Algorithm and key library generation and updating method
An update method and key store technology, which are applied in the field of algorithm key store generation and update, can solve the problems that data information cannot achieve high security, algorithm protocol identification, and low security, so as to increase the difficulty of cracking and improve security The effect of high sex and safety improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described below in conjunction with the examples, but the protection scope of the present invention is not limited to the following specific examples.
[0022] The new version of the algorithm key storehouse described in the embodiment of the present invention is generated by the initial version of the algorithm key storehouse, the increment factor and the PCode according to certain operation rules, and realizes real-time update, and the algorithm key storehouse can be according to the process Synchronize or enable the rule, and receive the feedback result of synchronization and activation. The state of the algorithm keystore is one or more of disabled, synchronizing, synchronizing, enabling, enabled, and deactivated. Further In other words, data that is not enabled or disabled in the stated status will be periodically deleted by the system.
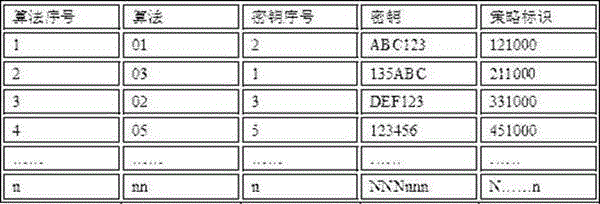
[0023] This embodiment provides a method for generating and updating an algorithm keystore...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com