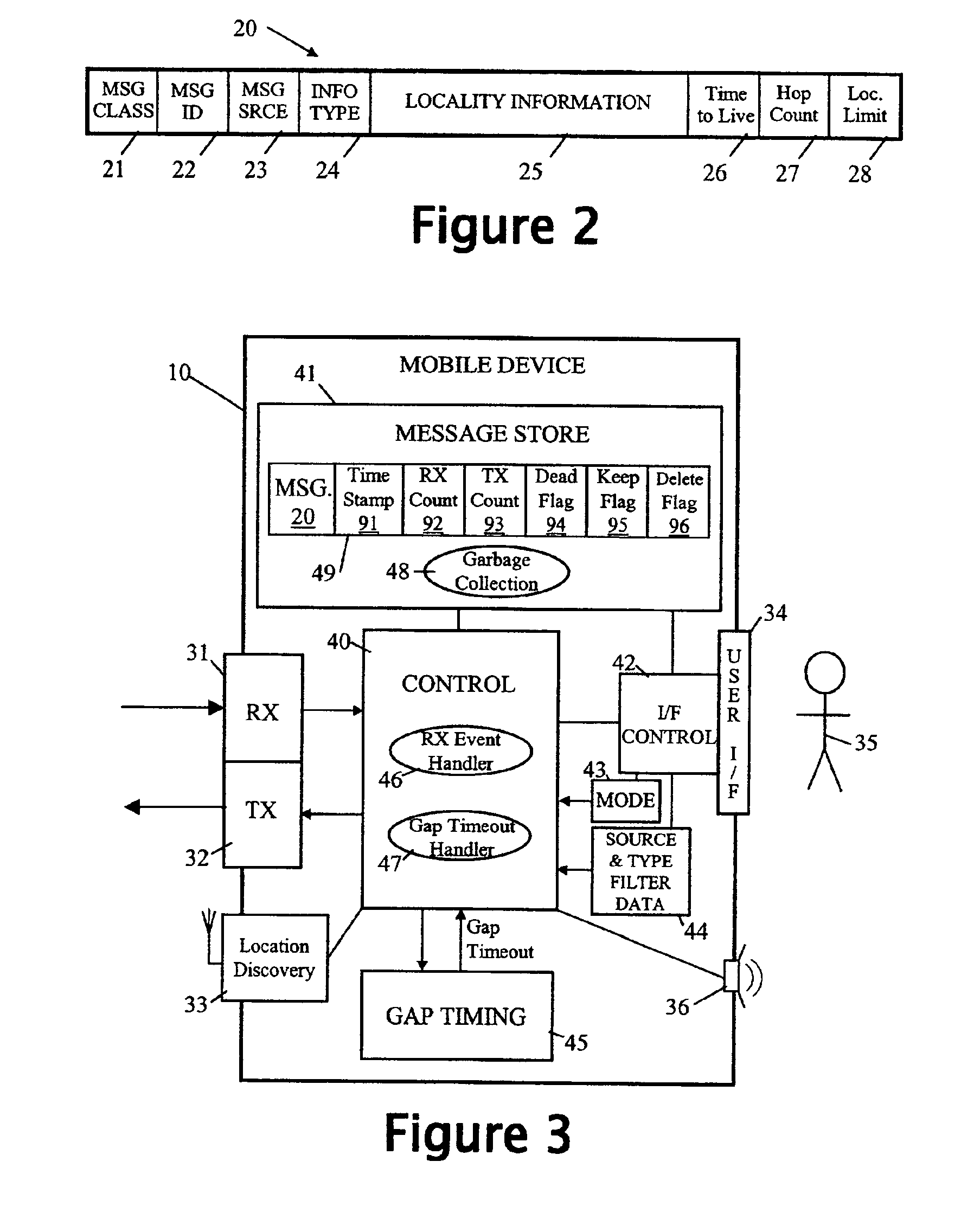
Patents
Literature
149 results about "Message propagation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
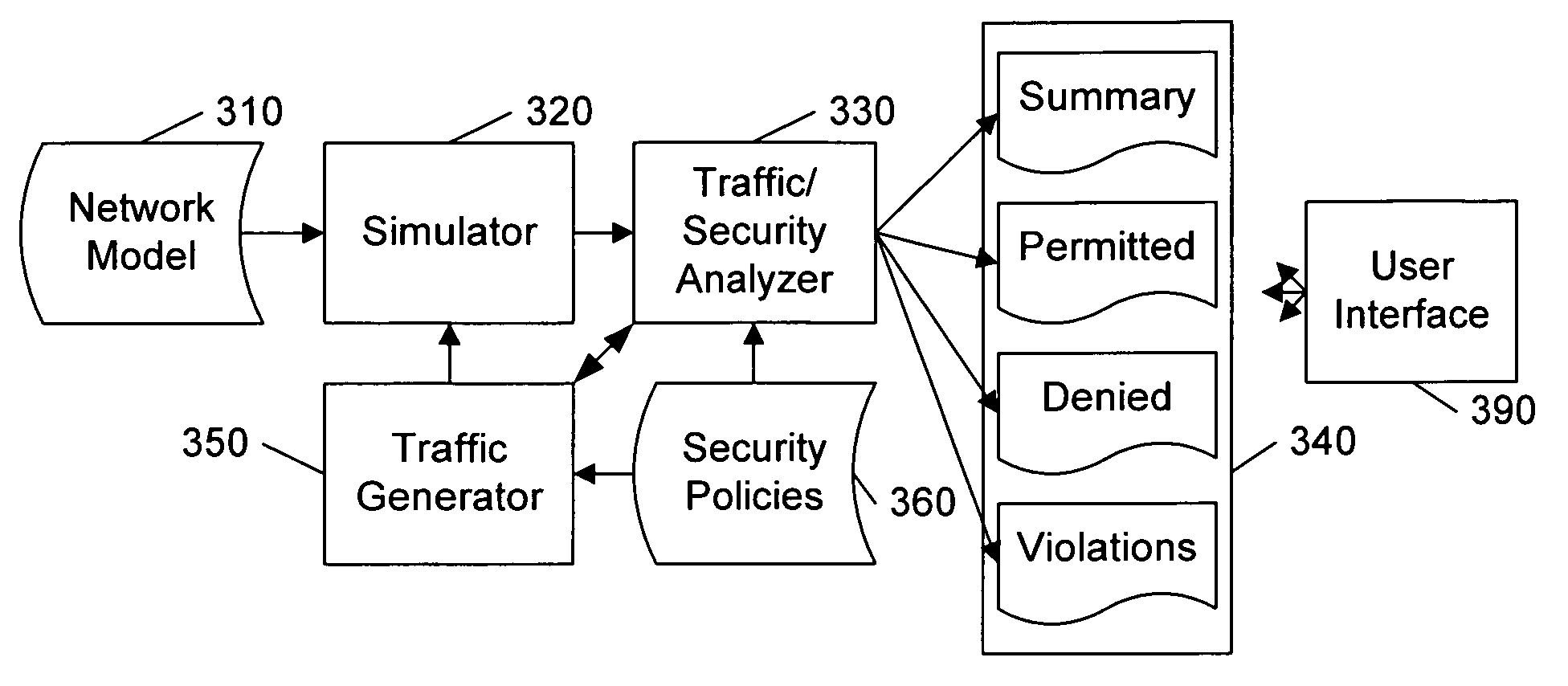
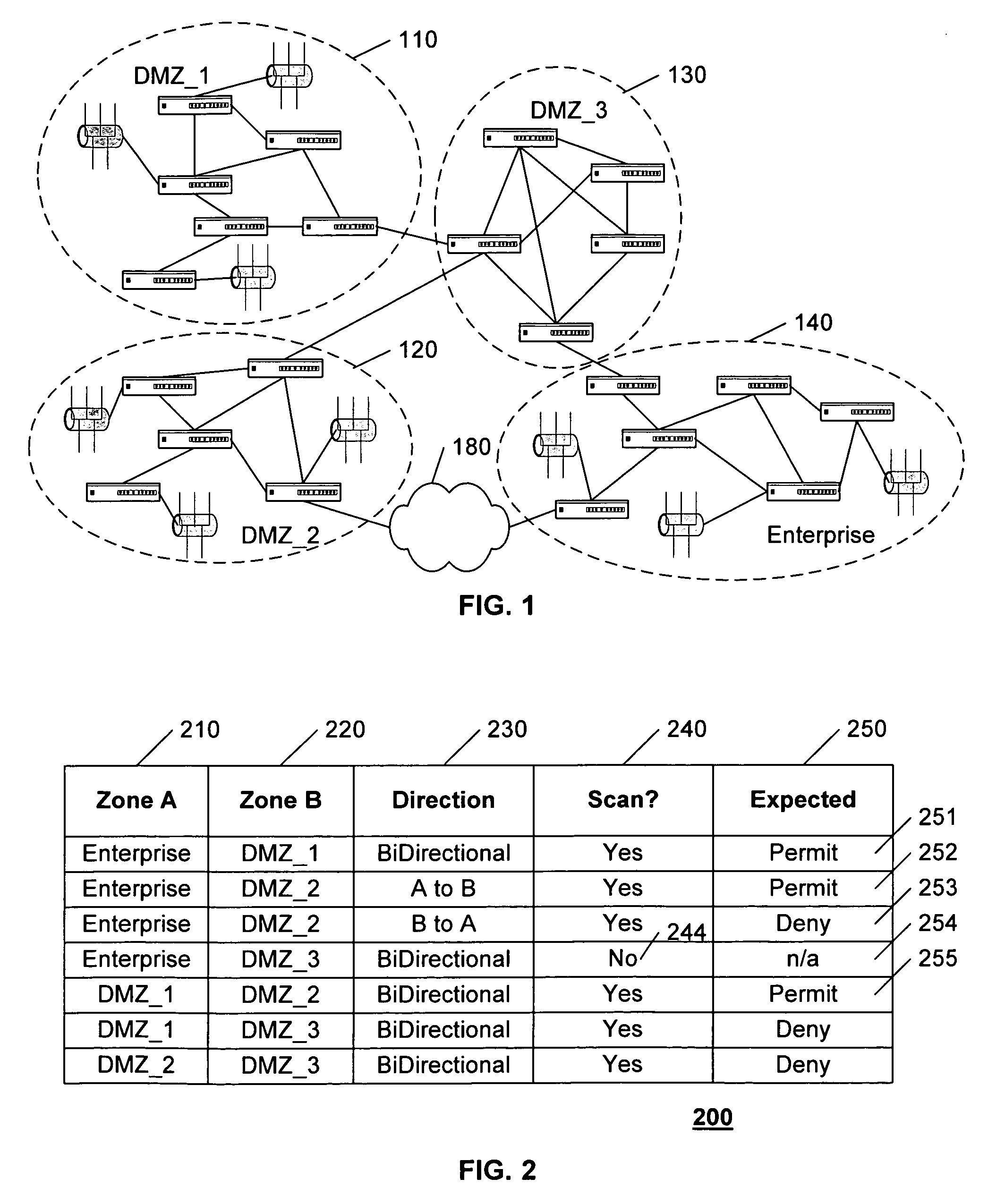
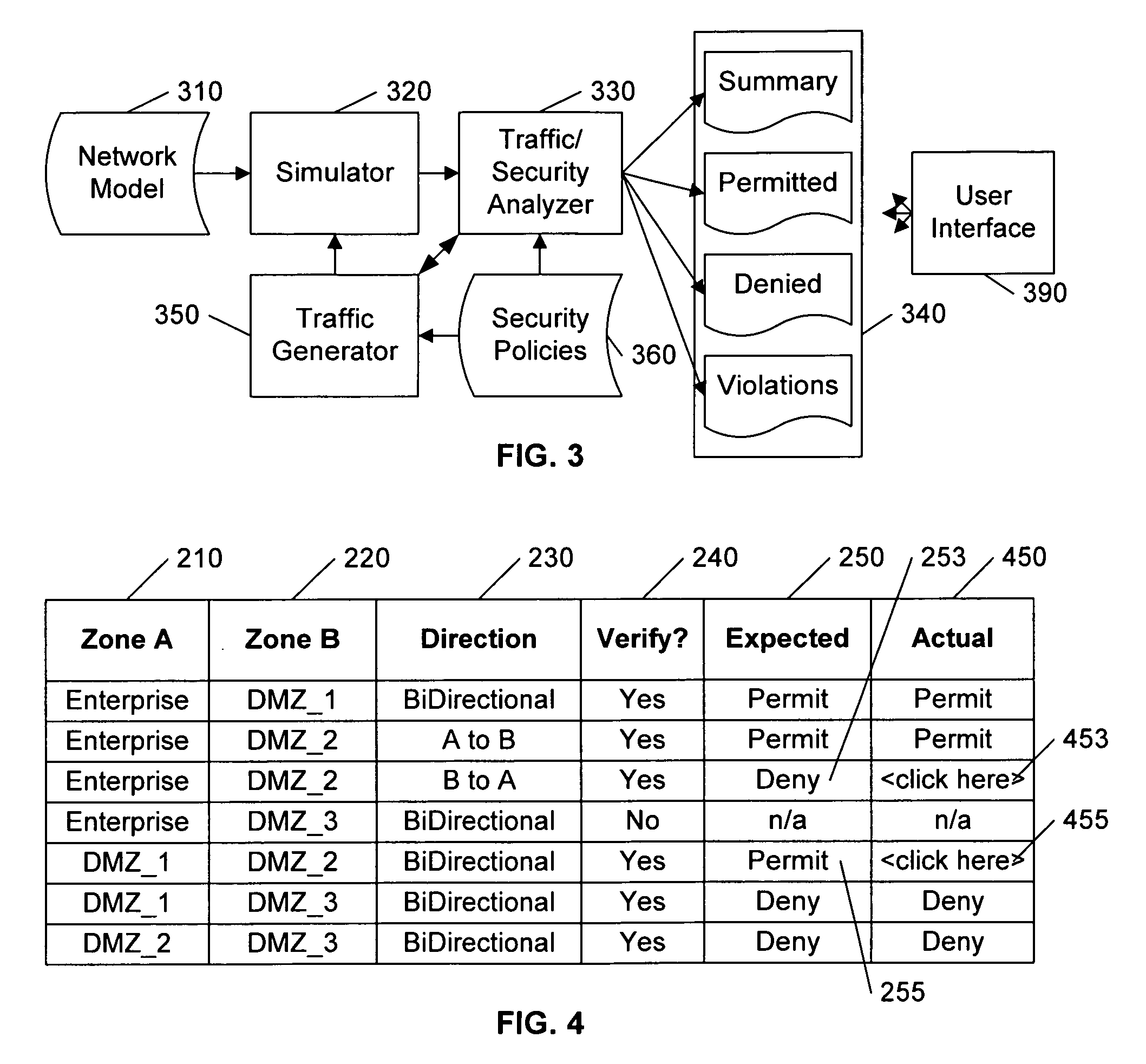
Analyzing security compliance within a network
ActiveUS20070157286A1Data switching networksSpecial data processing applicationsTraffic capacitySecurity compliance
A security policy database identifies the intended security policies within a network, a traffic generator provides test traffic that is configured to test each defined security policy, and a simulator simulates the propagation of this traffic on a model of the network. The model of the network includes the configuration data associated with each device, and thus, if devices are properly configured to enforce the intended security policies, the success / failure of the simulated test traffic will conform to the intended permit / deny policy of each connection. Differences between the simulated message propagation and the intended security policies are reported to the user, and diagnostic tools are provided to facilitate identification of the device configuration data that accounts for the observed difference. Additionally, if a network's current security policy is unknown, test traffic is generated to reveal the actual policy in effect, to construct a baseline intended security policy.
Owner:RIVERBED TECH LLC
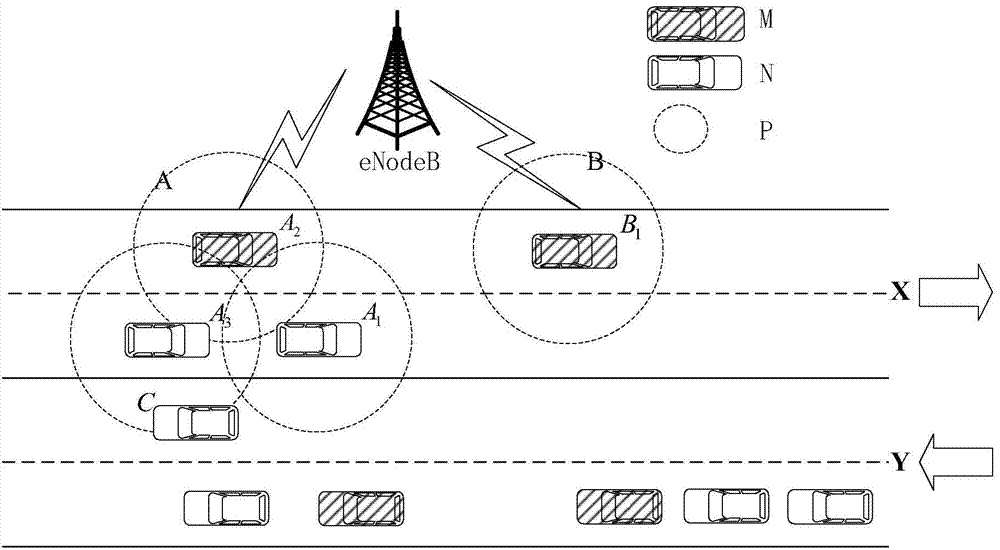
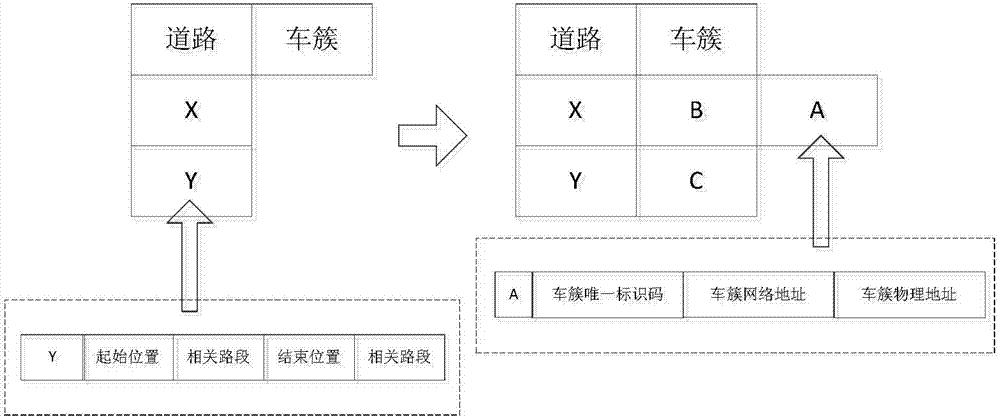
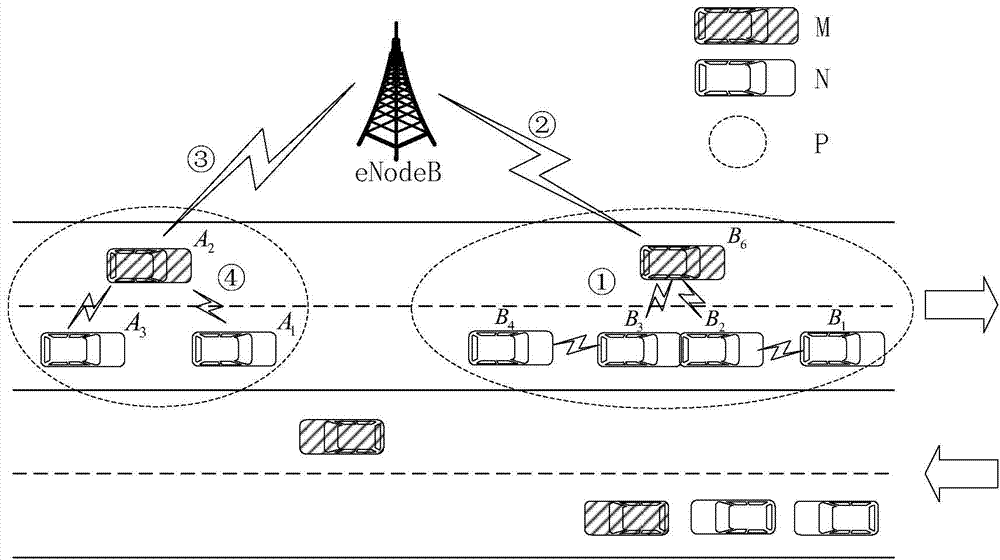
802.11p and LTE/LTE-a based vehicle networking message propagation method
InactiveCN103781198AAvoid rear-end accidentsAvoid occupying LTE/LTE-A system resourcesNetwork topologiesNetworks interconnectionBroadcastingSTI Outpatient
The invention relates to an 802.11p and LTE / LTE-A based vehicle networking message propagation method, which is characterized in that a GPS information collection module collects the running speed, the running direction and positional information of a vehicle, a 802.11p communication module of a vehicle which is in the same road section and runs in the same direction and a 802.11p communication module located in an effective communication range form an Ad hoc network, vehicles in the Ad hoc network form a vehicle cluster, the cluster head sends a secure message to an LTE / LTE-A base station at a scheduled time interval, and the LTE / LTE-A base station updates a road table of the vehicle cluster; in an emergency case, vehicles in the same vehicle cluster use the 802.11p communication module to carry out message broadcasting, the cluster head sends the message to the LTE / LTE-A base station, and the LTE / LTE-A base station broadcasts the message to the cluster head of a related vehicle cluster according to the vehicle cluster road table. The 802.11p and LTE / LTE-A based vehicle networking message propagation method has the advantages of high practicability, low deployment cost and the like.
Owner:TONGJI UNIV
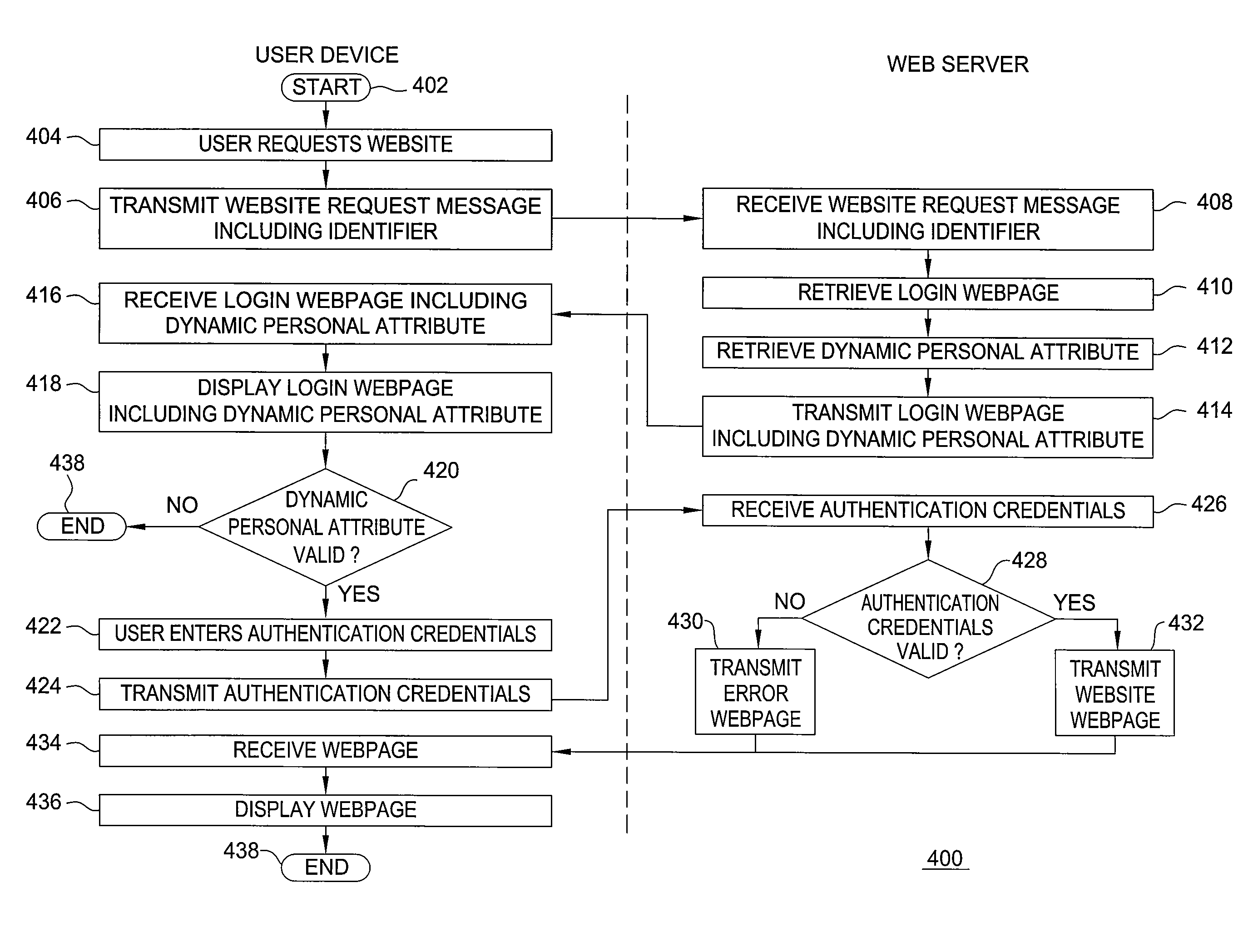
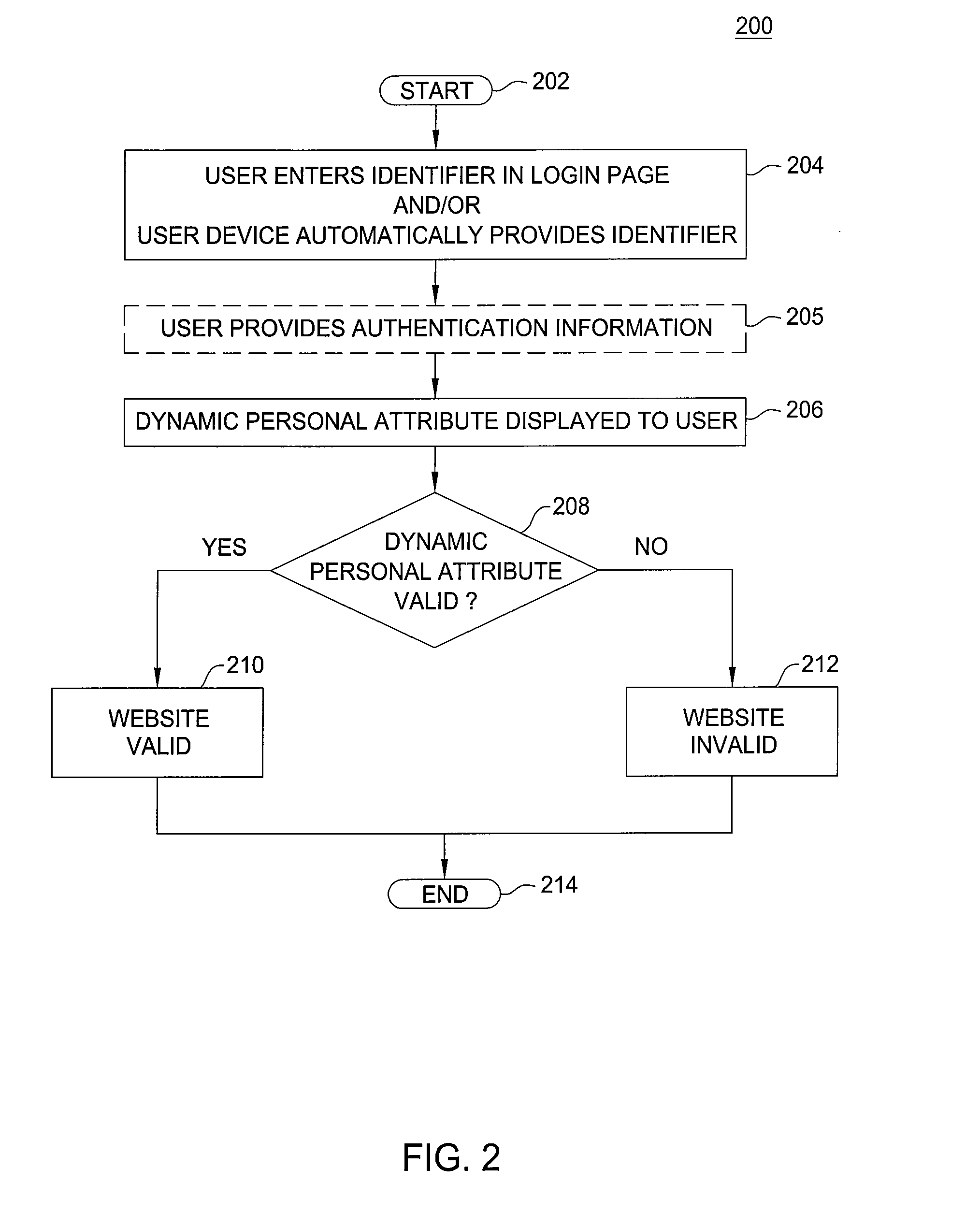
Method and apparatus for preventing phishing attacks
ActiveUS20090077637A1Preventing phishing attackFinanceDigital data processing detailsWeb serviceAuthentication server
The invention includes a method and apparatus for preventing phishing attacks. A first method, for informing a user that a remote server is valid, includes receiving a request for information available from the remote server where the request includes an identifier, obtaining a dynamic personal attribute associated with the user using the identifier, and propagating the dynamic personal attribute toward the user, wherein the dynamic personal attribute is adapted for use by the user in validating the remote server. The remote server may be a web server, an authentication server, or any other remote device with which the user may desire to authenticate. A second method, for informing a user that a received message is associated with a valid website, includes obtaining a dynamic personal attribute associated with a user, generating a message for the user where the message is adapted to enable the user to request a website and includes the dynamic personal attribute associated with the user, and propagating the message toward the user. The received message may be any type of message, such as an email message, an instant message, a text message, and the like.
