Patents
Literature
52 results about "Security policy database" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
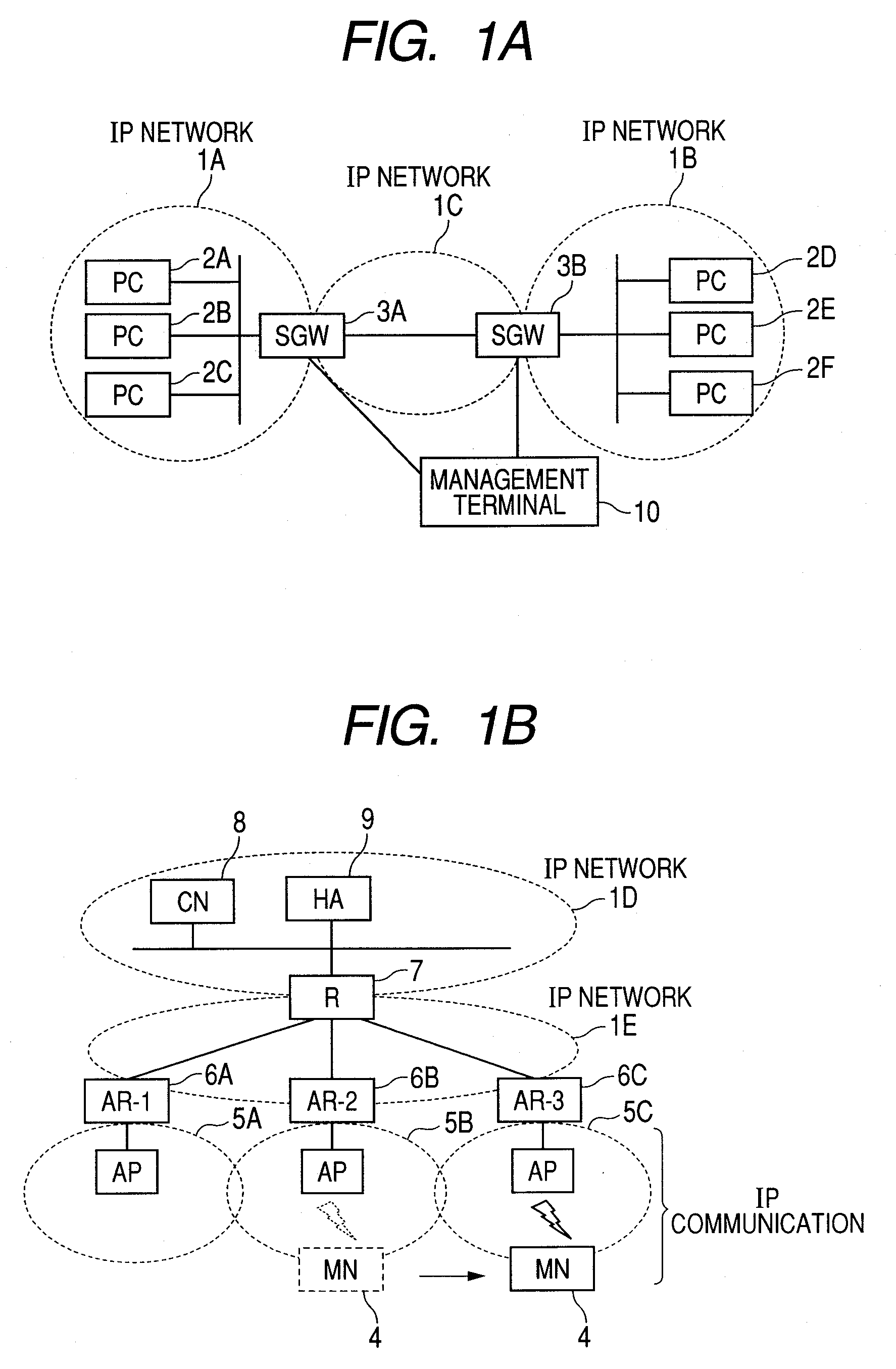
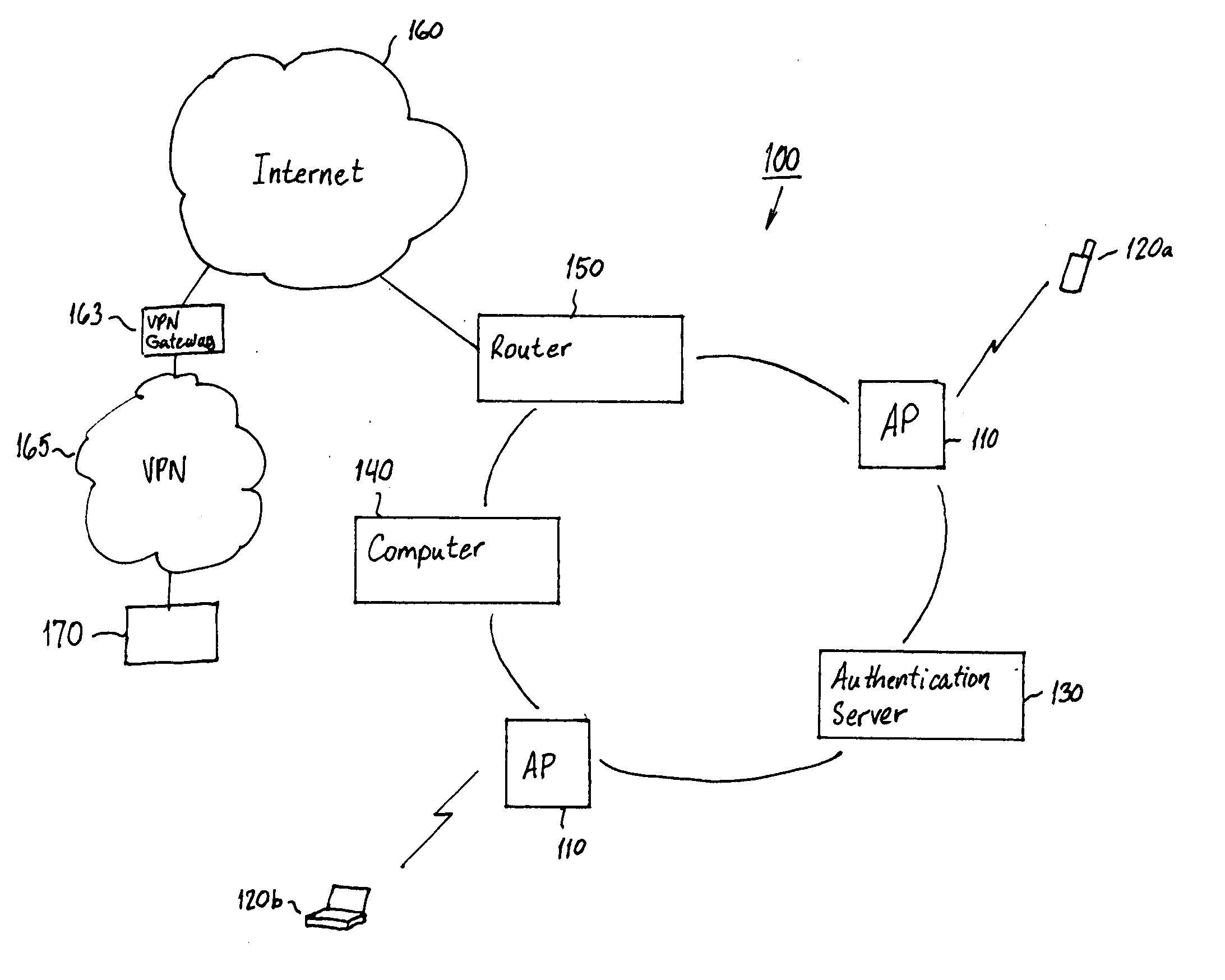
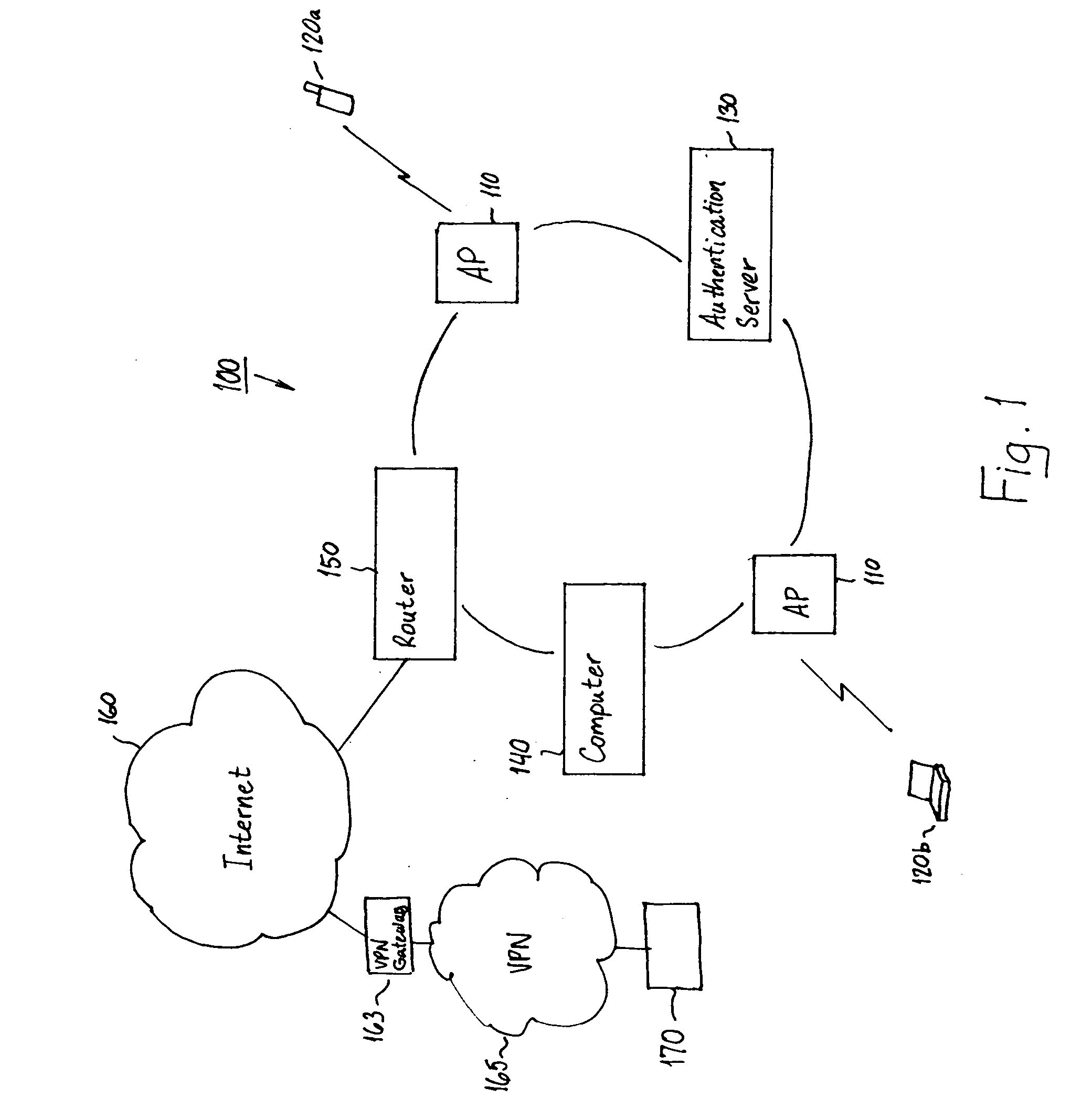
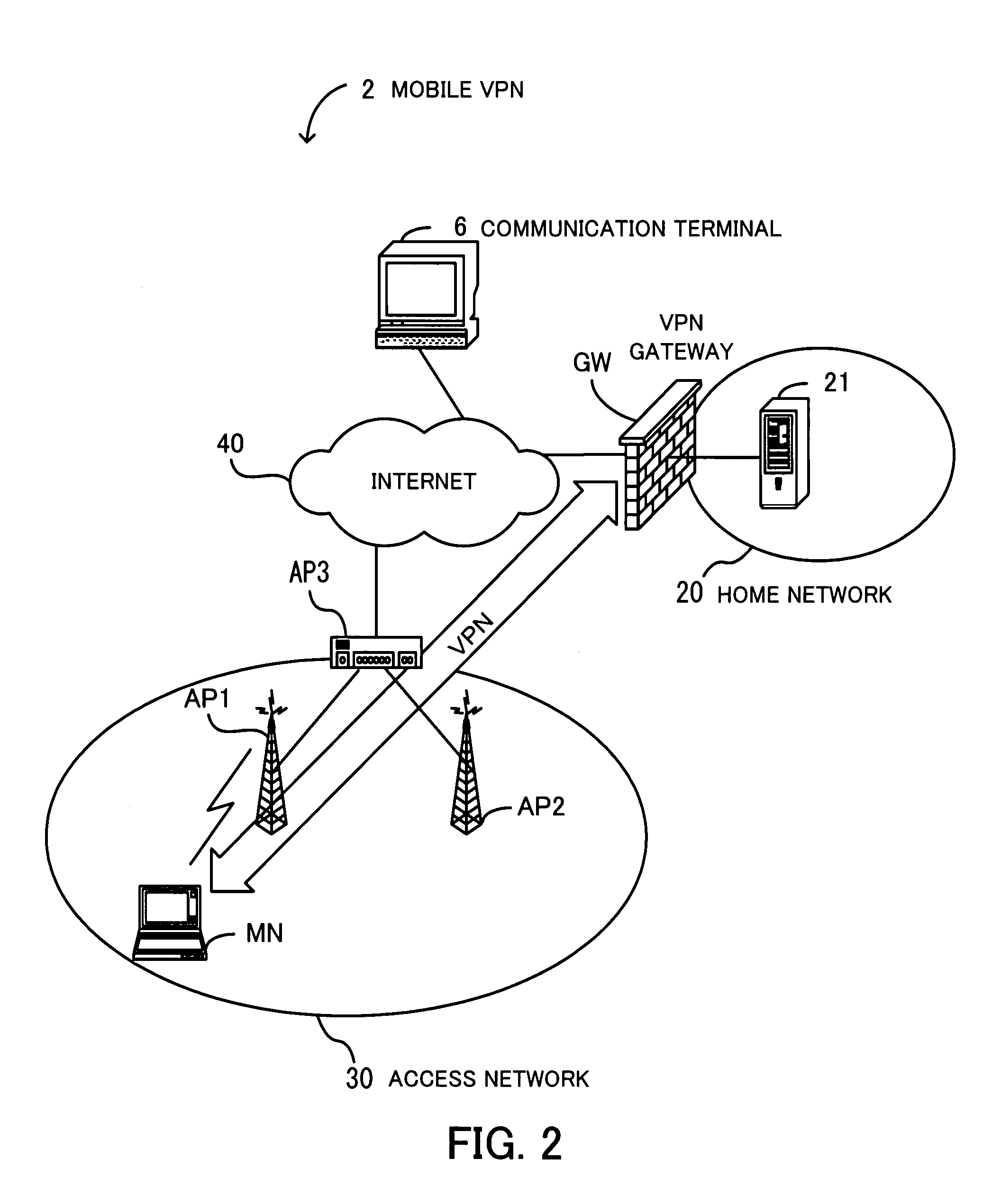
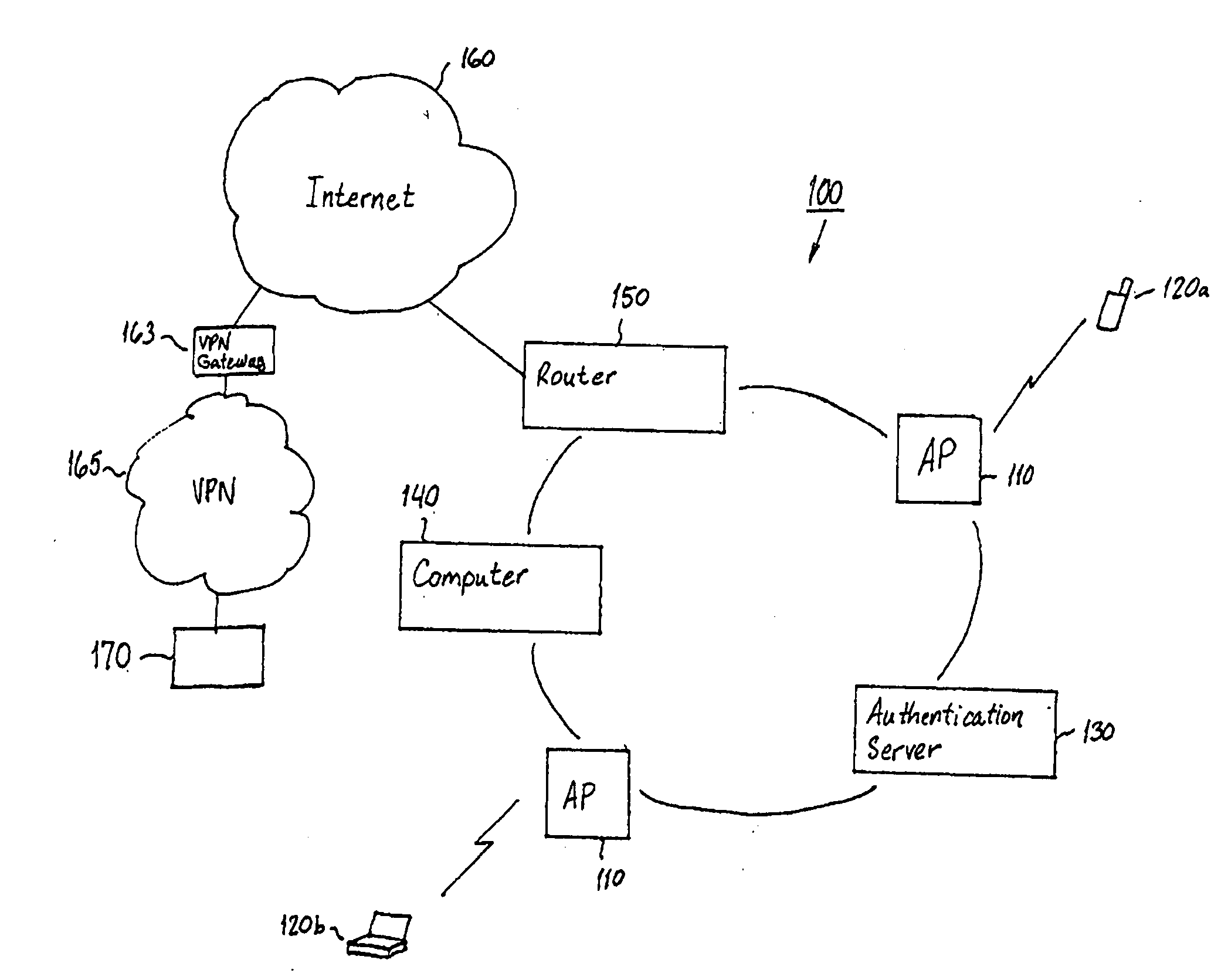
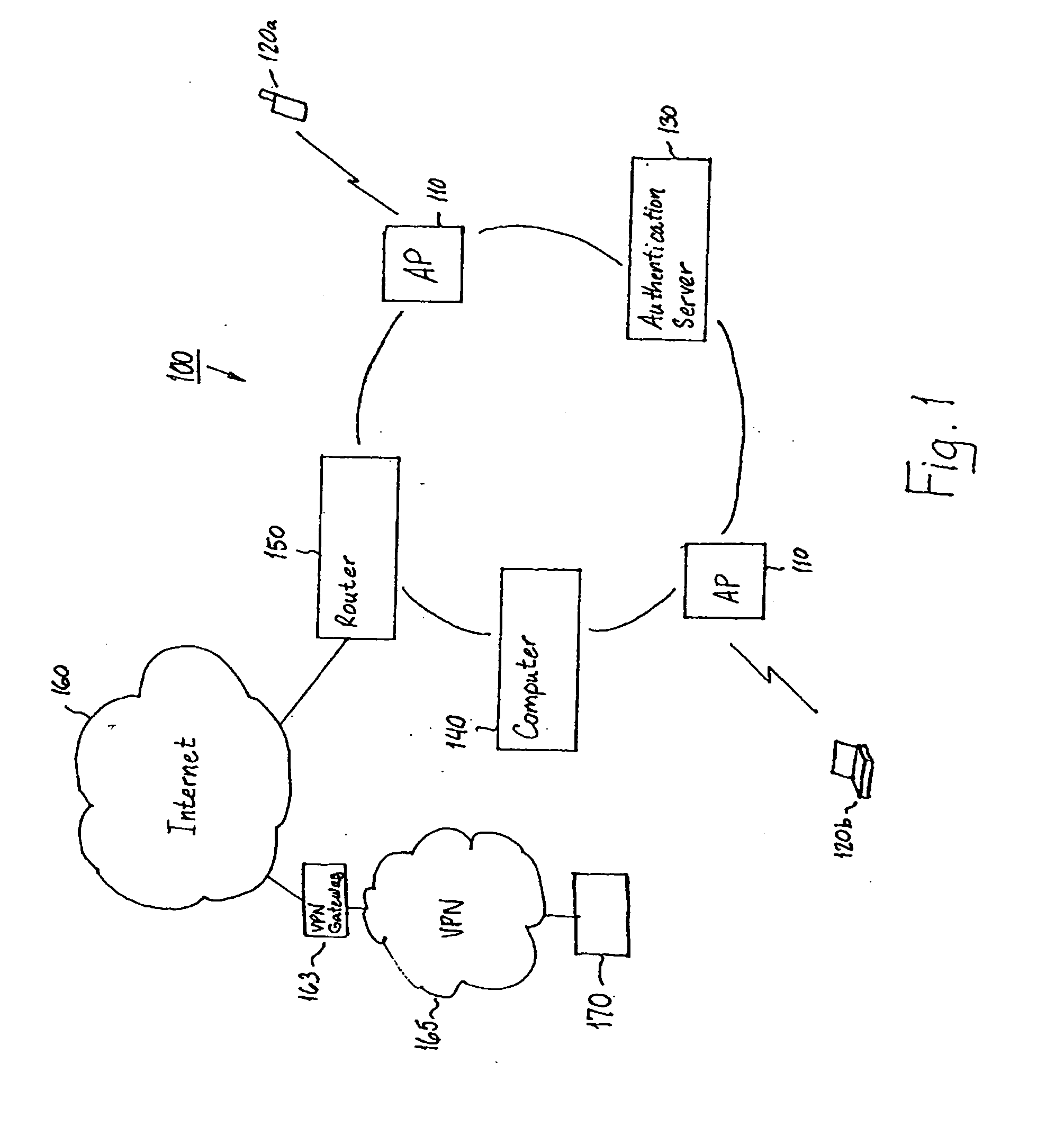
System and method for using virtual local area network tags with a virtual private network
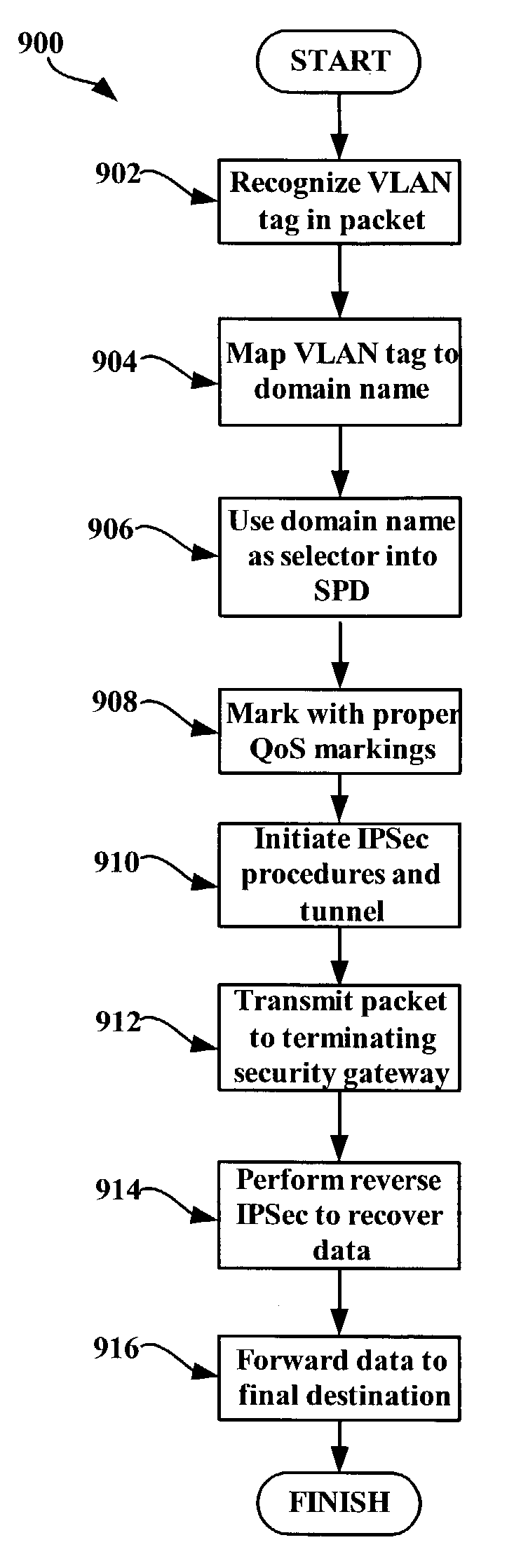
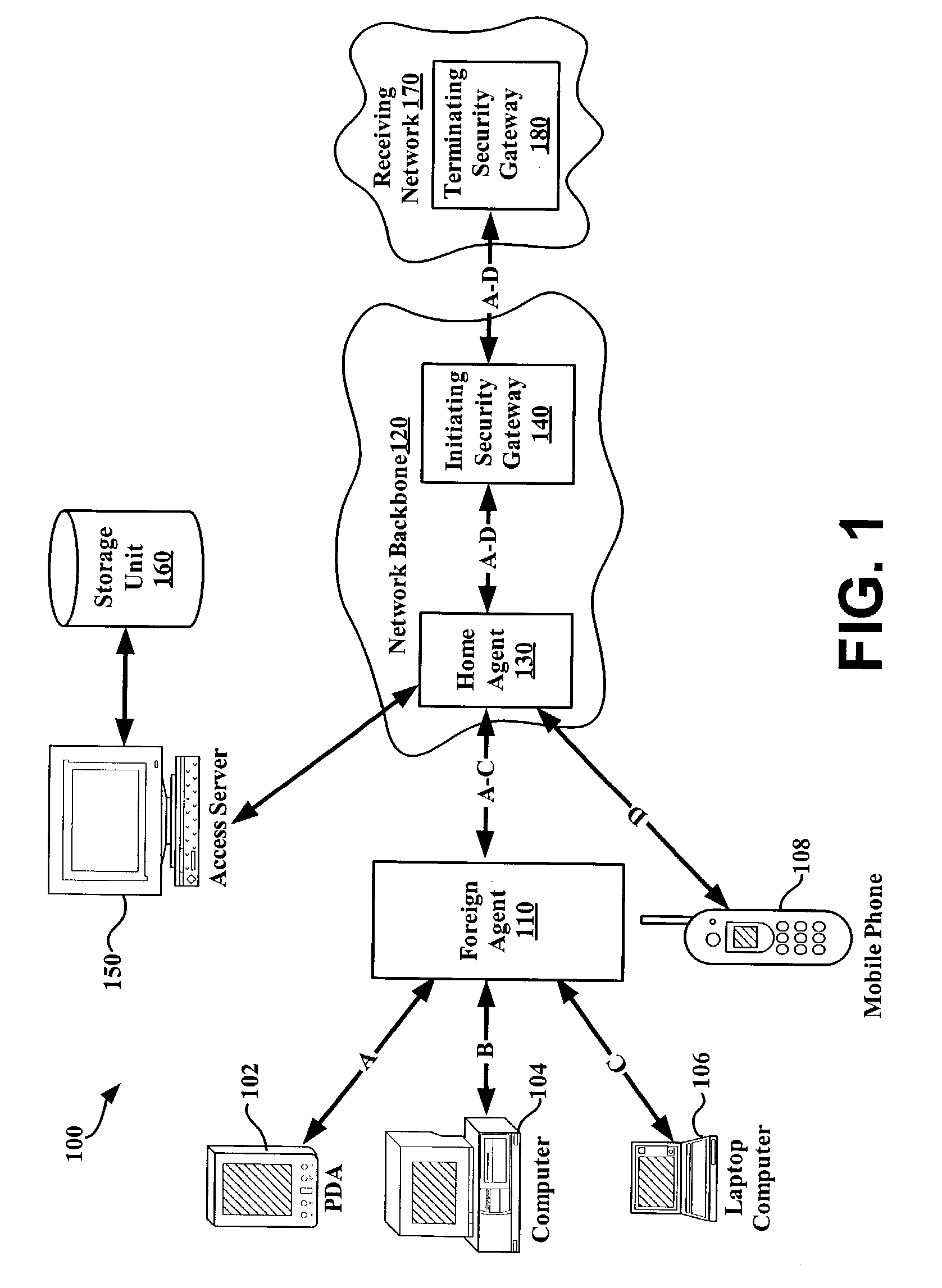
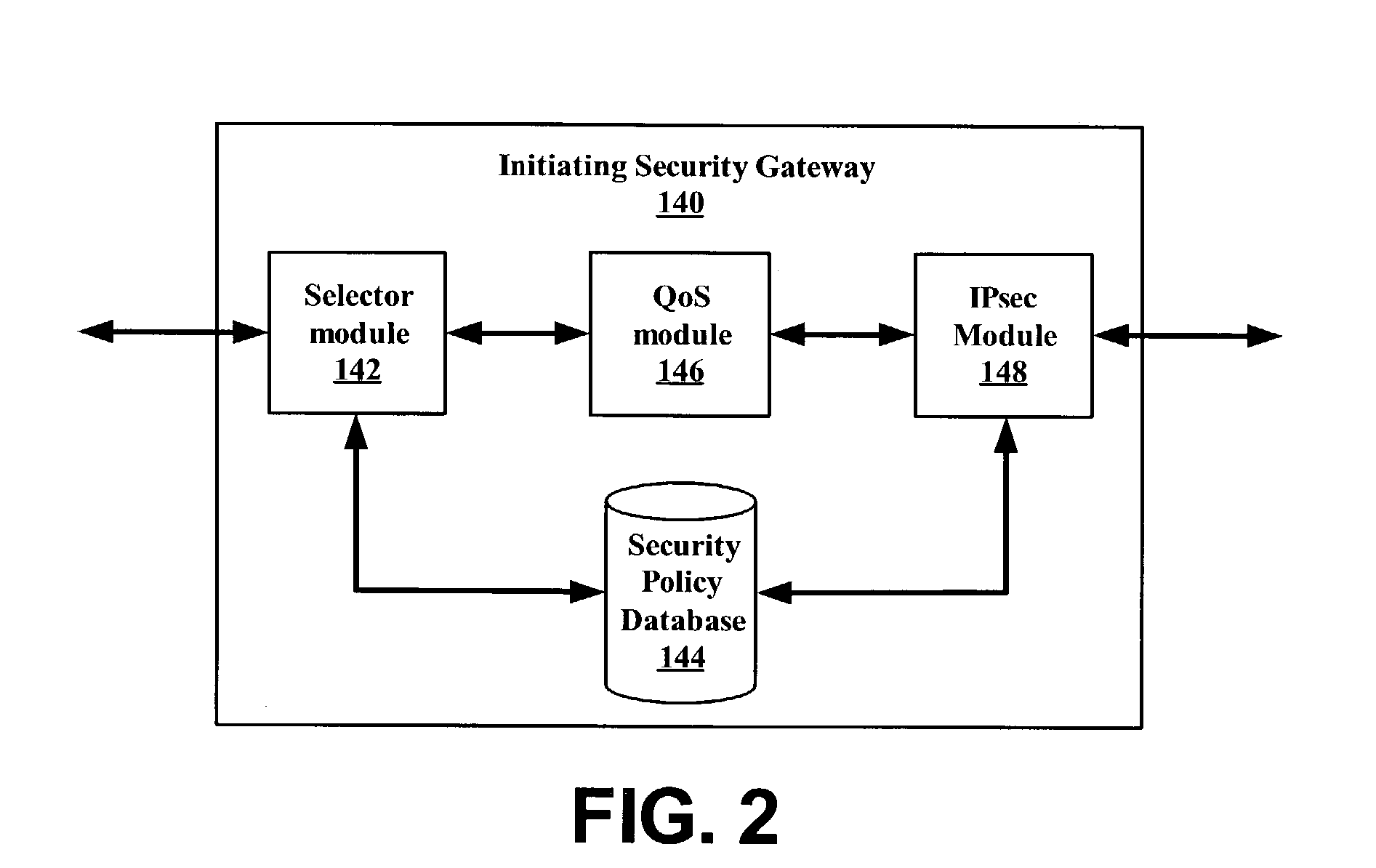
An exemplary system and method for using a network access system, such as a virtual private network (VPN), are provided. A user device may have a user session with a home agent. Additionally, an initiating security gateway may be in communication with the home agent, and a terminating security gateway may be in communication with the initiating security gateway via a tunnel (e.g., Internet Protocol in Internet Protocol (IP-in-IP) or Internet Protocol security (IPsec) tunnel). Further, a virtual local area network (VLAN) tag associated with the user session may map to a selector operable in a security policy database. The selector may be used to find a security policy defining an IPsec procedure, and the security policy may be applied to the tunnel. Also, the initiating security gateway may also include a Quality of Service (QoS) module that determines QoS markings for a packet traveling along the tunnel.
