A method for enhancing security of authentication process between network elements of core network based on 5G AKA
A core network and security technology, applied in security devices, electrical components, wireless communications, etc., can solve problems such as information theft, achieve the effects of preventing leakage, low cost, and avoiding failure of security measures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
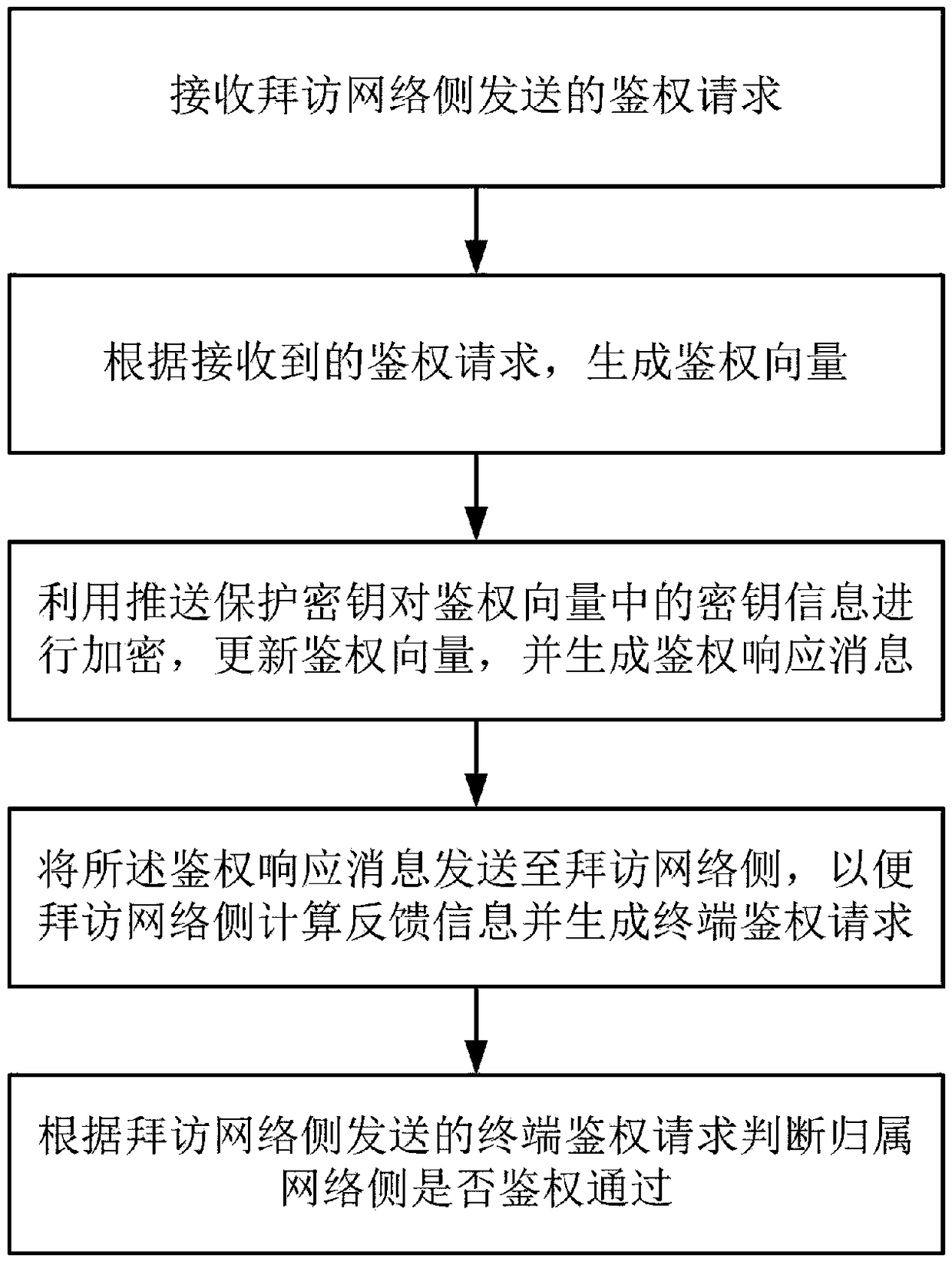
[0095] Embodiment 2 of the present invention discloses a 5G AKA-based authentication process security enhancement method between network elements of the core network, which is applied to the home network side, such as figure 2 As shown, the steps are as follows:
[0096] Receive the authentication request sent by the visited network side;
[0097] Generate an authentication vector according to the received authentication request;
[0098] Encrypt the key information in the authentication vector by using the push protection key, update the authentication vector, and generate an authentication response message;
[0099] Sending the authentication response message to the visited network side, so that the visited network side calculates feedback information and generates a terminal authentication request;
[0100] According to the terminal authentication request sent by the visited network side, it is judged whether the home network side has passed the authentication.
