Data encryption method and system, client and computer readable storage medium
A data encryption and encrypted technology, applied in the field of data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
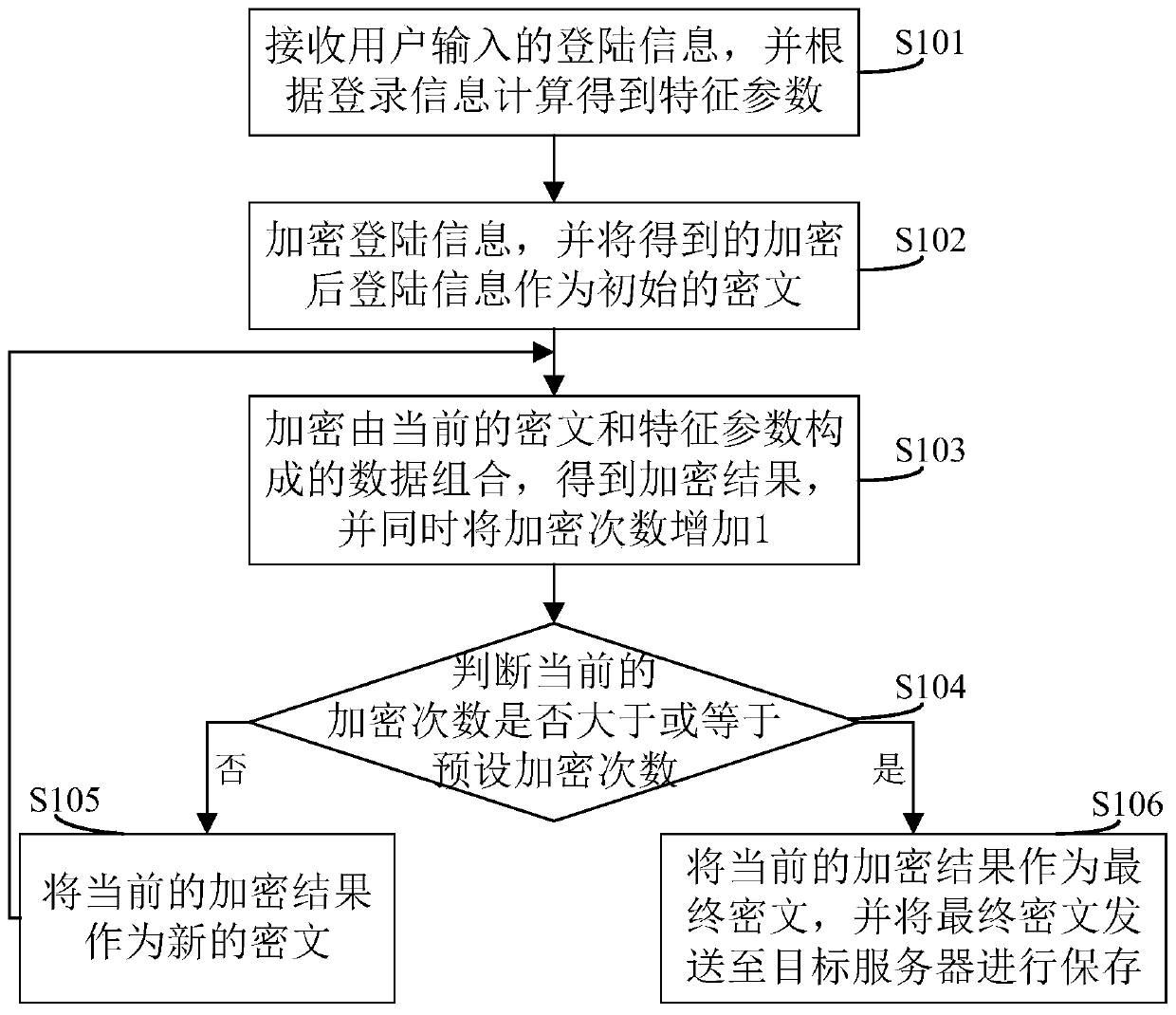
[0054] See figure 1 , figure 1 It is a flow chart of a data encryption method provided by the embodiment of this application. It should be noted that the solution provided by this embodiment is mainly applied in the Client / Server mode. The user uses the client to enter his login information to try to log in to the target server or In the scenario of the personal account provided by the target server, in order not to transmit the plaintext login information in the network and save it in the server, the server verifies whether the login is legal based on the received ciphertext, so the user input The process of encrypting plaintext login information into ciphertext is completed by the client (Client), so the execution subject of this embodiment is the client, which includes the following steps:
[0055] S101: Receive login information input by the user, and calculate characteristic parameters according to the login information;
[0056] This step is aimed at the client receivi...