Owner:VALTRUS INNOVATIONS LTD
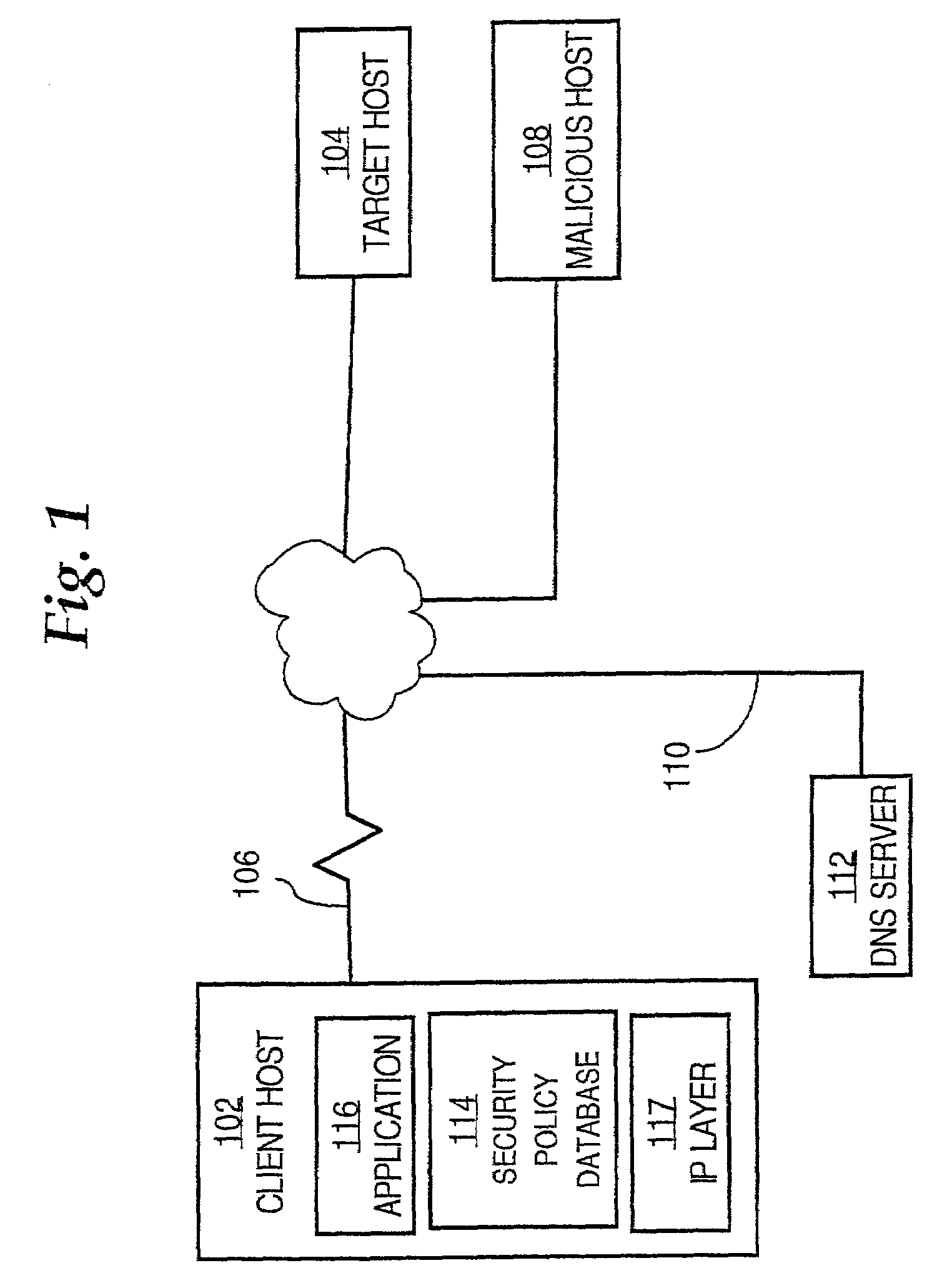
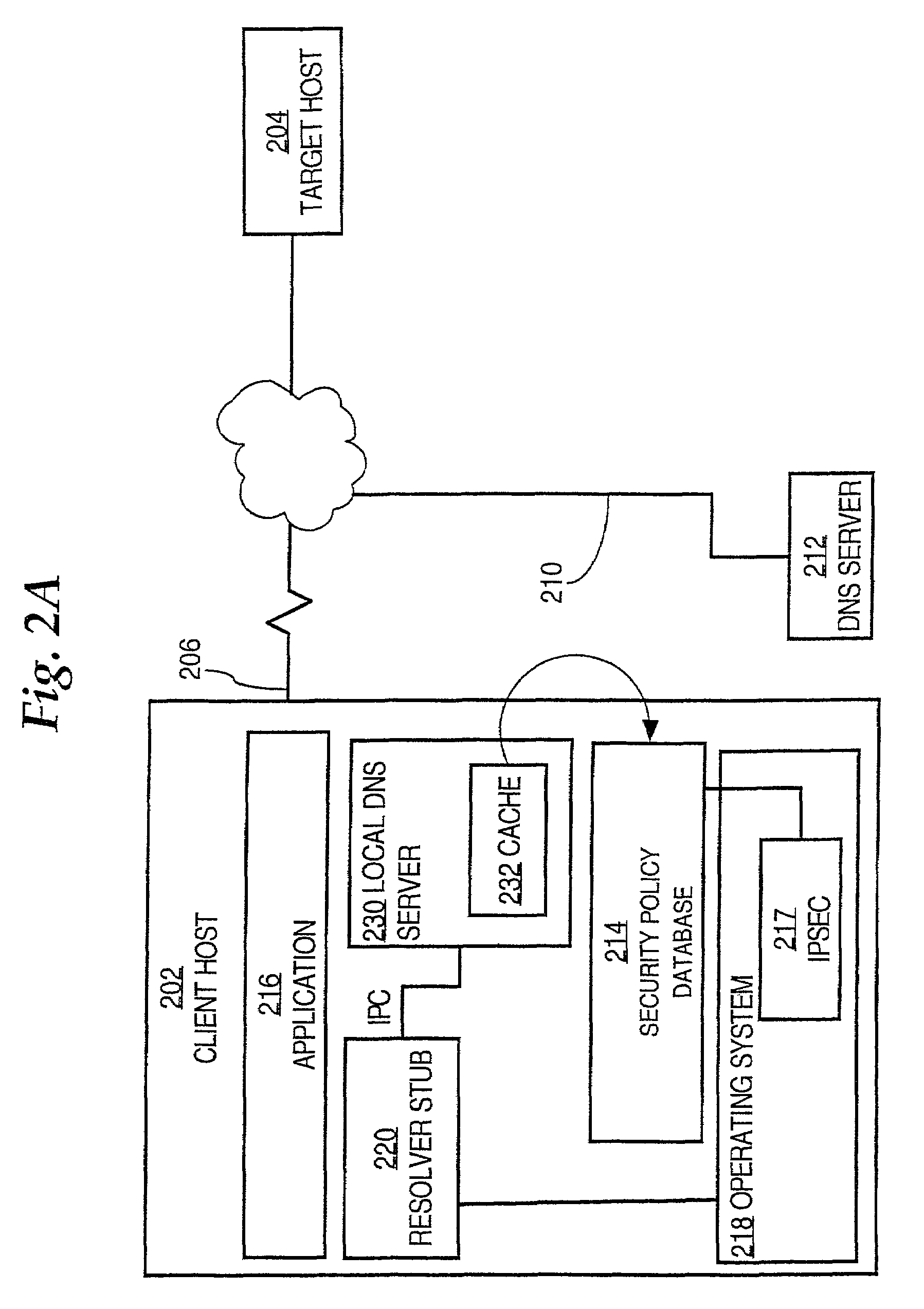
Process and system providing internet protocol security without secure domain resolution
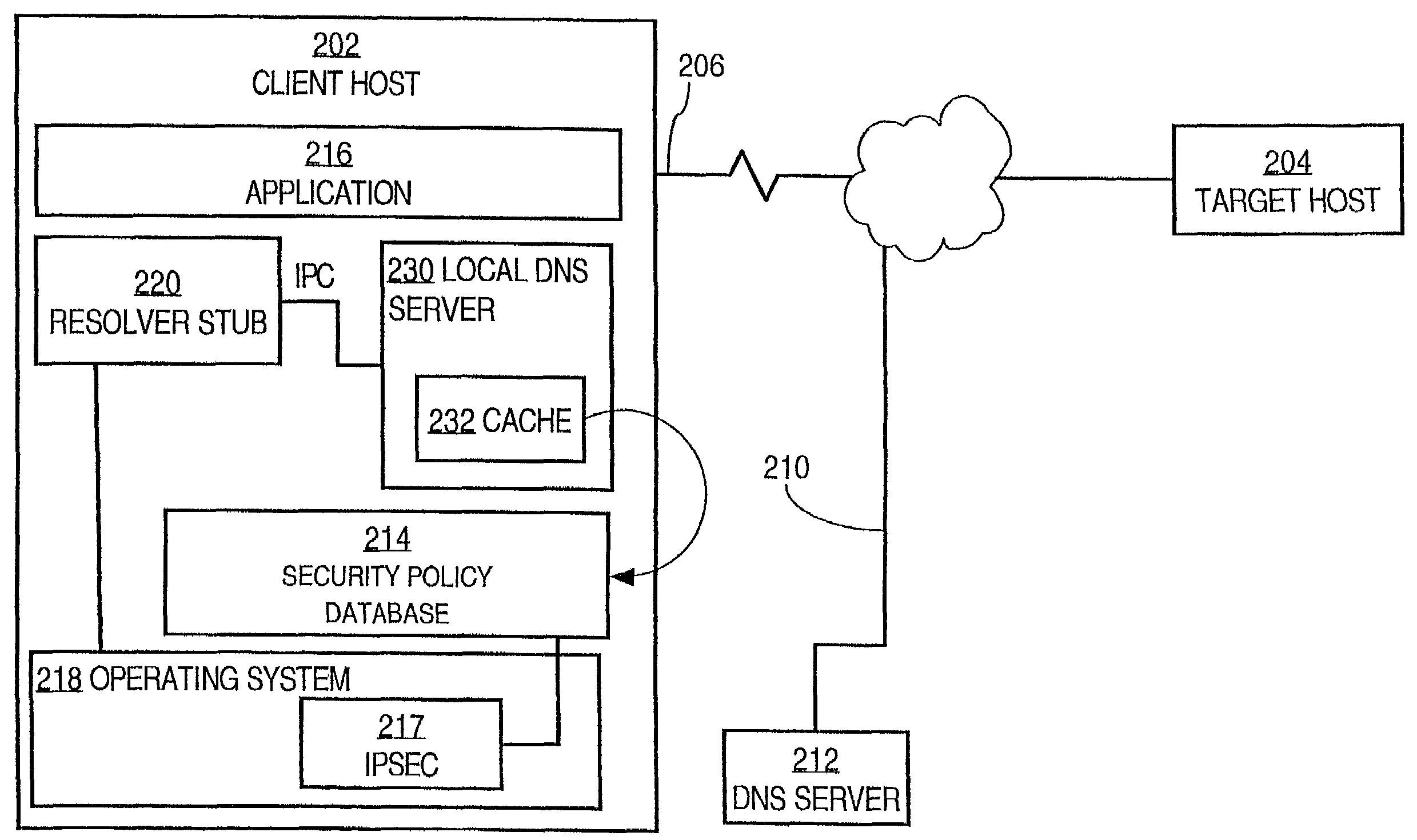
A system and method providing Internet protocol security without secure domain name resolution are disclosed. A processor that periodically needs to resolve domain names into network addresses has a local DNS server that includes a secure IPSEC cache, a resolver function, a security policy database, and an IPSEC layer. The cache is readable only by the IPSEC layer. Resolved domain names are cached with process and transaction identifiers that uniquely associate the resolved names with an application process and time. When resolution is needed, the cache is used to ensure that IP addresses are resolved from names that came from the application. As a result, IPSEC connections may be established without use of DNSSEC to provide secure domain name resolution.
Owner:CISCO TECH INC
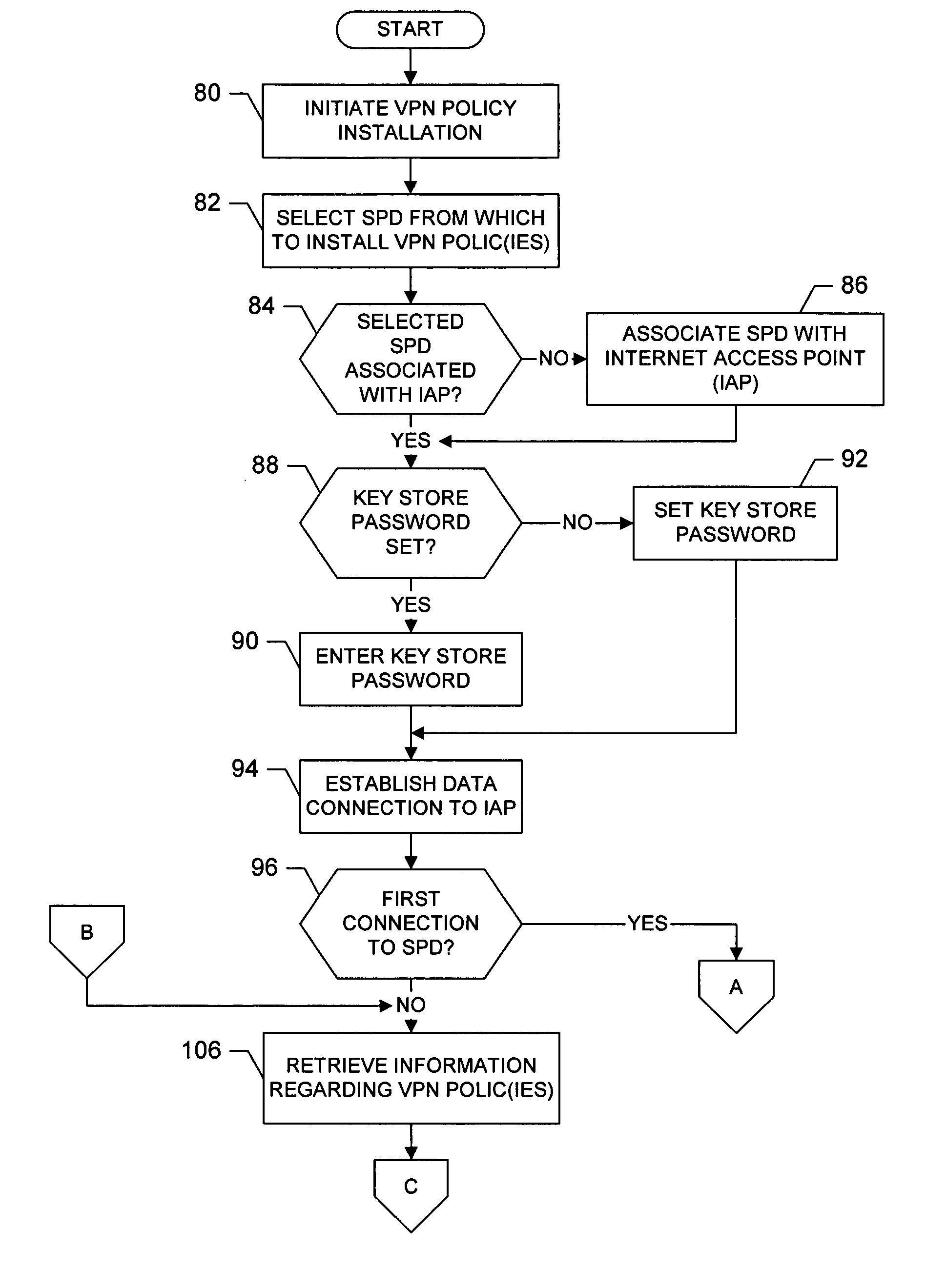
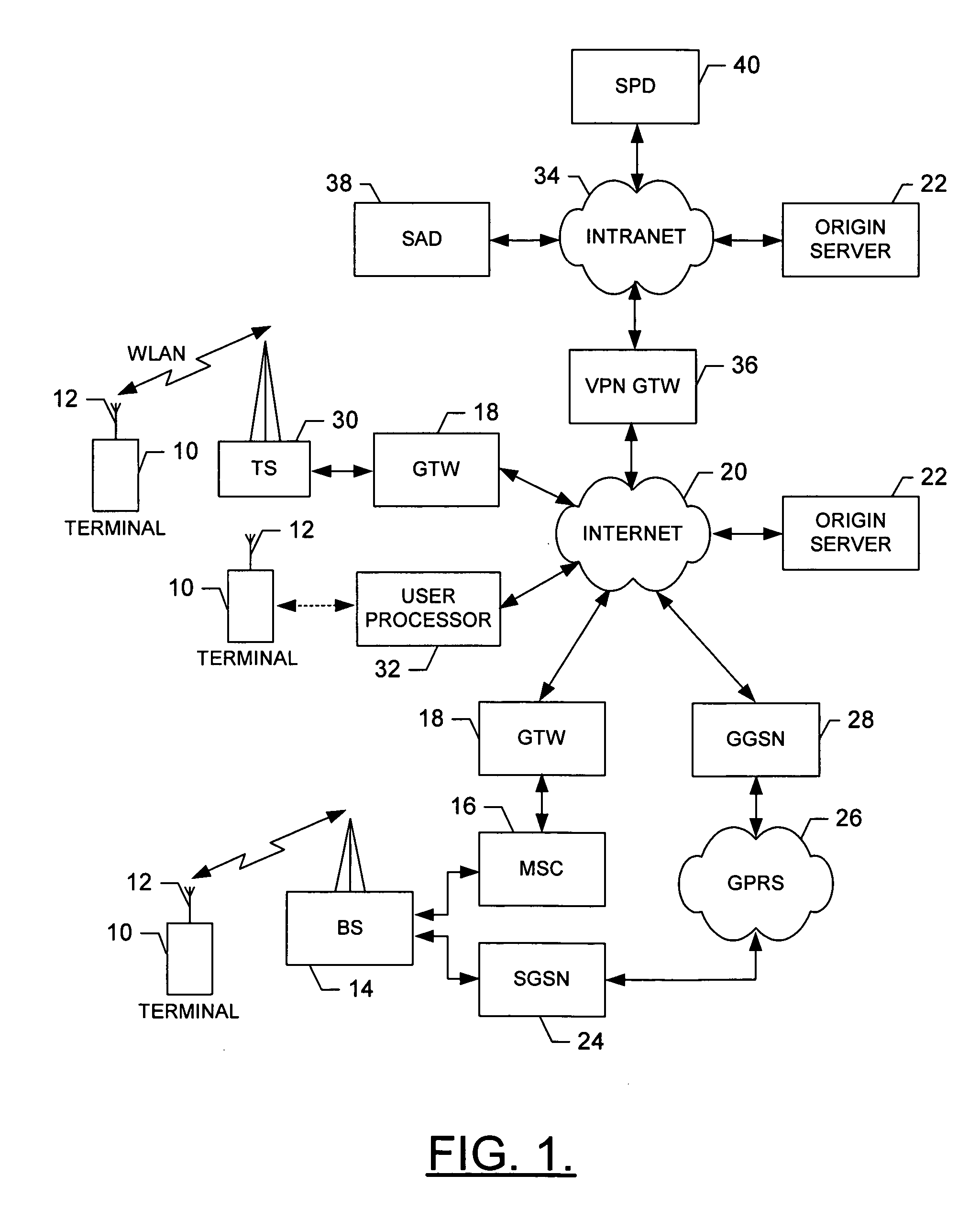
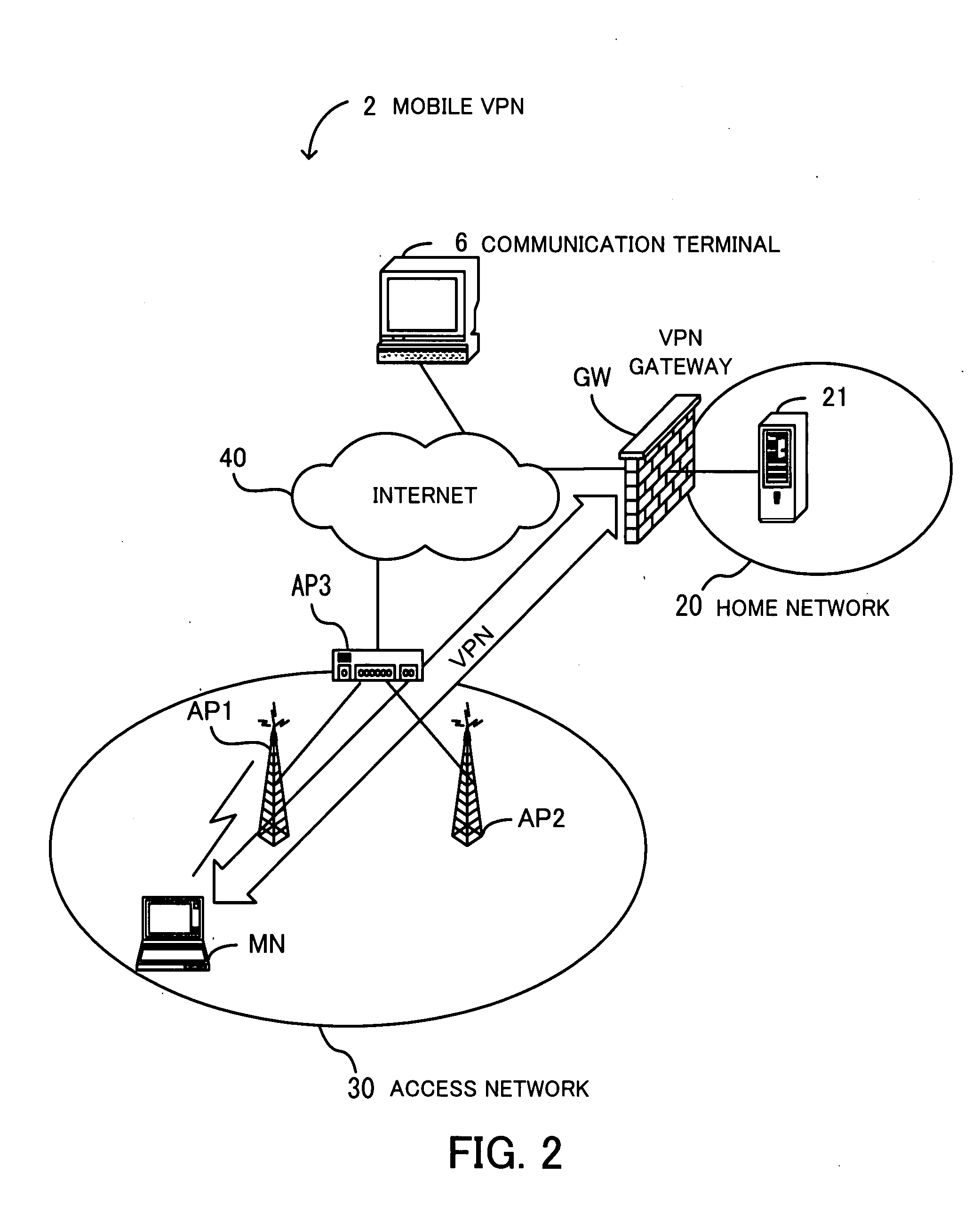
System, method and computer program product for accessing at least one virtual private network
ActiveUS20050198306A1Reduce the burden onSolve the real problemMultiple digital computer combinationsNetworks interconnectionData connectionPrivate network
A system for accessing at least one Virtual Private Network (VPN) includes a terminal, and can include at least one Security Policy Database (SPD). The terminal is capable of communicating with a VPN client and at least one application. The VPN client, in turn, is capable of defining at least one VPN access point, each VPN access point including an associated physical access point and VPN policy. Thereafter, the VPN client can access at least one VPN based upon the VPN access point(s) to thereby establish at least one data connection from at least one application across the at least one VPN. In addition, the VPN client can be capable of downloading at least one VPN policy from the SPD. A system for managing at least one Virtual Private Network (VPN) policy is also provided, where the VPN polic(ies) are for use in accessing at least one VPN.
Owner:NOKIA TECHNOLOGLES OY
Method and circuit to accelerate IPSec processing
ActiveUS7017042B1Unauthorized memory use protectionHardware monitoringNetwork packetSecurity association
Methods and apparatus' for performing IPSec processing on an IP packet being transmitted onto a network and being received from a network are described. The methods and apparatus' further described perform IPSec processing inline which results in a reduced number of transfers over the system bus, reduced utilization of system memory, and a reduced utilization of the system CPU. An IP packet which requires IPSec processing enters an acceleration device. In one embodiment, the acceleration device is coupled to a security policy database (SPD) and security association database (SAD). IPSec processing is performed at the acceleration device without sending the IP Packet to system memory for processing.