[0101] C...
Embodiment 3
[0102] Embodiment 3 of the present invention discloses that when the authentication method is 5G AKA, the following operations are performed inside the home network side, wherein the network elements on the home network side include AUSF and UDM:
[0103] The AUSF receives the authentication request sent by the visited network side, and sends the authentication request to the UDM;
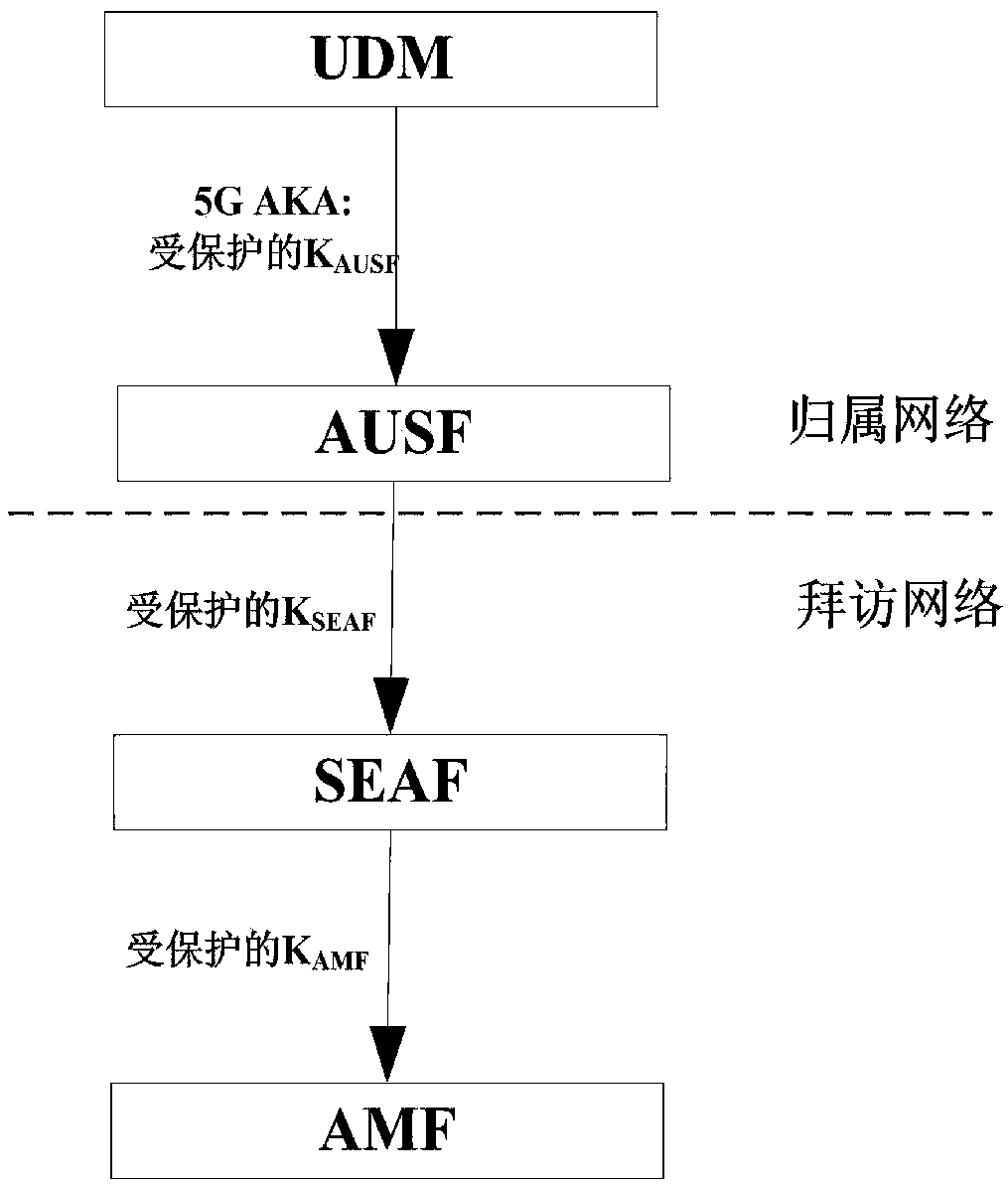
[0104] UDM generates a 5G home authentication vector, and the 5G home authentication vector is RAND||XRES*||K AUSF ||AUTN, where, RAND (random number), XRES (Expected Response, expected response), K AUSF (AUSF security key), AUTN (Authentication Token, authentication token), AUTN contains serial number, AMF and MAC fields;
[0105] Protect key K with push T1 (Push protection key between AUSF and UDM) to AUSF security key K AUSF Encrypt to get the encrypted AUSF security key K AUSF ';
[0106] UDM assigns the K in the 5G home authentication vector AUSF Replaced with the encrypted AUSF security...
