates and upgradesMultiplex system selection arrangementsTime-division multiplexRing protectionSignaling process
Owner:BEIJING UNIV OF POSTS & TELECOMM
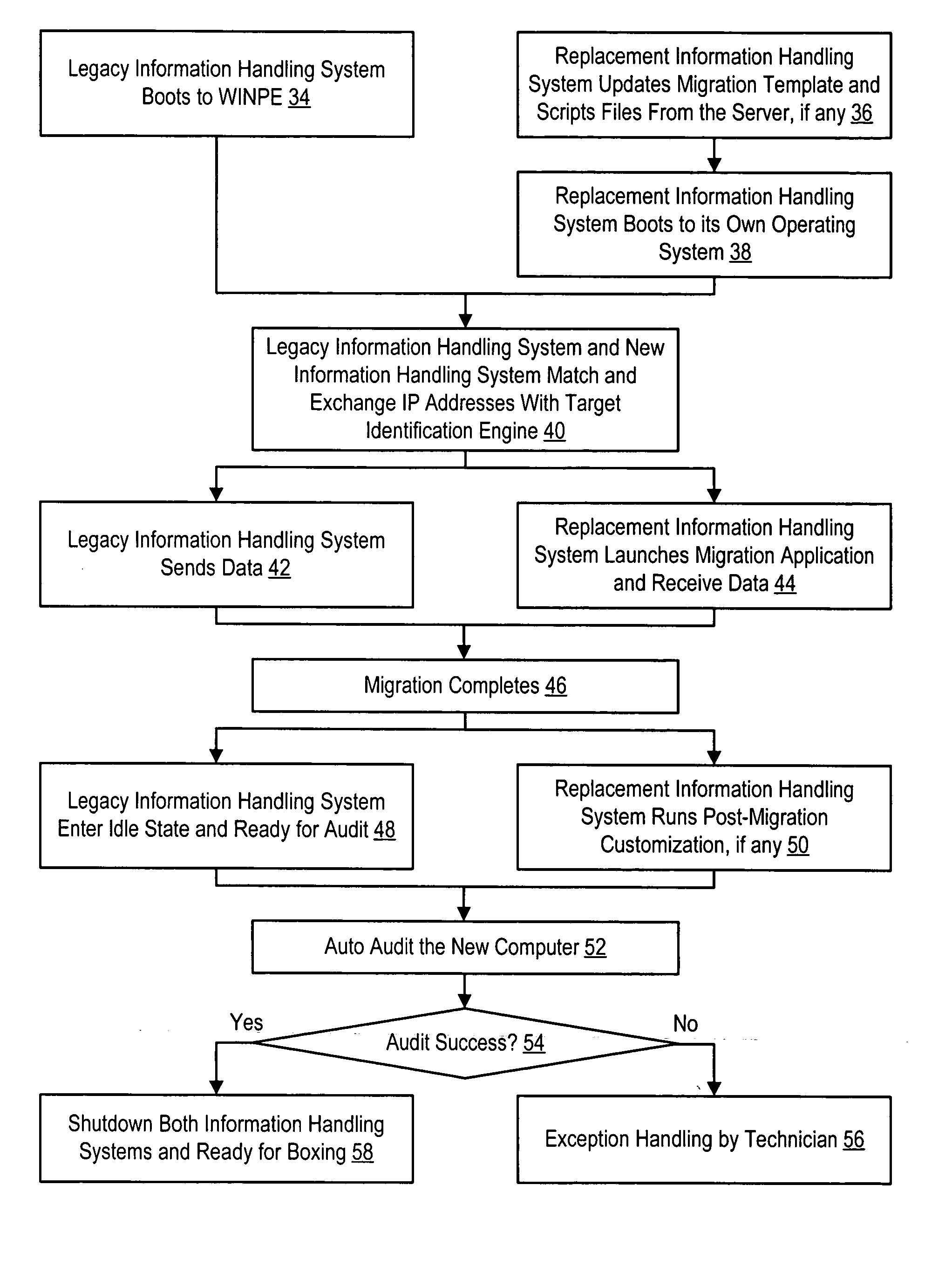
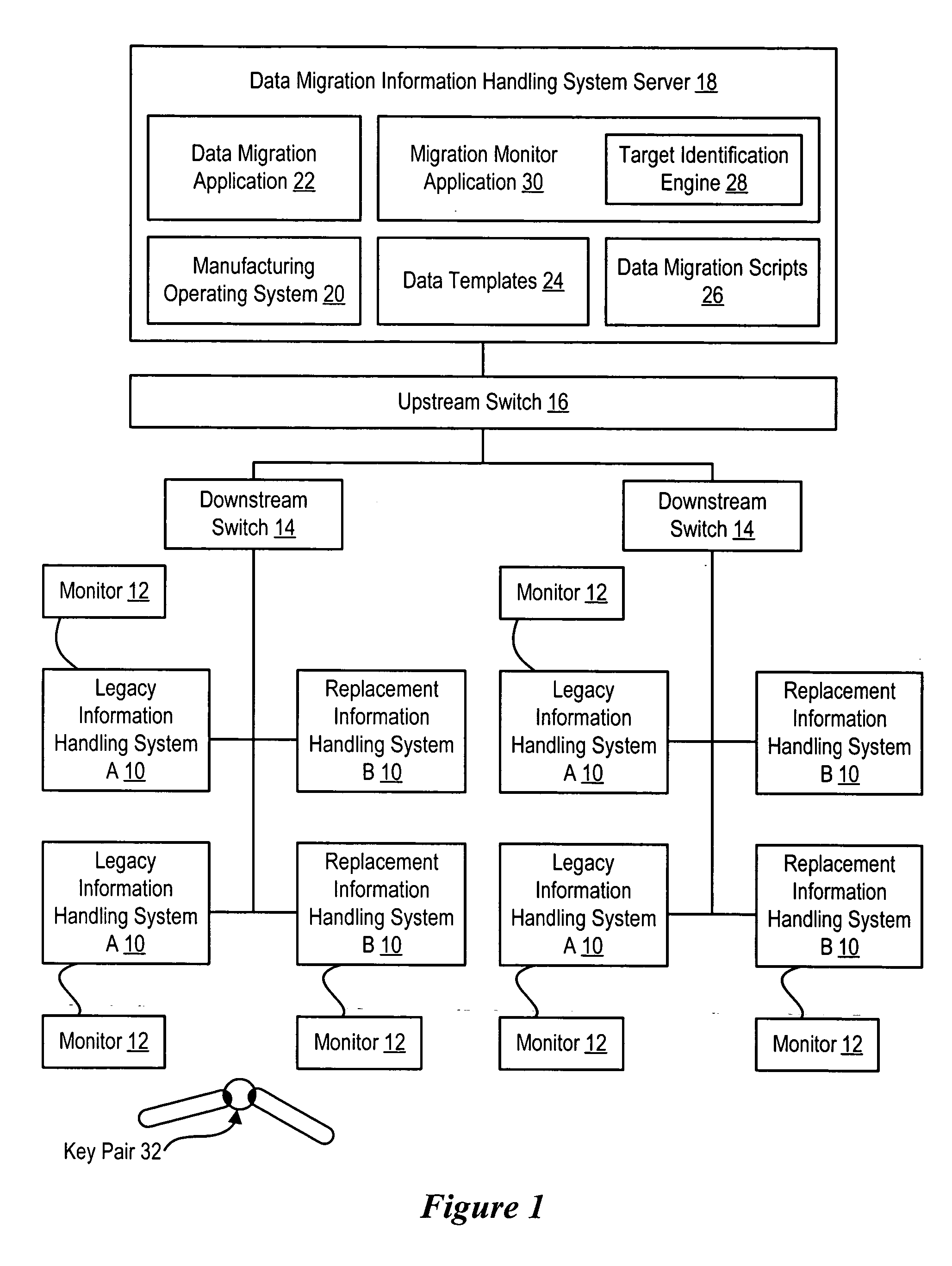
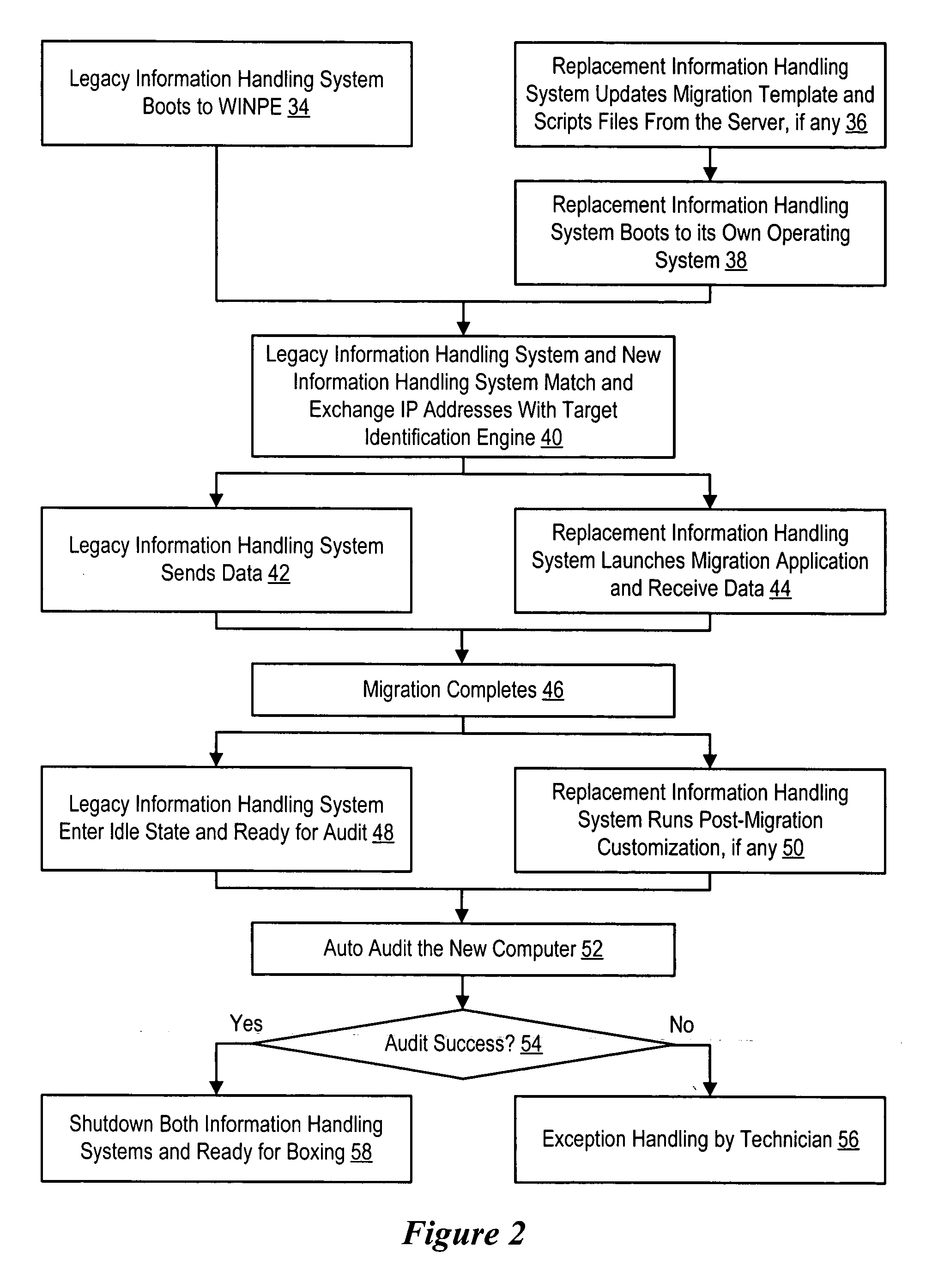
System and method for migration to manufactured information handling systems
InactiveUS20060129769A1Reduce disadvantagesReduce problemsMemory loss protectionProgram controlInformation processingOperational system
Data migration directly from legacy to replacement information handling systems is managed over a set of one or more switches. The legacy information handling system boots with a manufacturing operating system provided from a data migration information handling system server and runs a data migration application also provided from the server. Running the data migration application over the manufacturing operating system avoids password protection of the legacy information handling system. A pair of target storage device keys interface with a legacy and associated replacement system to aid in location of the replacement system on the network for direct system-to-system data transfer.
Owner:DELL PROD LP
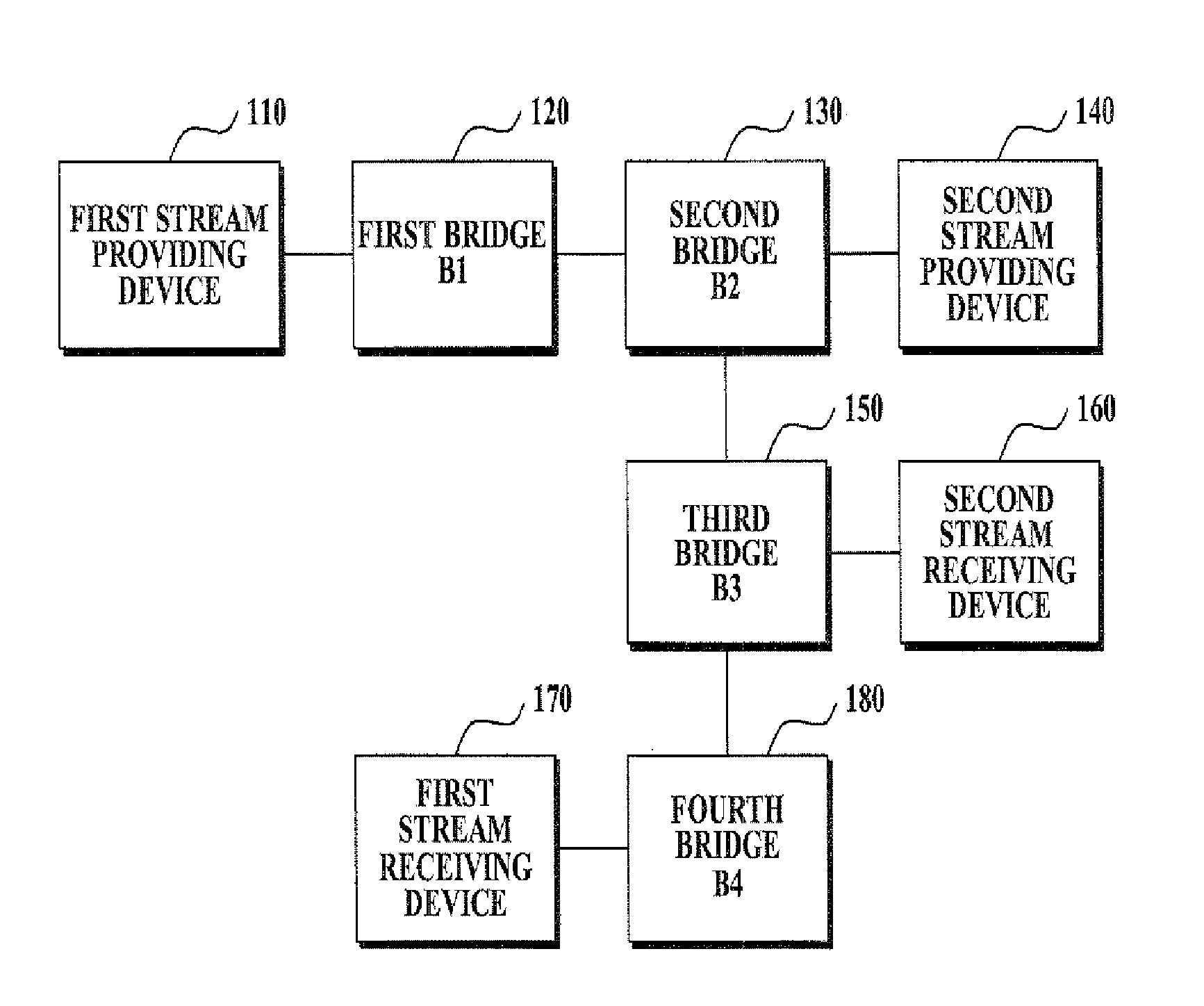
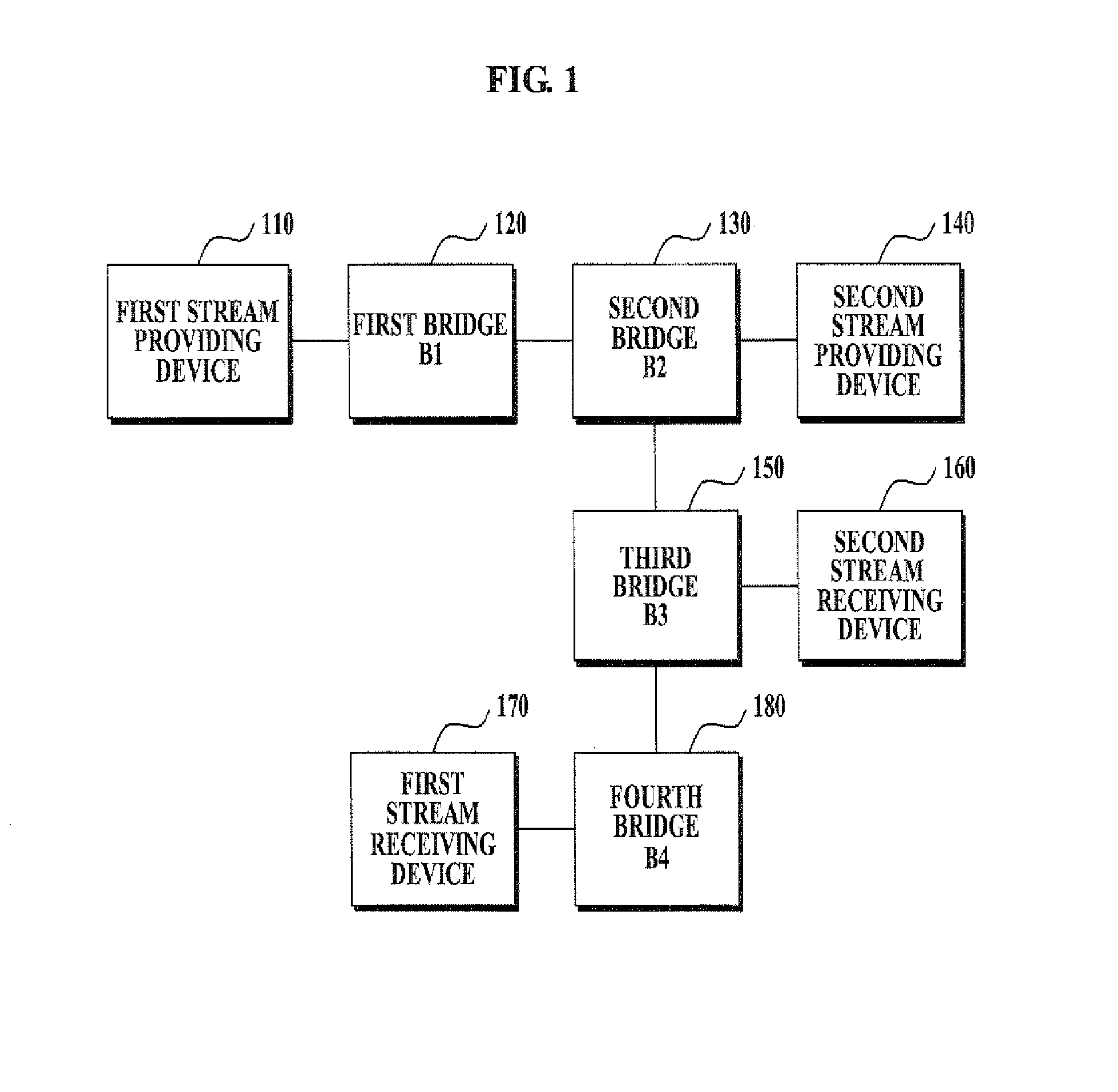
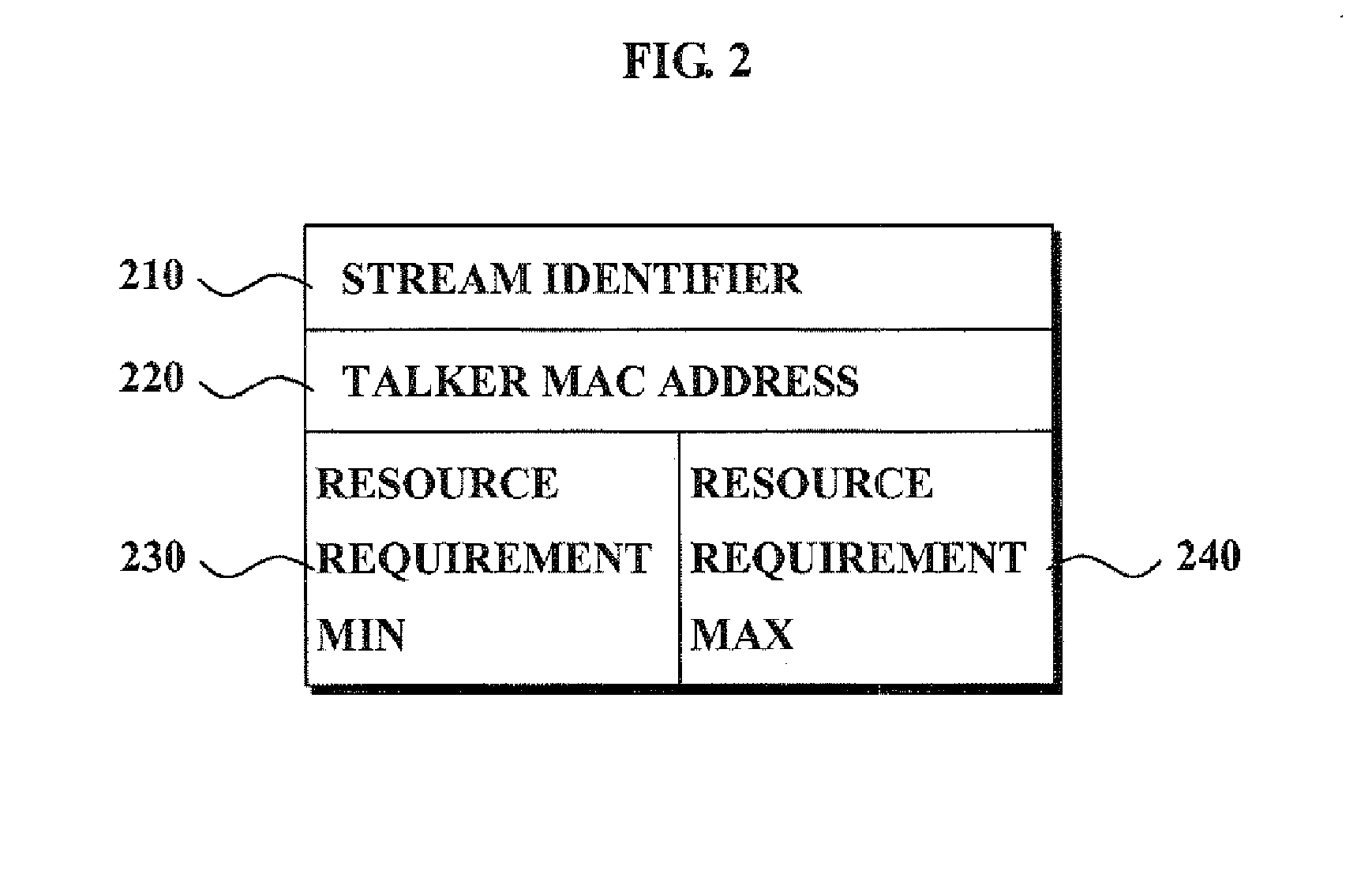
System for providing quality of service in link layer and method using the same
InactiveUS20080235699A1Reduce in quantityQuality improvementTime-division multiplexMultiprogramming arrangementsQuality of serviceData link layer
A system and method of providing a quality of service (QoS) is provided. The method of providing the QoS in the link layer includes receiving, by a stream providing device, minimum and maximum resource requirement information of a stream receiving device; transmitting, by the stream providing device, a reservation message including the minimum and maximum resource requirement information; allocating a resource, by at least one bridge, based on the reservation message transmitted from the stream providing device; and receiving, by the stream receiving device, a stream transmitted from the stream providing device via the resource.
