Access control method and apparatus, terminal and Internet of Things home system
An access control and terminal technology, applied in the field of communication, can solve problems such as the identity authentication of Internet of Things visitors, weak management of access control rights, hidden dangers of Internet of Things home system security, etc., to improve effectiveness, ensure security, and prevent replay The effect of the attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
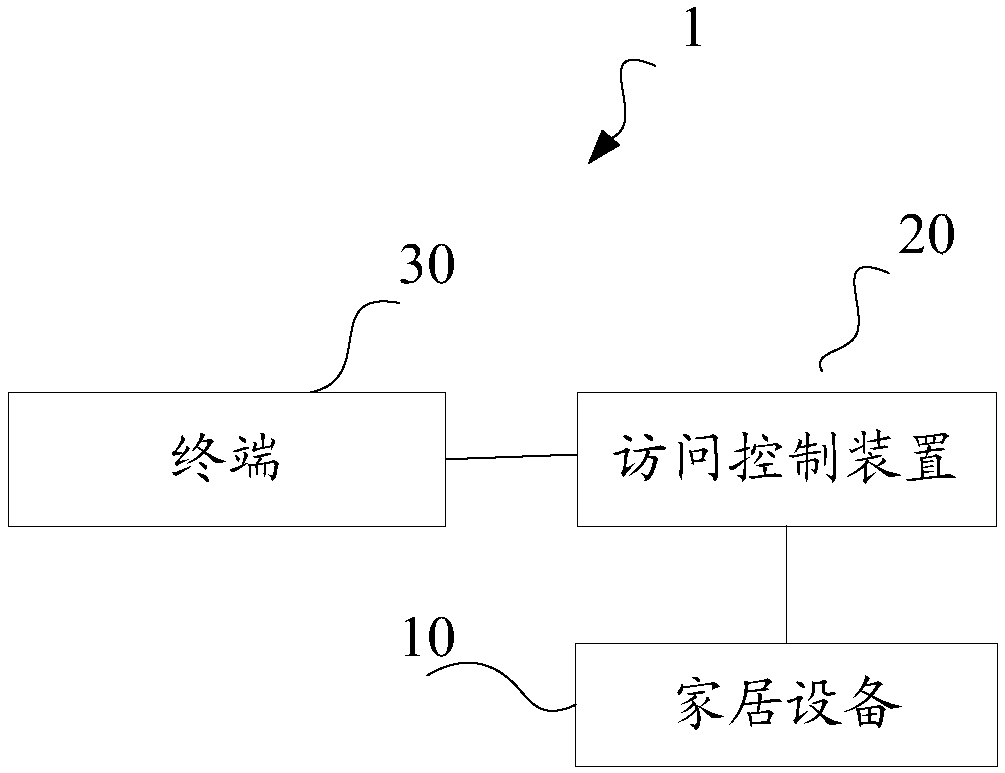
[0064] This embodiment provides an access control method for Internet of Things home devices. Before introducing the access control method, first combine figure 1 The IoT home system involved in this embodiment is introduced:
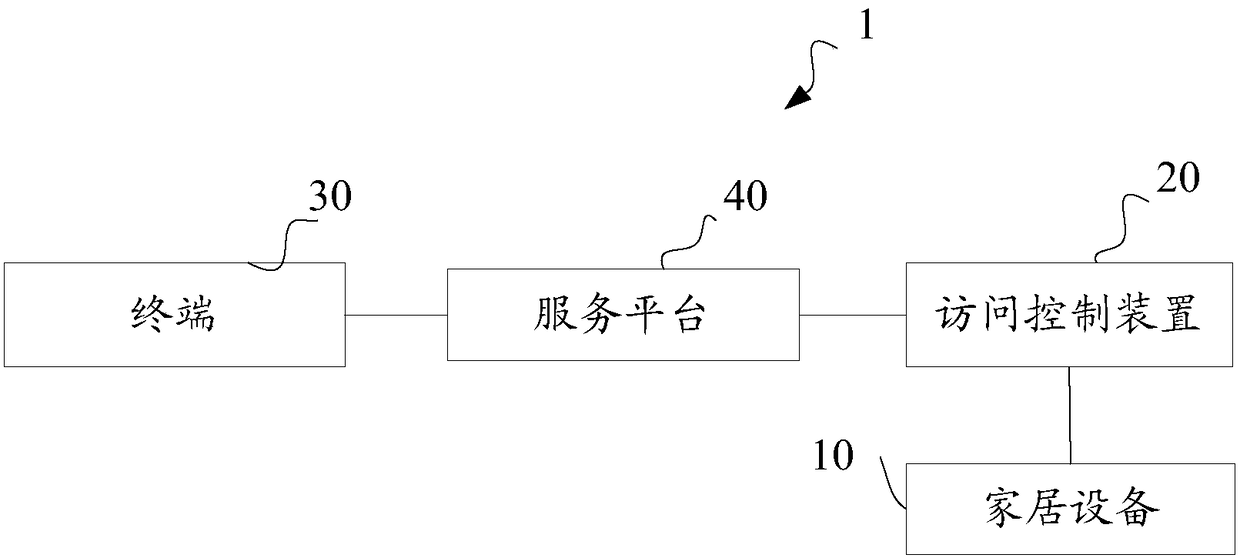
[0065] The IoT home system 1 includes a home device 10 , an access control device 20 and a terminal 30 , and the access control device 20 communicates with the home device 10 for authenticating and controlling a user's access request through the terminal 30 . The home device 10 is any smart home appliance used in a home environment, including but not limited to a monitoring probe, a smart refrigerator, a smart washing machine, a smart TV, a smart rice cooker, a smart air conditioner, and the like. The terminal 30 may be a user's mobile phone, smart phone, notebook computer, digital broadcast receiver, PDA (Personal Digital Assistant), PAD (Tablet Computer), PMP (Portable Multimedia Player), navigation device, etc., and mobile terminals such as Stationa...