Owner:DIGITAL ARCHWAY +1
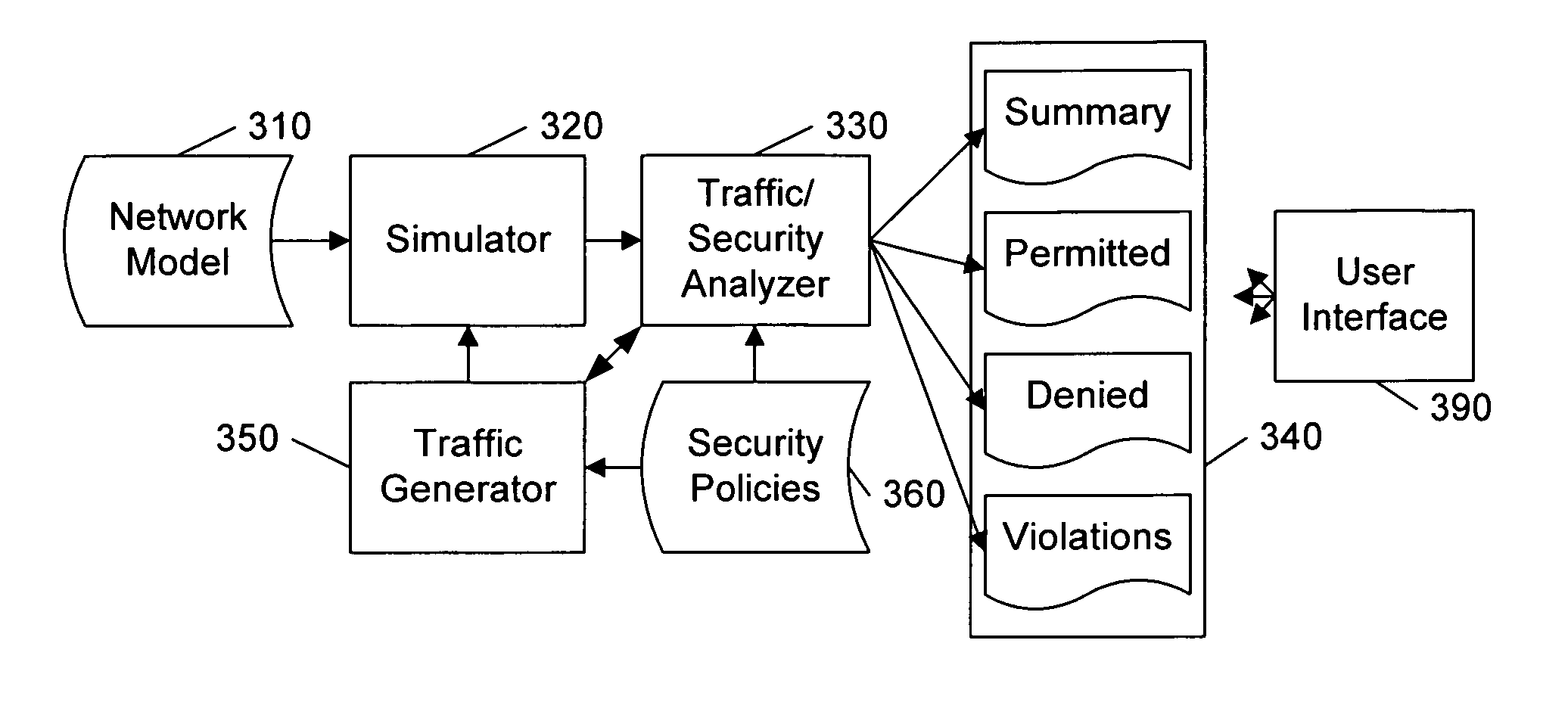
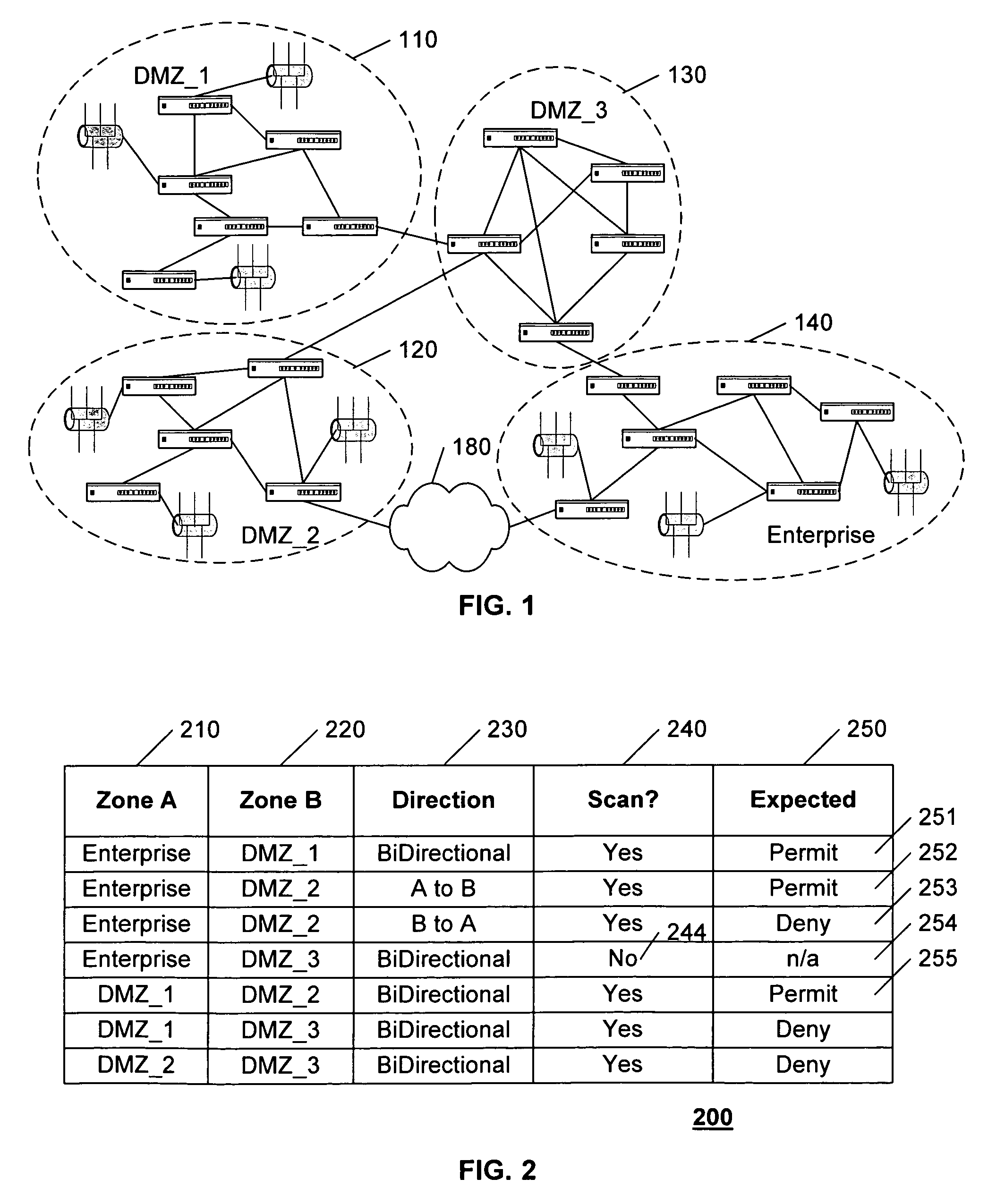
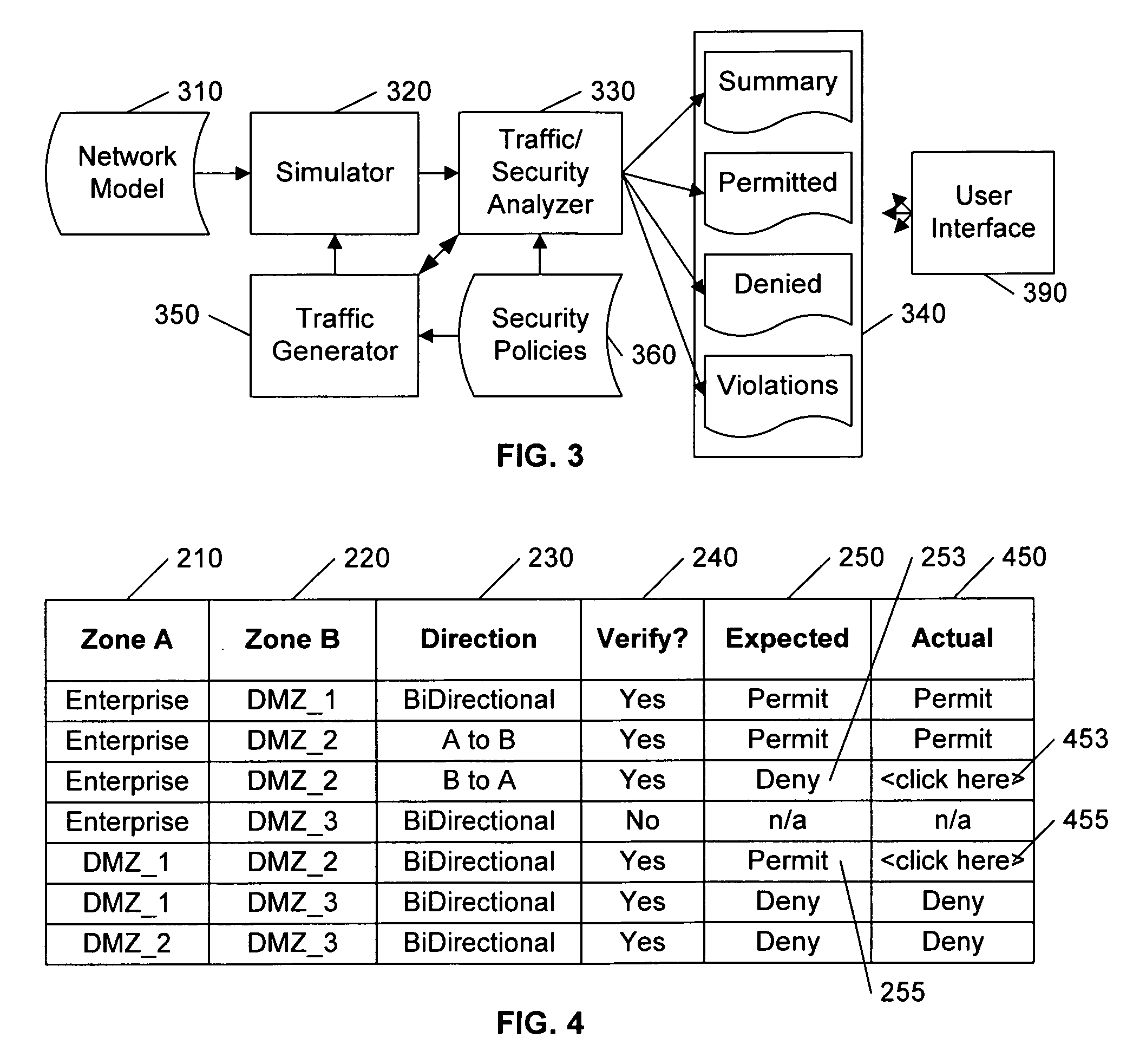
Analyzing security compliance within a network
ActiveUS20070157286A1Data switching networksSpecial data processing applicationsTraffic capacitySecurity compliance
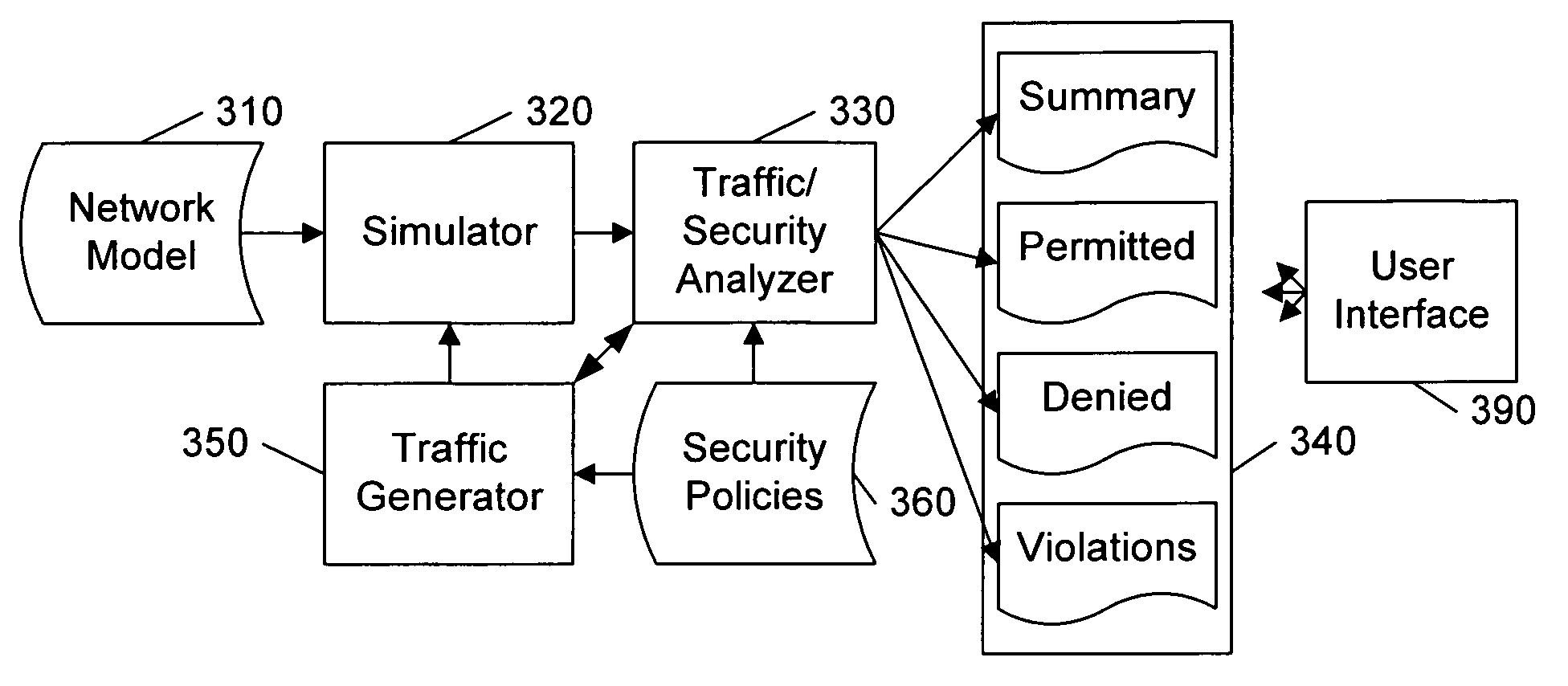
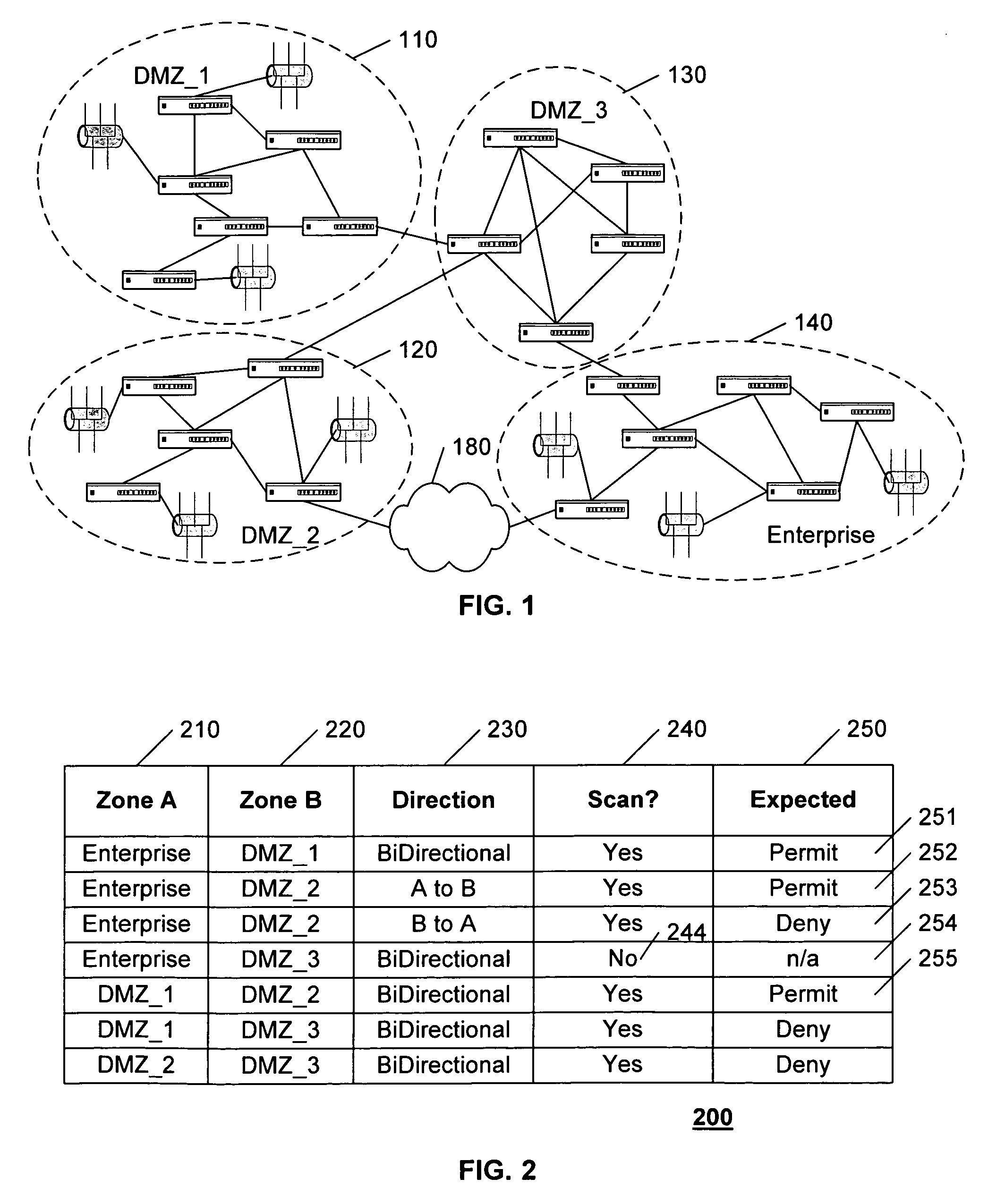
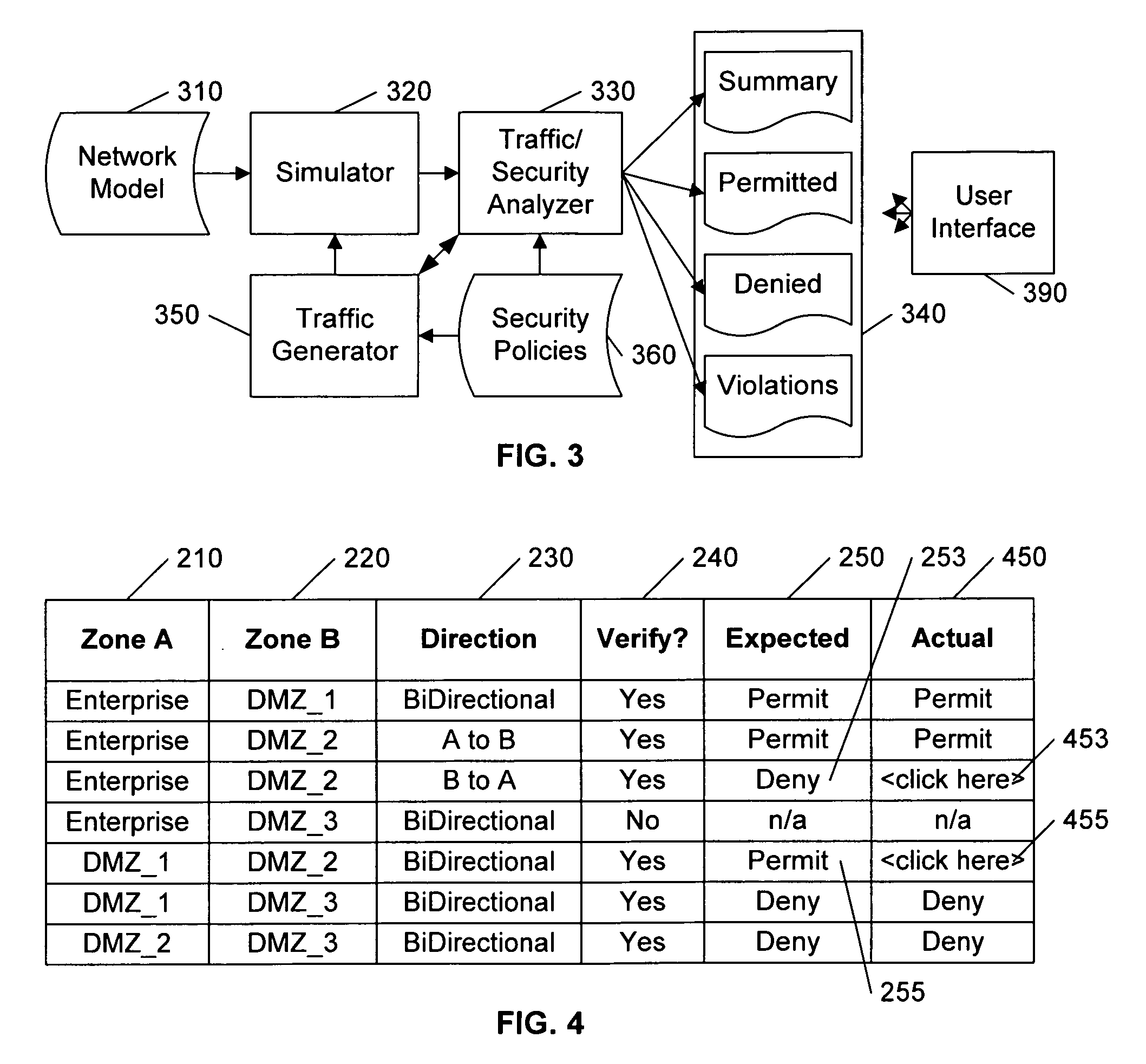
A security policy database identifies the intended security policies within a network, a traffic generator provides test traffic that is configured to test each defined security policy, and a simulator simulates the propagation of this traffic on a model of the network. The model of the network includes the configuration data associated with each device, and thus, if devices are properly configured to enforce the intended security policies, the success / failure of the simulated test traffic will conform to the intended permit / deny policy of each connection. Differences between the simulated message propagation and the intended security policies are reported to the user, and diagnostic tools are provided to facilitate identification of the device configuration data that accounts for the observed difference. Additionally, if a network's current security policy is unknown, test traffic is generated to reveal the actual policy in effect, to construct a baseline intended security policy.
Owner:RIVERBED TECH LLC
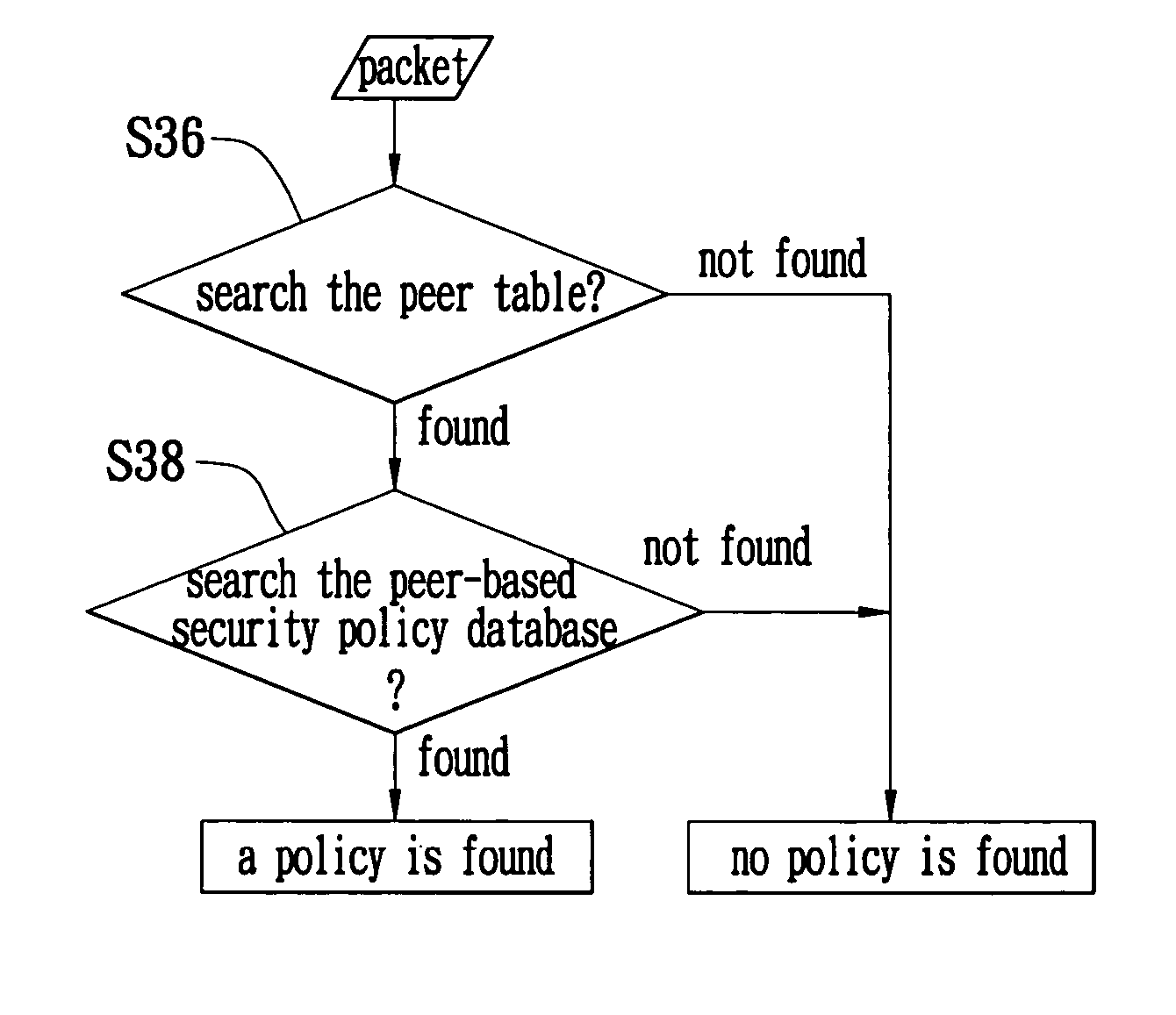
Searching method for a security policy database
ActiveUS20050044068A1Improve search capabilitiesShorten the timeData processing applicationsDigital data processing detailsIPsecDatabase
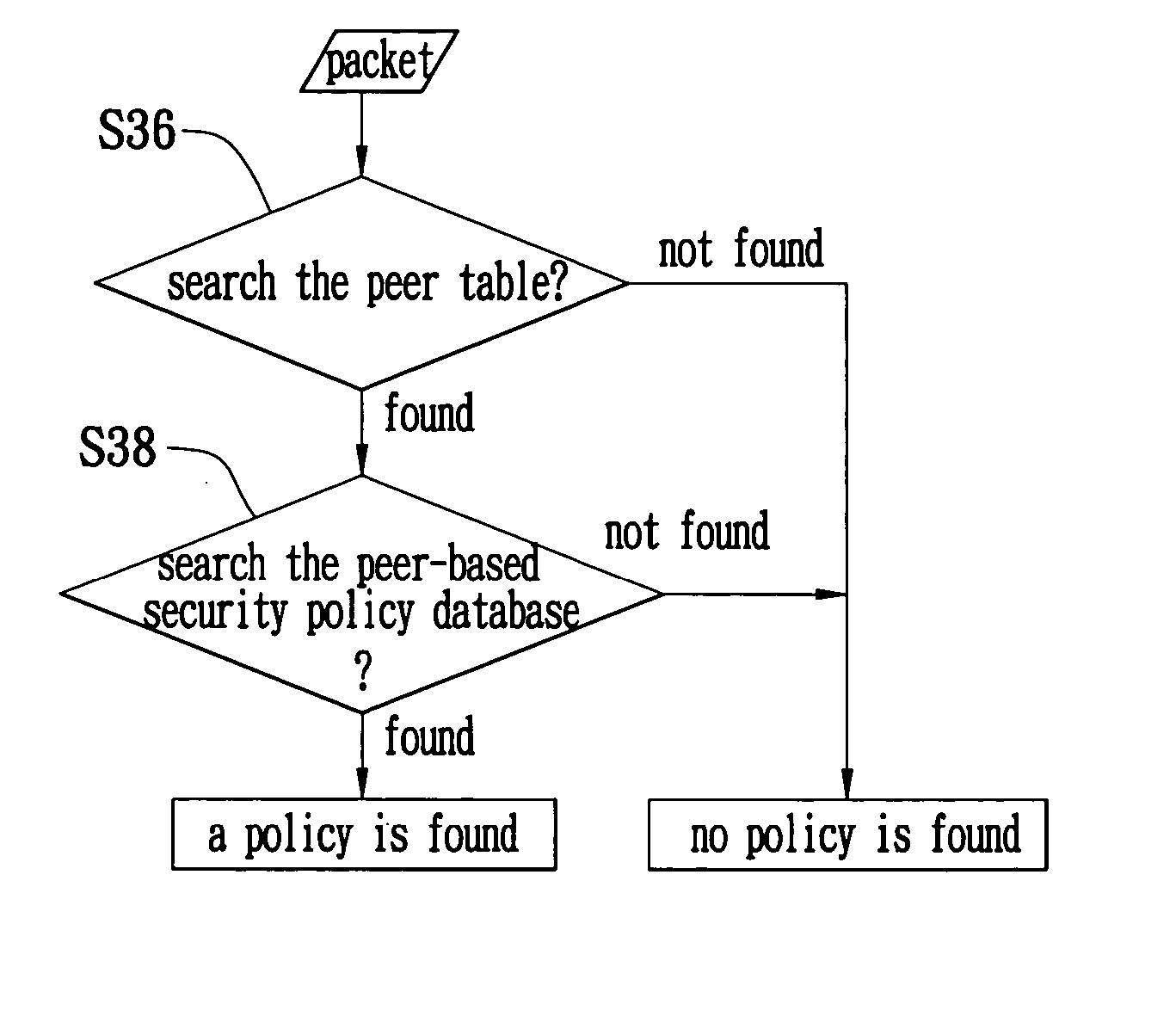
A searching method for a Security Policy Database (SPD) is proposed. The characteristic of peer gateway of the IPSec is applied to divide the original SPD into multiple smaller peer-based SPDs, and build a peer table corresponding to the peer-based SPDs. When it is required to search the policies in the database, the peer-based SPD according to the present invention can be directly used so as to save the time of data searching.
