An eap-aka'-based method for enhancing the security of the authentication process between network elements of the core network
An EAP-AKA, core network technology, applied in security devices, secure communication devices, and key distribution, can solve problems such as information theft, and achieve the effects of enhanced security, low cost, and low system transformation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0093]Example 1 of the present invention discloses an EAP-AKA '-based core network element interval security enhancement method, including the following steps:
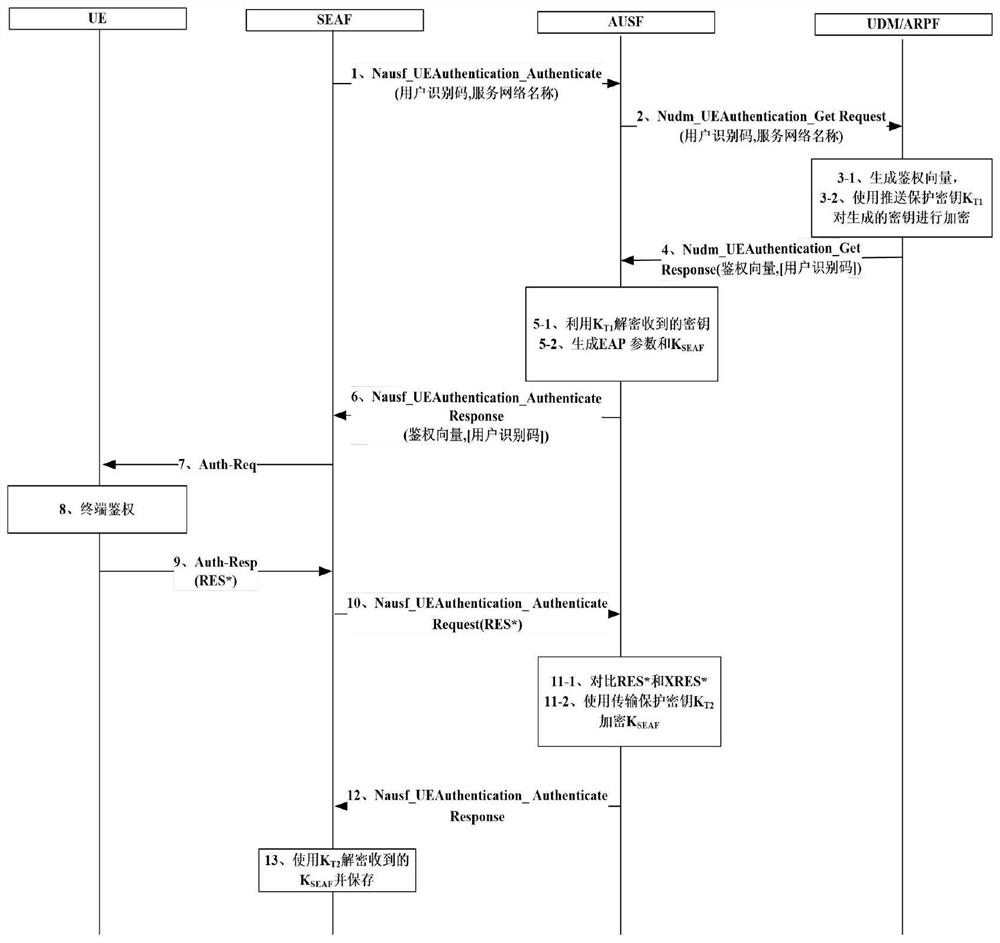
[0094]Visit the network side to send authentication requests;
[0095]The home network side generates authentication vector according to the received authentication request; use the push protection key KT1Encrypt the key information in the authentication vector, and update the authentication vector, and generate an authentication response message; send the authentication response message to the reference network side;
[0096]Visiting the authentication response message of the home network side feedback, calculates the feedback information, determines whether the feedback network is authenticated according to the feedback information; pass, then send a terminal authentication request to the home network side;
[0097]The home network side determines whether the home network side is authenticated according to the terminal authentication...
