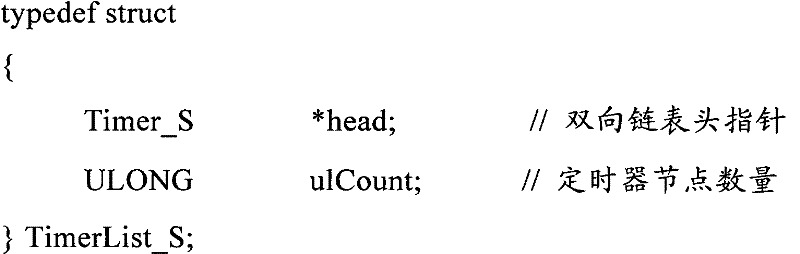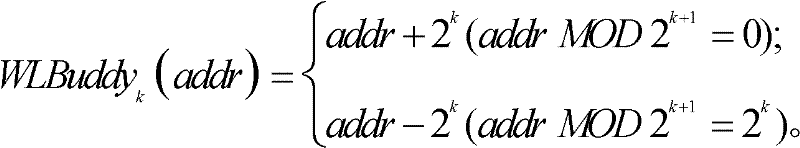Patents
Literature
199 results about "Doubly linked list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
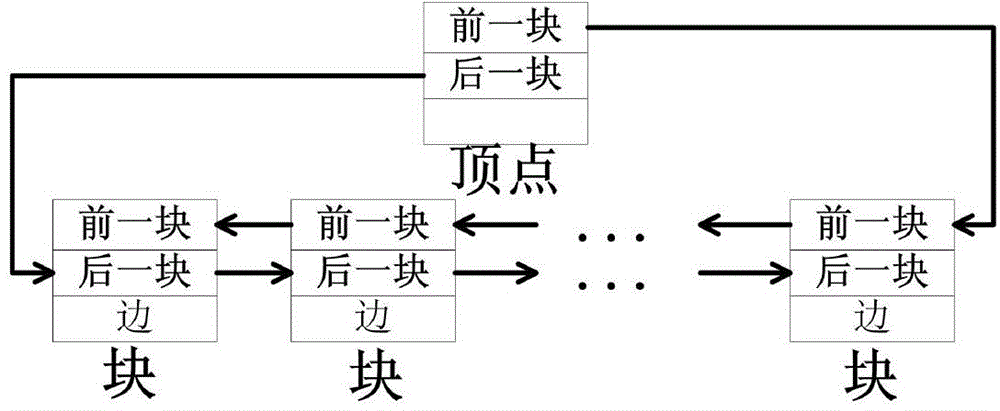
In computer science, a doubly linked list is a linked data structure that consists of a set of sequentially linked records called nodes. Each node contains three fields: two link fields (references to the previous and to the next node in the sequence of nodes) and one data field. The beginning and ending nodes' previous and next links, respectively, point to some kind of terminator, typically a sentinel node or null, to facilitate traversal of the list. If there is only one sentinel node, then the list is circularly linked via the sentinel node. It can be conceptualized as two singly linked lists formed from the same data items, but in opposite sequential orders.
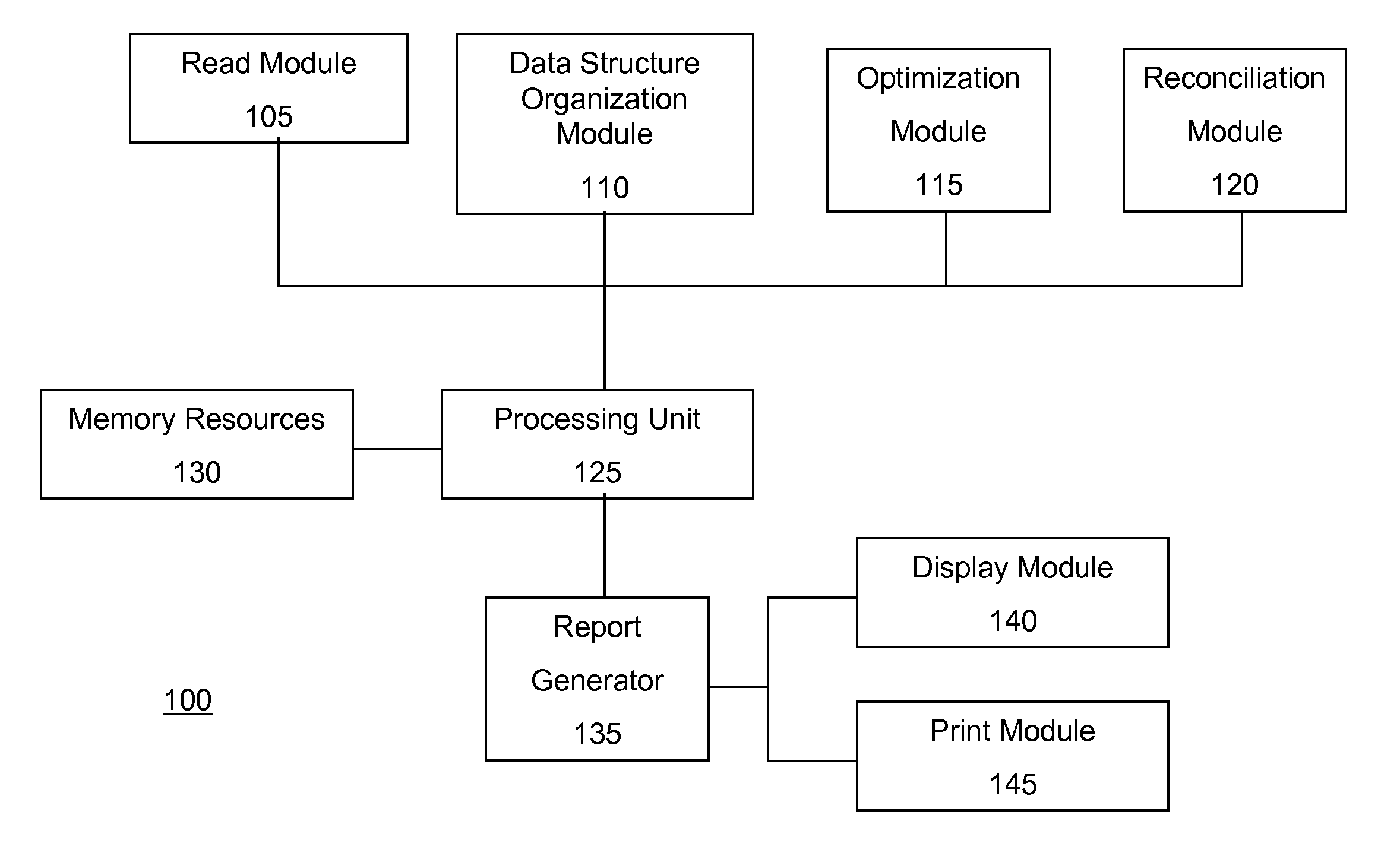
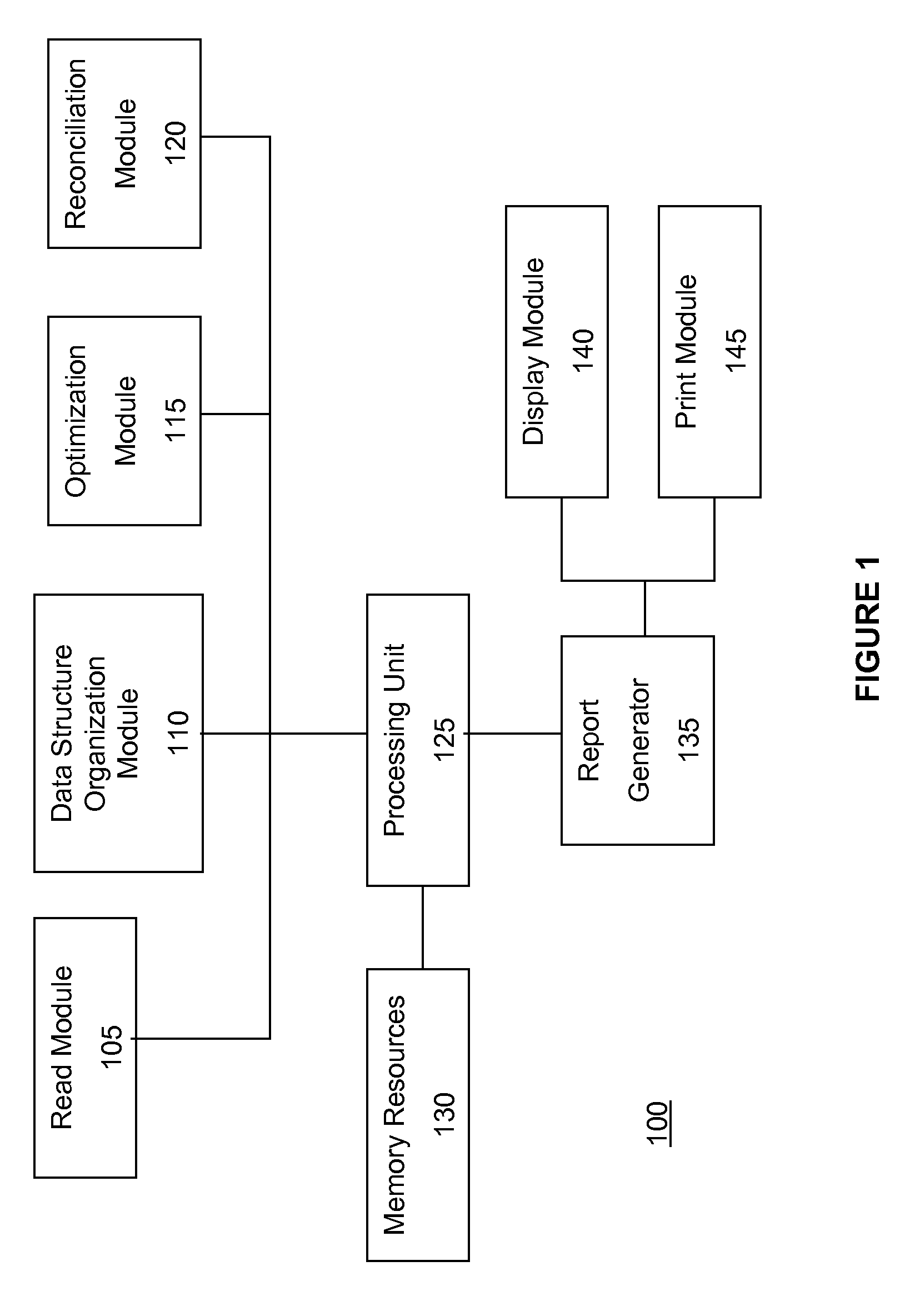
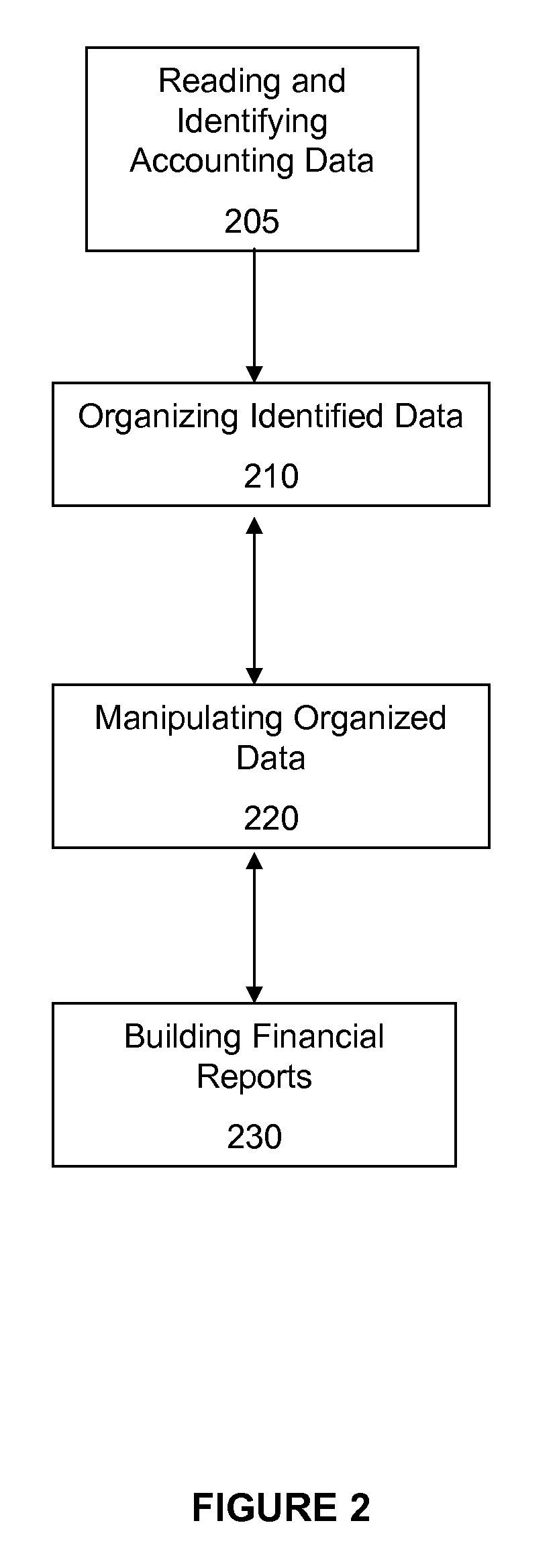
Reading, organizing and manipulating accounting data
InactiveUS20070088636A1Expenses-increasing and decreasing equity-andComplete banking machinesFinanceDatabaseDoubly linked list
A financial reporting system for reading, organizing and manipulating any accounting data and producing financial reports that may be customized to the preferences of the user. In one embodiment there is an organizational data structure for accounting data, including a trial balance data structure having a plurality of trial balance data structure elements containing accounts of the accounting data, wherein the trial balance data structure elements are linked by a distinct doubly linked list of trial balance data structure elements pointers, further comprising sub-lists of trial balance data structure elements pointers to group the accounts of the accounting data into financial statement items.
Owner:NAULT JACQUES
Large-scale social network service-oriented graph data storage and query method
ActiveCN104899156AIncrease usageSolve operational problemsMemory adressing/allocation/relocationTimestampSocial network service
The invention discloses a large-scale social network service-oriented graph data storage and query method. A data storage manager stores received graph data in a Key-Value way, wherein the vertex ID (Identity) of the graph data is taken as the Key, a vertex neighbourhood is taken as the Value, and the data of each vertex neighbourhood is stored; and a plurality of edges connected with the vertex neighbourhood are orderly stored in a memory block with a fixed size via a timestamp, a double linked list is formed, and the attribution information and the index information of the vertex are stored in a data structure. When the data storage manager receives an access request that the vertex v is accessed, the data storage manager transmits the vertex v and a k-order neighbourhood of the vertex v to a requester; and the requester caches stored data locally, firstly checks local cache during next query, and sends the access request to the data storage manager if no queried vertexes exist. The graph data storage and query method can meet a scene which is dynamically updated and is suitable for processing data sparseness, and random access.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI +1
Linked list implementing method for quickly searching data
ActiveCN101276334AFunction increaseAvoid wastingSpecial data processing applicationsArray data structureDatabase
The invention relates to an implement method that searches linked list of data rapidly. The technical problem that needs to solve is that not only the advantages of an array and a linked list are maintained, but also limitations of use thereof are overcame. The implementations lie in that appointing a data item of each node in the linked list to an array space; each element in the array appointed by the data item has a unique index number; the linked list can be a signal linked list or a double linked list; the array can be dynamically distributed array or appointed array. The data in the entire linked list is stored in sequence. The array is combined with the linked list, which is capable of enhancing the number of the nodes of the linked list to realize the dynamical array. Because of each node appoints to an array space that appoints size, but not a data item only, the function of the double linked list is extended and frequently distribution and waste of the memory are avoided too. Storing after ordering the entire data to position the data rapidly by dichotomy is convenient to operate.
Owner:SHANGHAI XIN YUE LIAN HUI ELECTRONICS TECH
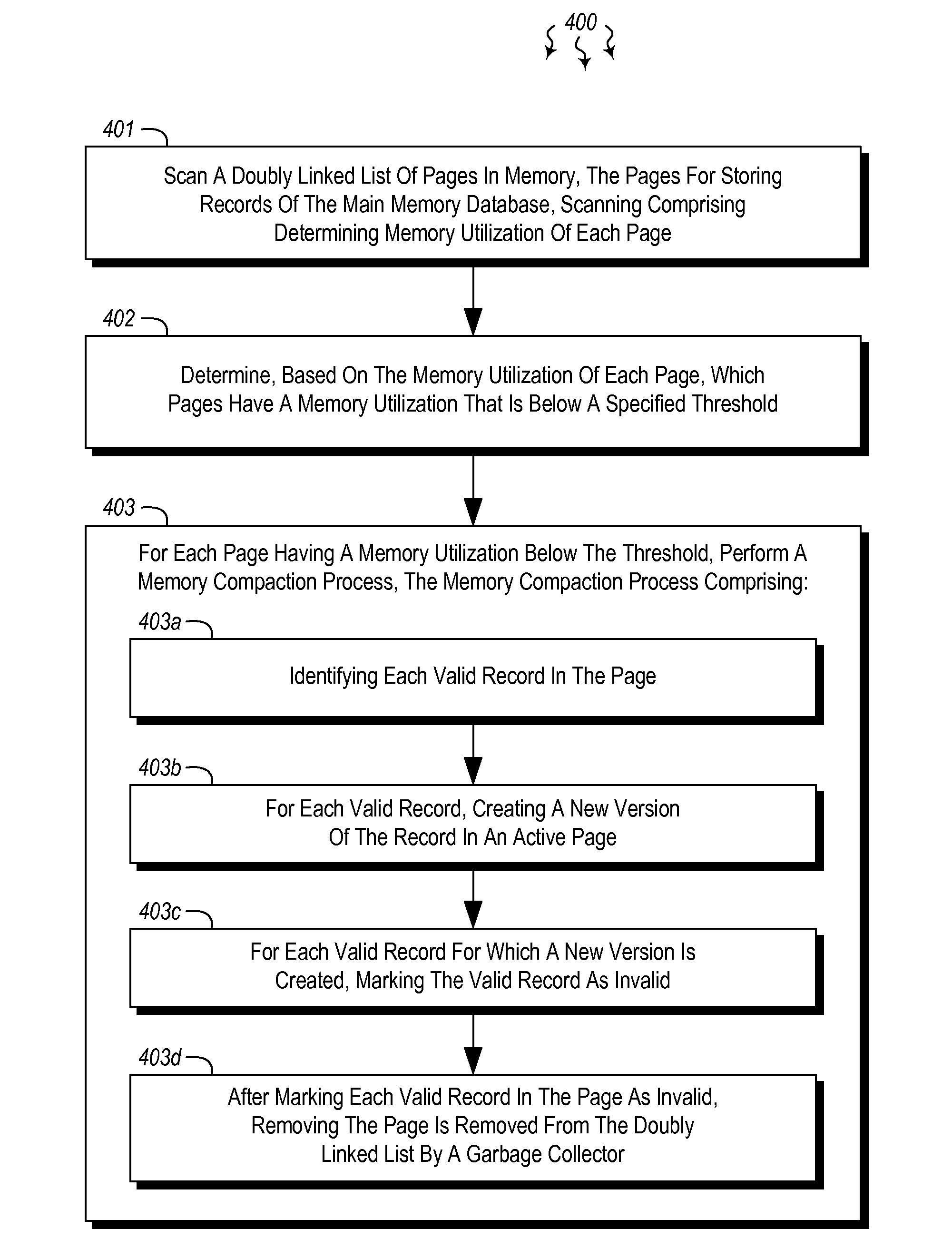
Memory compaction mechanism for main memory databases
InactiveUS20130346378A1Memory architecture accessing/allocationDigital data processing detailsIn-memory databaseData content
The present invention extends to methods, systems, and computer program products for performing memory compaction in a main memory database. The main memory database stores records within pages which are organized in doubly linked lists within partition heaps. The memory compaction process uses quasi-updates to move records from a page to the emptied to an active page in a partition heap. The quasi-updates create a new version of the record in the active page, the new version having the same data contents as the old version of the record. The creation of the new version can be performed using a transaction that employs wait for dependencies to allow the old version of the record to be read while the transaction is creating the new version thereby minimizing the effect of the memory compaction process on other transactions in the main memory database.
Owner:MICROSOFT TECH LICENSING LLC
Implementing optimistic concurrent data structures
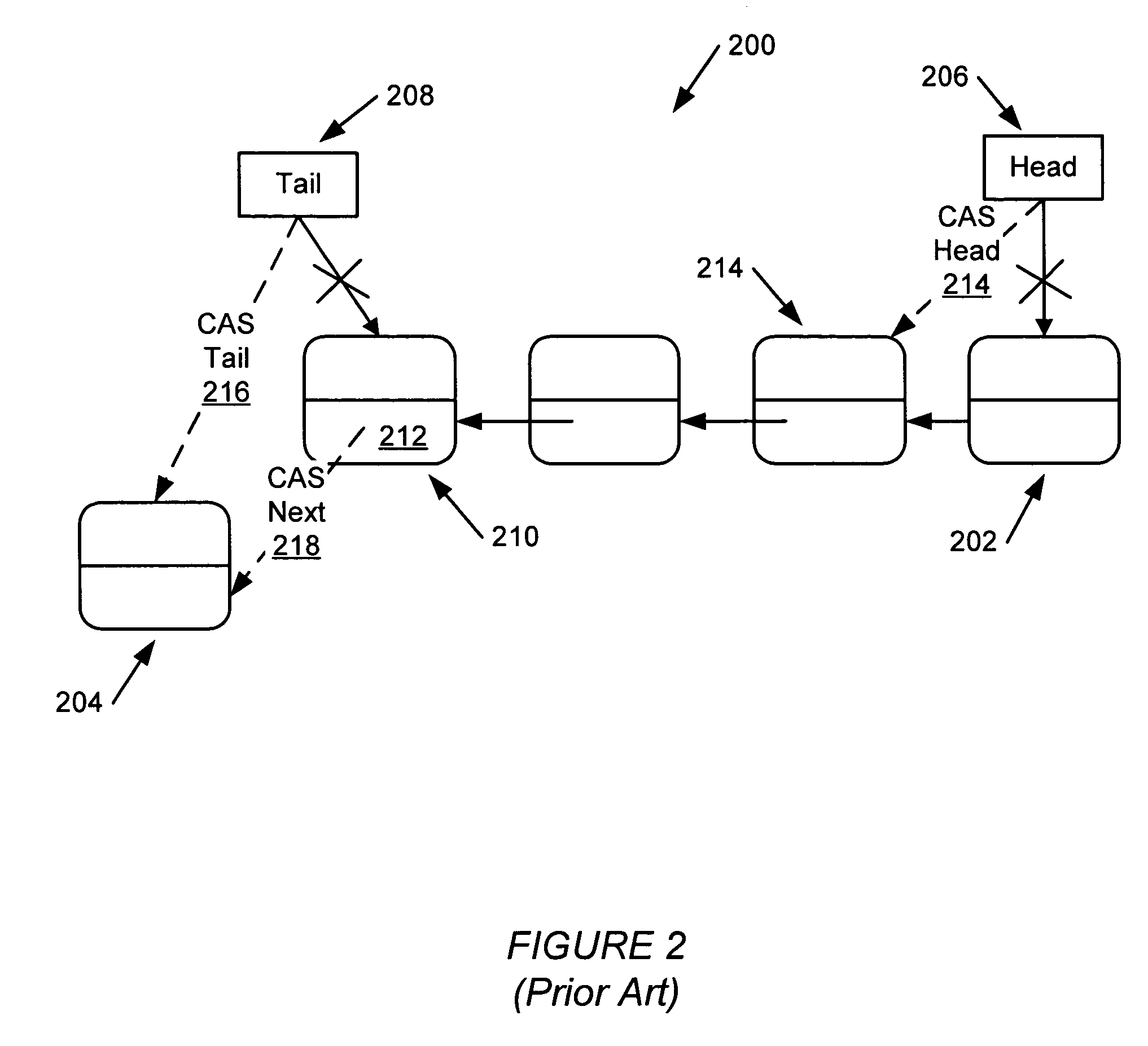
A concurrent FIFO queue is implemented as an “optimistic” doubly-linked list. Nodes of the optimistic doubly-linked list are allocated dynamically and links between the nodes are updated optimistically, i.e., assuming that threads concurrently accessing the FIFO queue will not interfere with each other, using a simple store operation. Concurrent, linearizable, and non-blocking enqueue and dequeue operations on the two ends of the doubly-linked list proceed independently, i.e., disjointly. These operations require only one successful single-word synchronization operation on the tail pointer and the head pointer of the doubly-linked list. If a bad ordering of operations on the optimistic FIFO queue by concurrently executing threads creates inconsistencies in the links between the nodes of the doubly-linked list, a fix-up process is invoked to correct the inconsistencies.