Owner:SAMSUNG ELECTRONICS CO LTD
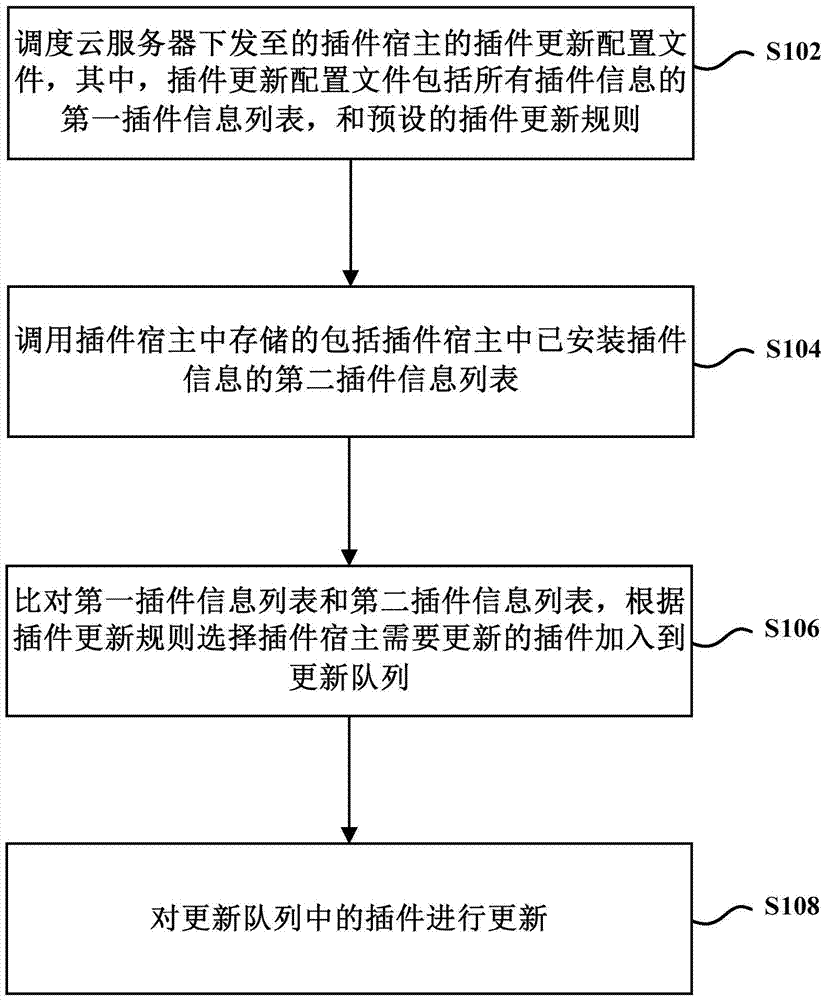
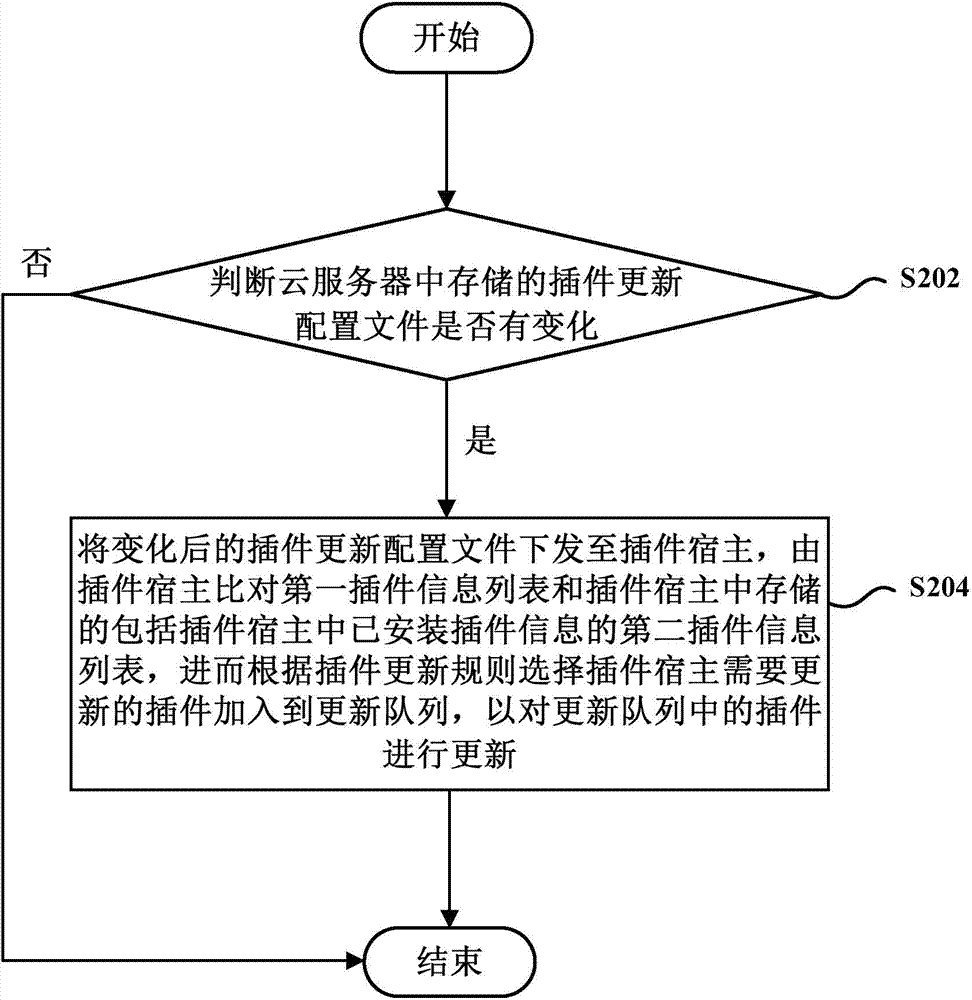
Plug-in update method and device
ActiveCN104714827AAccurate updateUpdate flexibleProgram loading/initiatingOperating systemCloud server
The invention provides a plug-in update method and device. The method comprises the following steps: scheduling a plug-in update configuration file transmitted to a plug-in host by a cloud server, wherein the plug-in update configuration file comprises a first plug-in information list of all plug-in information and a preset plug-in update rule; calling a second plug-in information list which is stored in the plug-in host and comprises installed plug-in information in the plug-in host; comparing the first plug-in information list and the second plug-in information list, and selecting a plug-in needing to be updated by the plug-in host to be added into an update queue according to the plug-in update rule; and updating the plug-in in the update queue. According to the technical scheme provided by the embodiment of the invention, the plug-in is intelligently updated, the plug-in version control, compatibility control and other problems are solved, and the breakdown ratio of plug-in application is reduced.
Owner:BEIJING QIHOO TECH CO LTD
Method, terminal and server for realizing customization function of wireless terminal
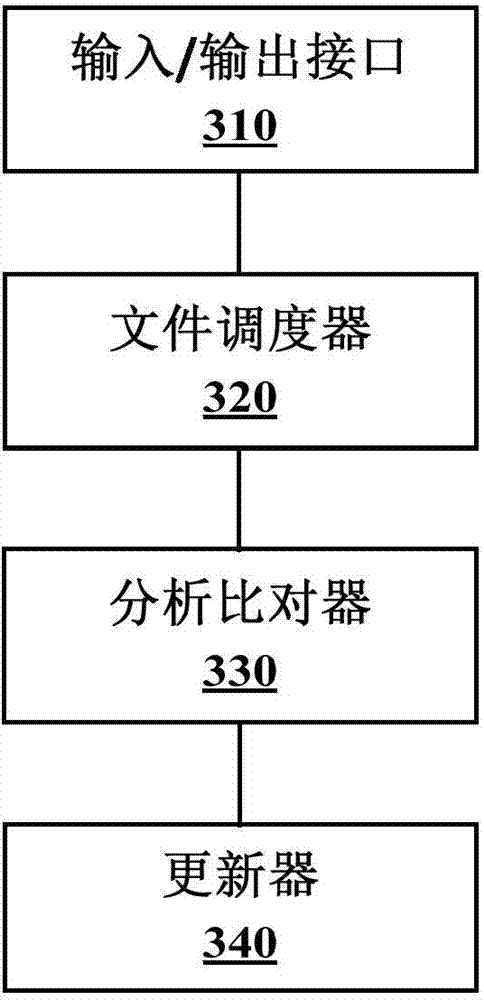
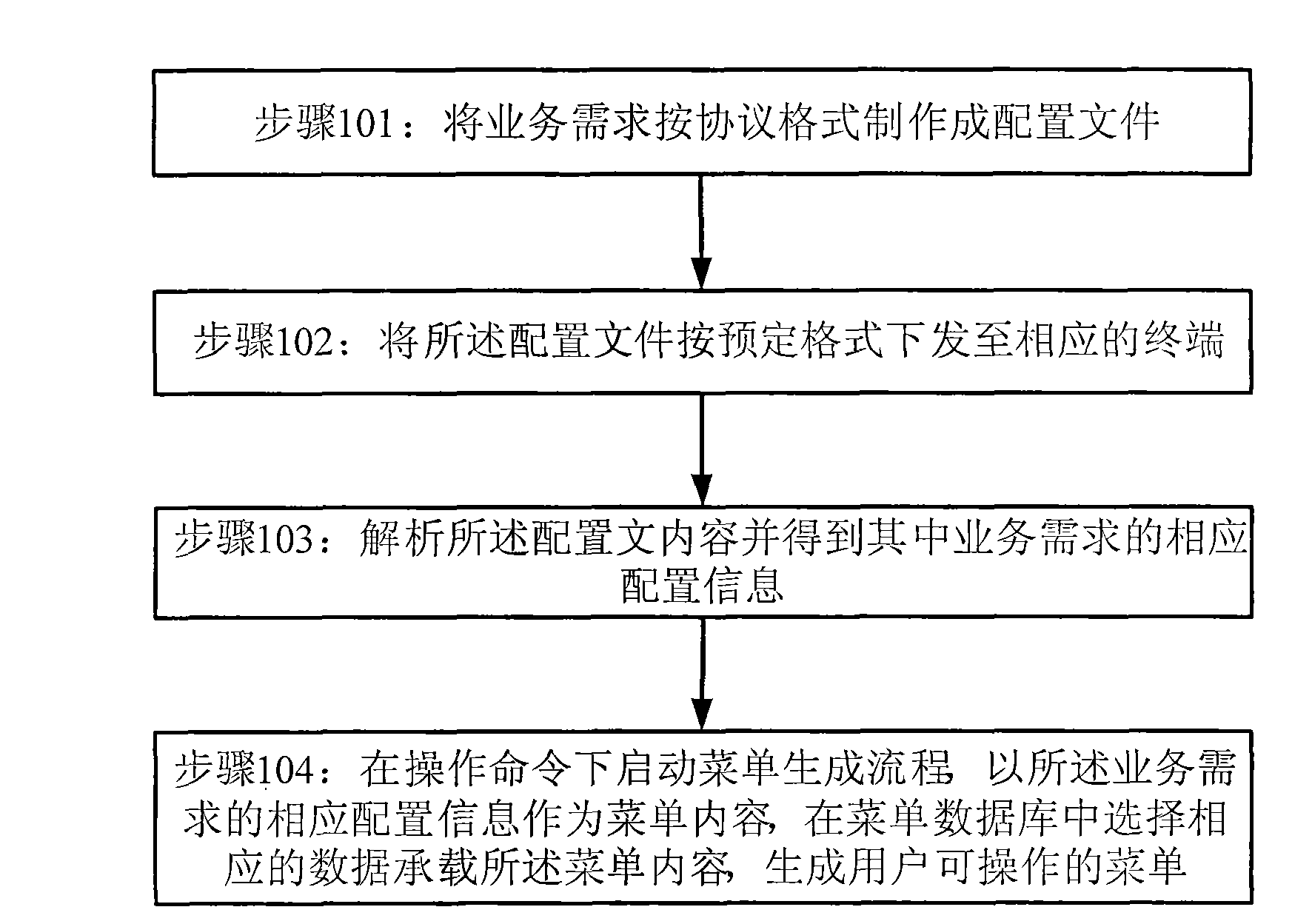
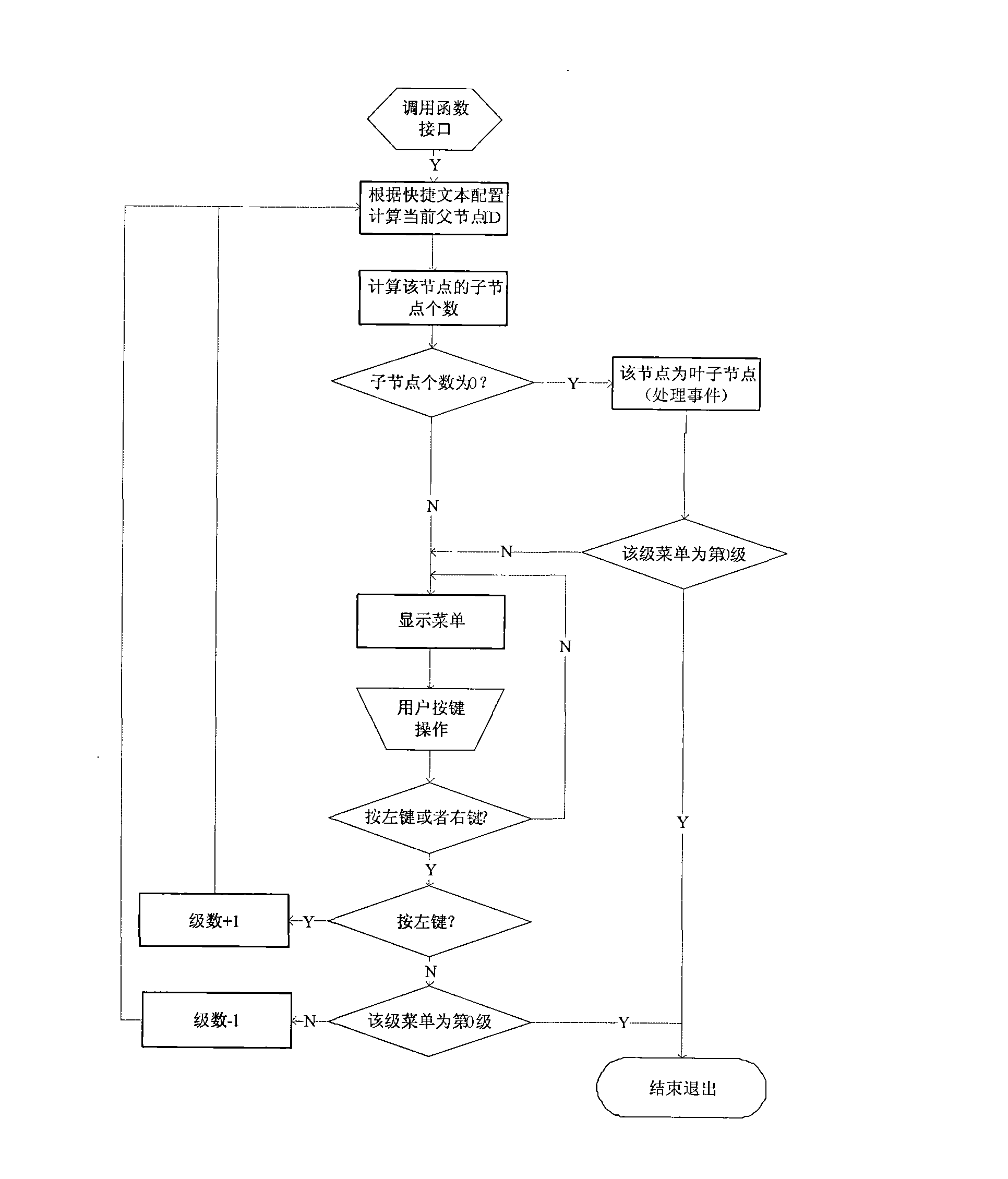
InactiveCN101583125AEasy to updateRealize the application functionNetwork data managementData bankBusiness requirements
The invention discloses a terminal, a server and a method for realizing the customization function of a wireless terminal; the method for realizing the customization function of the wireless terminal comprises the following steps of: preparing a service requirement into an allocation document according to a protocol format; sending down the allocation document to corresponding terminals according to the prearranged format; analyzing the contents of the allocation document and obtaining the corresponding allocation information of the service requirement wherein; starting a menu generation flow under an operation command; and taking the corresponding allocation of the service requirement as the menu content, selecting corresponding data out of a menu database so as to bear the menu content, and generating the menu operable for the user. The method, the terminal and the server can flexibly custom the terminal functions by the parameter allocation so as to meet requirements of various new services.
