Temporary authorization method for mobile communication equipment of authorizing party and authorized party and temporary authorization management method and device for manager
A mobile communication device, temporary authorization technology, applied in the direction of user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of rigid authorization content, long waiting time, user inconvenience, etc., to reduce temporary authorization time, reduce waiting time, the effect of reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
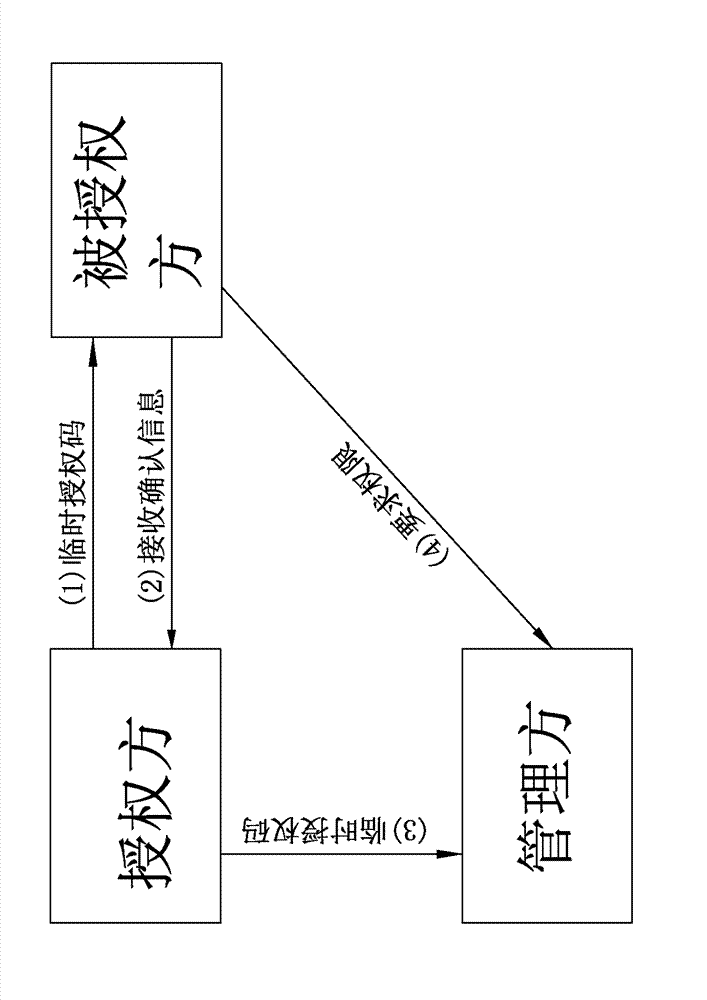
[0041] Such as figure 1 As shown, a specific embodiment of a temporary authorization method for a mobile communication device in the present invention includes:
[0042] Step A: The authorized party sends the authorization request information including the authorized party identification code to the authorizing party;
[0043] Step B: The authorizing party associates the temporary authorization information, the authorizing party identification code and the authorized party identification code, encrypts and generates a temporary authorization code, and then sends the temporary authorization code to the authorized party;
[0044] Step C: The authorized party verifies and decodes the temporary authorization code according to the pre-stored authorizing party identification code and authorized party identification code to obtain the temporary authorization information;
[0045] Step D: The authorizing party sends receipt confirmation information after successfully obtaining the te...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com