Designing method for integrating multilevel ubiquitous network security perception component
A design method, multi-level technology, applied in the field of integrated ubiquitous network security awareness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
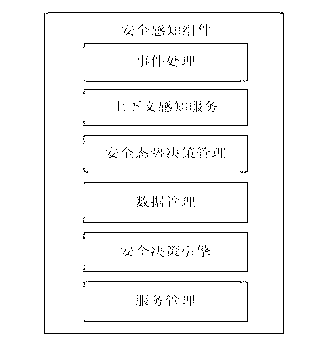
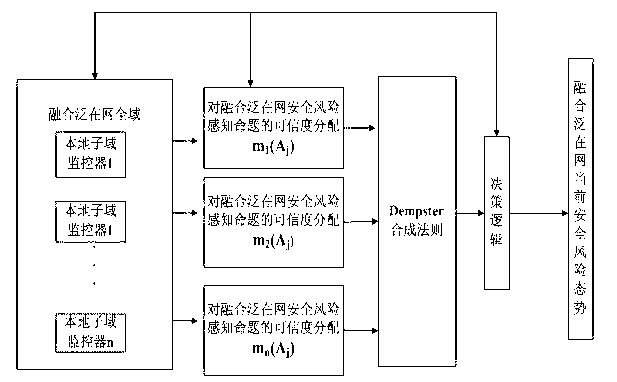
Image
Examples
Embodiment Construction
[0026] The present invention will be described in further detail below in conjunction with the accompanying drawings.
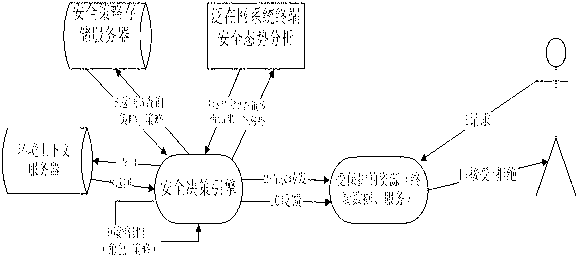
[0027] combine figure 1 , the present invention relates to a method for designing a multi-level security perception component of a fusion ubiquitous network. The steps of the security decision-making process are as follows:
[0028] 1. The user makes an access request to the protected resource;
[0029] 2. The protected resource forwards the user's access request to the security decision engine;
[0030] 3. According to this request, the security decision-making engine requests the "system terminal security situation model" assigned with the basic credibility to analyze the security situation;
[0031] 4. The security situation model returns the analysis results to the security decision engine;
[0032] 5. The security decision engine queries the security policy database for relevant security policies, such as access control policies;
[0033] 6. The sec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com