Working key generation method and device and computer readable storage medium
A work key and key technology, applied in the field of information security, can solve the problems of terminal equipment user loss, reduce the security of terminal equipment, etc., and achieve the effect of a wide range of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
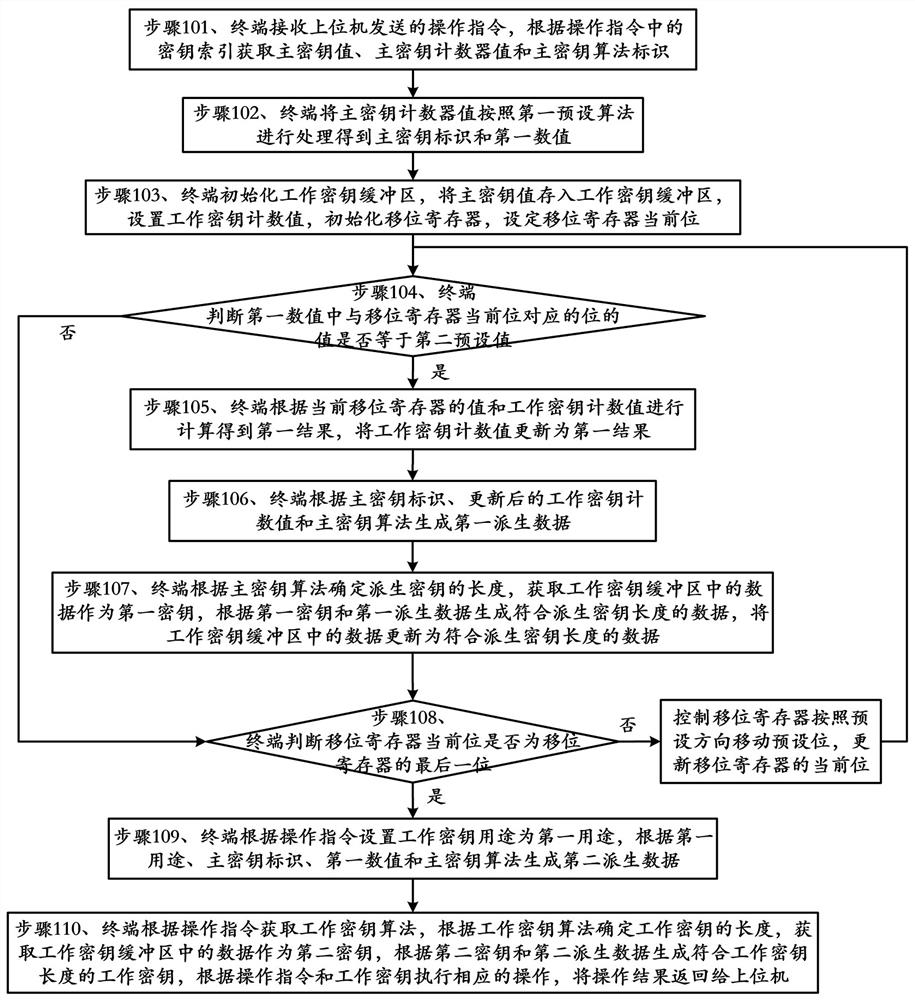
[0037] Embodiment 1 of the present application provides a method for generating a work key, such as figure 1 As shown, the method includes:
[0038] Step 101, the terminal receives the operation command sent by the host computer, and obtains the master key value, the master key counter value and the master key algorithm identifier according to the key index in the operation command;
[0039] In this embodiment, the operation instructions specifically include: data encryption instructions, data decryption instructions, PIN code encryption instructions, Mac check value generation instructions or verification instructions, etc.;
[0040] In this embodiment, obtaining the master key value, the master key counter value, and the master key algorithm identifier according to the key index in the operation instruction specifically includes: obtaining the master key according to the key index in the operation instruction; key to obtain the master key value, master key counter value, an...
