User anonymous identity authentication protocol based on k-pseudonym set in wireless network
A wireless network and identity authentication technology, applied in the field of user anonymous identity authentication protocol, can solve the problems of weak security and low performance, and achieve the effect of reducing resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
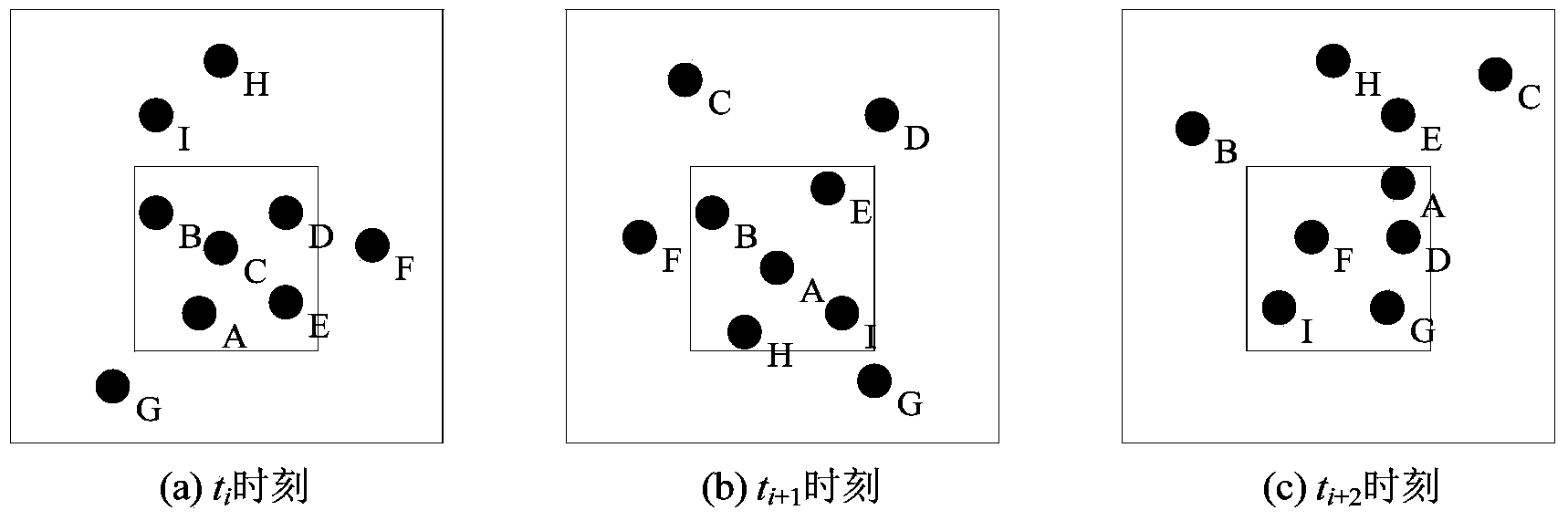
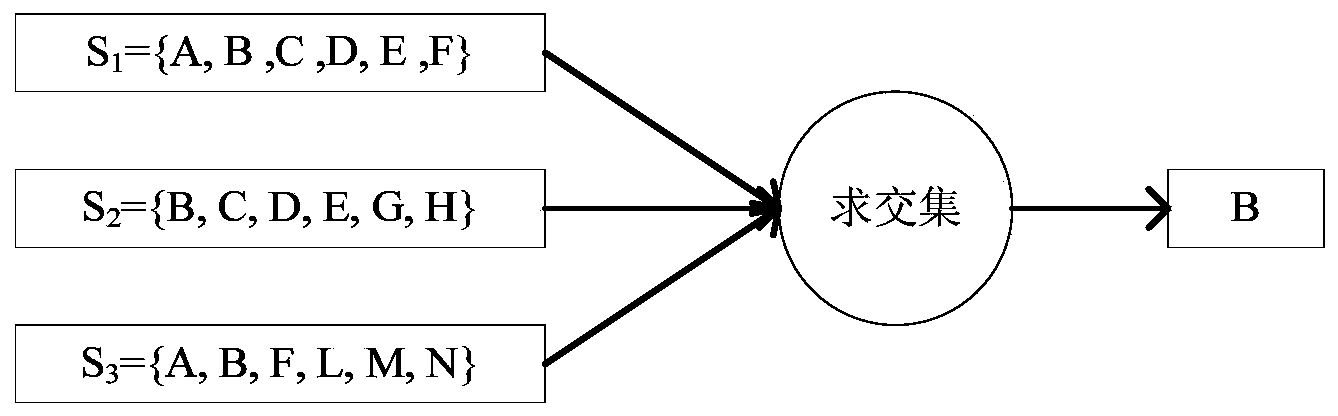
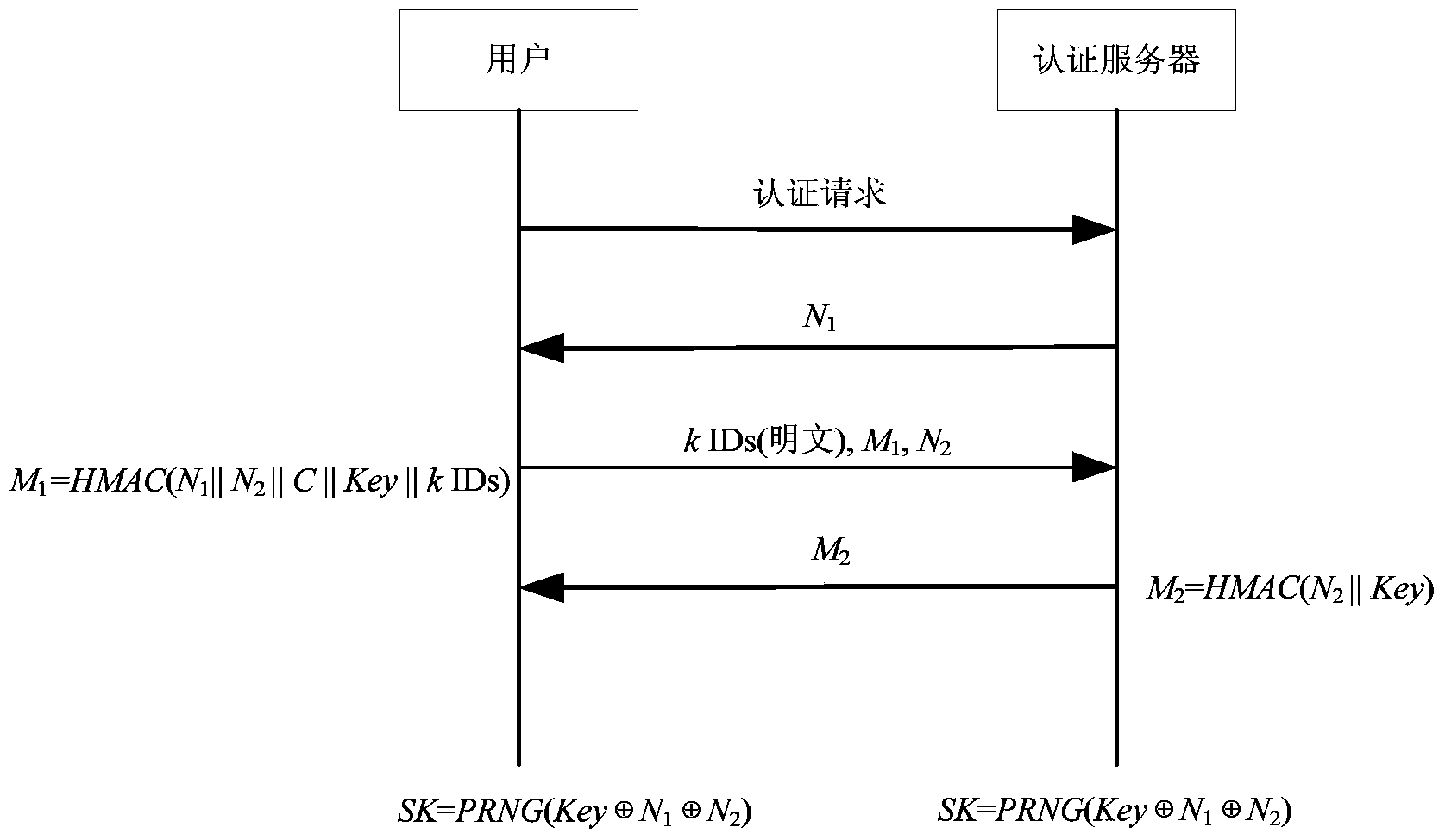
[0052] The present invention will be further described below in conjunction with the accompanying drawings. It should be noted that this embodiment is based on the technical solution and provides detailed implementation modes and implementation steps, but is not limited to this embodiment.
[0053] First, a description of the assumptions on which this agreement is based:
[0054] 1. Dolev-Yao model
[0055] The Dolev-Yao attacker model is widely used in the research and analysis of security protocols. Dolev and Yao studied the behavior of active attackers. Active attack means that the attacker first eavesdrops on the communication line to obtain information and then tries to crack the obtained information. The following assumptions are made about the behavior of the attacker in the model:
[0056] (1) The attacker can eavesdrop and intercept any message passing through the network;
[0057] (2) The attacker can store intercepted or self-constructed messages;
[0058] (3) Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com