Owner:ALCATEL LUCENT SAS
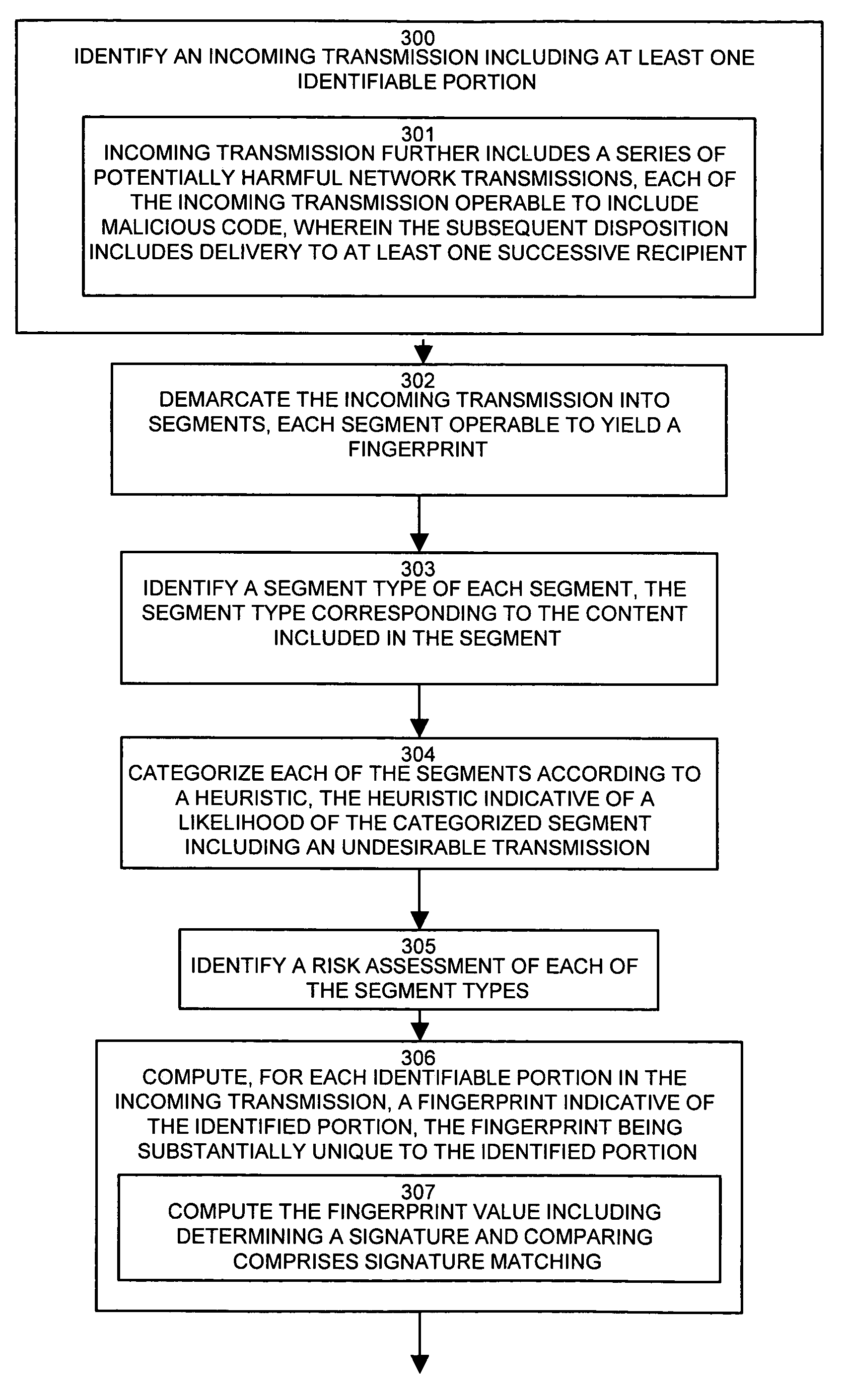
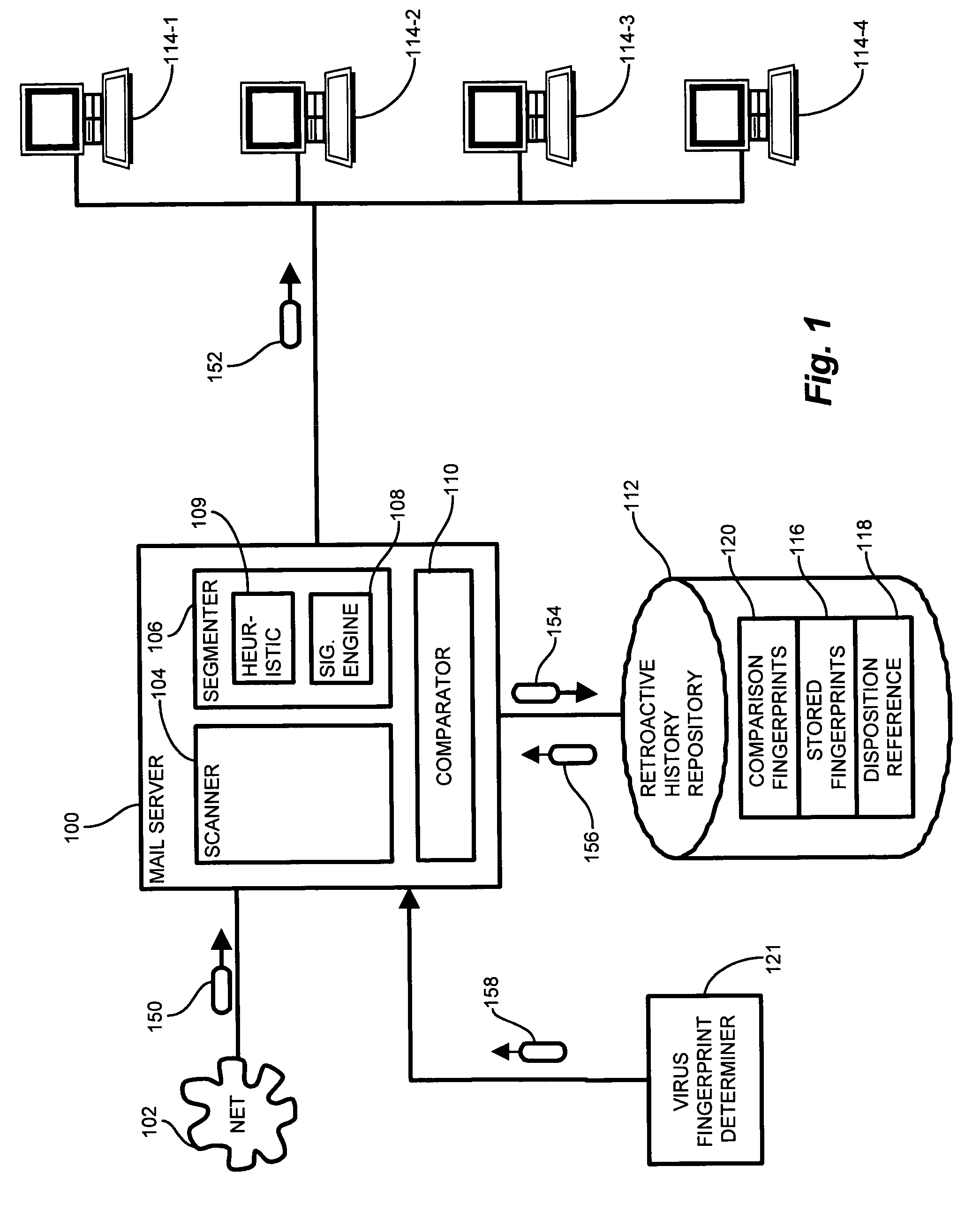
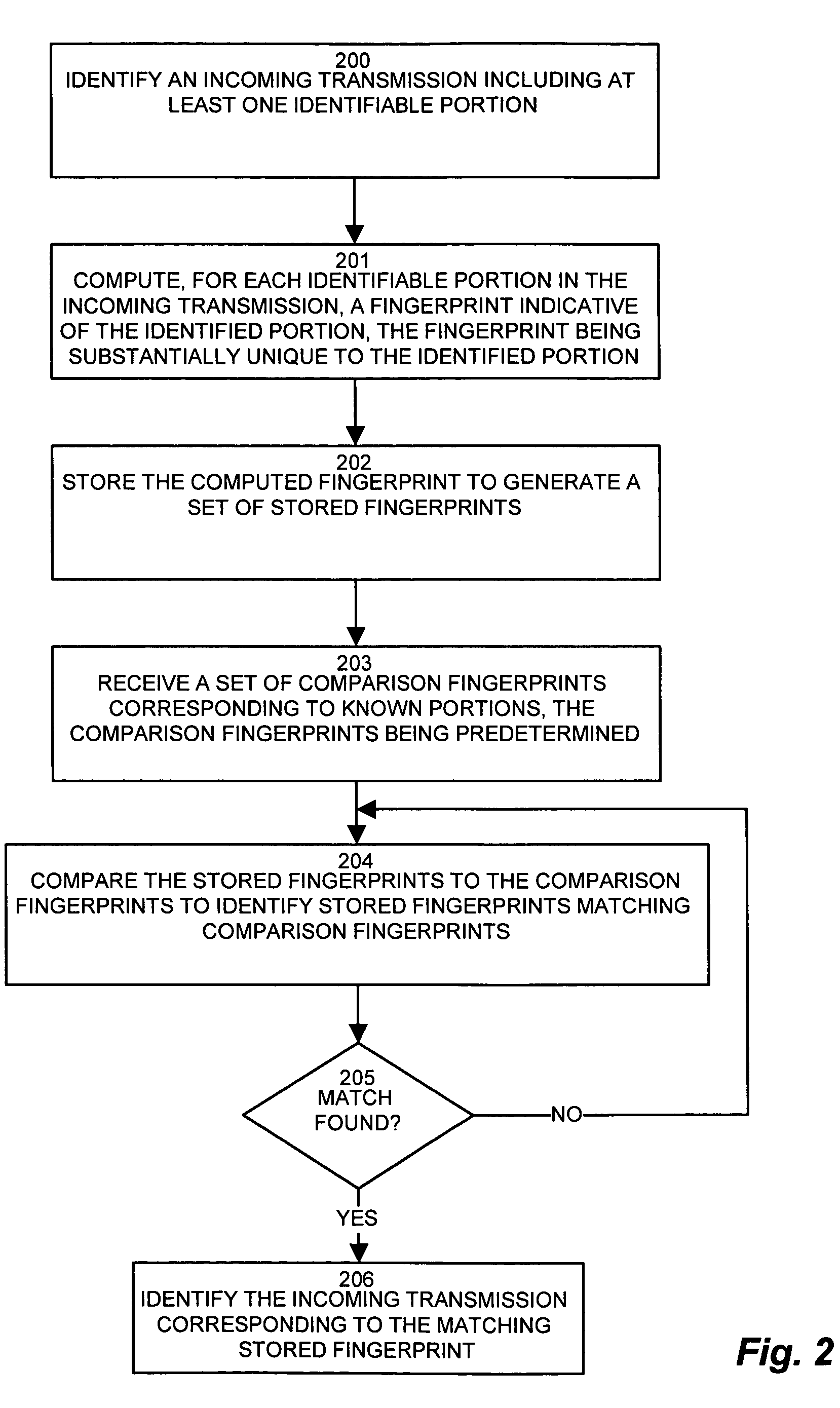
System and method for identifying message propagation
ActiveUS7539871B1Overcomes shortcomingShorten the overall cycleUser identity/authority verificationComputer security arrangementsRemedial actionComputer science
Conventional virus detection software monitors incoming arrivals of network traffic. Retroactive analysis and / or monitoring of previously accepted traffic is not included in the scope of protection. A retroactive virus detection and propagation history tracking mechanism provides identification of successive recipients of a newly discovered virus which may have eluded detection during the lag time prior to effecting the detection of a new virus. A propagation history maintains a set of recipients receiving a potentially harmful transmission. Upon detection of a particular transmission or portion thereof as being a virus, the propagation history contains a set of infected recipients, which the tracking mechanism notifies so as to perform remedial action and contain the virus to the known set of infected recipients. In this manner, configurations of the invention maintain a set of successive recipients of a virus, and retroactively track and contain the newly propagated virus once detected.
Owner:ORACLE INT CORP
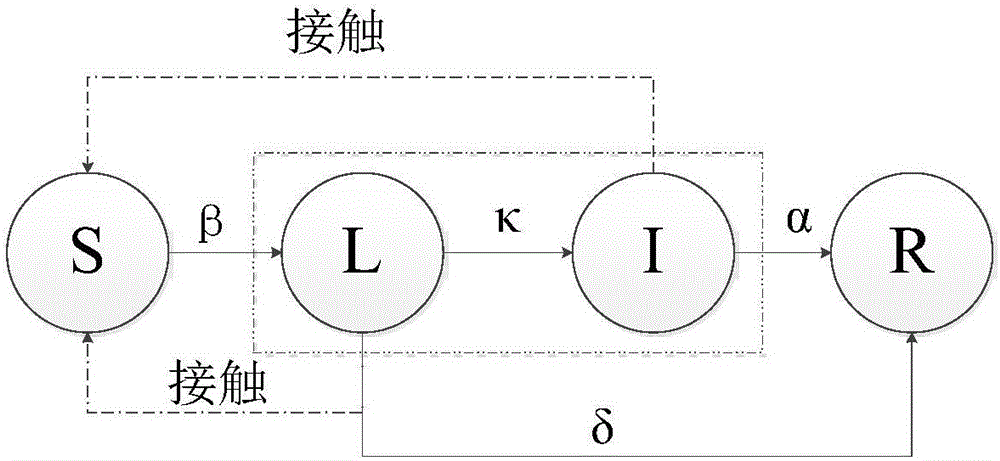
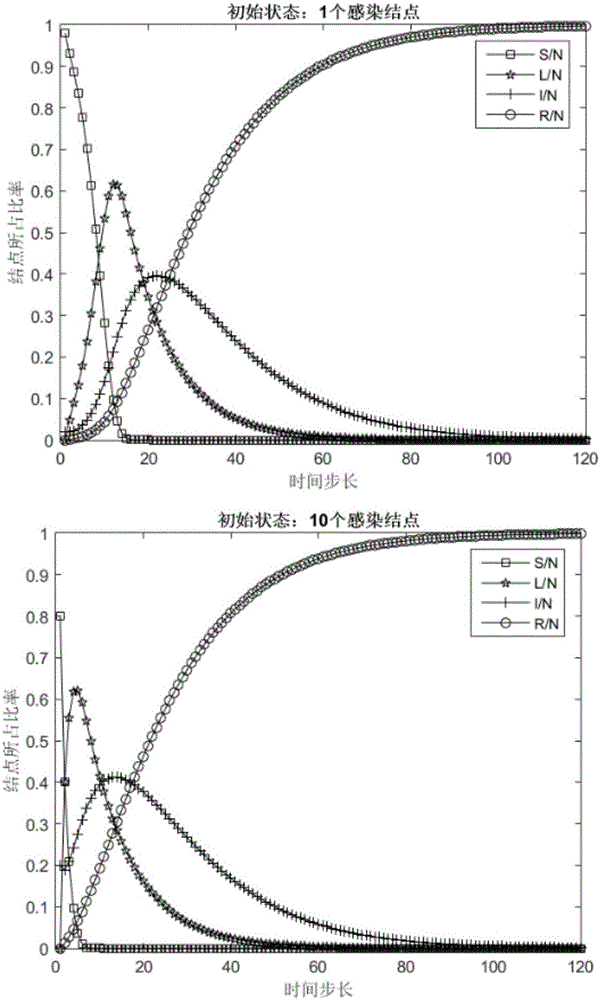
Social network based message propagation model
ActiveCN106096075AGood inhibitory effectHigh similarityData processing applicationsData switching networksDynamic equationCrowds
The present invention discloses a social network based message propagation model, which is a method, based on the special line of the crowd in the network and the average degree of the nodes in the social network, for carrying out modeling analysis on message propagation in the social network and proposing a node importance based rumor immune strategy. The dynamic equations of the <k> SLIR message propagation model are established in the small-world network; by virtue of the method disclosed by the present invention, influences of nodes in various states in the social network, on message propagation can be realistically taken into consideration; and according to the node importance based improved rumor immune strategy proposed by the present invention, propagation of rumors in social network can be better inhibited.
Owner:SUN YAT SEN UNIV
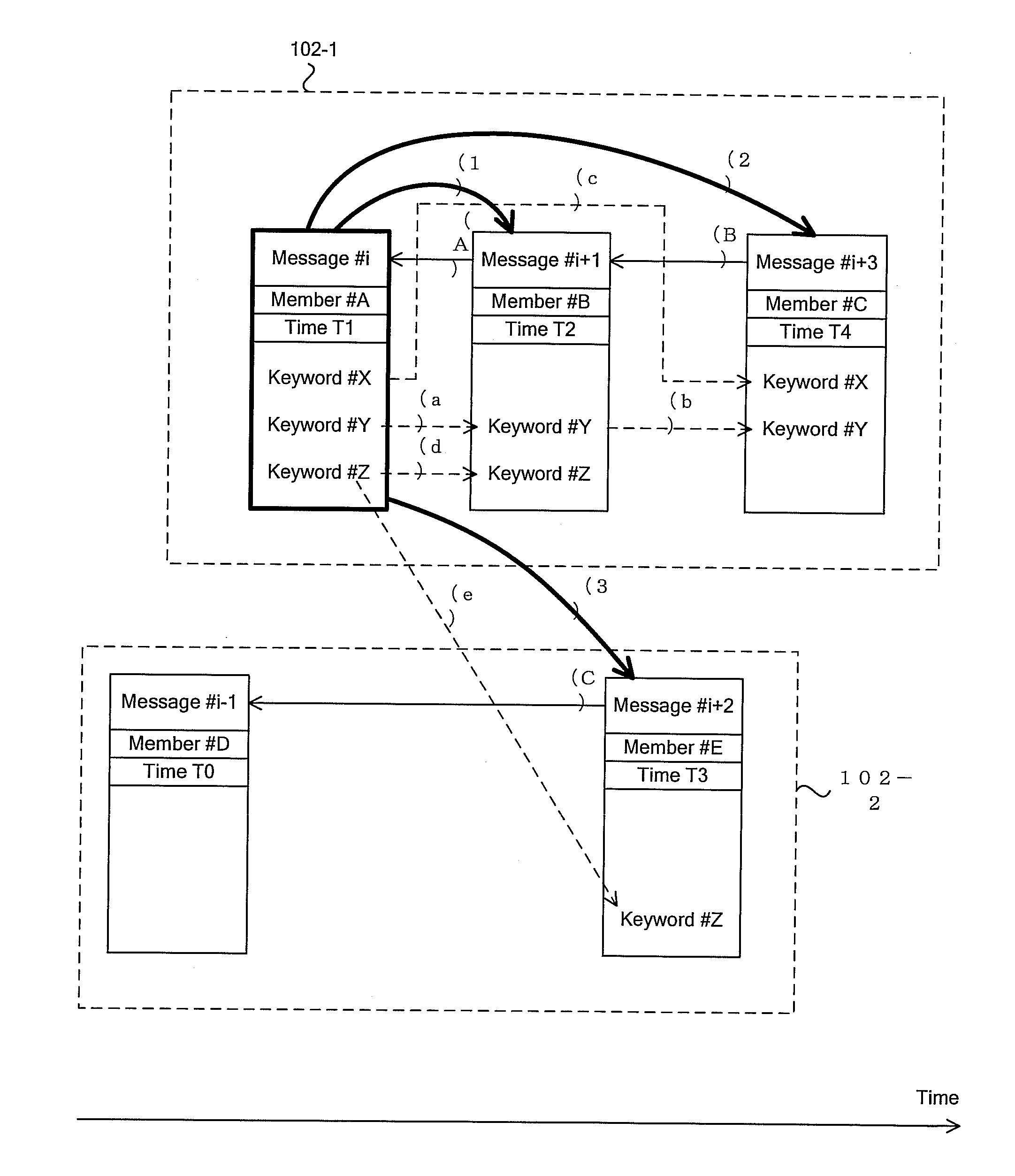
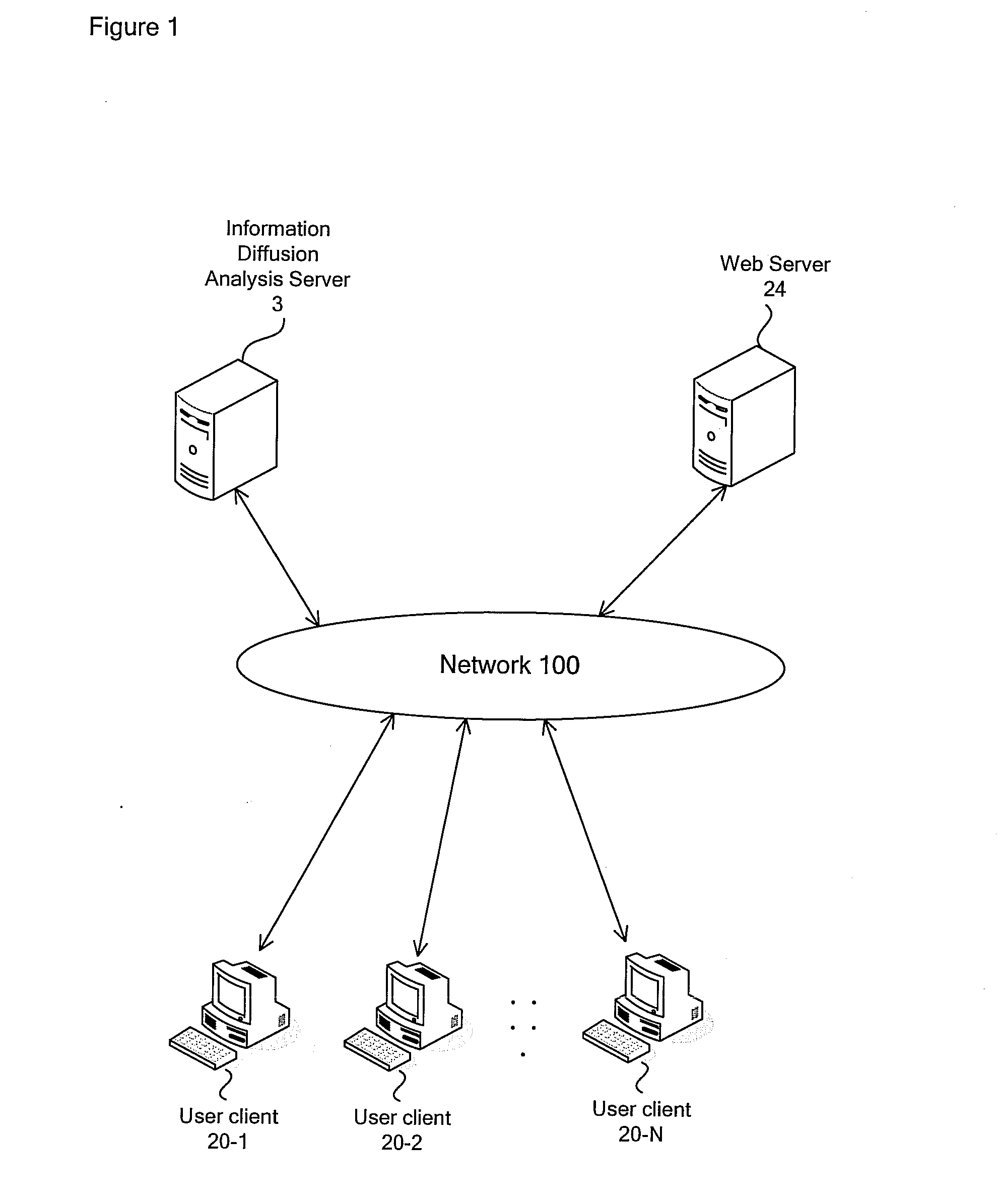
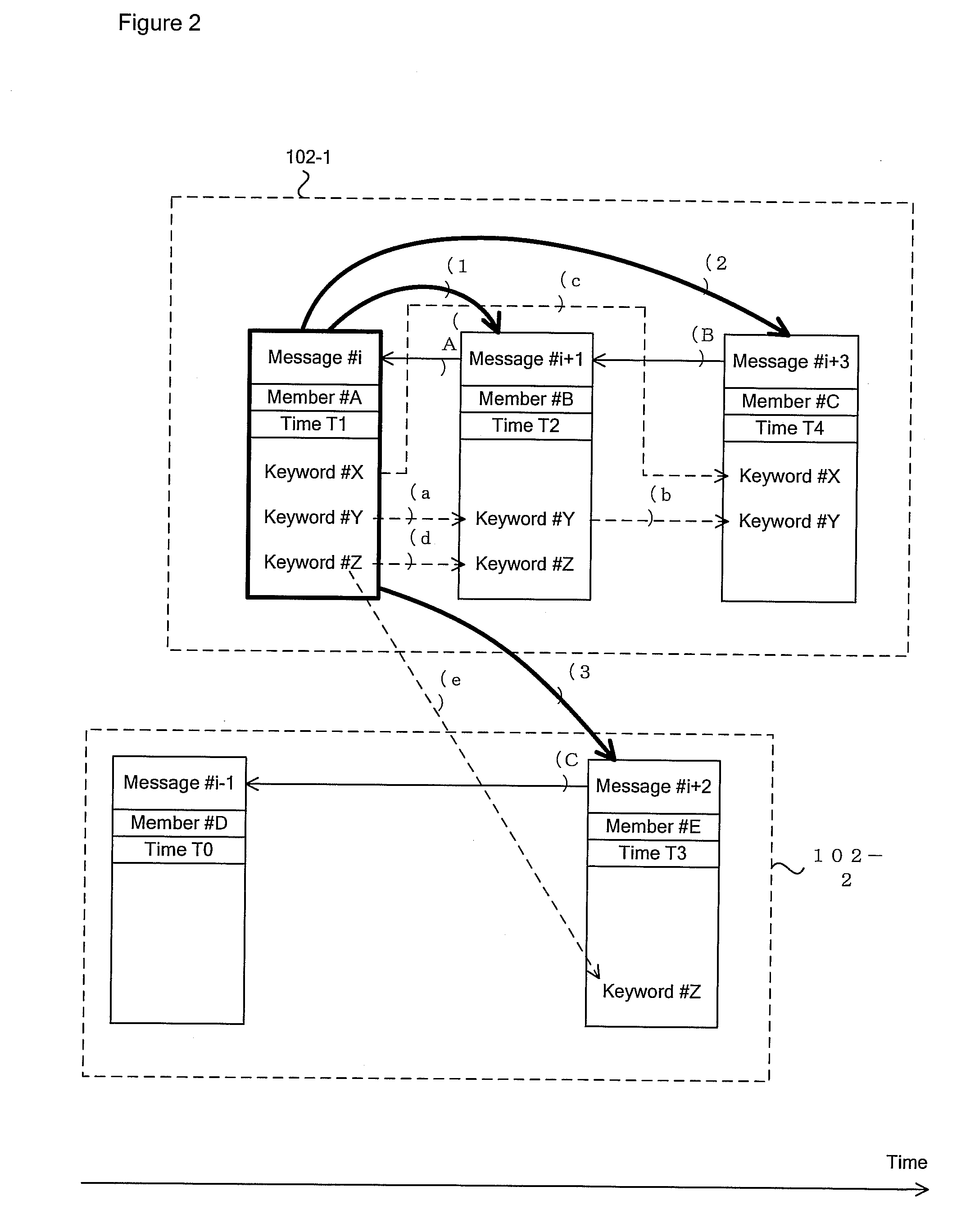
Information propagation analyzing system, information propagation analyzing apparatus, method of information propagation analysis and program therefor
InactiveUS20100241713A1Data processing applicationsMultiple digital computer combinationsInformation propagationWeb service
An information propagation analyzing system and method of information propagation analysis. Information propagation analyzing apparatus (3) analyzes the relationship among multiple message informations exchanged within a community space monitored by web server (24) and creates information on inter-message chain structure. The information propagation analyzing apparatus (3) computes the message propagation capacity for each of the message informations on the basis of the inter-message chain structure. The information propagation analyzing apparatus (3) computes the degree of information propagation between members belonging to the community on the basis of the message propagation capacity. The information propagation analyzing apparatus (3) constructs a social network consisting of a group wherein information is likely to easily propagate on the basis of the degree of information propagation between members.