Owner:ORACLE INT CORP
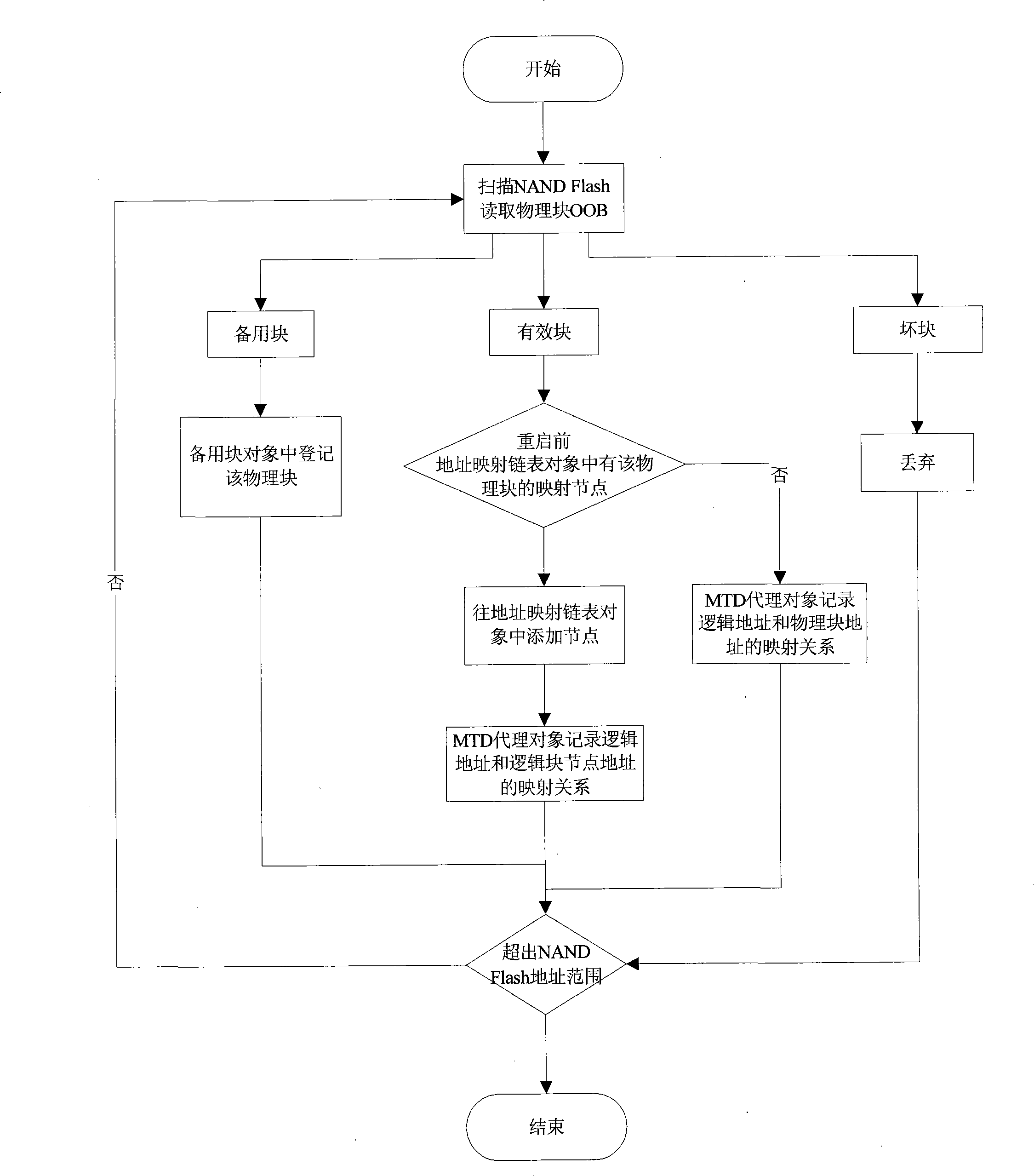
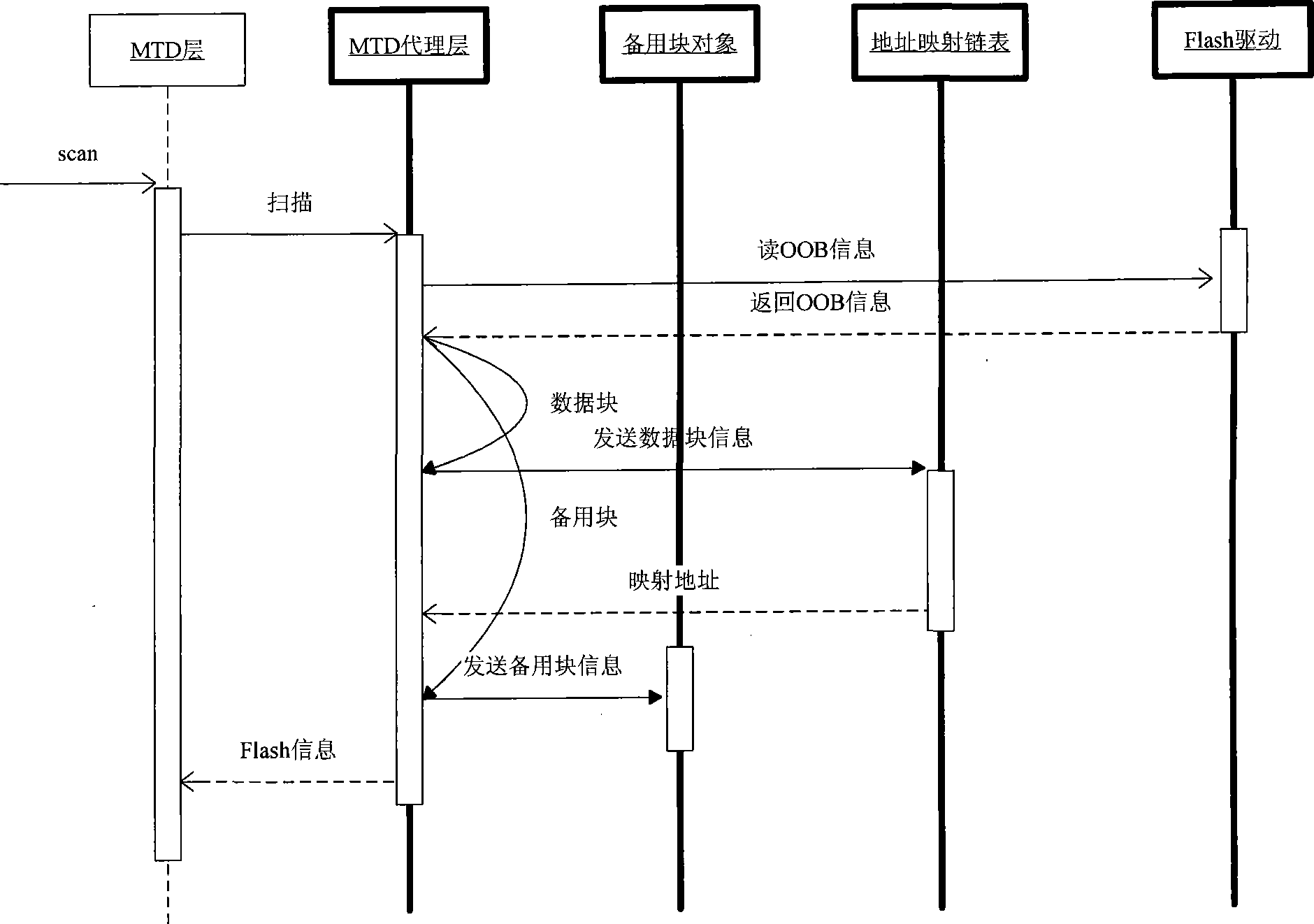
Management method of Nand-Flash memory system
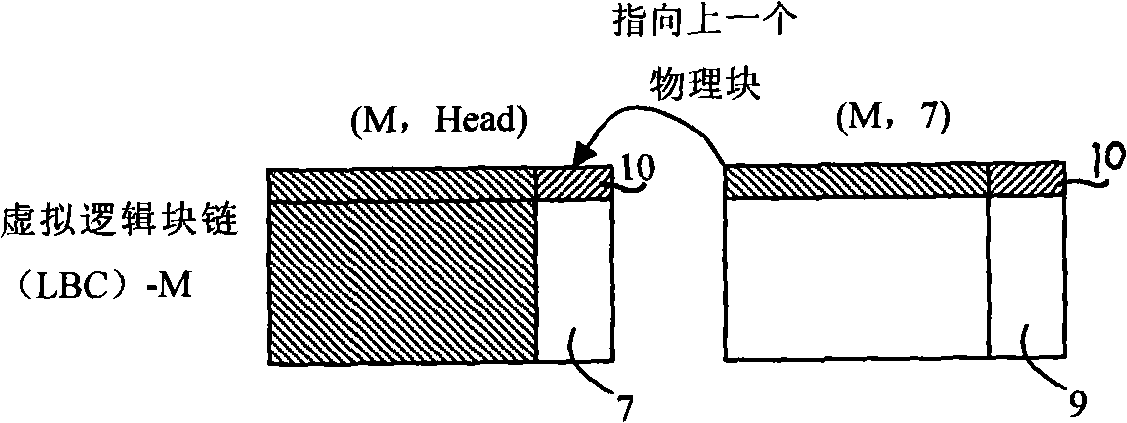
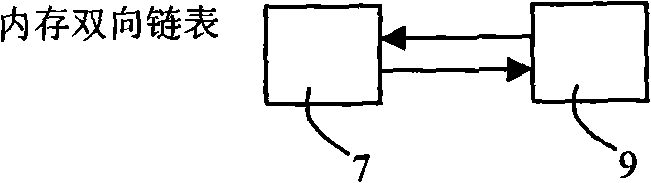
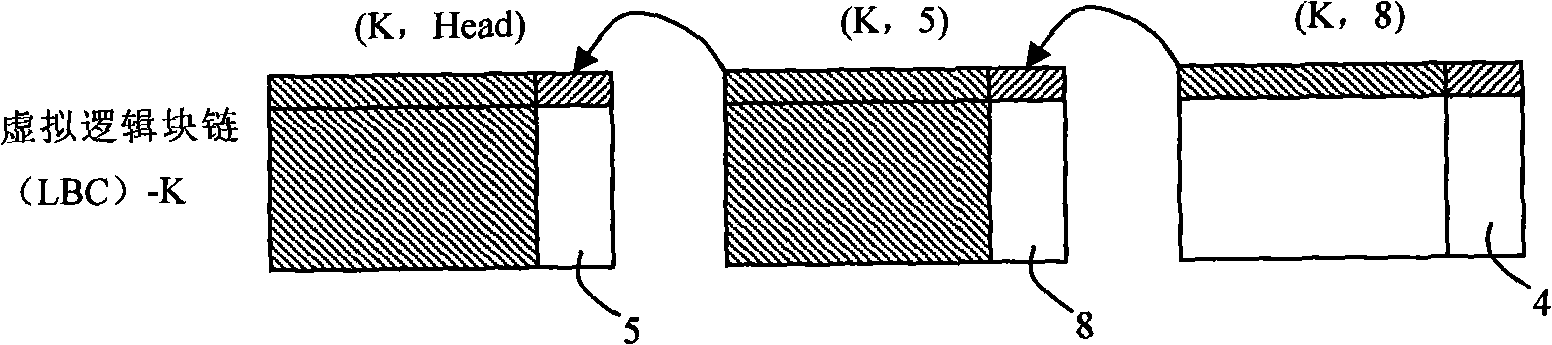
InactiveCN101329656AMeet the write-once requirementIntegrity guaranteedMemory adressing/allocation/relocationDoubly linked listBlock number
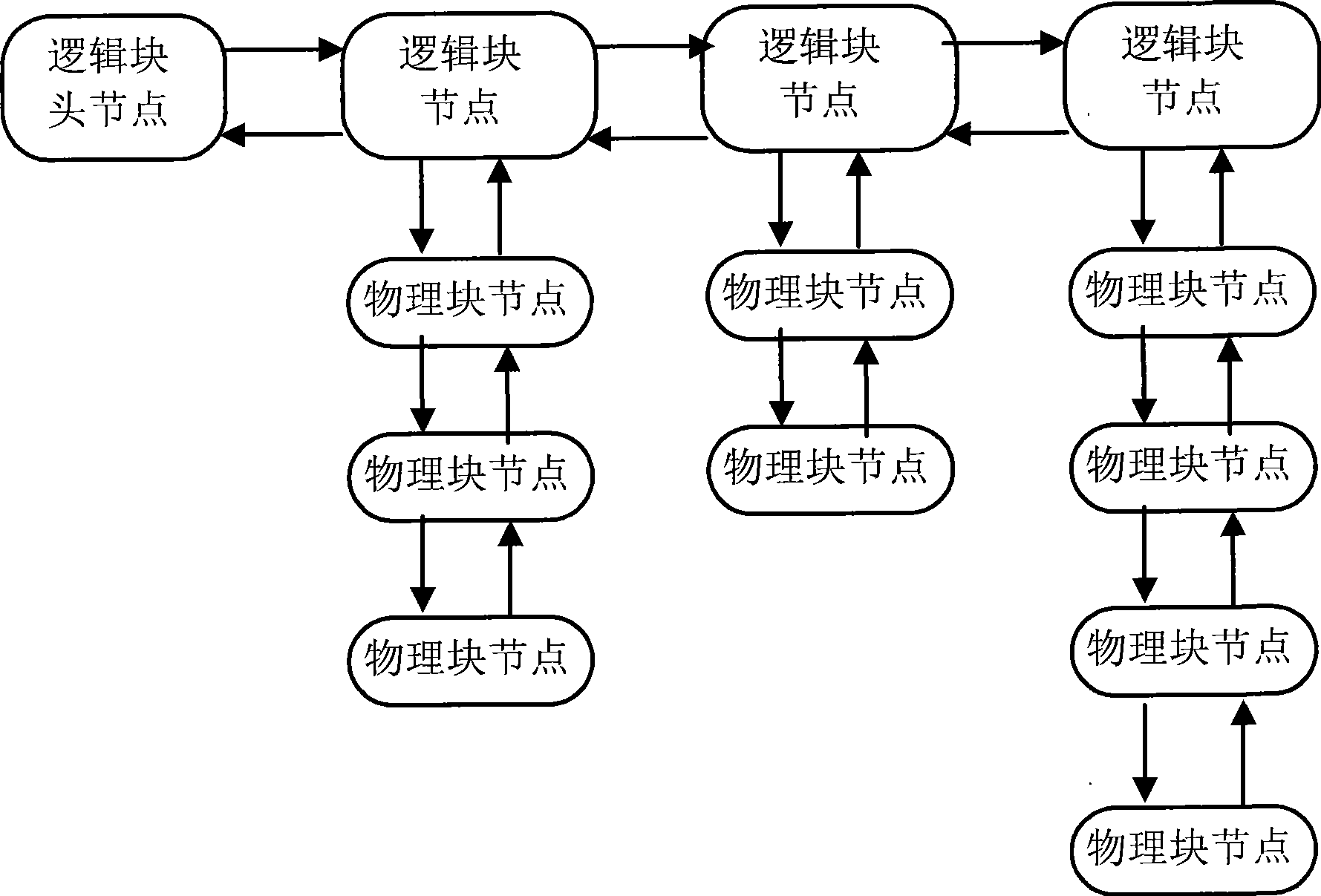
The invention relates to a management method for a computer Nand-Flash storage system. A plurality of physical blocks form a logic block chain; the information of the block numbers of the physical blocks and the block number of a forward physical block thereof are stored in an extended area of a first physical page of each physical block; when the system is initialized, a bidirectional chain table of the logic block chain is reconstructed by the stored information. When in read operation, the bidirectional chain table is utilized to research forwards and read a target physical block; the number of a read physical page is the same as the number of a logic page. When in write operation, the bidirectional chain table is utilized to research backwards; when a first physical block with the number of used pages on the logic block chain smaller than the number of a logic page requested to write, data is directly written in the logic page requested to write by the physical block; if the numbers of used pages of all physical blocks are larger than the number of the number of the logic page requested to write, a free physical block is added into the logic block chain; the data of effective pages is copied to the new current free physical block, and the data of the current page is written.
Owner:常州新超电子科技有限公司
Practical lock-free doubly-linked list
ActiveUS7533138B1Guaranteed progressData processing applicationsSpecial data processing applicationsOperating systemDoubly linked list
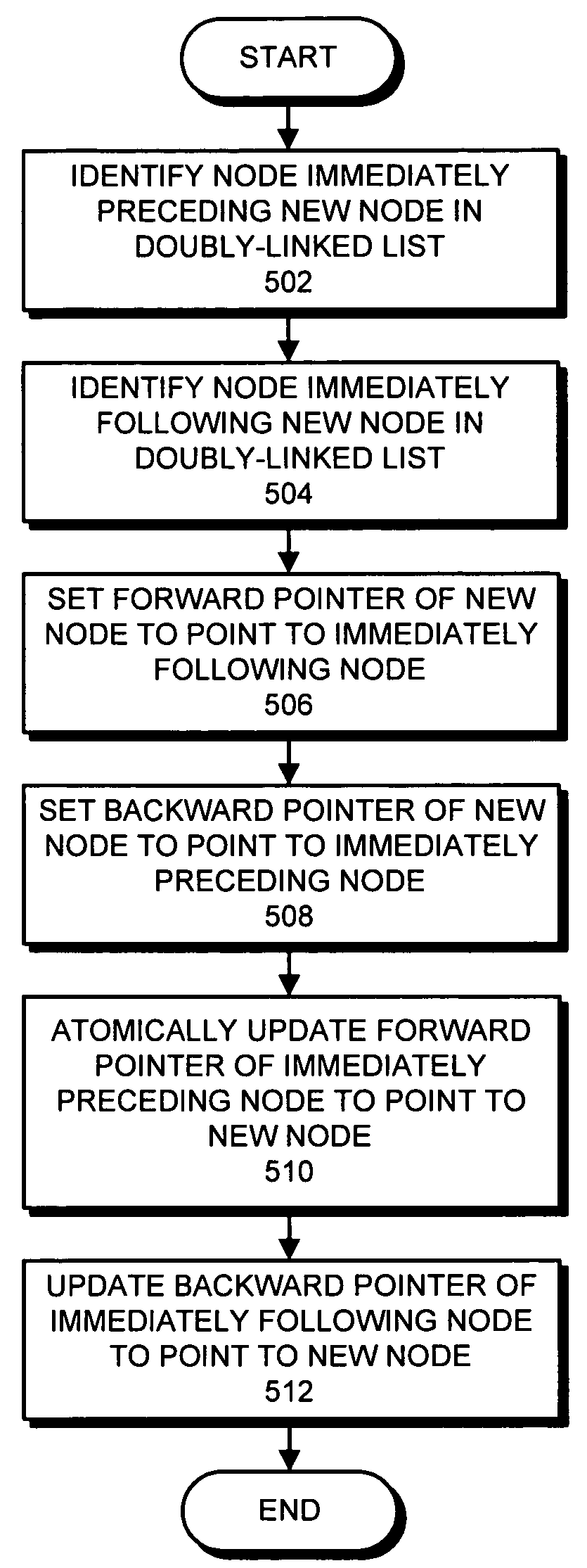
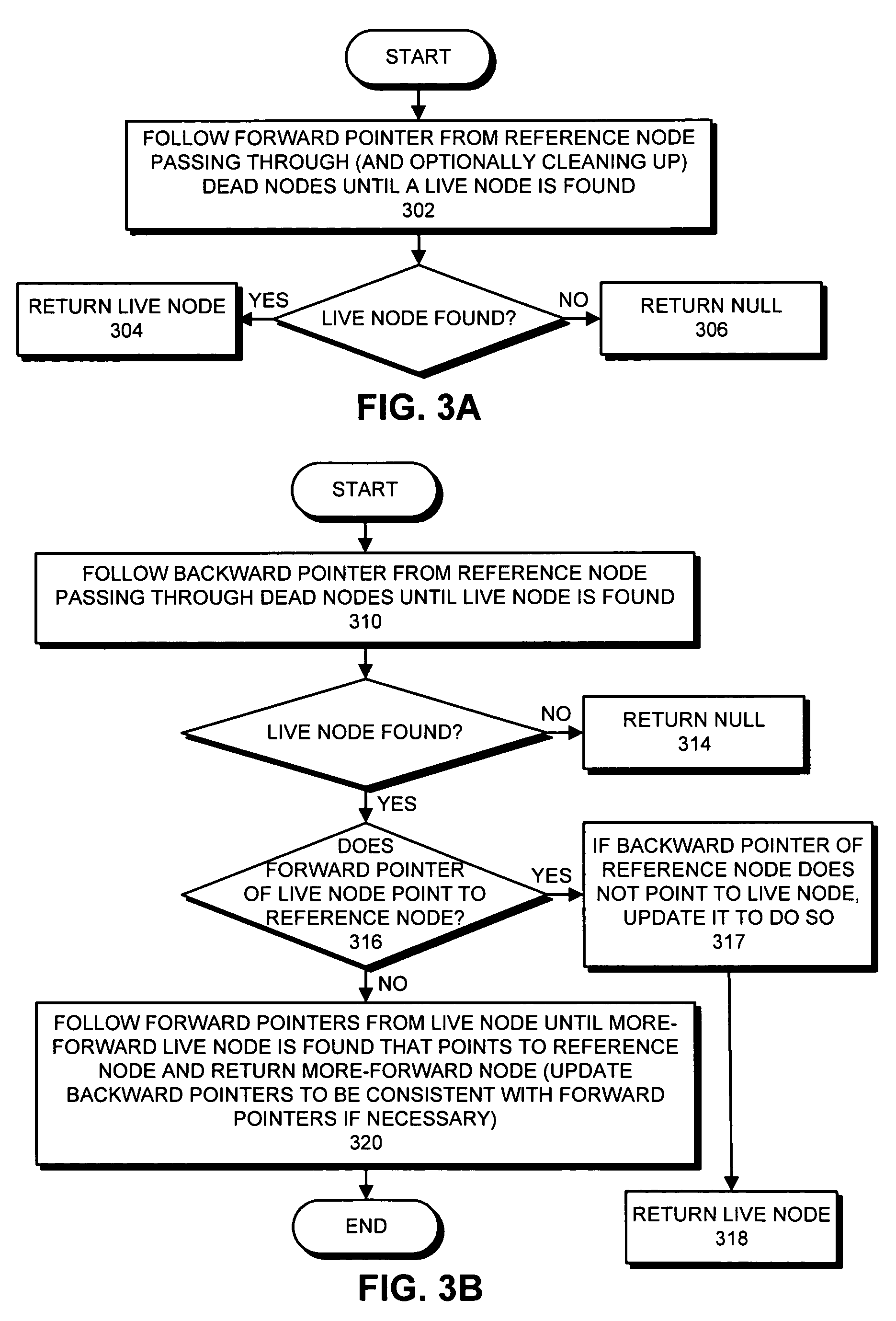
One embodiment of the present invention provides a system that supports inserting or deleting nodes at any location within a doubly-linked list which is lock-free, wherein lock-free means that the doubly-linked list can be simultaneously accessed by multiple processes without requiring the processes to perform locking operations (non-blocking) and furthermore that a finite number of steps performed by a process will guarantee progress by at least one process (lock-free). During operation, the system receives a reference to a target node to be deleted from the doubly-linked list. Next, the system atomically marks a forward pointer in the target node to indicate that the target node is deleted, wherein the forward pointer contains the address of an immediately following node in the doubly-linked list, and wherein the marking operation does not destroy the address of the immediately following node. Additional cleanup steps are then done by this or any other process. The system may also receive a new node which is accessible by only the requesting thread and may then insert the new node into the doubly linked list after a reference node. The system accomplishes this by setting the new node's backward pointer to the reference node and forward pointer to the successor of the reference node. Next, the system atomically changes the forward pointer of the reference node from the successor node to the new node. Additional cleanup steps are then done by this or any other process. An update operation that atomically performs a delete of an old node and an insert of its replacement node is also described.