Owner:XIAMEN STELCOM INFORMATION & TECH
Pump system
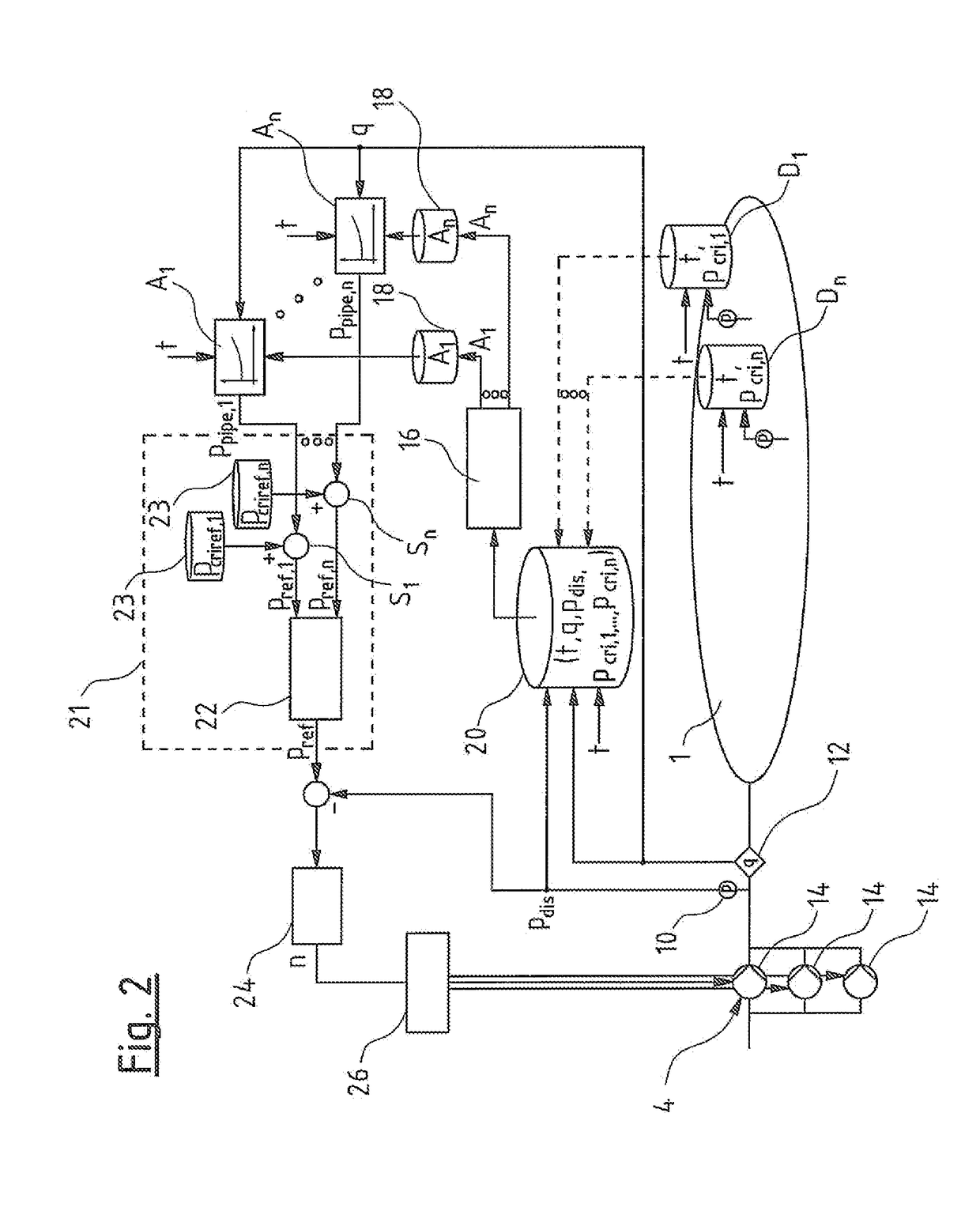
ActiveUS20140255216A1Improve recognition accuracyImprove accuracyFlexible member pumpsFluid-tightness measurementComputer moduleEngineering
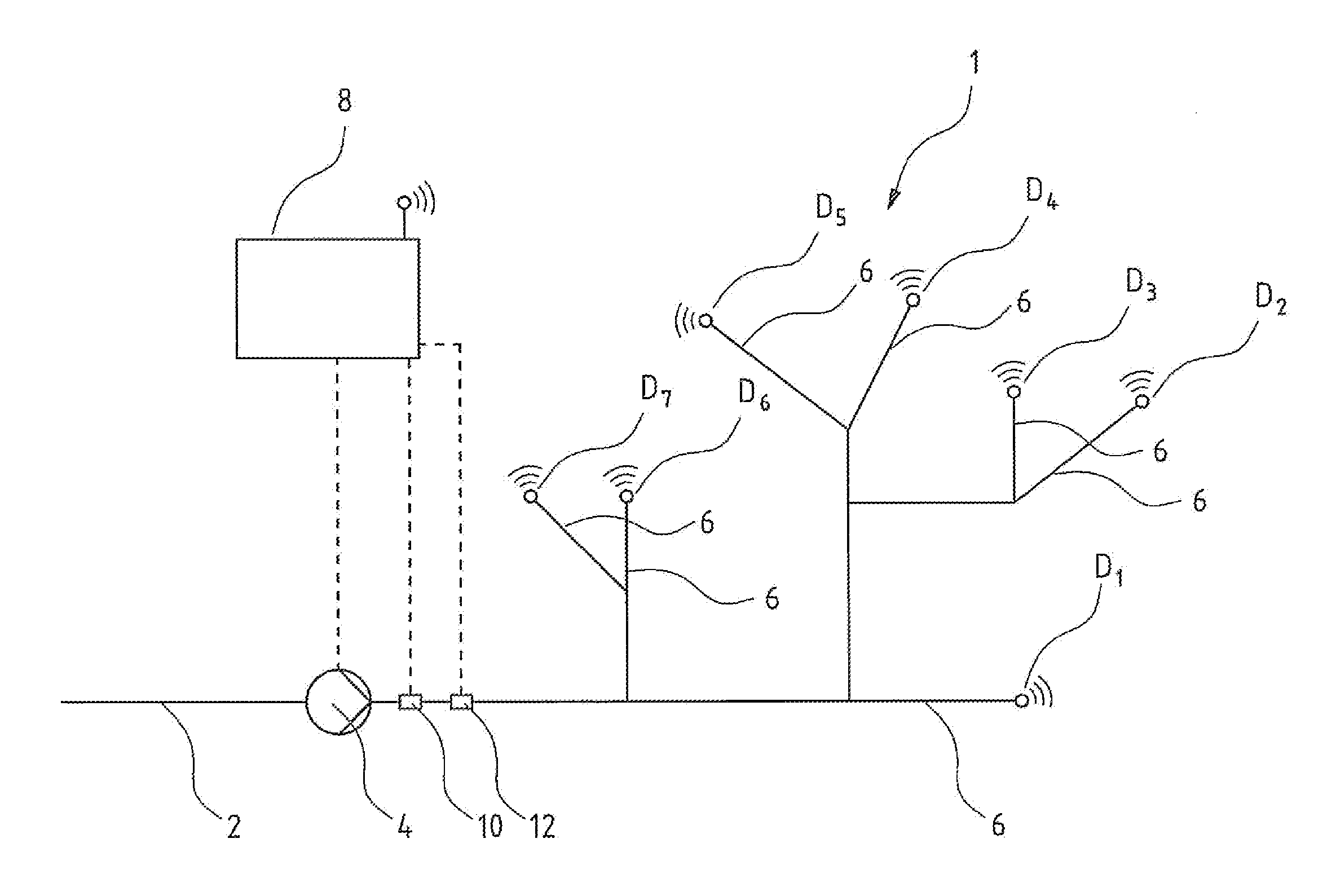
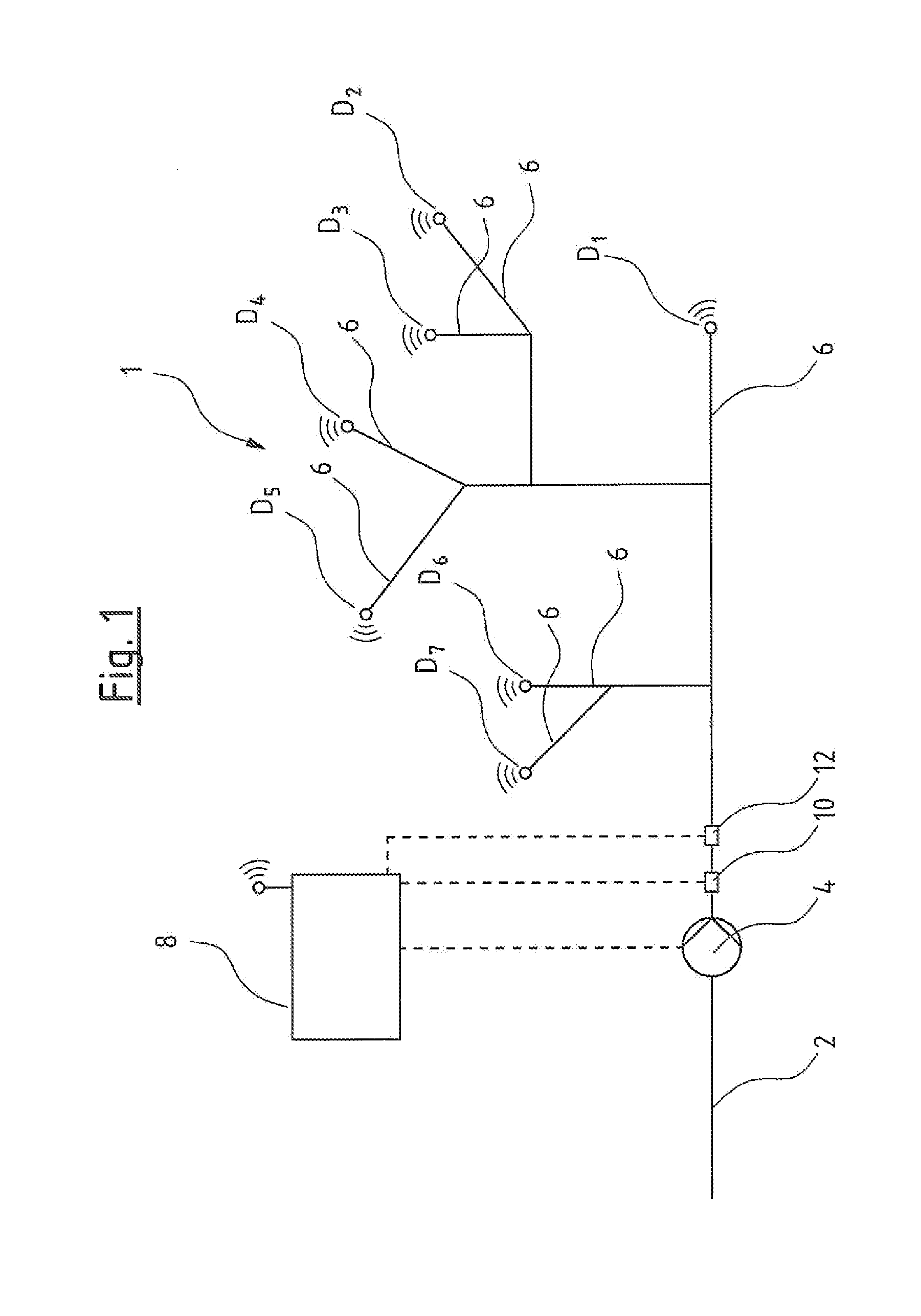
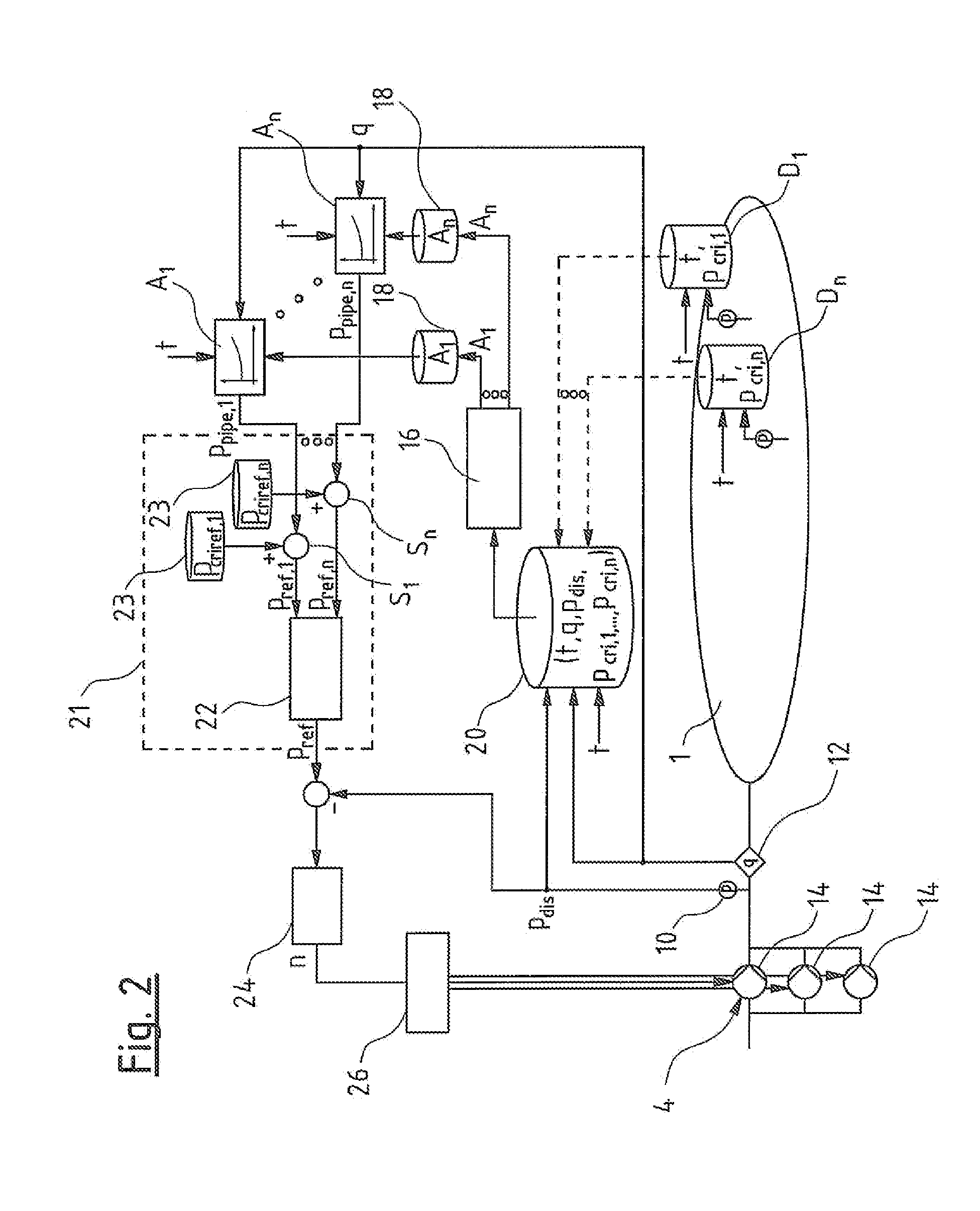
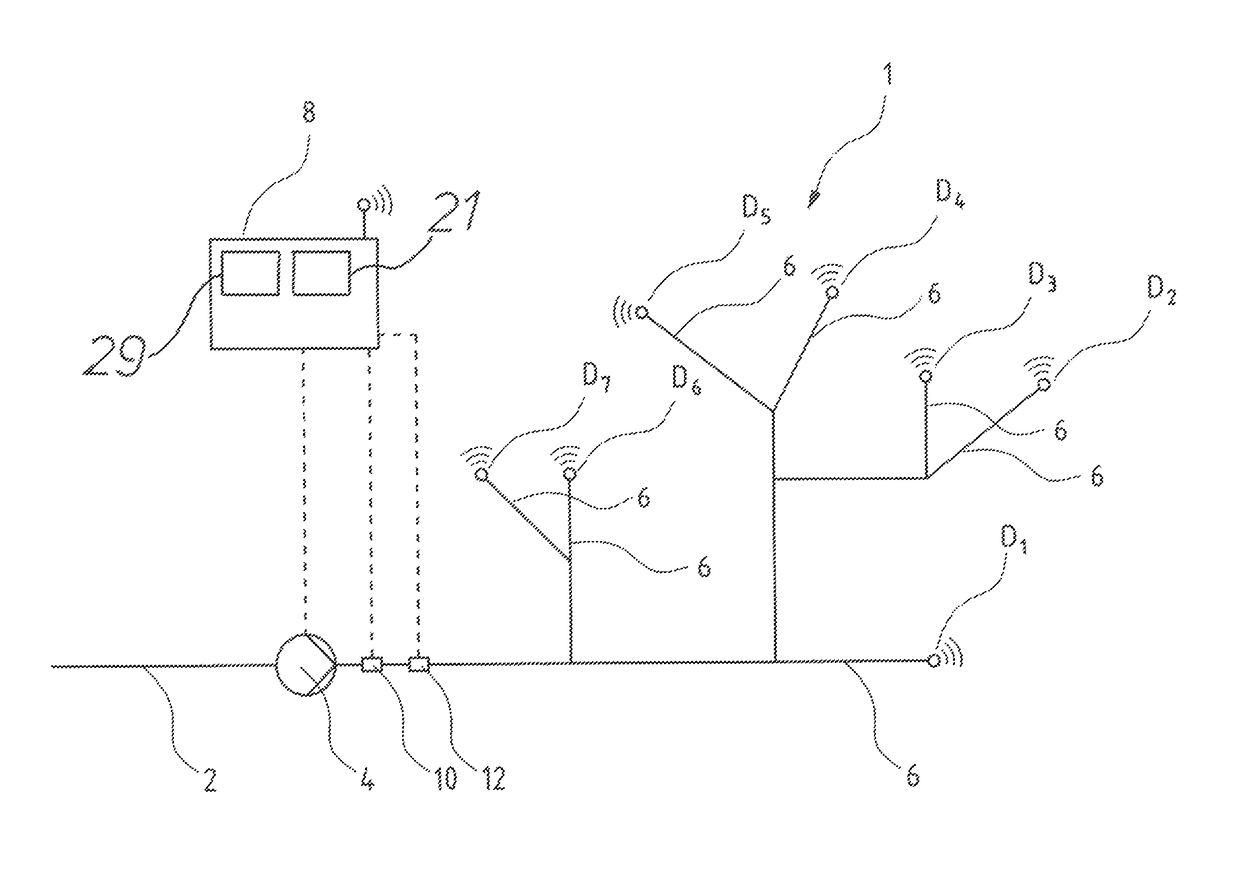
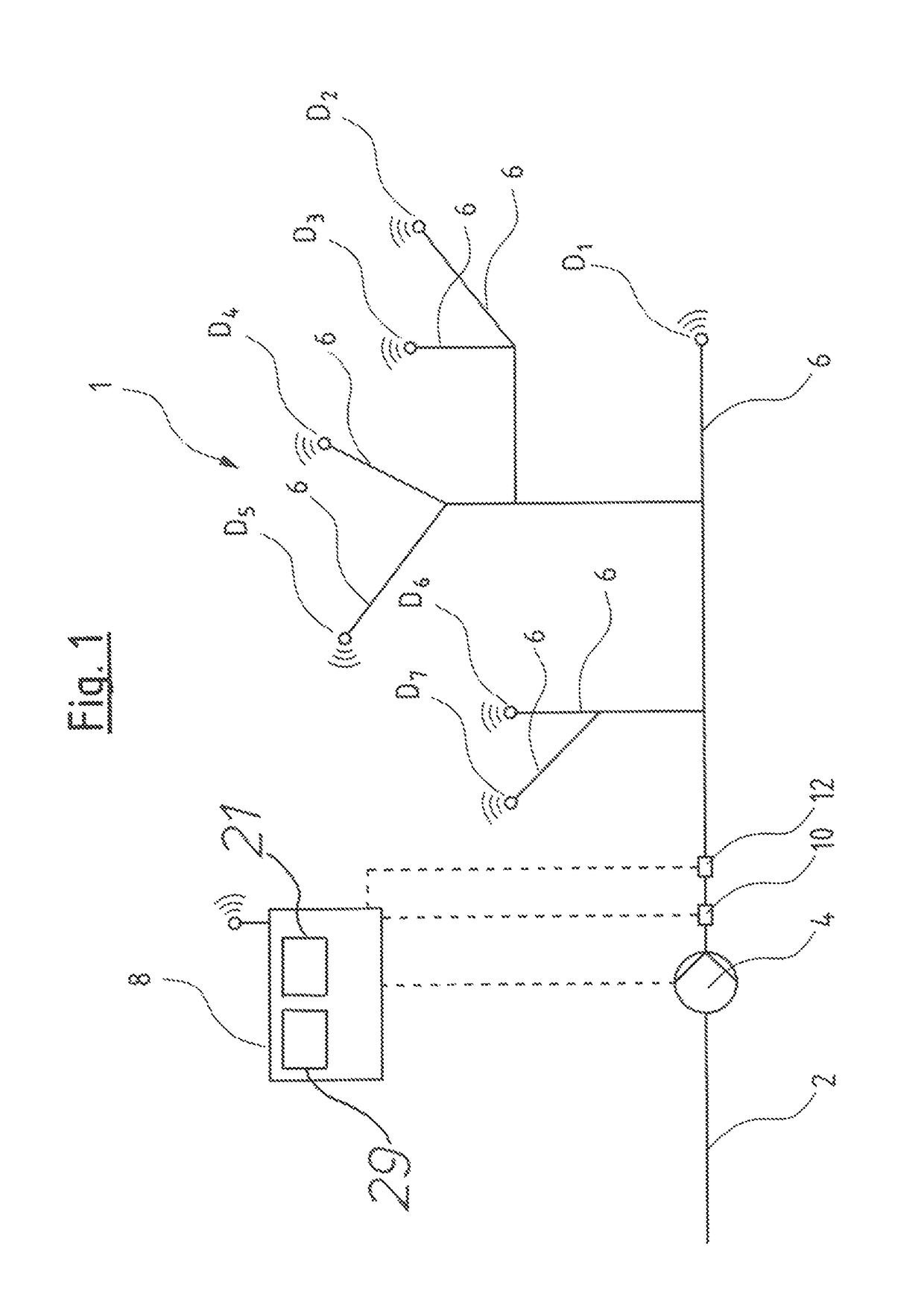
A pump system for a water supply mains has at least one pump device, a pressure detecting sensor at the pressure side of the pump device, a flow detecting sensor of the pump device, several pressure sensor units (D) remote arranged remotely from the pump device in different part regions of the mains, and a pump control device. The control device includes a model formation module designed in each case to produce a model (A) representing pressure loss from the pressure sensor to the position of the respective pressure sensor unit (D), based on several pressure measured values of at least two pressure sensor units (D) for the at least two associated part regions. The control device is designed for regulation of the pump device based on produced models (A), as well as to a corresponding method for regulation of a pump device in a water supply mains.
