Real-time intrusion detection method based on data mining
A technology of intrusion detection and data mining, applied in the direction of electrical digital data processing, special data processing applications, instruments, etc., can solve the problem of incomplete and inaccurate expert knowledge, difficult to modify or merge with new detection models, and lack of detection of attack methods Ability and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
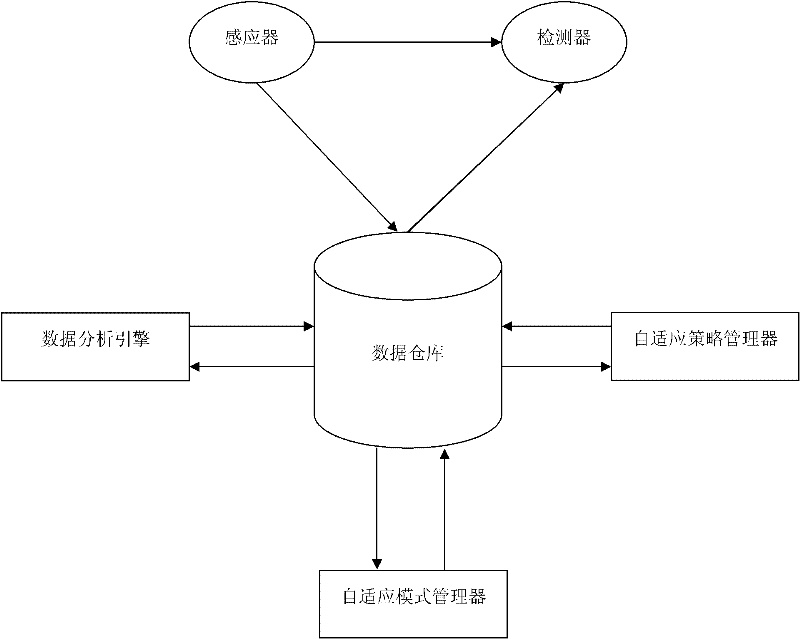
[0038] figure 1 is an architecture of the present invention which includes sensors, detectors, a data warehouse, data analysis engine, adaptive policy manager and adaptive pattern manager. The system adopts a distributed architecture and consists of a series of automation components. The components here are independent in design, but can be centrally managed through the data warehouse. Components access each other through a public protocol, where the public protocol uses Extensible Markup Language (XML).
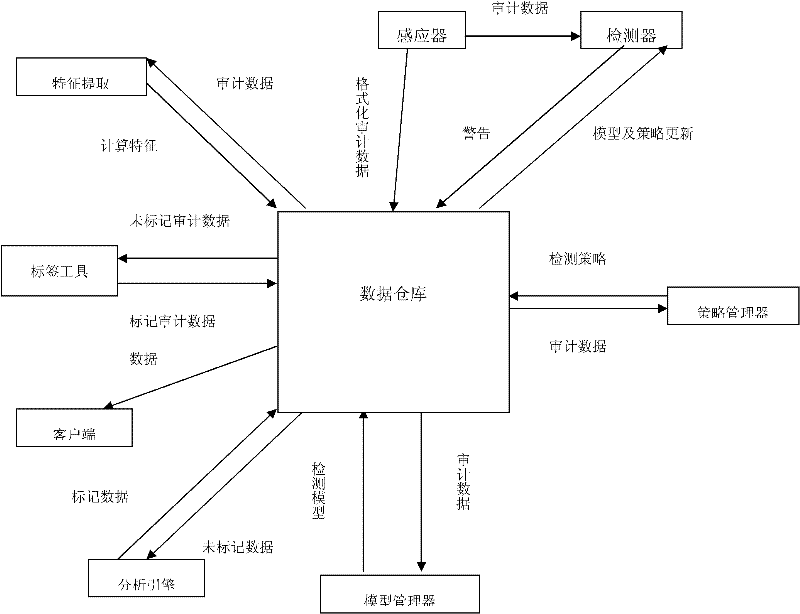
[0039] The basic working relationship between various components such as figure 2 shown.
[0040] Below is the main workflow of the present invention:
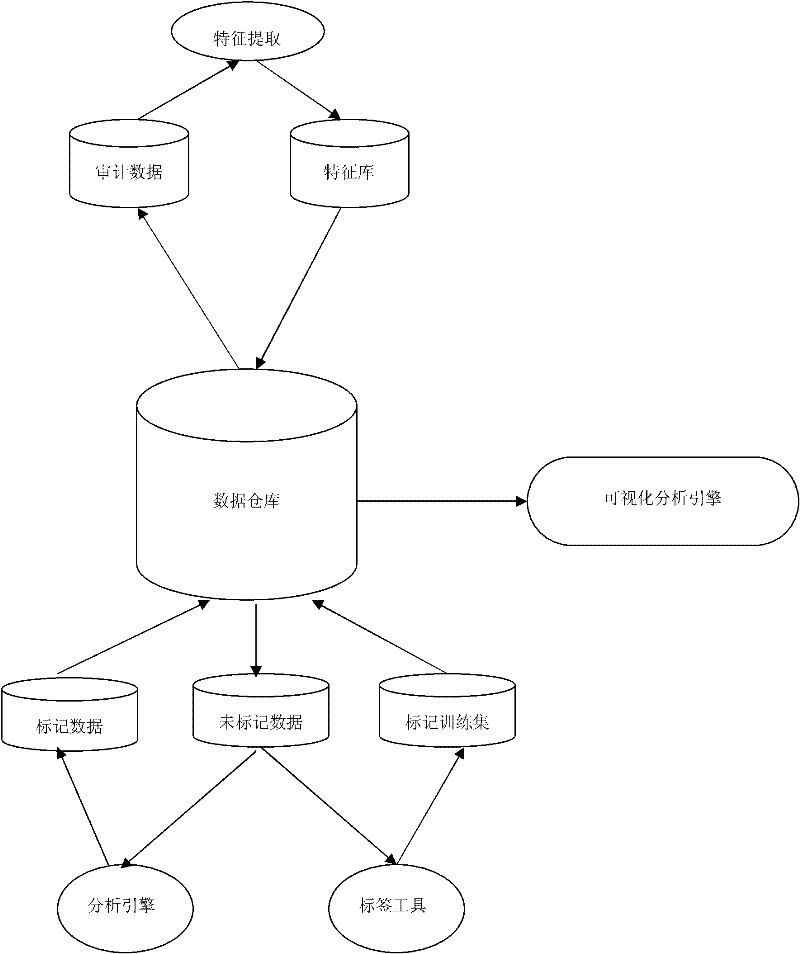
[0041] The sensor collects and formats information from the system environment or network environment, and then sends it to the data warehouse for storage. The data analysis engine extracts information from the data warehouse in real time, uses the marking tool to mark the data, and extracts the features of the marked i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com