Owner:HEWLETT PACKARD DEV CO LP
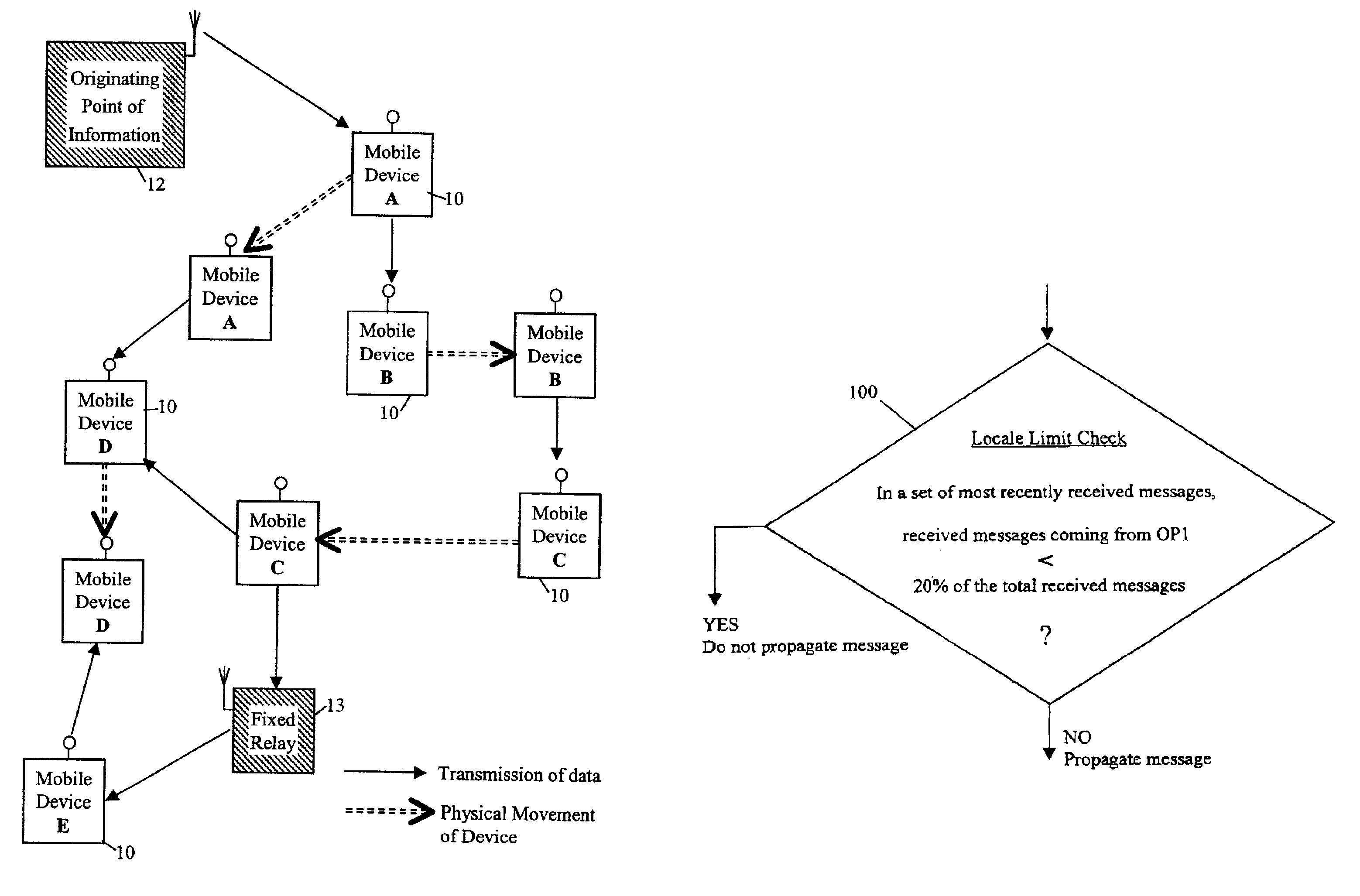
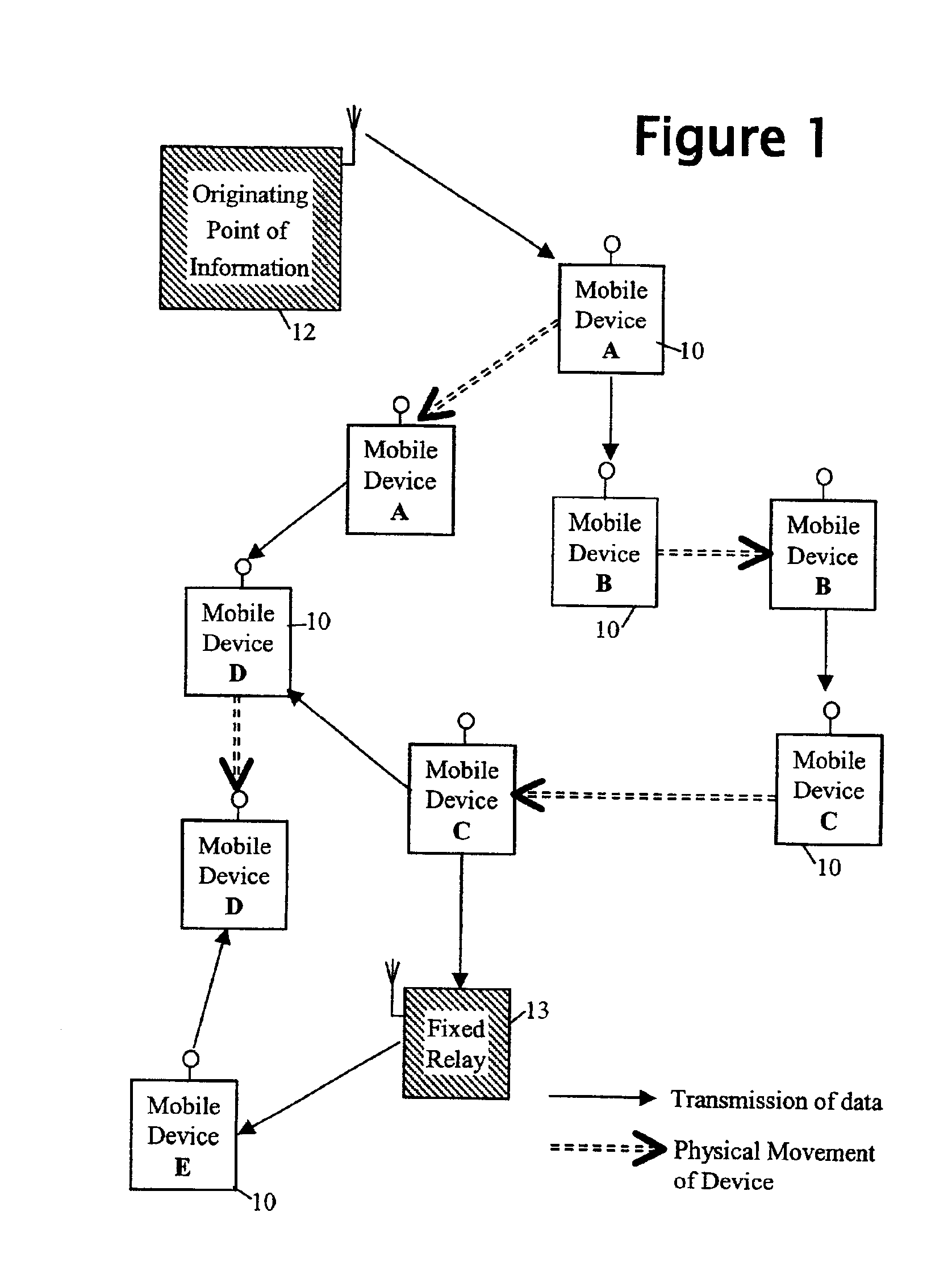
Limiting message diffusion between mobile devices
InactiveUS6999717B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile deviceReal-time computing
Information with local relevance is diffused locally using mobile devices equipped with non-wired short-range communication means, the information being propagated from an originating point in messages passed from device to device in an unstructured way. The devices implement measures for limiting message propagation including controlling propagation of a message from a particular originating point (OP1) in dependence on the prominence of the occurrence of that originating point in a set of most recently received messages.
Owner:HEWLETT PACKARD DEV CO LP
Microblog message influence measuring method based on microblog message propagation tree
InactiveCN104537096AEffective evaluationFilter the impact of the influence metricSpecial data processing applicationsComputer scienceMessage propagation
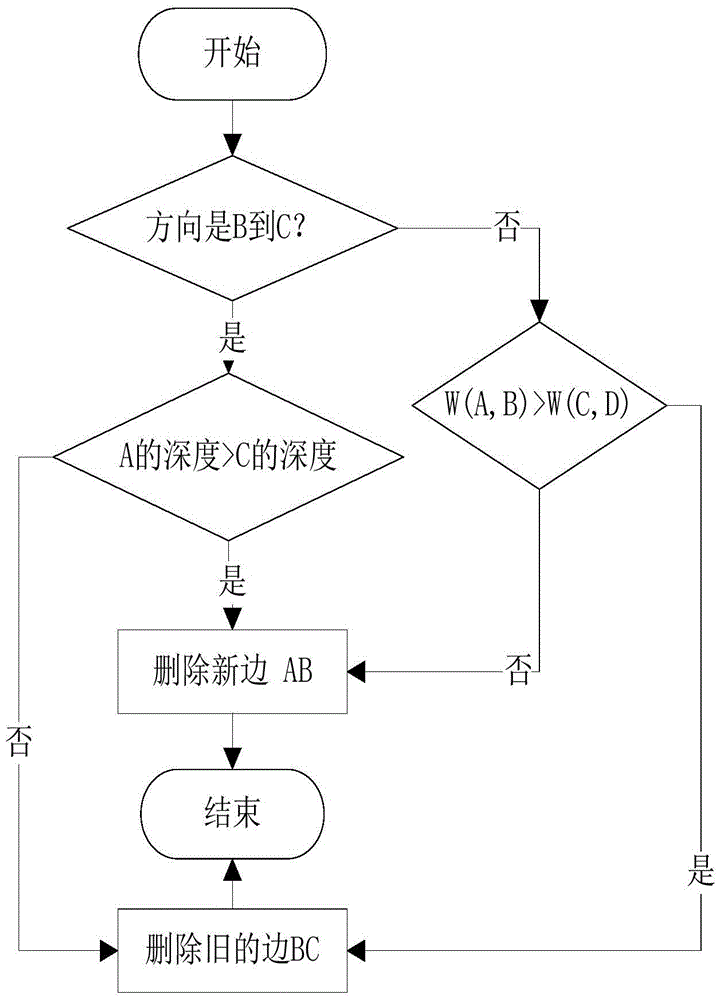
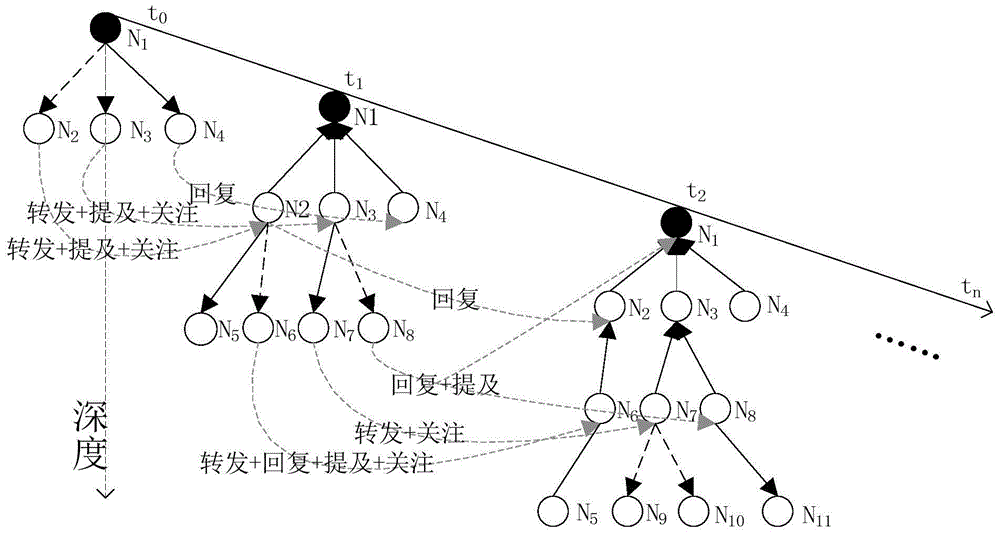
The invention discloses a microblog message influence measuring method based on a microblog message propagation tree. The method comprises the following steps that messages issued by a user in microblog are obtained, the message types and interaction types of the messages are read, the messages are ranked into a message queue according to the chronological order, and the historical interaction attribute of the user is read; the kth message is read from the message queue, the user issuing the current message serves as a node, the interaction type of the current message serves as an edge and is added into a propagation picture of the previous (k-1) messages, and the propagation picture is processed to form the propagation tree; the influence weight of each edge of the propagation picture is obtained; the influence weights of the edges are added to obtain the microblog message influence. According to the method, the implicit interaction behavior of the micoblog is taken into consideration, and the microblog message influence is comprehensively and effectively calculated.
Owner:HARBIN ENG UNIV
Message propagating method and system
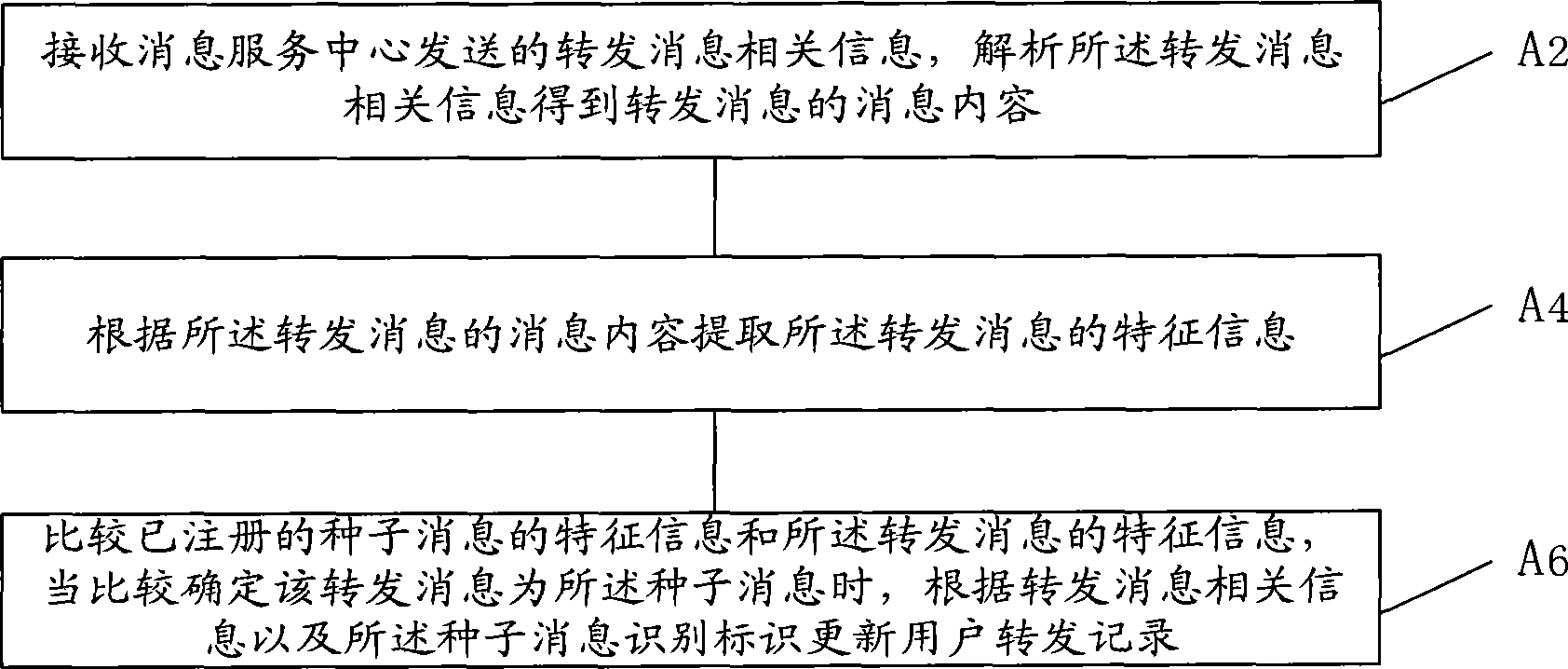
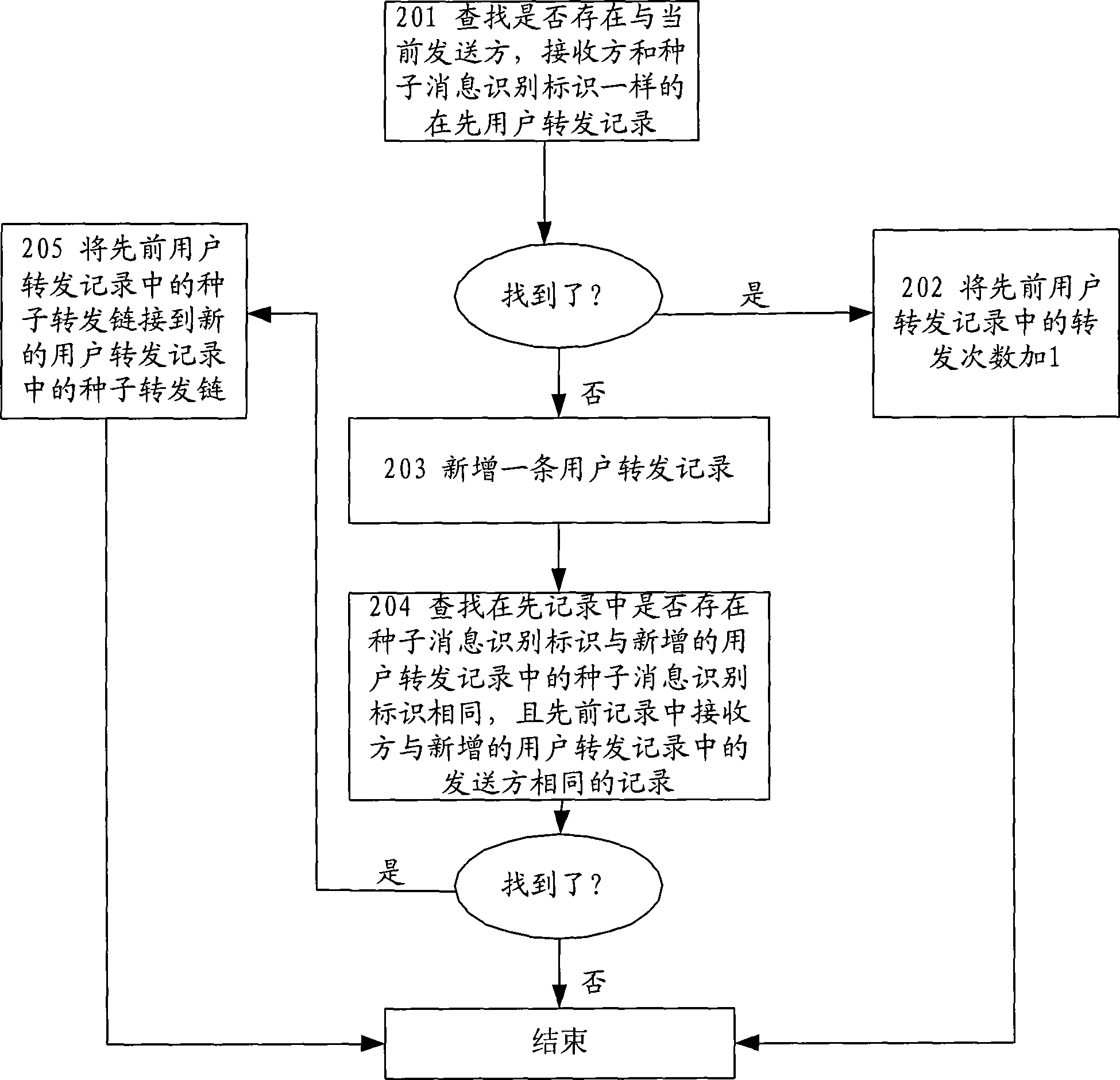
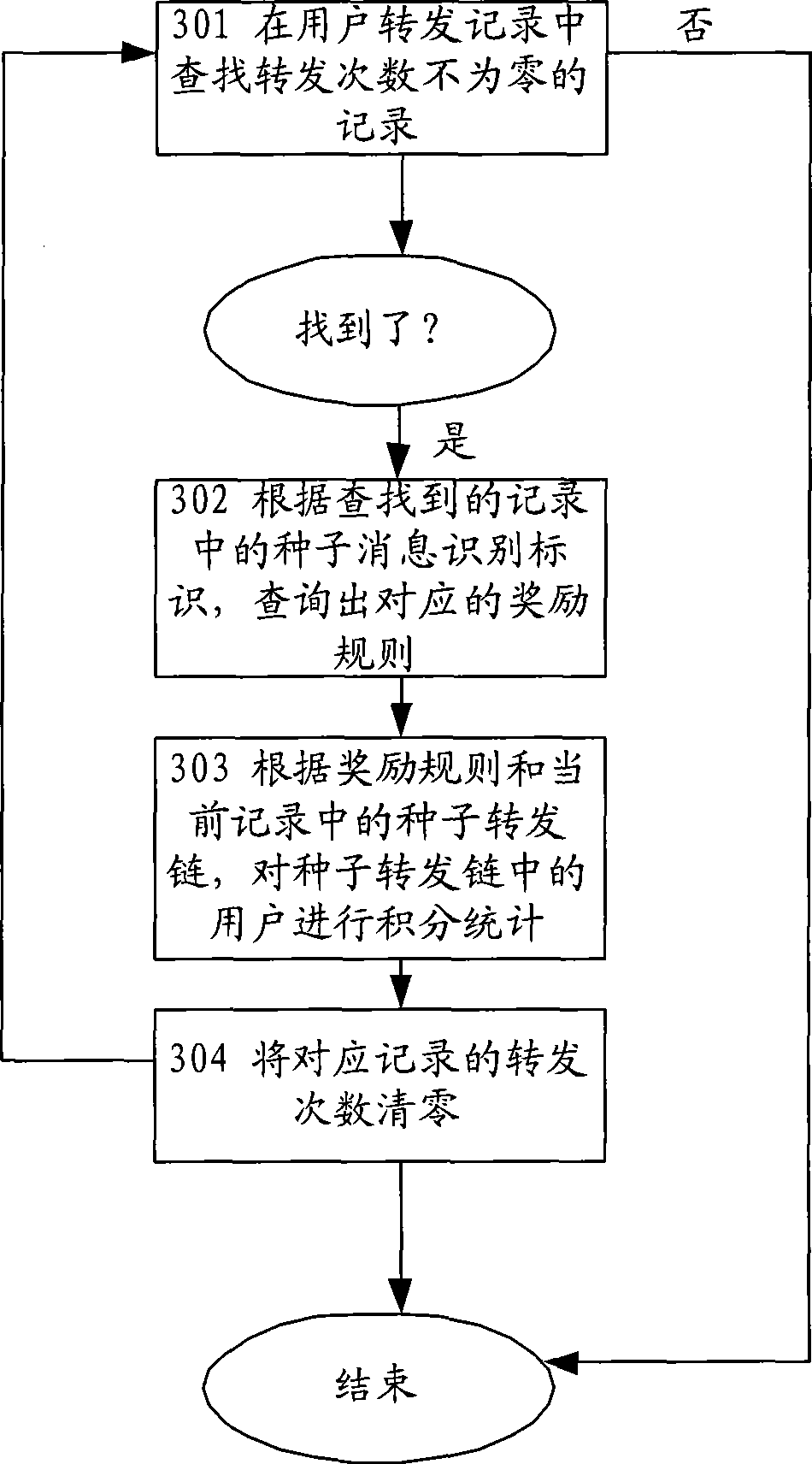
InactiveCN101389082AAccurate rewardEasy to handleRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsWorld Wide WebEngineering
The embodiment of the invention discloses a message transmitting method and system. The embodiment of the invention, by comparing characteristic information of seed message with that of a forwarded message of an information service centre, when the forwarded message is seed message determined by comparison, updates user forwarding record according to related information of the forwarded message of an information service centre and a seed information identifier and processes chain statistics for the user according to the user forwarding record. When the user forwards the message, the operation is simple and feasible and the user is rewarded in chain, which improves zeal of users.