Embodiment 8
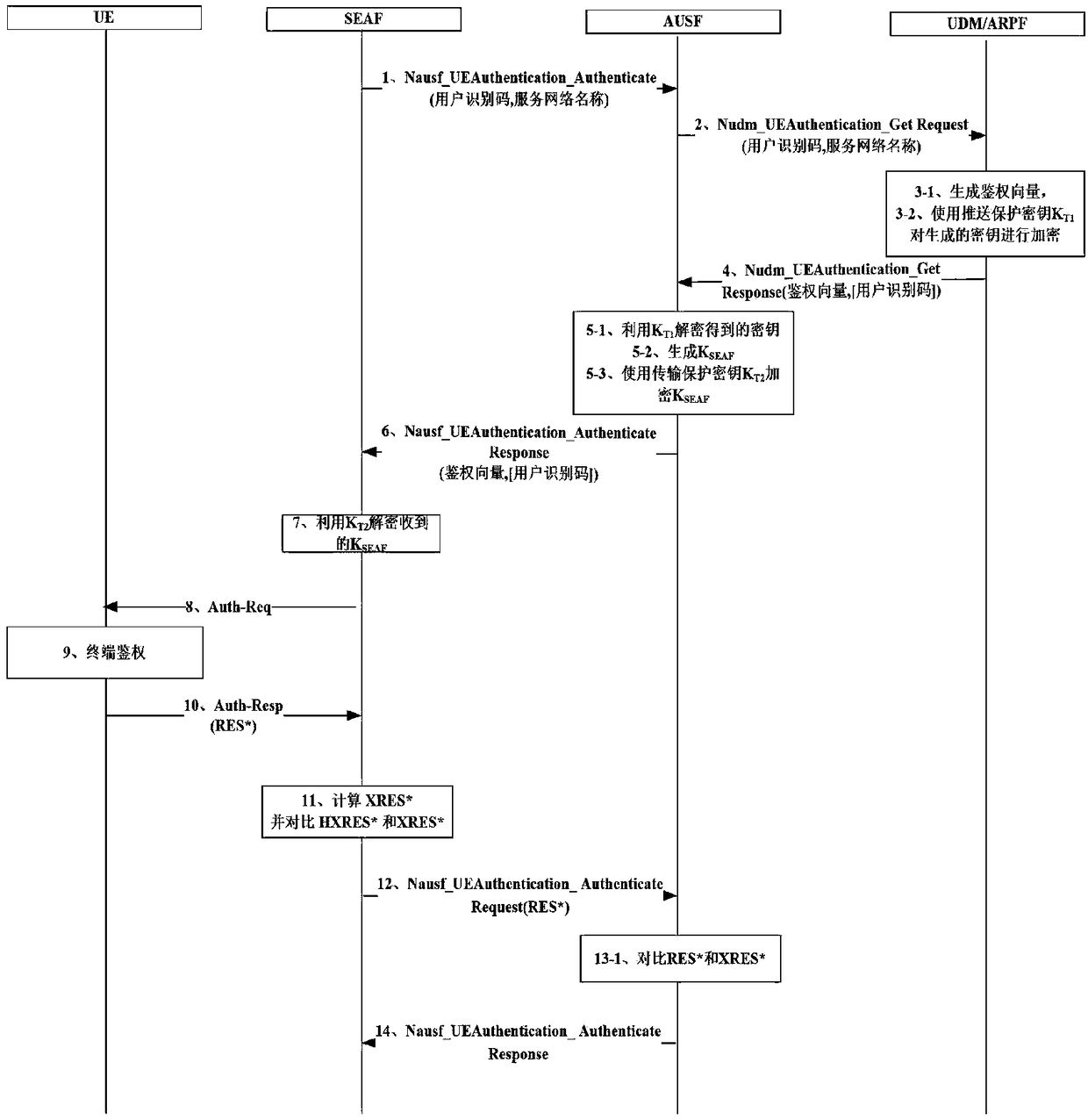
[0157] Embodiment 8 of the present invention discloses the encrypted transmission process of key information between network elements of the core network when the authentication method is 5G AKA, as shown in image 3 As shown, the steps are as follows:
[0158] Step S1: According to the 3GPP standard process, SEAF receives the registration of the terminal user UE, sends an authentication request to the network element AUSF on the home network side of the terminal user, and sends SUPI (Subscription Permanent Identifier, registered user permanent identification code) and service network name ( SN name) and other information are sent to AUSF;
[0159] Step S2: According to the 3GPP standard procedure, the AUSF sends the authentication request information to the UDM;
[0160] Step S3: UDM generates an authentication vector and encrypts the key information in it:
[0161] Step S3-1: According to the 3GPP standard process, the 5G home authentication vector generated by UDM include...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com