Owner:A10 NETWORKS
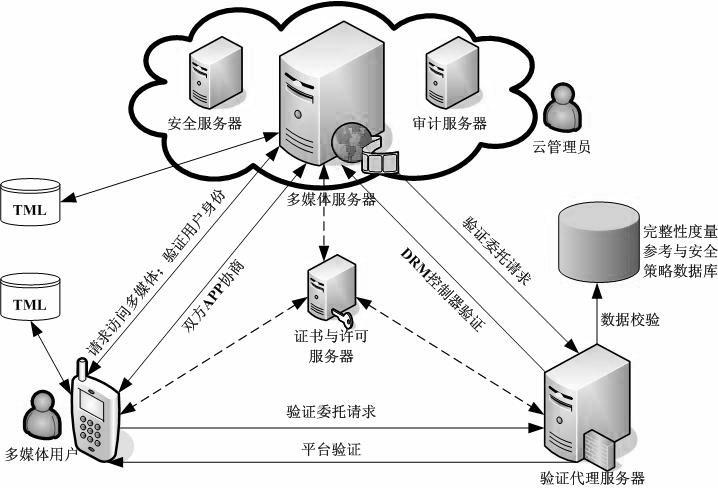
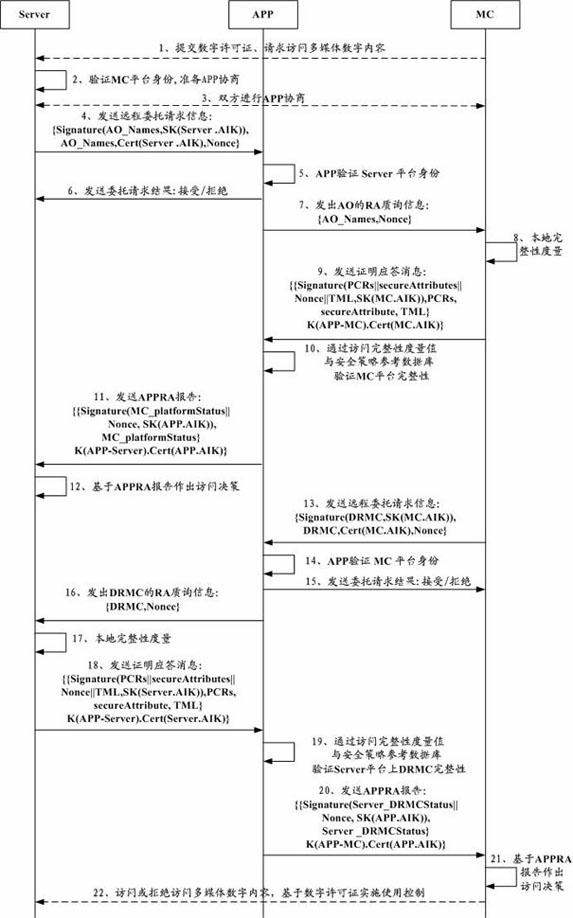
Digital content trusted usage control method based on cloud computing
The invention discloses a digital content trusted usage control method based on cloud computing. The system framework comprises a multimedia server, a mobile terminal, a verification agent server, a certificate and license server, an integrity measurement reference and security policy database and a trust measurement log, wherein the mobile terminal uses the multimedia digital content on the multimedia server through a graphical user interface of a DRM (digital rights management) controller; a multimedia server platform runs the DRM controller and performs usage control on the DRM controller through a DRM license; the mobile terminal and the multimedia server determine a verification agent through negotiation; and by adopting a remote proof method and a bidirectional integrity verification security protocol, which support the verification agent, the bidirectional trust relationship between the multimedia content provider and the terminal user is guaranteed, and the secrete privacy data on the terminal equipment of the user is protected as well. In the invention, as the DRM controller is configured on the multimedia server, the possibility of malicious attack such as breaking, tampering and the like, performed by an illegal user, is avoided.
Owner:HENAN UNIV OF SCI & TECH
Searching method for a security policy database
ActiveUS7392241B2Shorten the timeImprove search capabilitiesData processing applicationsDigital data processing detailsIPsecData mining
A searching method for a Security Policy Database (SPD) is proposed. The characteristic of peer gateway of the IPSec is applied to divide the original SPD into multiple smaller peer-based SPDs, and build a peer table corresponding to the peer-based SPDs. When it is required to search the policies in the database, the peer-based SPD according to the present invention can be directly used so as to save the time of data searching.
Owner:A10 NETWORKS
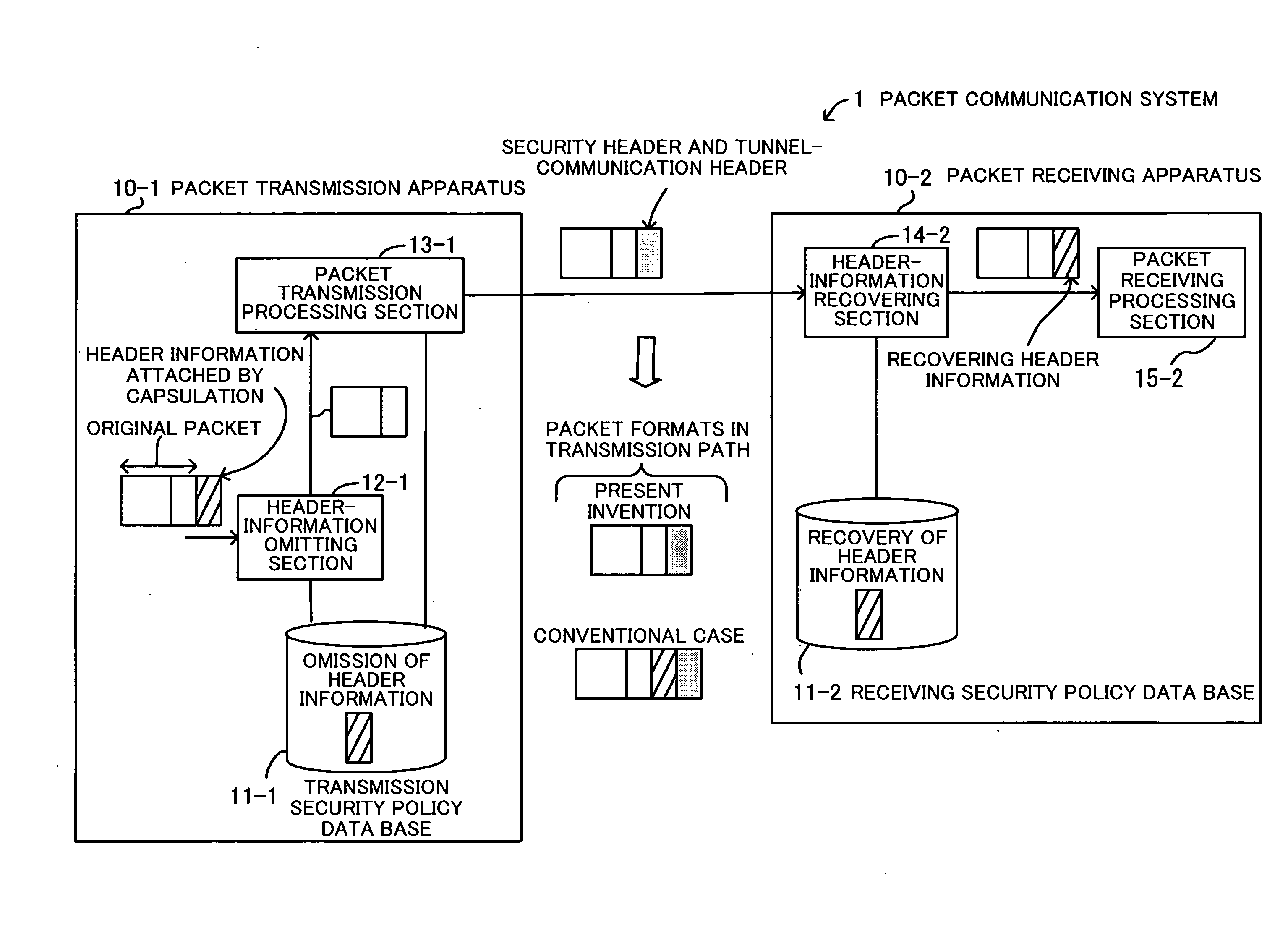
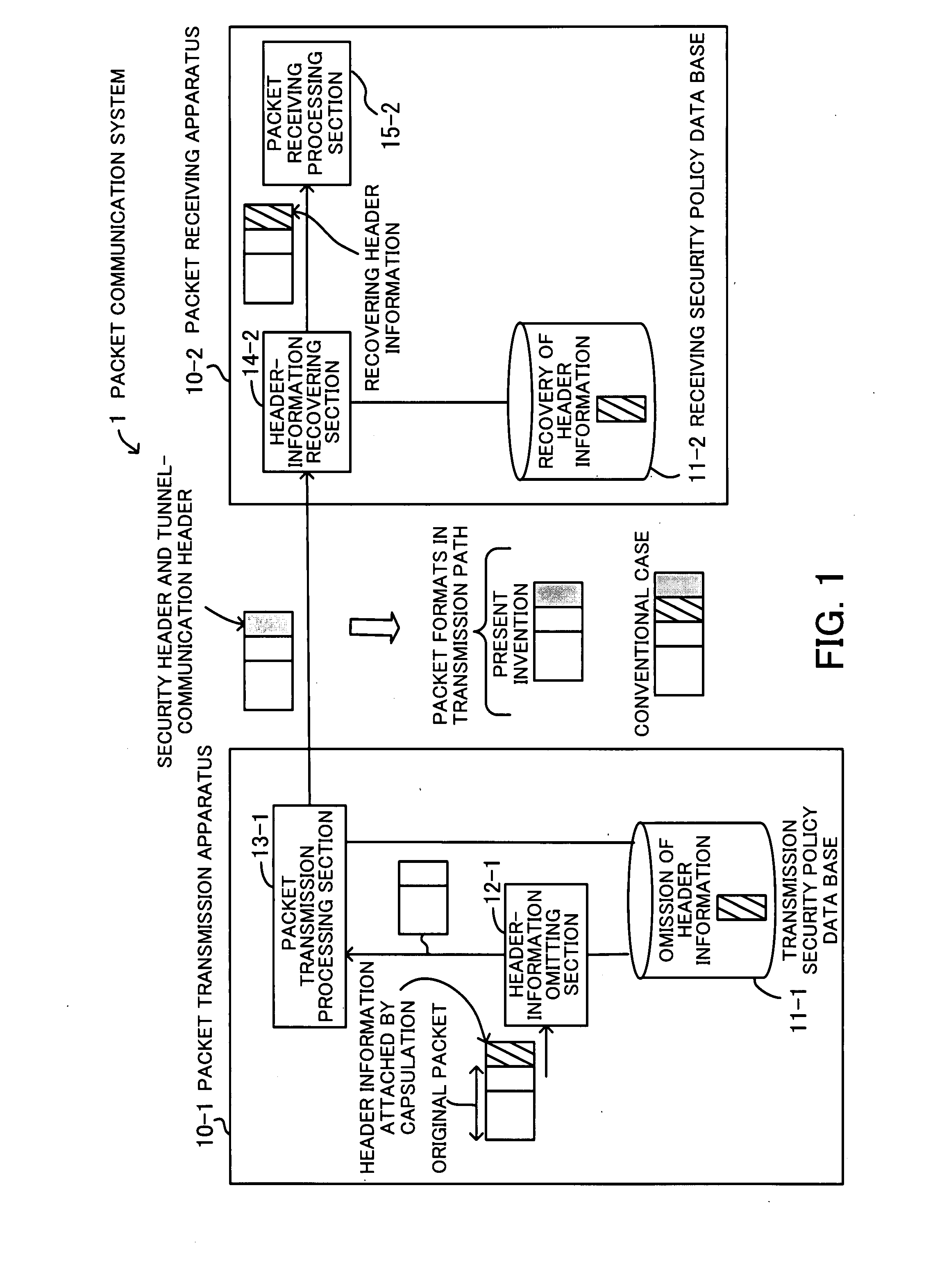
Packet communication system
InactiveUS20070186100A1Easy to useImprove security levelNetwork traffic/resource managementDigital computer detailsPacket communicationGroup communication systems
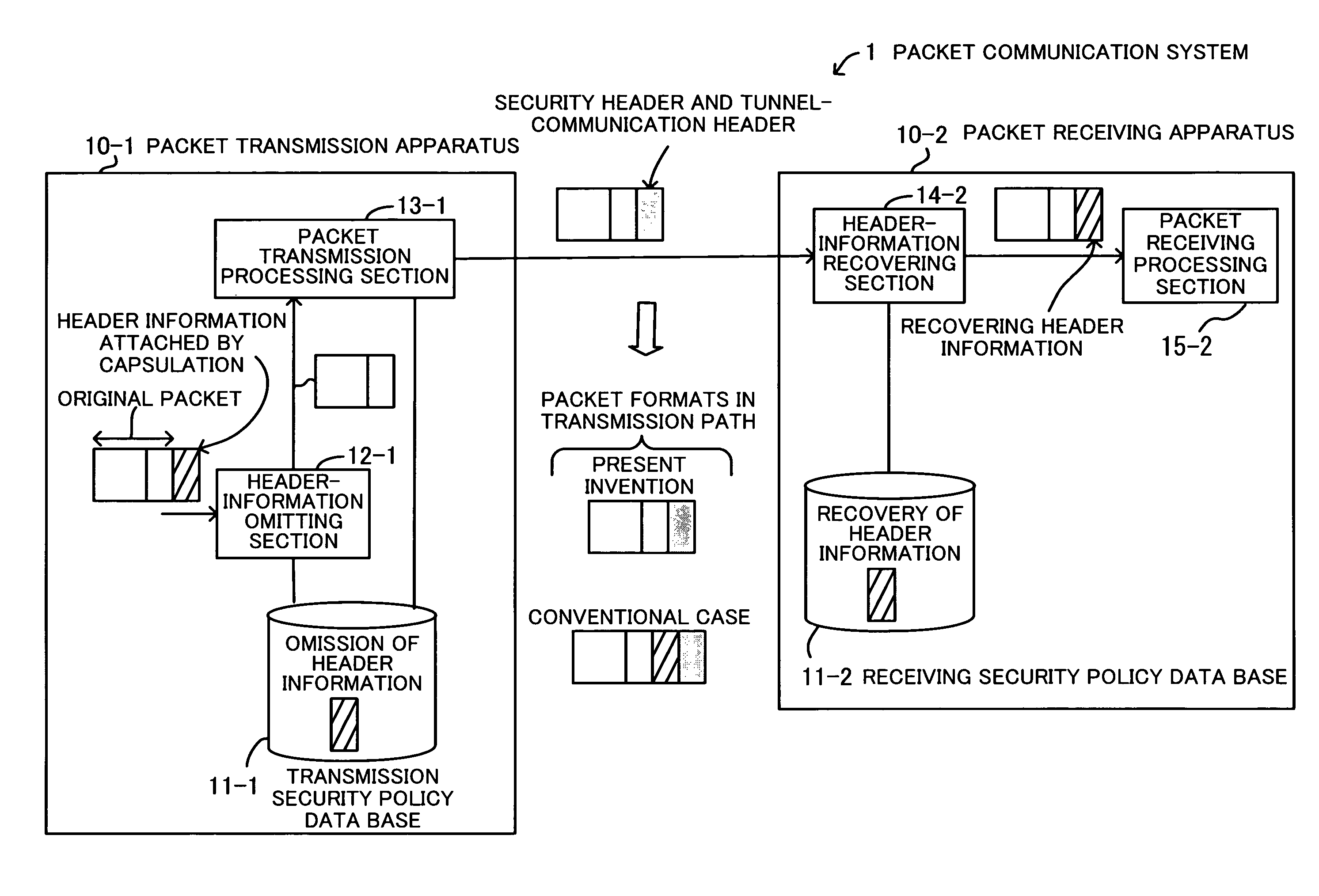
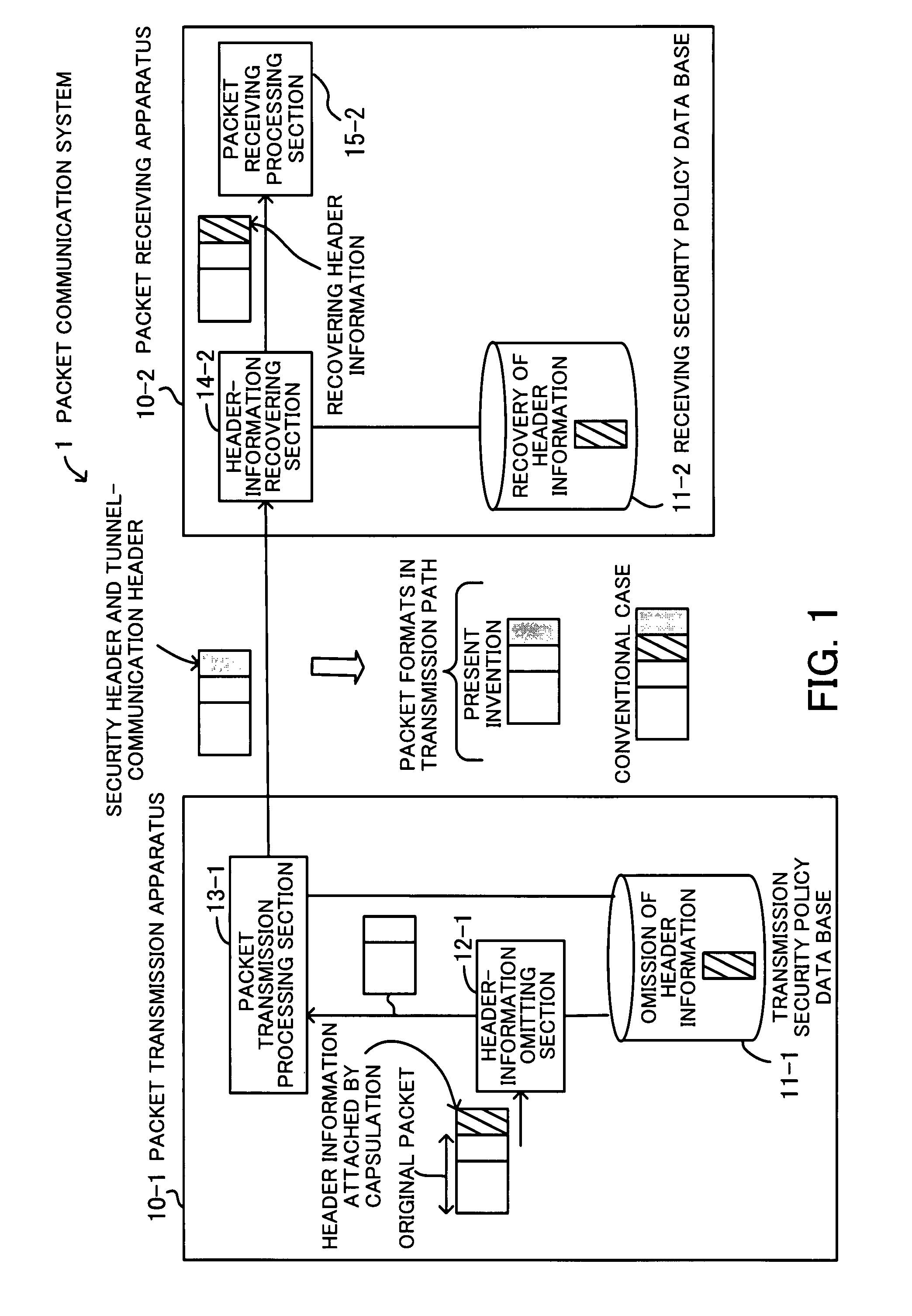
A packet communication system for effectively using network resources and for improving network operability. A transmission security policy database specifies the omission of header information attached when a transmission packet is capsulated, as a transmission security policy. A header-information omitting section omits the header information of the capsulated transmission packet. A packet transmission processing section adds a security header and a header for tunnel communication to the packet from which the header information has been omitted and transmits the packet. A receiving security policy database specifies that the header information has been omitted, as a receiving security policy. A header-information recovering section searches the receiving security policy database for a security policy for a received packet, and when recognizing that the received packet is a target packet from which the header information has been omitted, recovers the header information.
Owner:FUJITSU LTD
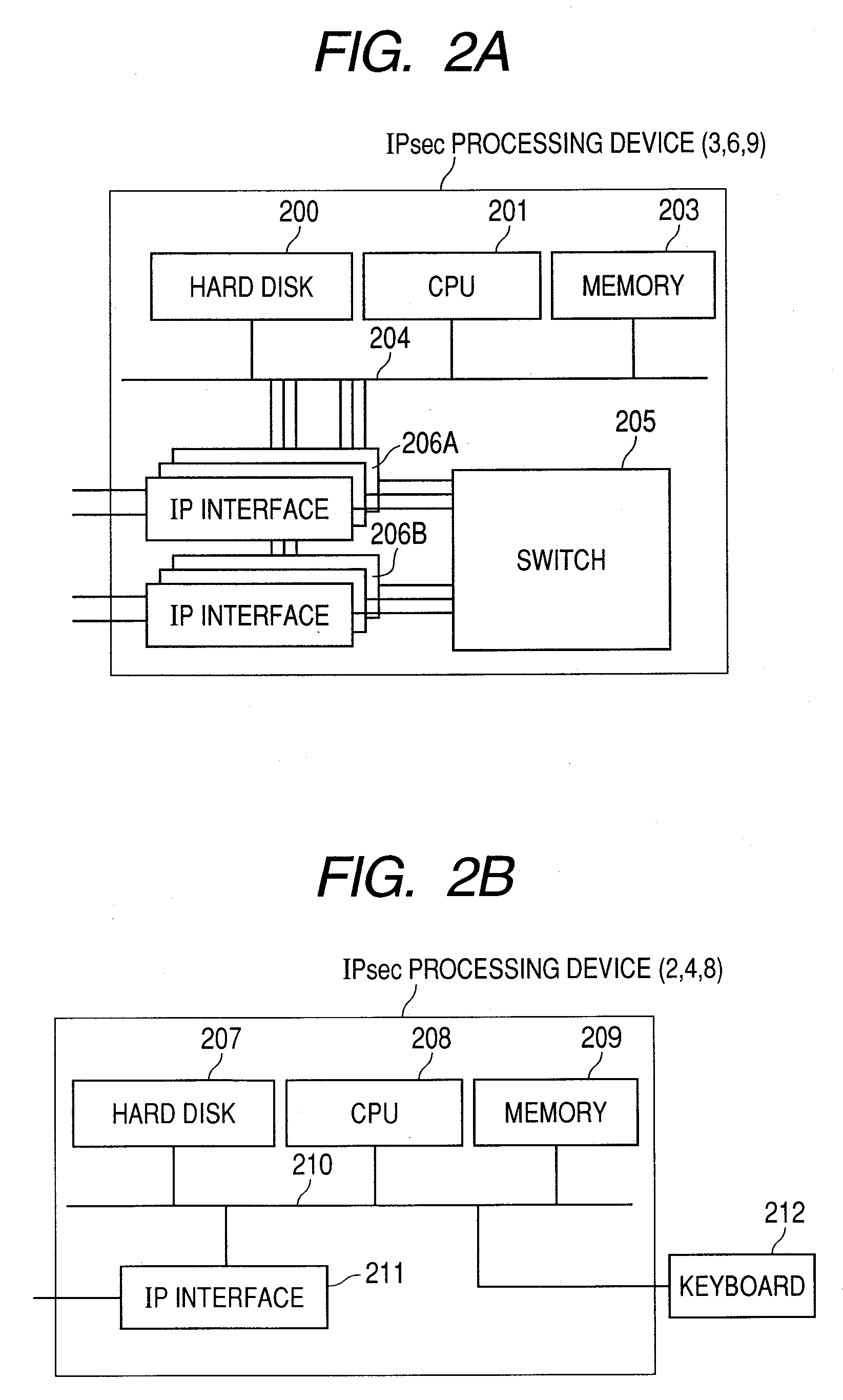
IPSec PROCESSING DEVICE, NETWORK SYSTEM, AND IPSec PROCESSING PROGRAM
InactiveUS20080052756A1Quick searchImprove retrieval speedDigital data processing detailsSpecial data processing applicationsNetworked systemIPsec
Security policy databases capable of being fast retrieved while securing sequentiality. An IPSec processing device of the present invention performs communications by encrypting IP packets exchanged between a first IP network and a second IP network. The IPSec processing device includes a security policy database that stores security policies. The security policy database includes first, second, and third security policy databases. The first and third security policy databases include a linear list structure, and the second security policy database includes a hash list structure. The IPSec processing device, when performing at least one of transmission and reception of the IP packet, retrieves a security policy in the order of the first, second, and third security policy databases.
Owner:HITACHI LTD
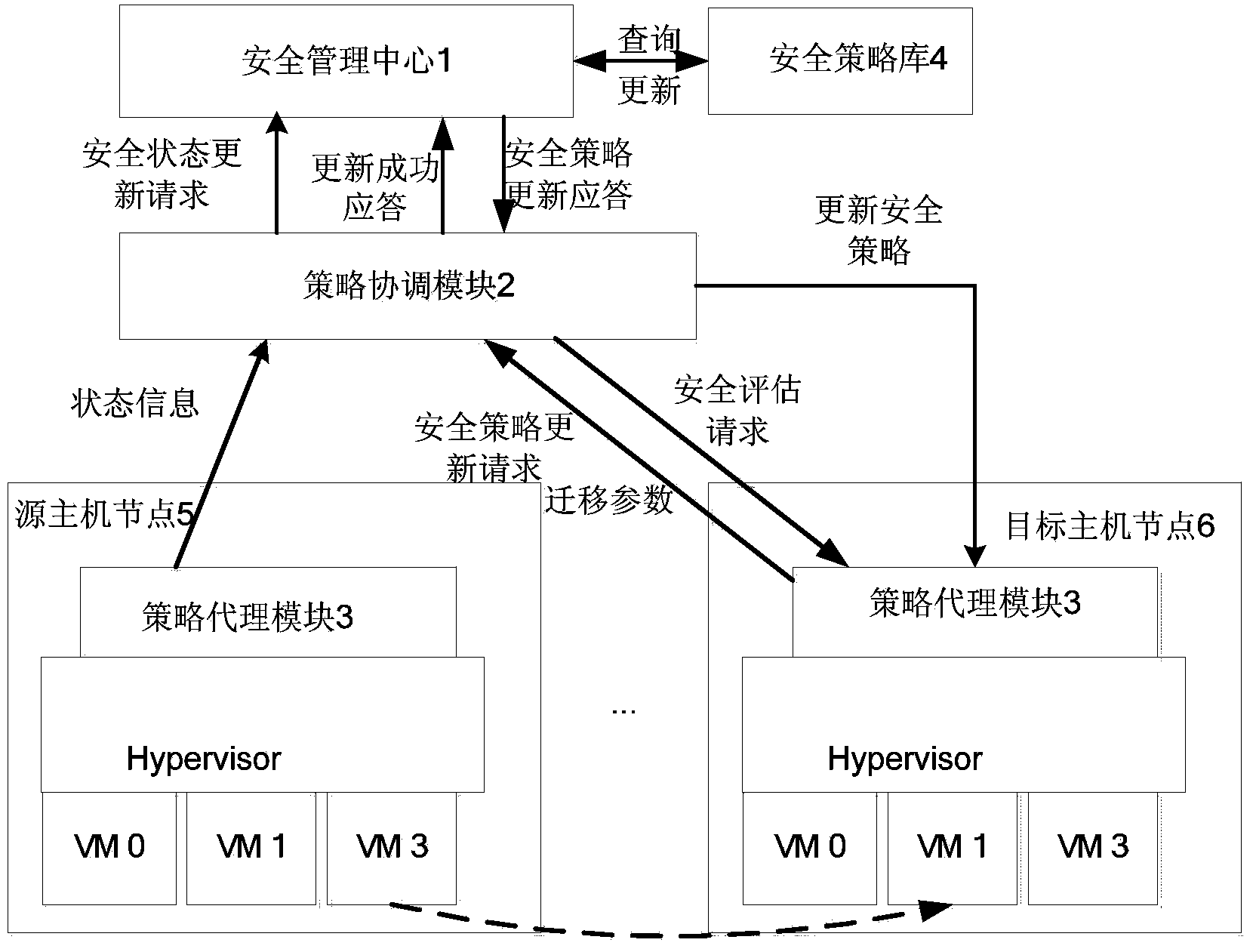
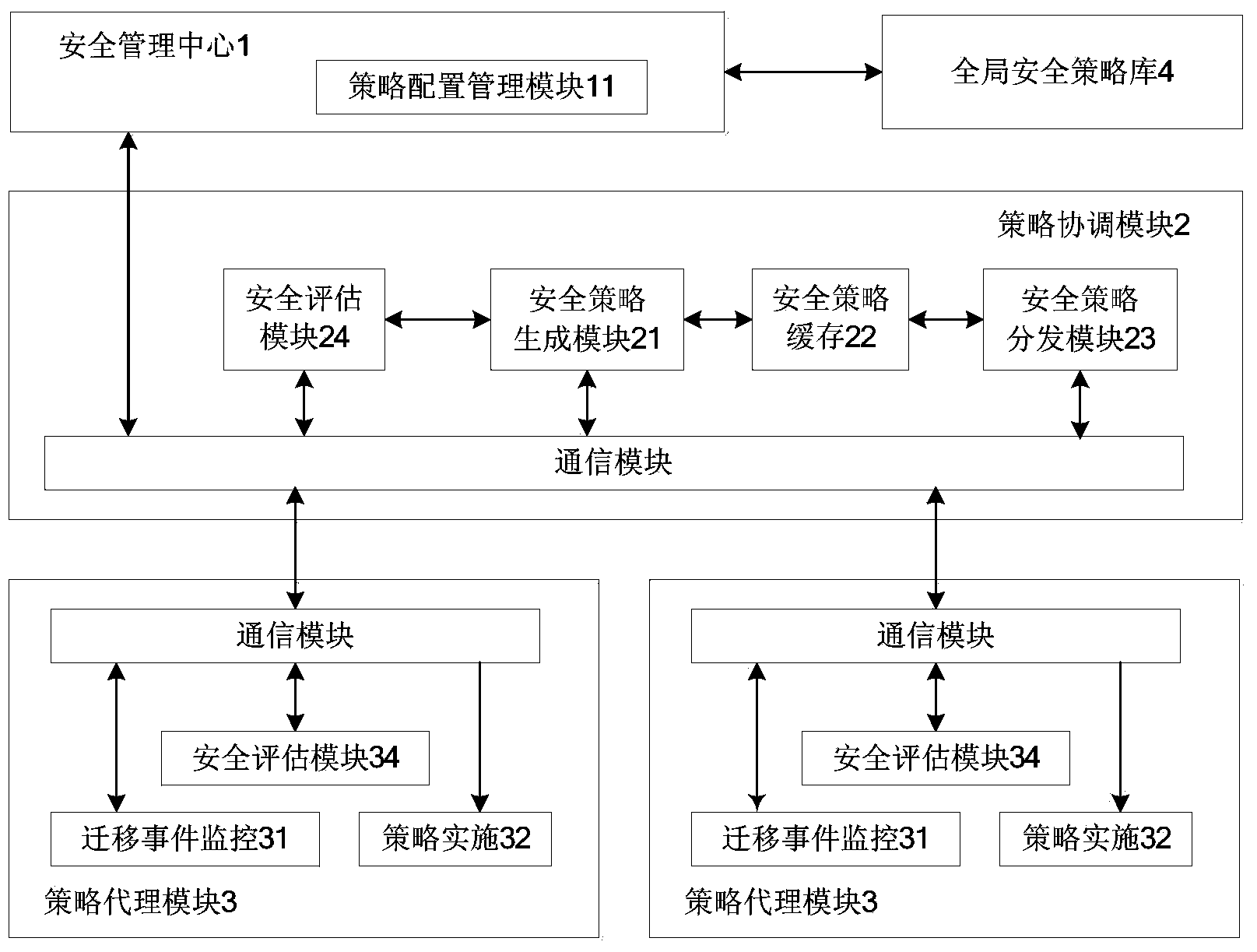
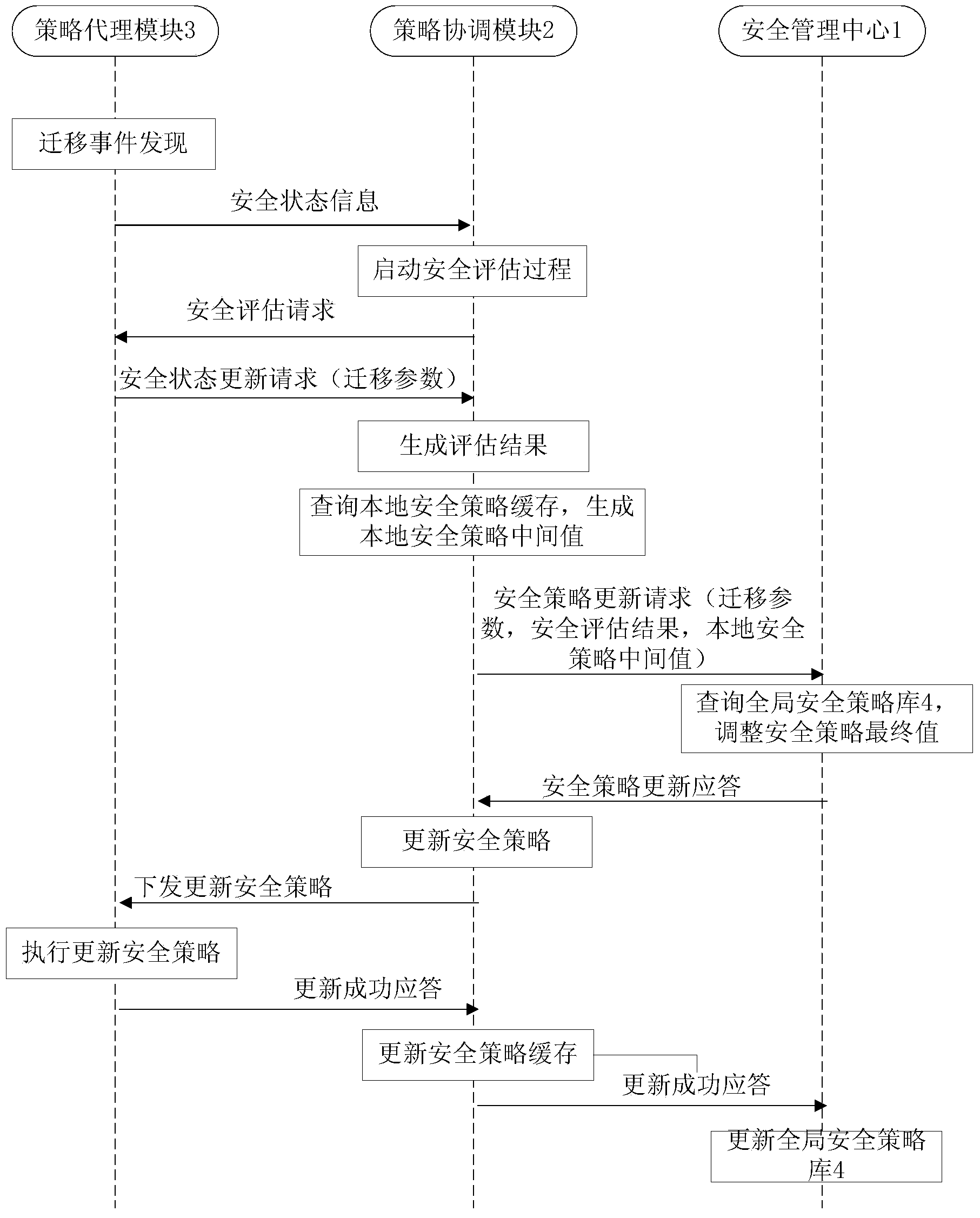
System and method for dynamically configuring virtual machine migration security policy
ActiveCN103457933AGet Service ContinuitySafety assessment method simplifiedTransmissionSecurity policySecurity management
The invention relates to a system and method for dynamically configuring a virtual machine migration security policy. A source host node and a target host node are both provided with strategy agent modules; a security policy database and a policy coordination module are respectively connected with a security management center; the policy coordination module is further connected with all the strategy agent modules; the security management center is used for inquiring the security policy database to judge whether a local security policy intermediate value violates a global security policy or not; if yes, the local security policy intermediate value is adjusted to be a security policy final value; if not, the local security policy intermediate value is set to be the security policy final value. Due to the fact that the global security policy is introduced in the process of generating the security policy final value, the security policy final value can violate the global security policy under no circumstances; after a virtual machine is migrated, a local security policy on the target host node is adjusted and brought into global security policy planning, and therefore the virtual machine is effectively prevented from lowering in security before and after migration.