Owner:HUAWEI TECH CO LTD
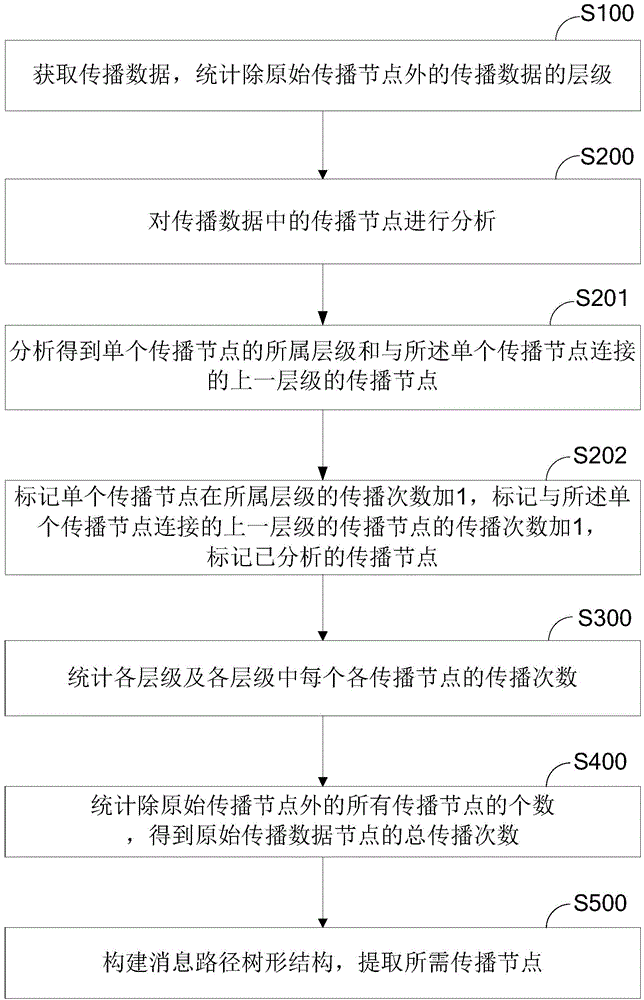
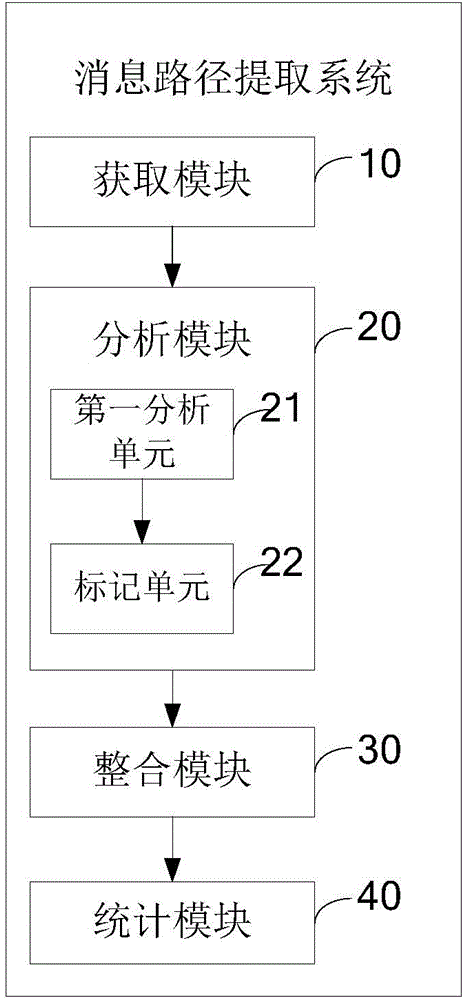
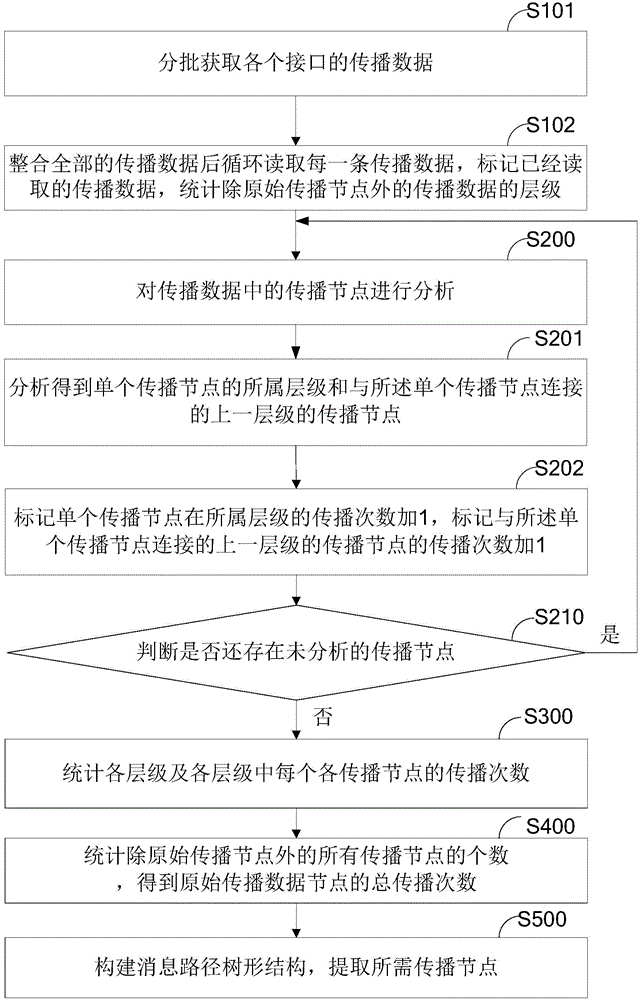
Message propagation path extraction method and system
InactiveCN104092598AEasy to analyzeUnderstand the spread effectData switching networksSpecial data processing applicationsStructure chartComputer science
The invention provides a message propagation path extraction method and system. The method comprises the first step of obtaining propagation data and conducting statistics on hierarchies of the propagation data except original propagation nodes, the second step of analyzing the propagation nodes in the propagation data, wherein the analyzing process includes the steps of conducting analysis to obtain the hierarchy which the single propagation node belongs to and the propagation node of the previous hierarchy connected with the single propagation node, marking the propagation frequency of the single propagation node in the hierarchy where the single propagation node is located and adding one to the propagation frequency, marking the propagation frequency of the propagation node, connected with the single propagation node, of the previous hierarchy, adding one to the propagation frequency and marking the analyzed propagation nodes, the third step of conducting statistics on all the hierarchies and the propagation frequencies of all the propagation nodes in all the hierarchies, the fourth step of conducting statistics on the number of all the propagation nodes except the original propagation nodes to obtain the total propagation frequency of the original propagation nodes, and the fifth step of constructing a message path tree structure and extracting required propagation nodes. By the adoption of the message propagation path extraction method and system, the message propagation nodes and message propagation paths are analyzed and then integrated to obtain a path structure chart, the key propagation nodes are obtained, and the propagation effect is achieved.
Owner:厦门欣欣信息有限公司
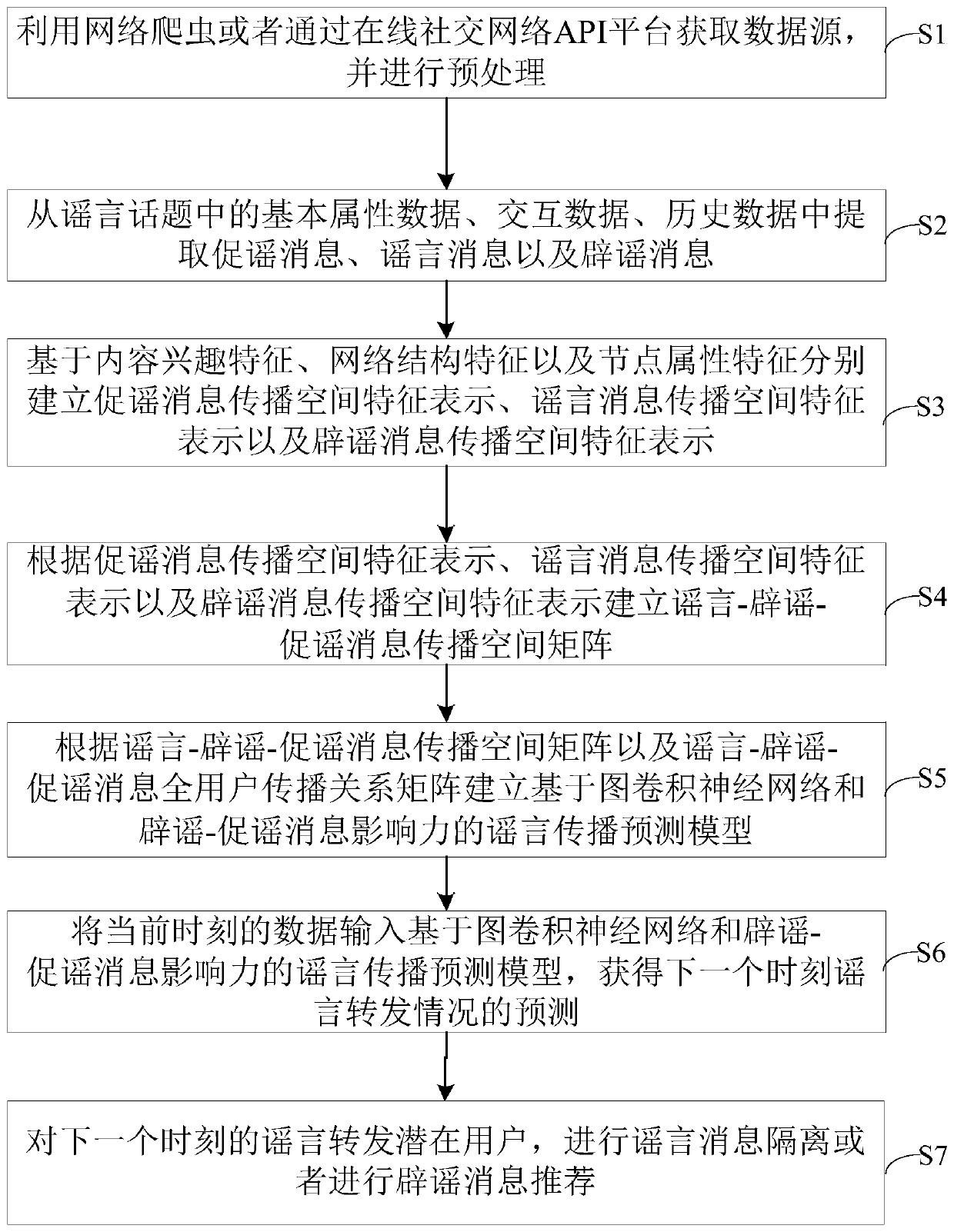
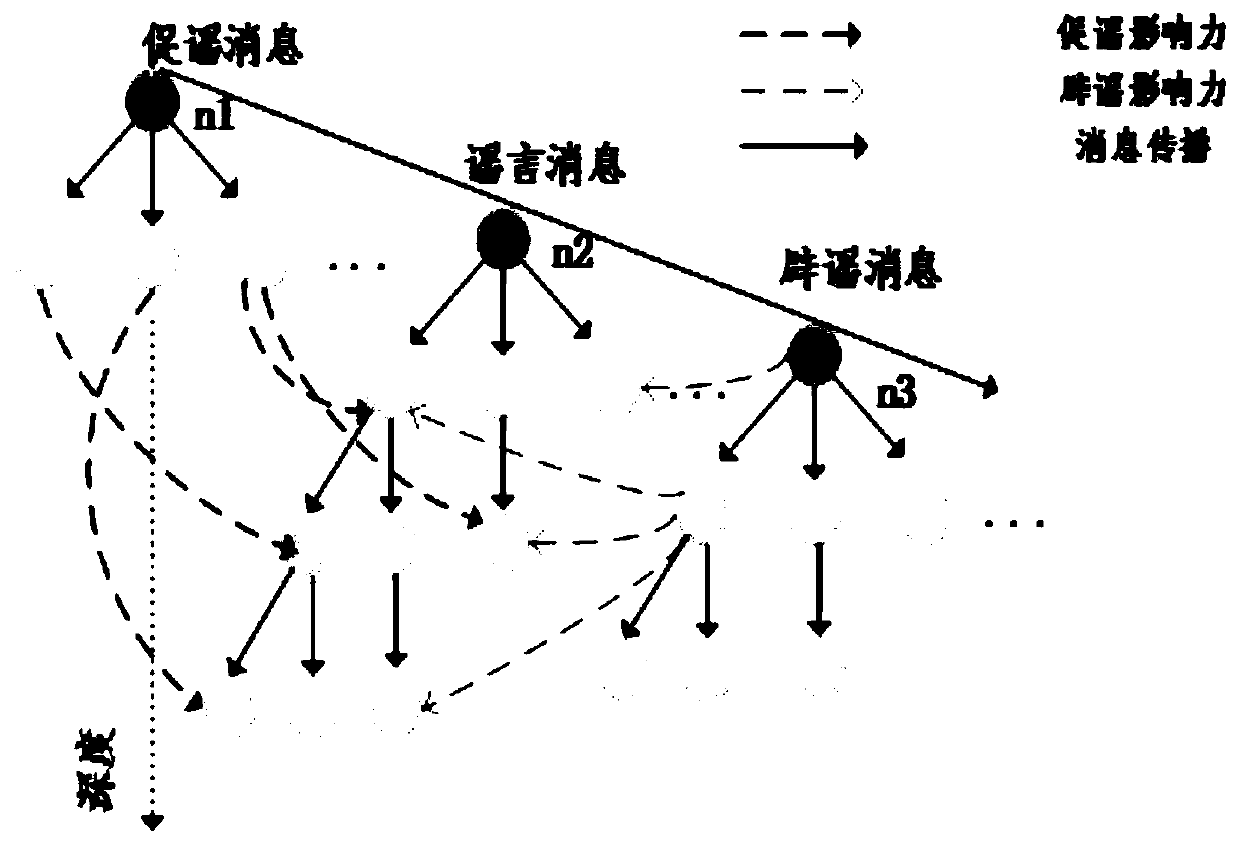
Rumor propagation control method based on rumor promotion-rumor refuting message and representation learning
ActiveCN110825948ATrue portrayalForecast forwardingData processing applicationsWeb data indexingNetwork structureEngineering
The invention belongs to the technical field of social network control, and relates to a rumor propagation control method based on rumor promotion-rumor refuting message and representation learning. The rumor propagation control me, extracting propagation space characteristics of rumor promotion messages, rumor messages and rumor refuting messages based on content interest characteristics, networkstructure characteristics and node attribute characteristics, and establishing a rumor-rumor refuting-rumor promotion message propagation space matrix; establishing a rumor propagation prediction model based on a graph convolutional neural network and rumor refuting-rumor promoting message influence according to the matrix and the rumor-rumor refuting-rumor promoting message full-user propagationrelationship matrix; inputting the current data into a rumor propagation prediction model to obtain prediction of a rumor forwarding situation; carrying out rumor message isolation or rumor refutingmessage recommendation on the rumor forwarding potential user at the next moment. According to the method, the user forwarding situation under the rumor topic can be effectively predicted, and meanwhile, the rumor propagation dynamic process can be more truly described.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
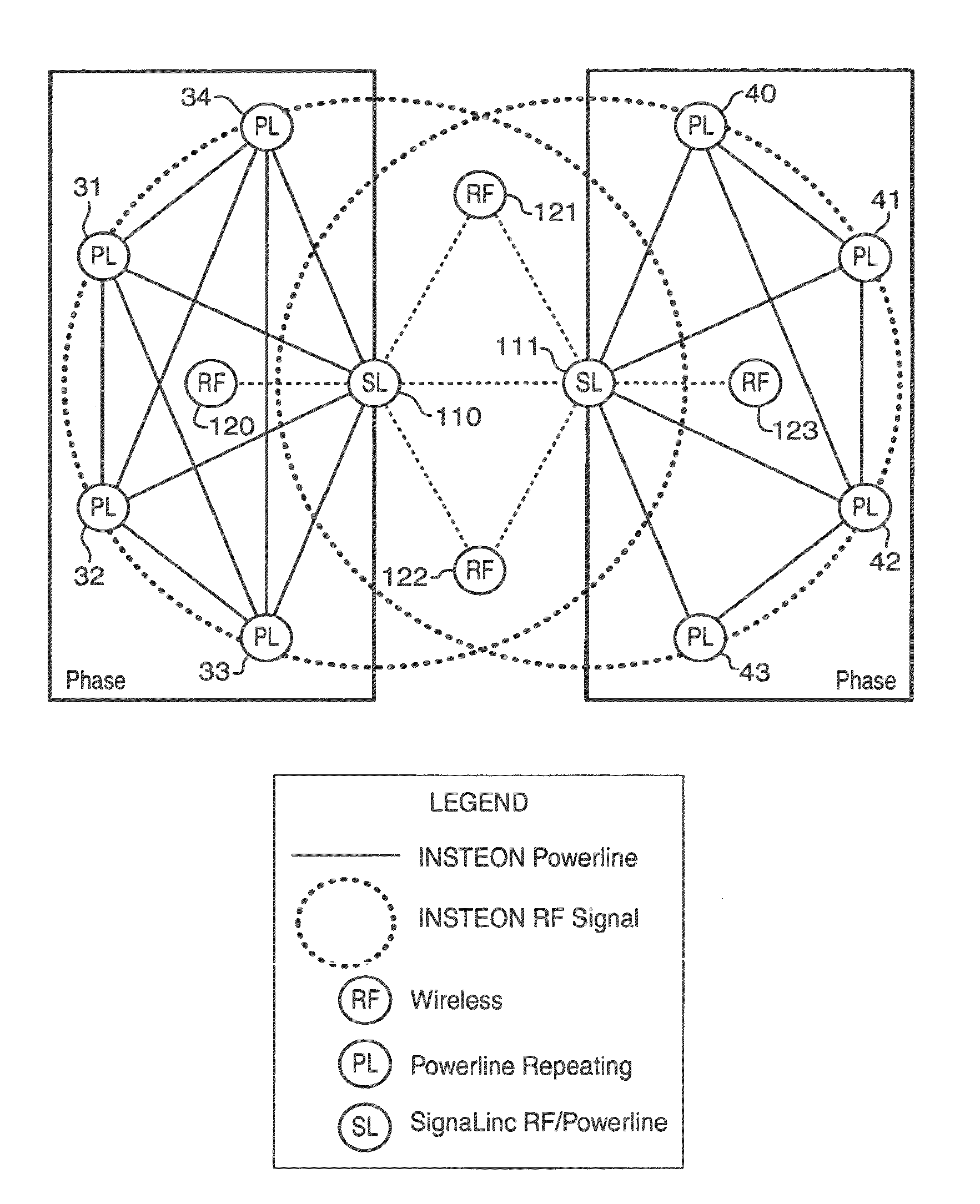
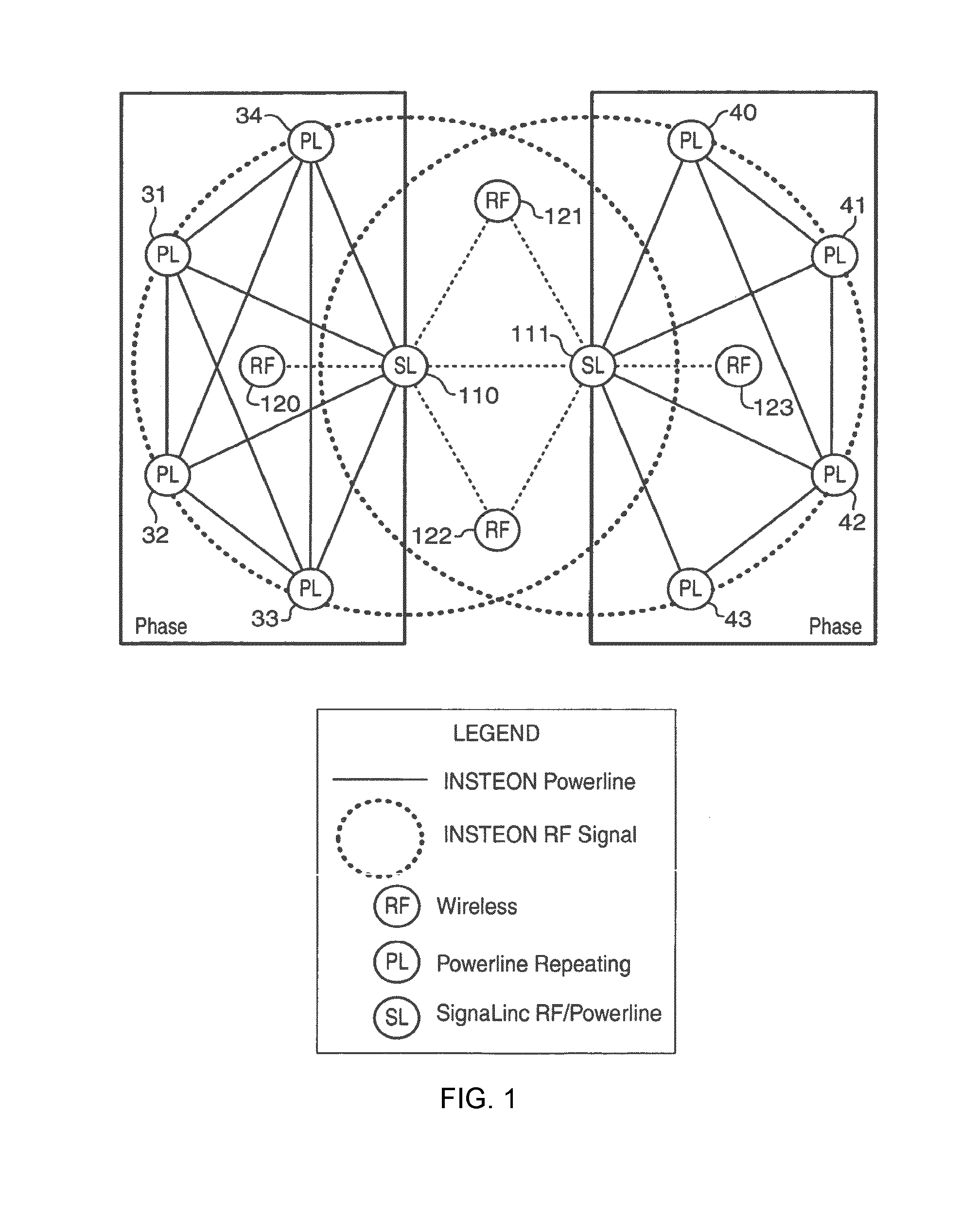