Owner:ORACLE INT CORP
Optimizing method for establishing FAT file systems on NAND FLASH memory
ActiveCN101425041AHigh speedRandomMemory loss protectionMemory adressing/allocation/relocationFile systemDoubly linked list
Owner:ANYKA (GUANGZHOU) MICROELECTRONICS TECH CO LTD
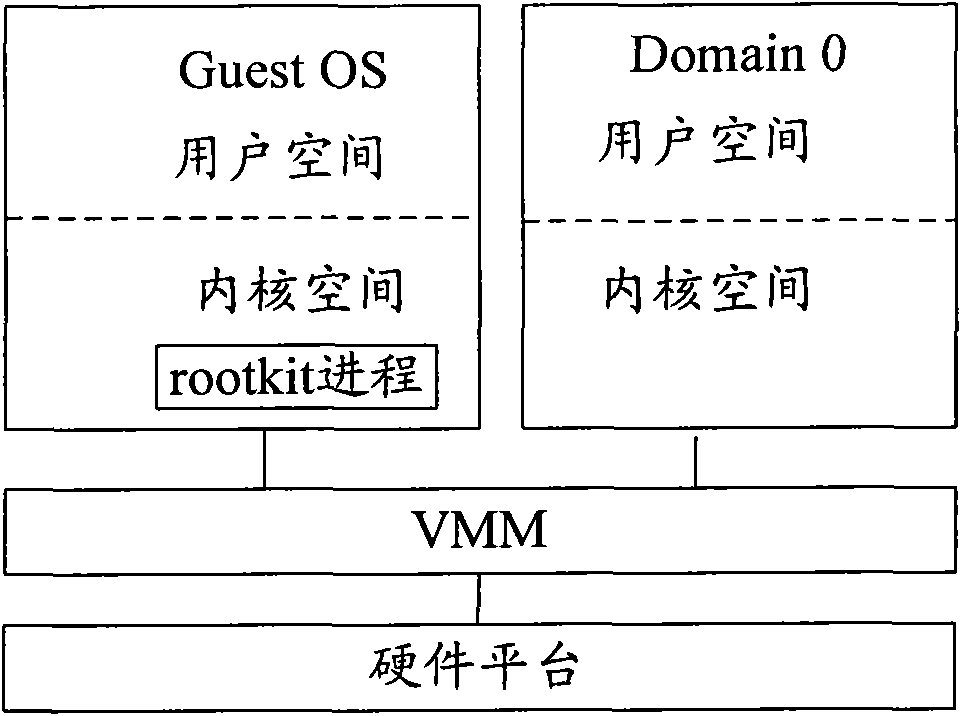
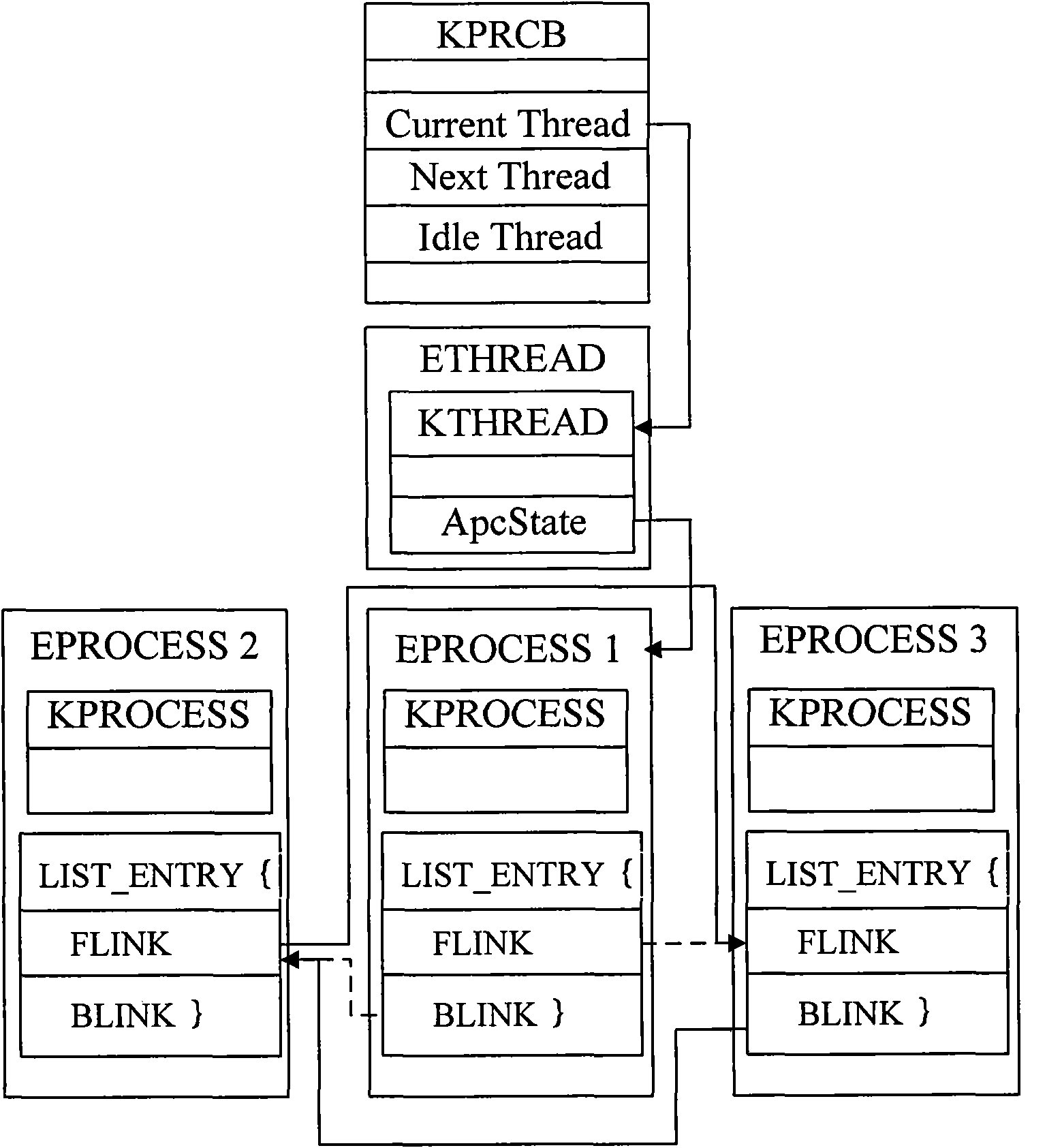
Computer and abnormal progress detection method
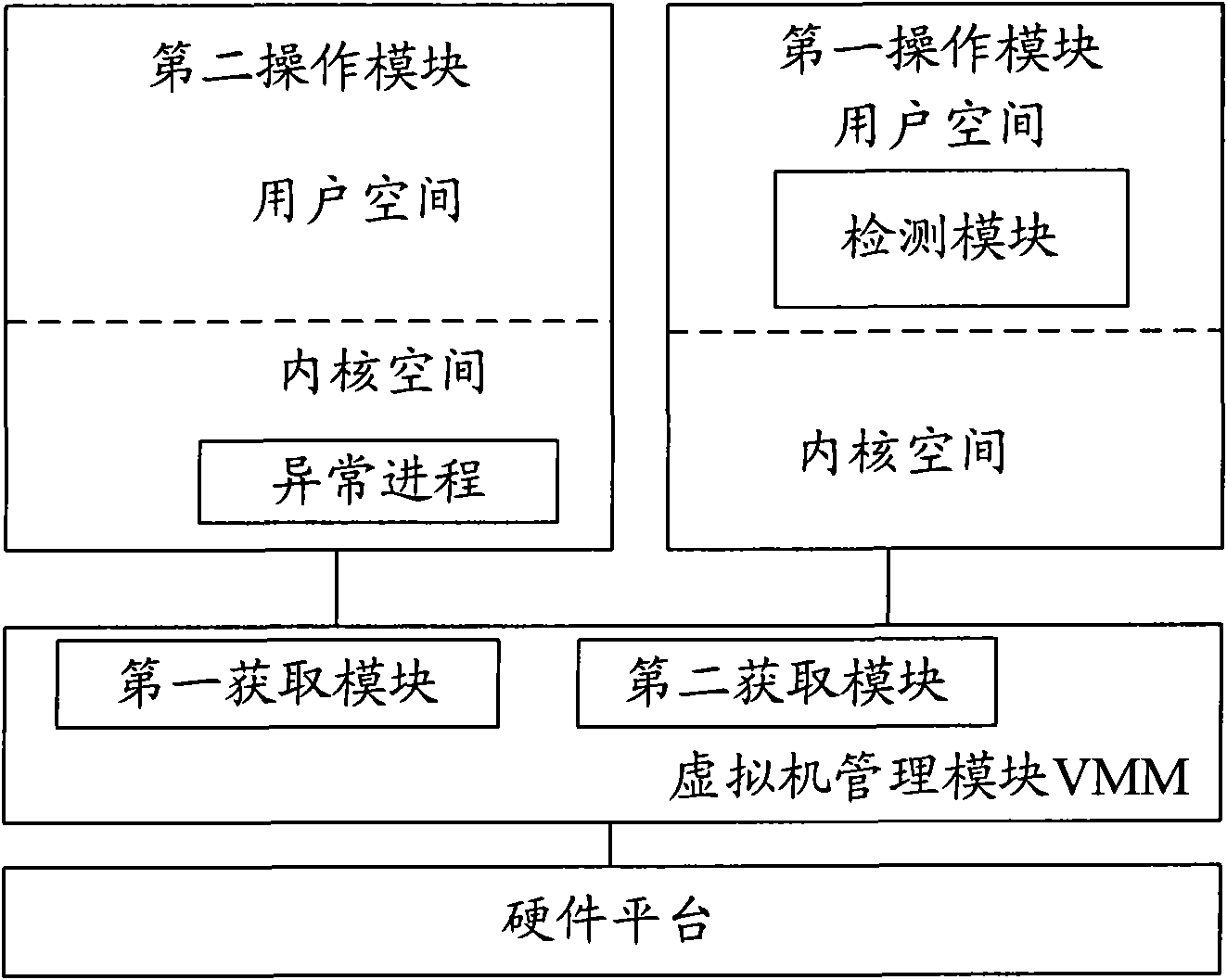
ActiveCN101782954AImprove securityAvoid safety hazardsMemory adressing/allocation/relocationMultiprogramming arrangementsOperational systemSystem safety
The invention provides an abnormal progress detection device and a method thereof, comprising a hardware platform, a virtual machine management module, a first operation module and a second operation module, wherein the virtual machine management module is used for installing a virtual machine manager, the first operation module is provided with a first operation system, and the second operation module is provided with a second operation system which operates on the virtual machine manager; the virtual machine management module comprises a first acquisition module and a second acquisition module, wherein the first acquisition module is used for obtaining the value of the identifier of a currently operating progress in the second operation system, and the second acquisition module is used for obtaining the doubly linked list of the currently operating progress in the second operation system. The device also comprises a detection module which is used for traversing the value of the identifier in the doubly linked list; and if the doubly linked list does not have the value of the identifier, the currently operating progress is determined to be an abnormal progress. The invention avoids the potential safety hazard of the operation system in a virtual machine system and improves the system safety.
Owner:LENOVO (BEIJING) LTD
Method and device for adding, searching and deleting hash table
InactiveCN102314485AImprove utilization efficiencySpecial data processing applicationsHash tableComputer science
The invention discloses a method and a device for adding, searching and deleting a hash table. The method for adding a hash table comprises the following steps of: extracting keywords of data to be added; performing hash operation on the keywords to obtain a hash address and a hash fingerprint; judging whether a corresponding target storage position is occupied according to the hash address; when the target storage position is occupied, searching for an unoccupied idle storage position from the hash table, and judging whether an occupied node at the target storage position is a first node of a bidirectional linked list; if so, adding a target node at the idle storage position according to the hash fingerprint, and linking the target node to the tail of the bidirectional linked list where the occupied node is positioned; and otherwise, moving the occupied node to the idle storage position, linking the occupied node to the tail of the bidirectional linked list where the occupied node is positioned, and adding a target node at the target storage position to constitute a single-node bidirectional linked list according to the hash fingerprint,. According to the method and the device, the utilization efficiency of the hash table and the utilization ratio of a storage space can be increased.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
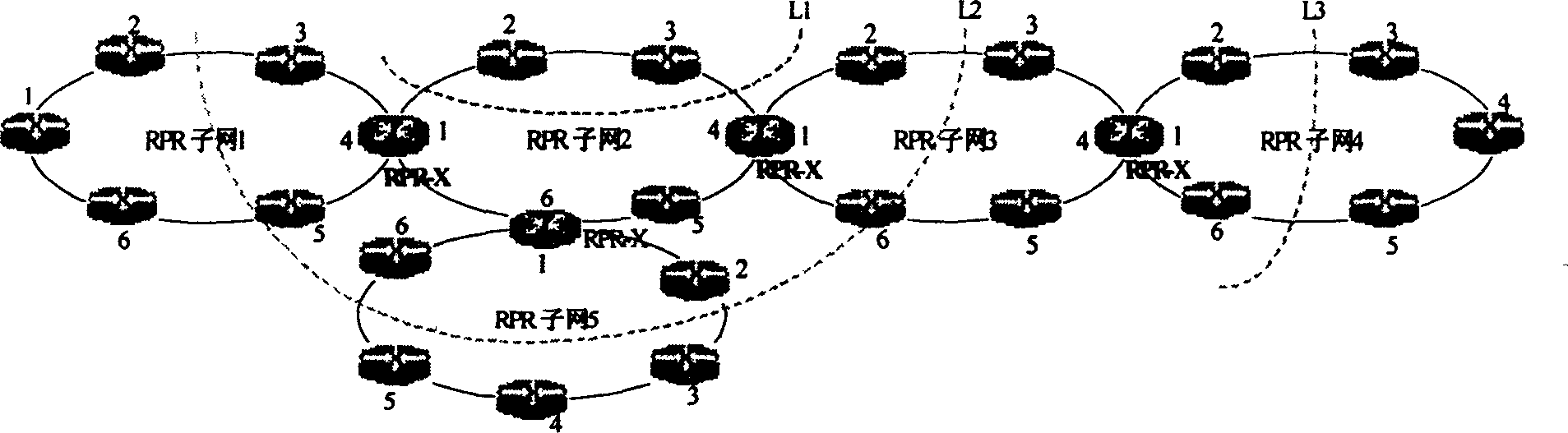
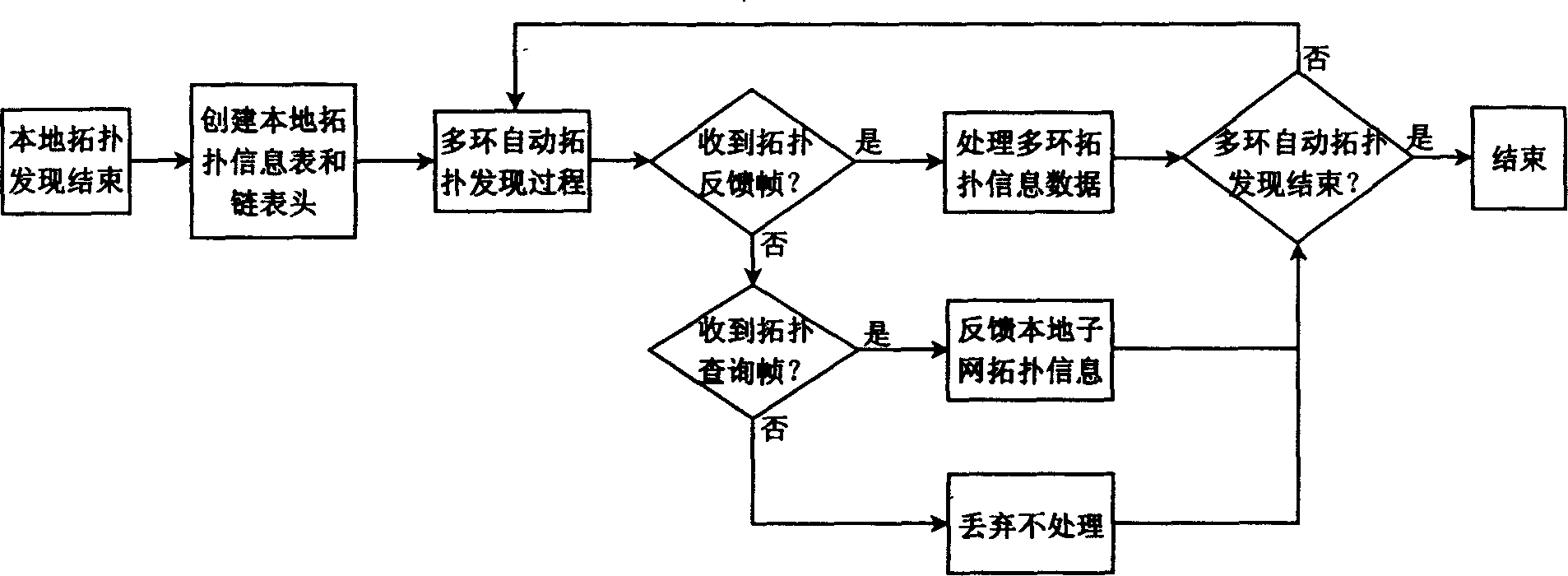
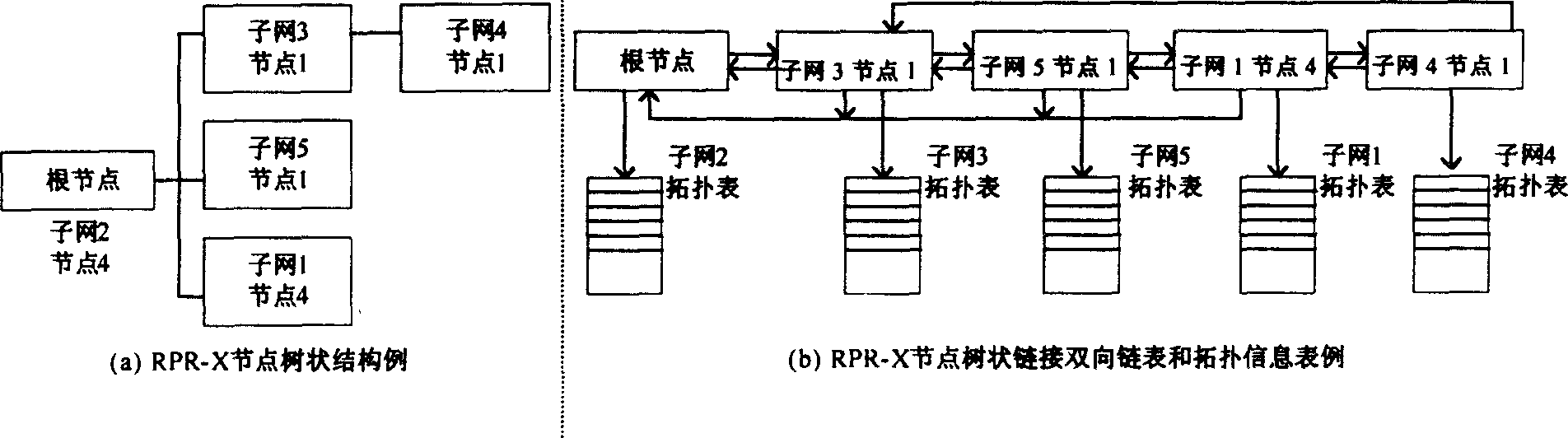
Implement method for automatic topology discovery of resilient packet multi-ring interconnection network
InactiveCN1547359ASolve problems in automatic control, etc.Solve wasteLoop networksAutomatic controlTopology information
The invention is a method for realizing automatic topology discovery of a kind of elastic grouping multi-ring mutual-connection method, at first, the standardized grouping ring RPR single ring network media is accessed to the address which controls the MAC, the representation method is defined extensively, then constructs the double direction chain and the topology information table unit structure of the tree connection, in order to preserve the topology information and the joint information in the network, finally, based on the constructed chain table and the automatic topology discovery., it uses clockwise layering method to realize the automatic topology discovery of the multi-ring mutual-connection network. The invention has character of distributed automatic control of single ring structure and the merits of automatic topology discovery algorithm, it solves the problem of route information automatic discovery and the automatic control of the RPR multi-ring mutual-connection network topology, based on the topology information and the joint information in the chain table and the information table, it can complete the calculation of the second layer route, thus, any joint in the network can works out the route series to other joint in the network quickly.
