Authentication method, device and system based on two-dimensional code
A technology of two-dimensional code and two-dimensional code information, which is applied in the field of communication, and can solve the problems of cumbersome authentication process and low efficiency of authentication method of wireless network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
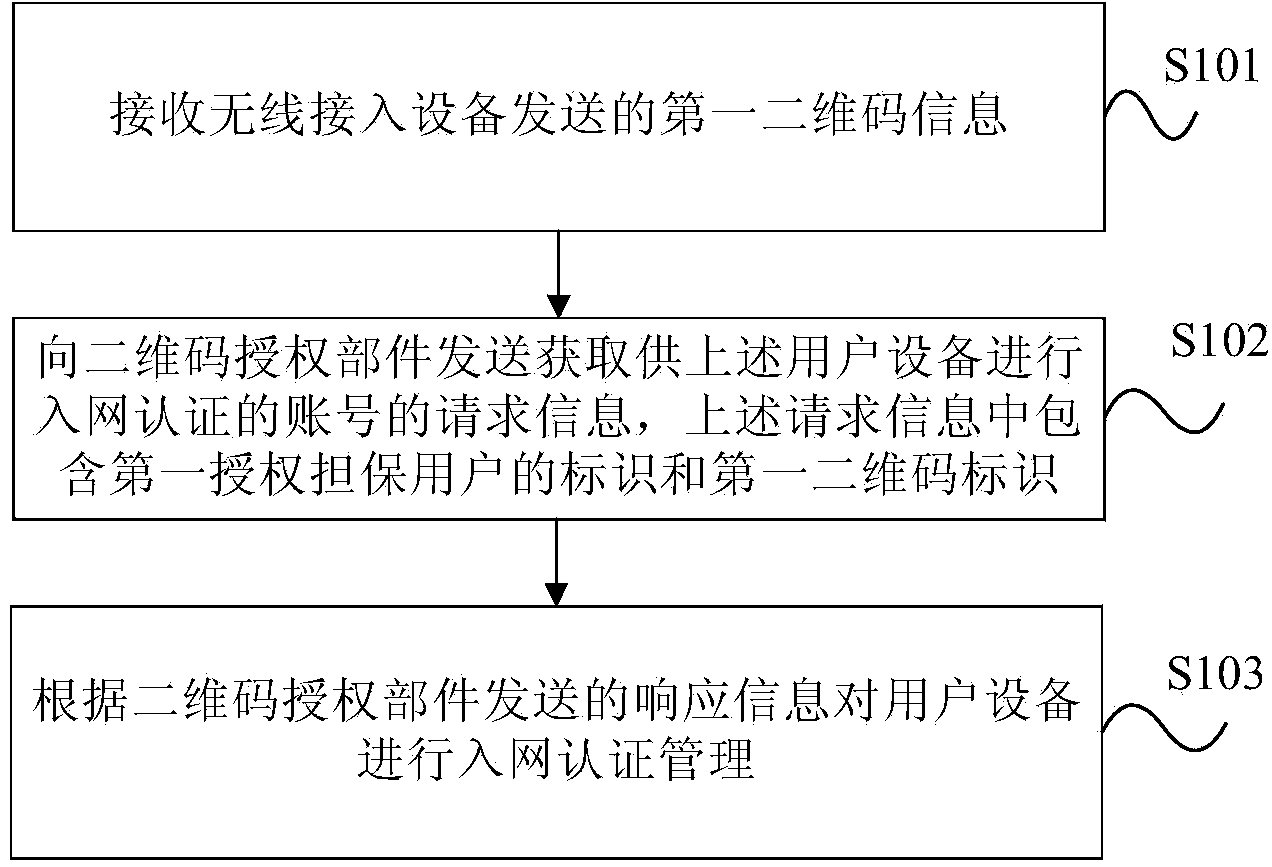
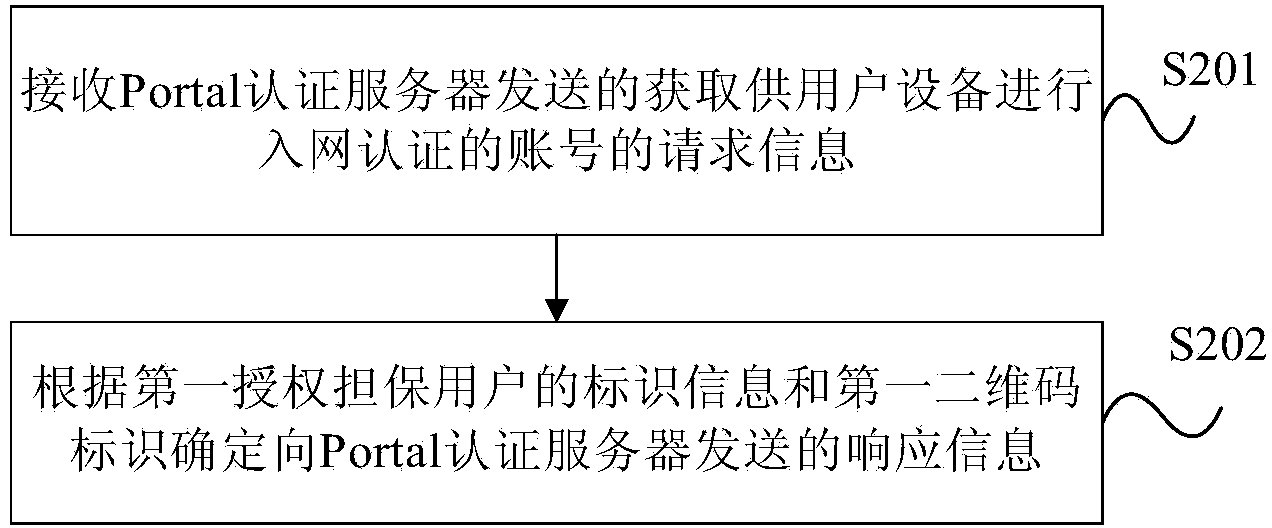
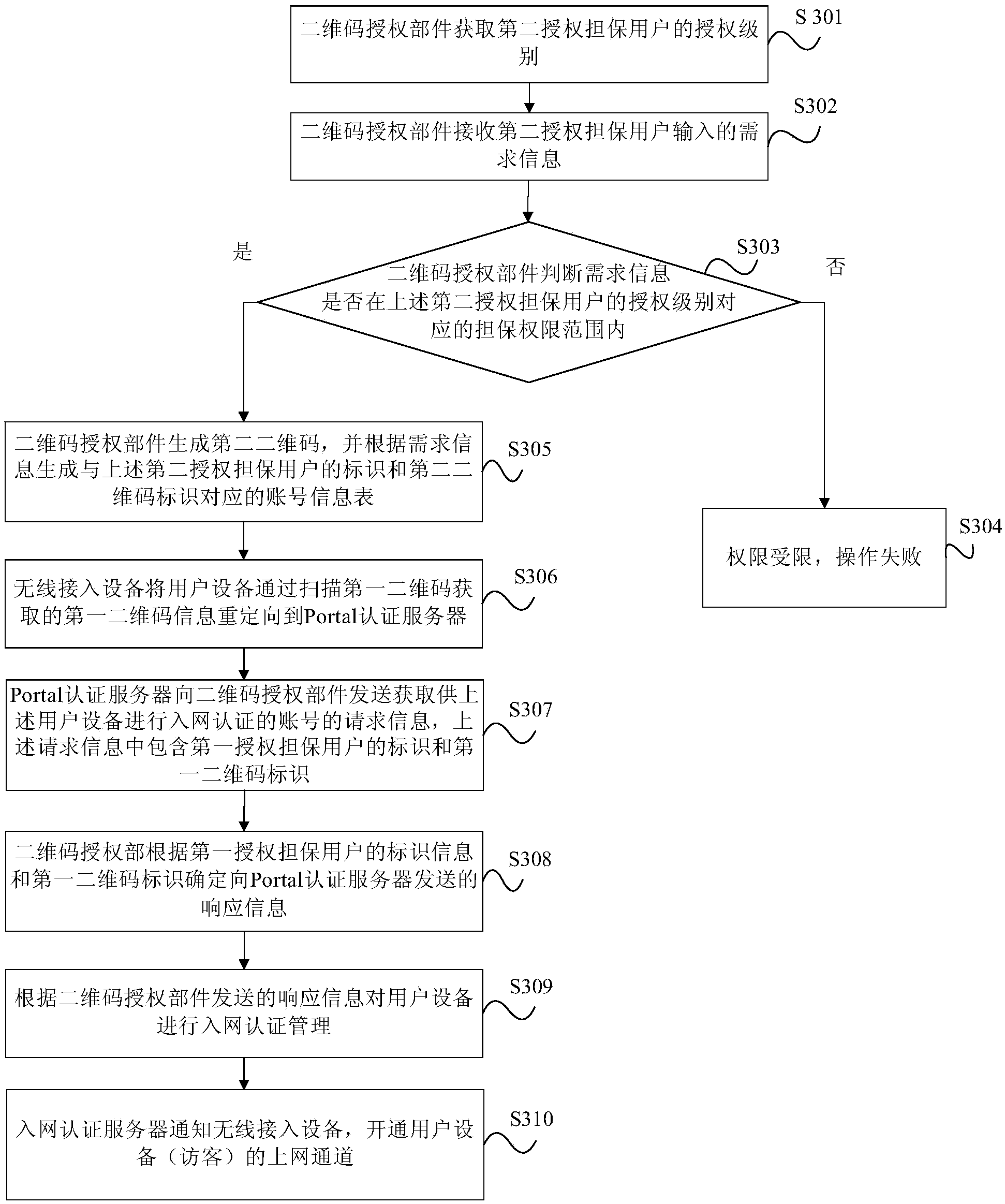
[0024] In order to improve the efficiency of the authentication of the use authority of the wireless network, the network management center grants legal users who can know the specific identity information to have a certain guarantee authority, and the user with a certain guarantee authority is called an authorized guarantee user. The authority of the legal identity of the number of visitors, that is, the visitor can obtain the authority to use the wireless network by using the identity of the authorized guarantee user guaranteed by the visitor. The present invention establishes a two-dimensional code and an account information table corresponding to the two-dimensional code according to the demand information of the authorized guarantee user. The two-dimensional code contains the identification of the authorized guarantee user and the two-dimensional code identification, and is scanned by the user equipment used by the visitor. The QR code obtains the identity information of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com