Embodiment 2
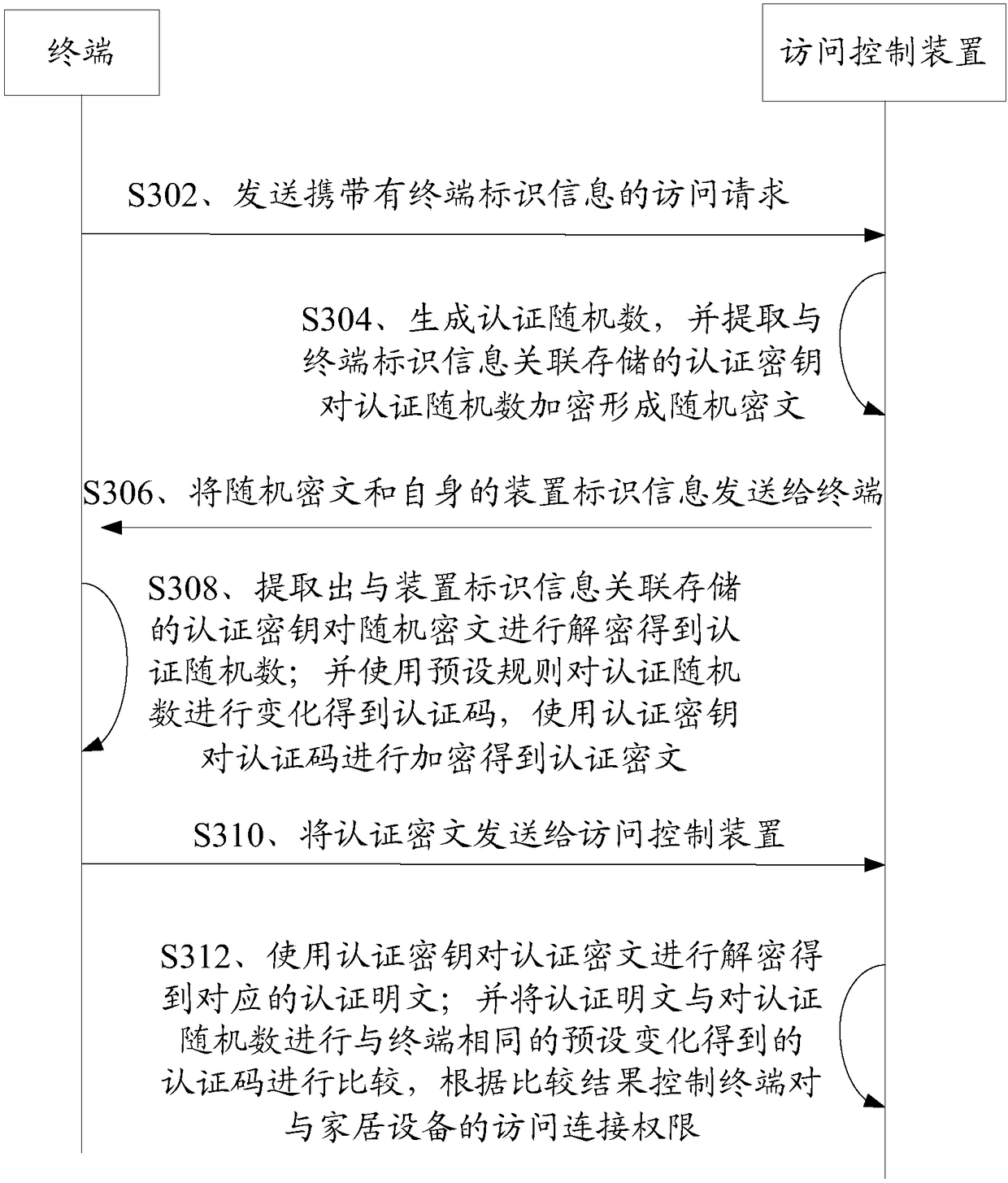
[0086] This embodiment will introduce the access control method provided in Embodiment 1 in detail with reference to the accompanying drawings and specific examples:
[0087] In this embodiment, the authentication key used by the access control device and the terminal in the authentication process is set by the access control device. Figure 4 The process of determining the authentication key between the access control device and the terminal is introduced:
[0088] S402. The terminal sends its own terminal identification information to the access control device.
[0089] As described in Embodiment 1, the terminal identification information sent by the terminal to the access control device may be at least one of its own MAC address, hardware serial number and other information.
[0090] S404. The access control device generates a key random number, and generates an authentication key corresponding to the terminal according to the key random number and the terminal identificat...
Embodiment 3
[0131] This embodiment provides an access control device. As a member of the Internet of Things home system, the access control device can cooperate with the terminal to execute the access control methods in Embodiment 1 and Embodiment 2. Please refer to Figure 7 A schematic structural diagram of an access control device shown:
[0132] The access control device 20 includes a request receiving module 202 , a ciphertext generating module 204 , a random ciphertext sending module 206 , an authentication ciphertext receiving module 208 and an authentication processing module 210 .
[0133] The request receiving module 202 is configured to receive an access request sent by a terminal, and the received access request carries terminal identification information. After the request receiving module 202 receives the access request sent by the terminal, the ciphertext generating module 204 may randomly generate an authentication random number. Then use the authentication key to encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com