Owner:SHANGHAI JIAO TONG UNIV
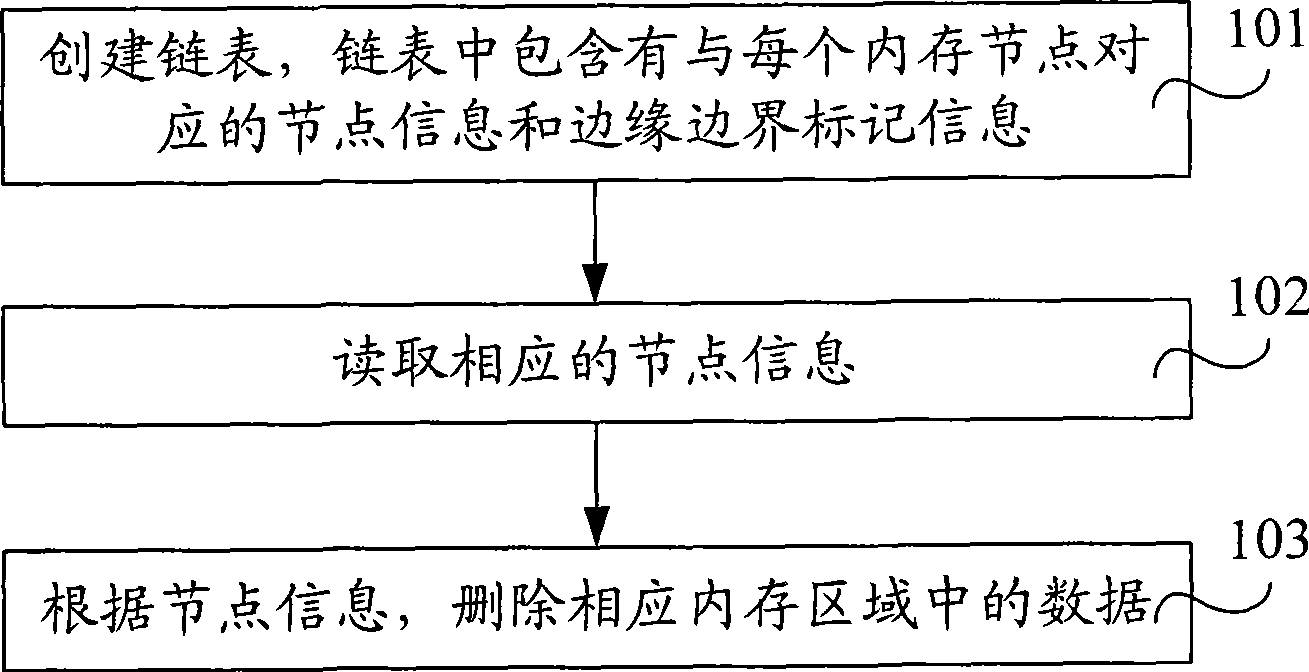
Sharing internal memory management method and apparatus
InactiveCN101470632AEfficient managementOvercome the inability to effectively manage shared memory management defectsResource allocationInternal memoryData information
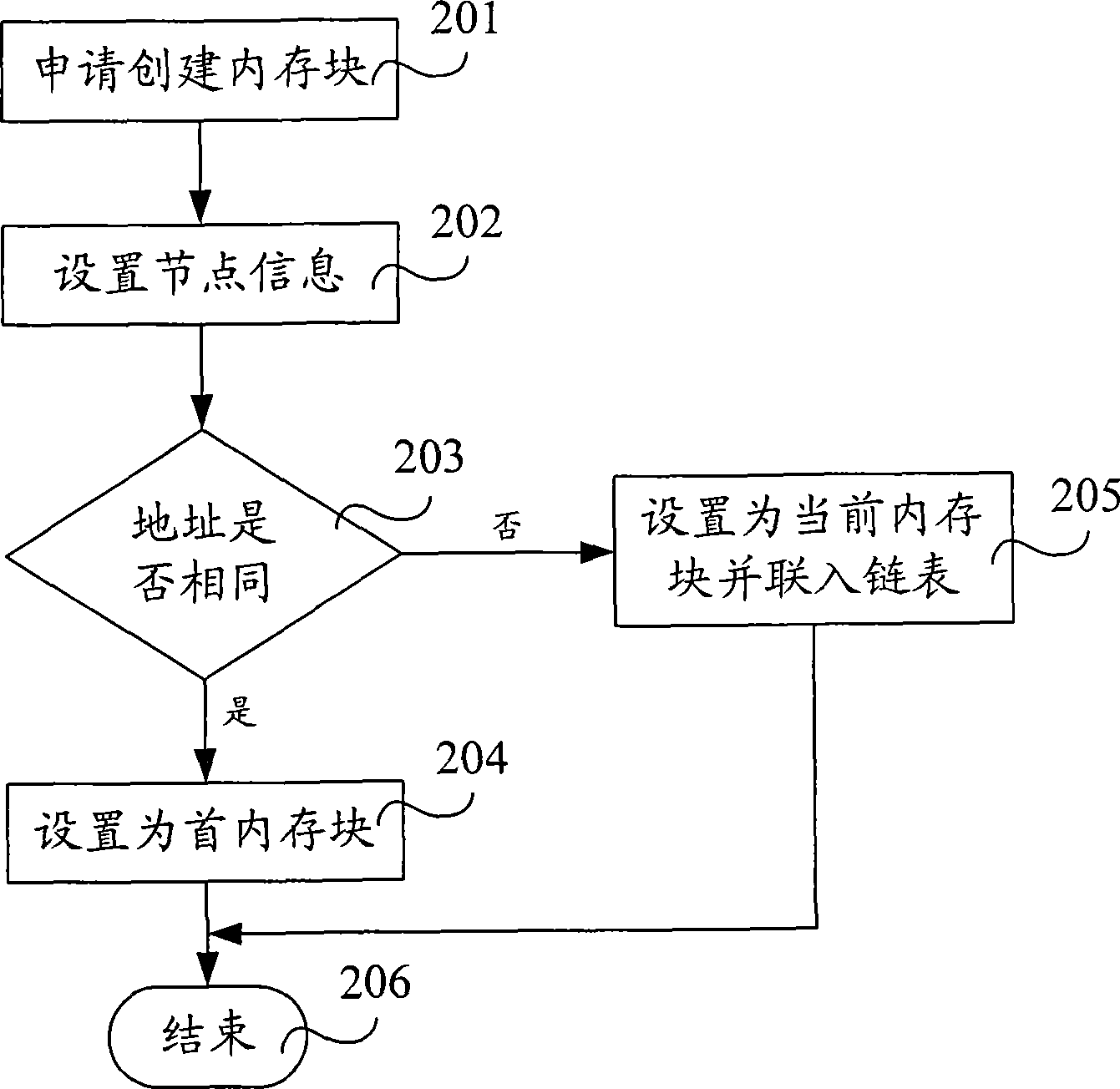
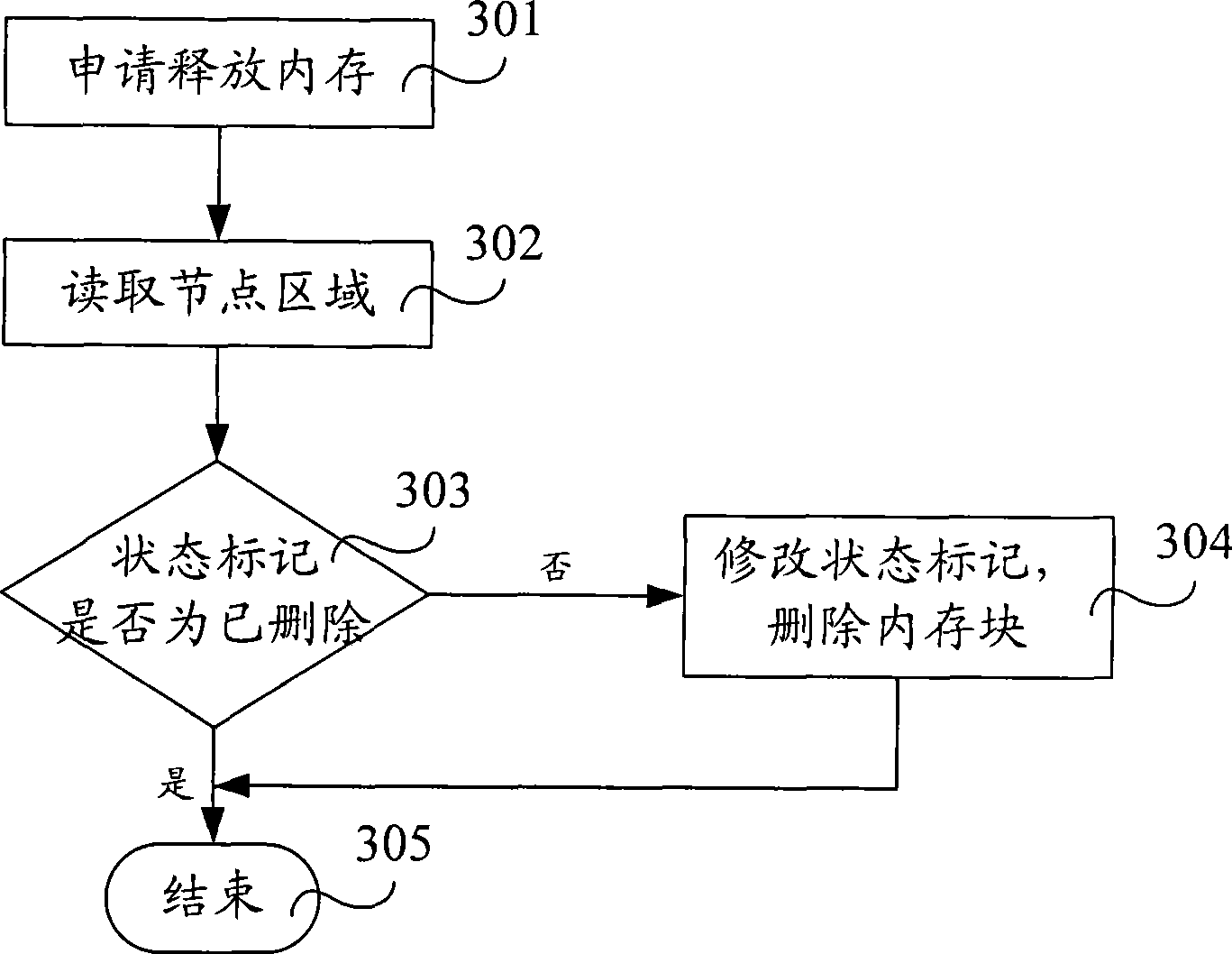
The invention relates to a management method of shared memory and a device, wherein the method comprises a memory double linked list is built, the memory double linked list comprises node information, data information and edge boundary marker information which correspond to each memory block, the node information is located in a node area, the data information is located in a data area, and the edge boundary marker information is located in a marker area. The node information at least comprises the size of the data area, a state marker, an address of a forward memory clock and an address of a backward memory block, wherein the state marker is used to express whether the data area has the data information, corresponding node information is read, and corresponding memory blocks are deleted according to the node information. The invention overcomes the management defect in the prior art that the shared memory can not be effectively managed after building a memory linked list, provides an effective protection mechanism of the shared memory, which leads an application program to effectively manage the space of the shared memory.
Owner:HUAWEI SOFTWARE TECH
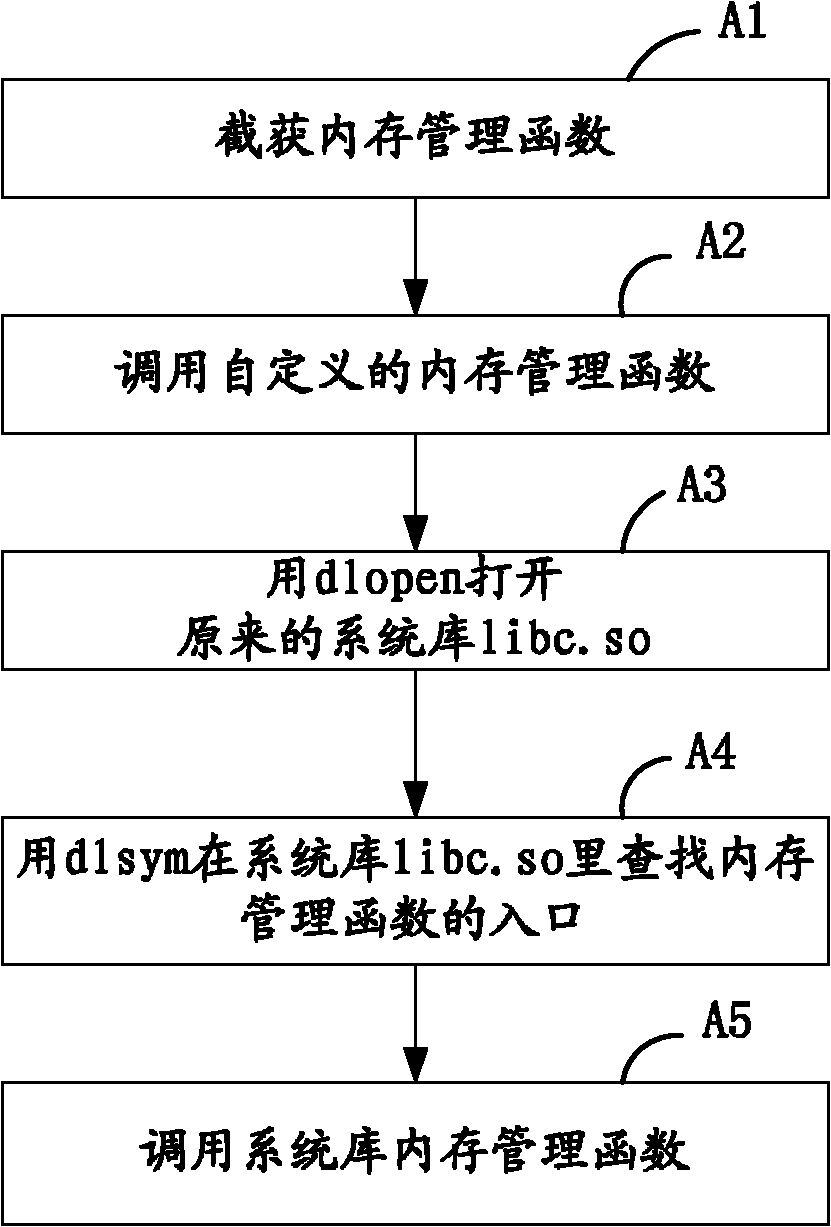
Method and system for detecting memory occupancy state of embedded system
InactiveCN102073591AEasy to detectImprove general performanceSoftware testing/debuggingMemory footprintComputer science
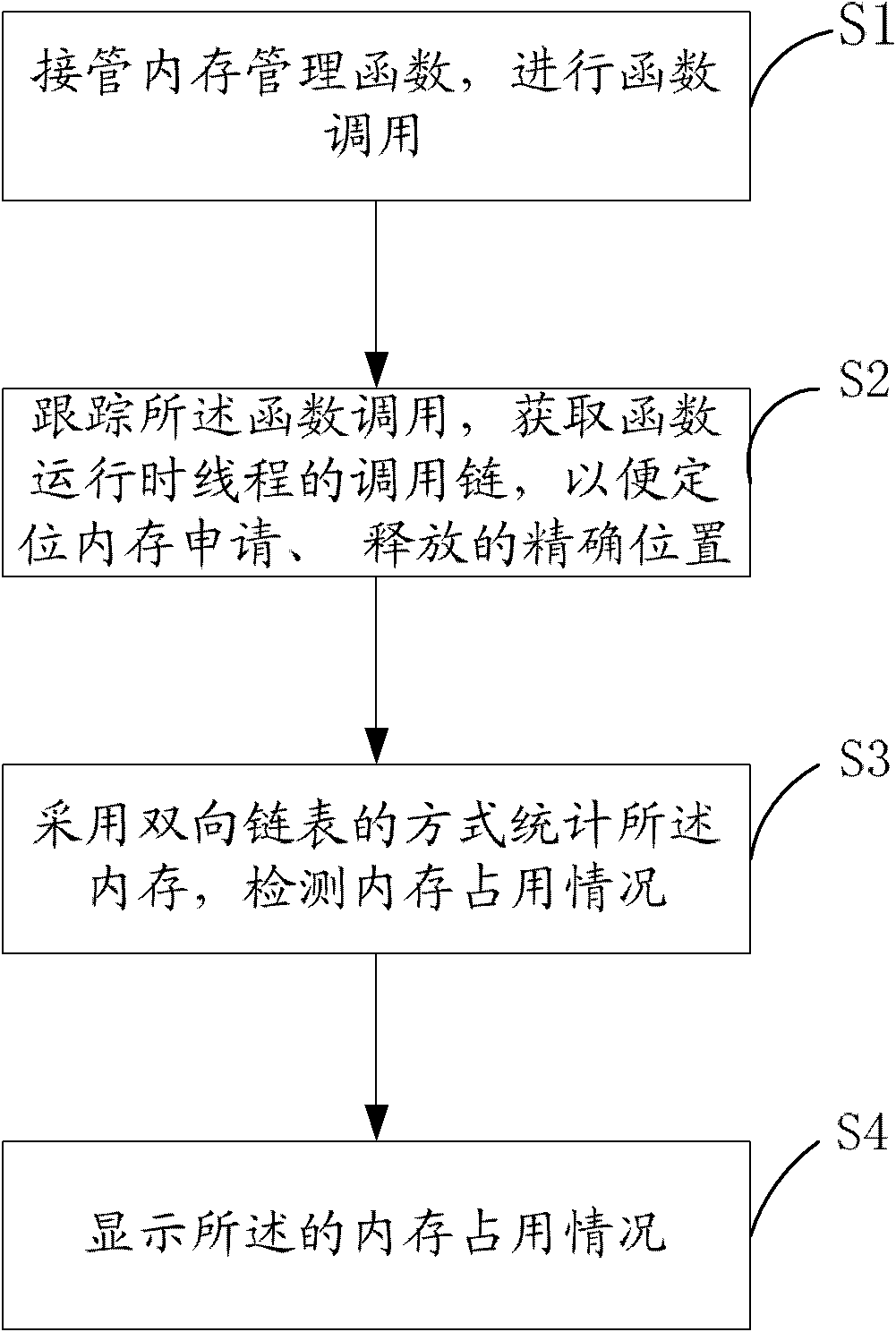
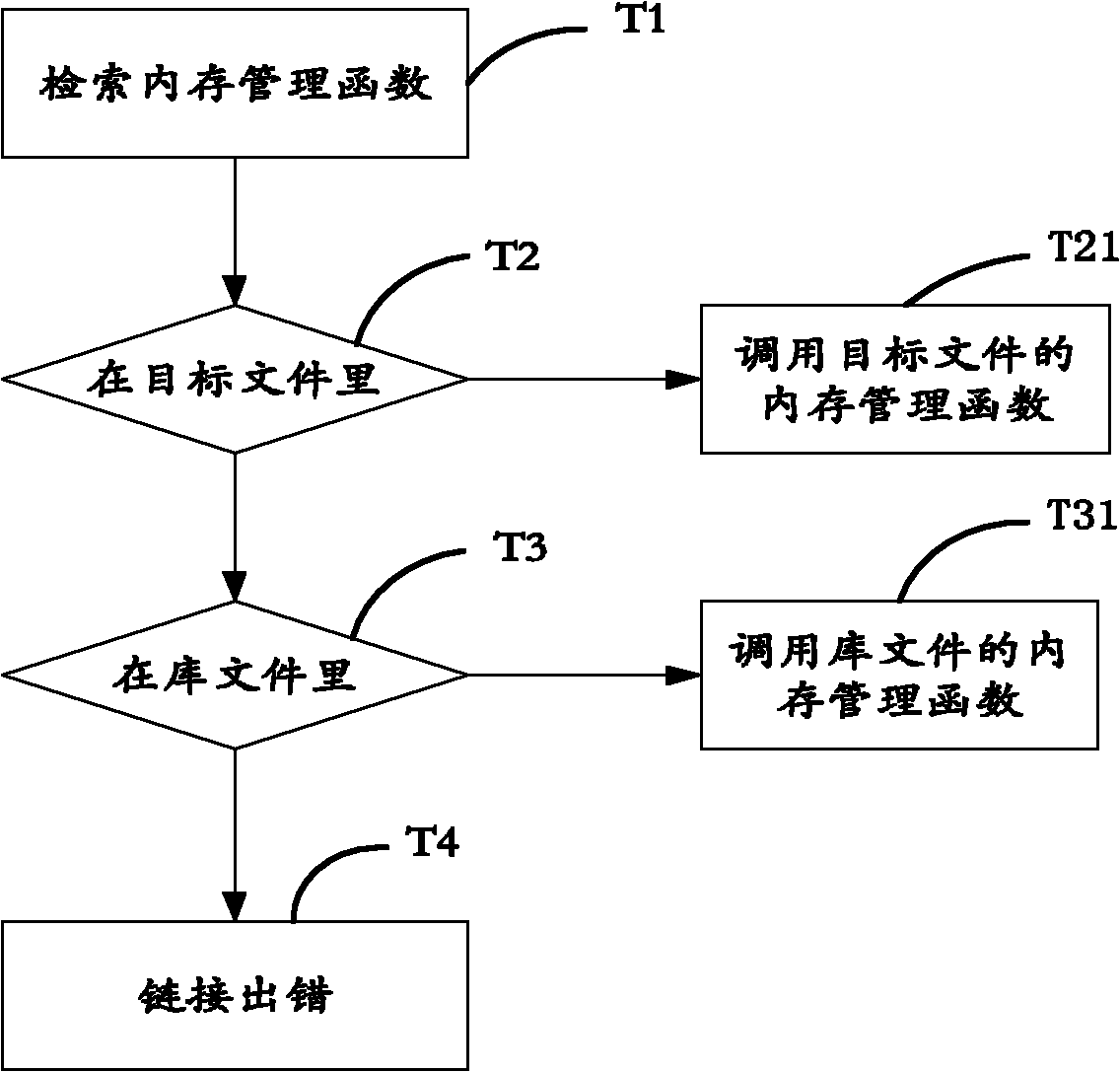
The invention discloses a method and a system for detecting memory occupancy state of an embedded system, and the method for detecting the memory occupancy state of the embedded system comprises the following steps: S1) taking over a memory management function and performing function call; S2) tracking the function call and acquiring a call chain of a thread when the function runs so as to be convenient to position precise positions for applying for and releasing a memory; S3) performing statistics on the memory by adopting the way of a two-way chained list and detecting the memory occupancy situation; and S4) displaying the memory occupancy situation. The invention further discloses the system for detecting the memory occupancy state of the embedded system. As for the method and the system for detecting the memory occupancy state of the embedded system, the memory management function is taken over, call information of the current function is tracked, the memory leakage position can be accurately positioned, the memory occupancy situation can be displayed, the universality is strong, and the detection of the memory using problem can be greatly facilitated.
Owner:FUJIAN STAR NET EVIDEO INFORMATION SYST CO LTD
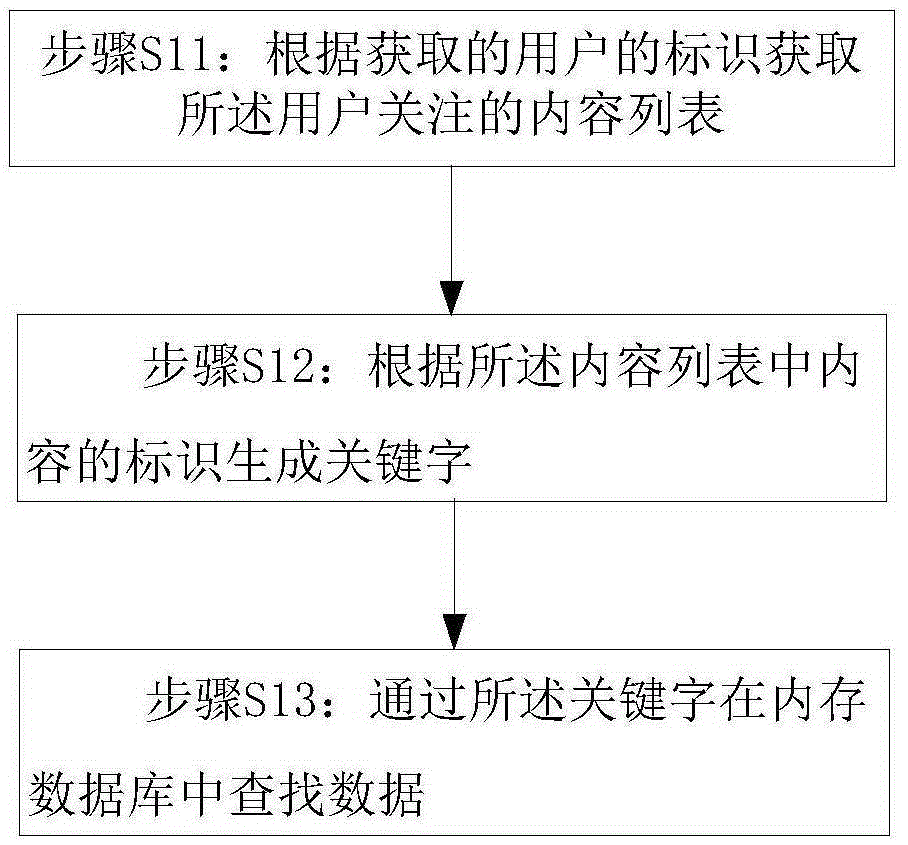
Data searching method, data saving method and related equipment
ActiveCN105260475AImprove query speedGuaranteed query speedRelational databasesSpecial data processing applicationsIn-memory databaseSpeed reading
The invention provides a data searching method, a data saving method and related equipment. The method comprises the following steps: obtaining a content list concerted by a user according to an obtained identity of the user; generating key words according to contents in the obtained content list; searching for data in a memory database according to the key words, wherein each key word corresponds to a doubly liked table in the memory database. According to the technical scheme, the high-speed reading and writing features of the Redis memory database are utilized for assisting in RDBMS searching, so that the searching speed is greatly improved, and the high searching speed can still be guaranteed when the data volume is high; meanwhile, the Redis memory database is updated timely according to newly-added contents, so as to further guarantee the data searching speed and validity.