Owner:GRUNDFOS HLDG
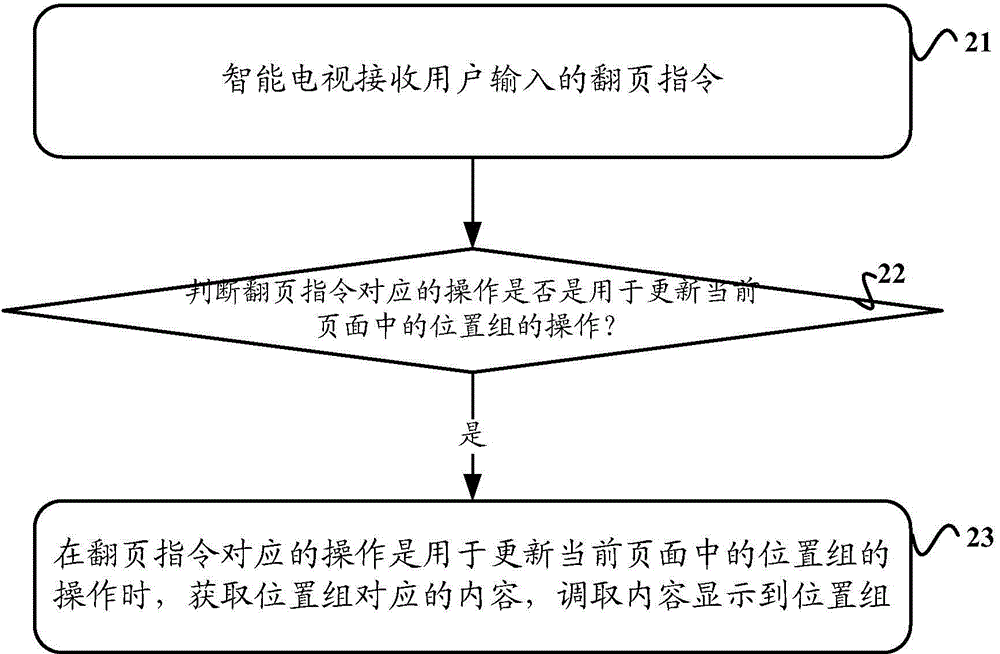
Method for updating and issuing page content, smart television and system
ActiveCN104902327AUpdate flexibleImprove display efficiencySelective content distributionComputer hardwareCable television
The embodiment of the invention discloses a method for updating and issuing page content, a smart television and a system, and relates to communication field. The method for updating and issuing the page content, the smart television and the system of the invention are used to provide a solution of updating the content displayed in a local area in current page of the smart television. The method of the embodiment of the invention comprises the steps as follows: receiving a page turning instruction input by a user with the smart television, judging whether an operation corresponding to the page turning instruction is the operation for updating a position set in the current page; obtaining the content corresponding to the position set if the operation corresponding to the page turning instruction is the operation for updating the position set in the current page, and taking the content display to the position set, thereby solving the above problem.
Owner:QINGDAO HISENSE MEDIA NETWORKS CO LTD
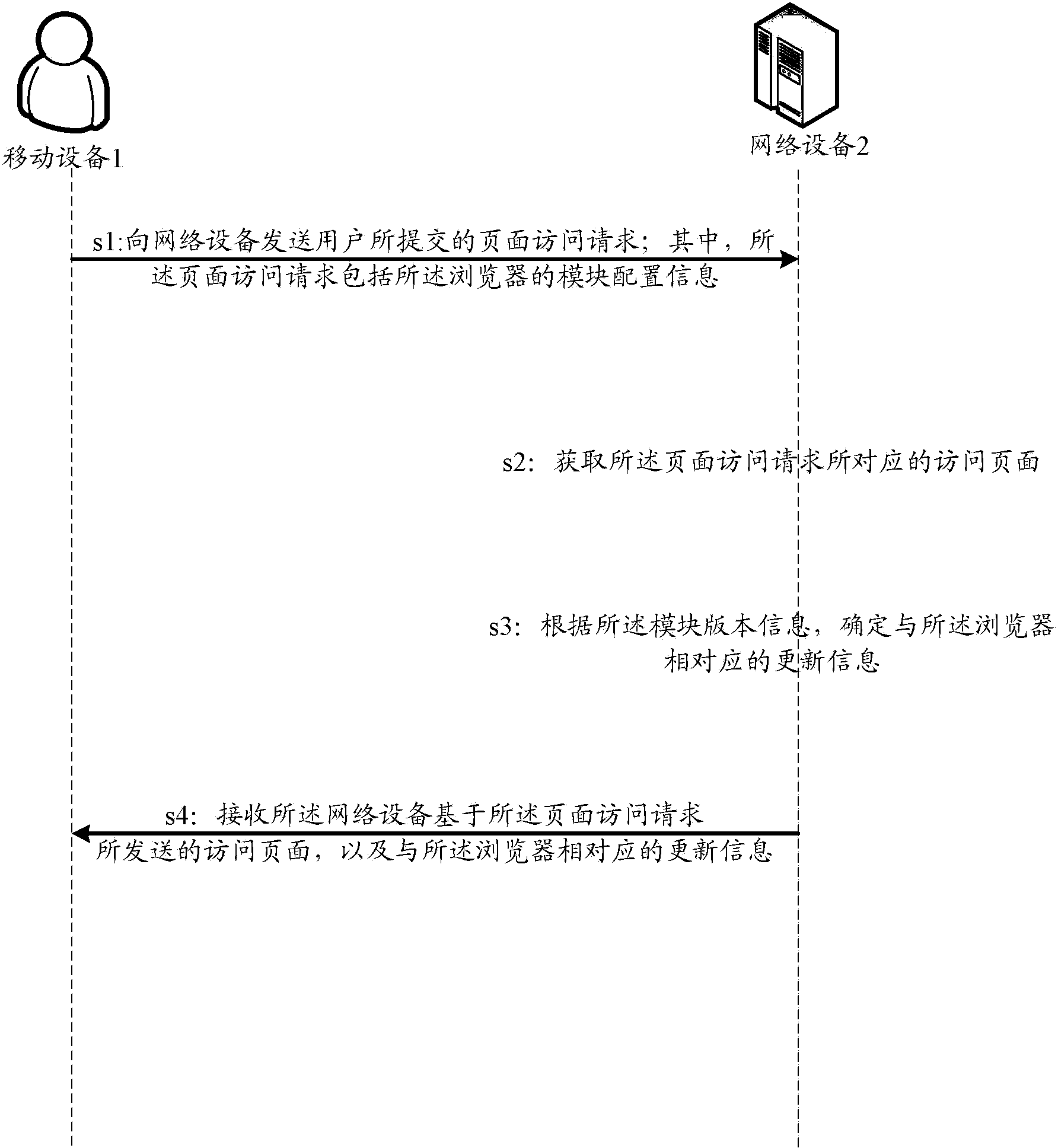
Method and device for updating browser
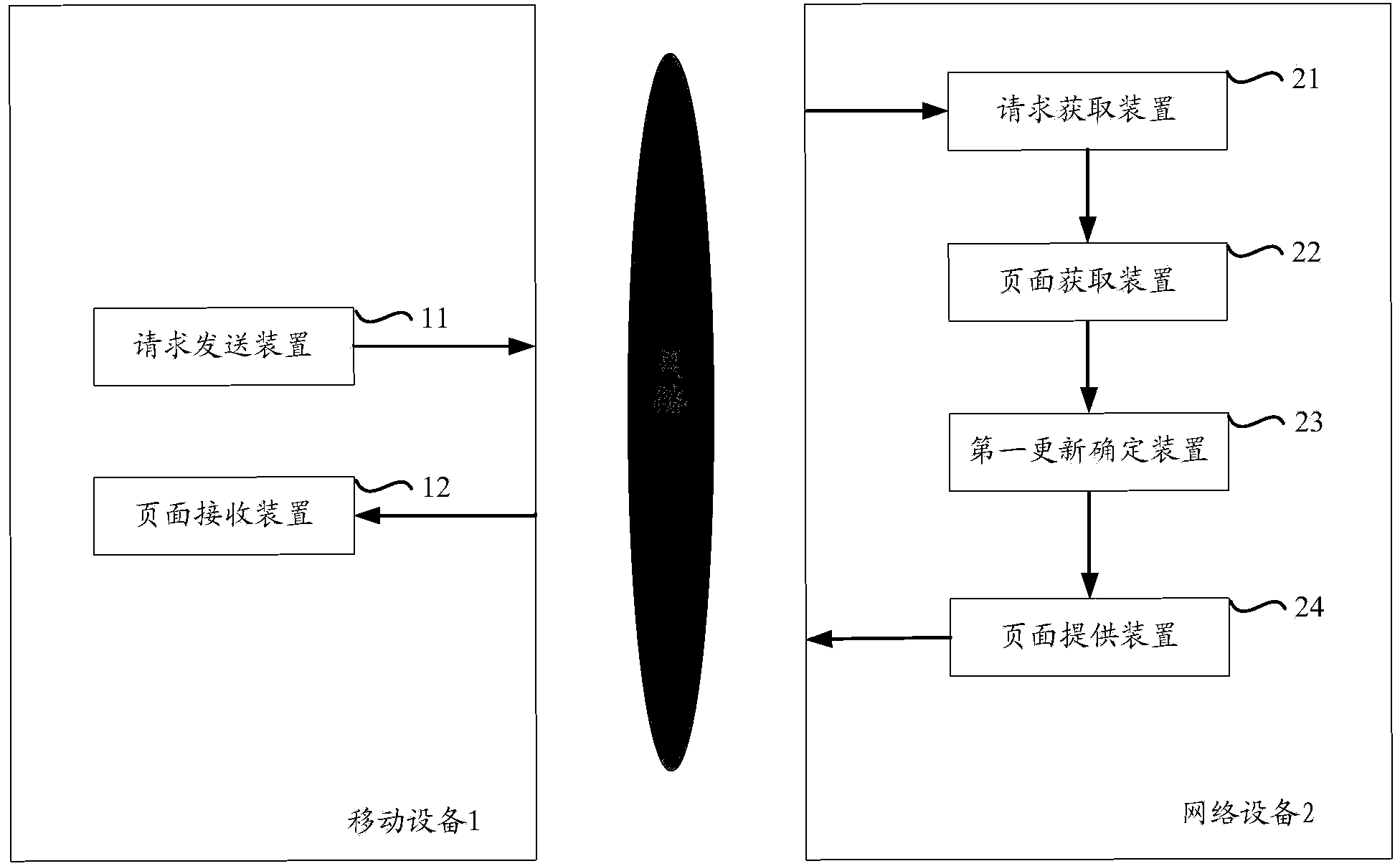
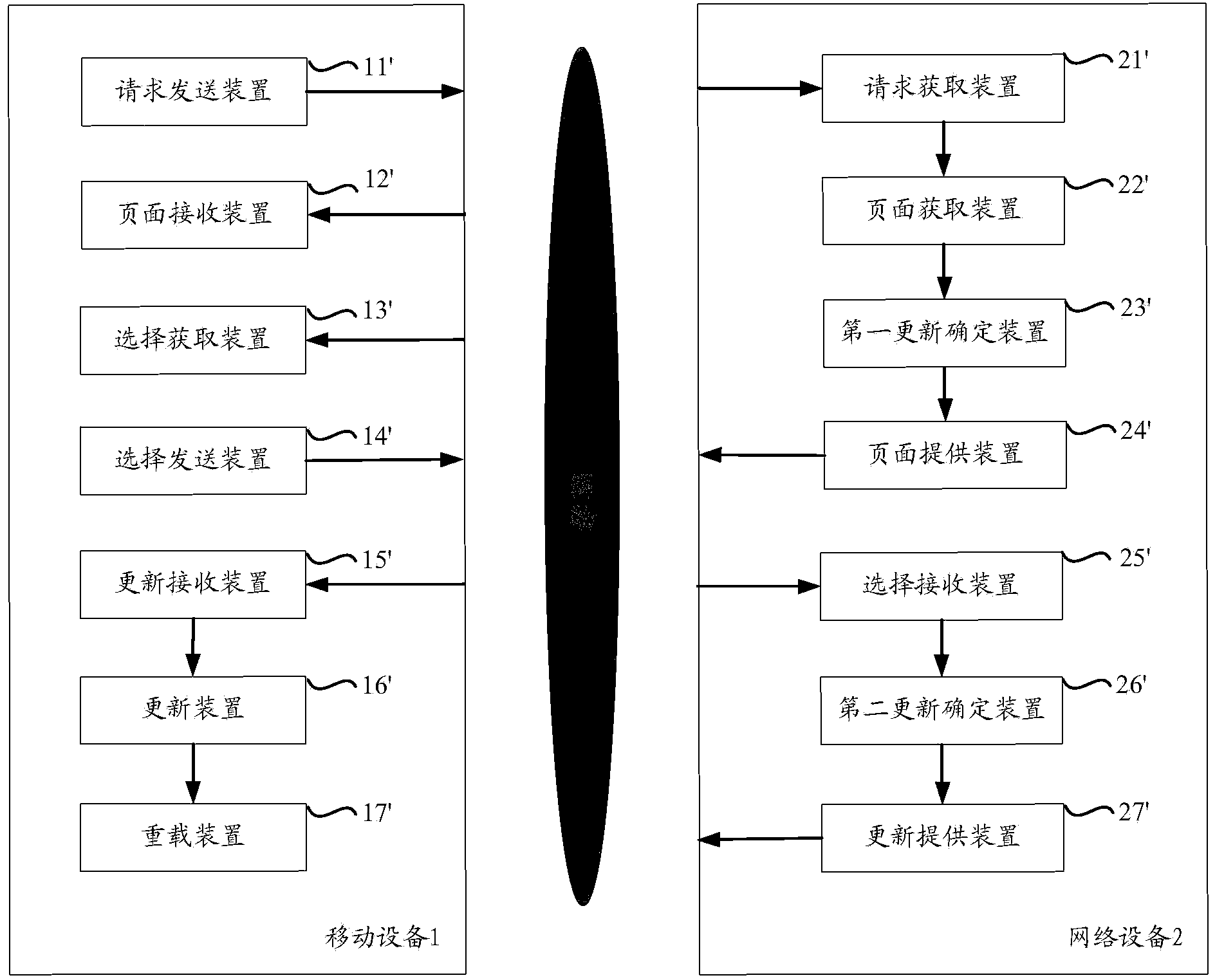
ActiveCN103677860AUpdate flexibleImprove update efficiencyProgram loading/initiatingSpecial data processing applicationsResource utilizationInformation provision
The invention aims at providing a method and device for updating a browser. The method includes the steps of dividing the browser into a browser frame module and a browser kernel module with the interface technology, wherein the browser frame module is in communication with the browser kernel module; enabling a mobile device to transmit a page access request submitted by a user to a network device, wherein the page access request comprises module configuration information of the browser; enabling a network device terminal to obtain an access page corresponding to the page access request; determining updating information corresponding to the browser according to module version information, and providing the access page and the updating information for the user. Compared with the prior art, the method and device have the advantages that separable updating of the frame module and the kernel module is carried out on the browser according to the page access request of the user, the bandwidth resource, the flow resource and the processing resource of the mobile terminal are effectively used, the efficiency of the user for obtaining the information is improved, the resource utilization rate of the mobile terminal is improved, and the user experience is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
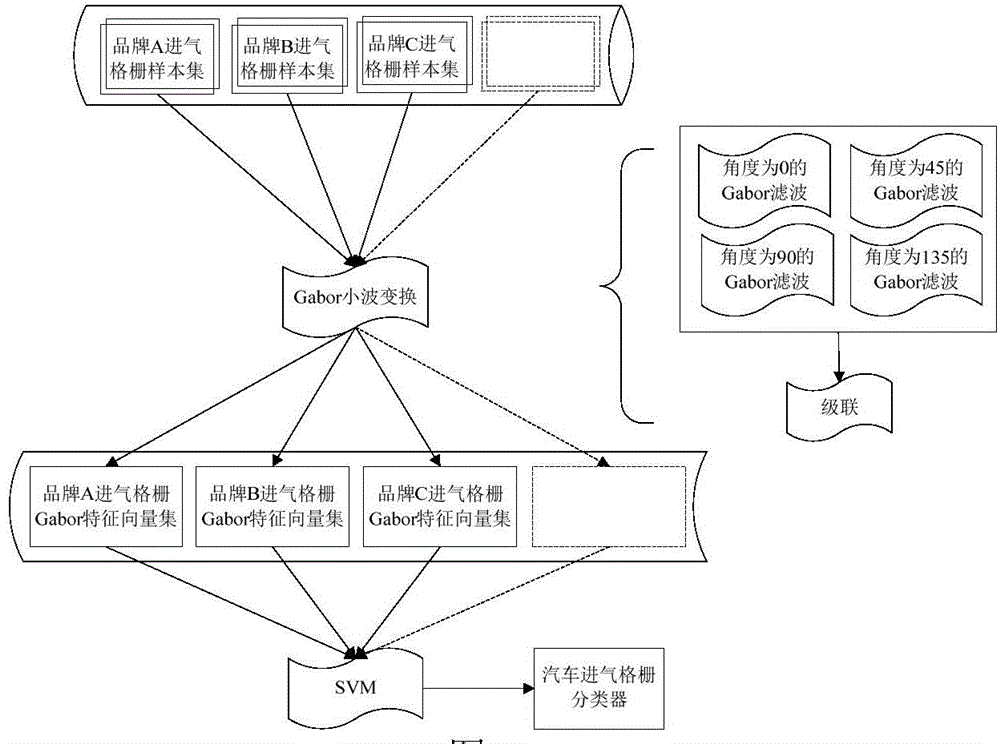
Automobile logo sample training and recognition method based on air-inlet grille positioning
InactiveCN104156692APreserve texture informationEasy to identifyCharacter and pattern recognitionPattern recognitionTemplate library
The invention discloses an automobile logo sample training and recognition method based on air-inlet grille positioning. The training process comprises the following steps: a, obtaining air-inlet grille samples of different automobiles and converting the samples to grayness images; b, classifying the air-inlet grille samples obtained in the step a according to automobile brands, and respectively performing normalization gauge processing on various sample sets to enable the air-inlet grille samples to be unified to the same size; c, conducting Gabor function conversion on the various samples obtained in the step b to perform size conversion and rotation transformation to obtain a Gabor wavelet expression. The automobile logo sample training and recognition method has the following benefits: 1, the automobile air-inlet grille, rather than the automobile logo, is adopted as the identification target, so that more effective image information is guaranteed for identification of automobile brands; 2, the Gabor wavelet conversion is utilized to keep texture information in each direction of the air-inlet grille; 3, the template library for classifying provided by the invention has an elastic structure, so that flexible expansion and update can be realized.
