SSH protocol behavior pattern recognition and alarm method based on total traffic of bypass network
A pattern recognition, full flow technology, applied in the field of network security, can solve problems such as cumbersome operations, and achieve the effect of improving work efficiency, improving accuracy, and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described in detail below in conjunction with the reaction scheme and specific examples.
[0029] A method for identifying and alerting SSH protocol behavior patterns based on bypass network full traffic, specifically comprising:
[0030] (1) The bypass monitoring device captures the mirrored traffic of the switch, separates the TCP traffic from it, and then filters out the traffic data of the SSH protocol according to the destination port.
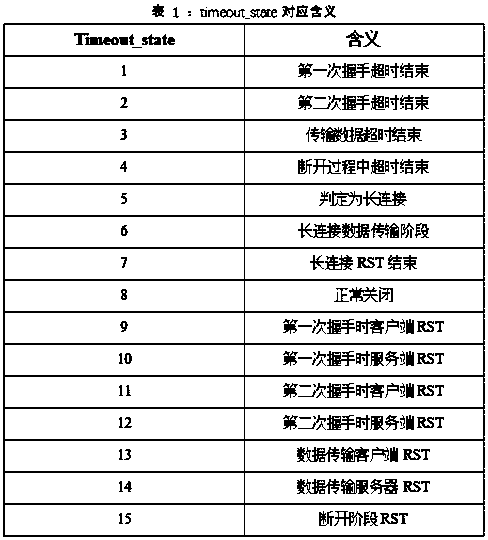
[0031] (2) Clean the traffic data of the SSH protocol, and extract the five-tuple information (sip, dip, inpackets, outpackets, timeout_state) from each piece of data.
[0032] (3) Judging the five-tuple information, analyzing and confirming whether it belongs to the scanning process, brute force cracking process or successful login process. The specific judgment process is as follows:
[0033] If the data of "inpackets >=30 AND outpackets >=30" exists in the traffic data of the SSH protocol, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com