Owner:NUBIA TECHNOLOGY CO LTD
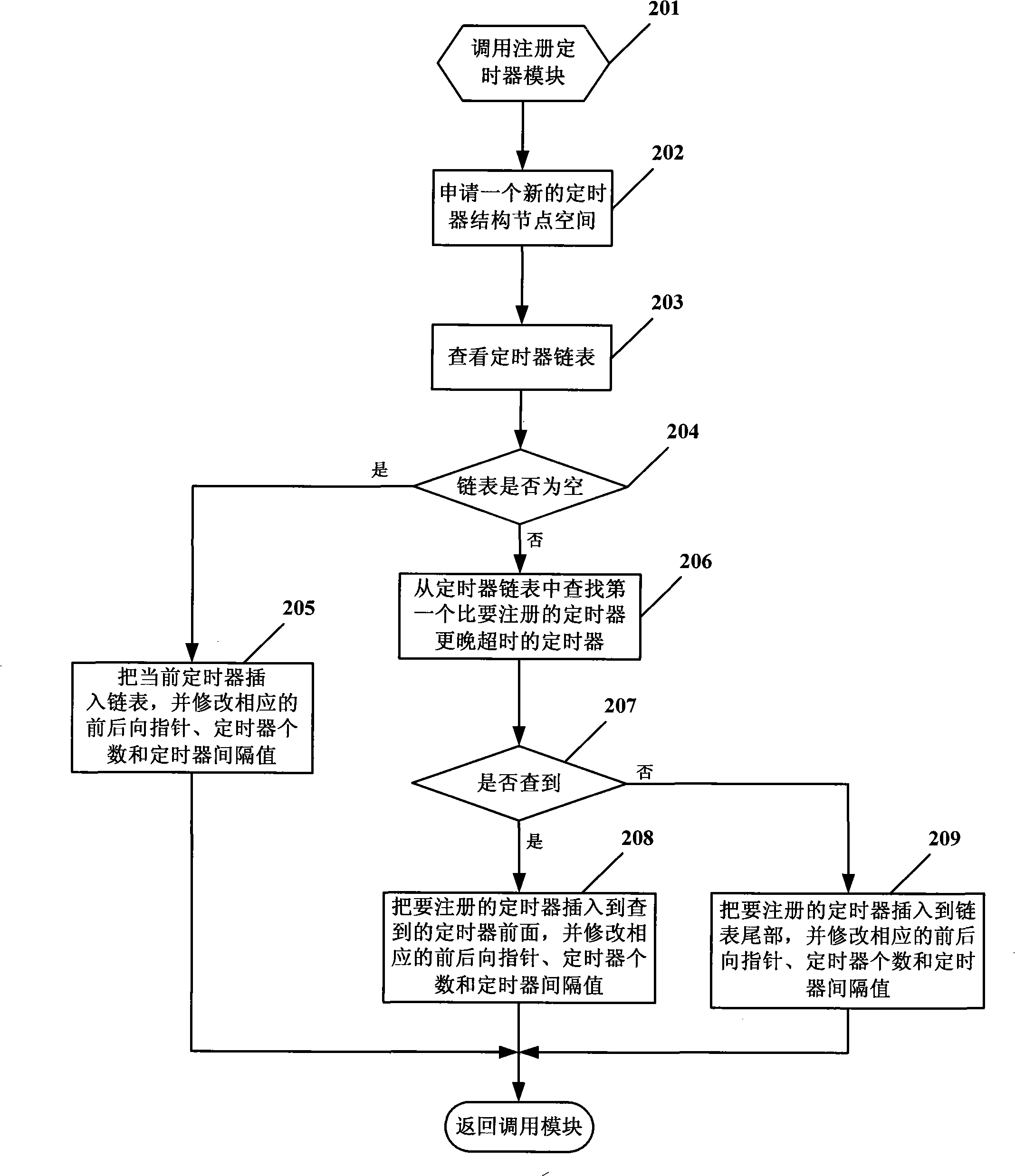
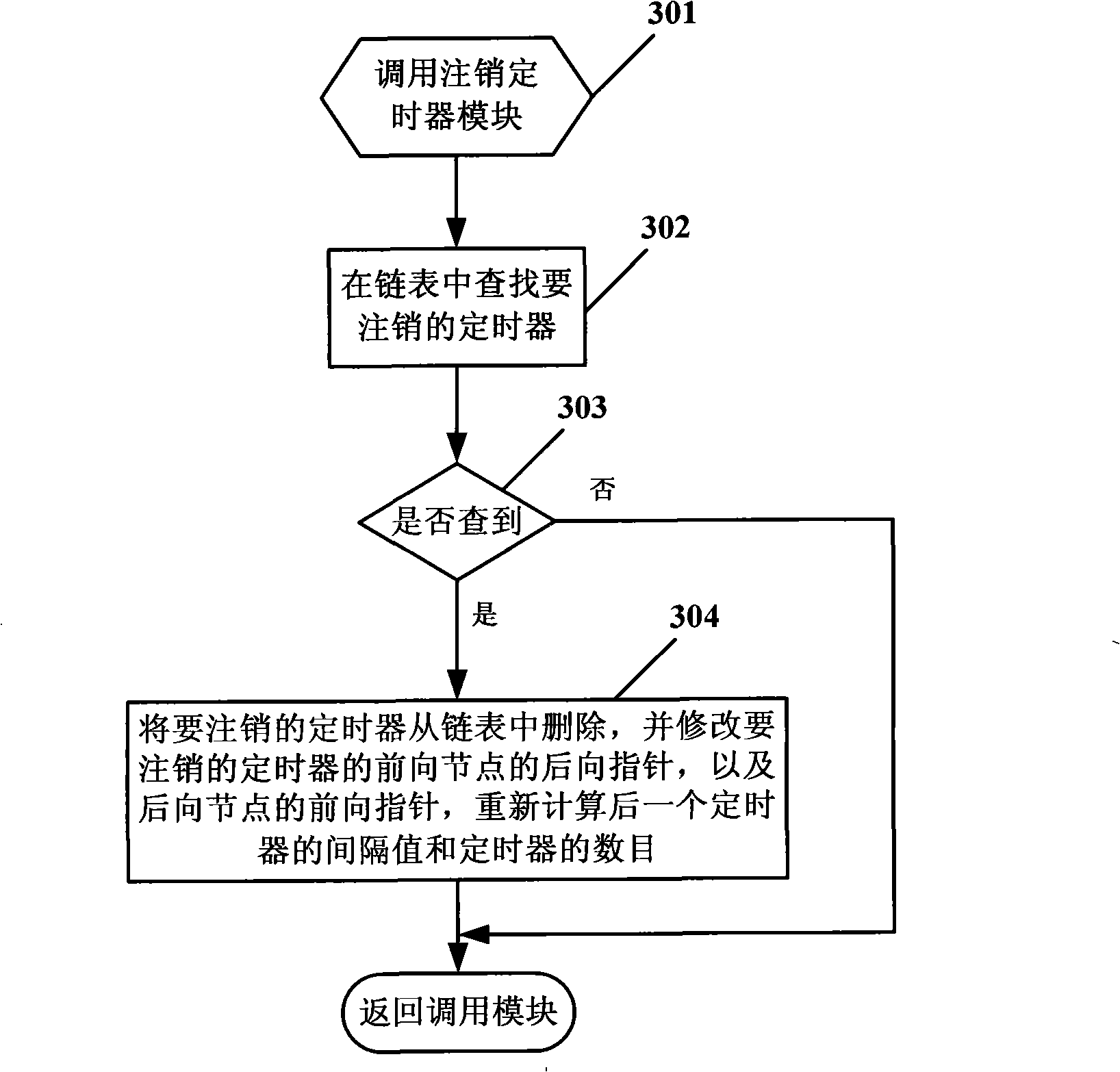
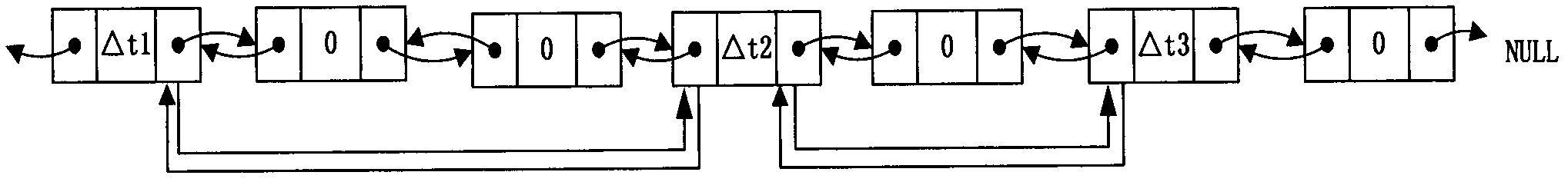
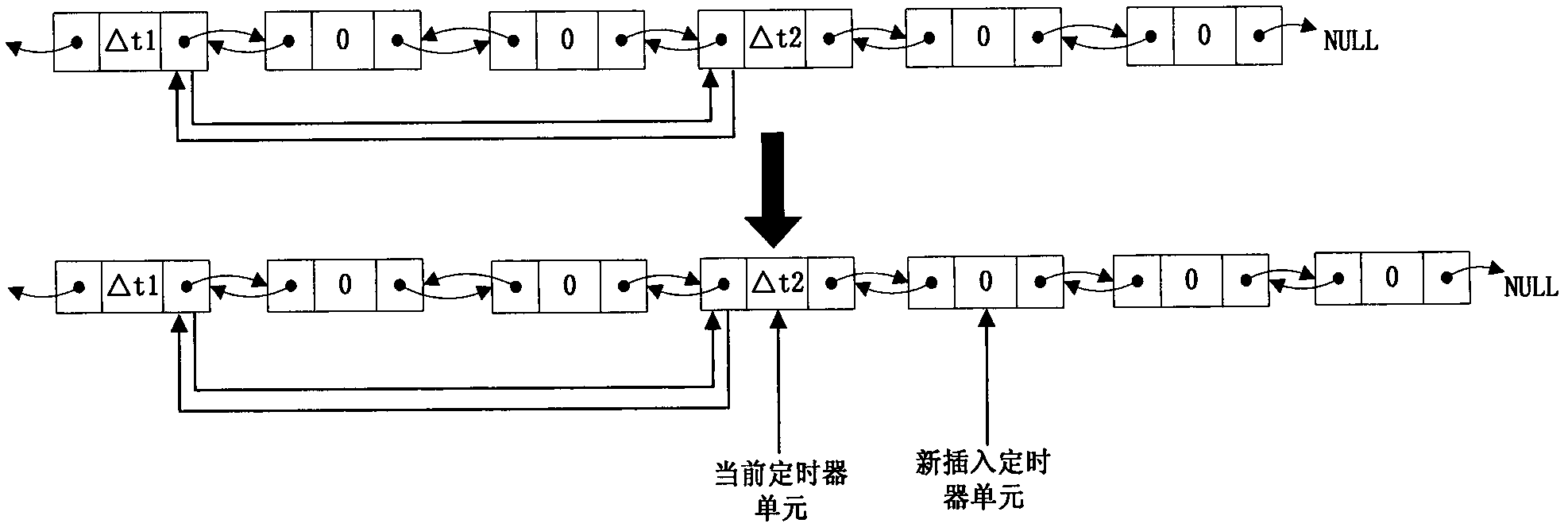
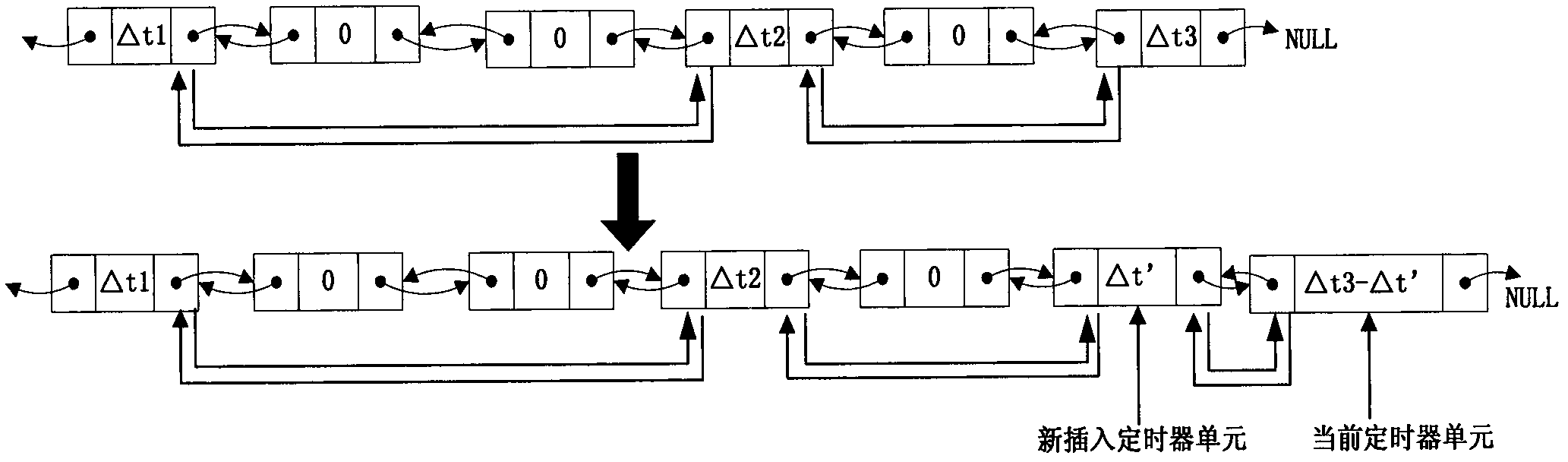
A real-time embedded system timer management method
InactiveCN102270156AReduce consumptionReduce the number of operationsProgram initiation/switchingResource consumptionComputer science
The invention provides a real-time embedded system timer management method, the method comprising: using a doubly linked list to uniformly manage all timers, each timer corresponding to a timer node in the doubly linked list; In the linked list, all timer nodes are sorted in the order of timeout, and when the timer timeout time is the same, they are sorted according to the priority of the timer from high to low; when the timing period is reached, start from the first timeout timer Check the timeout of the timer until you find the first timer that has not timed out; put all the timed out timers into the timeout queue for corresponding timeout processing. The application of the present invention can reduce the consumption of CPU resources and improve the real-time performance of the system.
Owner:BEIJING HUAYUAN TECH
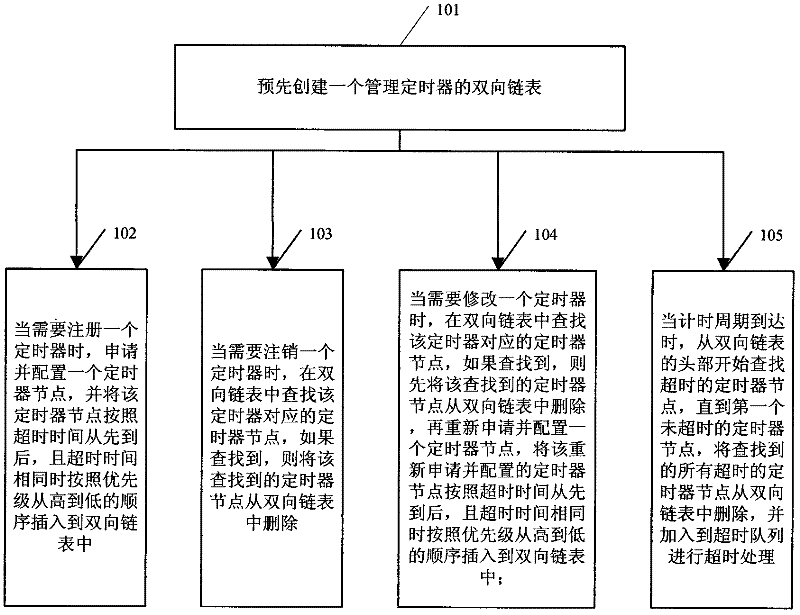
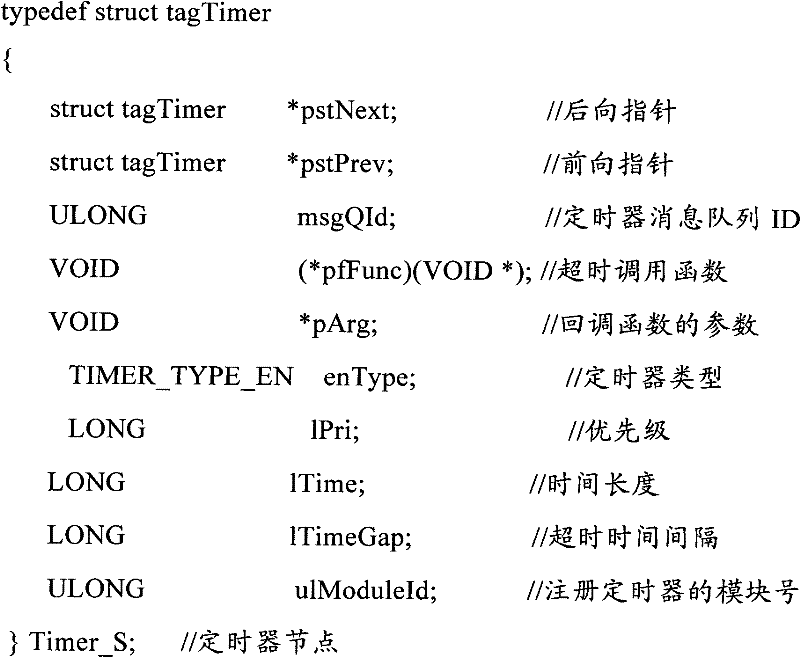
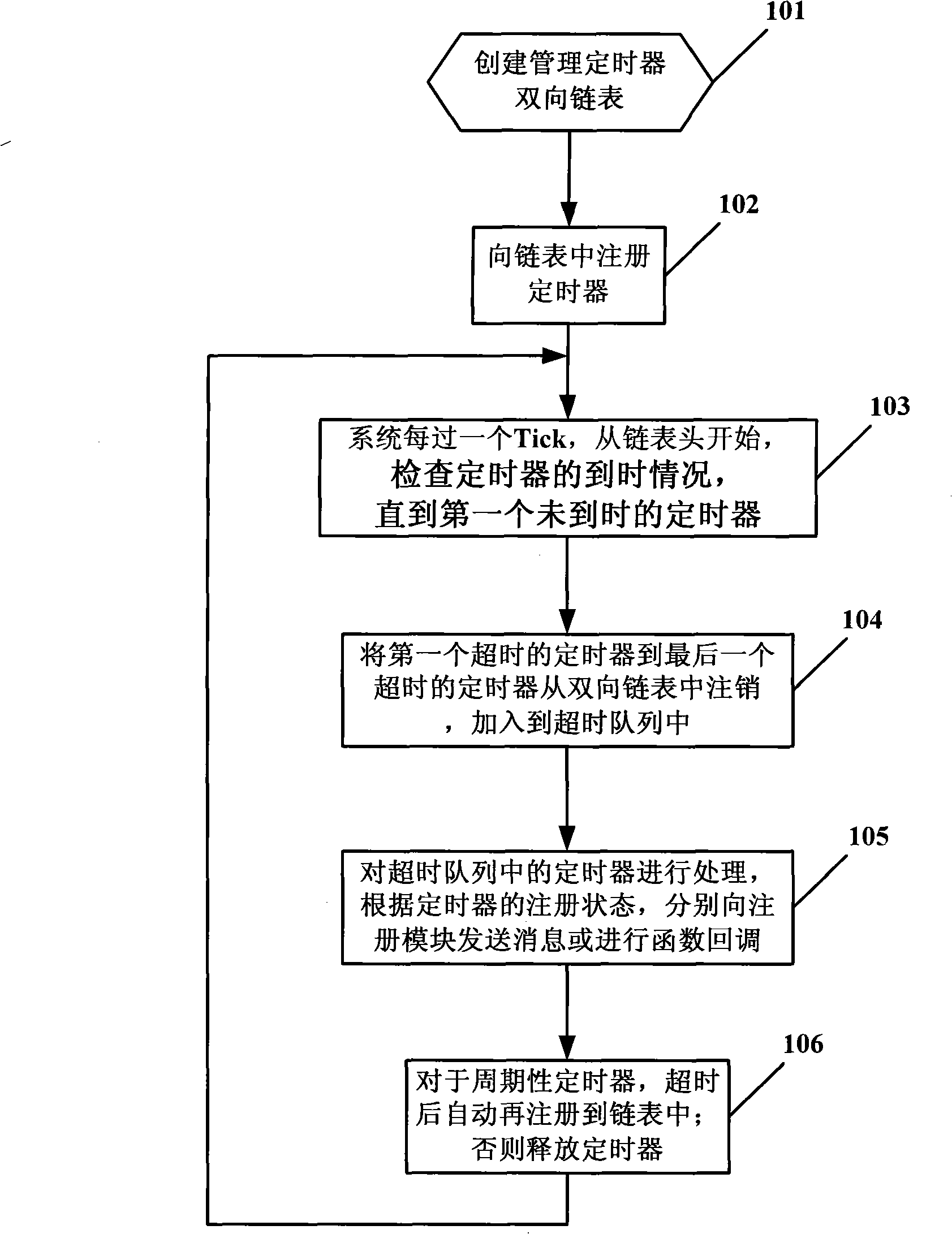
Management method for embedded system timer
The invention discloses a management method for an embedded system timer in the technical field of embedded system timer management. The technical proposal comprises the following steps: a two-way link list for managing the timers with the minimum size being 1 TICK is created; the timers are registered in the link list; when each TICK arrives the time, the head part of the link list starts checking the overtime status of the timers until reaching the first time which does not exceed the time; all the overtime timers are canceled from the two-way link list; according to the registering status of the canceled timers, messages or function callbacks are respectively sent to a registering module; and the overtime periodic timers can be automatically registered into the link list, or else, the timers are released. As the method adopts a two-way link list for management, the timers apply the memory during the registering, while the memory is released upon canceling; the memory overhead is decided by the current number of the timers, so as to effectively save the system memory.