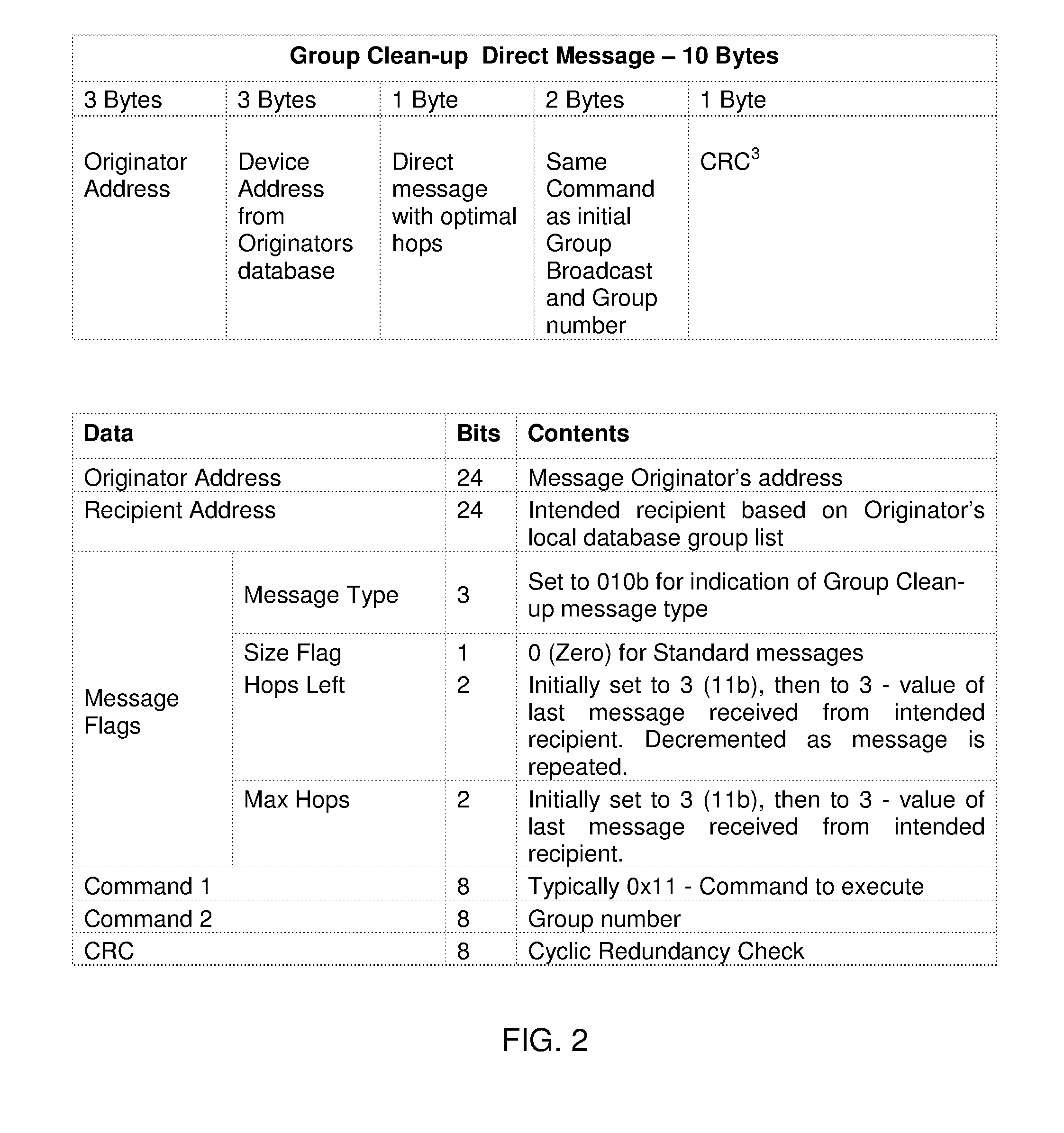
Acknowledgement as a propagation of messages in a simulcast mesh network
ActiveUS9300484B1Low costShorten the timeSpecial service provision for substationMultiple digital computer combinationsComputer hardwareMesh networking
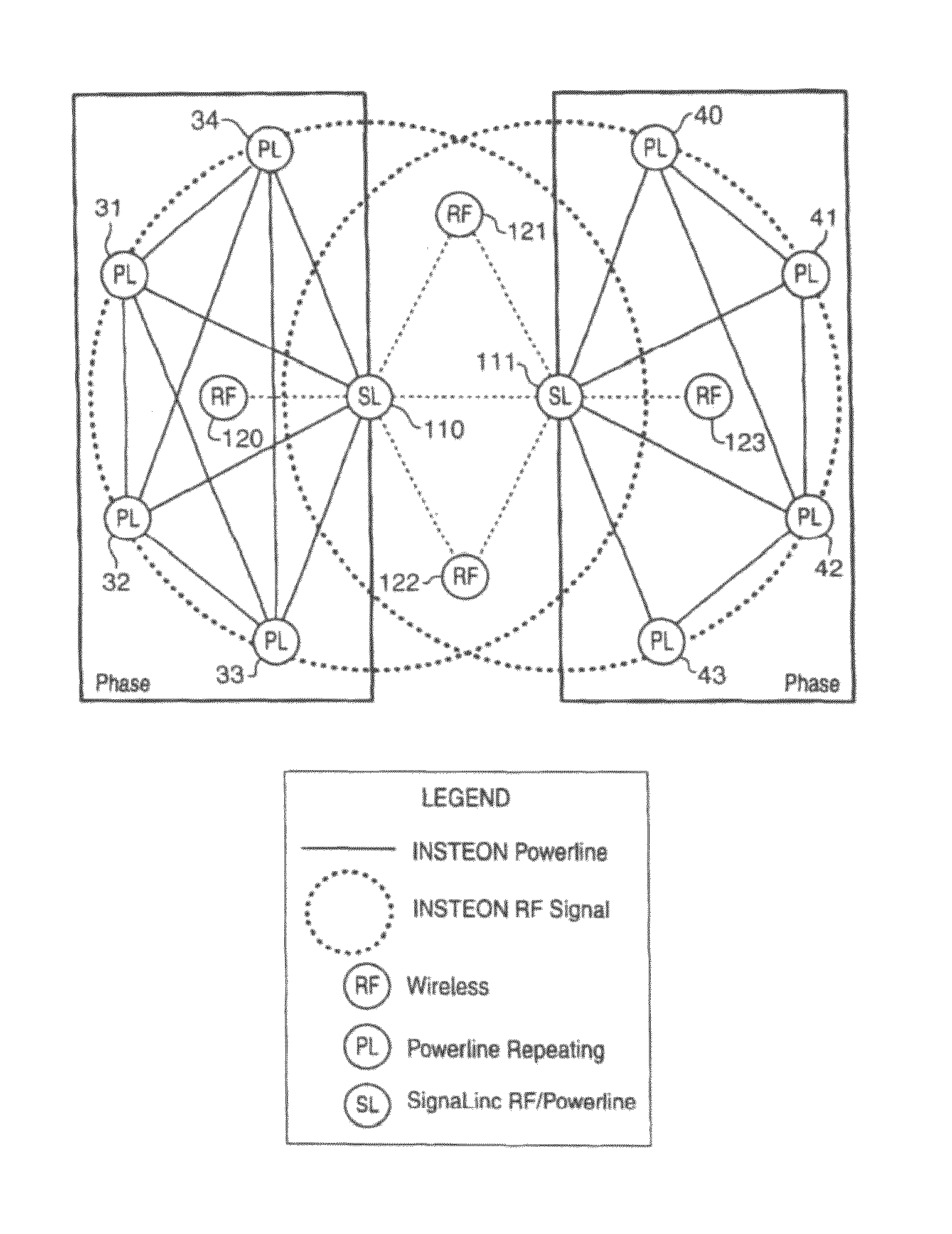
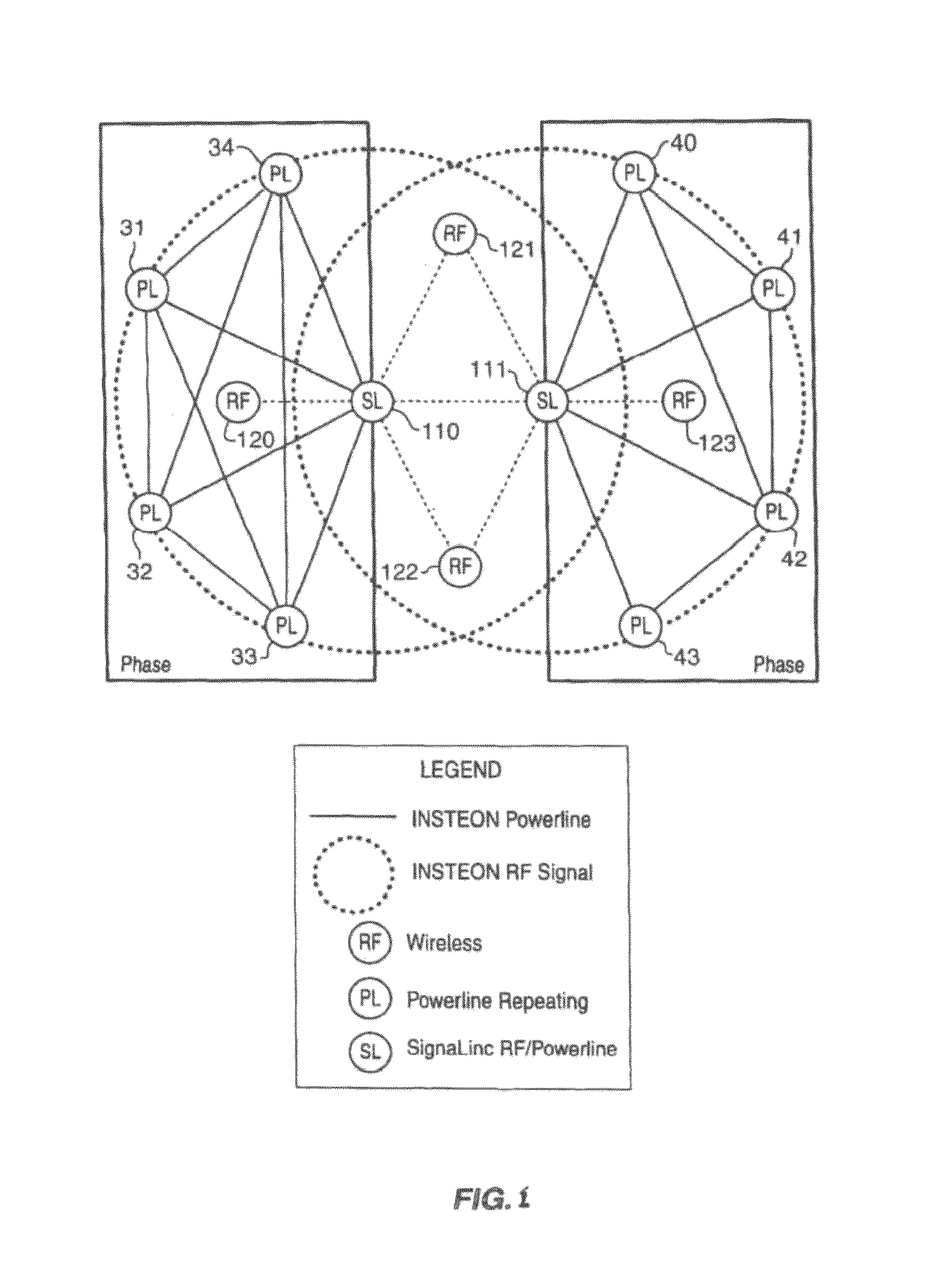
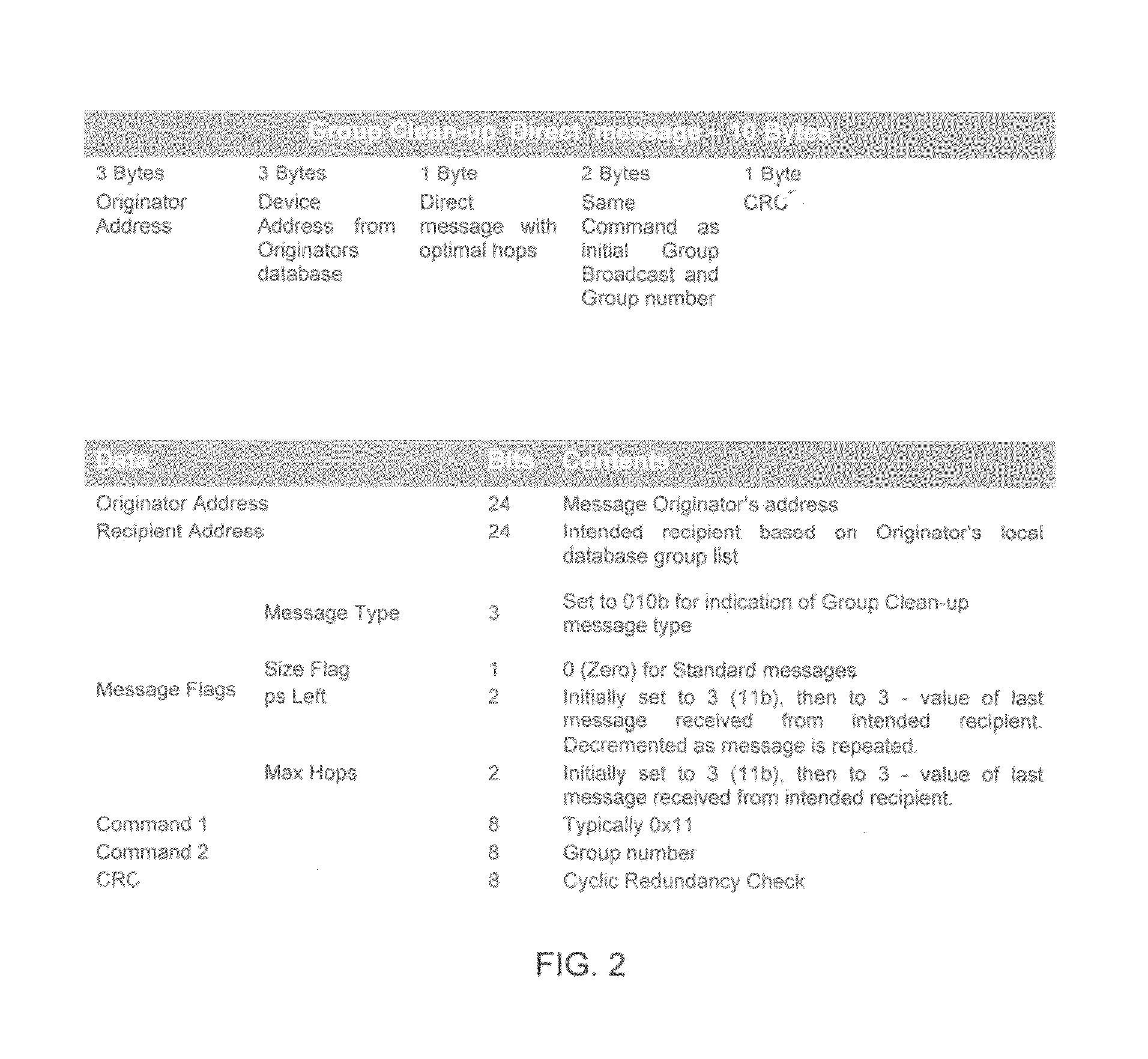
The presently described apparatus and method extends the capabilities of an Insteon network of devices. The method includes transmitting a group command message from a first device to a selected group of devices having a common group number, and receiving the group command message by a second device of the group or receiving a clean-up message transmitted by the first device, and resetting the state of the second one of the devices, and transmitting an acknowledgement message to the first devices from the second device, and receiving the first acknowledgement message by a third one of the devices that had not received the group command message or a clean-up message previously, and restoring the state of the third one of the devices.
Owner:SMARTLABS
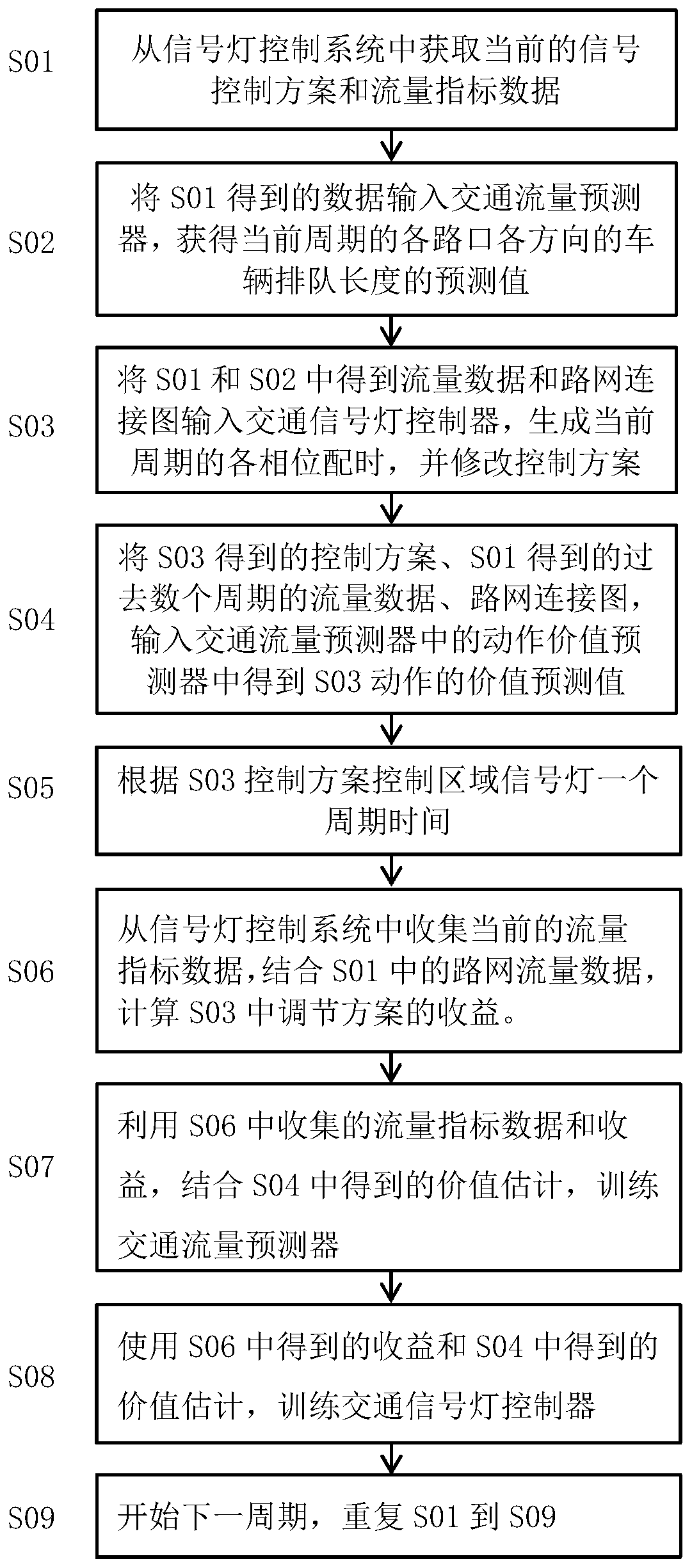
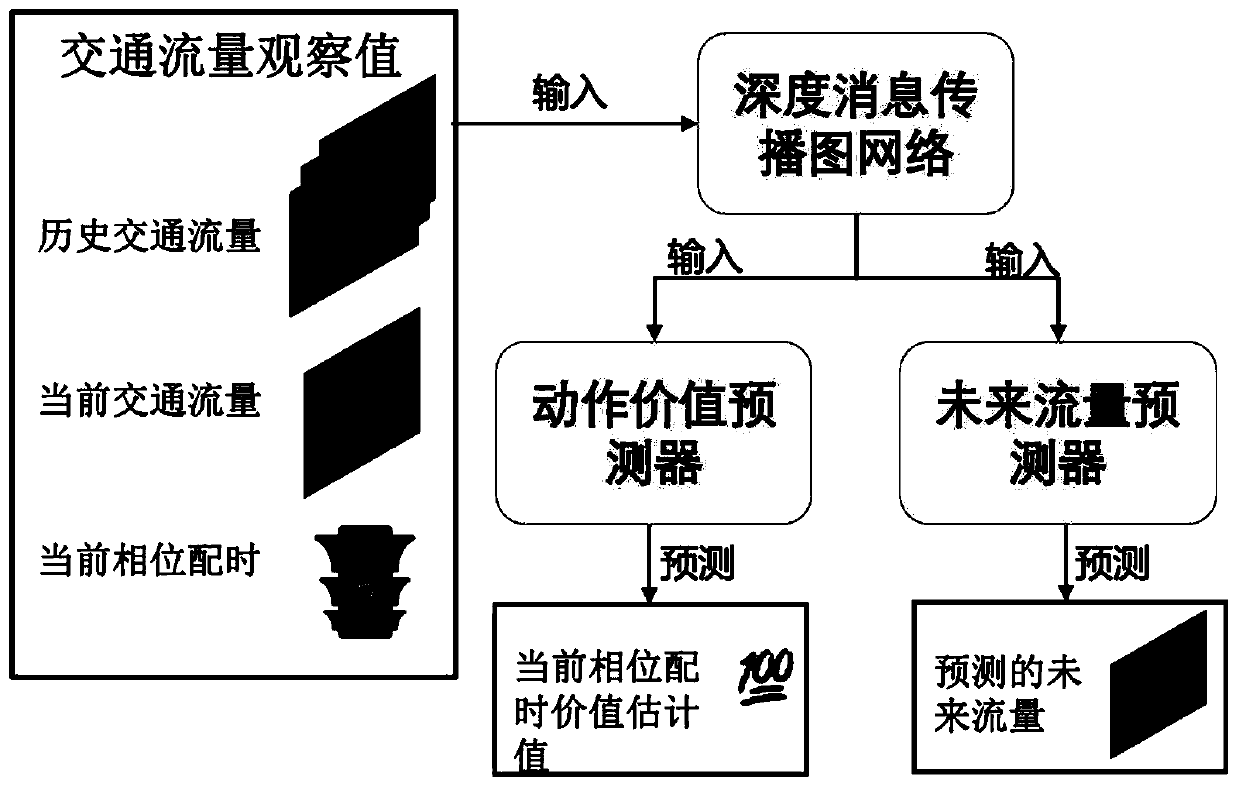
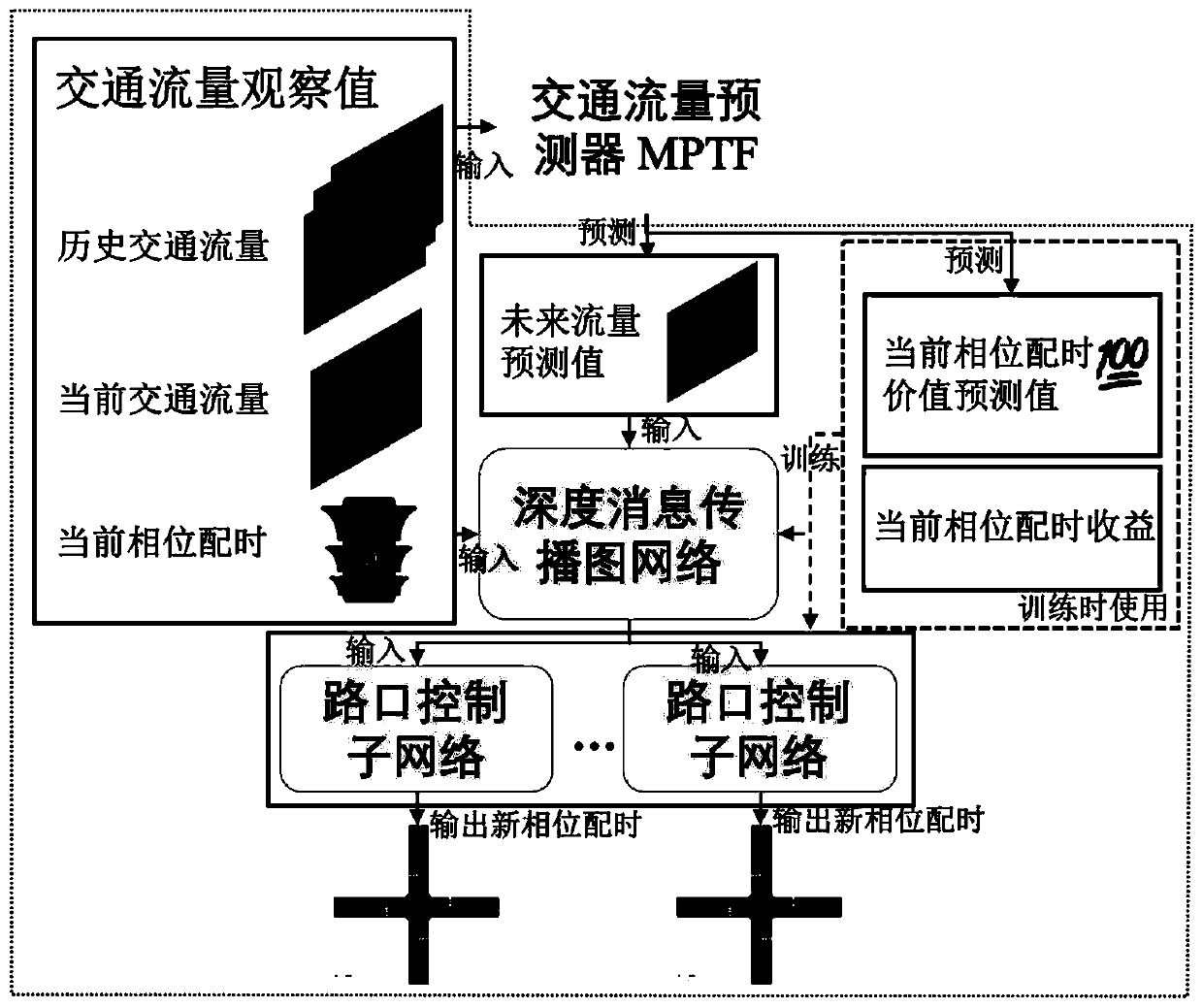
Regional traffic signal lamp control method based on graph neural network
ActiveCN110570672AImprove perceptionEasy to describeControlling traffic signalsNeural architecturesTraffic capacityTraffic signal
The invention provides a regional traffic signal lamp control method based on a graph neural network. A traffic flow predictor and a traffic signal lamp controller are trained at the same time, a future traffic flow change prediction value under a current intervention action is predicted by using the traffic flow predictor to help the traffic signal lamp controller to generate a new control scheme, the evaluation information of the traffic flow predictor to a value of the current action is used to assist in training the traffic signal lamp controller to maximize the long-term and short-term earnings of the traffic signal lamp control scheme. The traffic flow predictor and the signal lamp controller are built based on a depth message propagation graph network. According to the method, a system can be continuously optimized to adapt to changing traffic flows, and the road network smoothness degree and the traffic efficiency are improved.
Owner:ZHEJIANG UNIV
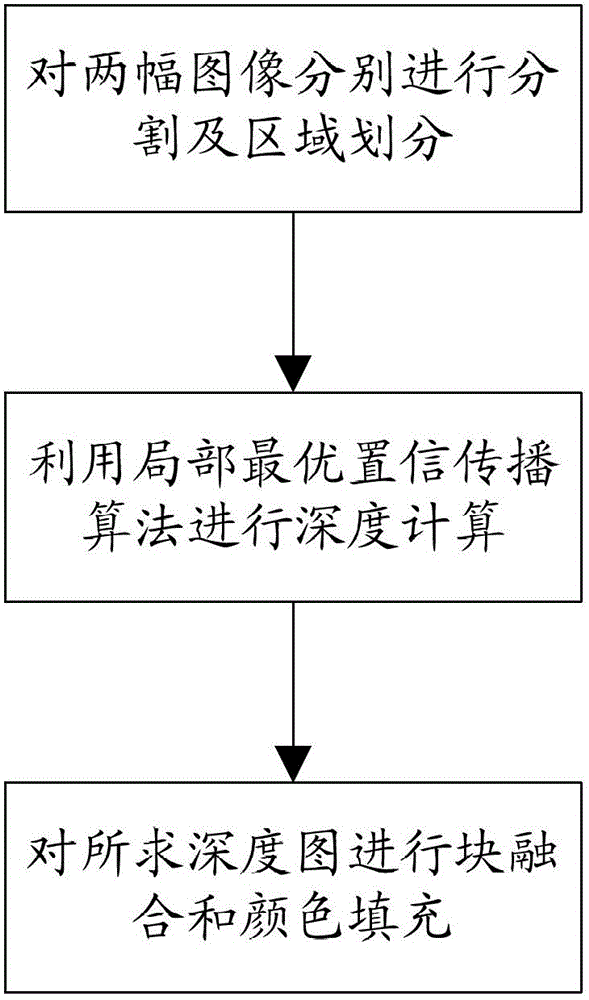
Local optimum belief propagation algorithm-based binocular video depth map solution method
ActiveCN102750694AAcquisition speed is fastSpread does not affectImage analysisParallaxPattern recognition
The invention provides a local optimum belief propagation algorithm-based binocular video depth map solution method. The method comprises the steps as follows: conducting partition and region division to two images; carrying out depth calculation by utilizing the local optimum belief propagation algorithm, processing different regions and different message values, wherein the message values are pixel visual difference information; and conducting zone fusion and color filing to the depth map. The method can conduct separate propagation in different regions by the improved belief propagation algorithm-based message propagation mode, and improve the depth map acquisition speed by changing the message propagation range and establishing the relation among the remote pixels, does not influence the propagation of a correct message by conducting separate processing to a shielded part, and greatly reduces the zone number and leads the optical parallax between zones to be more smooth by merging the small divided zones and conducting overall color filling to the object.
