Internet of Things security defense system for intelligent terminal
A security defense and intelligent terminal technology, applied in transmission systems, electrical components, etc., can solve problems such as security accidents, data leaks, and service crashes, and achieve the effects of protecting security, resisting network attacks, and resisting network penetration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
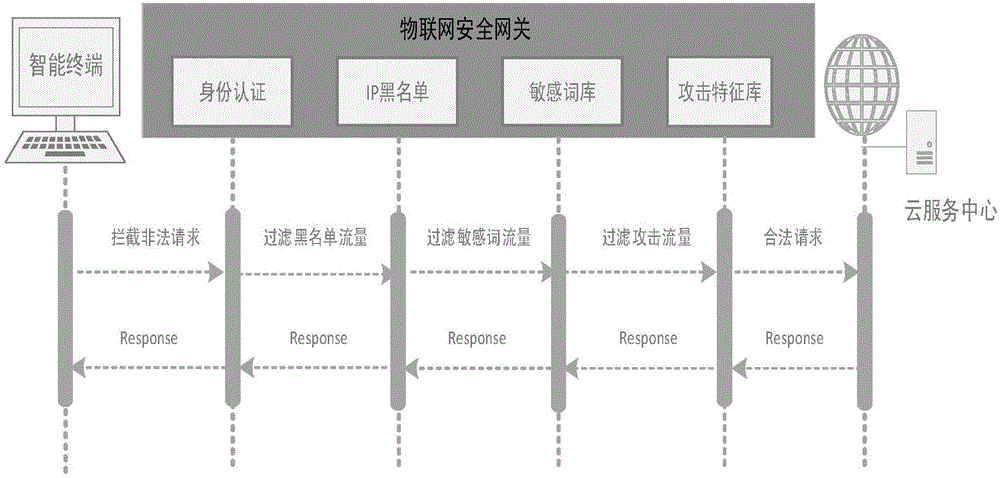
[0022] The purpose of the present invention is to propose an Internet of Things security defense system oriented to smart terminals, so as to ensure reliable, safe and controllable operation of smart terminal cloud services. The key points of realization of the Internet of Things security defense system in the present invention include:
[0023] (1) Deploy the IoT security gateway at the front end of the cloud service, and all open cloud services need to be registered and managed in the security gateway.
[0024] (2) The terminal business that accesses the cloud service needs to be registered and managed in the security gateway, and at the same time, specify the cloud service authority scope and terminal certificate that the terminal business can access.
[0025] (3) After the terminal access approval is passed, the terminal is assigned a unique terminal identifier APPKey and a terminal certificate. At the same time, the terminal developer can download the gateway SDK and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com