Owner:BEIJING JIAXUN FEIHONG ELECTRIC CO LTD
Timer setting method under multithreading environment
InactiveCN103019805ASuitable for technical requirementsEasy to set upMultiprogramming arrangementsTimerDistributed computing
The invention discloses a timer setting method under the multithreading environment. On the basis of the traditional increment timer, one index structure and a double linked list are introduced in to improve the time efficiency of the timer. The traditional increment timer adopts one double linked list to manage a timer unit according to a time overtime sequence, and the steps of setting a new timer, clearing the timer and carrying out timer overtime judgment are all carried out by the linked list. When the number of the timer unit is huge, the operations occupy a great quantity of CPU (central processing unit) resources. According to the index structure introduced by the invention, the timer unit can be quickly looked up and managed according to the unique identification of the timer, first timer units triggered at different time periods are connected by the newly-added double linked list, the setting operation performance of the new timer is improved, and the timer time efficiency is improved under the condition that little space overhead is added. The timer setting method under the multithreading environment, which is disclosed by the invention, has the advantage that an implementation method is simple and easy to understand, and is suitable for the requirement on the timer under the common environment.
Owner:PCI TECH GRP CO LTD
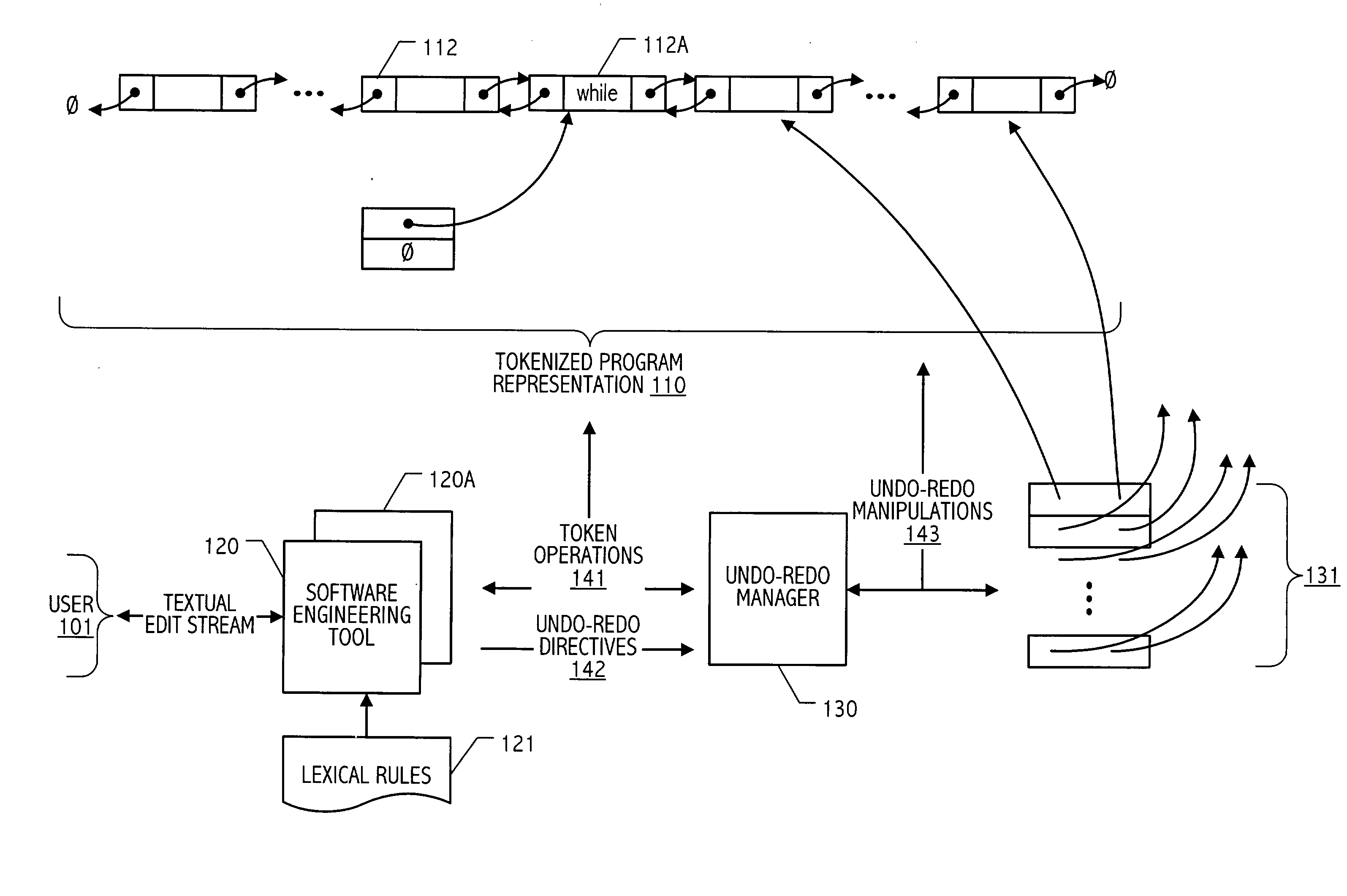
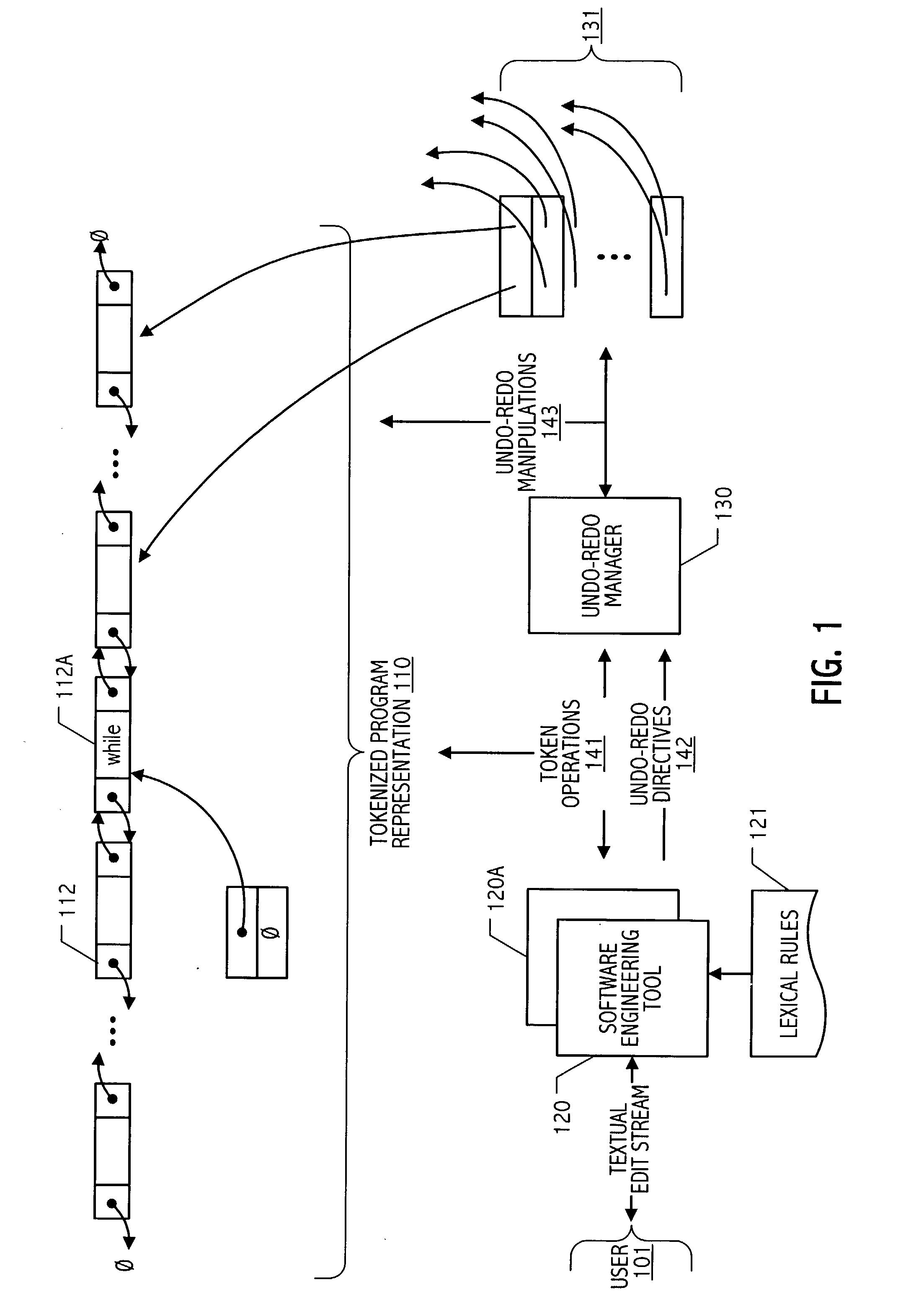
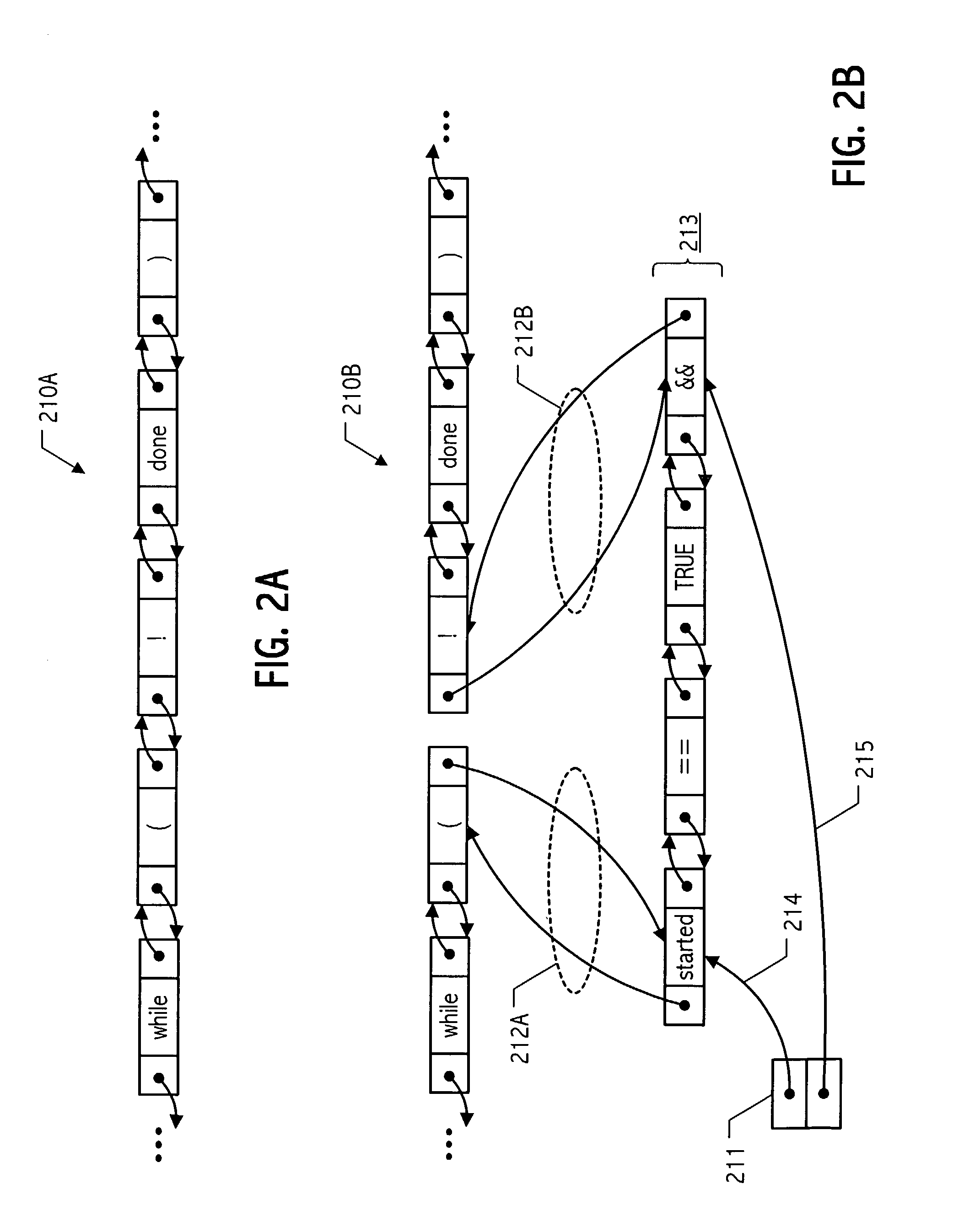
Undo/redo technique for token-oriented representation of program code
ActiveUS20040006764A1Efficient undo-redo supportDigital computer detailsIntelligent editorsEngineering toolDoubly linked list
An editor or software engineering tool may be configured to represent program code as a doubly-linked list of lexical tokens and to maintain, coincident with an operation that modifies contents of the list, an undo object that identifies opposing end nodes of a sublist of one or more lexical tokens corresponding to a substring that is either inserted into or removed from the list by the operation. In this way, lexical tokens corresponding to an inserted substring can be readily and efficiently excised to restore a pre-insertion tokenized list state. Similarly, lexical tokens corresponding to a removed substring can be readily and efficiently reinstated to restore a pre-deletion tokenized list state. Advantageously, undo support once employed to restore a prior tokenized list state is symmetrically available to support redo operations. In some embodiments in accordance with the present invention, undo-redo entries are maintained in an operation ordered set that is traversed to support one or more operations in either the undo or redo directions. In some realizations, such an ordered set of undo-redo entries is maintained by, or in conjunction with, an undo-redo manager.
Owner:ORACLE INT CORP
Service ordering method and service ordering platform
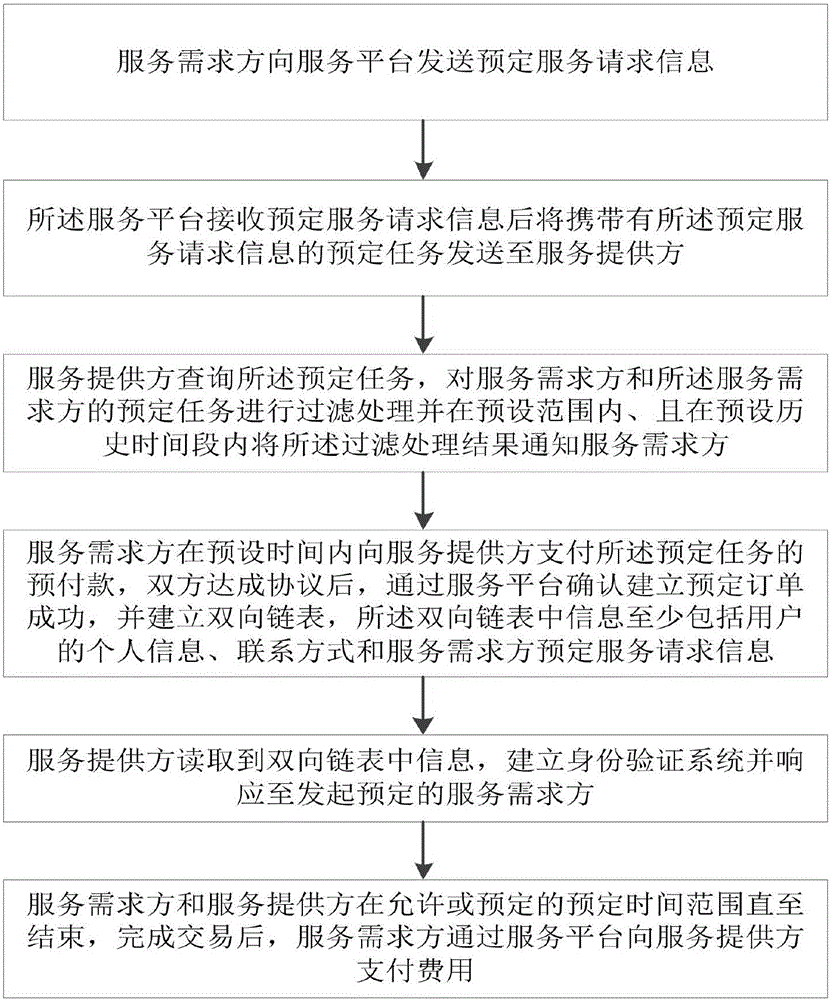
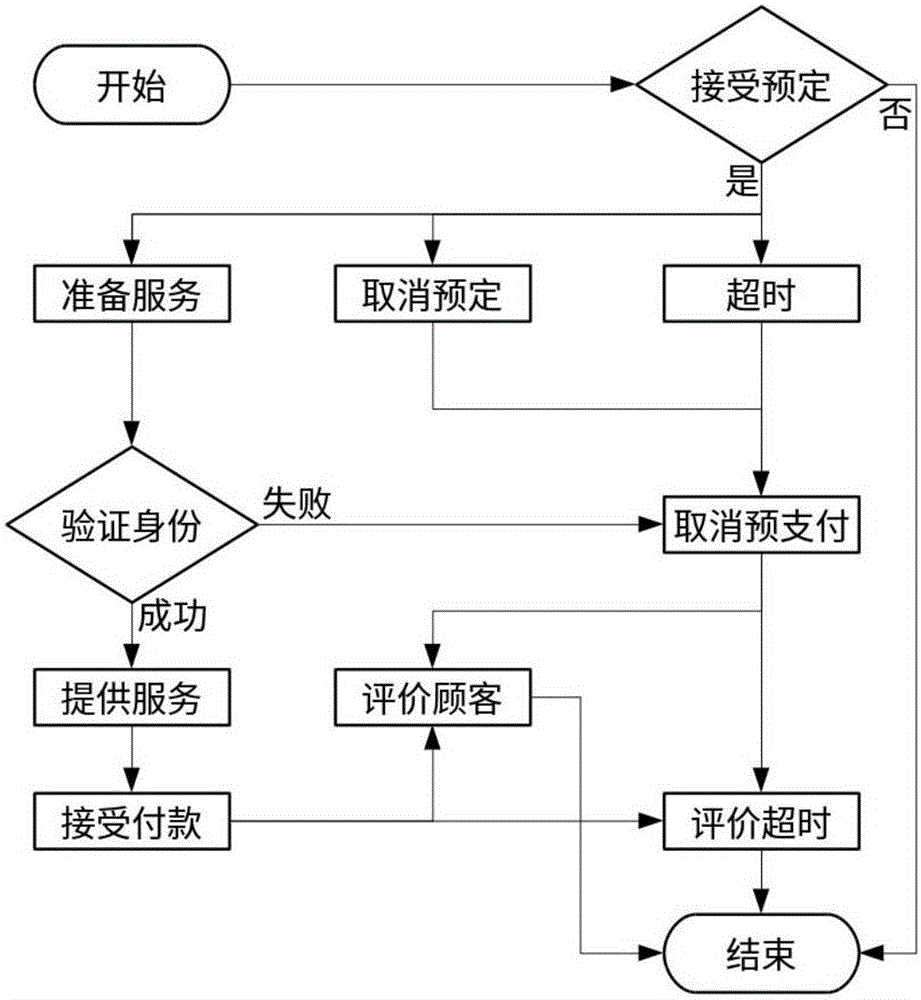
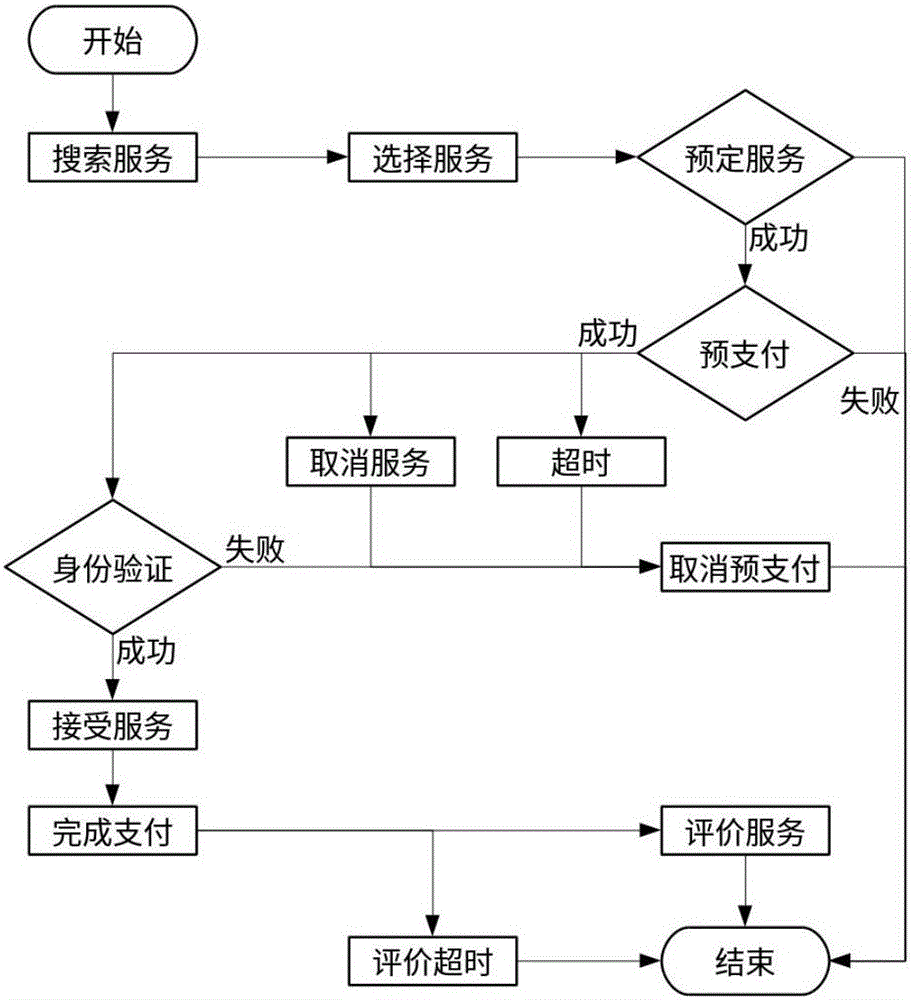
InactiveCN105701740AFair and secure payment modelReduce waiting timeData processing applicationsService provisionPayment service provider
The invention relates to a service ordering method and a service ordering platform. The service ordering method comprises the steps of transmitting preset service request information by a service requiring party to a service ordering platform; after receiving preset service request information by a service ordering platform, transmitting preset service request information to a service provider; querying a preset task by the service provider, and filtering the service requiring party and filtering the preset task of the service requiring party; paying advance payment of a preset task by the service requiring party to the service provider in preset time period, confirming successful order establishment and establishing a bidirectional chain table through the service ordering platform; reading information in the bidirectional chain table by the service provider, establishing an identity verification system; keeping the service requiring party and the service provider operate in an allowed or preset time period until time is up, and after transaction, paying cost by the service requiring party to the service provider through the service ordering platform. The service ordering platform comprises a terminal logging-on module, a service searching module, a service provider filtering module, a payment module, an identity verification module, an evaluation module and a platform processing module.