Embodiment 2
[0100]Embodiment 2 of the present invention discloses an EAP-AKA '-based core network element method for EAP-AKA', the steps are disclosed, and the steps are as follows:
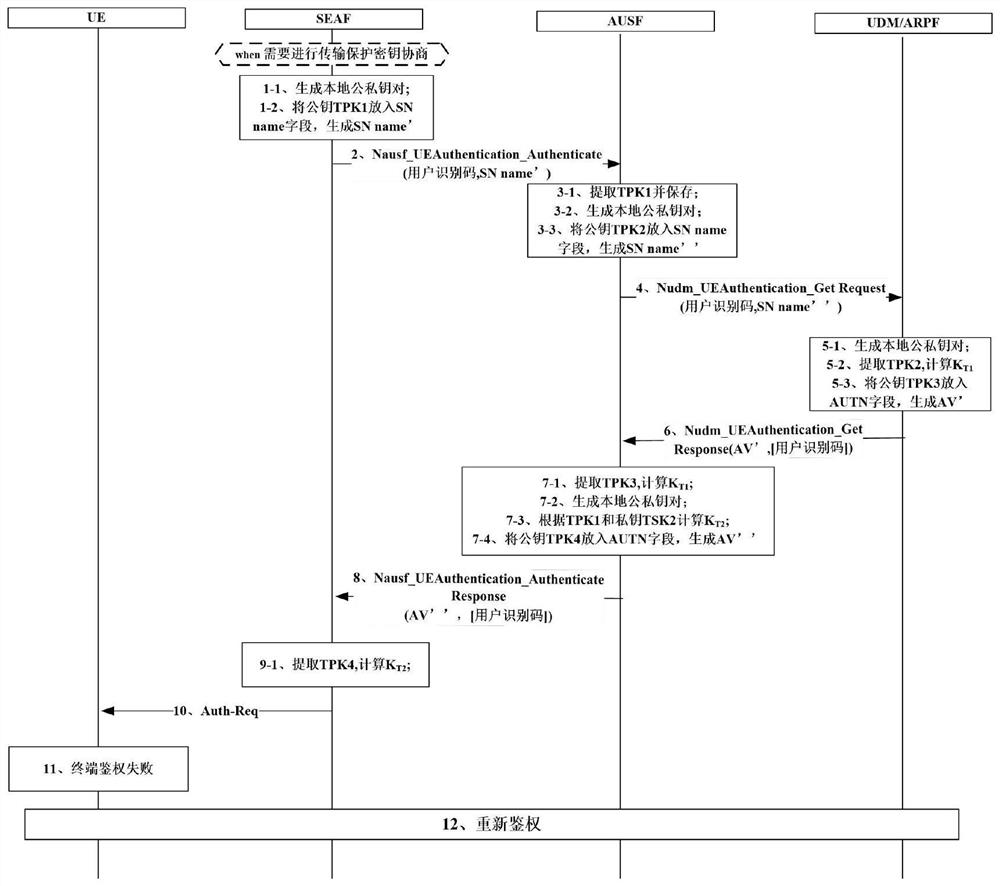
[0101]Receive the authentication request sent by the visiting network side;
[0102]Generate an authentication vector according to the received authentication request;
[0103]Using the push protection key to encrypt the key information in the authentication vector, update the authentication vector, and generate an authentication response message;
[0104]Send the authentication response message to the reference network side to place the feedback information on the network side and generate a terminal authentication request;
[0105]Judging whether the home network side is authenticated according to the terminal authentication request sent by the visiting network side.
[0106]Compared with the prior art, the EAP-AKA '-based core network element inter-AK-AKA's core network element is encrypted using the push protection key to encry...
Embodiment 3
[0107]Embodiment 3 of the present invention, when the authentication method is EAP-AKA ', the following operation is performed inside the home network side:
[0108]Receive the authentication request sent by the AUSF to the network side, and send the authentication request to the UDM;
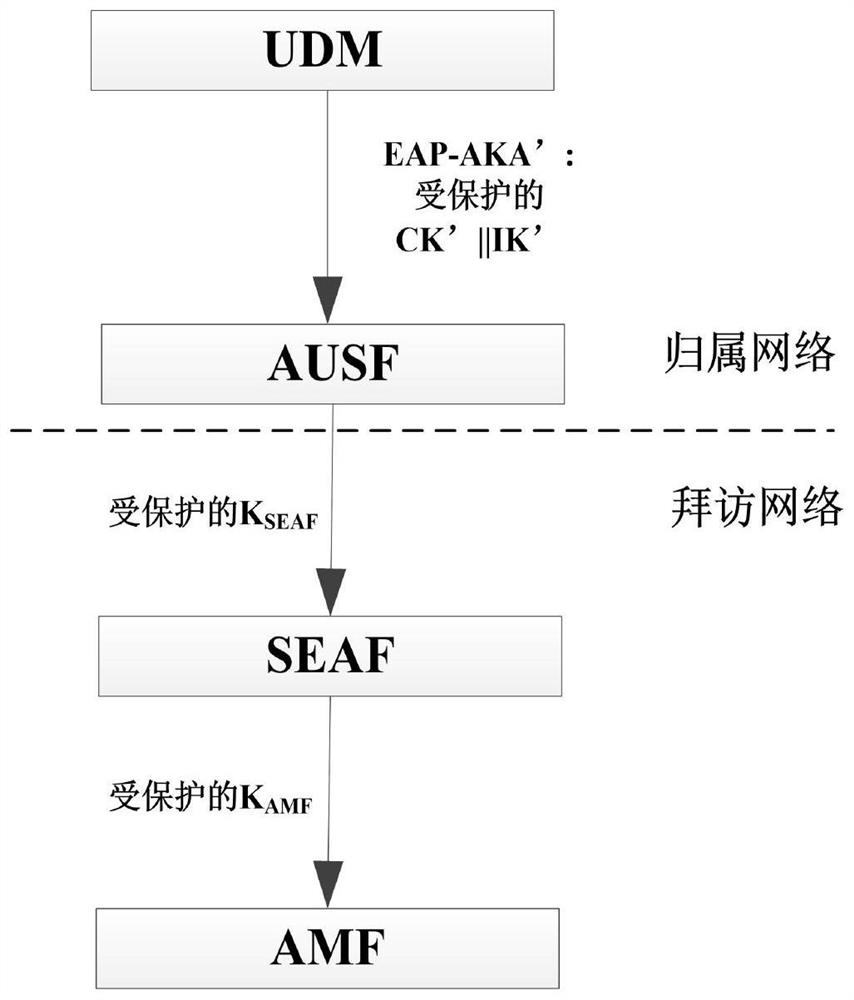
[0109]UDM generates authentication vector, the authentication vector is RAND || xres || ck '|| IK' || AUTN;
[0110]Use push protection key KT1Encrypt the key information CK '|| IK' to get the encrypted key information (CK '|| IK') ';
[0111]The UDM replaces the CK '|| IK' in the authentication vector to the encrypted key information (CK '|| IK') 'to obtain the protected authentication vector and transmit the protected authentication vector. To AUSF;
[0112]The AUSF receives the protected authentication vector sent by the UDM, using the push protection key KT1The protected authentication vector (CK '|| IK') 'is decrypted;
[0113]AUSF is derived and calculated by EAP security parameters, and also has a SEAF security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com