Owner:CEC CYBERSPACE GREAT WALL
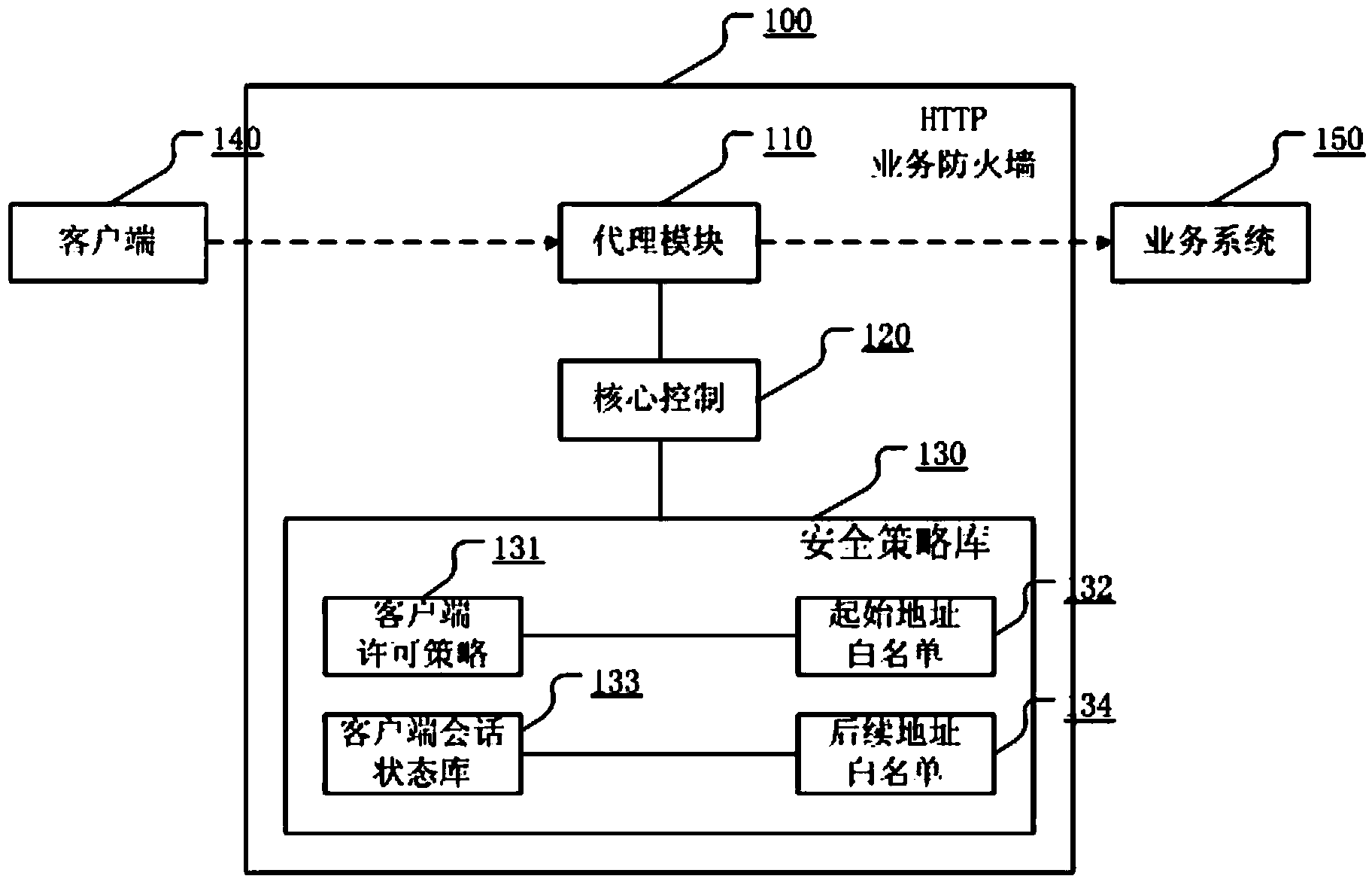
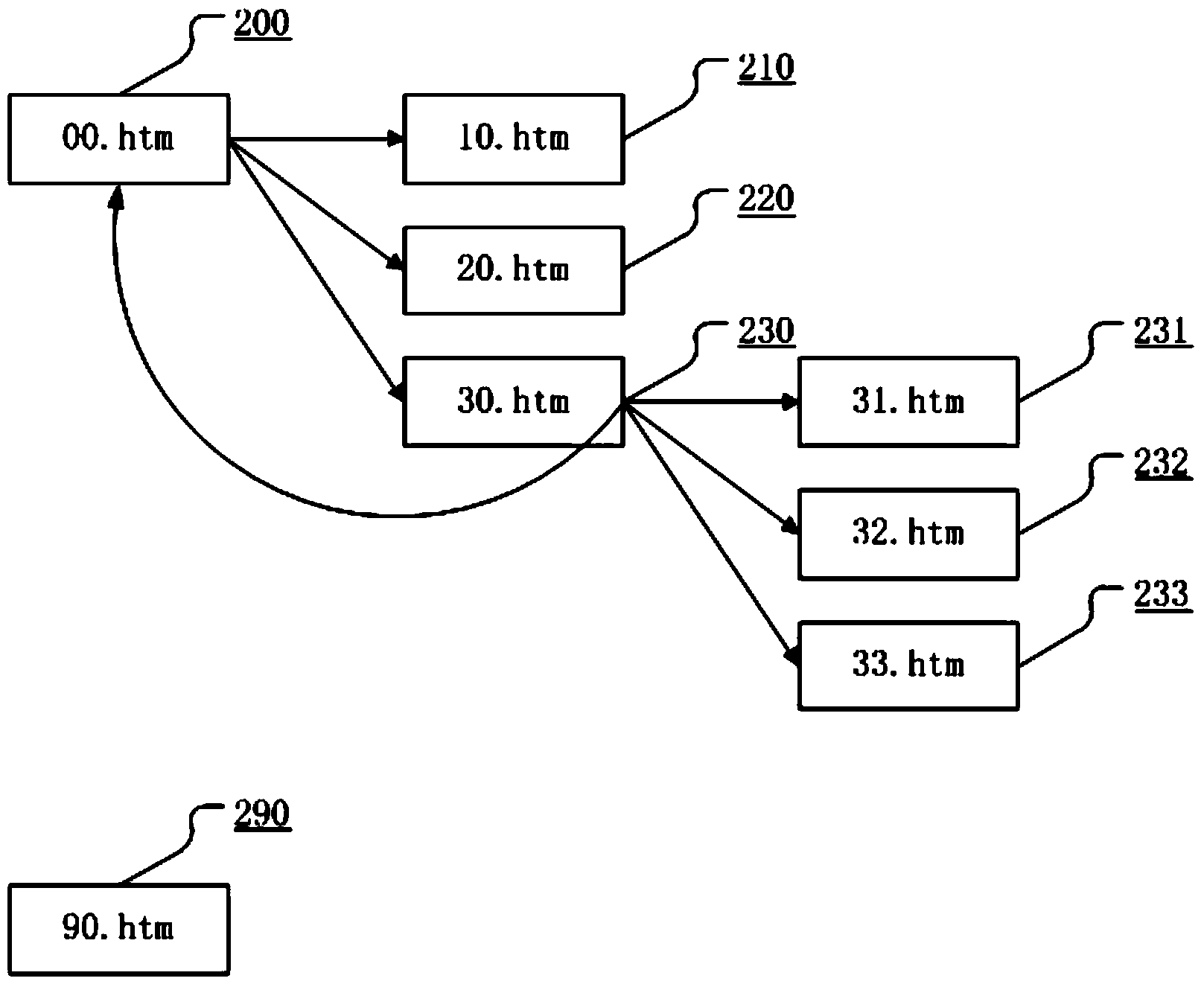
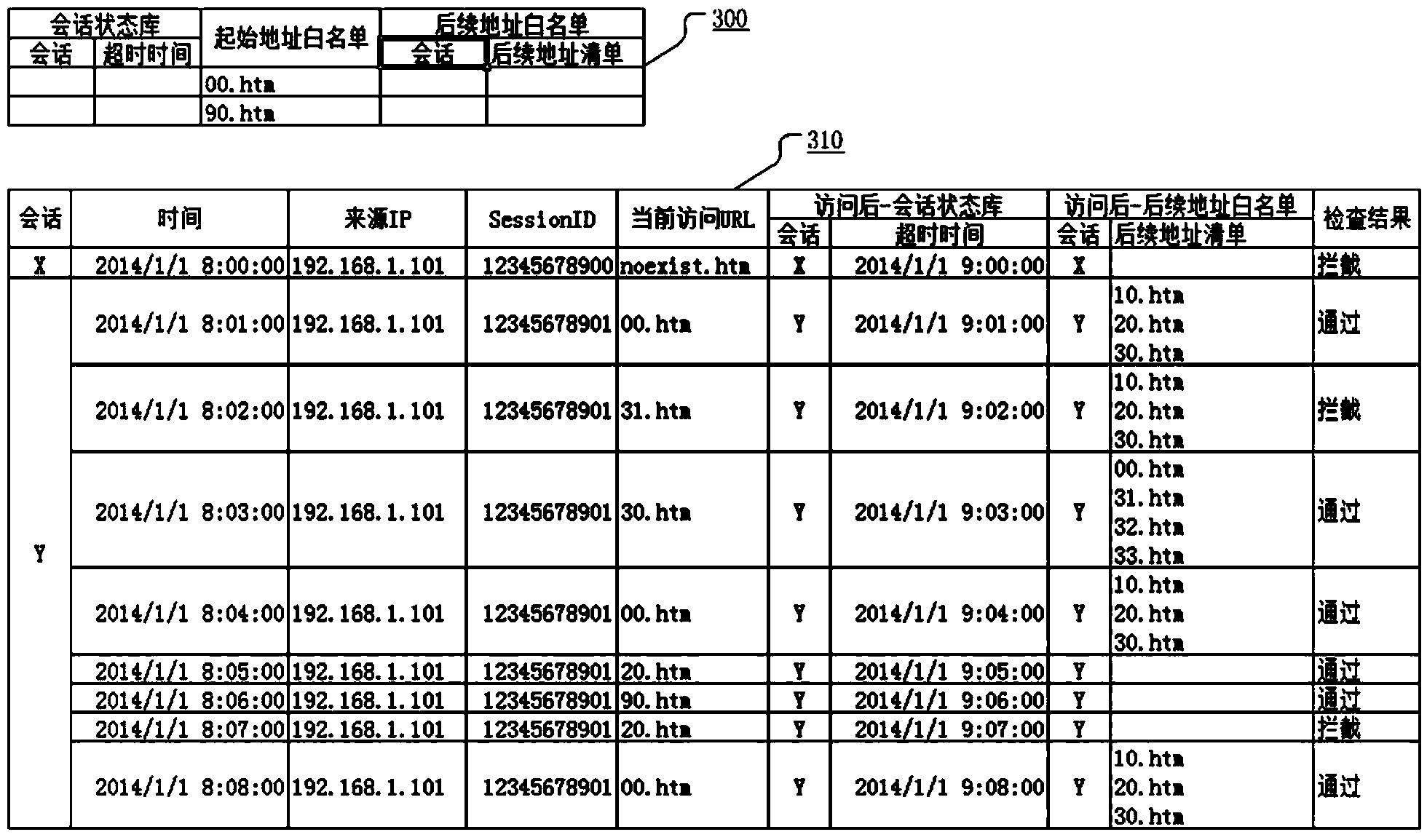
HTTP (Hyper Text Transport Protocol) service firewall based on adaptive agent mechanism
ActiveCN104394122AAccess as expectedEasy accessTransmissionComputer moduleHyper text transport protocol
The invention relates to the field of firewalls, and aims to provide an HTTP (Hyper Text Transport Protocol) service firewall based on an adaptive agent mechanism. The HTTP service firewall based on the adaptive agent mechanism comprises an agent module, a core control and a security policy database, wherein the agent module is used for accessing HTTP access from a client, acquiring various data, transmitting the acquired data to the core control, and performing execution after receiving a judgment conclusion of the core control; the core control is used for scheduling the cooperation of each module, receiving the request of each module, and updating data records, working modes and working methods in the security policy database; and the security policy database comprises a client permission strategy, a client session state database, a start address white list and a subsequent address white list. Through adoption of the HTTP service firewall, checking work on various security aspects of accidental access, accidental parameters, session parameter check, user associated data and the like needing to be considered in a protection system can be reduced, and the security level of the system is raised.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Internet of Things security defense system for intelligent terminal
The invention relates to the Internet of things security technology, and discloses an Internet of Things security defense system for an intelligent terminal for ensuring reliable operation and controllable security of cloud service of the intelligent terminal. The system comprises an Internet of Things security gateway deployed at a cloud service front end, the Internet of Things security gateway comprises a cloud service management module, an access terminal management module, an identity authentication module and a security policy database; the cloud service management module provides registration and management functions of all open cloud services; the access terminal management module provides registration and management functions of an access terminal; the identity authentication module is used for verifying the validity of the terminal after receiving a request of accessing the cloud service sent by the terminal; and the security policy database provides a corresponding security policy for providing security detection and network flow analysis functions after the request validity of the terminal is verified.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
High performance security policy database cache for network processing
A security policy database cache includes at least one primary table including signature values that indicate that a packet's security policy database information may be in the cache and at least one secondary table including cache entries having a selector, flags, security association information and an operation to perform on the corresponding packet for which a cache lookup was made.
Owner:REMEDIOS ALWYN DOS +3
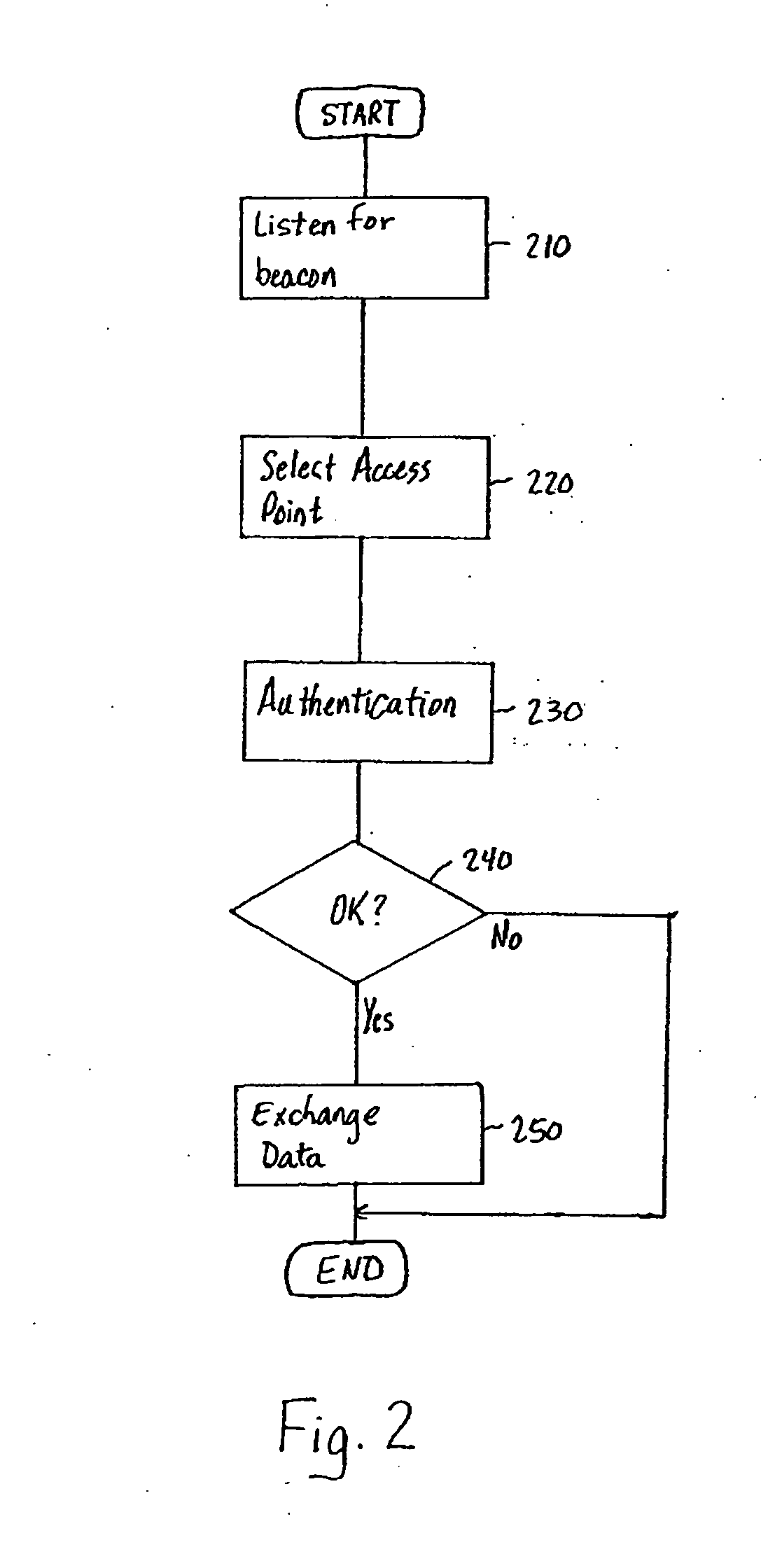
Security system for wireless networks
InactiveUS20060059538A1Good encryption algorithmSpecial data processing applicationsSecuring communicationTransport layerTransport control protocol
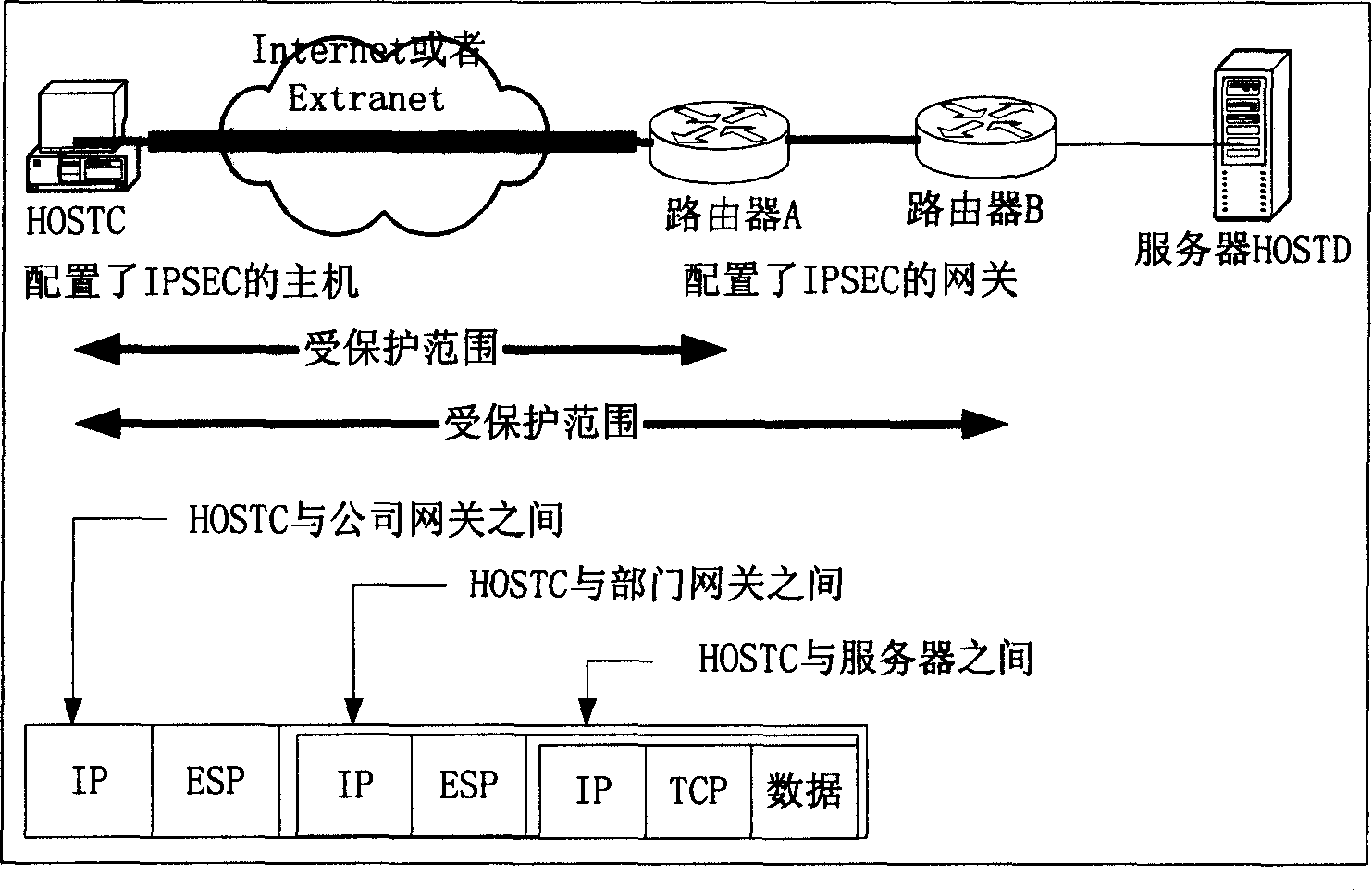
A security procedure for invoking IPsec security for communication of a packet in a network includes the steps of generating a message to be sent at the transport layer, building Internet Protocol and Transport Control Protocol headers for the message, selecting a security policy in accordance with a security policy database after the step of building Internet Protocol and Transport Control Protocol headers, and processing the packet according to the selected security policy.