Owner:叶茂
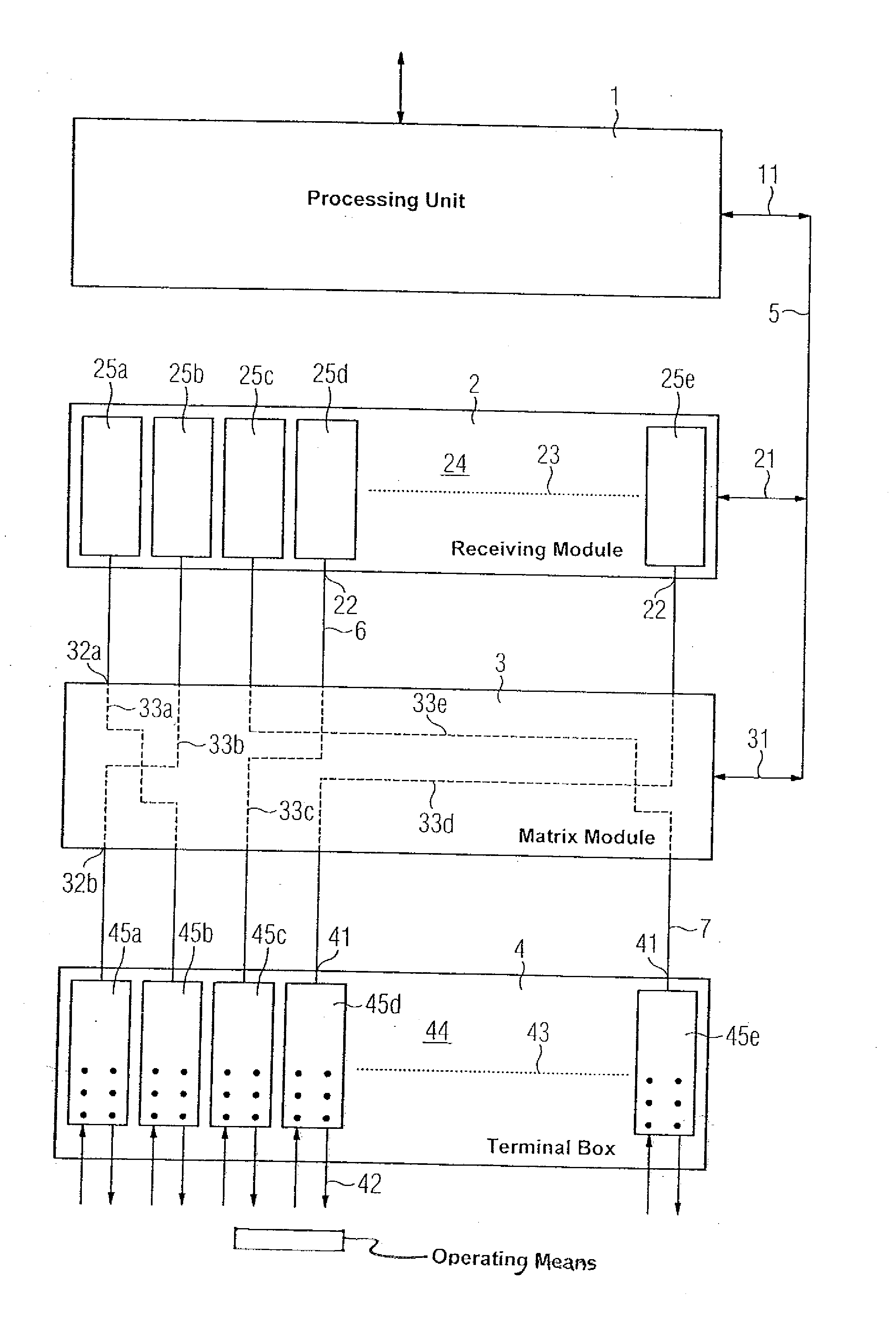
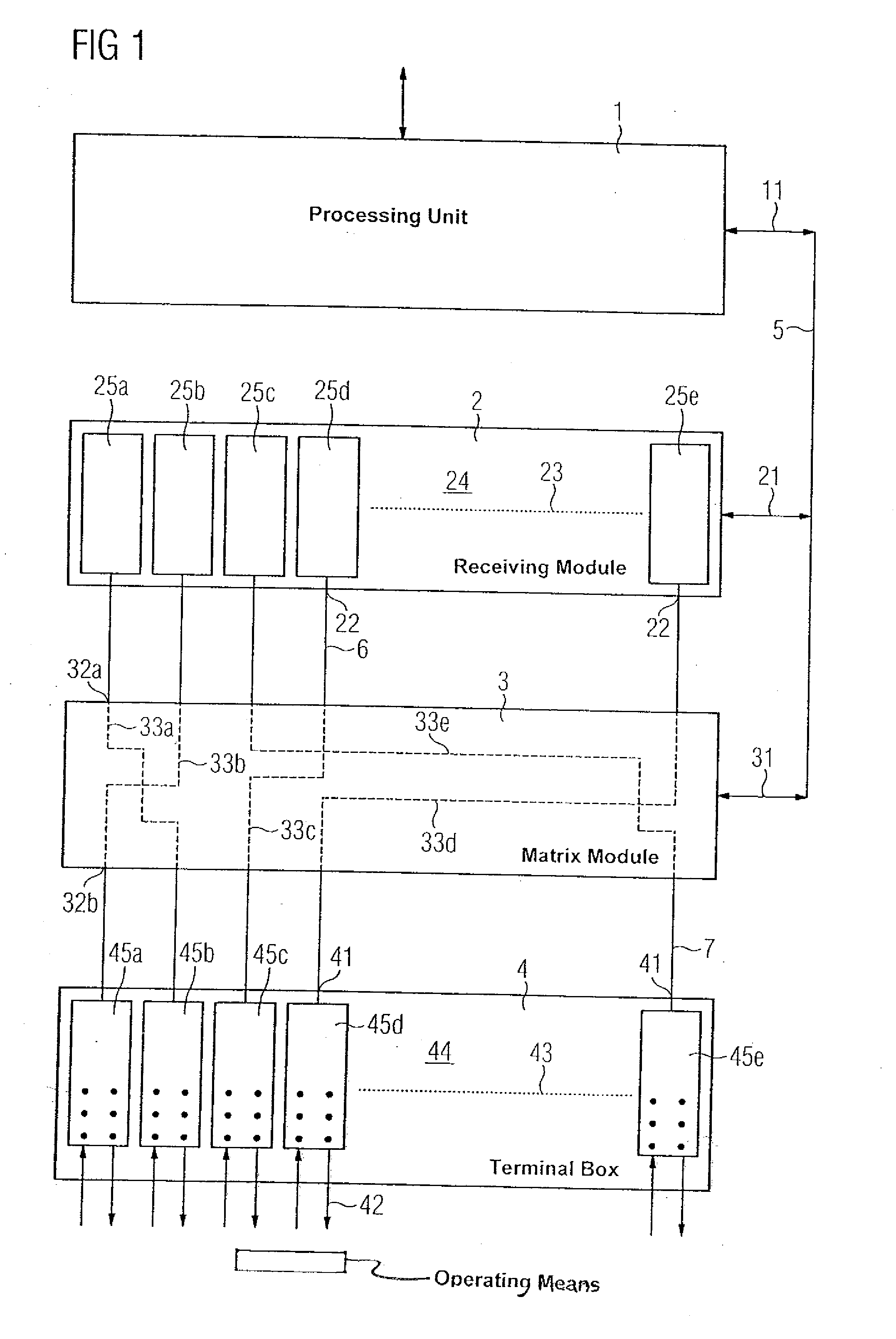
Automation System Having A Programmable Matrix Module
An automation system for controlling a technical process having an electronic processing unit, input / output (I / O) modules for inputting and outputting process signals to operating means of the technical process, such as sensors and actuators, and terminal modules for connecting the operating means to the I / O modules. The automation system also includes a programmable matrix module that can be used by the electronic processing unit to dynamically associate, i.e., connect, one or more I / O modules with one or more terminal modules.
Owner:SIEMENS AG
Creation method of end-to-end secure link and system
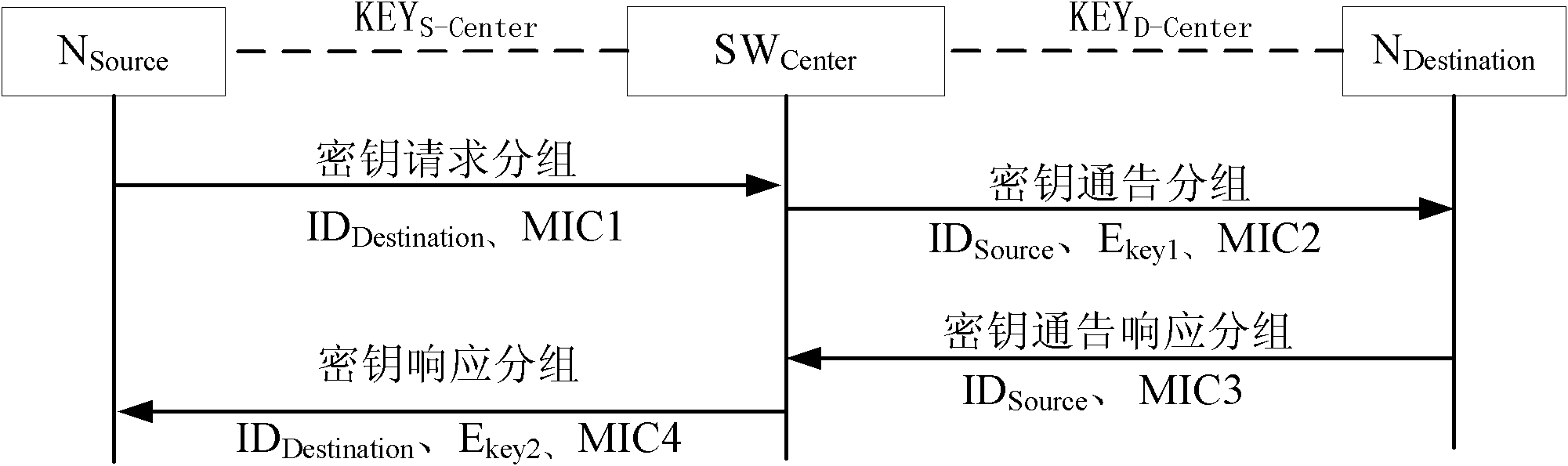
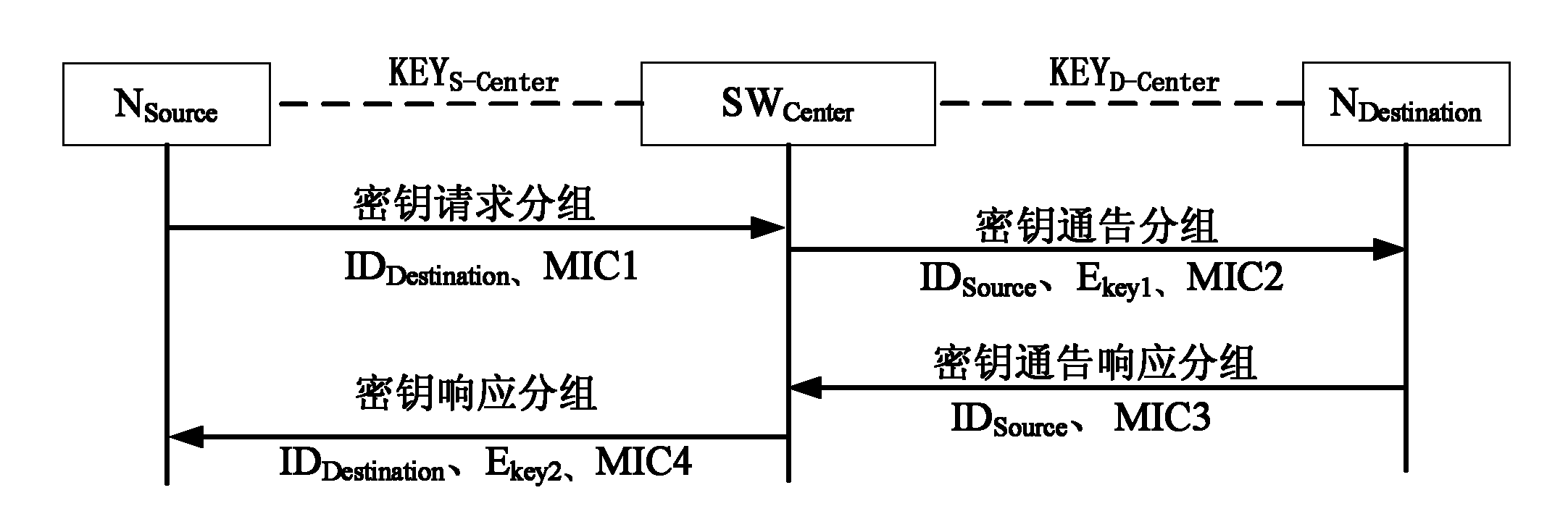
ActiveCN101841413ABuild flexibleUpdate flexibleKey distribution for secure communicationMultiple keys/algorithms usageEnd to end securityEngineering
The invention relates to a creation method of end-to-end secure link and a system. The creation method comprises the following steps that: 1) a transmission source node NSource transmits akey request packet to a core switch device SWCenter; 2) after receiving the key request packet, the core switch device SWCenter creates a key announce packet to a destination node NDestination; 3) after receiving the key announce packet, the destination node NDestination creates a key announce response packet to be transmitted to the core switch device SWCenter; 4) after receiving the key announce response packet, the core switch device SWCenter creates a key response packet to be transmitted to the transmission source node NSource; 5) and the transmission source node NSource receives the key response packet and creates the end-to-end secure link. The creation method and the system have higher network security.
