NFC (near field communication)-based point-to-point trusted authentication method
An authentication method and point-to-point technology, applied in user identity/authority verification and key distribution, can solve the problems of limited functional diversity and weak security in the access process, and achieve the effect of immediacy and controllability of access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
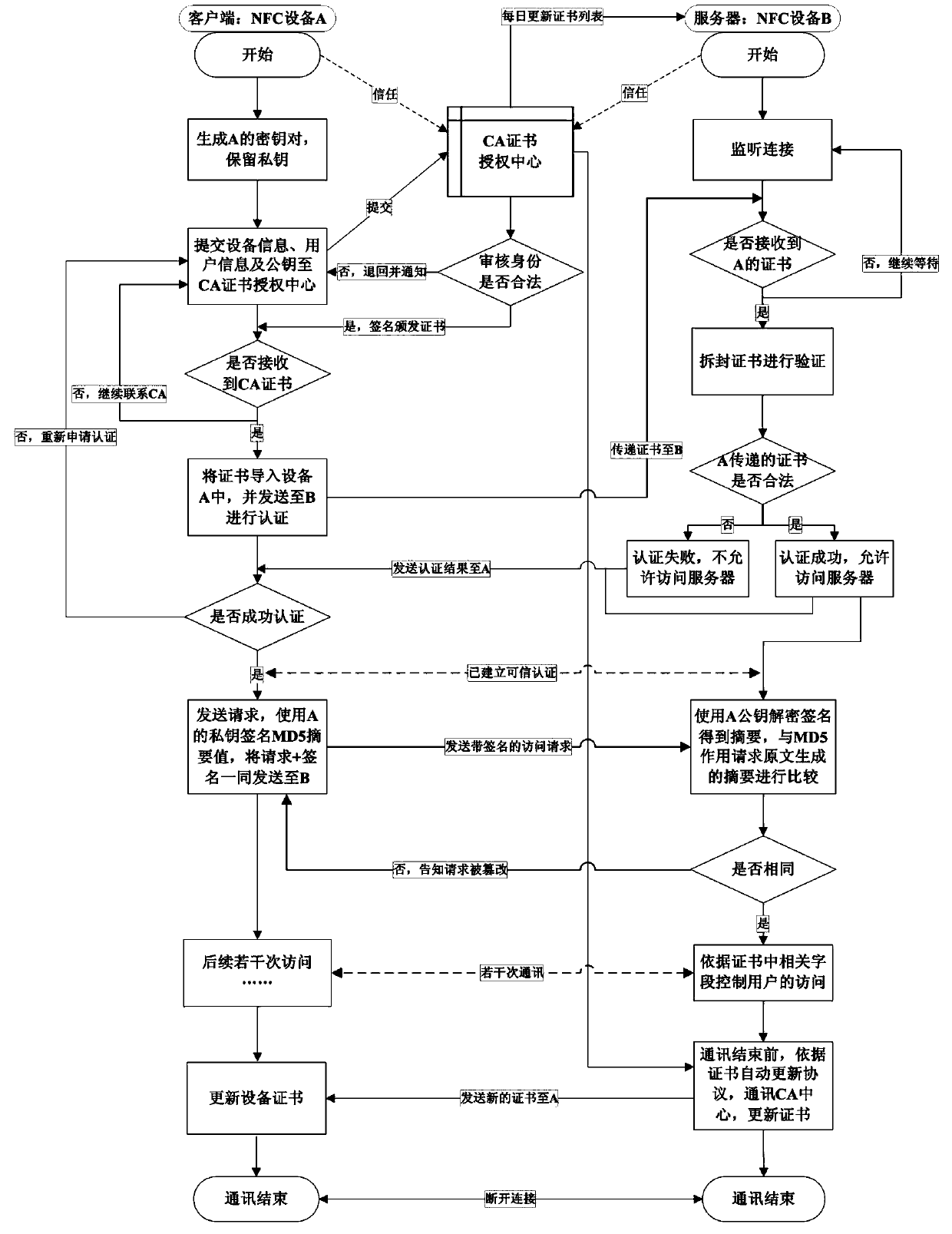
[0022] In order to make the purpose of the present invention, implementation scheme and advantages clearer, the specific implementation of the present invention will be described in further detail below, and the specific illustrations of the present invention can be found in figure 1 with figure 2 shown.
[0023] (1) When using two NFC devices to directly sense each other to authenticate the identity, because the authentication method only through the ID is too simple and the security cannot be guaranteed, a digital certificate issued by a trusted third-party authority CA is used instead of the ID for authentication. After the trusted authentication is established, access can be flexibly controlled by setting the relevant fields in the certificate to achieve multiple functional requirements. Down figure 1 It is a schematic diagram of the digital certificate structure issued by the CA center to the client device, listing the main parameters in the certificate.
[0024] (2) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com