A security cloud audit method and system with updatable verification label
A label, security technology, applied in the field of cloud computing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
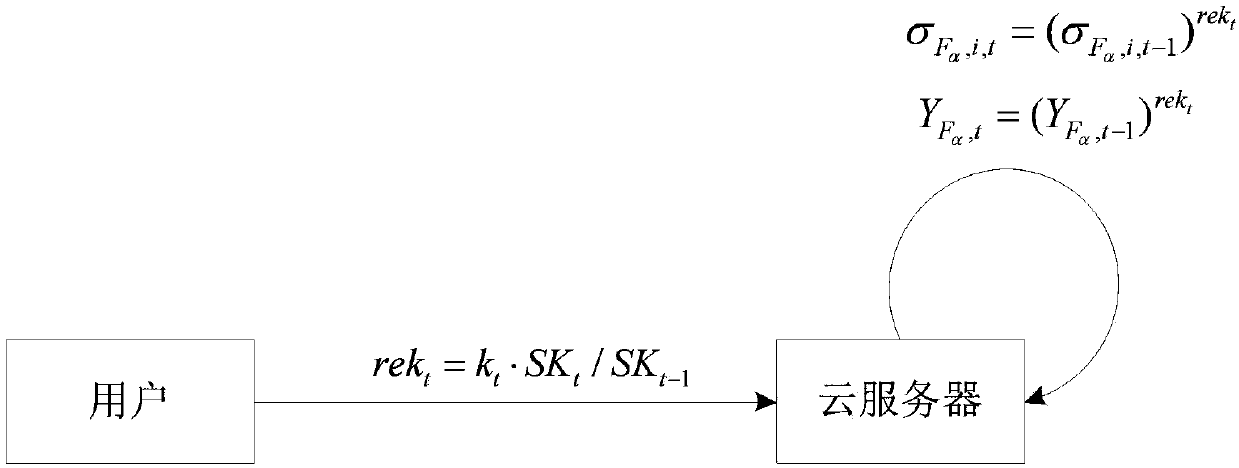
[0071] In this embodiment, a security cloud auditing method whose verification label can be updated is applied in a cloud storage environment composed of a user, a third-party audit organization TPA, and a cloud server. The security cloud auditing method is performed in the following steps:
[0072] Step 1. Initialization:
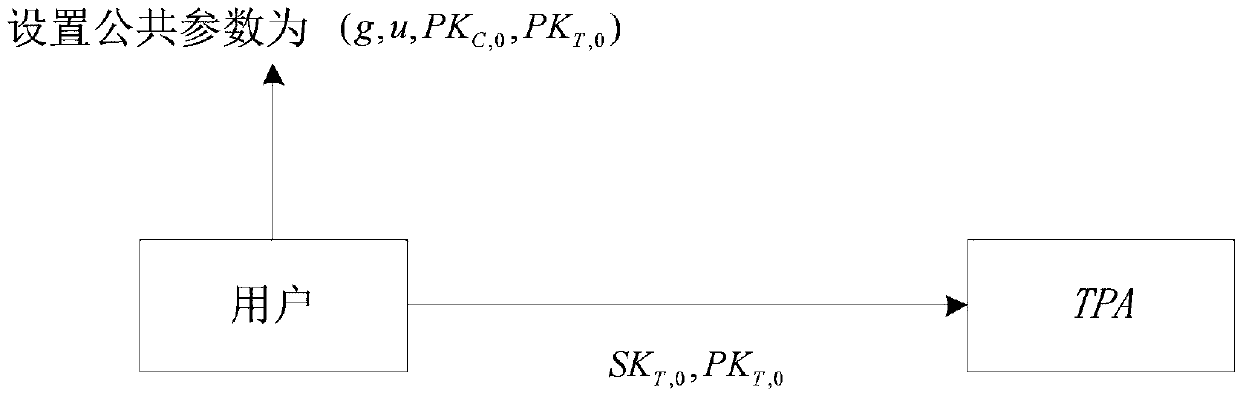
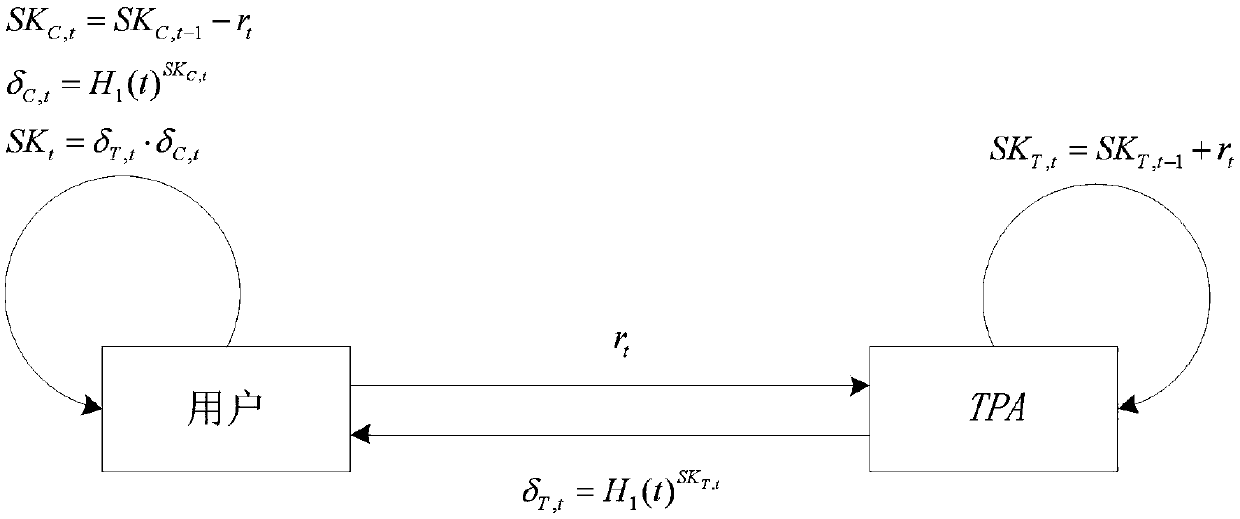
[0073] Step 1.1, such as figure 1 As shown, the user generates two multiplicative cyclic groups G whose order is a prime number q 1 and G 2 , two collision-resistant hash functions H 1 :{0,1} * →G 1 and H 2 :G 2 →G 1 , a computable bilinear pairing Group G 1 The two generators g and u and the user's initial public-private key pair (SK C,0 , PK C,0 ) and the initial public-private key pair (SK T,0 , PK T,0 ),in As the public key of the user and the third-party audit agency TPA respectively, and the initial public-private key pair (SK T,0 , PK T,0 ) to the third-party auditor TPA;
[0074] Step 1.2, the user sets the public parameters as (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com