Owner:XCOMM BOX
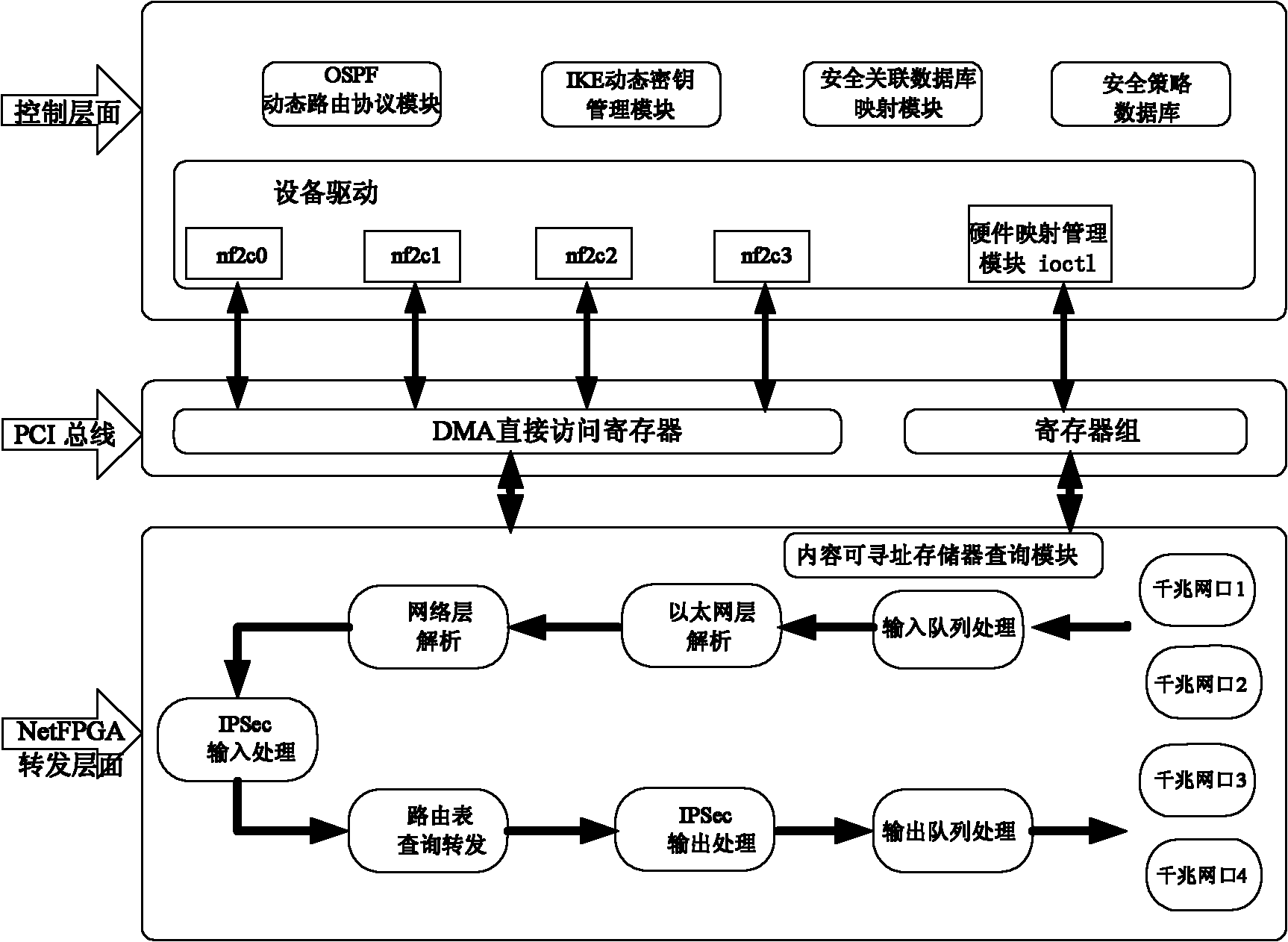
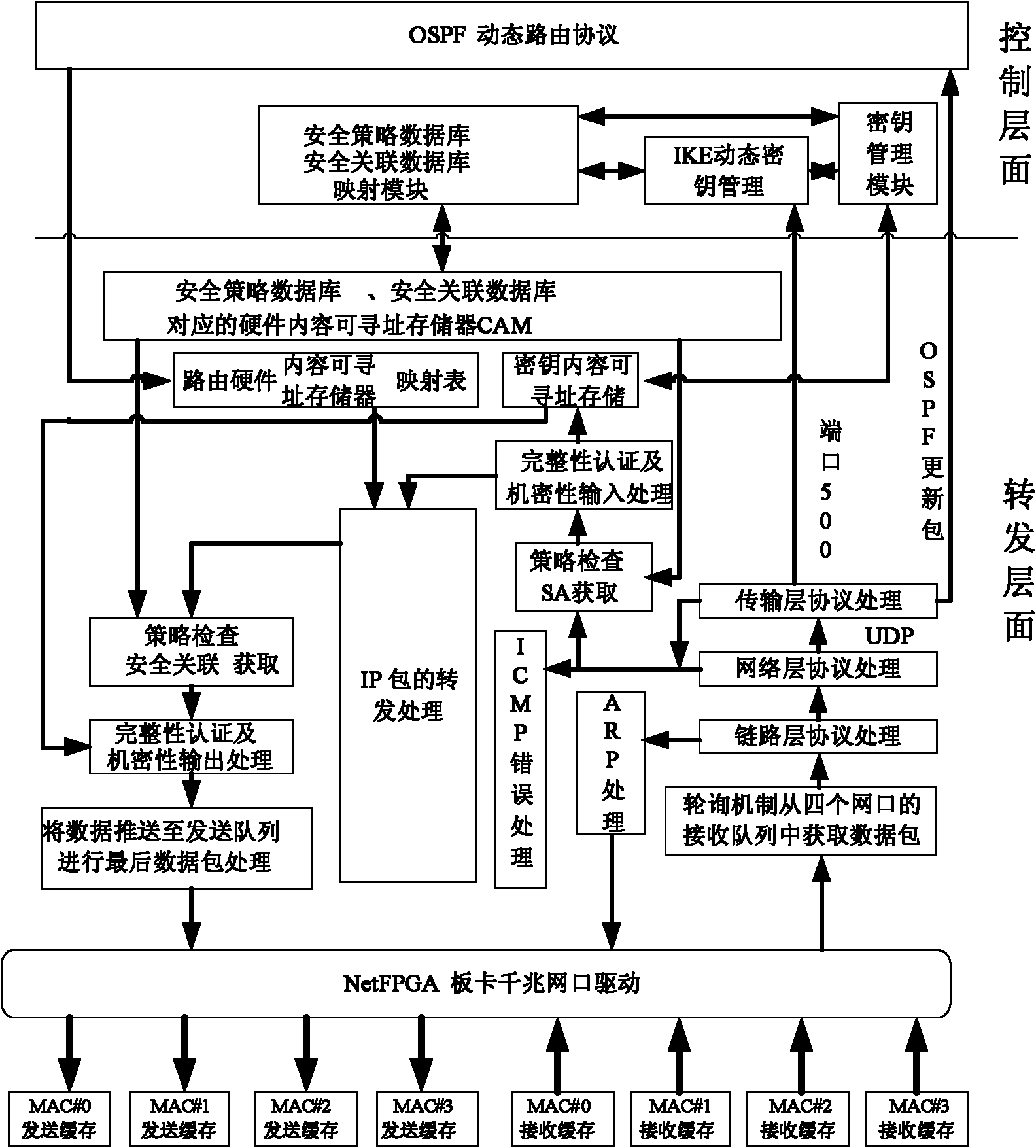
IPSecVPN (Internet Protocol Security Virtual Private Network) realizing system and method based on NetFPGA (Net Field Programmable Gate Array)
ActiveCN102065021AImprove processing speedRealize forwarding functionNetworks interconnectionData streamControl layer
The invention relates an IPSec VPN (Internet Protocol Security Virtual Private Network) realizing system and method based on a NetFPGA (Net Field Programmable Gate Array), wherein a control layer of a router is additively provided with an IKE (Internet Key Exchange) module, a security relation database mapping module and a security policy database, and a key management module is used for dynamically managing the key, the security relation and the security policy; and a forward layer is additionally provided with two independently designed IPSec input and output process modules in the originalNetFPGA standard router architecture by sufficiently utilizing the modularization reusable idea of a NetPGA development board. The scheme of the invention can realize the route forward function of the data flow in a hardware manner, and can also realize the great mass of calculation functions required by the IPSecVPN in a hardware manner, such as safe detaching / packing load and completeness authentication; in addition, the invention can effectively make a compromise on the data flow forward performance and the IPSec protocol processing performance.
Owner:北京地平线轨道技术有限公司
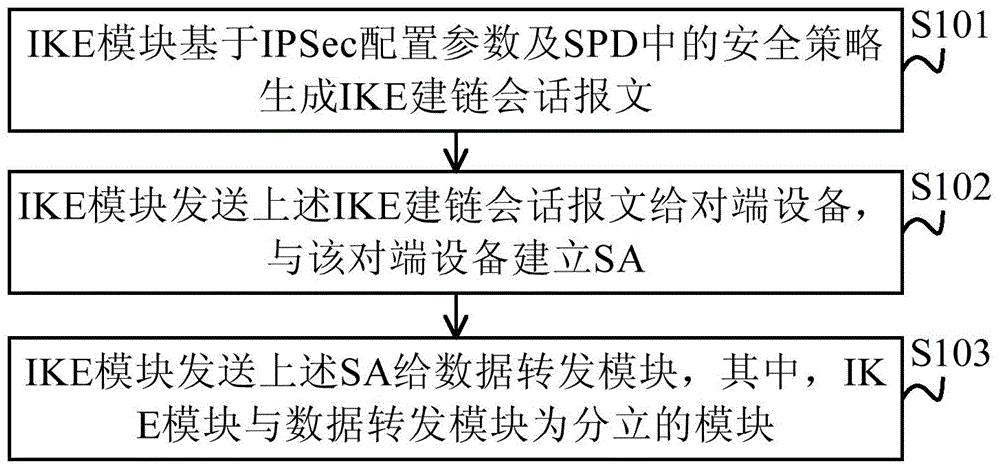
IPSec acceleration method, apparatus and system
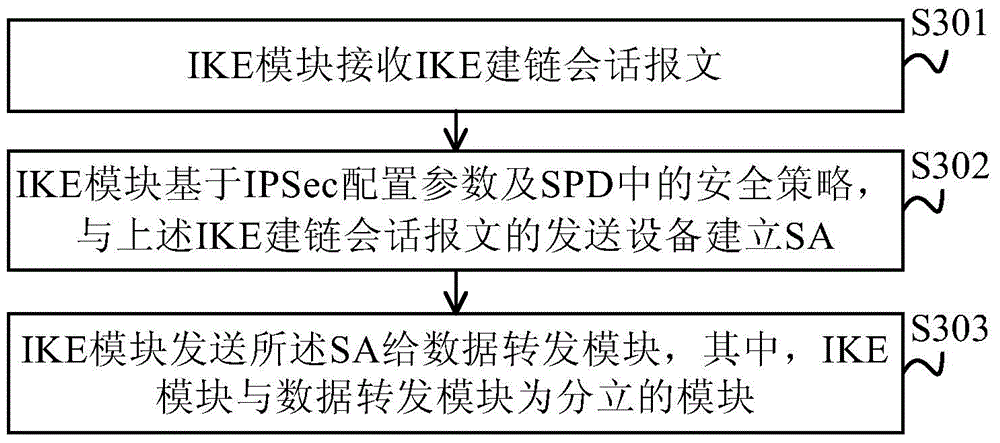
ActiveCN105991562AHigh speedIncrease flexibilityConnection managementSecuring communicationSecurity policySecurity policy database
The embodiment of the invention provides an IPSec (Internet Protocol Security) acceleration method, apparatus and system. The IPSec acceleration method includes the steps: an IKE (Internet Key Exchange) module generates an IKE chain building session message, based on an IPSec configuration parameter and a safety strategy in an SPD (Security Policy Database); the IKE module sends the IKE chain building session message to opposite-end equipment, and establishes SA (Security Association) with the opposite-end equipment; and the IKE module sends the SA to a data forwarding module, wherein the IKE module and the data forwarding module are discrete modules. The embodiment of the IPSec acceleration method, apparatus and system discretely sets the IKE module and the data forwarding module, so that the IKE module and the data forwarding module can be arranged in different equipment to improve the IPSec speed.
Owner:HUAWEI TECH CO LTD
IPSEC nesting strategy match correcting method
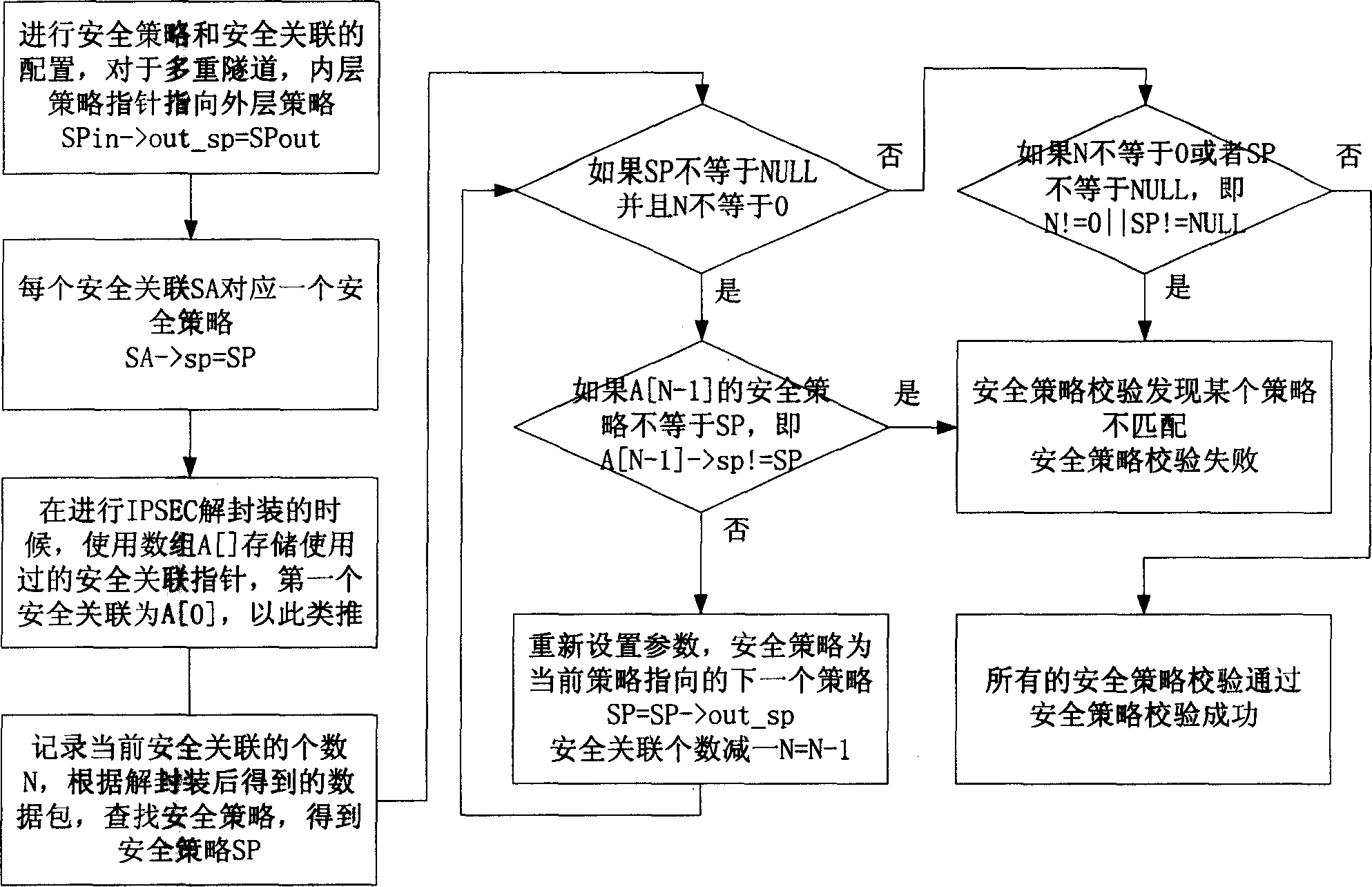
InactiveCN1529485AImprove verification efficiencySolve the problem of policy matching verificationUser identity/authority verificationData switching networksArray data structureSecurity association
For condition of multiple tunnel nest, associations are associated in format of doubly linked list or data array according to erosive precedence sequence. Based on content of data packet, strategy search is carried out. Strategy matching verification is carried out for each security strategy corresponding to a security association. The invention solves issue of strategy matching verification for IPSBC multiple tunnel-nested application. For condition of multiple tunnel nests, it is only needed to look up security strategy database once, and utilize association relationship between strategies to complete all operation for matching strategy. The invention raises efficiency for verifying security strategy and system performance.
Owner:ZTE CORP
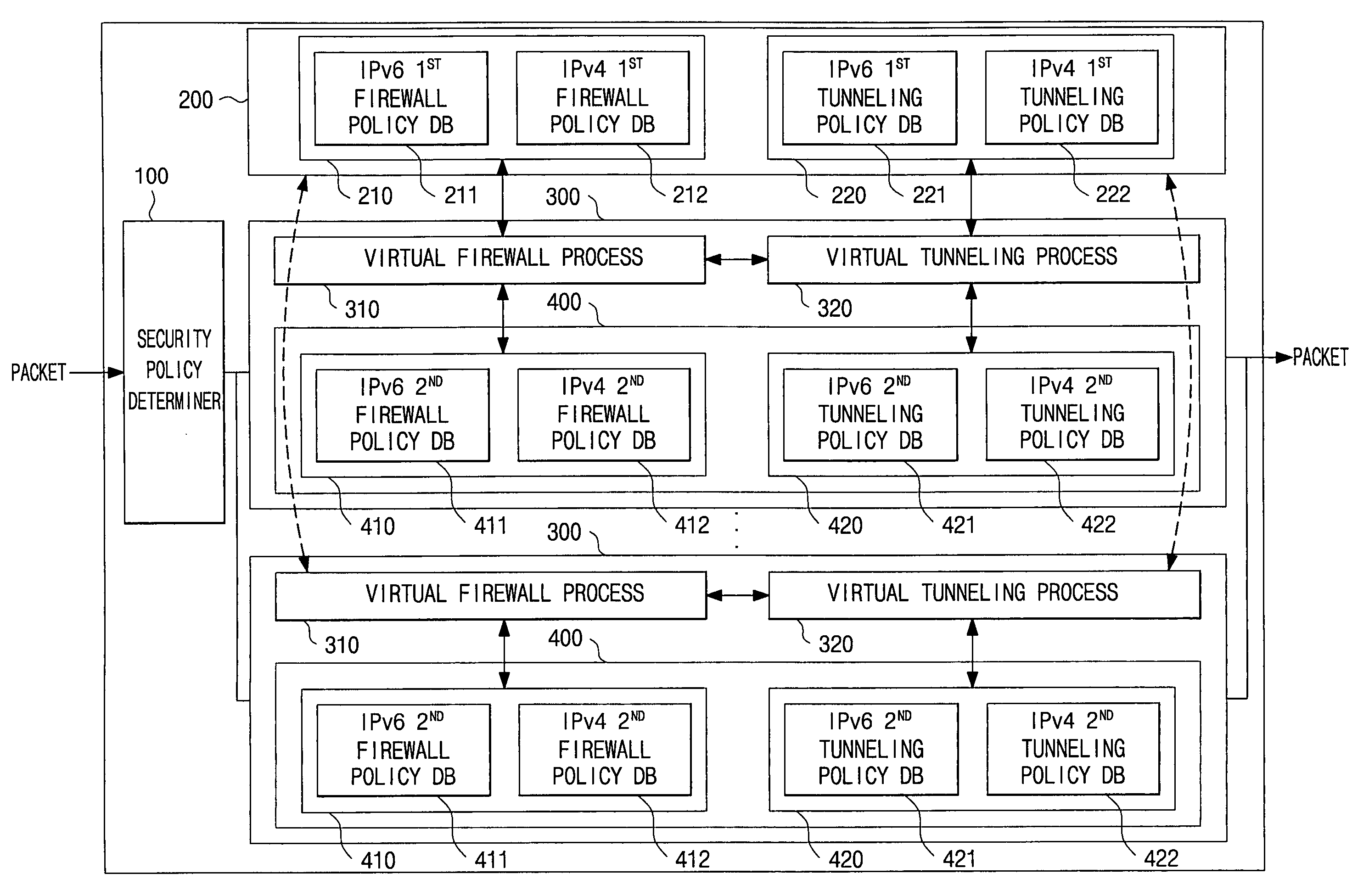
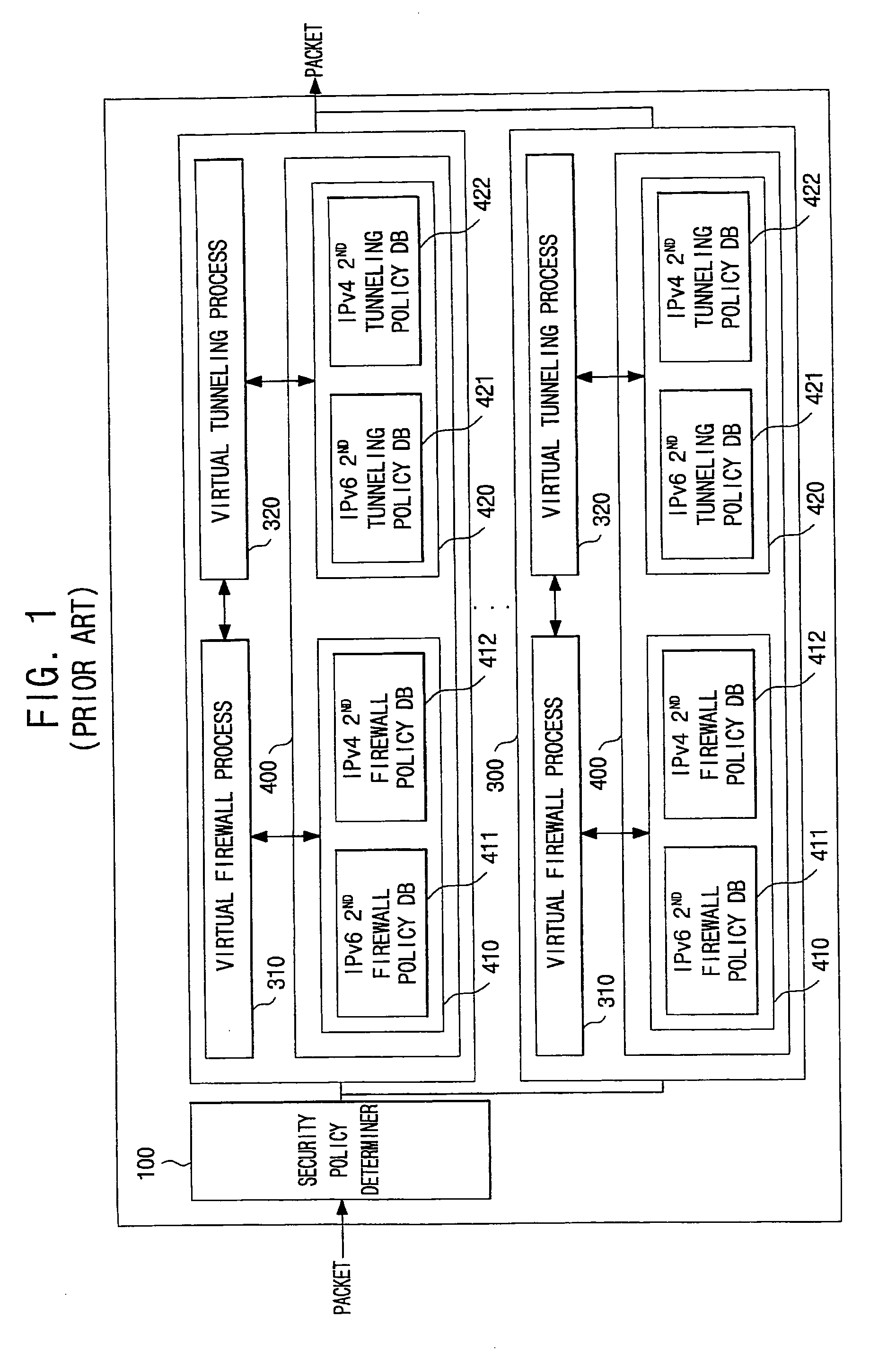
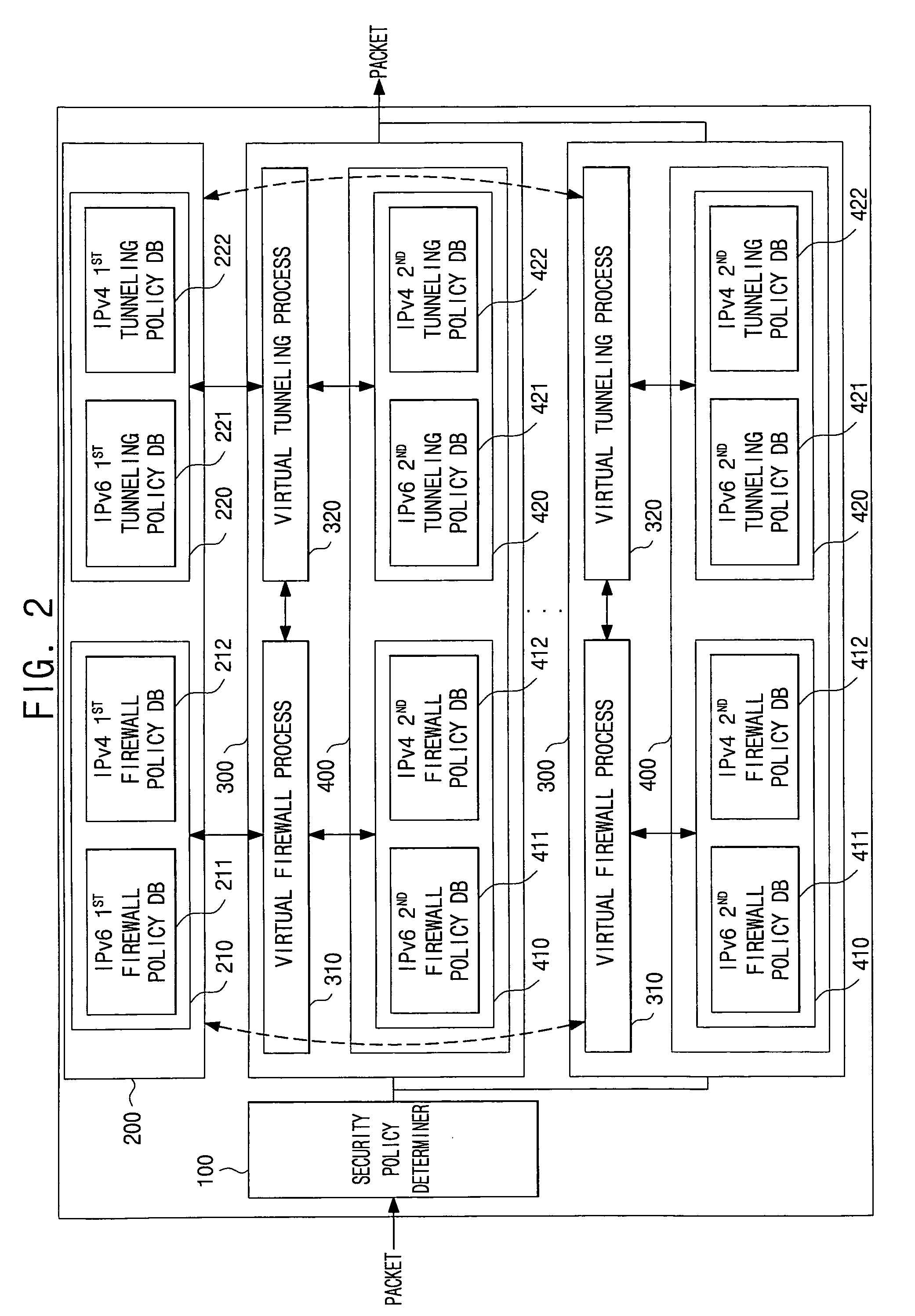
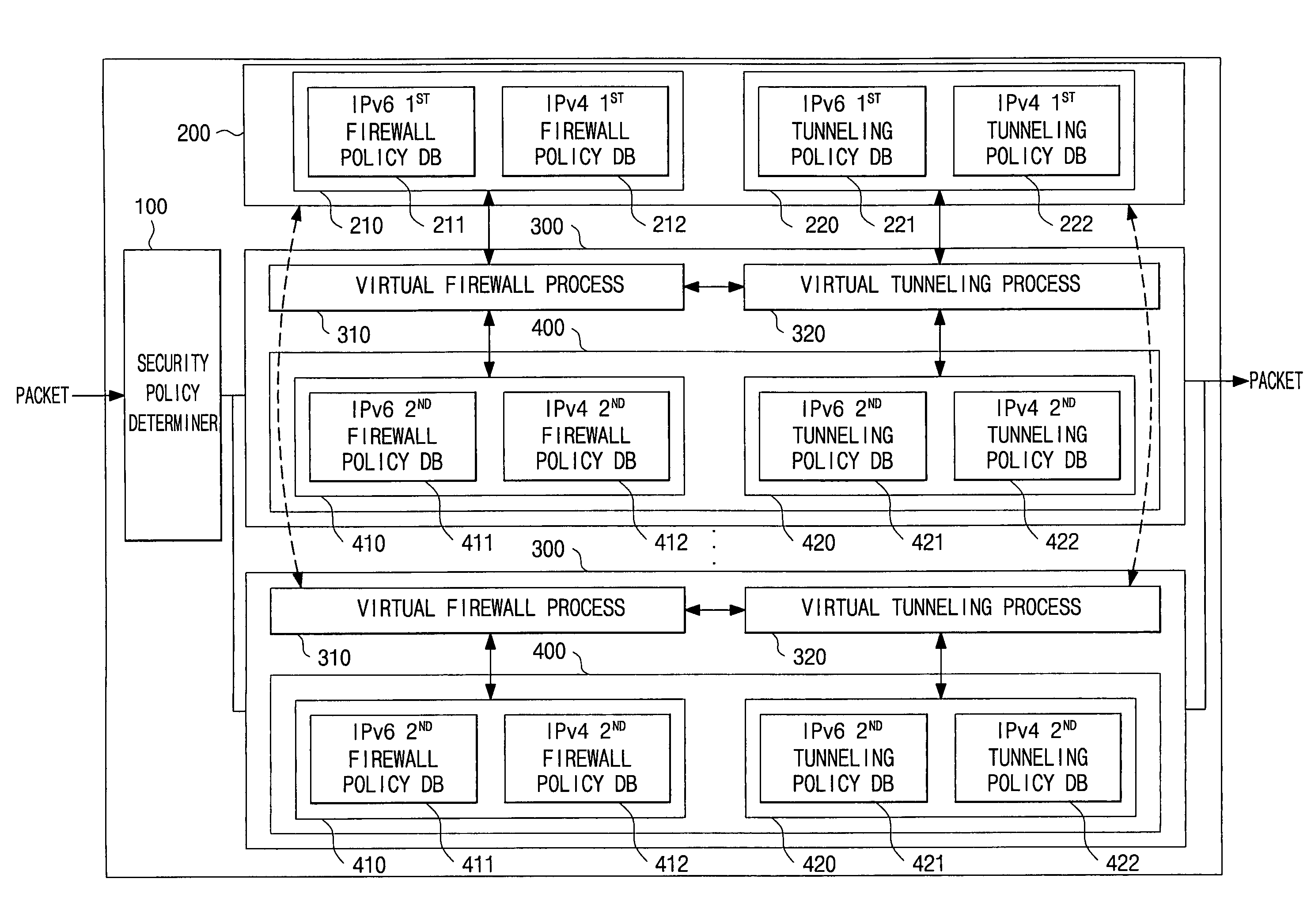
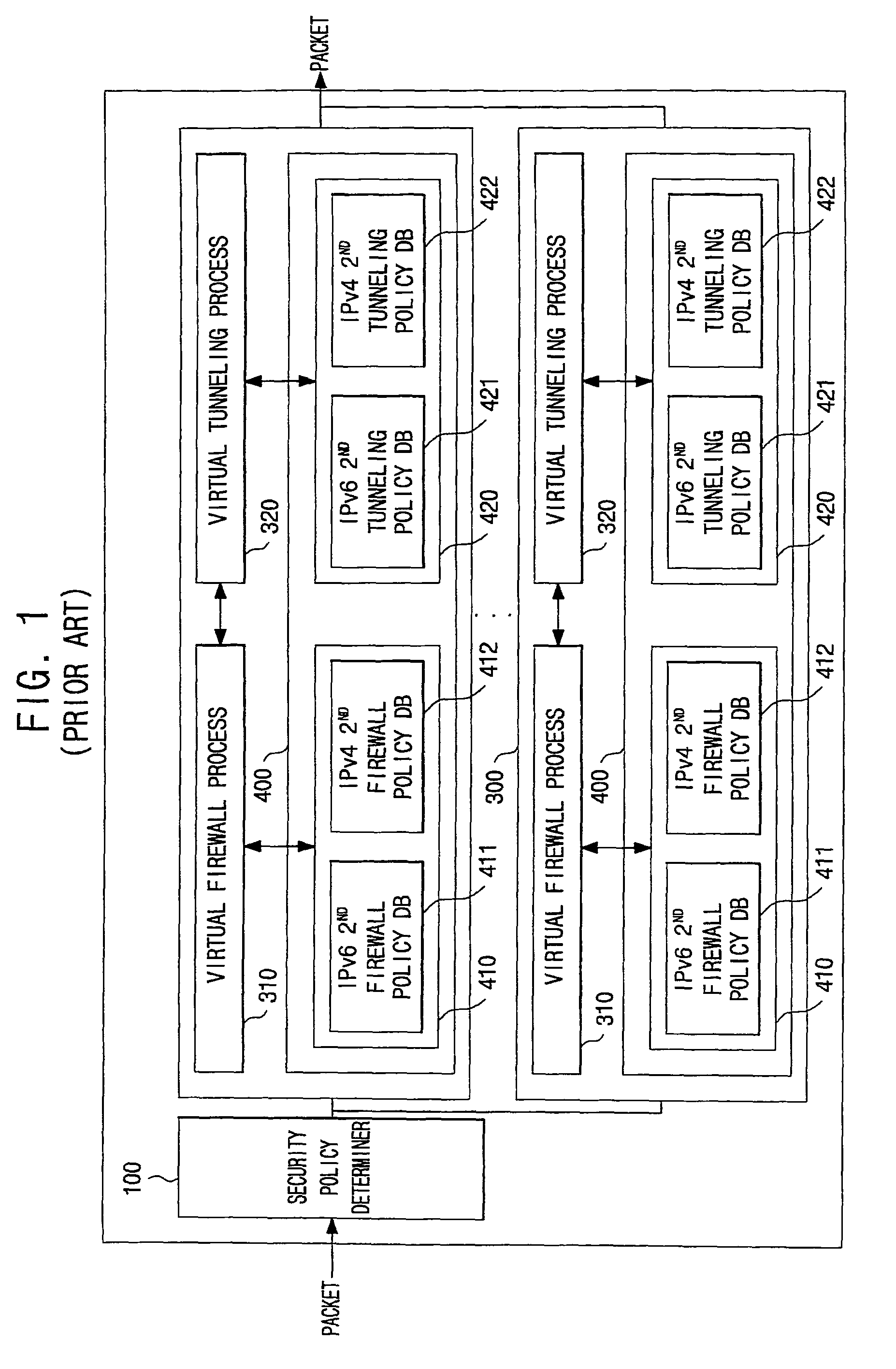
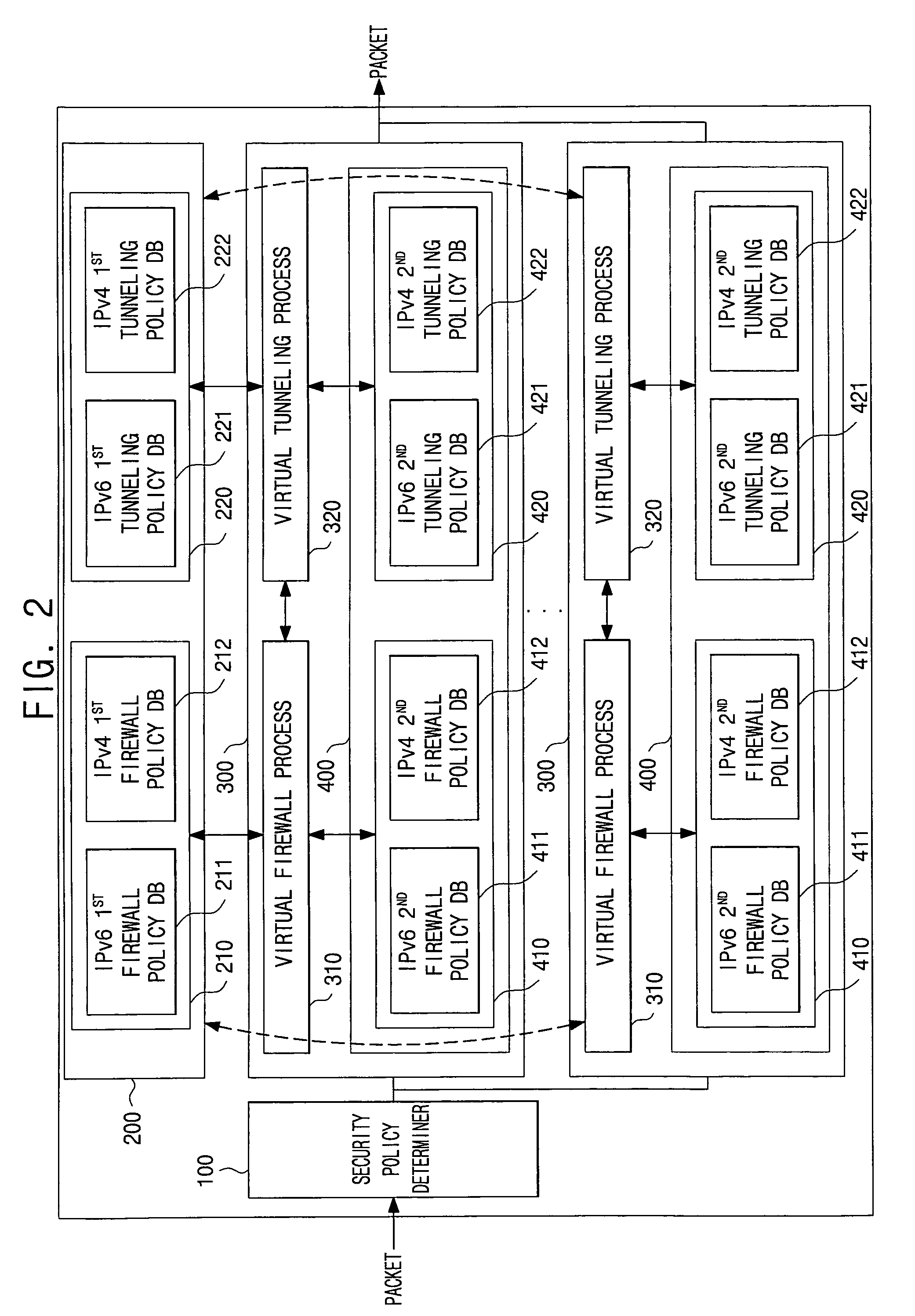
Virtual firewall system based on commons security policy and method of controlling the same
ActiveUS20090019518A1Easily and conveniently setEasily and conveniently and restoreData taking preventionData switching by path configurationData packVirtual firewall
A virtual firewall system based on a common security policy and a method of controlling the same. The virtual firewall system includes one or more virtual security policy modules, each of which includes a local security policy database; a security policy determiner, which determines, from the one or more virtual security policy modules, a virtual security policy module corresponding to a packet received from outside; and a common security policy database, which stores security policies. Each of the one or more virtual security policy modules determines whether or not to apply a security policy of the common security policy database to the received packet, and when the security policy of the common security policy database is applied, does not apply the security policy of a local security policy database. An operator can easily and conveniently set and restore the system.
