Generation method of a new keyed message integrity authentication code
A technology of message integrity and message authentication code, which is applied in the field of generation of new key-containing message integrity authentication code, can solve problems such as insecure message authentication code technology, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
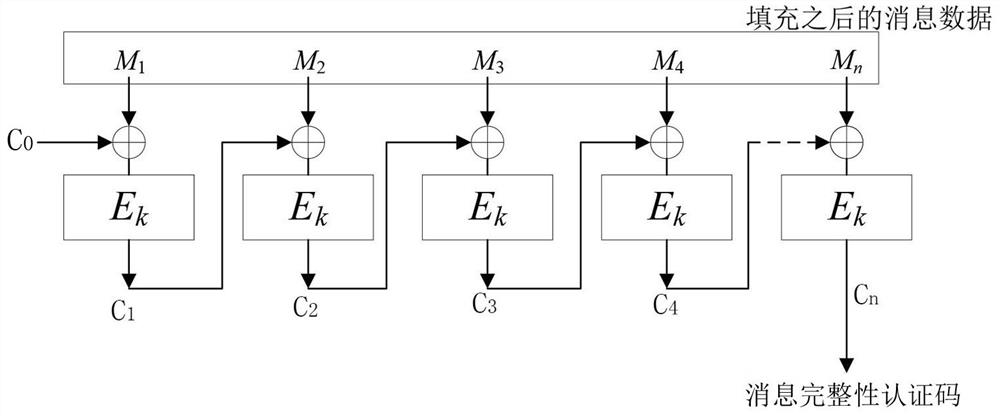
[0044] Embodiment one, see figure 2 , the present embodiment provides a method for generating a novel keyed message integrity authentication code, comprising the following steps:
[0045] Step S101, select two block cipher encryption transformations E with a block size of B bits 1 ,E 2 ;
[0046] Step S102, inject key k1 into E 1 , get the block cipher algorithm E 1,k1 ;
[0047] Step S103, inject key k2 into E 2 , get the block cipher algorithm E 2,k2 ;
[0048] To fill the message to be processed, follow steps S104 to S107 as follows.
[0049] Step S104, set the length of the original message as len, and calculate the value t of len mod B, that is, the remainder after dividing len by B is t;
[0050] Step S105, when the t value is less than 64, first add 1 after the original message, then add B+t-64 0s, and then add the 64-bit representation of the bit length value len of the original message, if len is less than 64 bits Add 0 in its high position;
[0051] Step ...
Embodiment 2
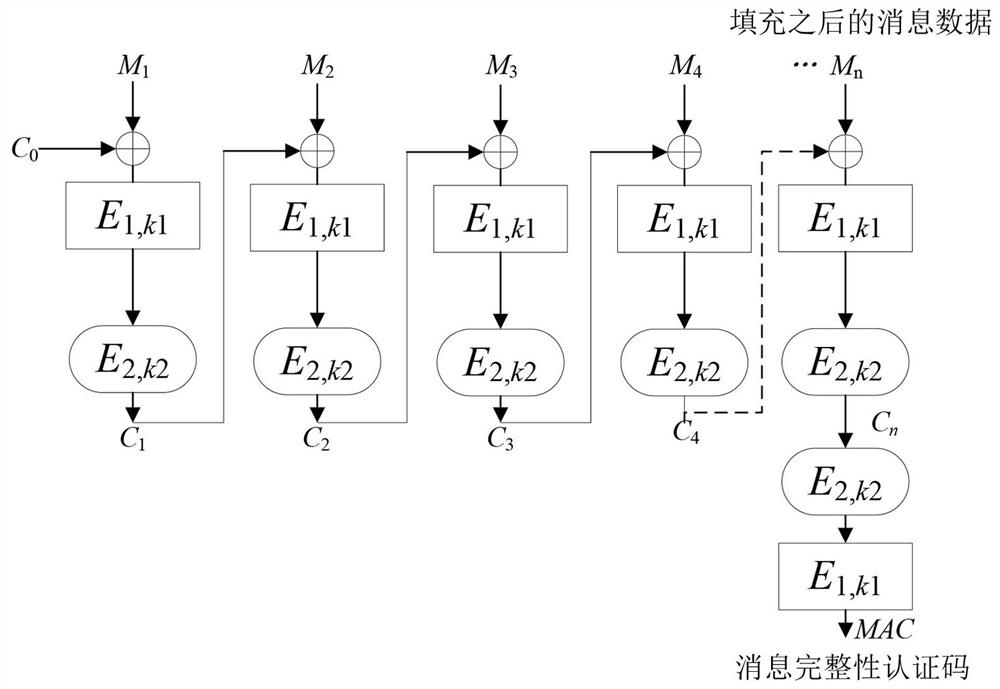
[0067] Embodiment 2, Advanced Encryption Standard AES and China's Block Cipher Algorithm Encryption Standard SM4 are two well-known block cipher algorithms. A method for generating a new key-containing message integrity authentication code of the present invention is constructed.
[0068] Step S201, generating two sets of 128-bit keys, namely k1 and k2;
[0069] Step S202, selecting two encryption algorithms as AES and SM4 encryption algorithms respectively, denoted as AES and SM4;
[0070] Step S203, injecting k1 and k2 into the encryption functions of AES and SM4 respectively to obtain the encryption algorithm AES k1 ,SM4 k2 ;
[0071] To fill the message to be processed, follow steps S204 to S207 as follows.
[0072] Step S204, set the original message length as len, and calculate the value t of len mod128, that is, the remainder after dividing len by 128 is t;
[0073] Step S205, when the t value is less than 64, first add 1 after the original message, then add 64+t 0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com