Owner:吴江
NAT session management method based on distributed system
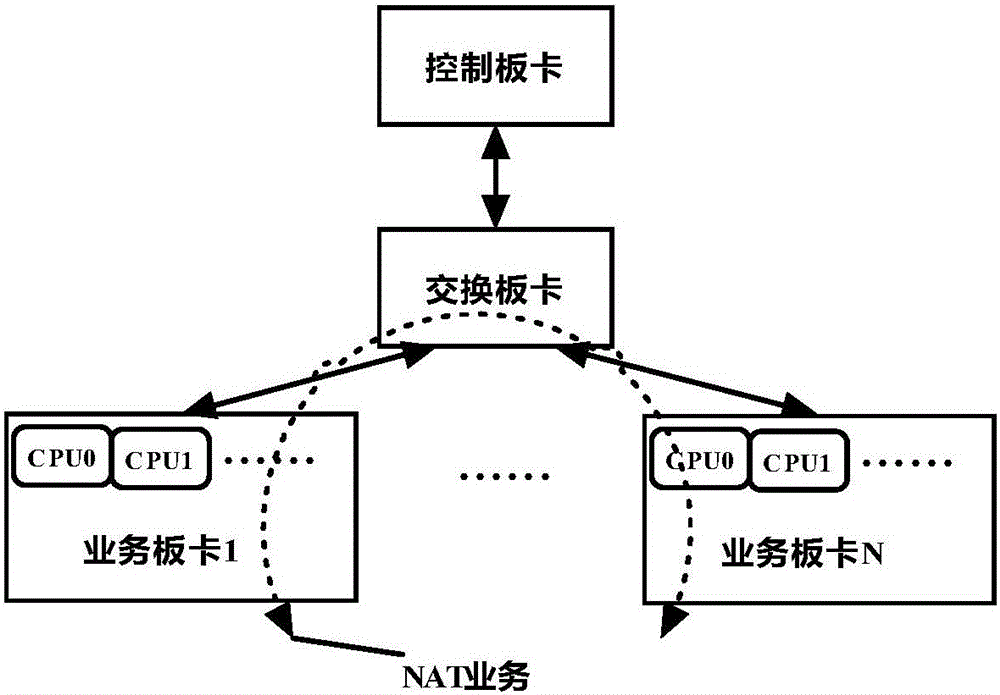
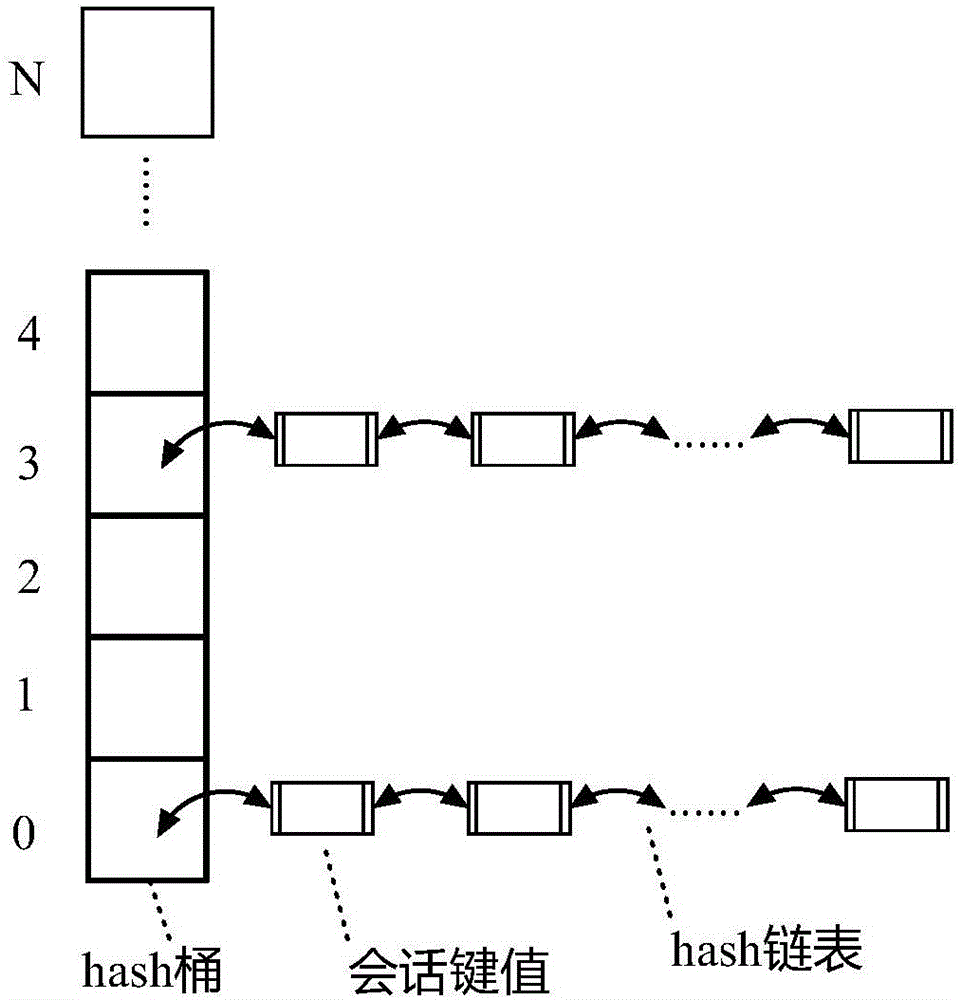
ActiveCN106790556AImprove search speedImprove aging efficiencyTransmissionSession managementMaintenance management
The invention discloses a NAT session management method based on a distributed system. The NAT session management method based on a distributed system comprises the following steps: (1) creating a NAT session; (2) maintaining updates to the created NAT session; (3) performing an aging operation on the updated NAT session; (4) querying the NAT session performed the aging operation. According to the NAT session management method based on a distributed system, the hash bucket, the hash linked list and other data structures are used to realize the creation and the update maintenance management of the NAT session, and the session key values can be hashed evenly into each hash bucket by setting the hash bucket parameters to proper values, therefore, the session key search speed can be effectively improved; meanwhile, the sessions are linked by means of the separate double linked list to complete the aging and query management of the created sessions, therefore, frequent locking of the hash buckets is avoided, and the aging and query efficiency of the sessions is improved.
Owner:SHENZHEN FORWARD IND CO LTD
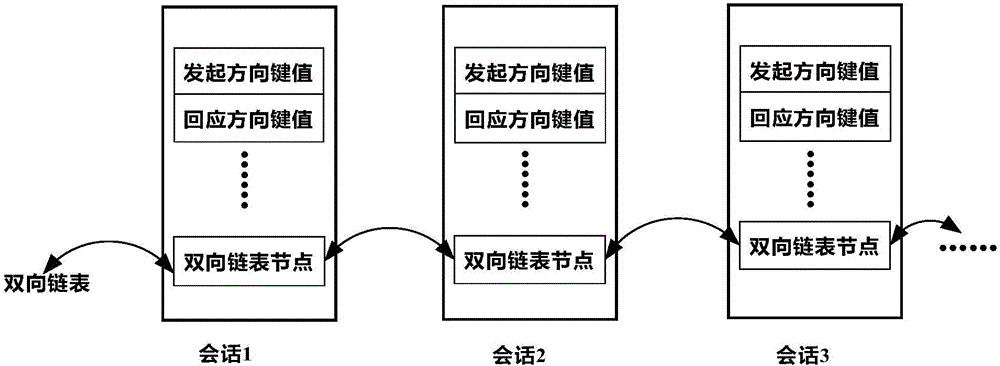
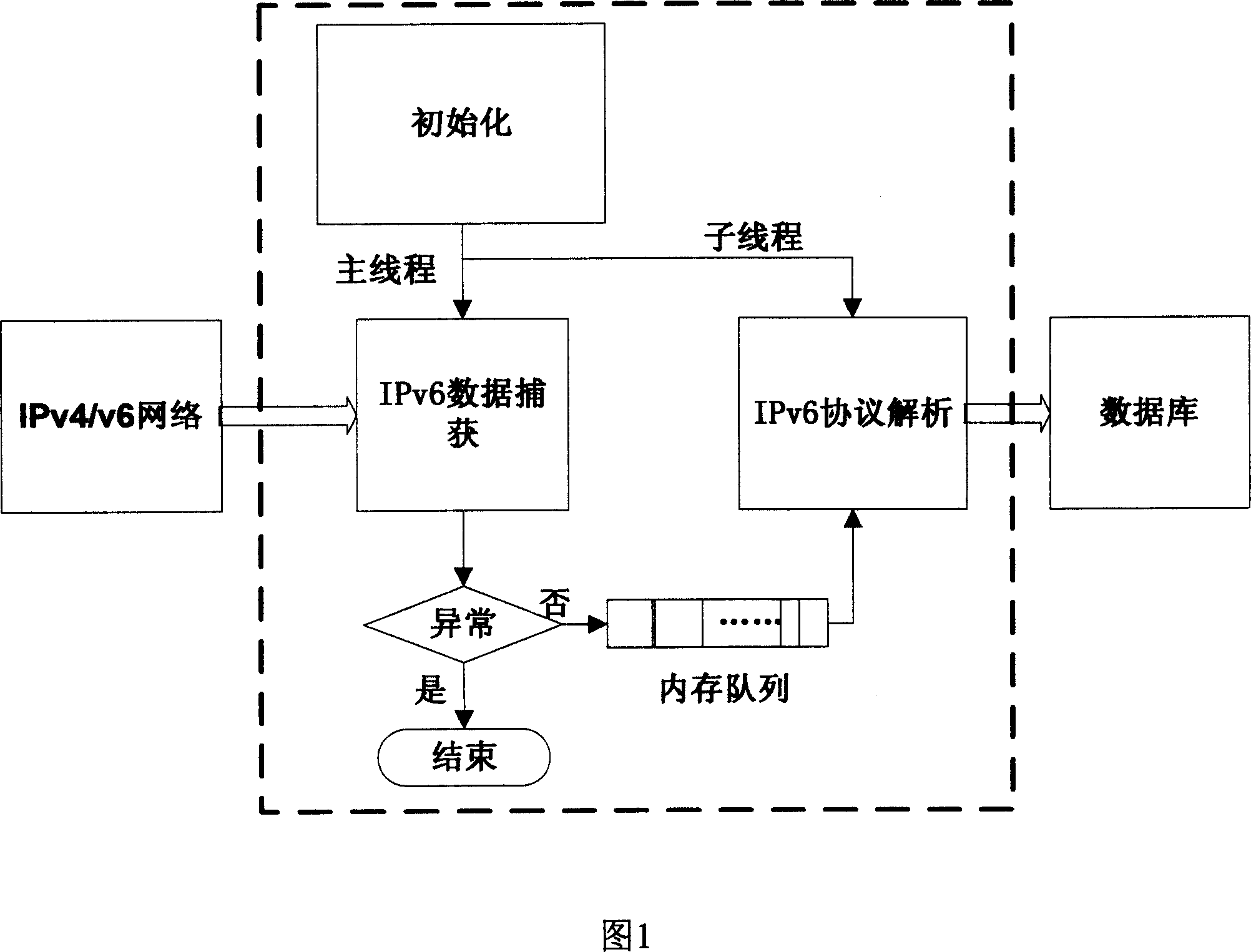
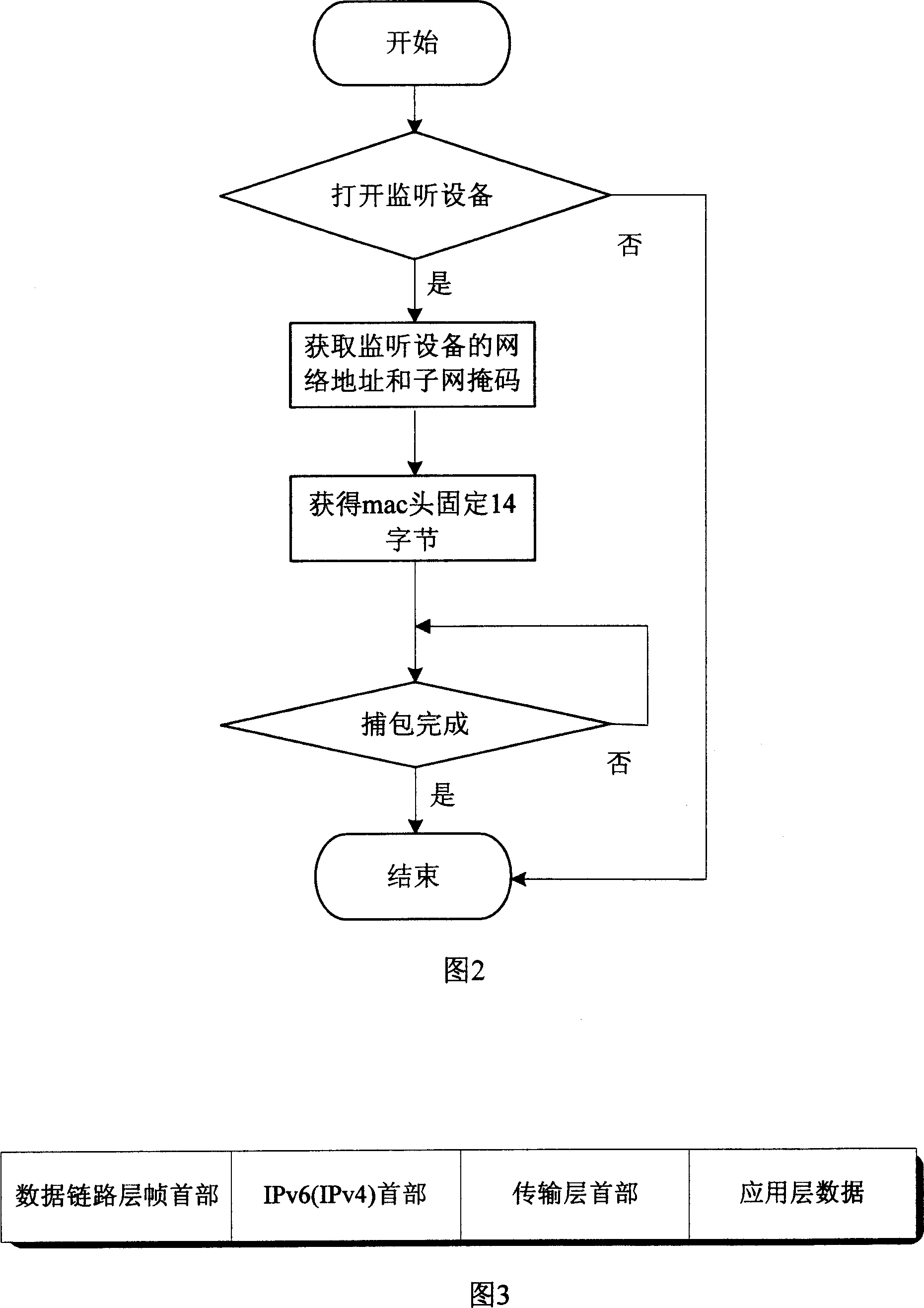
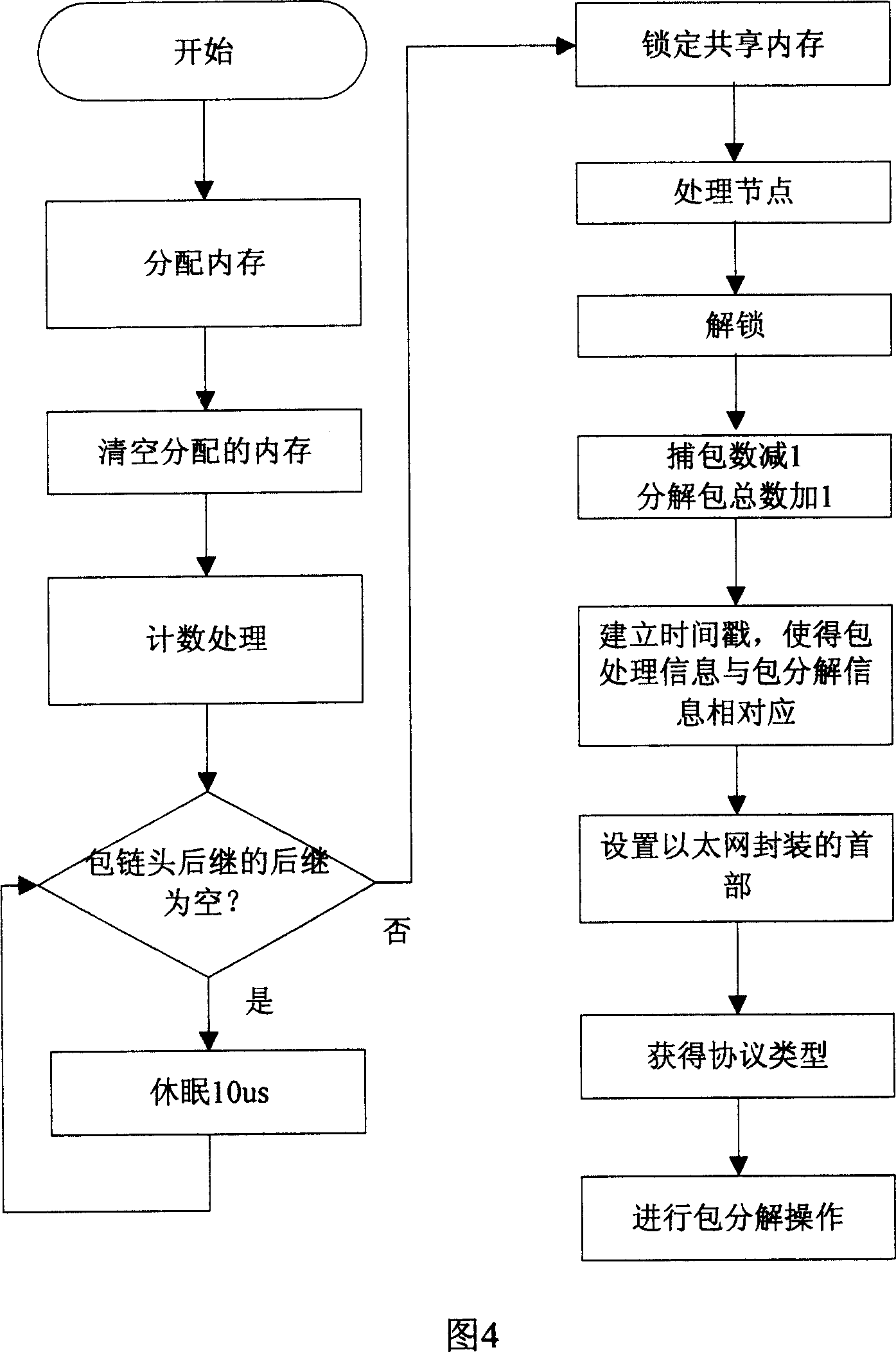
A system and realization method for high speed capture and quick storage of IPv6 data
The invention relates to a system for picking up IPv6 data at high speed and quickly storing, and a relative method. Wherein, it comprises an initialization module; an IPv6 data picking up module for real-time picking up the IPv4 / v6 dataflow through detecting interface, while the picked data can be used in following protocol analysis; IPv6 protocol analyze module for processing the picked IPc4 / v6 data to match the picked data from outer to inner with variable protocols, to analyze the protocols of all layers, to be stored in memory unit set for different protocols. The invention uses bidirectional linkage list technique to quickly write and discompose the picked IPv6 / v4 data pack in memory queue. And it uses multi-process technique to pick and record high-speed data at IPv6 / v4 network, to be analyzed and stored.
Owner:BEIJING JIAOTONG UNIV
Method for debouncing stream media
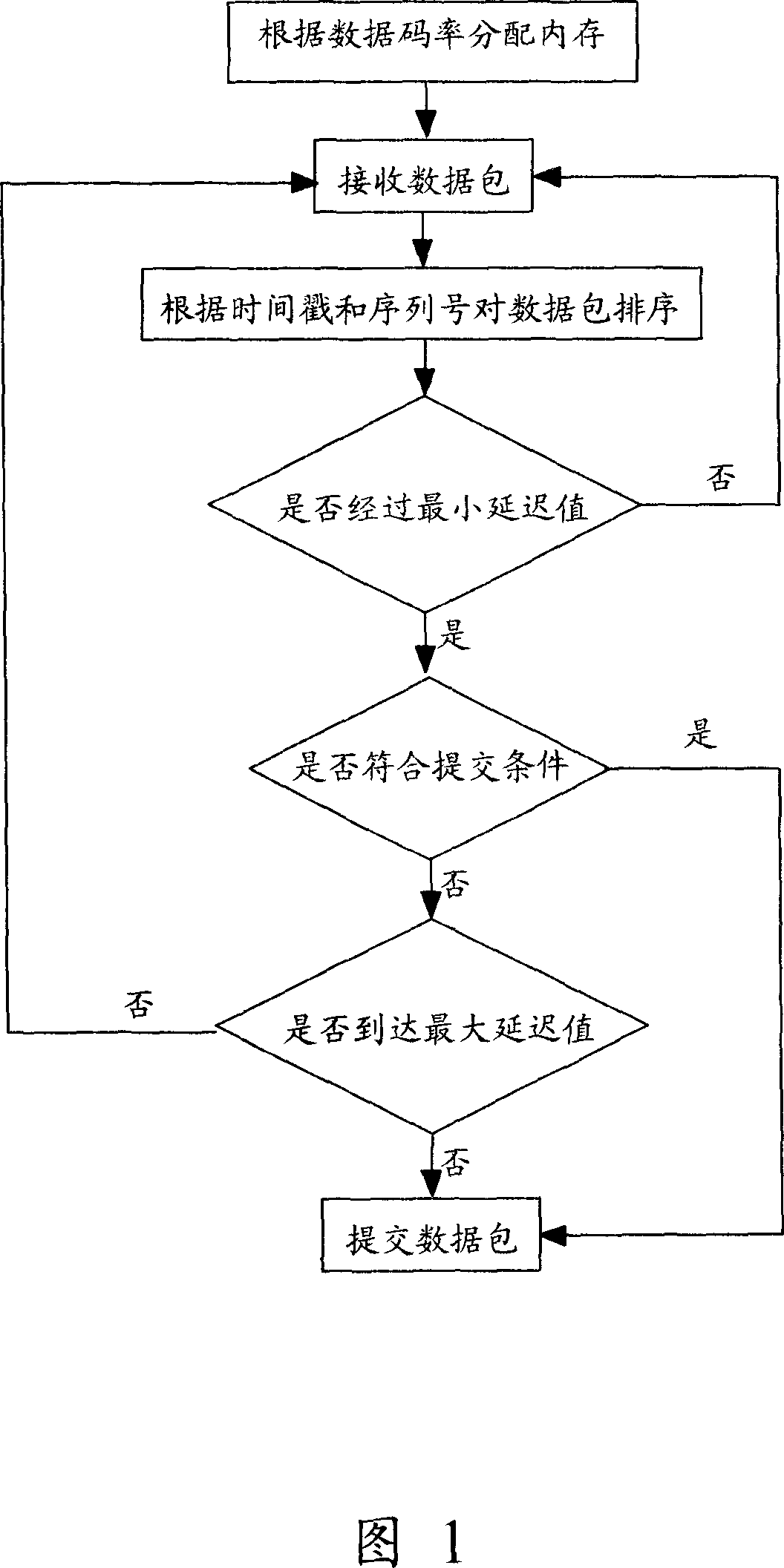
ActiveCN1960315AAvoid wastingQuality improvementData switching networksRelevant informationNetwork packet
The method comprises: applying a memory area having a fixed length as a buffer area; receiving packet and extracting the relevant information of the packet; ordering the packet in the buffer area according to relevant information; if passing through a minimal time delay value, then checking the packets in the buffer area to decide if it confirms with the referring condition; if yes, then referring the packets in the buffer area to the application program; if not, then continuing to receive the packets, until the packets in buffer area being accordance with the refereeing condition, the packet in the buffer area just be referred out; if passing through a maximal time delay value, then packets in the buffer area are forced to be referred out.