Owner:CHINA IWNCOMM
Embedded type system and method for renewing application program
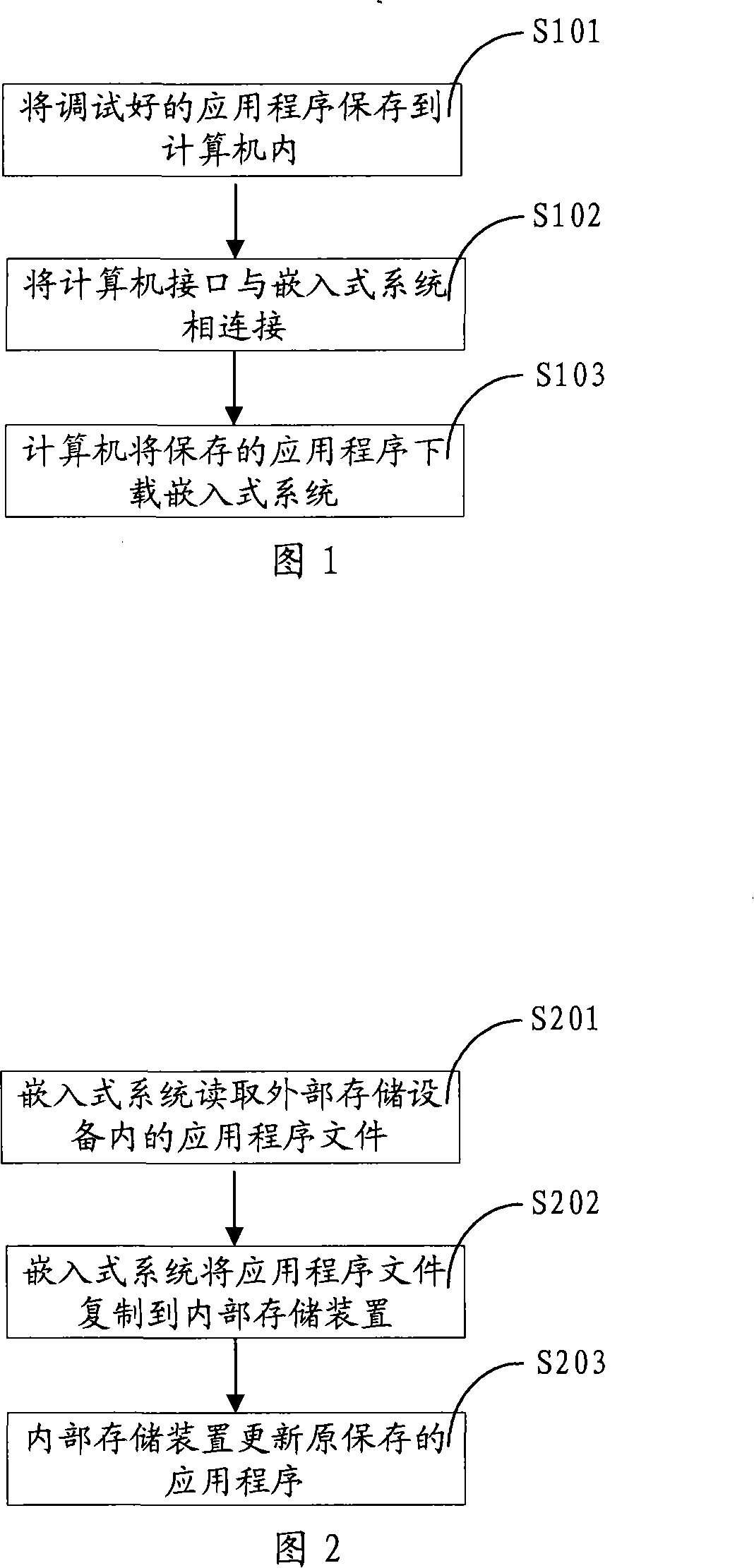
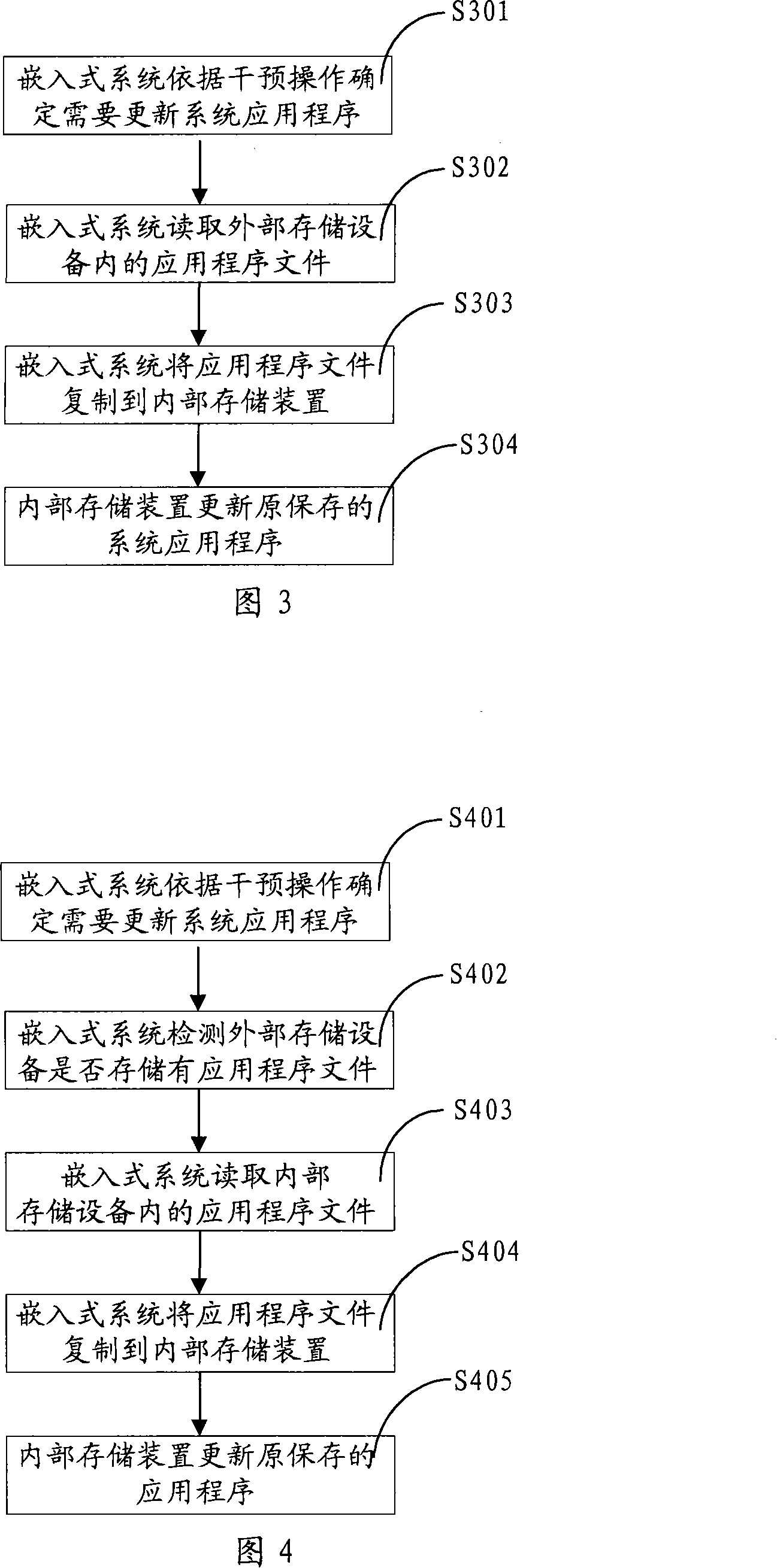
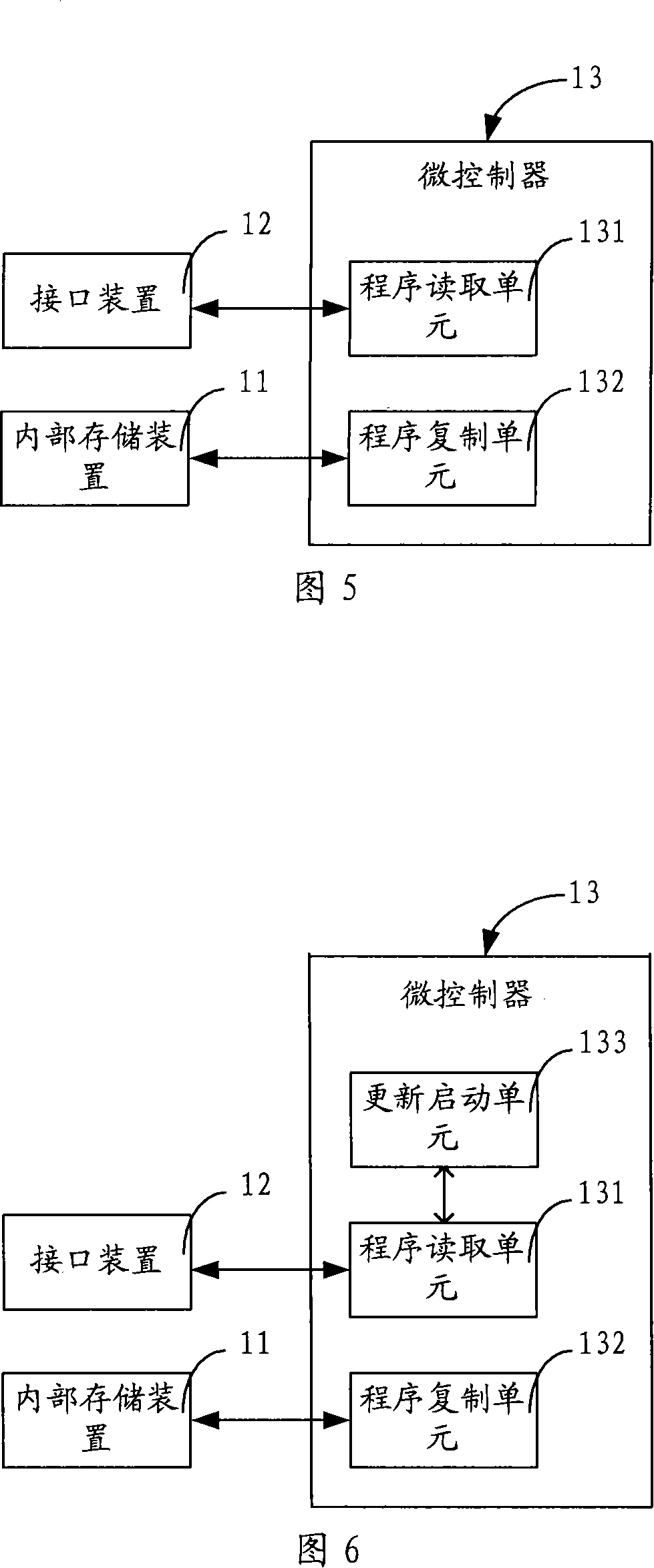
InactiveCN101169729AEasy to updateUpdate flexibleProgram loading/initiatingInternal memoryMicrocontroller
The invention relates to a method for updating application programs of an embedded system, which comprises detecting intervention operation, and if the detected intervention operation is the same as the preset intervention operation, updating the application programs. During the application program updating, the embedded system detects whether an internal interface device is connected with an external memory equipment, if yes, further determining whether the external memory equipment stores the application programs, the embedded system reads the application program files in the external memory equipment, copying the application program files to an internal memory device, which updates the application programs. Meanwhile, the invention also discloses an embedded system and a microcontroller. The invention can conveniently and flexibly update the application programs of the embedded system, and improve the maintainability of the equipment using the embedded system.
Owner:SANY HEAVY IND CO LTD (CN)
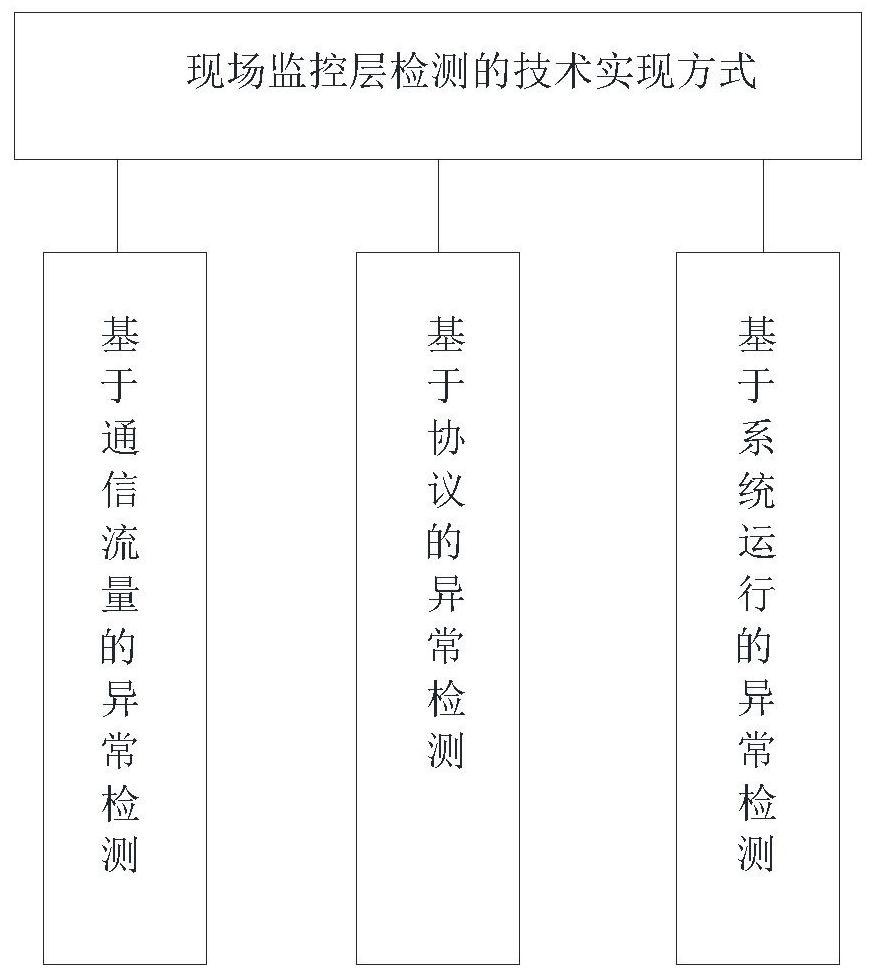
Industrial control security audit system based on protocol deep analysis and application thereof
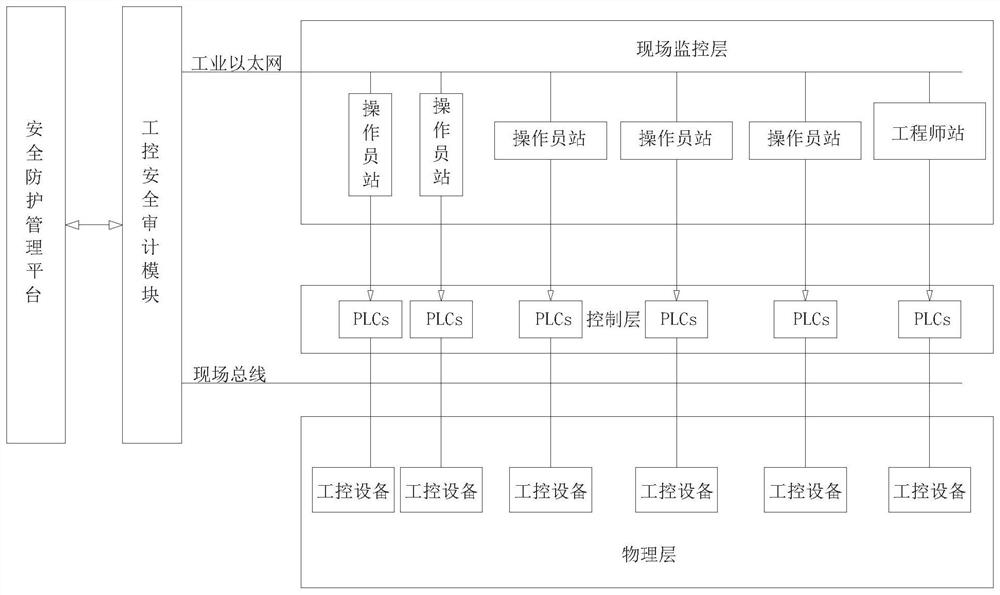
InactiveCN112306019AReal-time monitoring of data trafficAdd preliminary identificationTotal factory controlProgramme total factory controlReliability engineeringIndustrial network
The invention relates to an industrial control safety audit system based on protocol deep analysis and an application thereof. The system comprises an on-site monitoring layer, a control layer, a physical layer, an industrial control safety audit module and a safety protection management platform, the industrial Ethernet and an on-site bus are located between the field monitoring layer and the physical layer, the on-site monitoring layer performs data transmission and behavior control on the control layer through the industrial Ethernet, the physical layer is connected with the on-site bus through a sensor, an actuator and the like, and the on-site monitoring layer is mainly used for abnormality detection of an industrial network; according to the invention, targeted detection of abnormalbehaviors can be carried out, the accuracy is high, a physical layer realizes effective physical blocking of malicious behaviors such as network attacks and illegal access in operation of industrial control system equipment by controlling an interface of an external control line, and loss is stopped in time; the industrial control system equipment terminal security protection method is good in compatibility, better in applicability, convenient in equipment increase and decrease, and capable of flexibly updating the alarm rule base and improving the protection capability.
Owner:北京珞安科技有限责任公司
Network Video Unit
InactiveUS20150012590A1Update flexibleEfficient organizationTransmissionSelective content distributionDigital videoWorld Wide Web
Providing content to content receiving devices, such as digital video recorders, connected to a computer network through a content provider is described. According to one aspect, a server maintains a database correlating contact information to content receiving devices in its network. A user navigates to a web site of the content provider and selects a piece of content, which prompts the content provider to query the server for the contact information, and then transmit a request to download the piece of content to the content receiving device. The request can be a set of content identification information that automatically populates a content guide at the receiving device with an entry corresponding to the requested piece of content. This entry allows the user to confirm, interrupt, resume and cancel a download of the content as desired.
Owner:DIRECTV LLC
Method and integrity checking system for decoupled integrity monitoring
InactiveUS20190149557A1Update flexibleImprove integritySecuring communicationComputer hardwareCommunication unit
Provided is a method and an integrity checking system having an integrity checking unit and an integrity reporting unit for perturbation-free integrity monitoring of at least one first device, which is arranged in a first network having a high security requirement, by an integrity checking device, which is arranged in a second network having a low security requirement, having the method steps of: -providing check information for the data of the first device—that are to be monitored to an integrity checking device by means of a perturbation-free one-way communication unit, -checking the check information in the second network against at least one piece of reference information, and- transmitting a status report to an integrity reporting device in the first network.