Owner:TSINGHUA UNIV
Microblog popularity prediction model based on time and forwarding sequence of user
ActiveCN110336700ACharacterize the dissemination processForecastingData switching networksHidden layerMicroblogging
The invention relates to a microblog popularity prediction model based on time and a forwarding sequence of a user, which belongs to the field of message popularity prediction in a social network, andcomprises the following steps of: S1, modeling the forwarding sequence of a microblog by using a recurrent neural network to capture long-distance dependence of a message propagation process; s2, performing nonlinear network transformation on an output result of the hidden layer, and learning the rate of each time step in the propagation process; and S3, utilizing the early trend acceleration andthe early popularity obtained by the rate, and predicting the future popularity of the microblog under the optimization of the user activity. According to the method, it is guaranteed that the popular trend of the microblog in the future is more accurately predicted in the early stage of message propagation, and the model not only utilizes historical propagation information, but also well describes the propagation process of the microblog.
Owner:CHONGQING UNIV
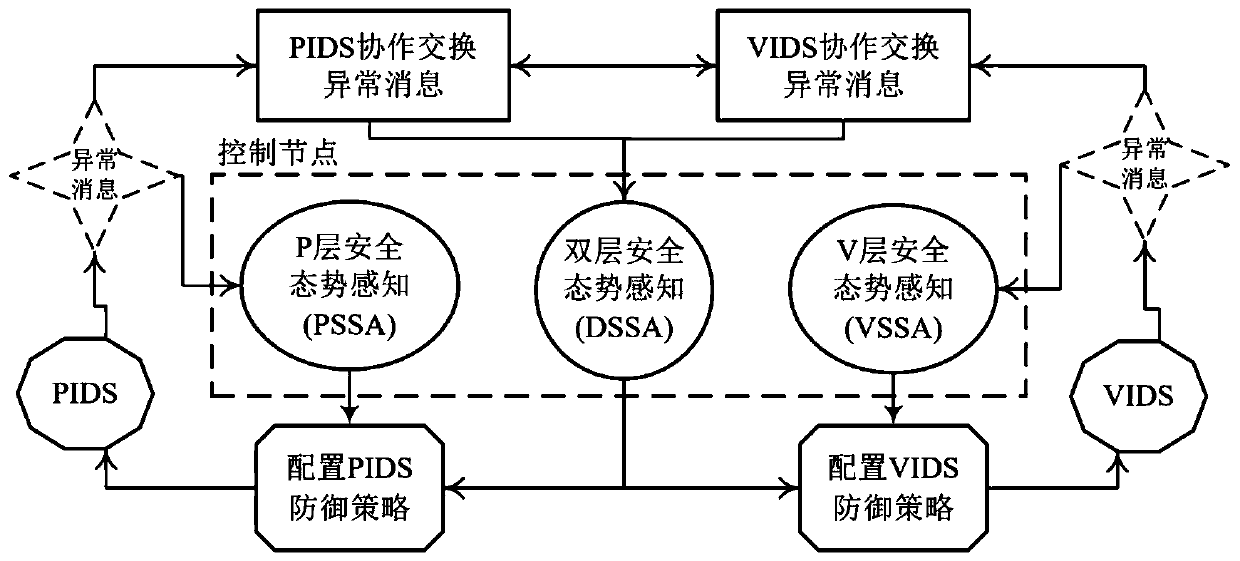
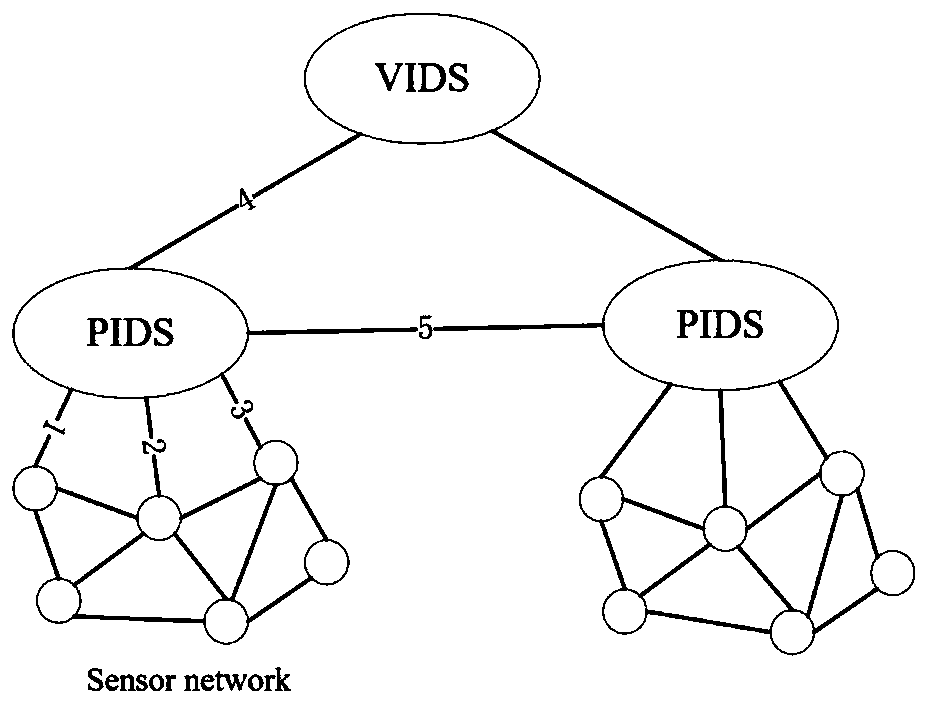
Sensing cloud double-layer network defense system and method based on security situation awareness
The invention discloses a sensing cloud double-layer network defense system and method based on security situation awareness. The system comprises a plurality of physical wireless sensor network intrusion detectors for capturing and forwarding abnormal messages, a plurality of virtual sensing service network intrusion detectors used for capturing and forwarding abnormal messages, a physical wireless sensor network security situation awareness device, a virtual sensing service network security situation awareness device and a double-layer security situation awareness device. The method comprises the following steps: in corresponding sensing time, respectively and simultaneously capturing the dynamic nature of abnormal message propagation of a physical wireless sensor network layer and a virtual sensing service network in the sensing cloud double-layer network, sensing the security situation of the physical wireless sensor network layer and the virtual sensing service network, and defending the physical wireless sensor network layer and the virtual sensing service network according to the security situation. According to the method, the abnormal message is detected through IDS cooperation, and the dynamic change trend of the abnormal message is tracked in the double-layer network, so that the attack situation of the uncertainty threat of the double-layer network is perceived.
Owner:SHAOXING UNIVERSITY
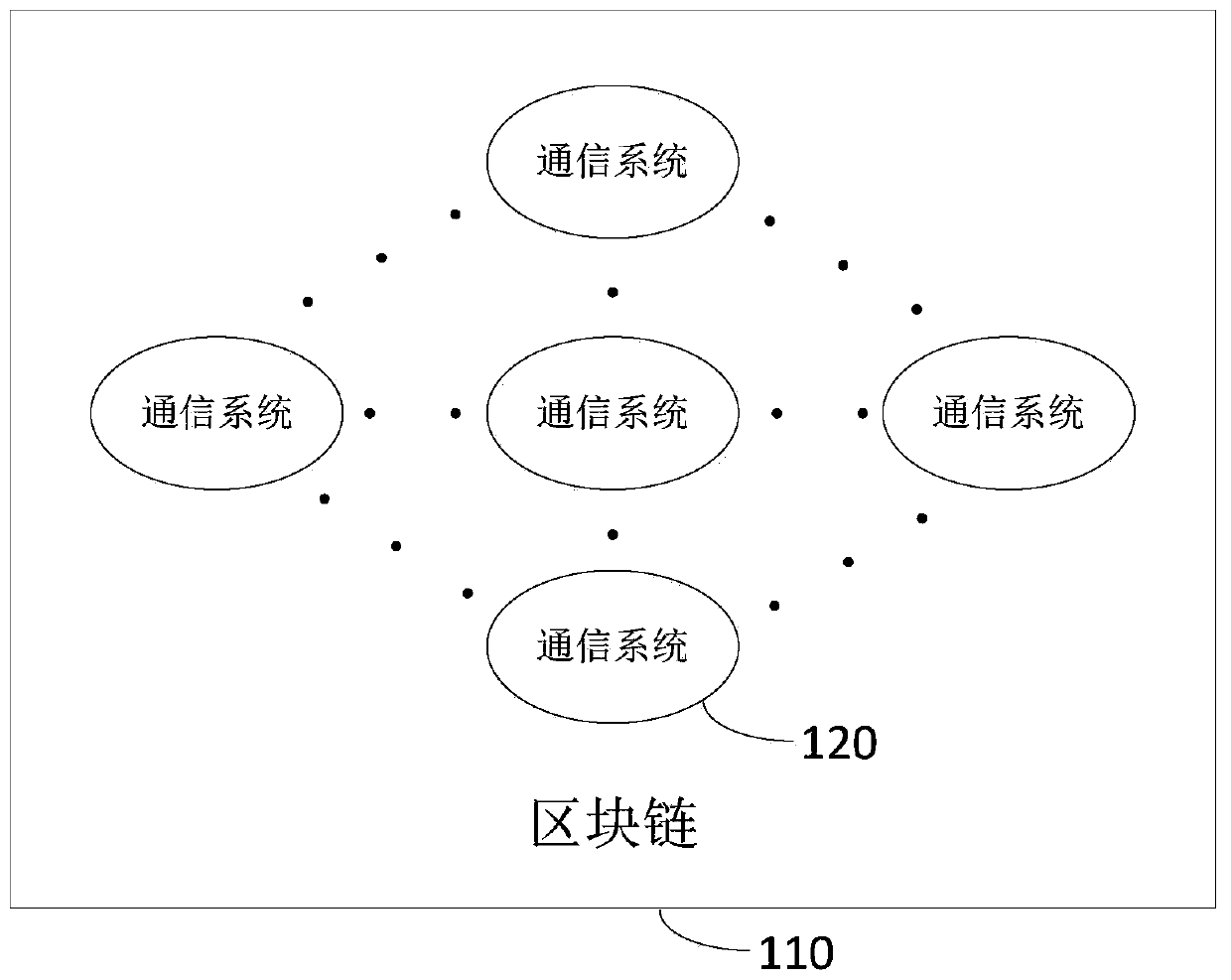
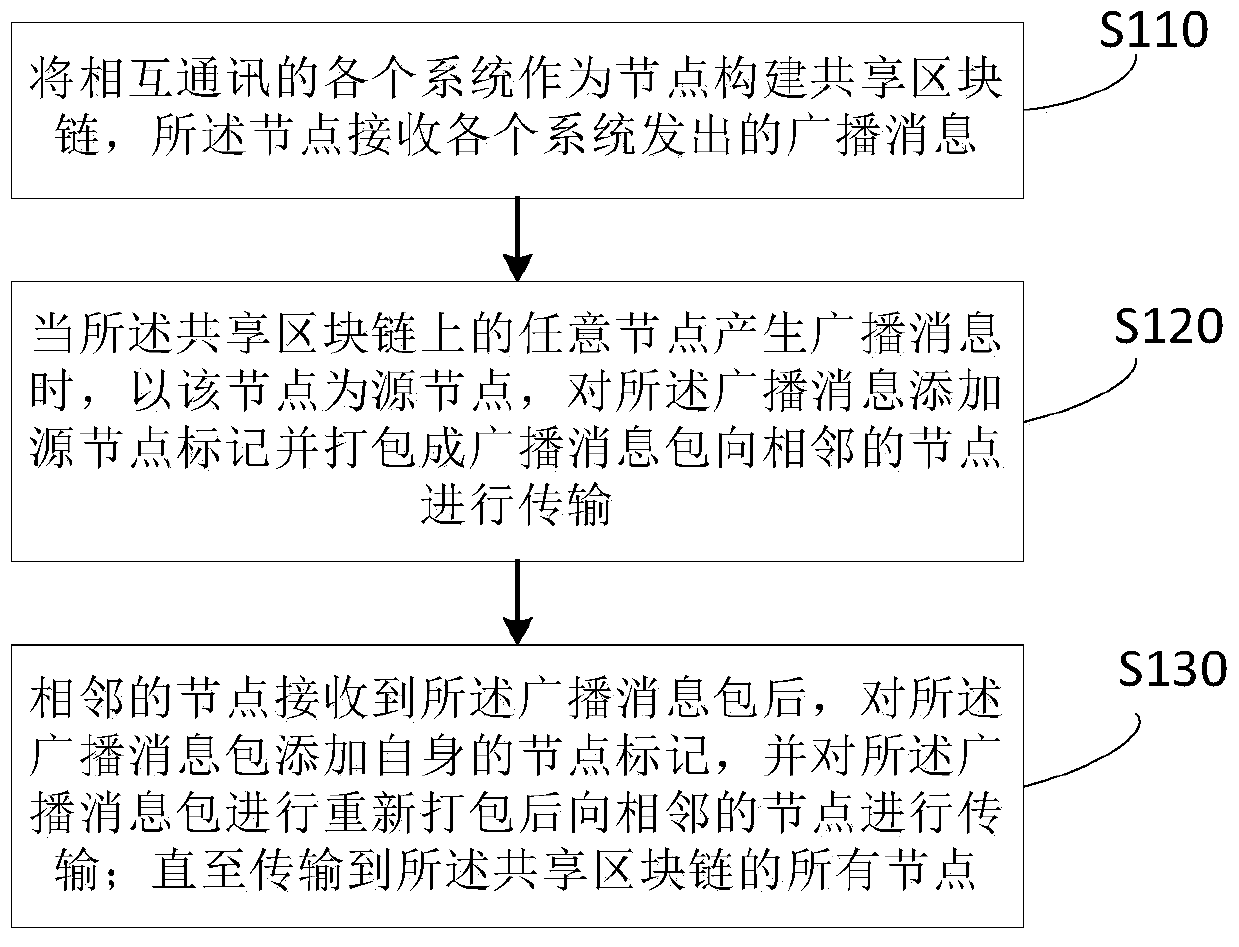
Broadcast message transmission method, device and system based on block chain technology
PendingCN110493020ASpread quicklyPrevent tamperingSpecial service provision for substationStructure of Management InformationBlock structure
The invention relates to the technical field of block structure improvement, in particular to a broadcast message transmission method and device based on a block chain technology, computer equipment and a storage medium. The method comprises the steps of all systems which communicate with one another serving as nodes to construct a shared block chain, and the nodes receiving broadcast messages sent by all the systems; when any node on the shared block chain generates a broadcast message, taking the node as a source node, adding a source node mark to the broadcast message, packaging the broadcast message into a broadcast message packet, and transmitting the broadcast message packet to an adjacent node; after receiving the broadcast message packet, the adjacent node adds a node mark of the adjacent node to the broadcast message packet, repackages the broadcast message packet and transmits the repackaged broadcast message packet to the adjacent node, until all nodes of the shared block chain are transmitted. According to the scheme, systems in mutual communication are used as nodes in the shared block chain for message propagation, and the reliability and authenticity of an information source are guaranteed while the hardware cost is reduced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
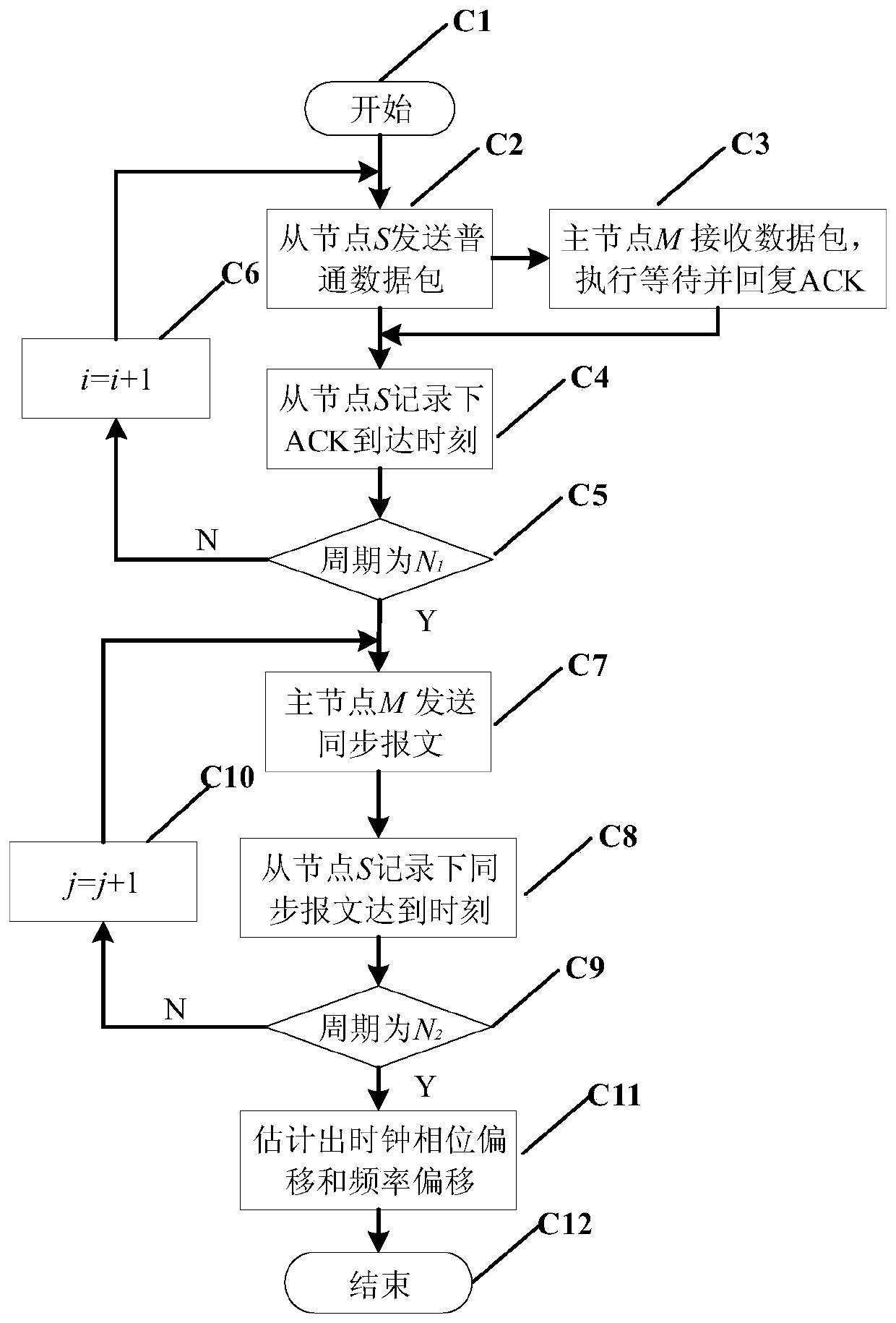
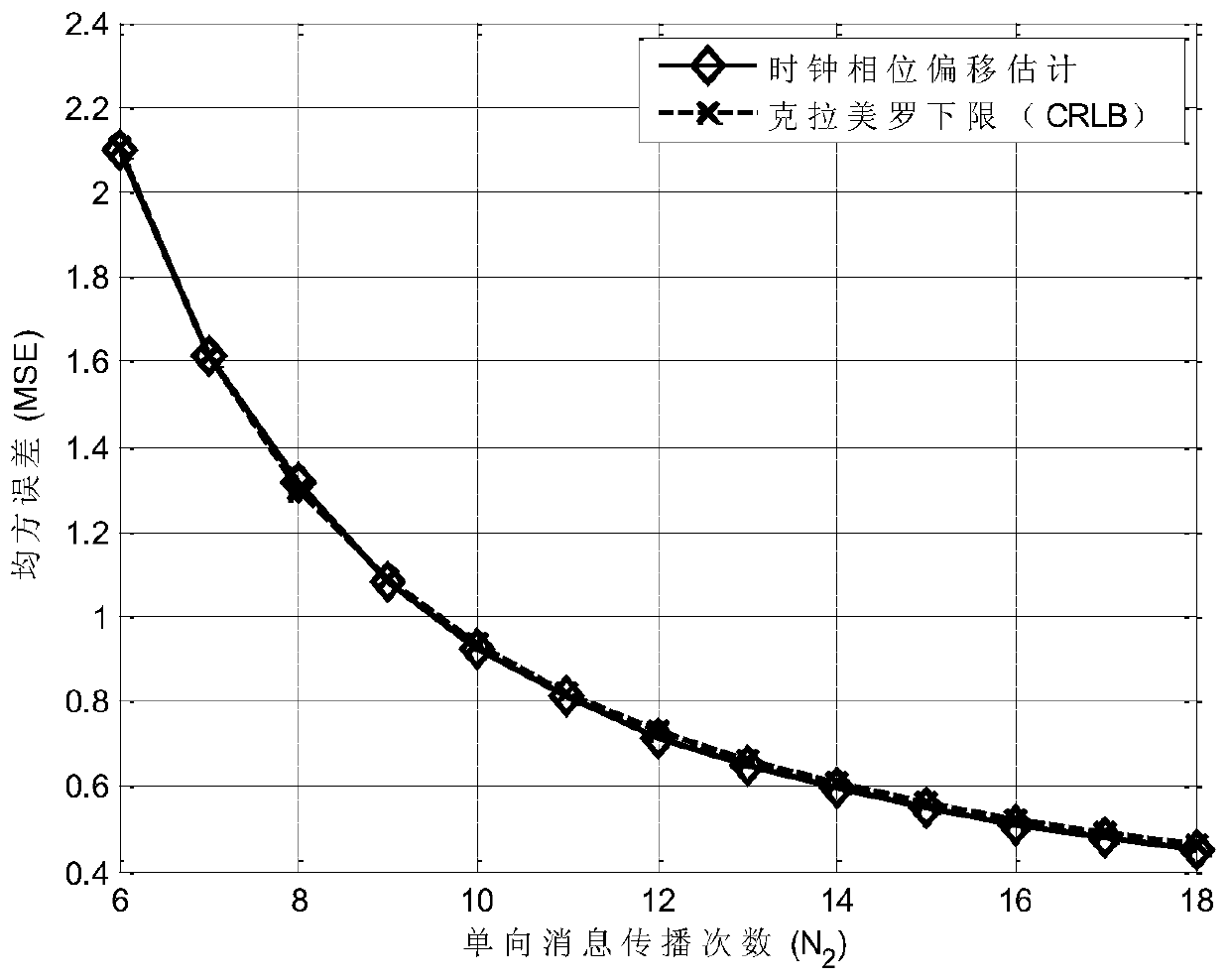
Hybrid clock synchronization method based on timestamp-free interaction and unidirectional message propagation
ActiveCN111556559AImprove estimation performanceEasy to integrateSynchronisation arrangementTime-division multiplexLine sensorData stream
The invention relates to a hybrid clock synchronization method based on timestamp-free interaction and unidirectional message propagation, and belongs to the technical field of wireless sensor networks. The method can be executed simultaneously with a broadcast mechanism according to a one-way message propagation synchronization mode. The timestamp-free interactive synchronization can implicitly acquire synchronization information in a network data stream, and the method performs joint design and optimization on a timestamp-free interactive synchronization mechanism and a unidirectional message propagation mechanism, so that seamless fusion of a time synchronization function and an actual wireless sensor network is realized. According to the method, the joint estimation of clock frequencyoffset, phase offset and fixed time delay can be realized without carrying out synchronization information transmission by a special synchronization message, the node synchronization communication overhead is effectively reduced, and the clock phase offset estimation performance is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
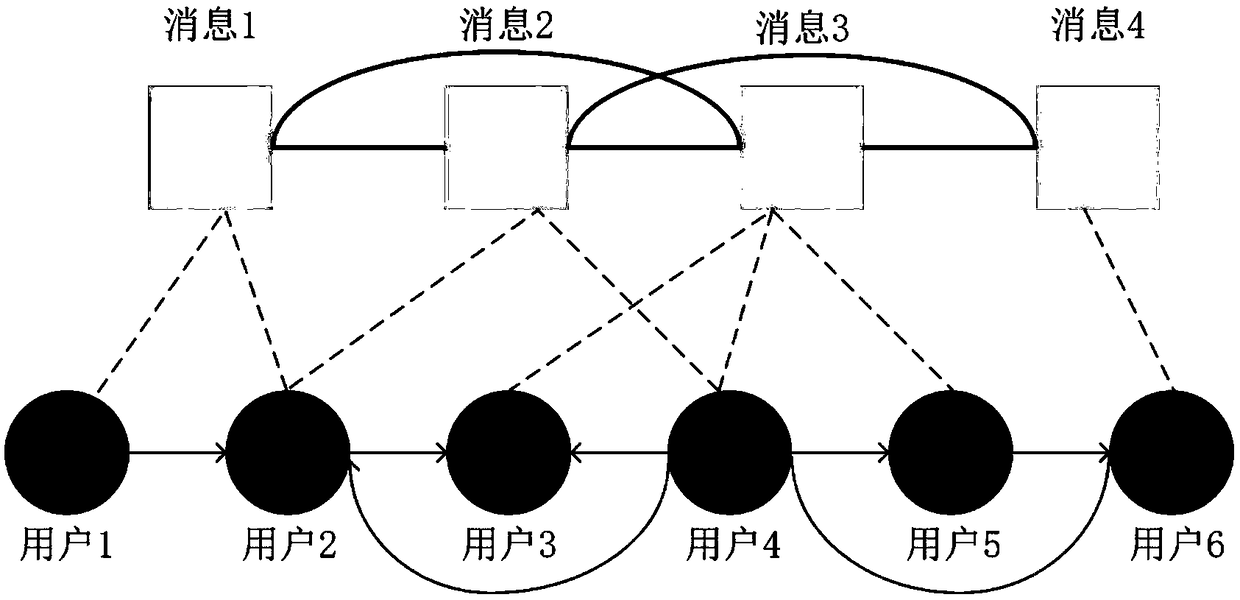
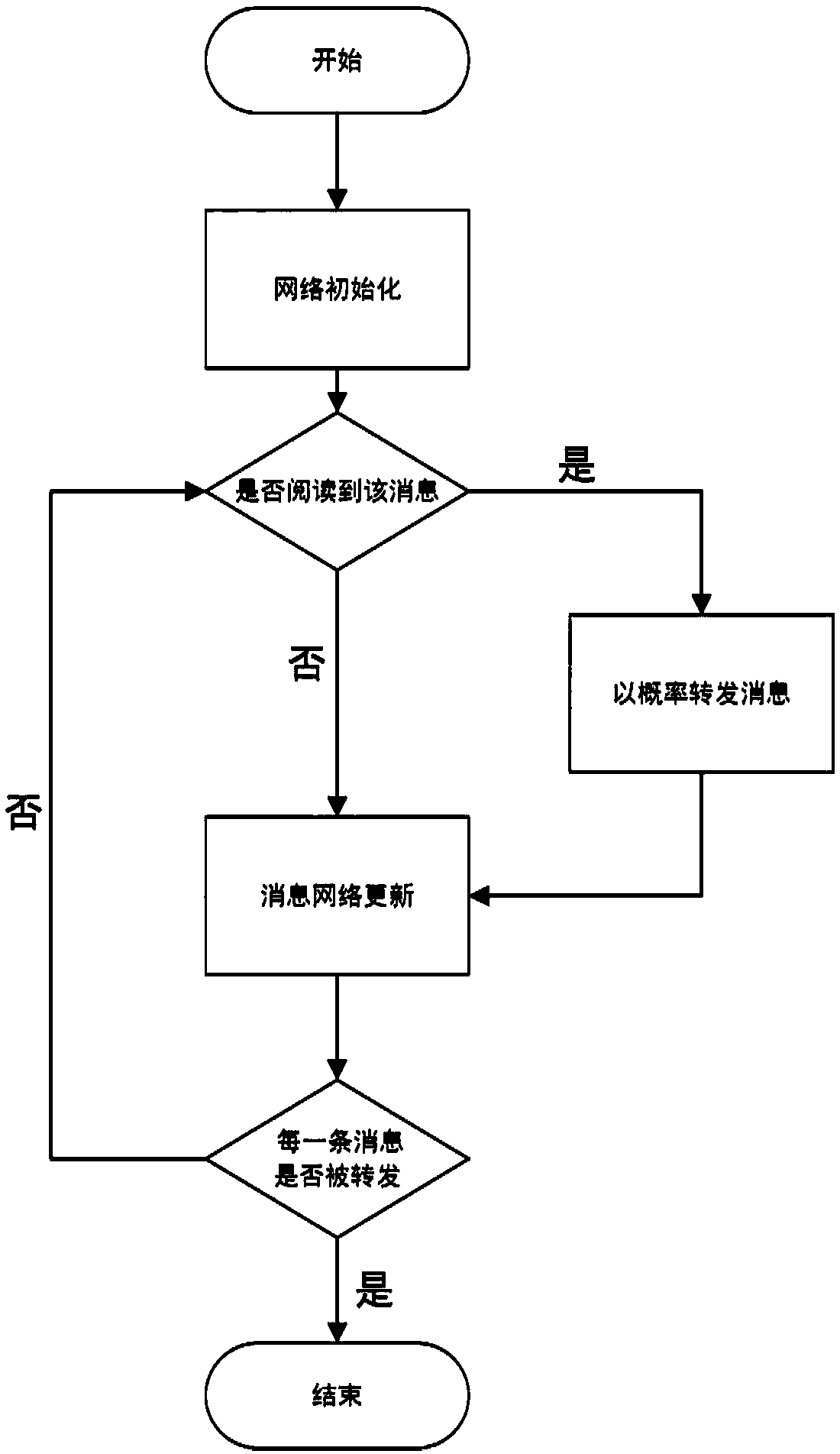
A modeling method of multi-information propagation model in social network
ActiveCN109213953AOptimize business behaviorImprove accuracyData processing applicationsWebsite content managementStable stateUltrasound attenuation
The invention discloses a modeling method of a social network multi-information propagation model. The method extends into a plurality of messages on the basis of a single message propagation model, introduces different associations among the messages and memory attenuation of users, and obtains the final evolutionary stable state of information propagation. The invention combines the mutual influence among multiple messages, and is closer to the actual situation of the common transmission of multiple messages in the social network. The present invention is socially based on message network framework models and demonstrates the phenomenon of multi-information dissemination in social networks. The invention improves the accuracy of multi-information propagation prediction in the network, and provides effective model support for different aspects such as topic prediction, public opinion control, disease control, network marketing, propaganda strategy of products or advertisements put outby a plurality of enterprises, and the like.
