Fusion and authentication method and system of identity and authority in industrial control system
An industrial control system and authentication method technology, which is applied in the field of identity and authority authentication, can solve the problems of inconvenient use and management, inconvenient confirmation of its authority, inapplicability of identity certificates and attribute certificates, etc., to achieve complete information preservation and management Convenience and large storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] In order to make the purpose, technical solution and advantages of the present invention clearer, the following will further describe the implementation of the present invention in detail in conjunction with the accompanying drawings.
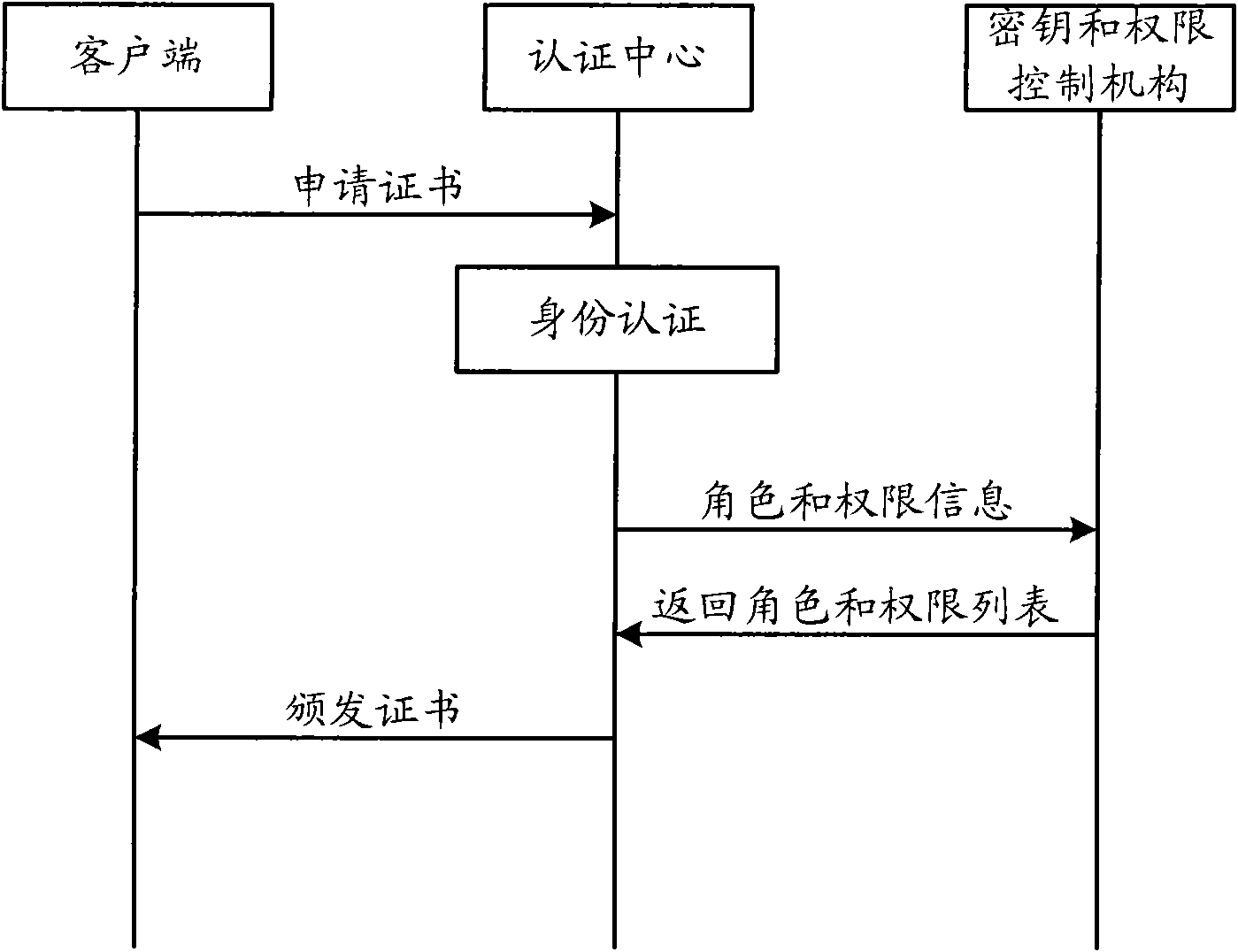
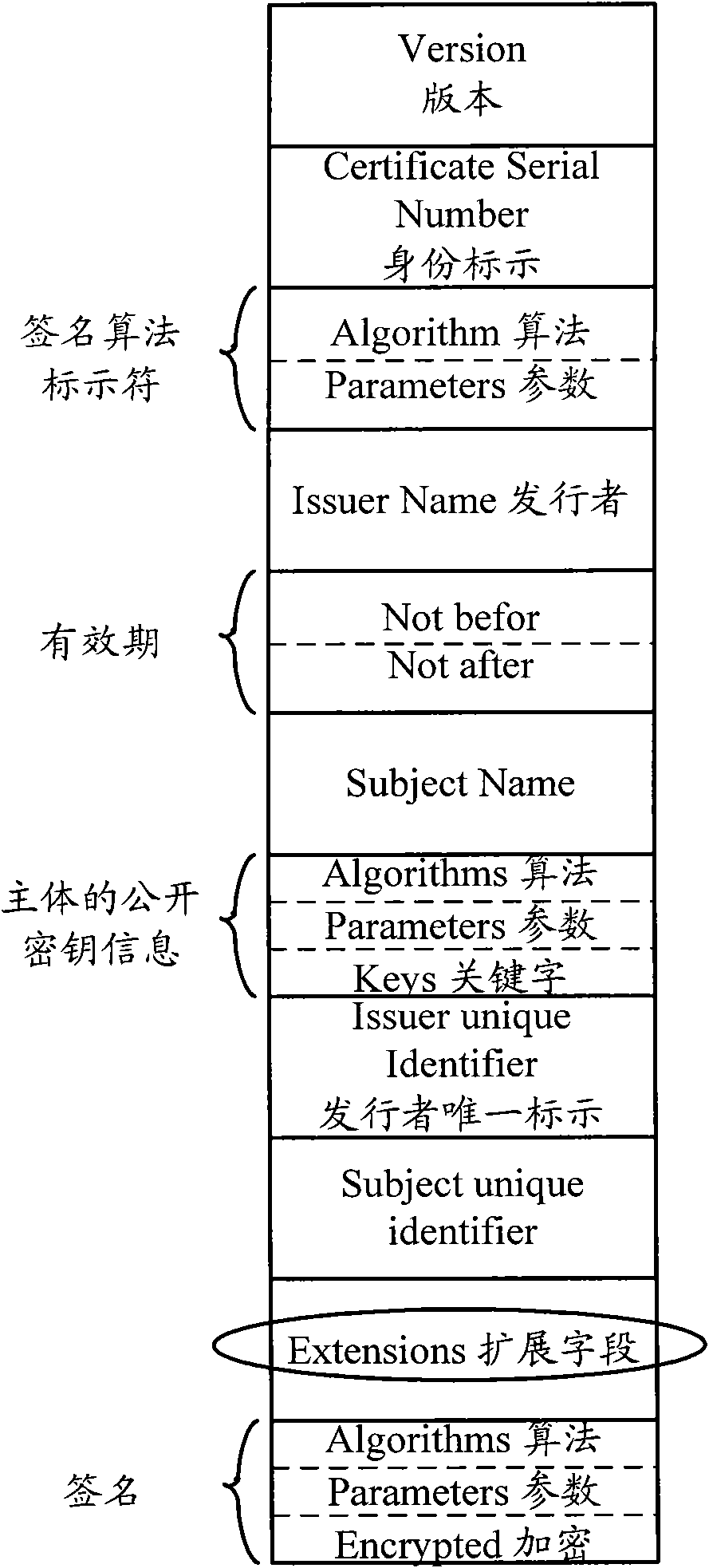
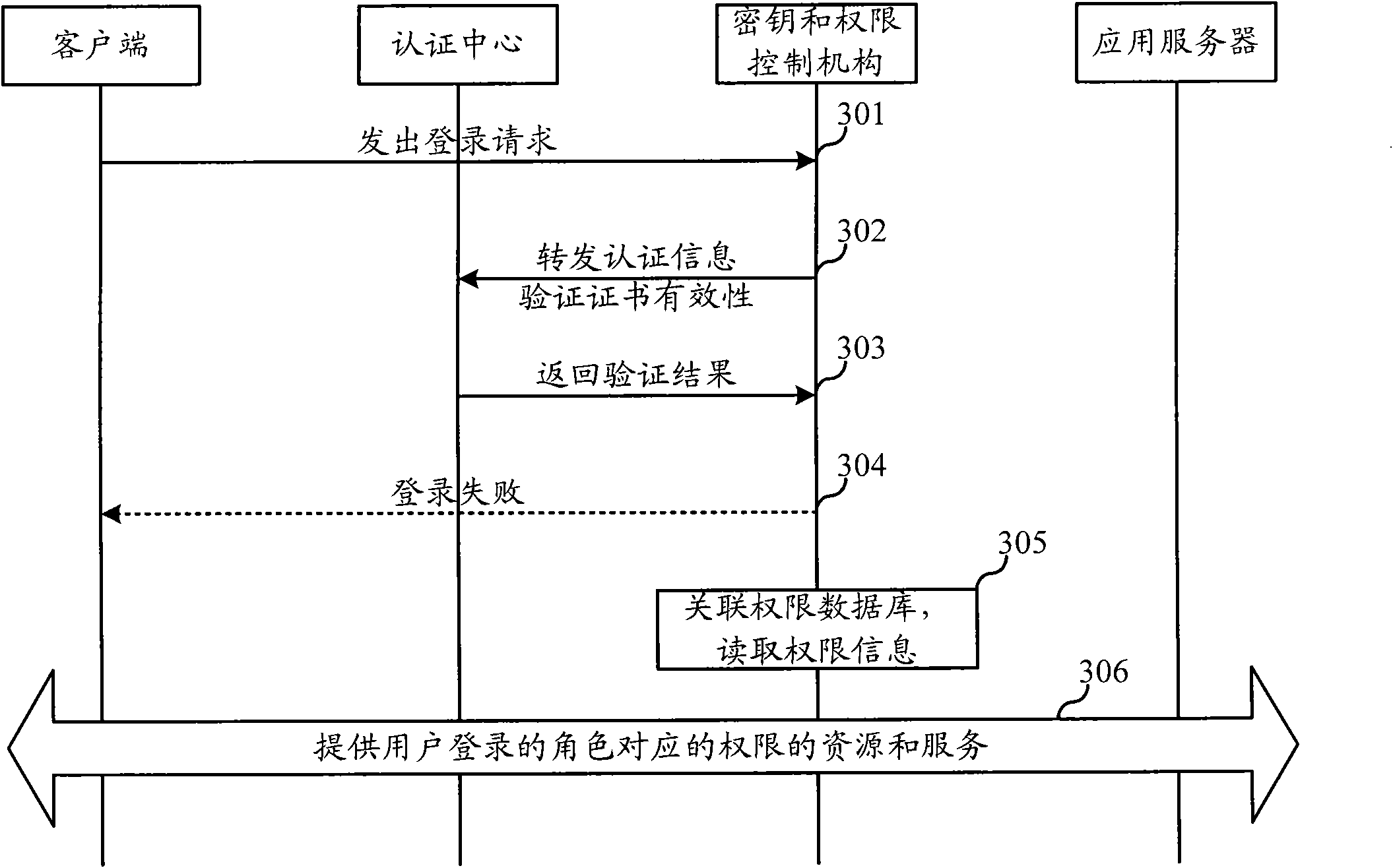
[0049] The first embodiment of the present invention relates to a fusion authentication method of identity and authority in an industrial control system. In this embodiment, CA and AA are fused together to form an authentication center, a key management institution (PKI) and a authority control institution (PMI) are fused together to form a key and authority control institution, and a An authority database, storing authority information corresponding to users with different roles.
[0050] In this embodiment, the user initiates a request to the administrator to apply for an identity certificate, and the administrator applies for the user's identity certificate through the client and sets corresponding permissions. The specific process o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com