Embodiment 2
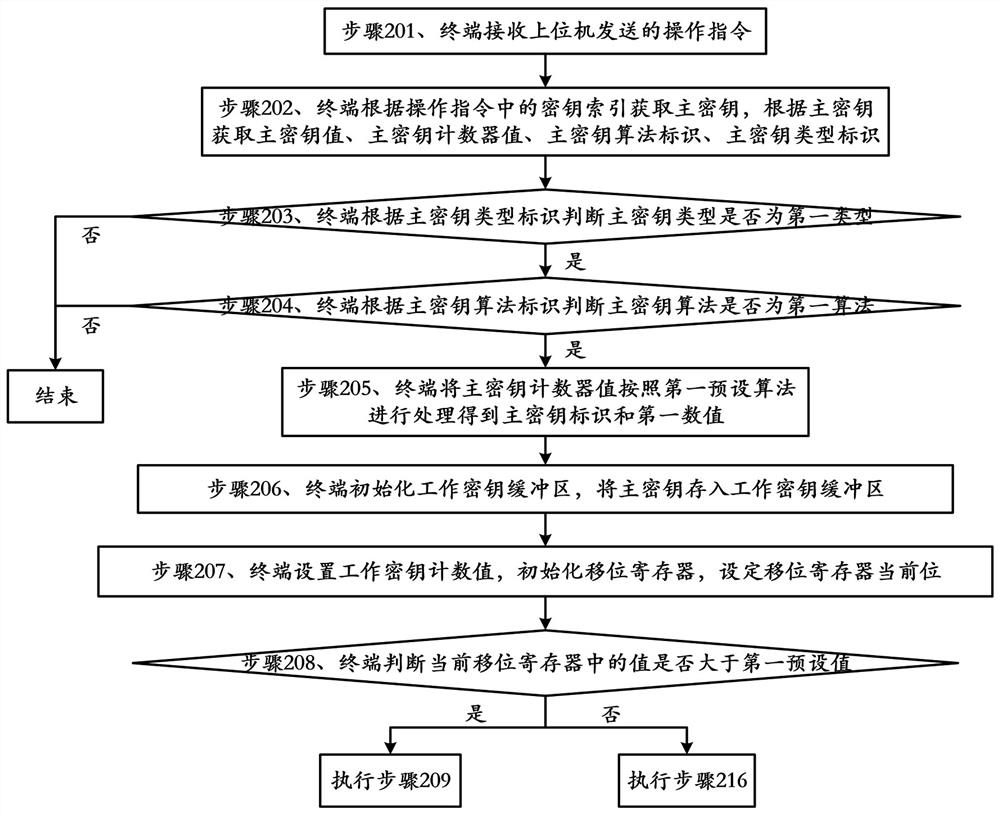
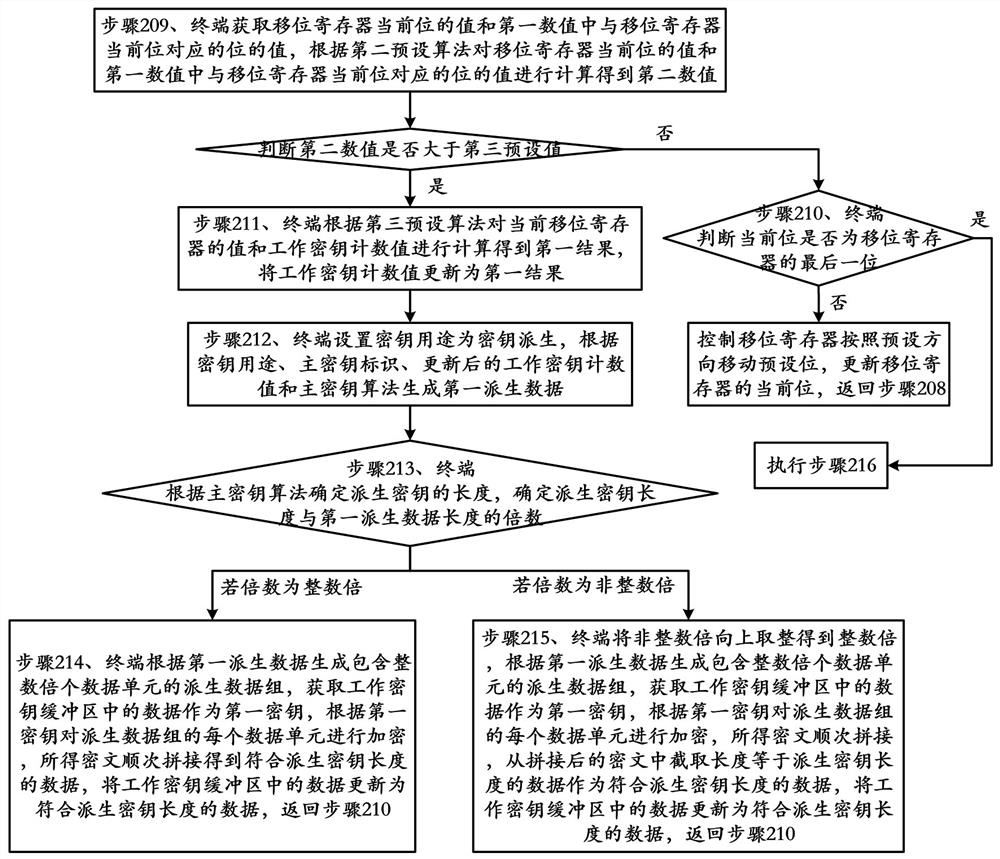
[0124] Embodiment 2 of the present application provides a method for generating a work key, such as figure 2 , image 3 , Figure 4 As shown, the method includes:
[0125] Step 201, the terminal receives the operation instruction sent by the host computer;
[0126] In this embodiment, the operation instruction specifically includes: a data encryption instruction, a data decryption instruction, a Mac check value generation instruction or a verification instruction, and the like.
[0127] Step 202, the terminal obtains the master key according to the key index in the operation instruction, and obtains the master key value, the master key counter value, the master key algorithm identifier, and the master key type identifier according to the master key;
[0128] In this embodiment, the terminal obtains the master key according to the key index in the operation instruction specifically: the terminal obtains the key index in the operation instruction, searches for the data corre...
Embodiment 3
[0241] Based on the above-mentioned technical solution of a work key generation method provided by this application, this application provides a corresponding structural diagram of a work key generation device, as shown in Figure 5 As shown, a work key generation device 300 of the present application may include:
[0242] The receiving module 301 is used to receive the operation instruction sent by the host computer;
[0243] An acquisition module 302, configured to acquire the master key value, the master key counter value and the master key algorithm according to the key index in the operation instruction;
[0244] A processing module 303, configured to process the master key counter value according to a first preset algorithm to obtain the master key identifier and the first value;
[0245] The setting module 304 is used to initialize the working key buffer, store the master key value into the working key buffer, set the counting value of the working key, initialize the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com