Owner:FUDAN UNIV
Method and system for implementing information propagating by short message
InactiveCN1719915AData processing applicationsRadio/inductive link selection arrangementsInformation transmissionTerminal equipment
A method for realizing information transmission via short messages includes 1, setting up a website for displaying the due transmitted short message contents, 2, designing at least one short message service access number, 3, users with the short message T-R end devices can actively send / forward the due transmitted short messages shown on said website via the access number to the T-R terminals held by the short message receiving party, 4, designing monitor to the sending of short messages containing due transmitted short messages via the number and user award integration based on statistic data, 5, providing user service at the website, so that, users can exchange the award selectively according to the awarding policy.
Owner:廖用铁 +2
Compound property prediction method and device, computer equipment and readable storage medium
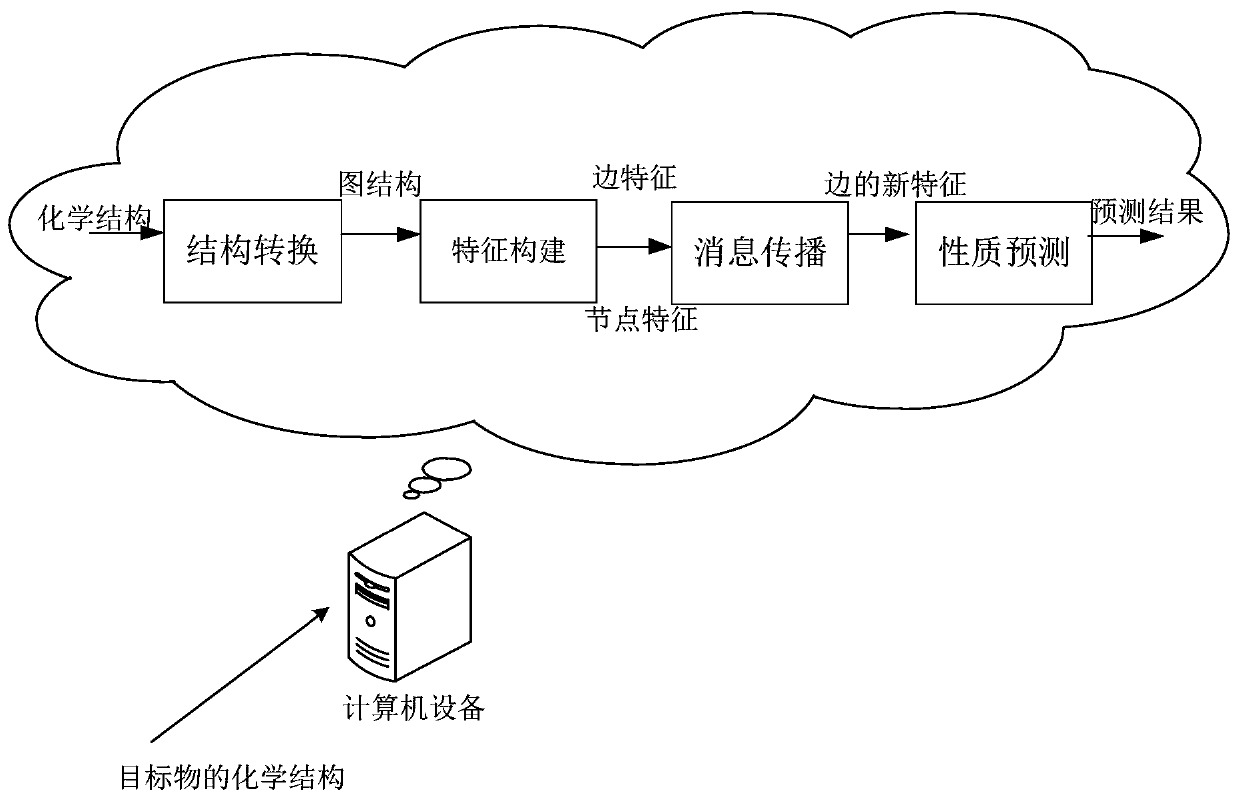
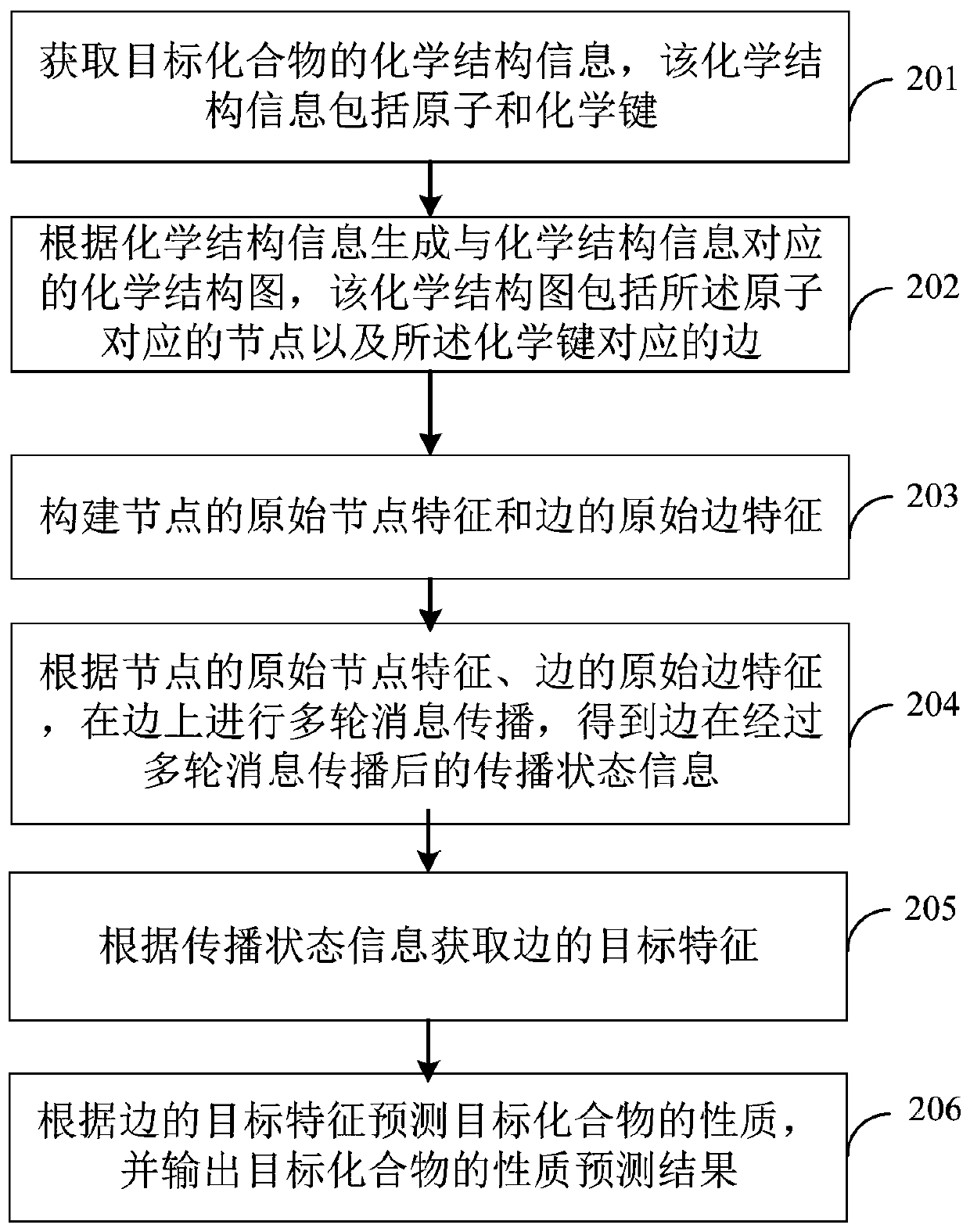
ActiveCN110767271APredictive propertiesImprove accuracyChemical property predictionMolecular designChemical structureAlgorithm
The embodiment of the invention discloses a compound property prediction method and device, computer equipment and a readable storage medium, and relates to the computer vision technology of artificial intelligence. Specifically, the method is characterized in that the chemical structure information of a target compound can be obtained, the chemical structure information comprises atoms and chemical bonds; a chemical structure diagram corresponding to the chemical structure information is generated according to the chemical structure information, and a chemical structure diagram comprises nodes corresponding to the atoms and edges corresponding to the chemical bonds; original node characteristics of the nodes and original edge characteristics of the edges are constructed; according to theoriginal node characteristics of the nodes and the original edge characteristics of the edges, multiple rounds of message propagation on the edges are performed to obtain the propagation state information of the edges after the multiple rounds of message propagation; target characteristics of the edges are obtained according to the propagation state information; the property of the target compoundis predicted according to the target characteristics of the edges, and the property prediction result of the target compound is outputted. The method is advantaged in that scientific research of thescheme greatly improves accuracy of compound property prediction.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method, device and system for managing P2P system set
ActiveCN101465753AReduce overloadReduce overheadSpecial service provision for substationData switching by path configurationStructure of Management InformationDistributed hash table
The invention discloses a P2P system group management method, a node device thereof and a system; the P2P system includes a plurality of node groups, node management groups of distributed hash table structure constructed by a node of each node group; when a node requires to joint the P2P system, the following step is executed that the node which requires to joint the P2P system adds a group management node in node management group to a message propagation destination node view PView of the node; the group management node informs nodes in the message propagation purpose node view APView in the node group; the nodes which receive notifications add the requiring node to PView of each own or refuse to add the node according to PView and capabilities of the nodes. The invention is adopted to reduce system cost, avoid nodes form having overload and realize system load balancing and improve system reliability.
Owner:CHINA MOBILE COMM GRP CO LTD
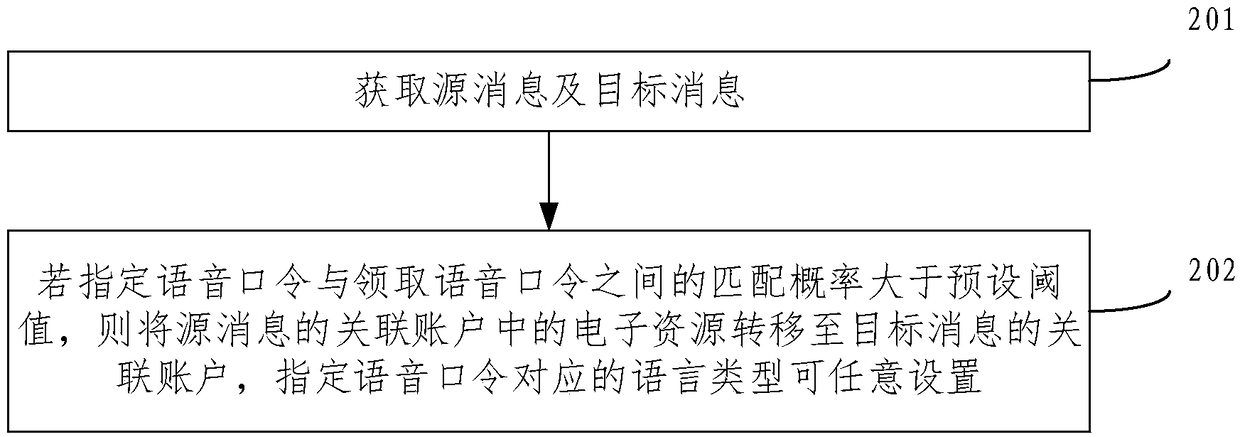
Message processing method and device
ActiveCN109003600AStrong disseminationWide spreadDiscounts/incentivesNatural language data processingComputer hardwarePassword
The embodiment of the invention provides a message processing method and device, and belongs to the technical field of computer application. The method comprises the following steps: obtaining a source message and a target message, wherein the source message includes a designated voice password, and the target message includes a getting voice password; and if the matching probability between the designated voice password and the getting voice password is greater than the preset threshold, the electronic resources in the associated account of the source message are transferred to the associatedaccount of the target message, wherein the language type corresponding to the designated voice password can be arbitrarily set. The language type corresponding to the designated voice password can bearbitrarily set, and the language used in the message processing course can be the languages of different countries and regions in addition to Mandarin so that the message processing course can be applied to different language scenes, and the message propagation power is high and the propagation range is wide.
Owner:IFLYTEK CO LTD
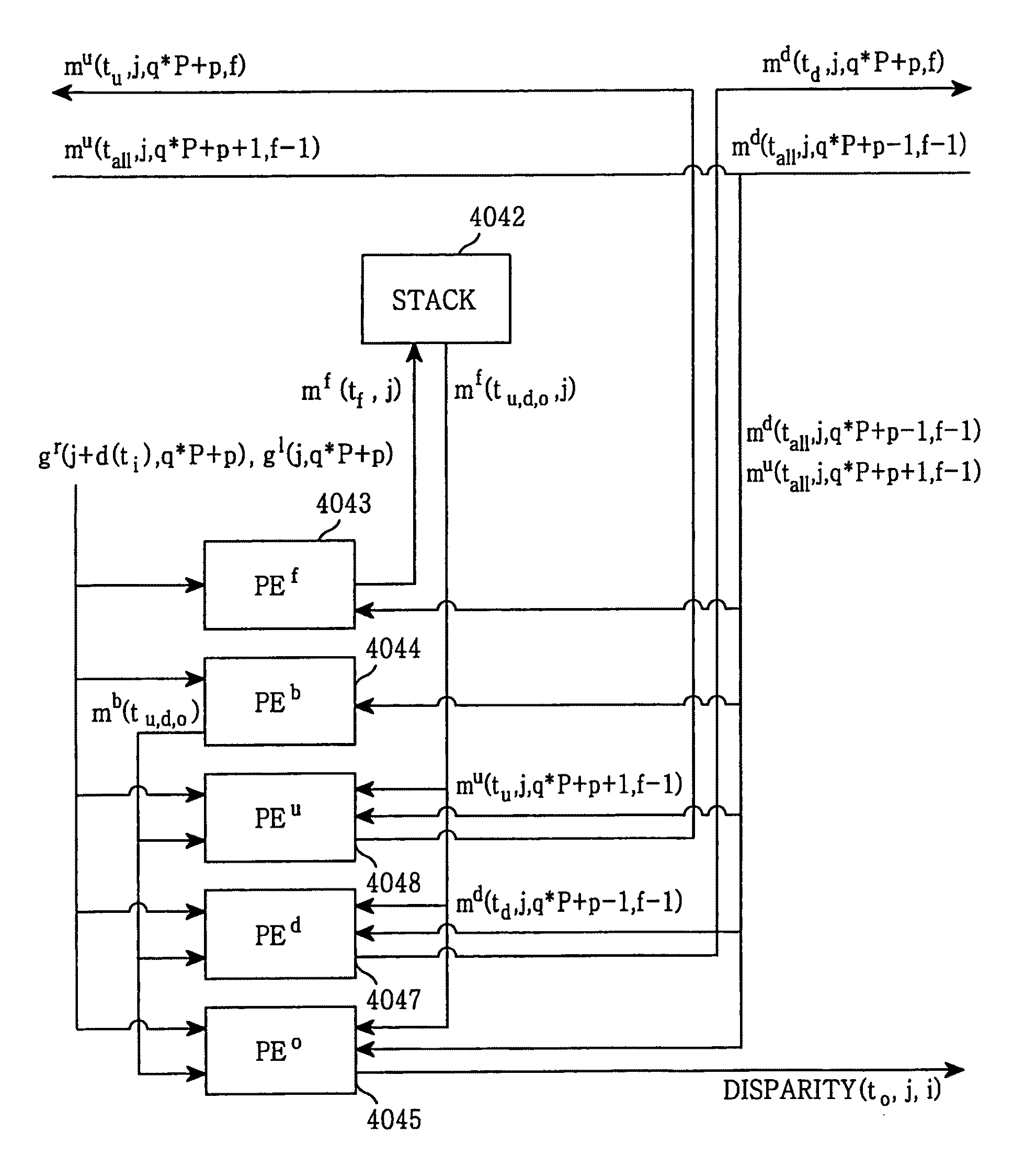
Message propagation-based stereo image matching system
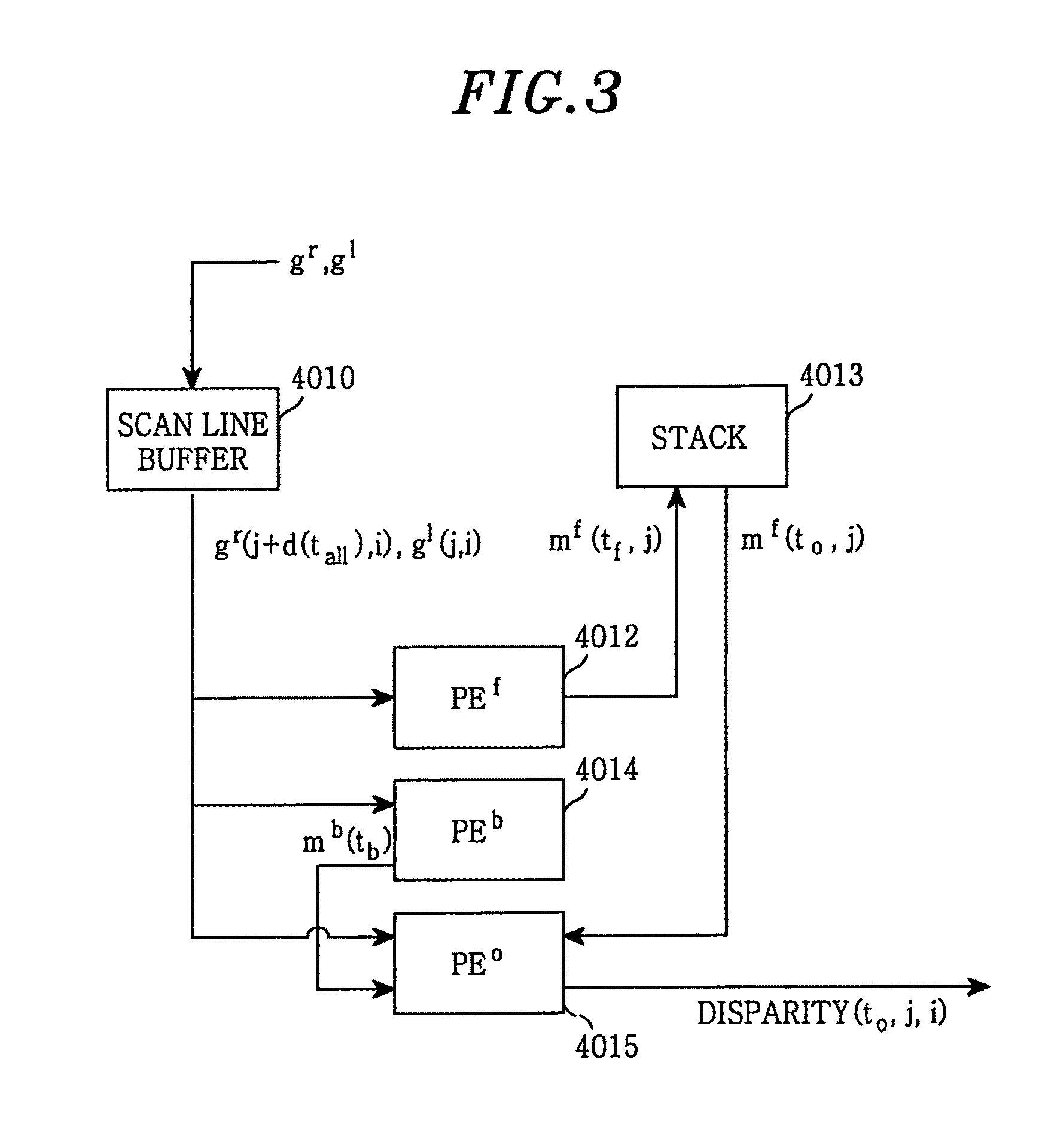
InactiveUS8427524B2Easy to implementImprove the environmentImage analysisCharacter and pattern recognitionTime complexityImage conversion
A stereo image matching system includes an image processing unit for converting input images inputted from a first and a second image acquisition unit into digital signals to output first and second pixel data; and an image matching unit for computing at least two of an upward, a downward, a forward and a backward message of each pixel by using data values of the first and the second pixel data that are located on a same epipolar line to calculate a disparity value of each pixel by using the computed messages corresponding to adjacent pixel(s). The stereo image matching system employs a parallel pipeline VLSI configuration with a time complexity of O(N). Thus, a plurality of image lines are used for matching, so that correct distance image information is obtained regardless of the conditions of the surrounding environment.