Owner:SAMSUNG ELECTRONICS CO LTD
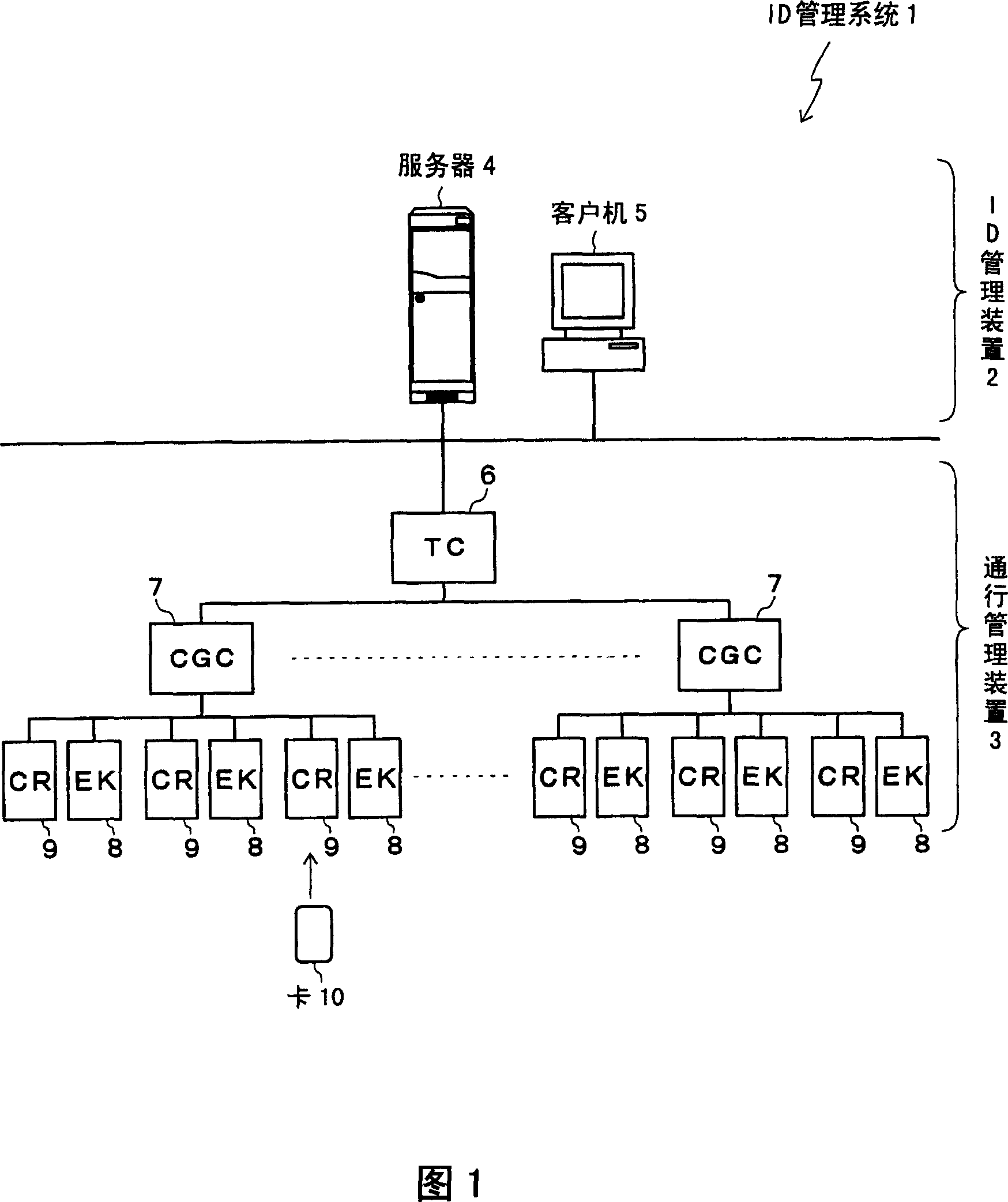
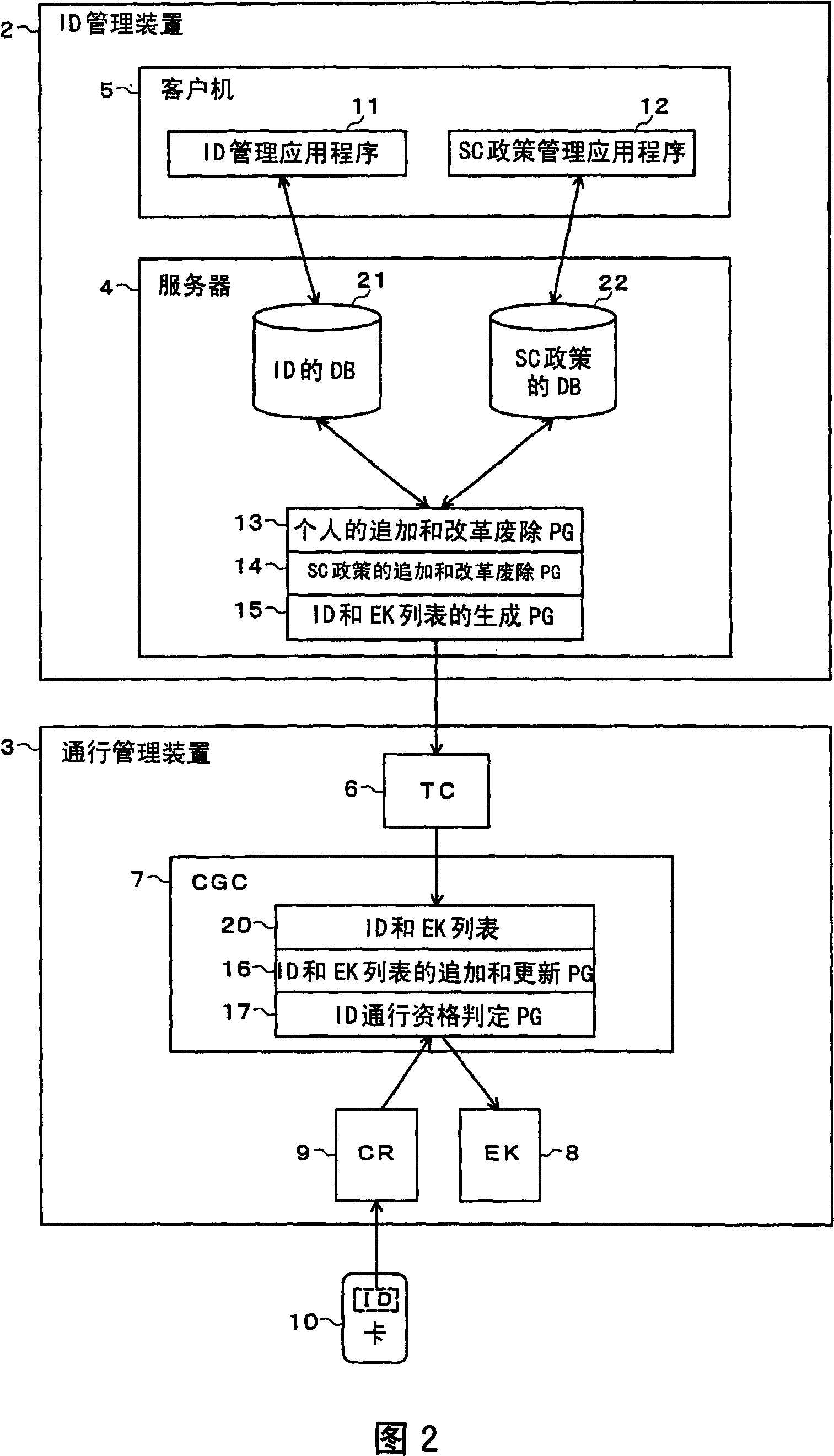
ID management device, ID management system and ID management method
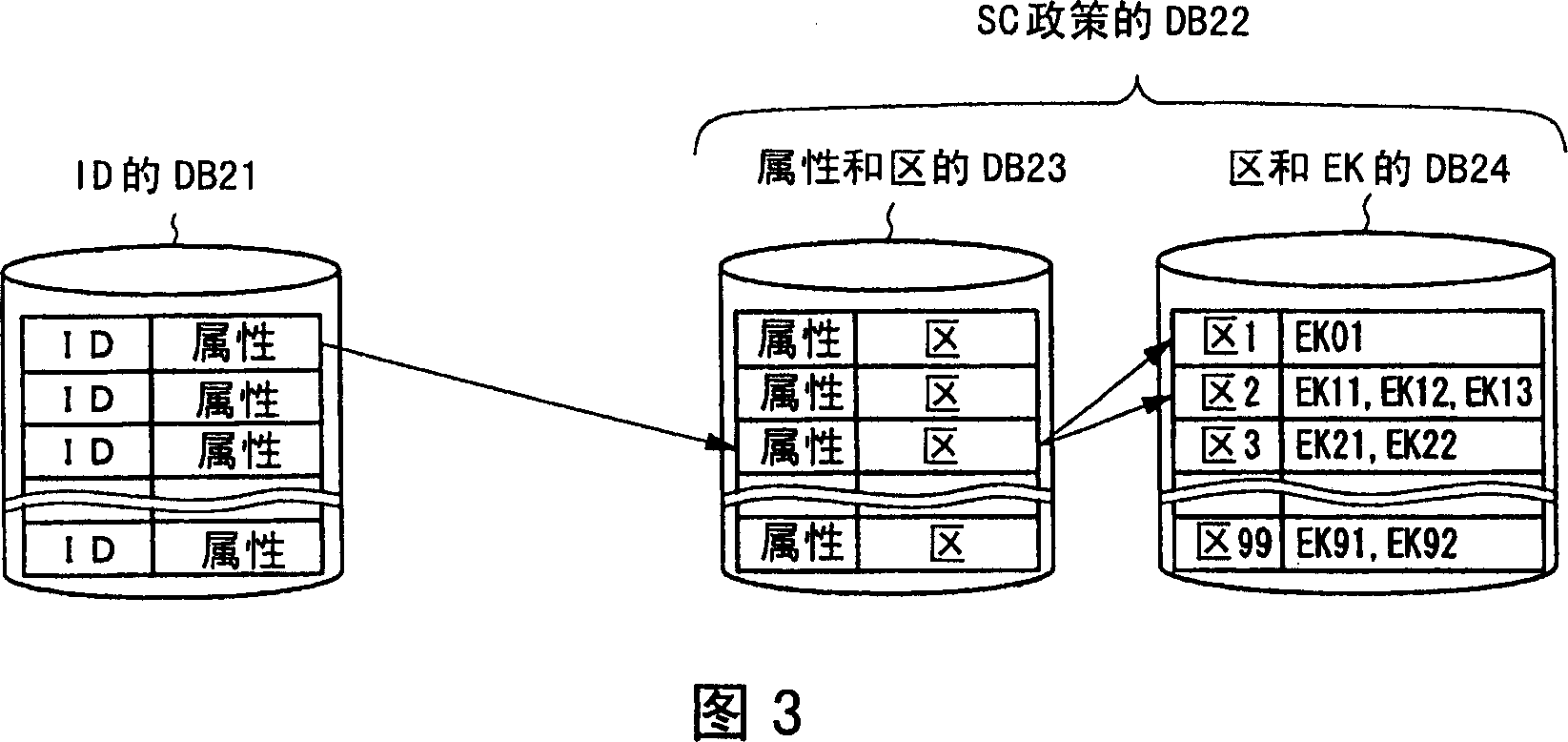
Saving the input personal identification ID and personal attribute information corresponding to the ID into a database 21 of ID. Saving the input personal attribute and region information corresponding to the attribute into the database 23 of regions and attributes contained in database 22 of a security policy. Saving the input region and the information of an electronic lock of gate setting corresponding to the access of region into the database 24 of regions and electronic locks contained in the database 22 of security policy. Then, generating data representing the personal ID and the list of ID and electronic locks of region gate that can pass with the ID from all informations of security policy database 22 and ID database 21, and setting the data in the toll bar gate control for controlling the locking and unlocking of electronic locks.
Owner:ORMON CORP
Searching device and method for Ethernet internet protocol security (IPSec) database
InactiveCN103198105AMeet the requirements for lookup performanceSolutionTransmissionSpecial data processing applicationsSecurity associationNetwork packet
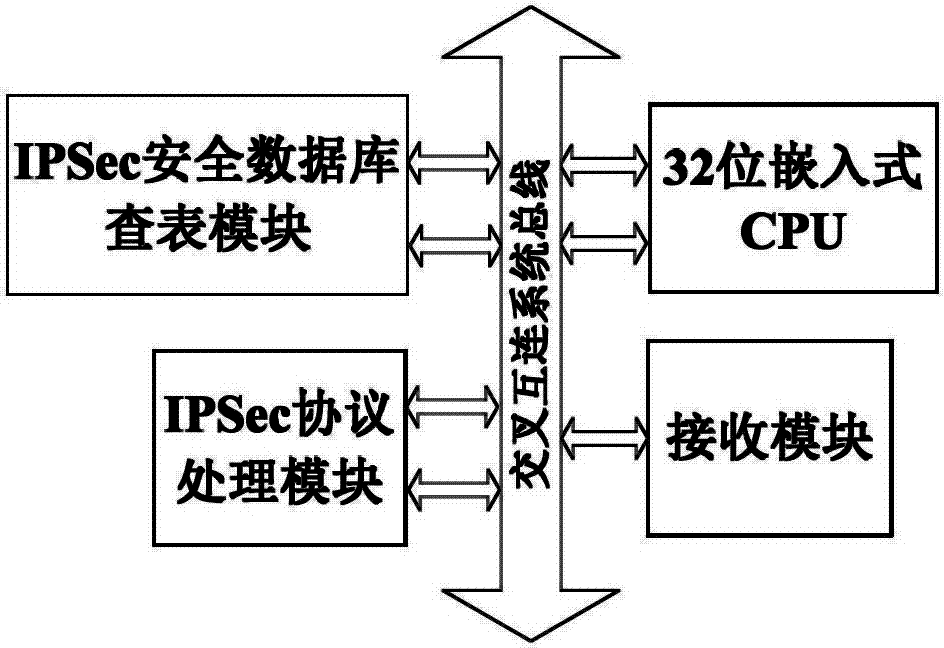
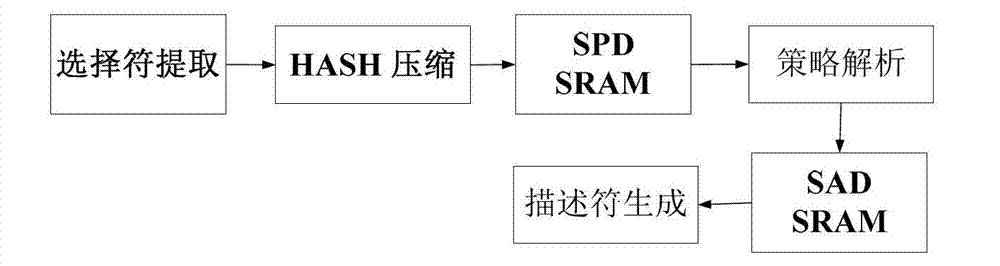
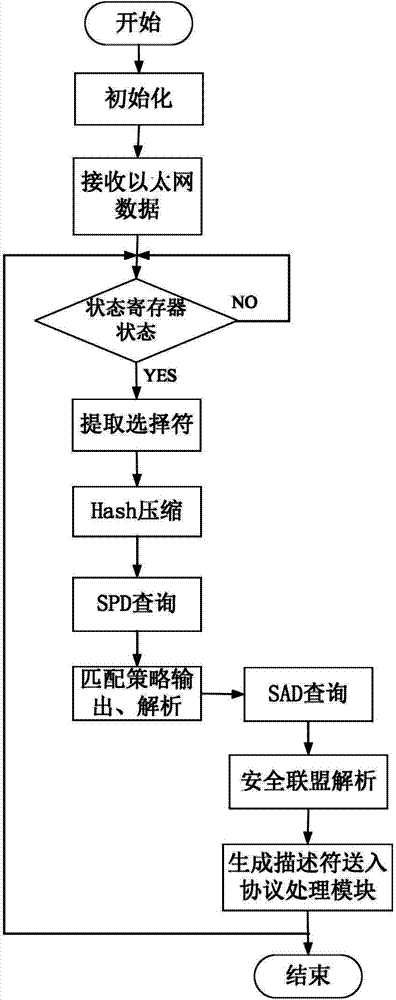
The invention discloses a searching device for an Ethernet IPSec database. According to the device, a processing unit configures a security database, a receiving module receives a data frame from the Ethernet and unpacks the data frame into an IP data packet, an IPSec database searching module conducts selector extraction and compression on the IP data packet unpacked by the receiving module, a compressed character serves as an input address of a security policy database (SPD) storage unit, the SPD storage unit outputs a security policy and submits the security policy to the IPSec database searching module for analysis, information that whether IPSec protocol processing is to be conducted or not and an input address of a security association database (SAD) storage unit can be obtained from the security policy, the SAD storage unit outputs a security association, and the IPSec database searching module analyzes the security association to generate a task descriptor. By the aid of the device, the requirements for high-speed searching can be met, and the security database can be configured simply and flexibly. The invention also discloses a corresponding security database searching method as well as a device and a method which are used for achieving Ethernet IPSec database searching.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Method for forwarding internet protocol security (IPSec)
InactiveCN102420769AIncrease bandwidth distributionImprove user experienceData switching networksQuality of serviceSecurity association
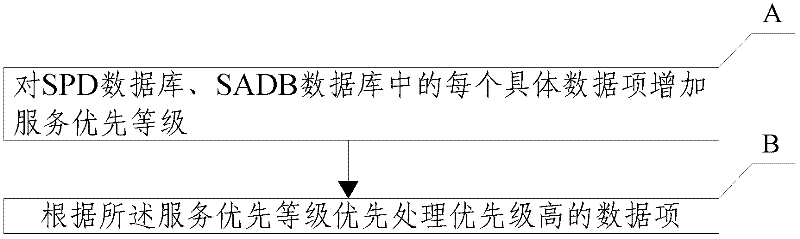
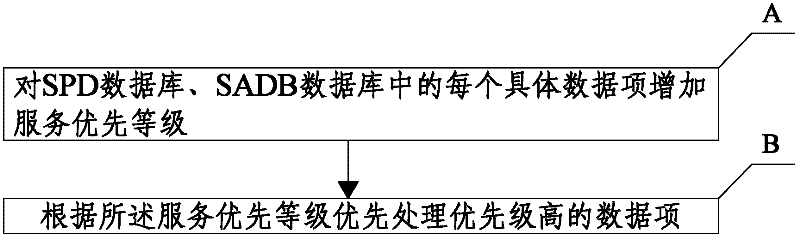
The invention discloses a method for forwarding internet protocol security (IPSec) and relates to the technical field of network security. The method comprises the following steps of: A, adding a service priority level to each specific data item in a security policy database (SPD) and a security association database (SADB); and B, according to the service priority level, performing priority processing on high-priority data items. The method for forwarding the IPSec has the advantages that: according to the situation of network flow and the size of the priorities of users, the bandwidths of the users with different priorities are dynamically changed; by improving the bandwidth distribution of high-priority users, using experiences of the high-priority users are improved; installation of quality of service (QoS) equipment is not required for network equipment without a QoS function; and cost is reduced.
Owner:OPZOON TECH
Packet communication system
InactiveUS7861080B2Easy to useImprove security levelNetwork traffic/resource managementDigital computer detailsGroup communication systemsComputer network
A packet communication system for effectively using network resources and for improving network operability. A transmission security policy database specifies the omission of header information attached when a transmission packet is capsulated, as a transmission security policy. A header-information omitting section omits the header information of the capsulated transmission packet. A packet transmission processing section adds a security header and a header for tunnel communication to the packet from which the header information has been omitted and transmits the packet. A receiving security policy database specifies that the header information has been omitted, as a receiving security policy. A header-information recovering section searches the receiving security policy database for a security policy for a received packet, and when recognizing that the received packet is a target packet from which the header information has been omitted, recovers the header information.
Owner:FUJITSU LTD
Analyzing security compliance within a network
ActiveUS8898734B2Error preventionFrequency-division multiplex detailsSecurity complianceNetwork model
A security policy database identifies the intended security policies within a network, a traffic generator provides test traffic that is configured to test each defined security policy, and a simulator simulates the propagation of this traffic on a model of the network. The model of the network includes the configuration data associated with each device, and thus, if devices are properly configured to enforce the intended security policies, the success / failure of the simulated test traffic will conform to the intended permit / deny policy of each connection. Differences between the simulated message propagation and the intended security policies are reported to the user, and diagnostic tools are provided to facilitate identification of the device configuration data that accounts for the observed difference. Additionally, if a network's current security policy is unknown, test traffic is generated to reveal the actual policy in effect, to construct a baseline intended security policy.
