Token based two factor authentication and virtual private networking system for network management and security and online third party multiple network management method
a network management and security technology, applied in the field of user authentication system for network security and management, can solve the problems of increasing the burden on consumers and suppliers of goods or services, the inherently problematic nature of online identity, and the difficulty of establishing and protecting identity, etc., and achieve the effect of efficient and effectiv
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
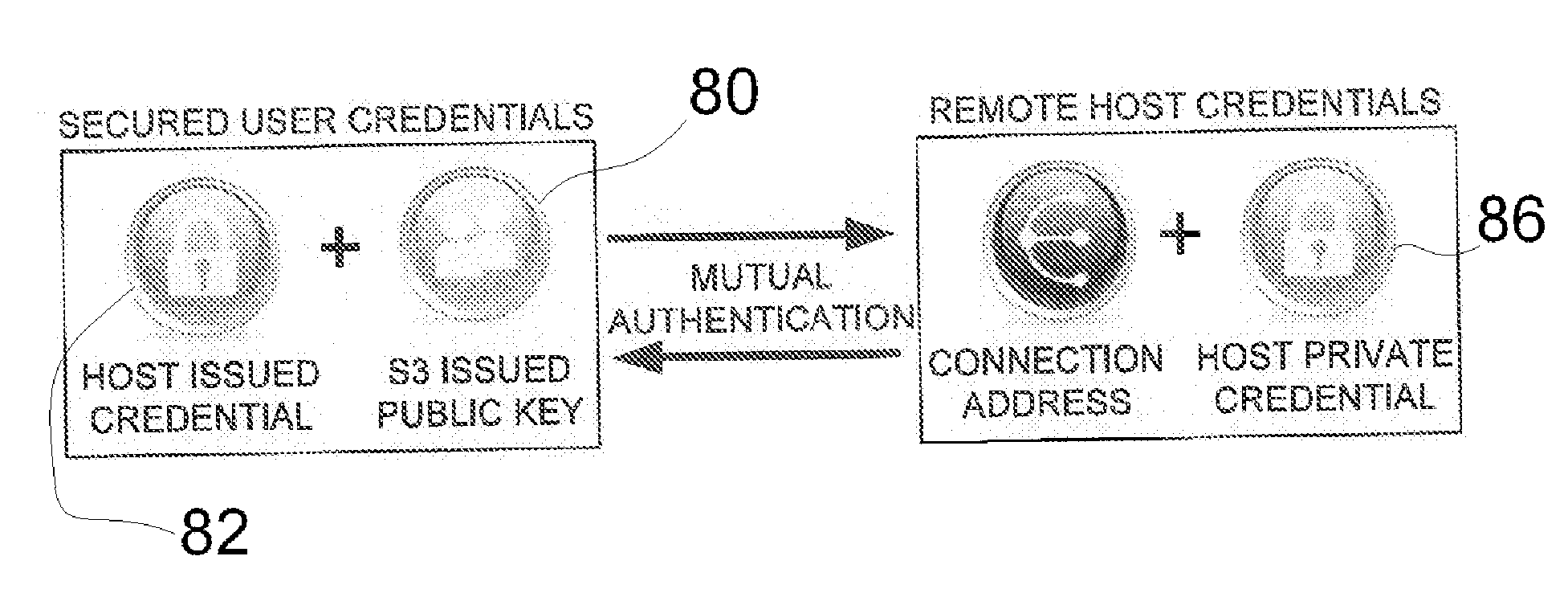
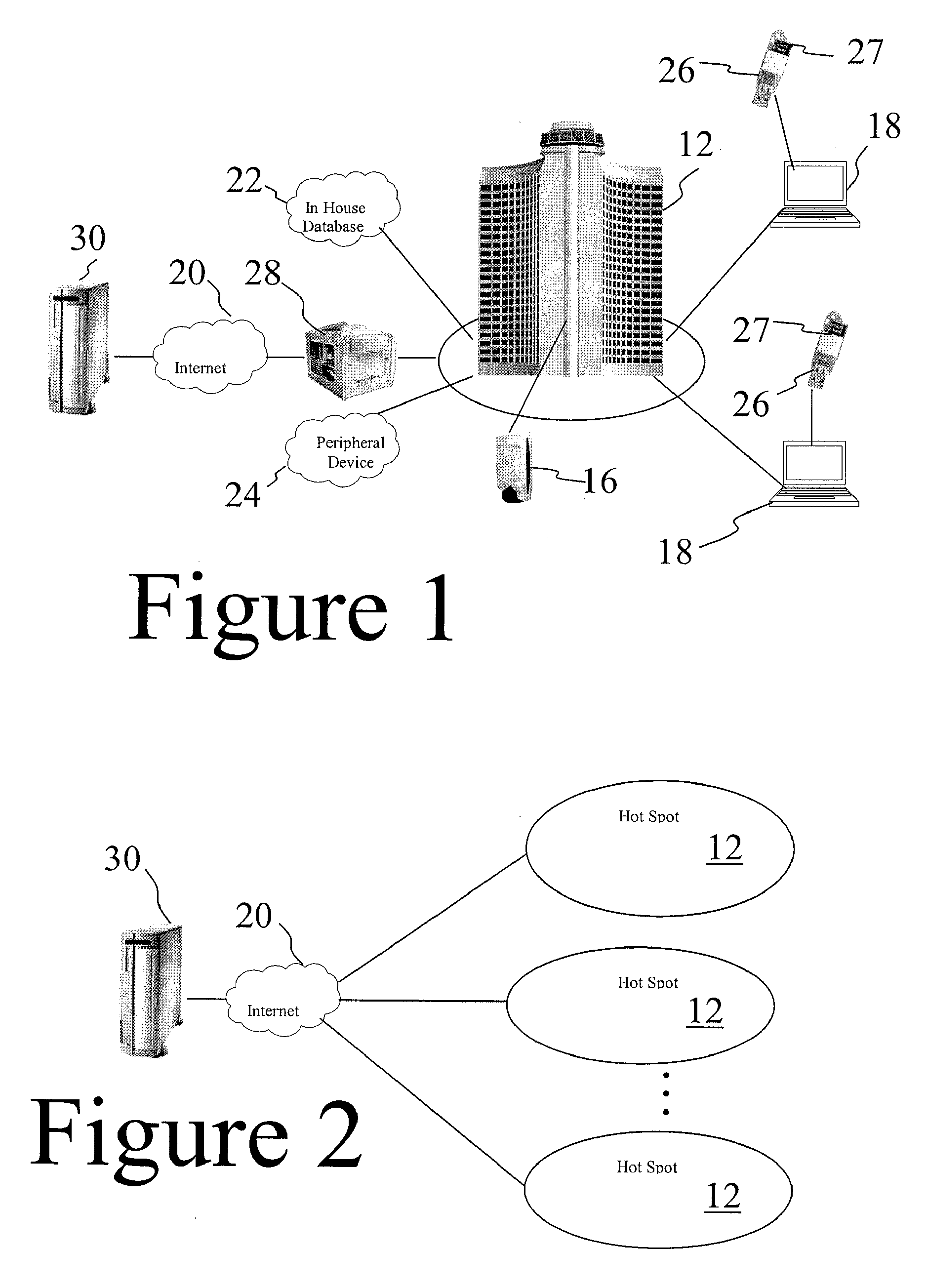
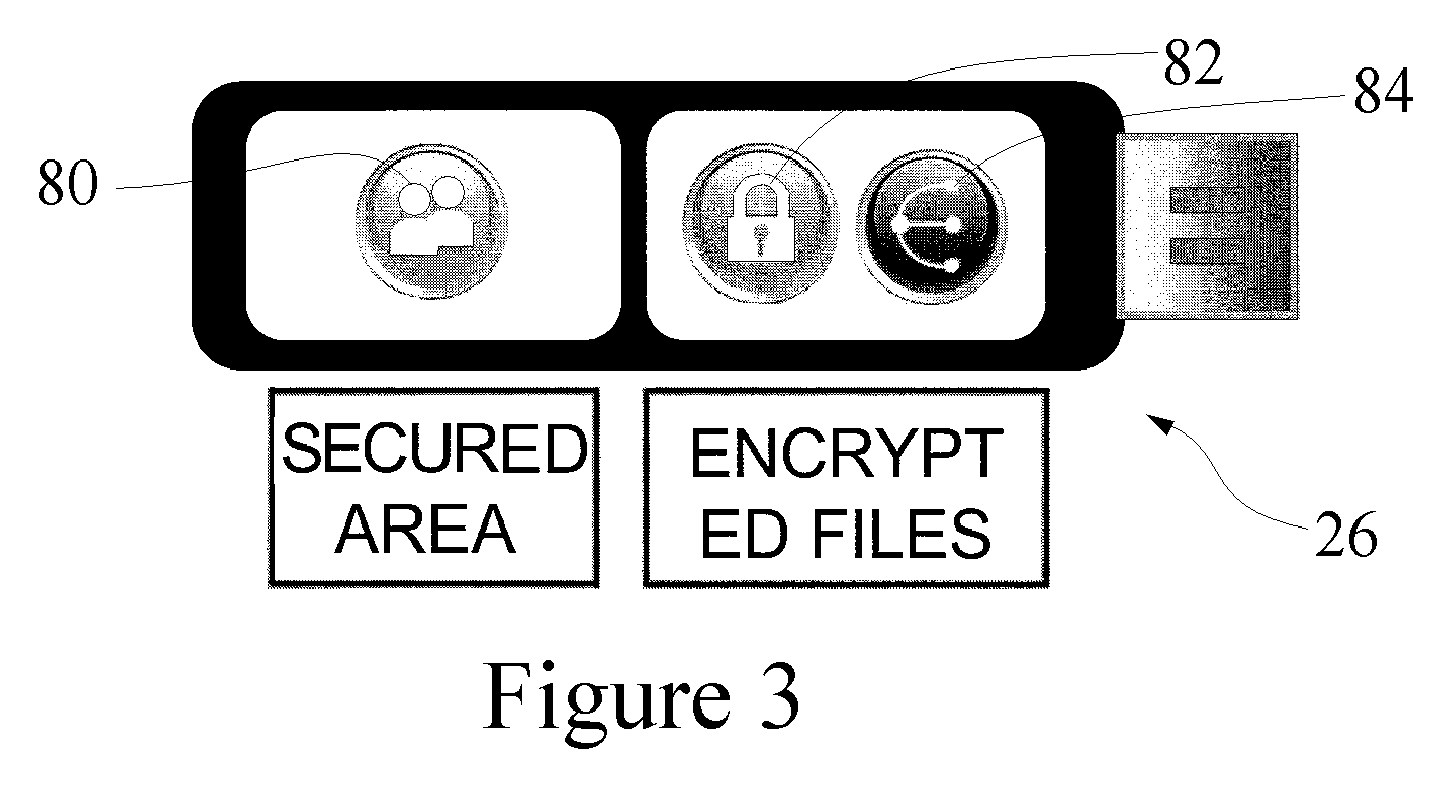
[0030] The present invention was developed and is based on the principle of simple security. The present invention provides products that effectively address the barriers and risks of adopting strong authentication and provide relief from the burden of identity for both users and providers. As described below the present invention provides a token-based two-factor authentication and virtual private networking (VPN) approach that simultaneously increases security and increases simplicity. The present invention is useful for management of effectively any network, and as described further below, a single user key may be implemented as a authenticating token for separate networks associated with the user. One non-limiting example of the invention is associated with authentication and network management of Wi-Fi networks 10, such as shown in FIGS. 1-2. This description is helpful for explaining the present invention, but the invention is not intended to be limited to Wi-Fi networks and i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com