Owner:SIEMENS AG
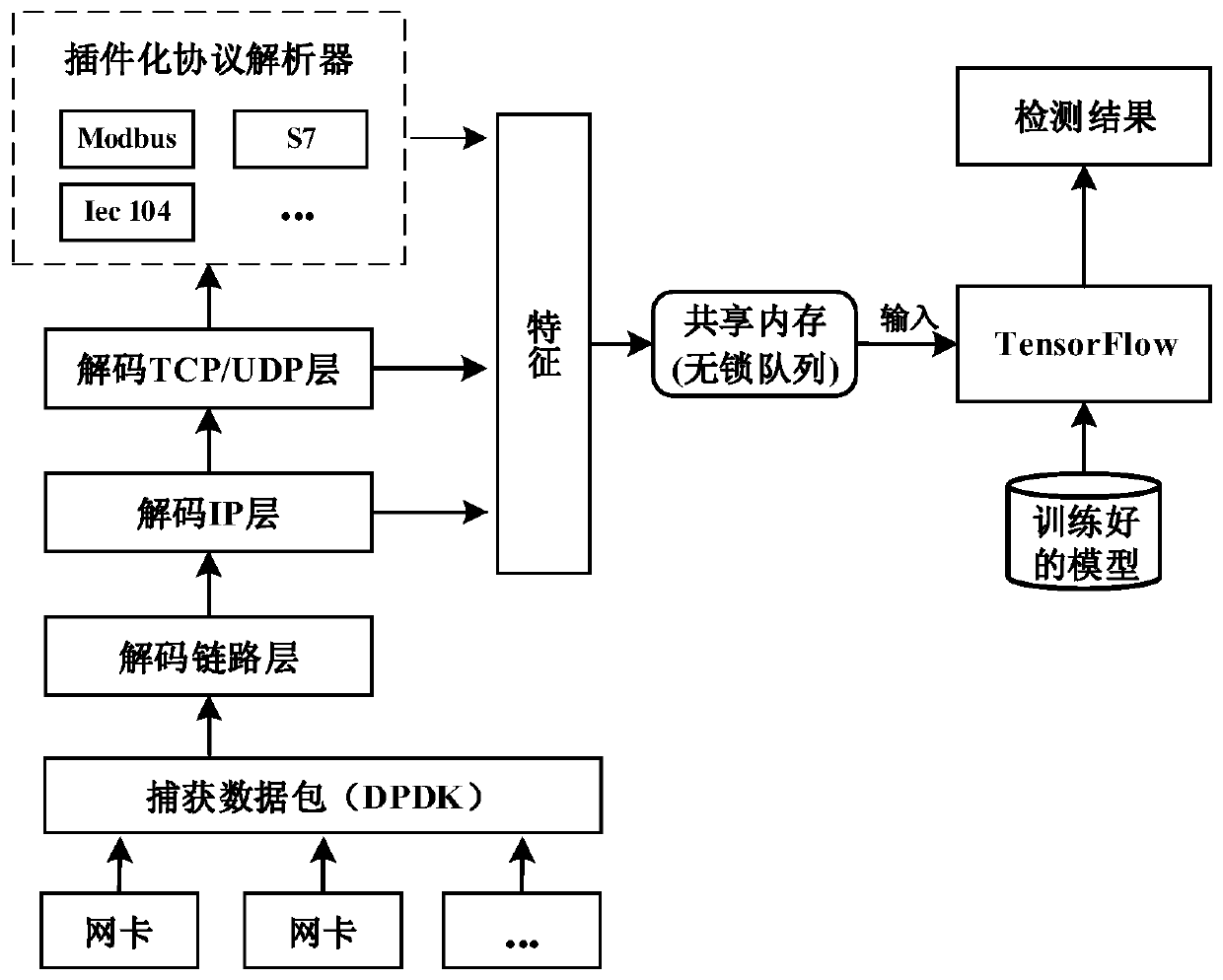
High-efficiency intrusion detection system for industrial control network
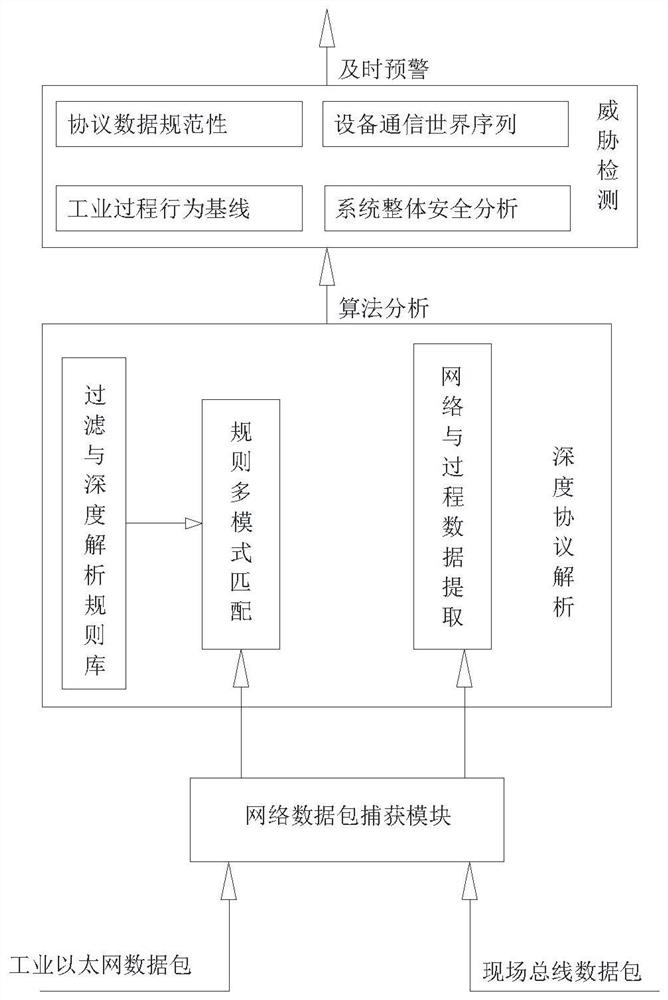
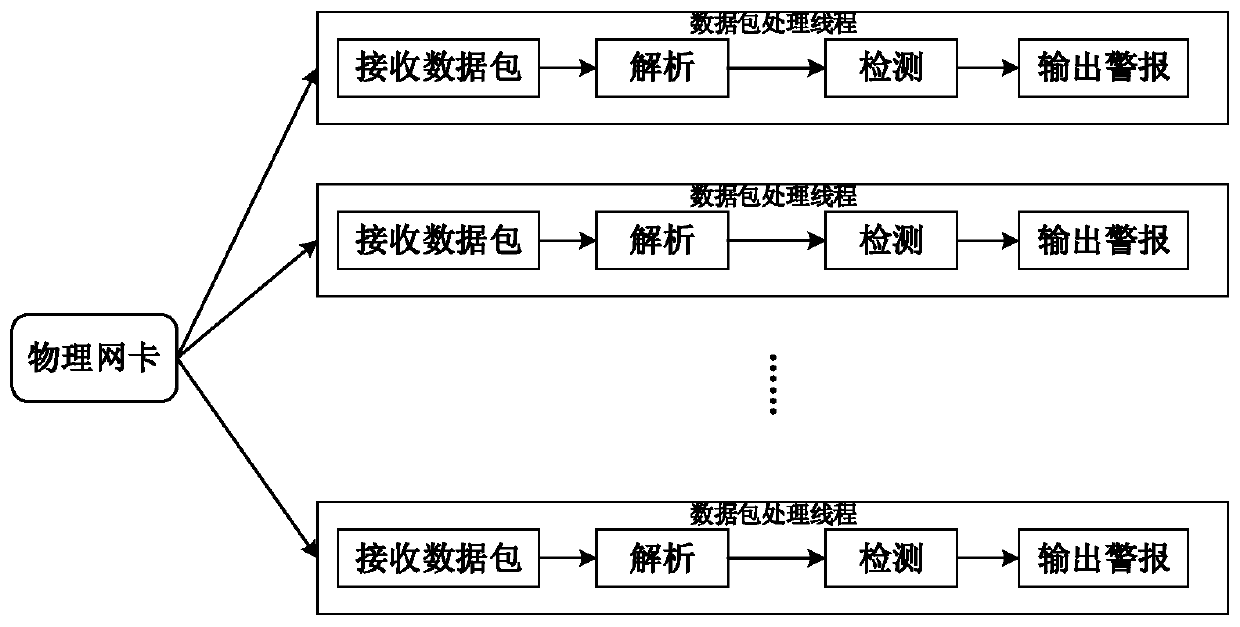
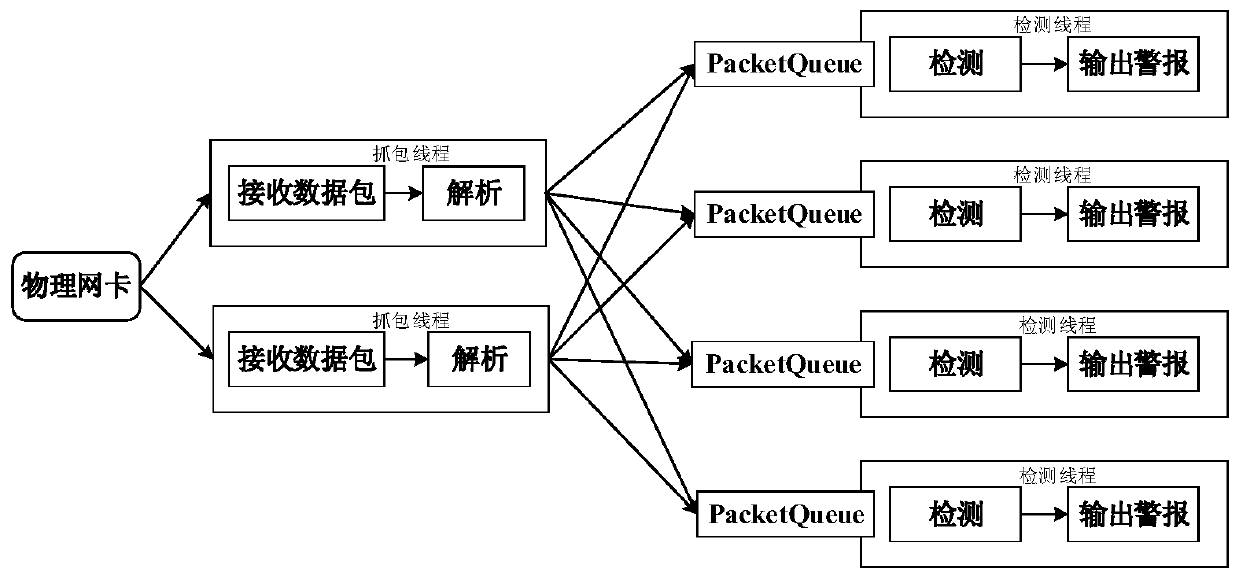
ActiveCN110995678AMeet the needs of capturing trafficAdd flexiblyTransmissionData packDistributed computing
The invention provides a high-efficiency intrusion detection system for an industrial control network. The system comprises a data packet capture system, a data packet analysis system and a TensorFlow-based detection system; the data packet capture system adopts DPDK to capture data packets, and then the data packet analysis system analyzes the captured data packets layer by layer and extracts features to queue into a shared memory; the TensorFlow-based detection system loads an offline training model, continuously takes out features from a shared memory as input for detection, and finally uploads a detection result to a Web end.
Owner:BEIHANG UNIV
Pump system
ActiveUS9863425B2Update flexibleAccurate and flexible regulationFluid-tightness measurementFluid pressure control using electric meansComputer moduleEngineering
A pump system for a water supply mains has at least one pump device, a pressure detecting sensor at the pressure side of the pump device, a flow detecting sensor of the pump device, several pressure sensor units (D) remote arranged remotely from the pump device in different part regions of the mains, and a pump control device. The control device includes a model formation module designed in each case to produce a model (A) representing pressure loss from the pressure sensor to the position of the respective pressure sensor unit (D), based on several pressure measured values of at least two pressure sensor units (D) for the at least two associated part regions. The control device is designed for regulation of the pump device based on produced models (A), as well as to a corresponding method for regulation of a pump device in a water supply mains.
Owner:GRUNDFOS HLDG
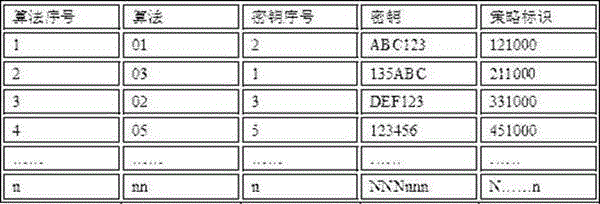
Algorithm and key library generation and updating method
ActiveCN106100834AUpdate flexibleImprove securityKey distribution for secure communicationSafety management systemsData information
The invention provides an algorithm and key library generation and updating method, and belongs to the technique of computer network communication and the field of information security. The method comprises the steps of generating an algorithm and key library through configuration of a safe management system, wherein the algorithm and key library is composed of an algorithm serial number, an algorithm, a key serial number, a key and a strategy identifier; calculating an increment factor according to the algorithm and key library and the initial version of the algorithm and key library, and issuing the increment factor to an encryption / decryption server; and generating the new version of the algorithm and key library by the encryption / decryption server through PCode operation according to the increment factor and the initial version of the algorithm and key library. The initial version of the algorithm and key library provided by the method is encrypted and then is stored in a database, the security is high and the storage quantity is high. According to the method, the increment factor can be generated randomly; the algorithm and key library can be updated flexibly; the algorithm and key library is safe and reliable; even if a key is intercepted by an attacker; data information contents will not be leaked; the cracking difficulty is increased; the security of data information transmission and user privacy is improved; and the method is high in popularization and implementation value.
Owner:咪付(深圳)科技有限公司
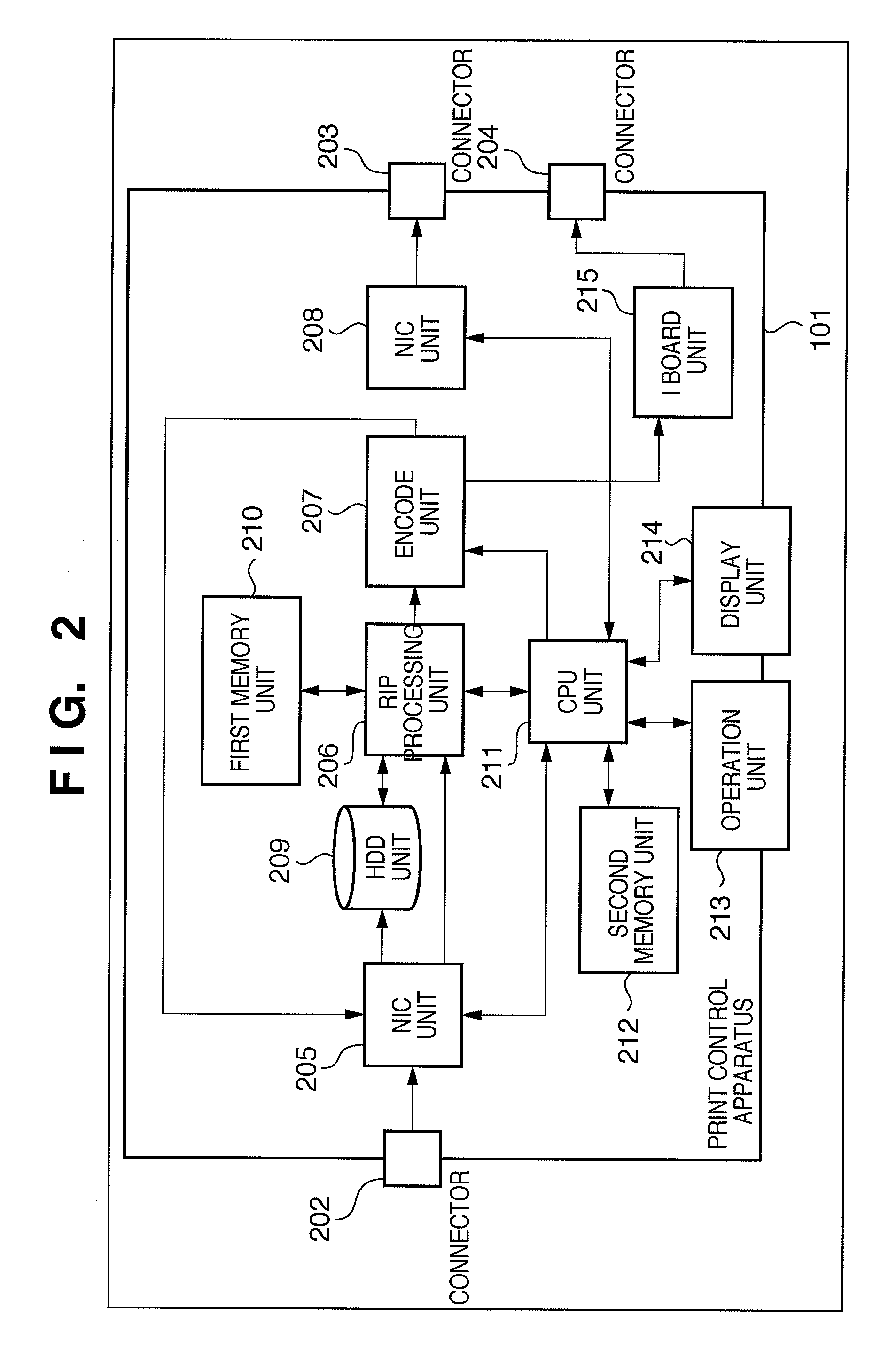
Print control apparatus, print control method and medium storing a print control program thereof
InactiveUS20090180139A1Updating of informationWithout degrading the print performance of the image forming apparatusDigitally marking record carriersDigital computer detailsComputer science
A print control apparatus of the present invention includes a database configured to manage counter information of an image forming apparatus; an obtain unit configured to periodically obtain the counter information from the image forming apparatus; an update unit configured to update the database based on the obtained counter information; a halt unit configured to halt the periodic obtaining of the counter information in response to start notification of processing based on a print job in the image forming apparatus; and a restart unit configured to restart the periodic obtaining of the counter information in response to completion notification of processing based on the print job in the image forming apparatus.
Owner:CANON KK
Real-time intrusion detection method based on data mining
InactiveCN102521378AReal-time detection capabilityFlexible storageTransmissionSpecial data processing applicationsModel managementEngineering
The invention relates to a real-time intrusion detection method based on data mining. An ASM (adaptive strategy management) module and an AMM (adaptive model management) module are added into a distributed real-time system framework and used for automatically generating and distributing detection strategies and detection models of an intrusion detection system based on data mining respectively. By the aid of the structure, the problems in terms of automation of related data, automatic generation and distribution of the detection models and the detection strategies, and real-time data evaluation can be solved. A distributed system comprises some components which can be flexibly changed in the system framework to adapt to different environmental changes and meet the demands of users.