Owner:RIVERBED TECH LLC
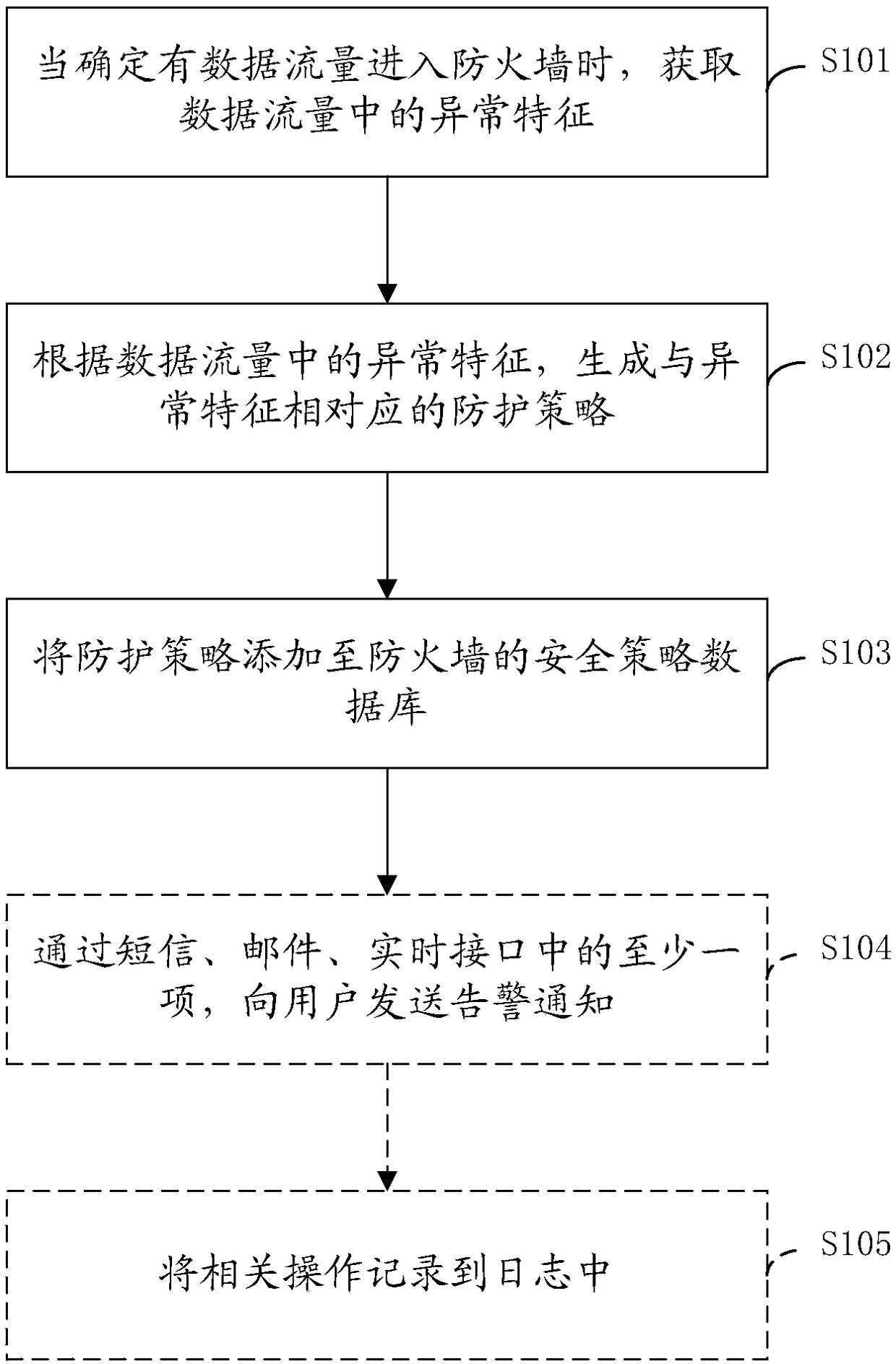
Method and device for adjusting defense strategy of firewall
The invention provides a method and a device for adjusting a defense strategy of a firewall, and relates to the technical field of network security. The method provided by the embodiment of the present application can generate the defense strategy corresponding to abnormal features in a current network in time according to a current network condition, and enable the defense strategy. Therefore, the firewall can actively sense network anomalies and adjust the defense strategy according to the network anomalies. The method comprises the following steps of: acquiring the abnormal features in a data traffic when it is determined that the data traffic enters the firewall; generating the defense strategy corresponding to the abnormal features according to the abnormal features in the data traffic; and adding the defense strategy to a safety strategy database of the firewall. The method and the device is applied to adjusting the defense strategy of the firewall.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
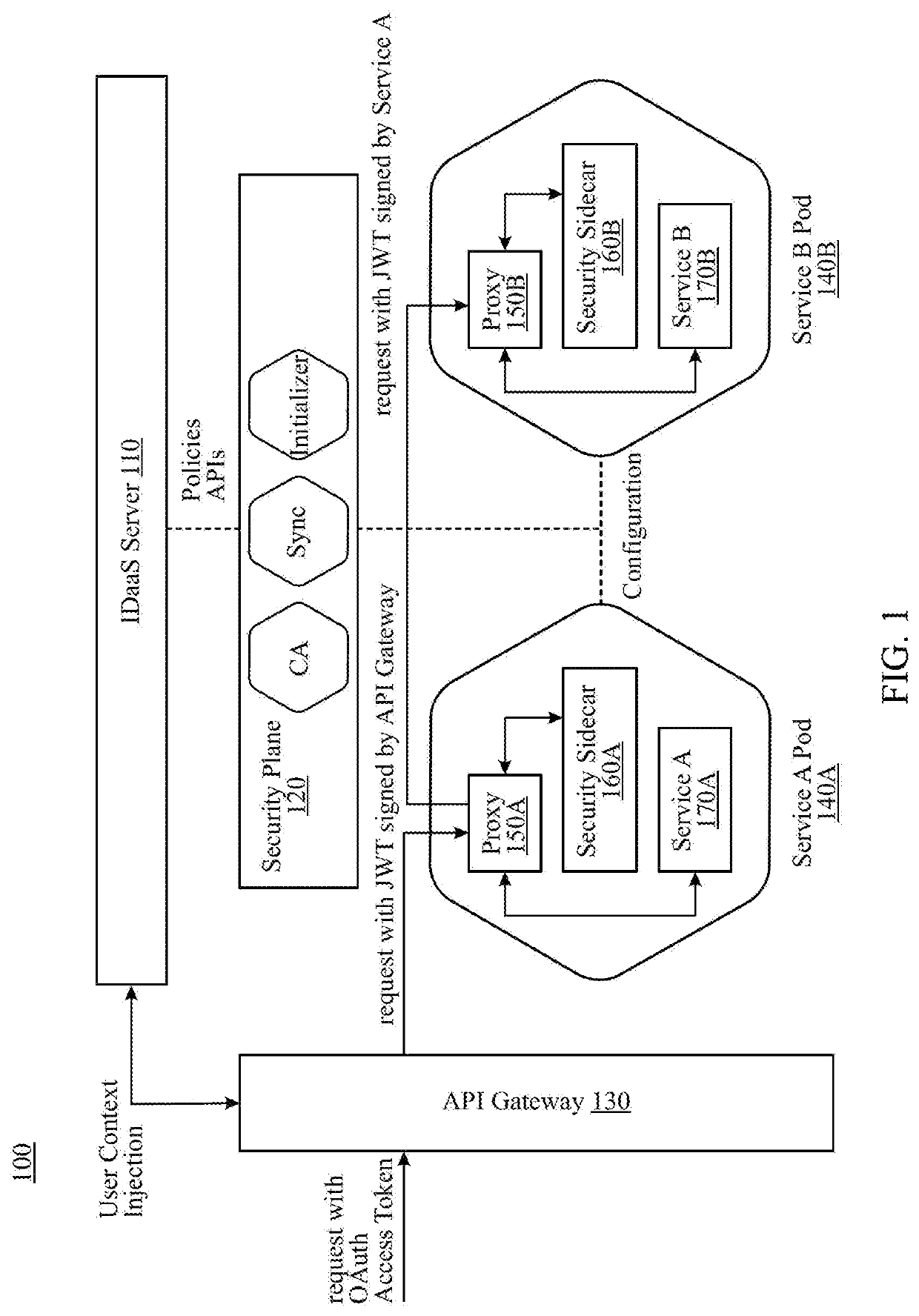
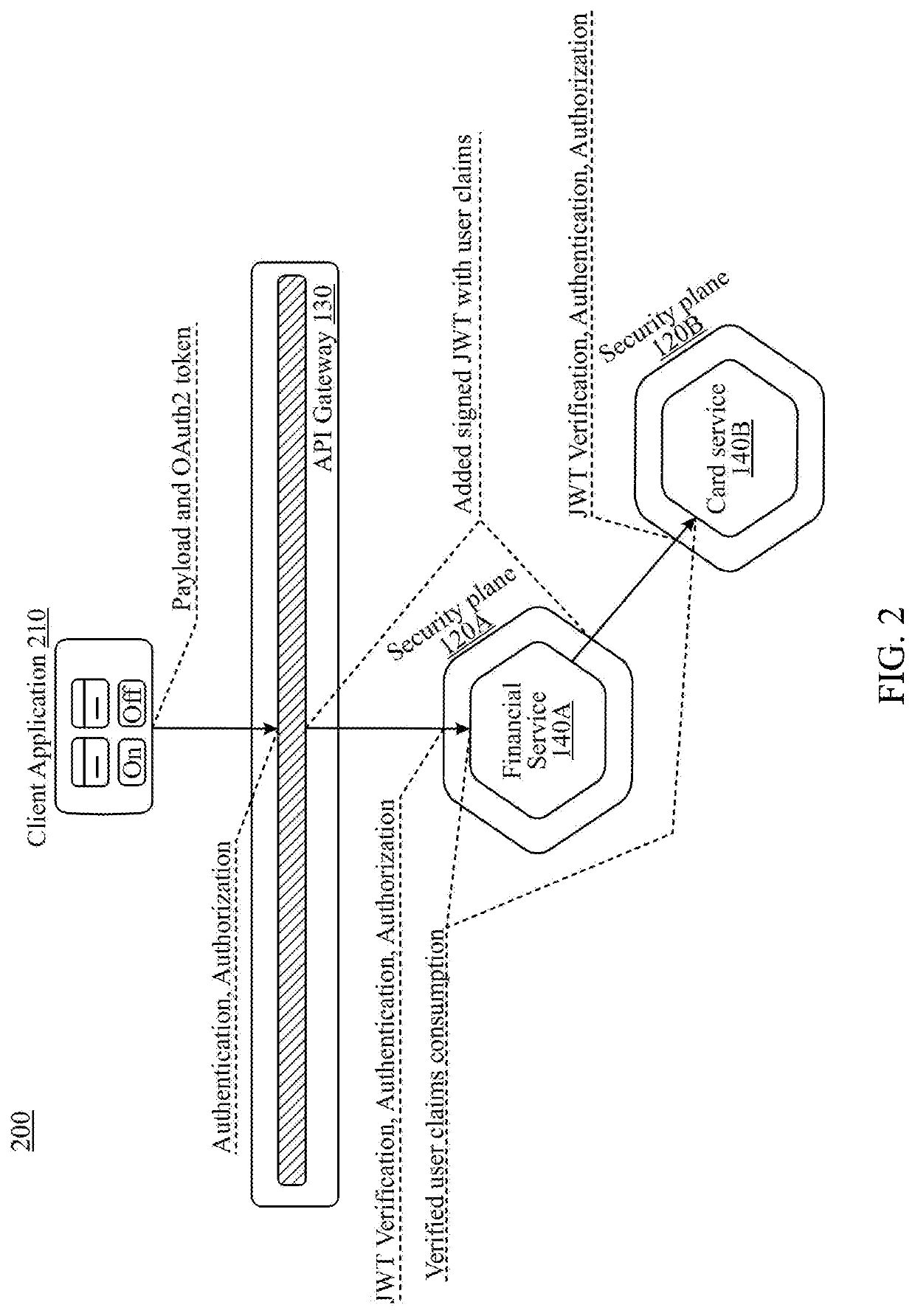
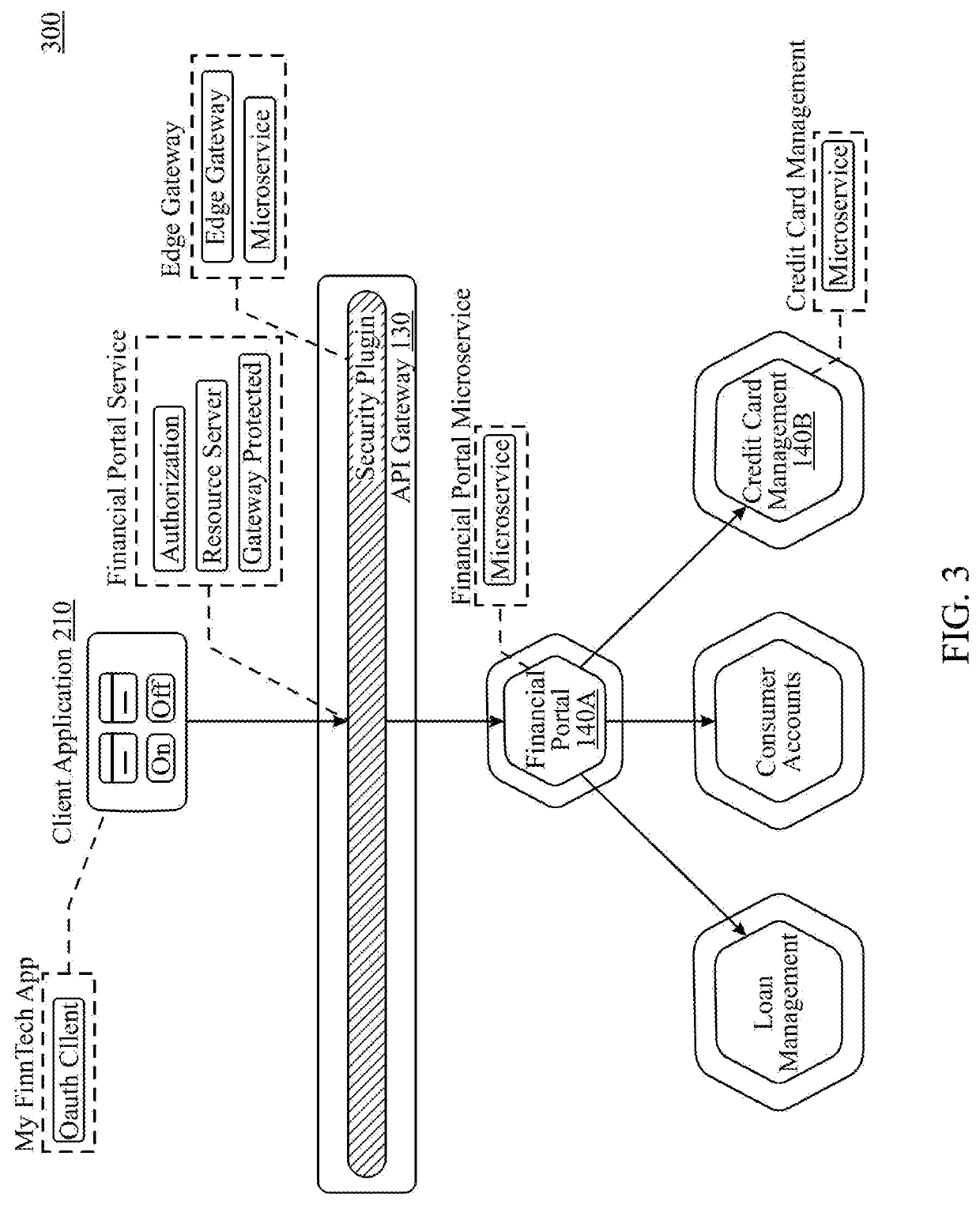
Microservice architecture for identity and access management
Systems and methods for identity and access management are provided in a service mesh that includes a plurality of interconnected microservices. Each microservice is associated with a microgateway sidecar. The associated microgateway sidecar may intercept a request for the associated microservice sent over a communication network from a user device. Such request may include data regarding a context of the request. A token associated with the request may be enriched based on the context data and sent to at least one other microservice. A database of security policies for each of the microservices may be maintained. An authentication engine may generate a risk profile for the request based on the context data of the request and one or more of the security policies in the database. One or more of a plurality of available security workflows may be selected based on the risk profile.
Owner:SYNTEGRITY NETWORKS INC
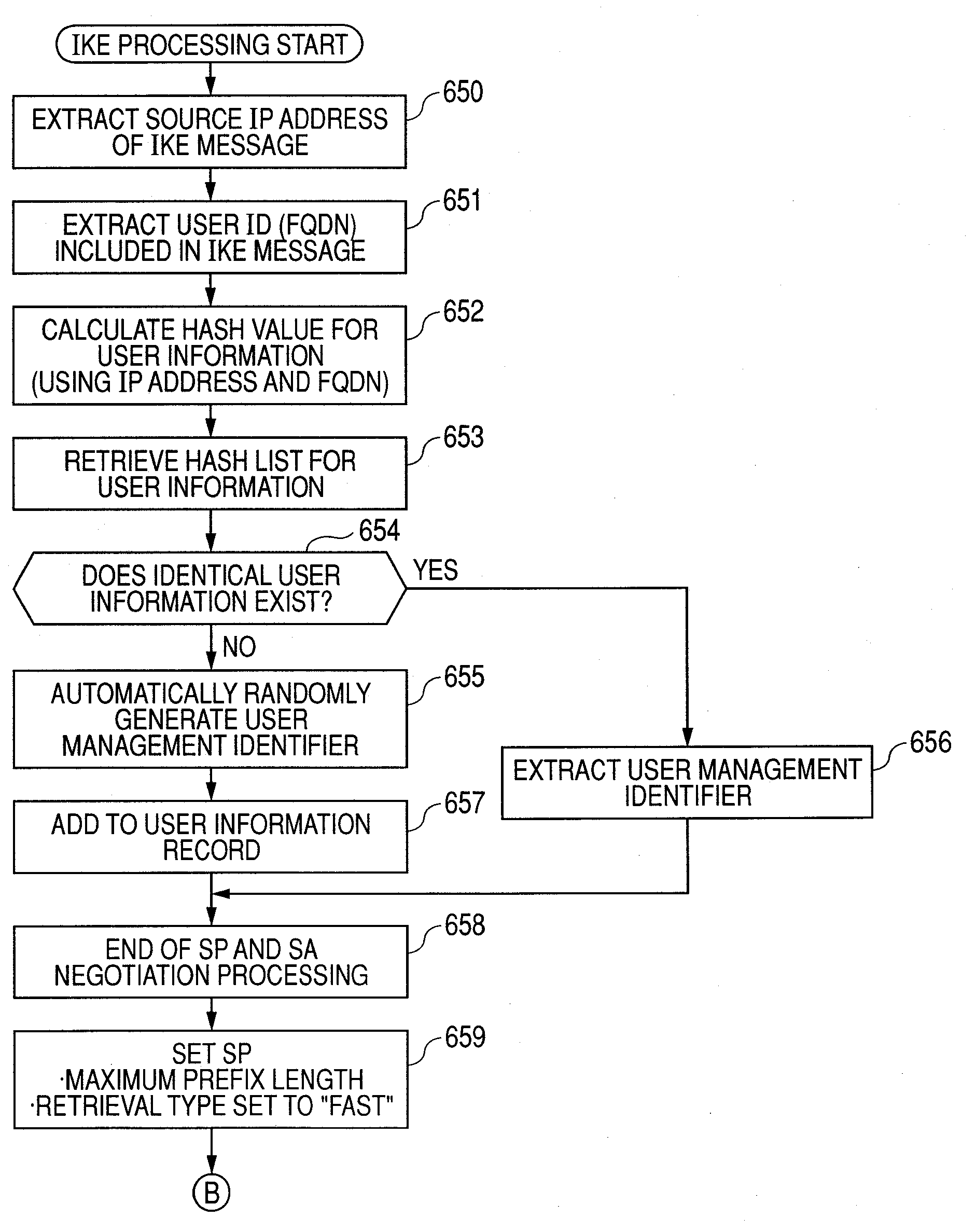
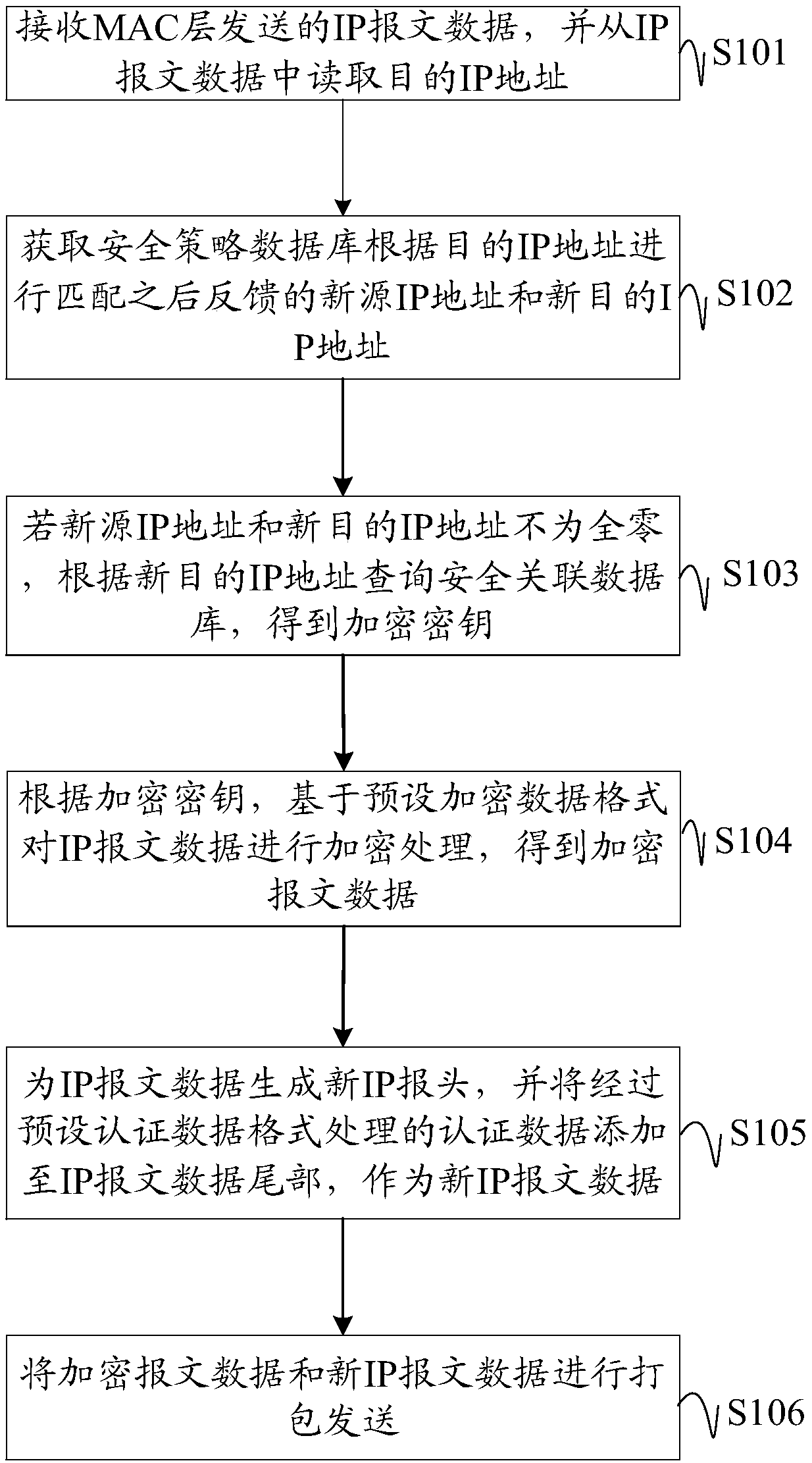
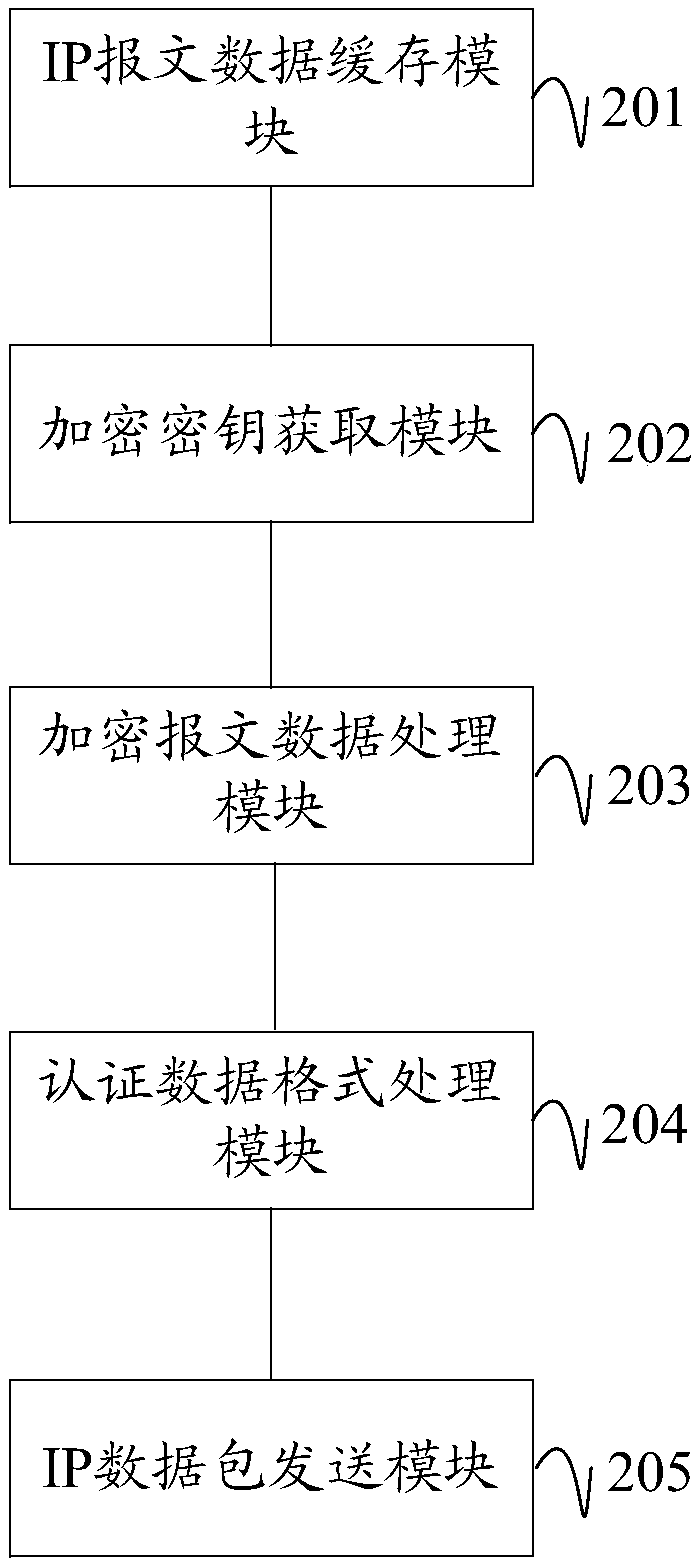
Internet Protocol security internet (IPsec) message format processing method, device and equipment, and storage medium
The embodiment of the invention discloses an Internet Protocol security internet (IPsec) message format processing method, device and equipment, and a storage medium, wherein the method comprises thesteps of receiving IP message data sent by a media access control (MAC) layer, and reading a destination IP address from the IP message data; obtaining a new source IP address and a new destination IPaddress by matching from a security policy database according to the destination IP address; if the new source IP address and the new destination IP address are not all zeros, querying a security association database according to the new destination IP address to obtain an encryption key; according to the encryption key, performing encryption processing on the IP message data based on an encrypted data format to obtain encrypted message data; generating a new IP header for the IP message data, and adding authentication data processed through a preset authentication data format to the end of the IP message data as new IP message data; and packaging and sending the encrypted message data and the new IP message data. According to the method, the device, the equipment and the storage medium in the application, the IP message data format is subjected to centralized and unified processing so as to adapt to various TCP (UDP) / IP network environments, thereby improving code standardization, and improving IPsec performance.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Security system for wireless networks
InactiveUS20090031395A1Digital data processing detailsUser identity/authority verificationTransport control protocolTransport layer
A security procedure for invoking IPsec security for communication of a packet in a network includes the steps of generating a message to be sent at the transport layer, building Internet Protocol and Transport Control Protocol headers for the message, selecting a security policy in accordance with a security policy database after the step of building Internet Protocol and Transport Control Protocol headers, and processing the packet according to the selected security policy.
Owner:XCOMM BOX
Virtual firewall system based on commons security policy and method of controlling the same
ActiveUS8099775B2Easily and conveniently set and restoreData taking preventionData switching by path configurationVirtual firewallSecurity policy
A virtual firewall system based on a common security policy and a method of controlling the same. The virtual firewall system includes one or more virtual security policy modules, each of which includes a local security policy database; a security policy determiner, which determines, from the one or more virtual security policy modules, a virtual security policy module corresponding to a packet received from outside; and a common security policy database, which stores security policies. Each of the one or more virtual security policy modules determines whether or not to apply a security policy of the common security policy database to the received packet, and when the security policy of the common security policy database is applied, does not apply the security policy of a local security policy database. An operator can easily and conveniently set and restore the system.
Owner:SAMSUNG ELECTRONICS CO LTD
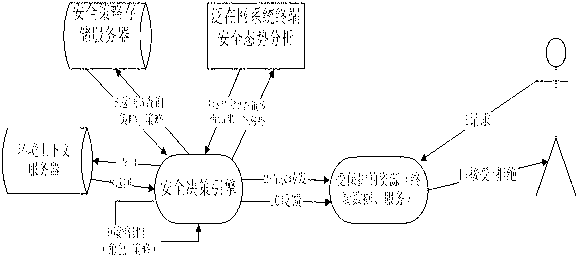
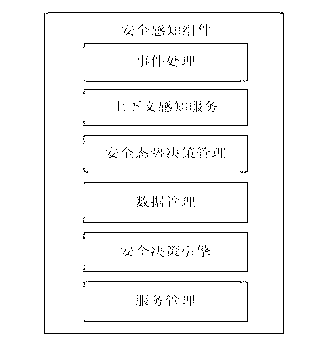
Designing method for integrating multilevel ubiquitous network security perception component
InactiveCN103312685AReal-time dynamic managementEnsure safetyTransmissionInteroperabilityMobile Information Device Profile
The invention belongs to the field of integrating ubiquitous network security perception, and discloses a designing method for a multilevel ubiquitous network security perception component based on security situation analysis, security policy management and the like. The method comprises the steps of firstly, developing a security engine by utilizing Java MIDP (Mobile Information Device Profile) 2.0, then sending a request of a terminal through an event driving mechanism, continuously calling the information on security situation management, security policy database, a context server and the like of the system terminal through the security engine so as to realize the dynamic roles or permission grant, making comprehensive evaluation to the request, responding the evaluation result to an application program (a carrier of protected resources), and allowing or rejecting the access of a user by the protected resource according to the response. According to the method, a middleware technology, a network security situation awareness technology, a network security analysis technology and the like are integrated, the security control problem under a terminal environment and the problems of heterogeneous authentication, access, interoperability control, privacy protection, data safe sharing and the like are solved, and safe guarantee is provided for the user.
Owner:WUXI NANLIGONG TECH DEV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com