Embodiment 2
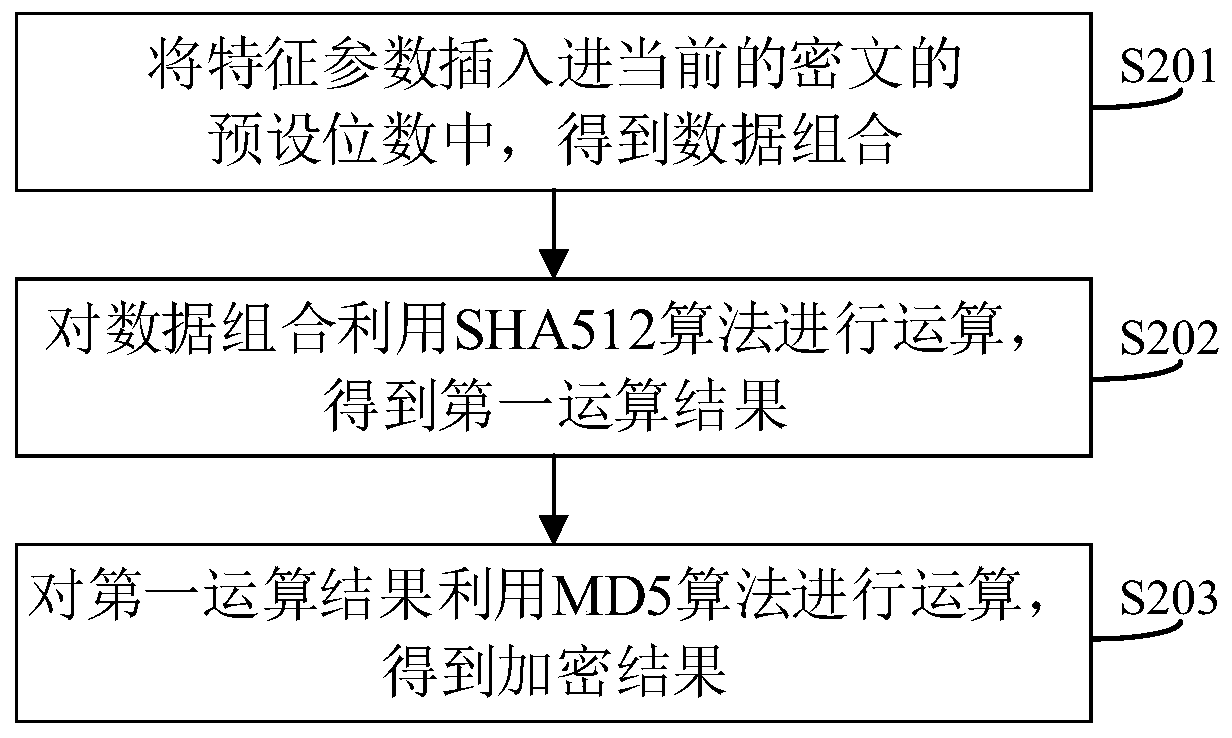
[0075] See figure 2 , figure 2 A flow chart of a method for forming a data combination and an encryption method for a data combination in the data encryption method provided by the embodiment of this application. On the basis of the first embodiment, this embodiment provides a method for how to form a data combination in S103. The specific implementation method includes the following steps:
[0076] S201: inserting characteristic parameters into the preset number of digits of the current ciphertext to obtain a data combination;
[0077] In this step, the data combination is obtained by inserting the feature parameter (equivalent to Y in the above example) into the preset number of digits of the current ciphertext.
[0078] S202: Perform operations on the data combination using the SHA512 algorithm to obtain a first operation result;
[0079] S203: Perform an operation on the first operation result using the MD5 algorithm to obtain an encrypted result.
[0080] S202 On th...
Embodiment 3
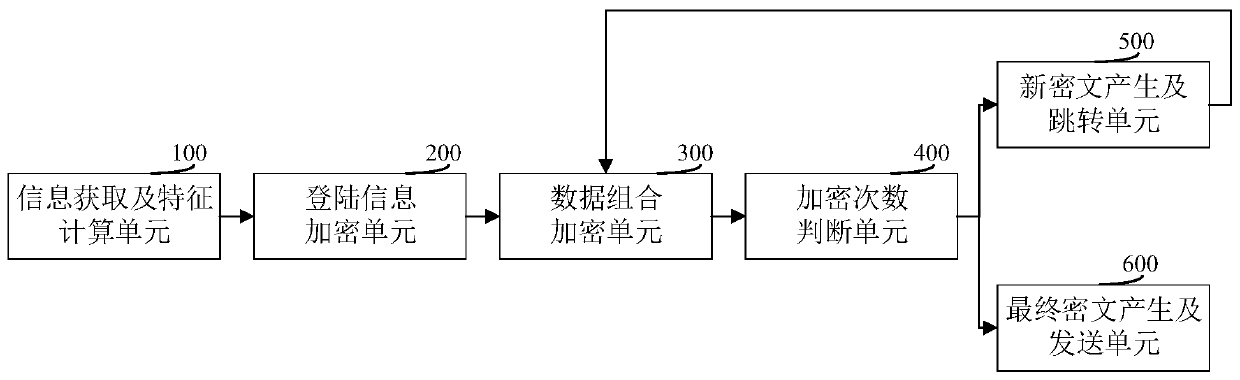
[0085] See image 3 , image 3 A structural block diagram of a data encryption system provided in the embodiment of this application, the data encryption system may include:
[0086] The information acquisition and feature calculation unit 100 is configured to receive login information input by the user, and calculate feature parameters according to the login information;
[0087] The login information encryption unit 200 is used to encrypt the login information, and use the obtained encrypted login information as the initial ciphertext;
[0088] The data combination encryption unit 300 is used to encrypt the data combination formed by the current ciphertext and characteristic parameters to obtain an encryption result, and increase the number of encryptions by 1 at the same time; wherein, the initial value of the number of encryptions is 1;
[0089] The number of encryption times judging unit 400 is used to judge whether the current number of encryption times is greater than...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com