Owner:POSTECH ACAD IND FOUND
Moving path planning method for mobile data collector in wireless sensor network
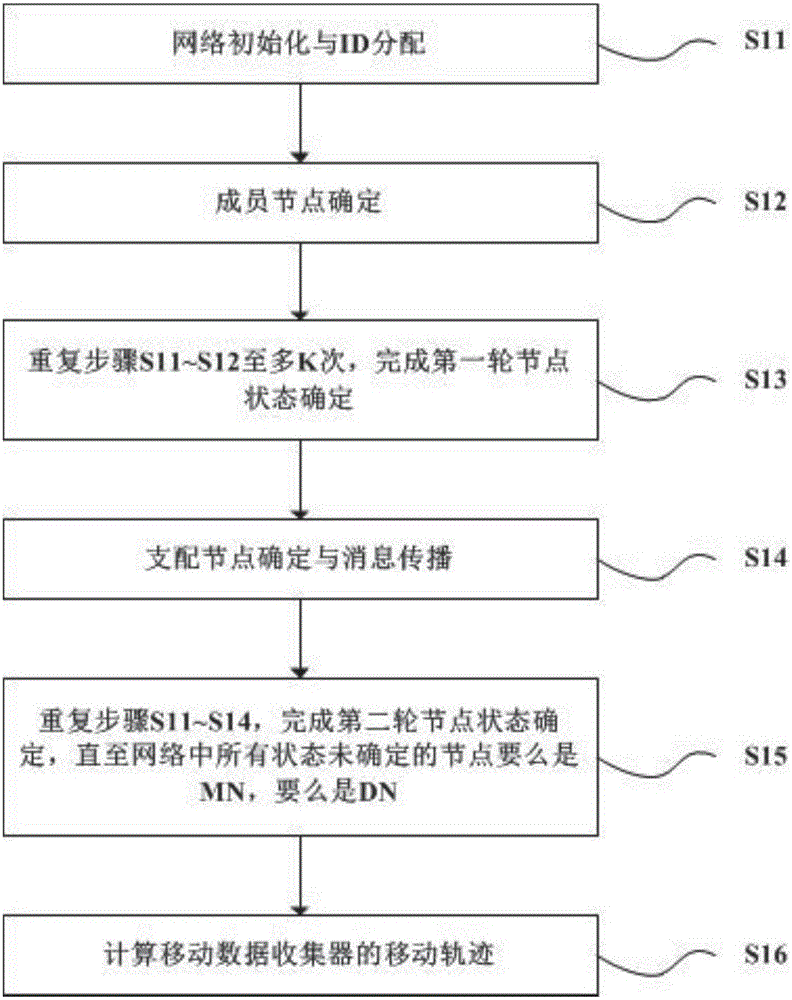
ActiveCN106658539AExtend the life cycleImplement automatic detectionNetwork topologiesNetwork planningWireless sensor networkingMobile data collector
The invention discloses a moving path planning method for a mobile data collector in a wireless sensor network. One random node in the network carries out distributed execution, and a routing hop count from the random node to a corresponding dominate node does not exceed a relay hop count k. The moving path planning method comprises the steps of: carrying out network initialization and ID allocation; determining member nodes; repeating the steps above by k times at most, and completing a first round of node state determination; carrying out dominate node determination and message propagation; repeating the steps above, and completing a second round of node state determination until all nodes in the network, of which states are not determined, are either MN or DN; and calculating a moving track of the mobile data collector. According to the moving path planning method for the mobile data collector in the wireless sensor network, which is disclosed by the invention, the hop count from one random node to the corresponding dominate node in the network does not exceed k, so that delay of data collection is reduced; by effectively regulating a load and distribution of each dominate node, a length of the moving track of the mobile data collector is effectively shortened, and delay is further promoted.
Owner:苏州砺行信息科技有限公司
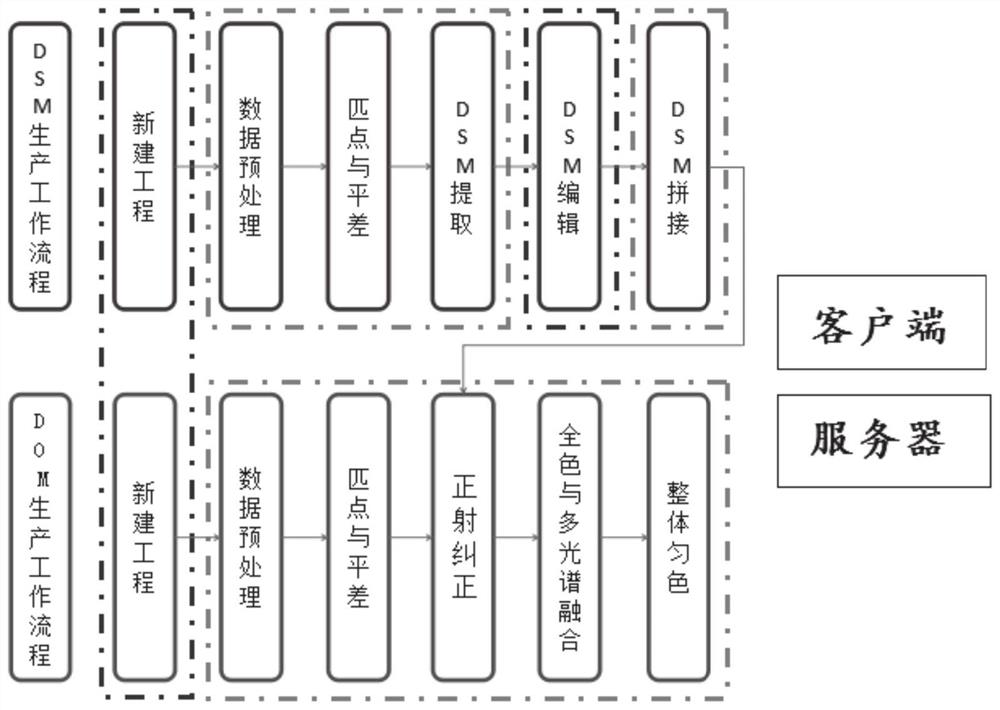
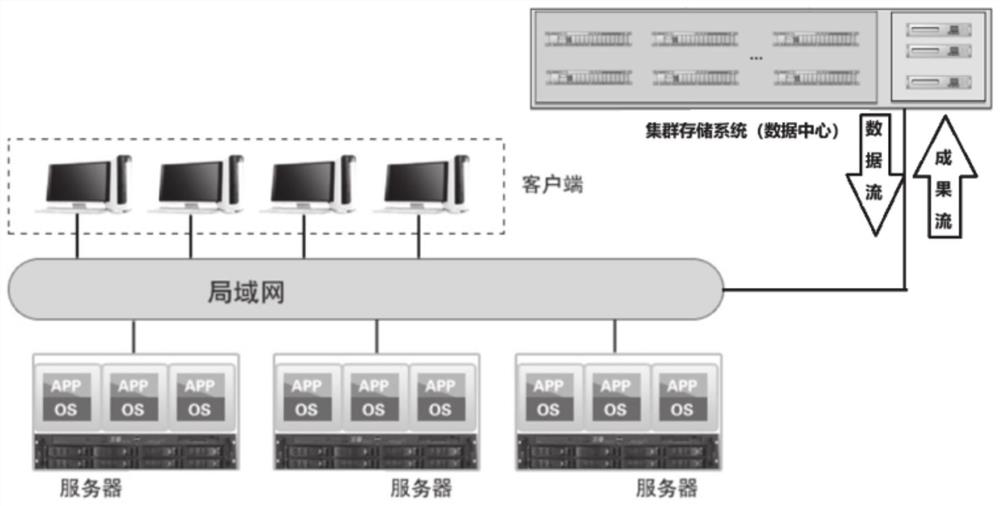
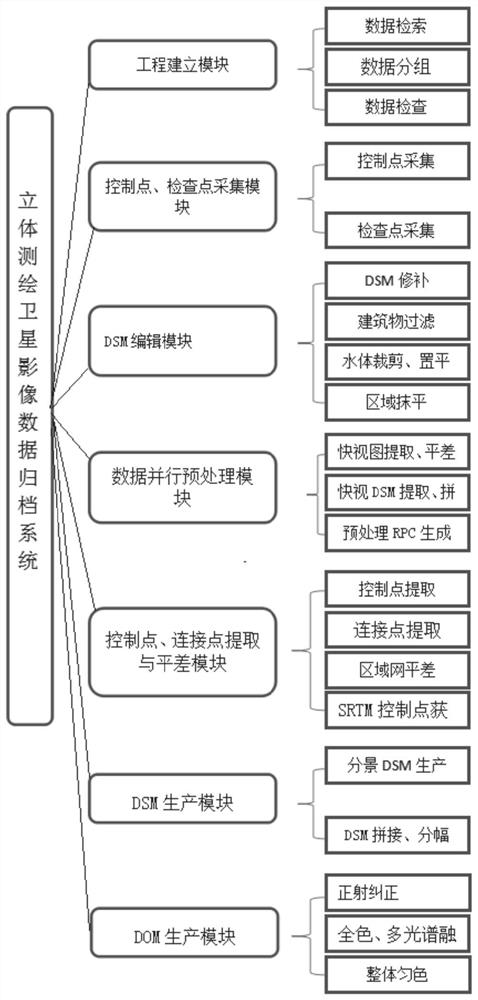
Three-dimensional surveying and mapping satellite image data archiving method and system
ActiveCN112765095AQuick searchGuaranteed redundancyImage enhancementGeometric image transformationSatellite imageDigital surface
The invention provides a three-dimensional surveying and mapping satellite image data archiving method and system. The method comprises the following steps: classifying received three-dimensional remote sensing image data; carrying out preprocessing and texture analysis on stereoscopic remote sensing image data, generating an image pyramid through wavelet transformation, transforming a top image of the pyramid, carrying out matching based on message propagation, carrying out layer-by-layer matching, and generating a digital surface model; performing radiation correction, differential correction and mosaic on the scanned stereoscopic remote sensing image data pixel by pixel by using a digital elevation model, and cutting according to a set mapsheet range to generate a digital orthoimage map; storing the generated digital surface model, the digital orthophoto map and the three-dimensional remote sensing image data; according to the input information, searching the stored data to find the corresponding data. The data storage space can be saved, the consulting path is provided, and the data processing efficiency is improved.
Owner:山东省国土测绘院
Acknowledgement as a propagation of messages in a simulcast mesh network
ActiveUS20160261538A1Low costShorten the timeSpecial service provision for substationComputer hardwareMessage propagation
The presently described apparatus and method extends the capabilities of an Insteon network of devices. The method includes transmitting a group command message from a first device to a selected group of devices having a common group number, and receiving the group command message by a second device of the group or receiving a clean-up message transmitted by the first device, and resetting the state of the second one of the devices, and transmitting an acknowledgement message to the first devices from the second device, and receiving the first acknowledgement message by a third one of the devices that had not received the group command message or a clean-up message previously, and restoring the state of the third one of the devices.
Owner:SMARTLABS
Message propagation method combining sociability of vehicles in Vehicular Ad-hoc Network
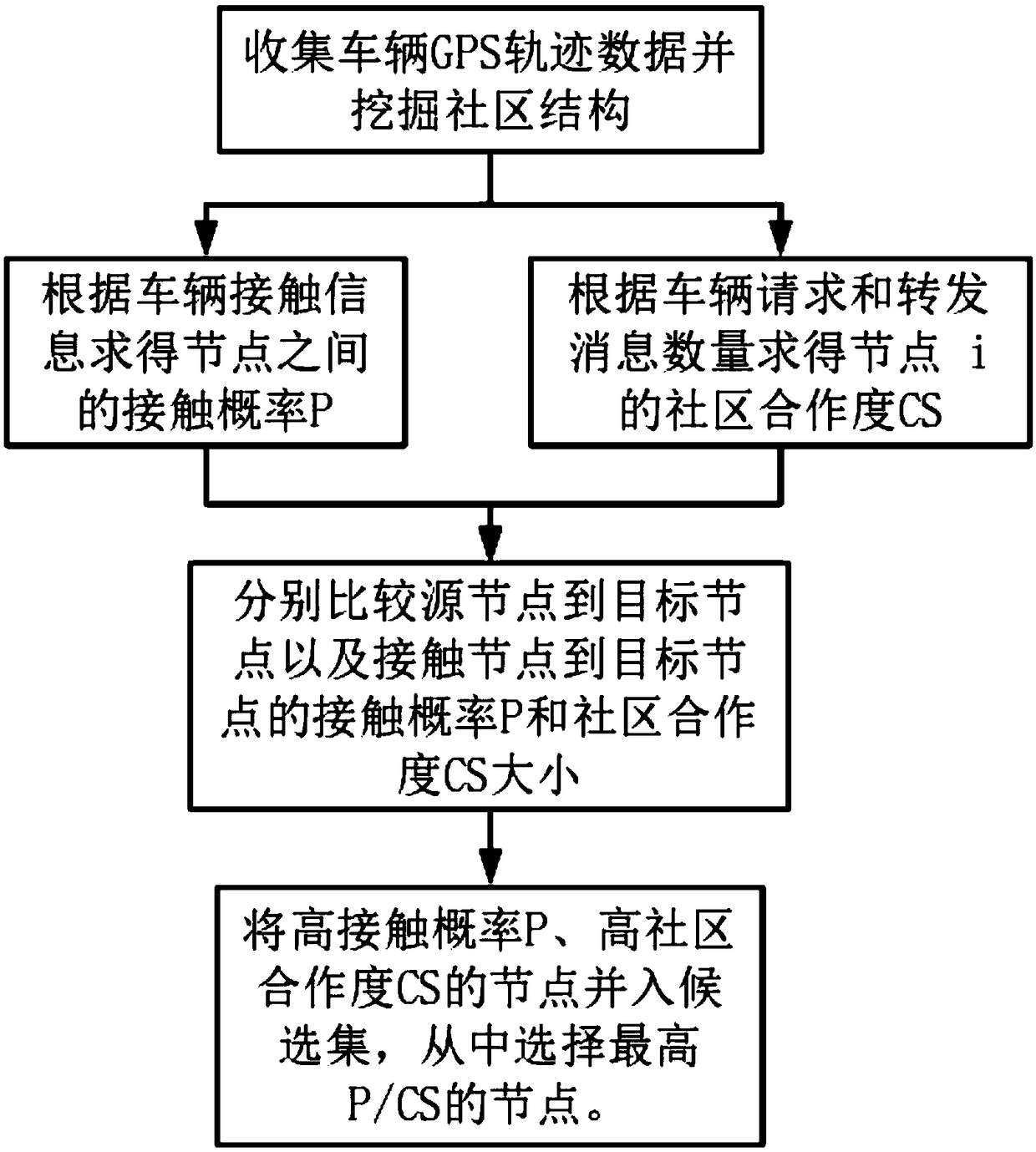
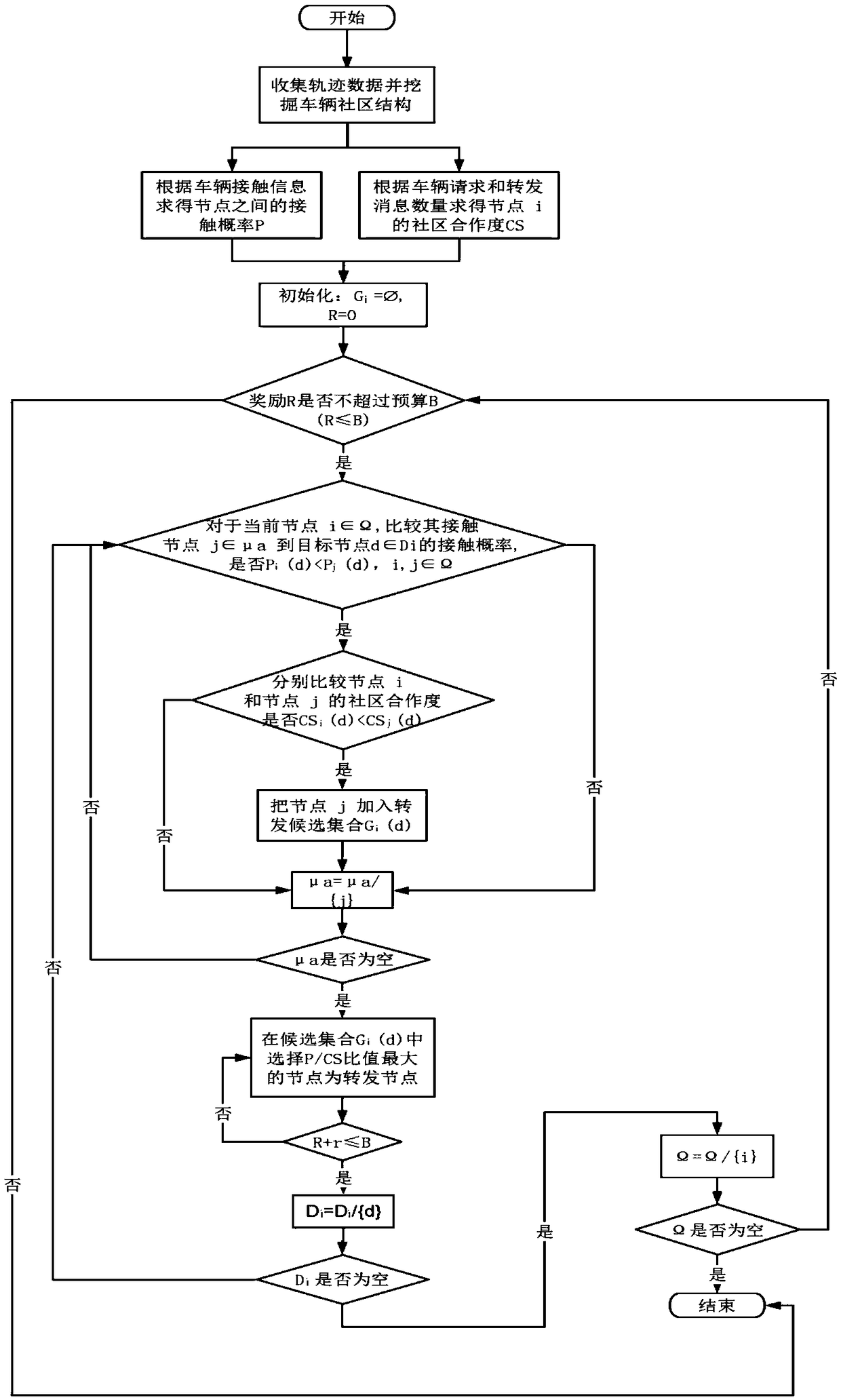
ActiveCN109327821ACause wasteRationalize message forwardingData processing applicationsParticular environment based servicesEffective solutionCommunity structure
The invention provides a message propagation method combining the sociability of vehicles in the Vehicular Ad-hoc Network. The message propagation method is characterized by comprising the steps: vehicle GPS trajectory data is collected, and a community structure is mined; the contact probabilities among nodes are solved according to vehicle contact information, and the community cooperation degrees of the nodes are obtained according to the request message numbers and forwarding message numbers of the vehicles; and the contact probability and community cooperation degree between a source nodeand a target node are compared with the contact probability and community cooperation degree between a contact node and the target node, the nodes with the high contact probability and the high community cooperation degree are added onto a candidate set, and the node with the highest contact probability to community cooperation degree ratio is selected from the candidate set to serve as a forwarding node. According to the message propagation method, the reality situation can be well simulated, an effective solution is reasonably provided for the sociability of vehicle movement, message forwarding can be more reasonable and efficient, and resource waste is avoided.
Owner:WUHAN UNIV OF SCI & TECH
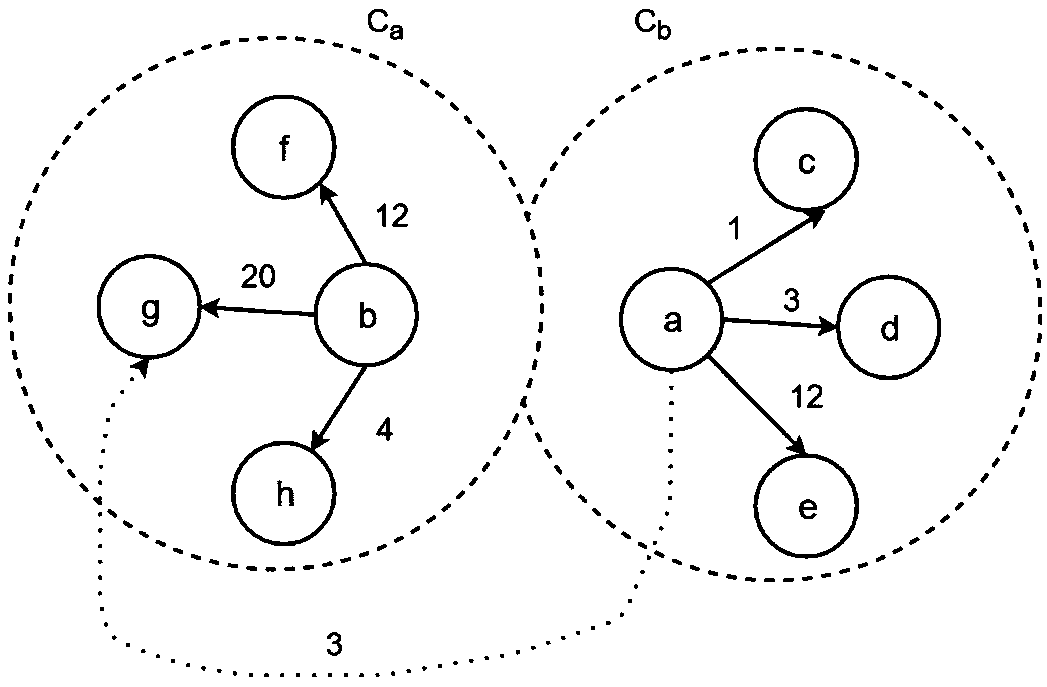
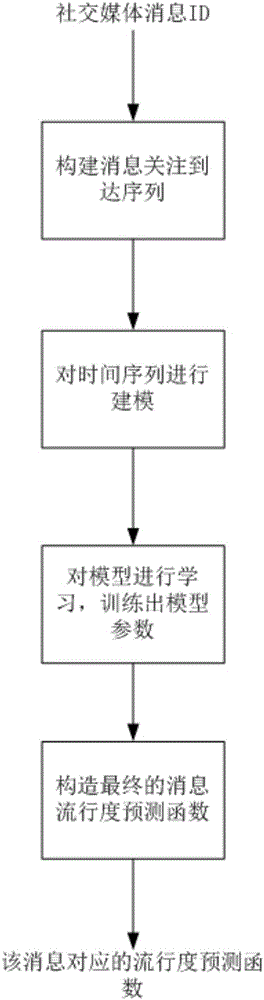
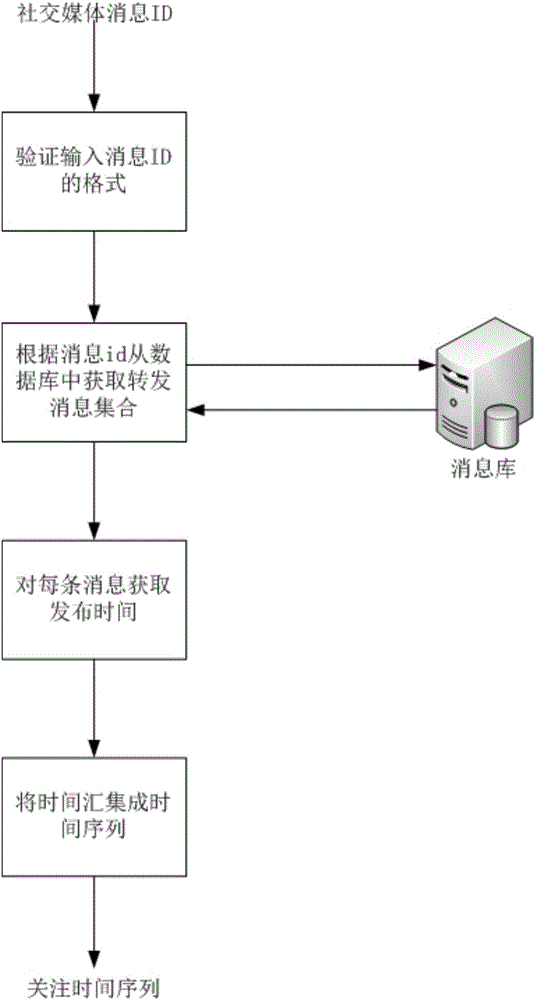
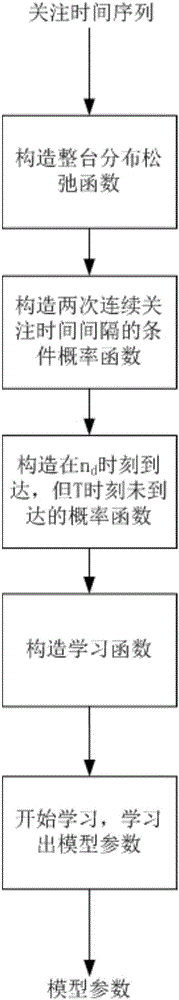
Message propagation prediction method and device based on online social relation network
The invention proposes a message propagation prediction method and device based on an online social relation network, and relates to the technical field of social media and big data. The method comprises the steps: 1, obtaining the time sequence of following behavior arrival time of users in a time period [0, T] for a message d after the sending of the message d; 2, modeling the time sequence, learning the model generated through modeling, training the parameters of the model, and obtaining a message popularity prediction function according to the model parameters. The method can avoid a data surge phenomenon. Compared with MAPE, the method is higher in accuracy, is flexible in mode, and can be used in other scenes.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
False message propagation inhibition method based on influence maximization
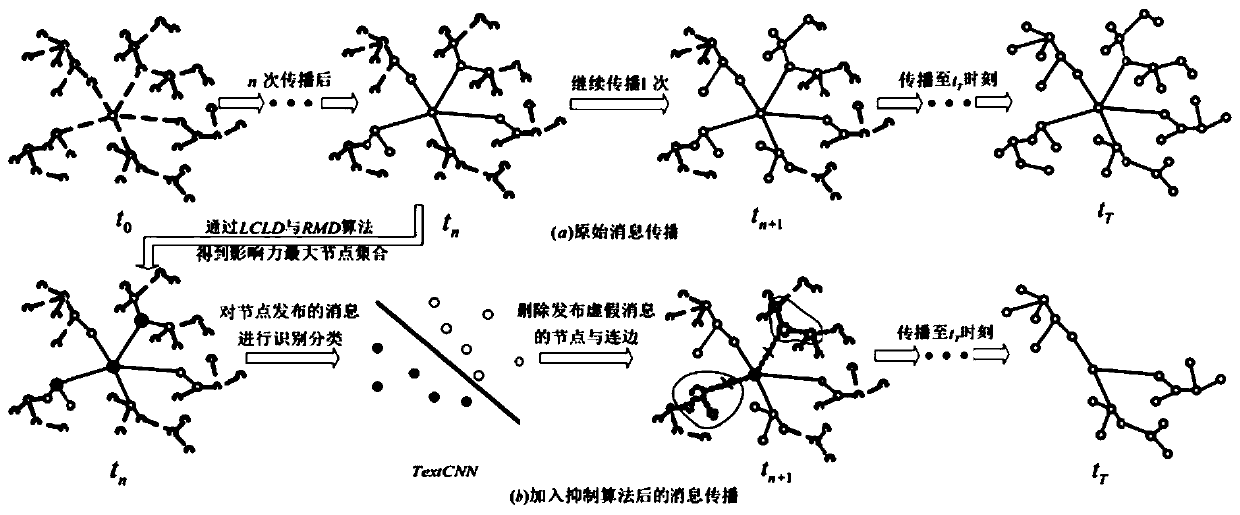
ActiveCN110990716AIncrease influenceStop the spreadData processing applicationsDigital data information retrievalAlgorithmTheoretical computer science
The invention discloses a false message propagation inhibition method based on influence maximization. The method comprises the steps: (1) carrying out the processing of a propagated information flowthrough employing a Louvain clustering locality centrality algorithm LCLD or a maximum random node degree algorithm RMD, and obtaining a node set with the maximum influence; (2) converting messages published by node users in the node set into three-dimensional word vectors by using Word2Vec, identifying and classifying the obtained word vectors by using a TextCnn network, and distinguishing real message nodes from false message nodes; and (3) filtering the nodes publishing the false messages in the node set. By utilizing the method for inhibiting the propagation of the false message, the falseuser node with the maximum influence can be automatically searched and deleted, so that the influence generated by releasing the false message node is inhibited.
Owner:ZHEJIANG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com