Owner:NANJING UNIV OF POSTS & TELECOMM
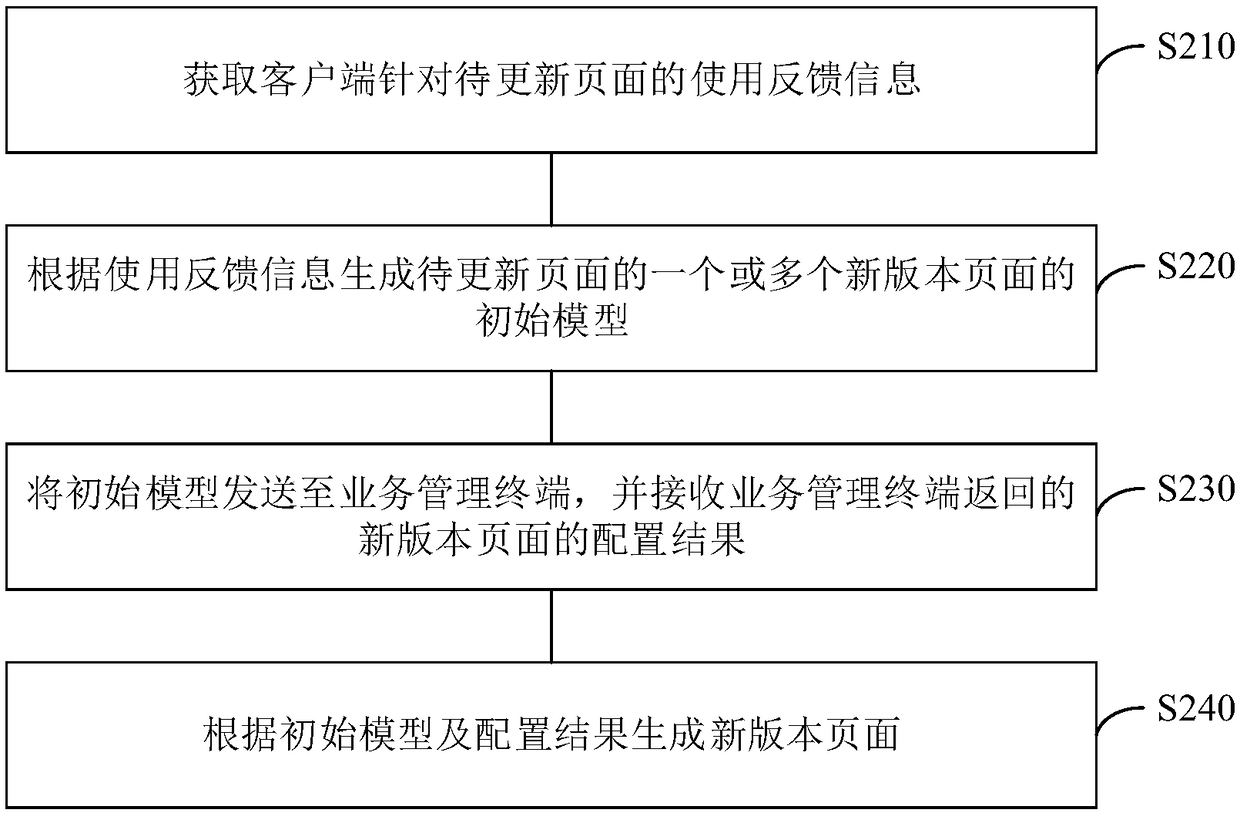
Big data-based page updating method and device, electronic device and storage medium
PendingCN109445818AShorten the update cycleFlexible update processSoftware deploymentPersonalizationElectronic equipment
The invention provides a big data-based page updating method and device, an electronic device and a computer readable storage medium, belonging to the technical field of big data. The method comprisesthe following steps of obtaining the feedback information of the use of the client for the page to be updated; generating an initial model of one or more new version pages of the page to be updated according to the feedback information; sending the initial model to a service management terminal, and receiving a configuration result of the new version page returned by the service management terminal; and generating the new version page according to the initial model and the configuration result. The invention can conveniently and quickly realize the page updating and meet the personalized requirements of users on the page.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
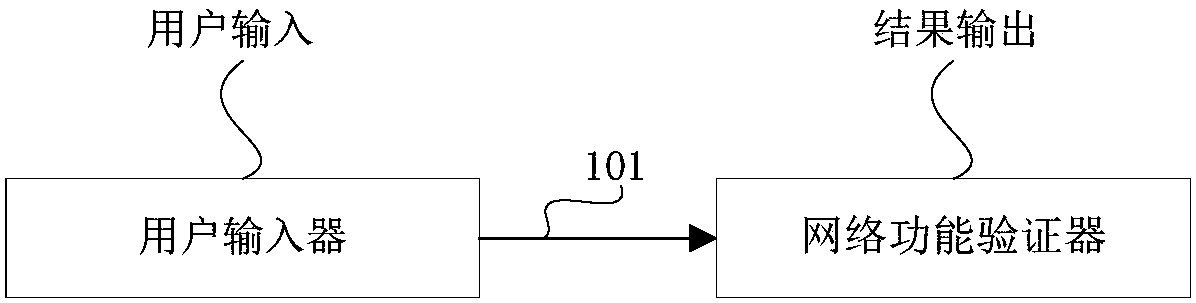
NFV-oriented network function verification method and verification system
ActiveCN107749807APromote rapid developmentRapid deploymentData switching networksService flowTest script
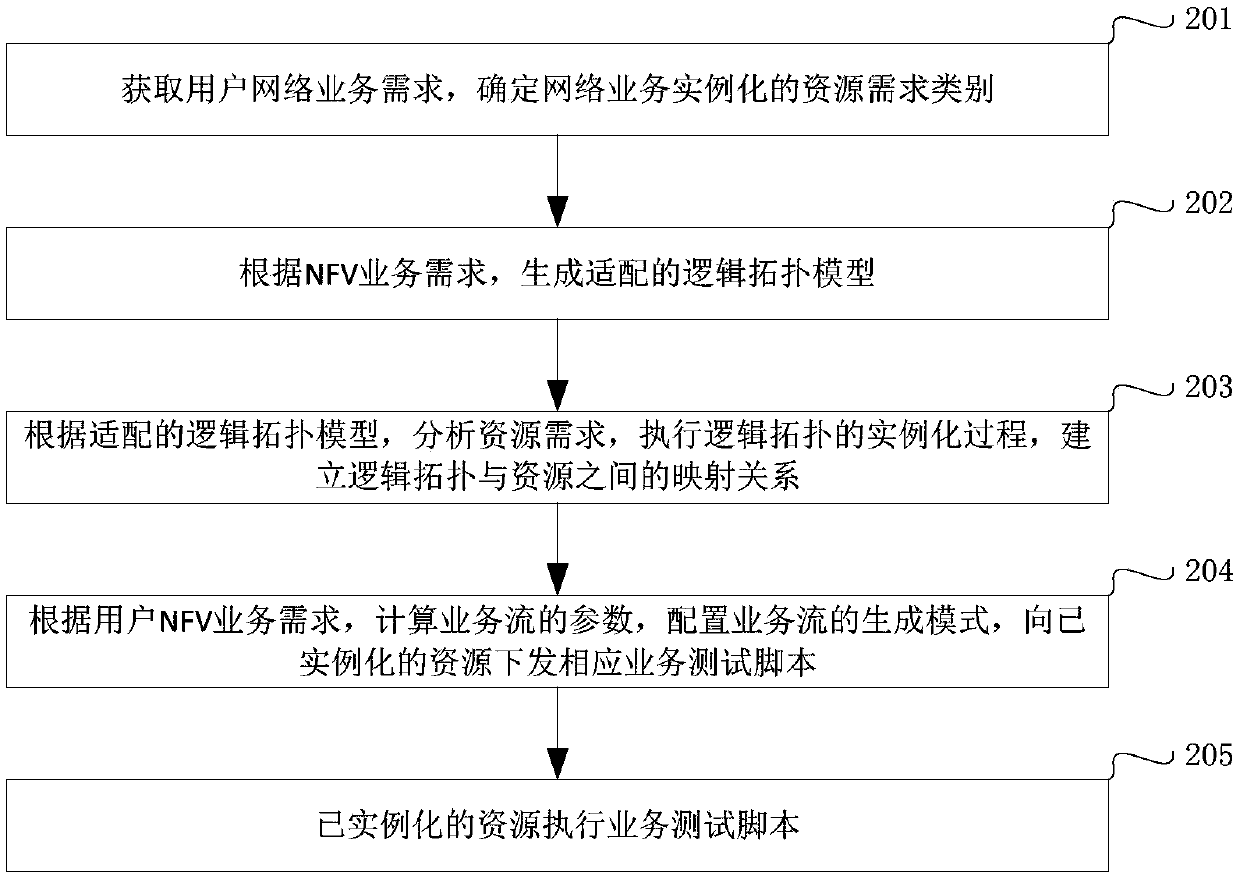
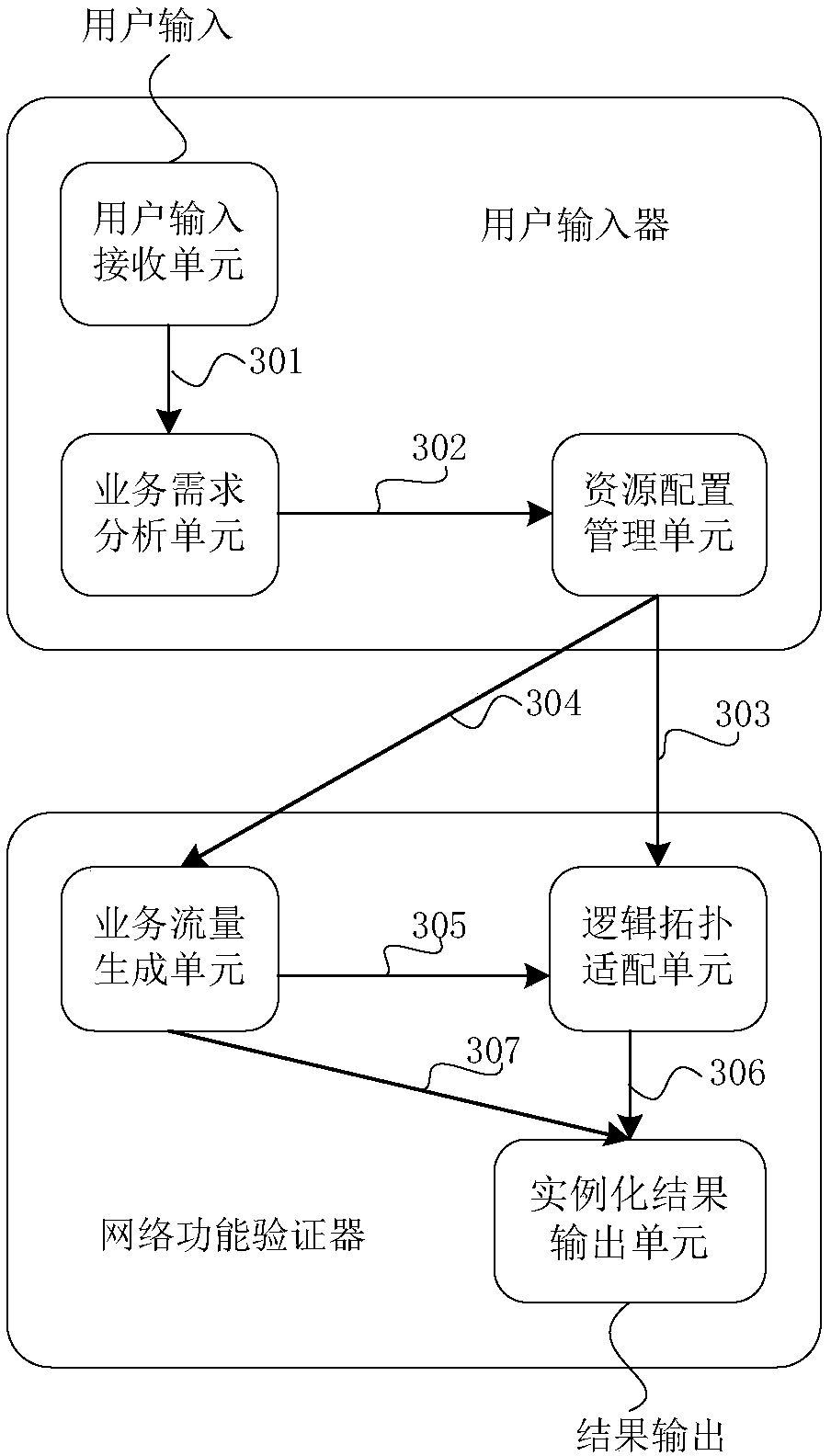
The invention discloses an NFV-oriented network function verification method and verification system. The verification method is based on a verification system which is composed of a user inputting device and a network function verifier, and specifically comprises a step 1 of obtaining a user network service demand and determining a resource demand category of network business instantiation; a step 2 of generating a logic topology model adaptive to the network service instantiation based on a network function virtual NFV service demand; a step 3 of analyzing a resource demand based on the logic topology model, performing the instantiation process of the logic topology model and building a mapping relationship between the logic topology and resources; a step 4, calculating parameters of a service flow based on the user NFV service demand configuring a generation mode of the service flow and distributing a corresponding service test script to instantiated resources; and a step 5 of executing the service test script for the instantiated resources. The NFV-oriented network function verification method can instantiate the network verification environment based on network service demandsof different users and can carry out service-flow-supporting test and analysis automatically.
Owner:JIANGSU FUTURE NETWORKS INNOVATION
OTA method and system based on instant messaging platform
ActiveCN1755613AImprove personalizationEasy to updateData switching networksSpecific program execution arrangementsPersonalizationClient-side
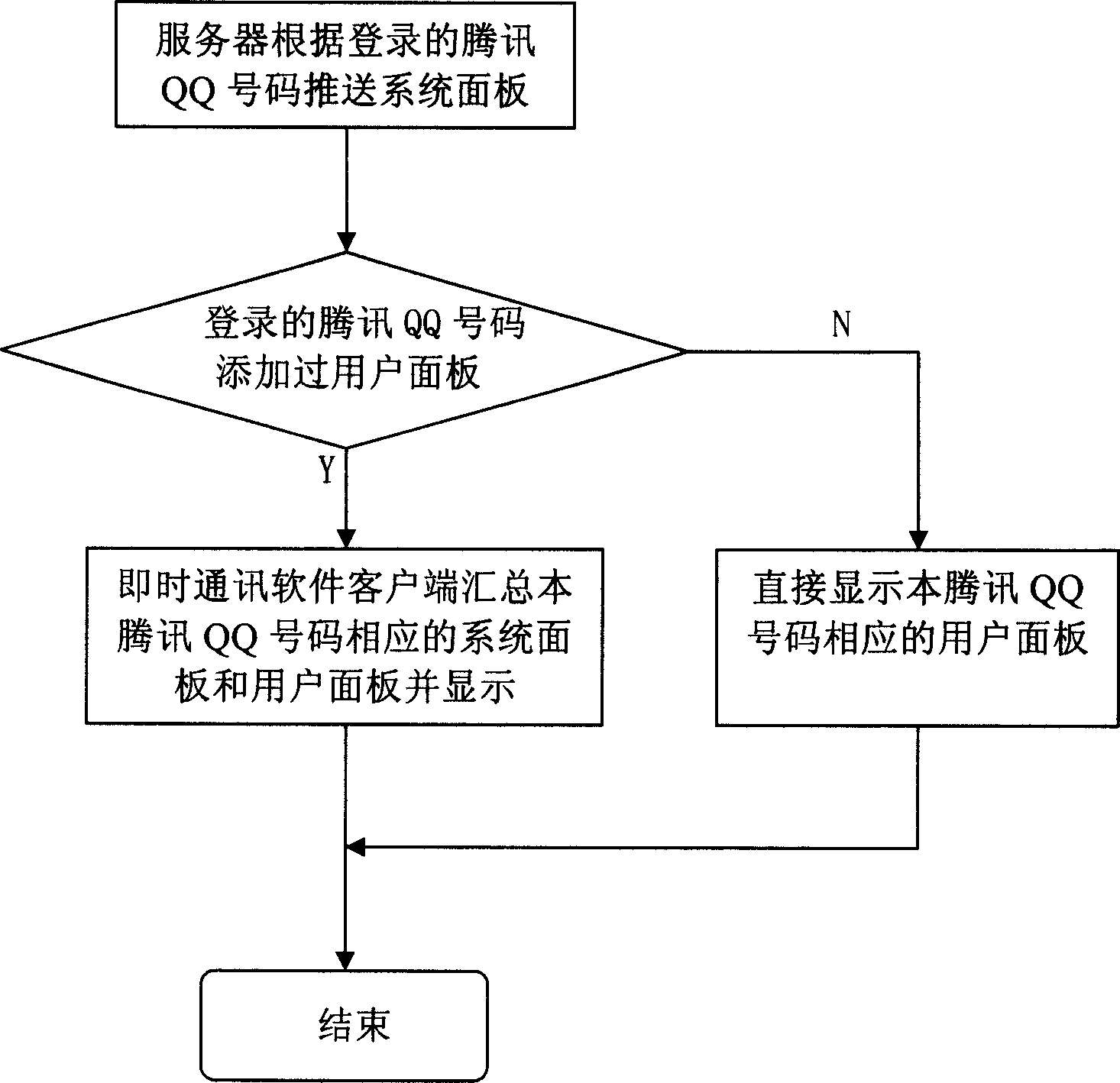
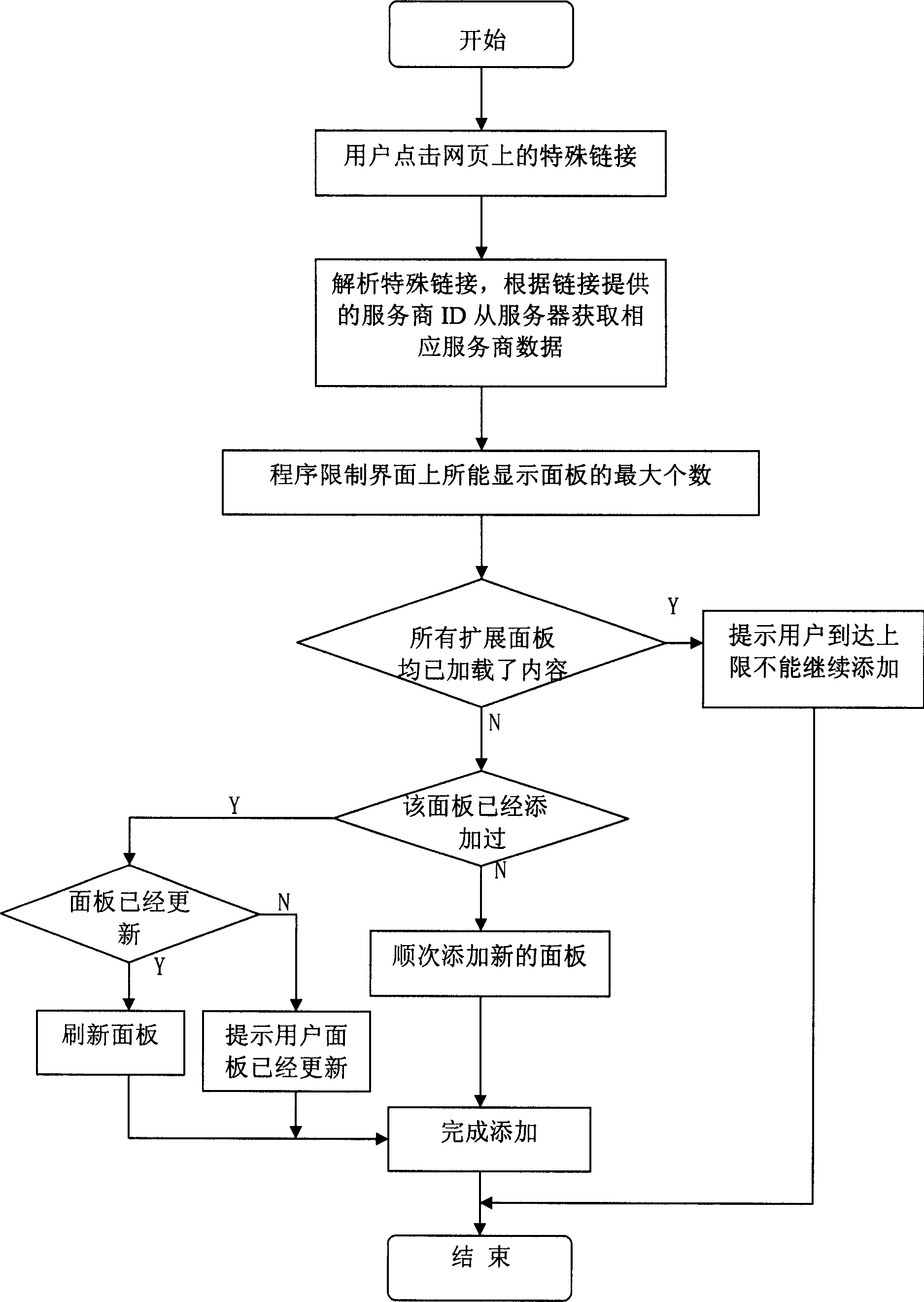
The invention relates to an air loading method and system based on a press communicating platform in the field of computer press communication and network online technology. The method comprises: 101, the press communicating software requests the plane data to the server when landing; 102, the server ascertains the content, the amount and the location of the display plane according to the plane data and displays them; 103, the press communicating server ascertains all of the user plane number has not amount to the top limit; 104, the press communicating server ascertains the waited plane has not been added and adds it into the user plane. The system comprises: a press communicating user end, a plane providing server and a press communicating server.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com