Owner:KONKA GROUP
Periodic wear balancing method and memory management method of phase change memory
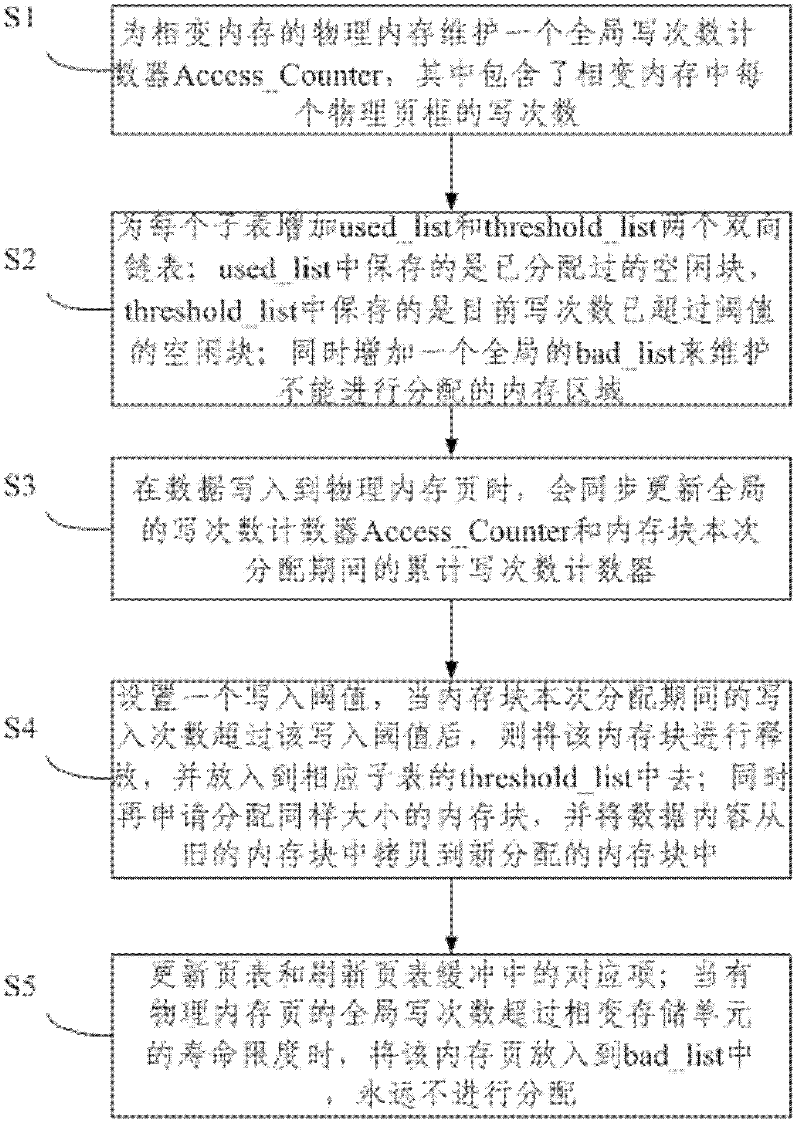
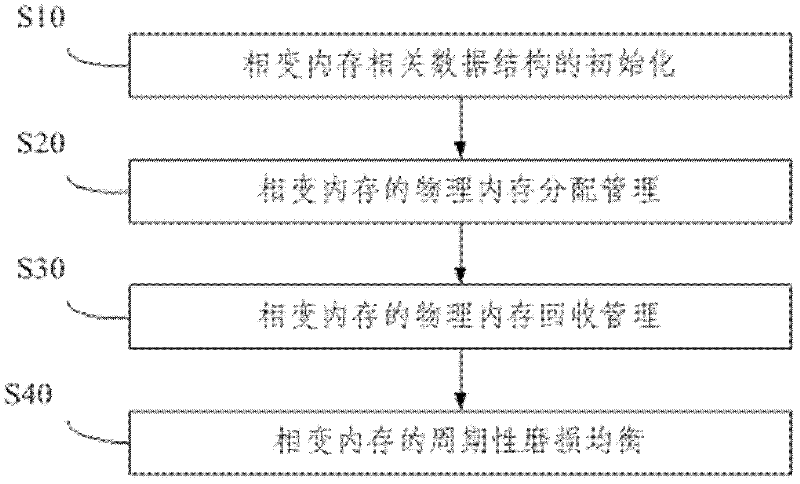
ActiveCN102495806AAdd supportImprove reliabilityMemory adressing/allocation/relocationPhase-change memoryData content
The invention relates to a periodic wear balancing method and a memory management method of a phase change memory. The method comprises the steps of: S1, maintaining a counter for overall writing times for a physical memory of the phase change memory; S2, increasing used-list and threshold-list doubly linked lists to each sublist, and simultaneously increasing an overall bad-list to maintain the memory region which can not be allocated; S3, when the data is written to a physical memory page, synchronously updating the counter for the overall writing times and a counter for accumulative writing times of a memory block during current allocation; S4, setting a writing threshold, after the writing times of the memory block during the current allocution exceeds the writing threshold, releasing the memory block and placing the memory block in the threshold-list of the corresponding sublist, then applying to allocate a memory block with identical capacity, and copying the data content from an old memory block to the new allocated memory block; and S5, when the overall writing times of the physical memory page exceeds the life limit of a phase change storage unit, and placing the memory page in the bad-list so as not to allocate for ever.
Owner:TSINGHUA UNIV
Method for distributing and reclaiming idle blocks of file
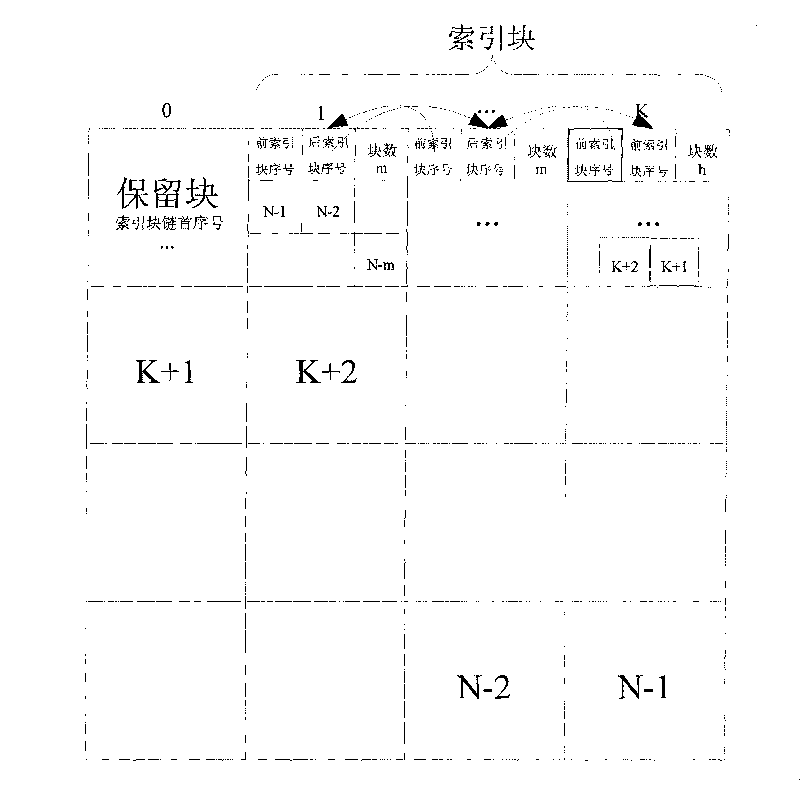
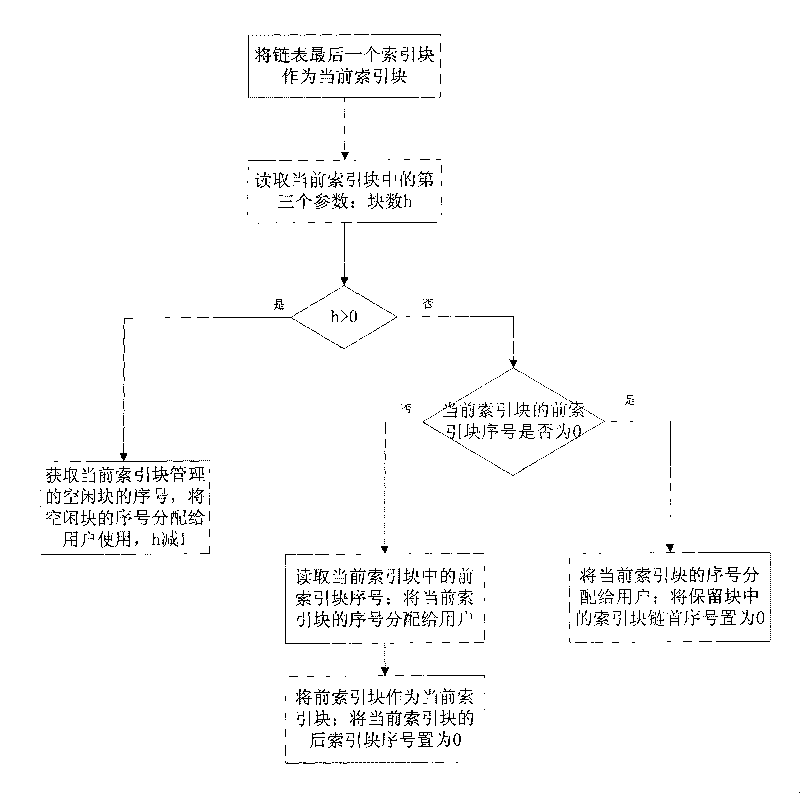
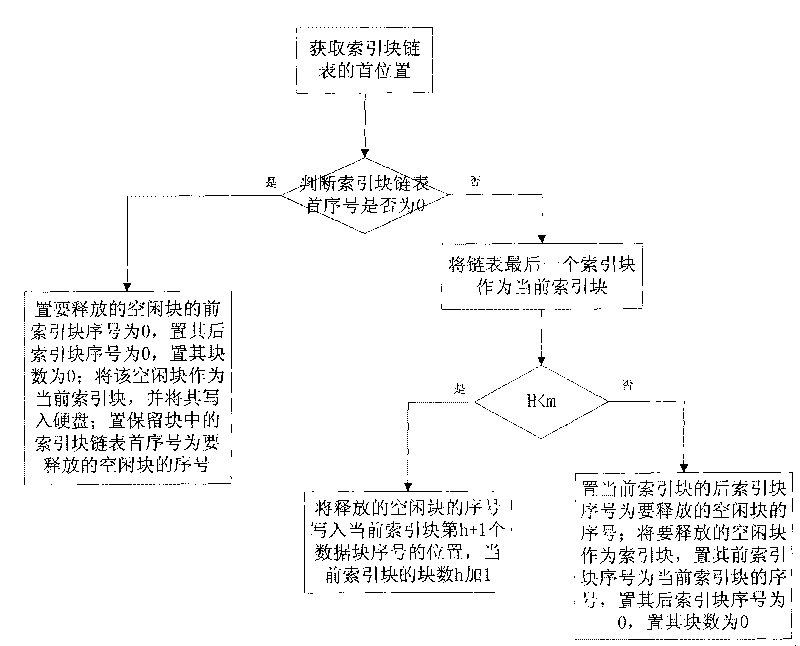
ActiveCN101692252ASeamless transitionSave memorySpecial data processing applicationsTime responseRecovery method
The invention discloses a method for distributing and reclaiming idle blocks of a file. The distributing method comprises the following steps: dividing the file into N file blocks according to the preset size, and numbering the file blocks; using K file blocks in the N file blocks as index blocks, and connecting the index blocks by adopting a bidirectional link table; storing a previous index block sequence number of the index block, a rear index block sequence number and the number of the idle blocks managed by the index block into the index blocks; and distributing the idle blocks managed by the index block in turn according to the order of the index blocks in the bidirectional link table, and correspondingly modifying information stored in the index blocks. The reclaiming method comprises the following steps: reclaiming the idle blocks in turn by the index blocks according to the order of the index blocks in the bidirectional link table, and correspondingly modifying the information stored in the index blocks. The method is particularly suitable for application situations with high real-time requirements. The method can save a large amount of storage space in the storage of mass historical data of the real-time database, and meanwhile can ensure the real-time response of the real-time database to the data due to extremely high idle block distribution speed.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
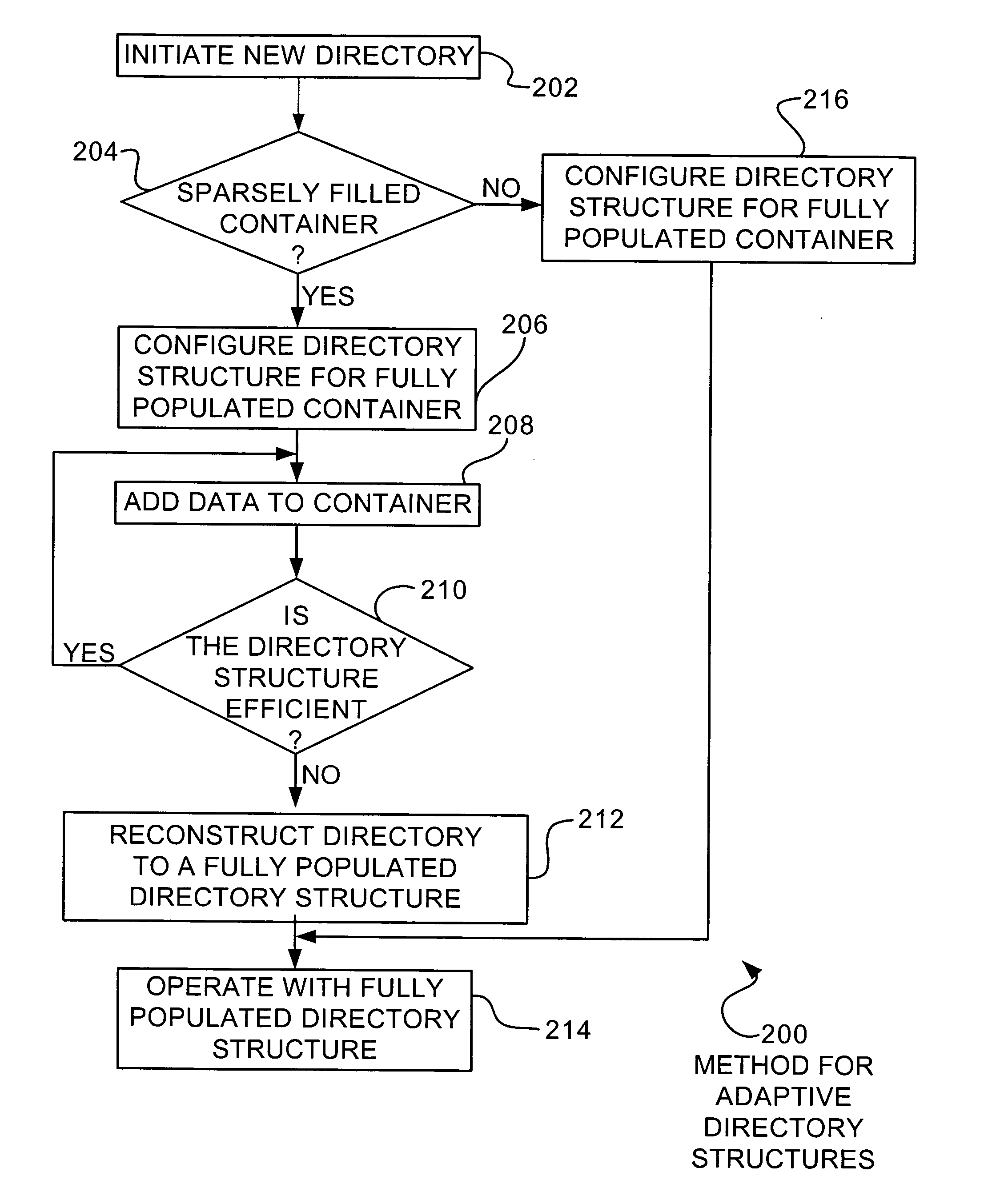
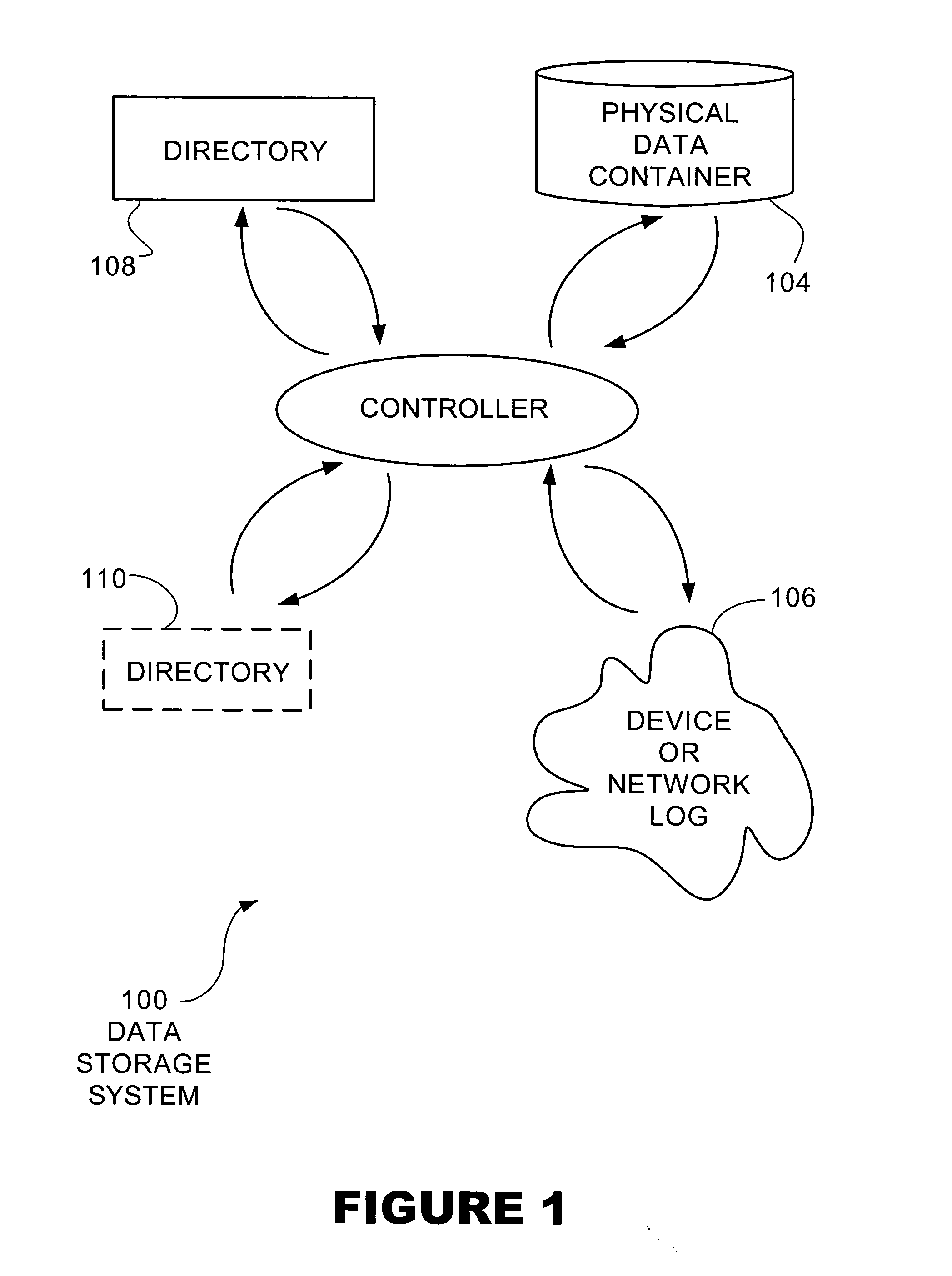
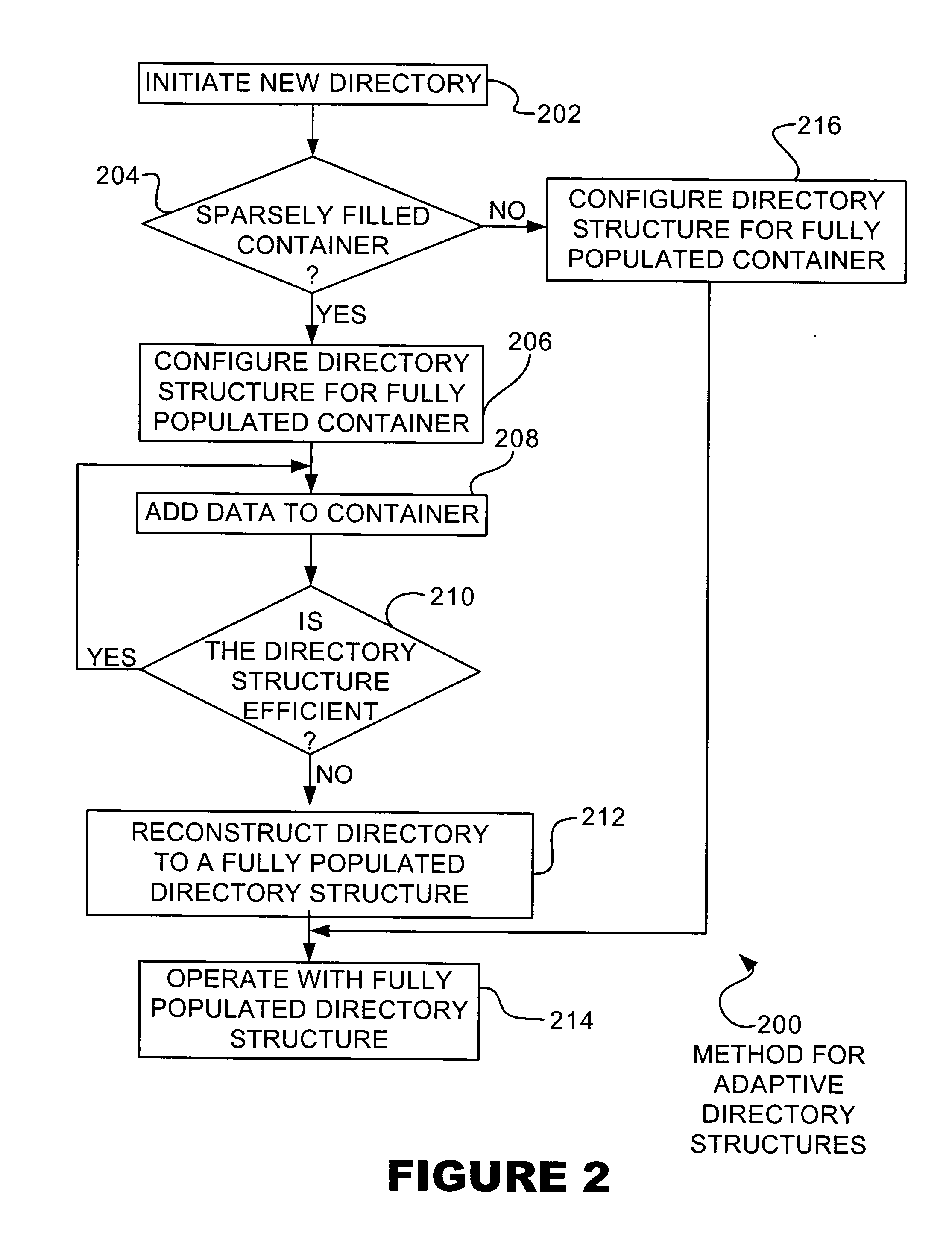
Adaptive mapping
InactiveUS20050055529A1Data processing applicationsMemory adressing/allocation/relocationSkip listDirectory structure
A directory structure for a sparsely filled data container comprises a linked list, doubly linked list, skip list, or other non-fully populated list technique. One or more hierarchical levels of such lists may be used for sparsely filled directories. The directory structure may be converted to a conventional look-up table directory by reconstructing the directory when the directory becomes populated to certain point.
Owner:SEAGATE TECH LLC
Distributed video transcoding scheduling method and system
InactiveCN102014282ATelevision systemsDigital video signal modificationArray data structureTranscoding
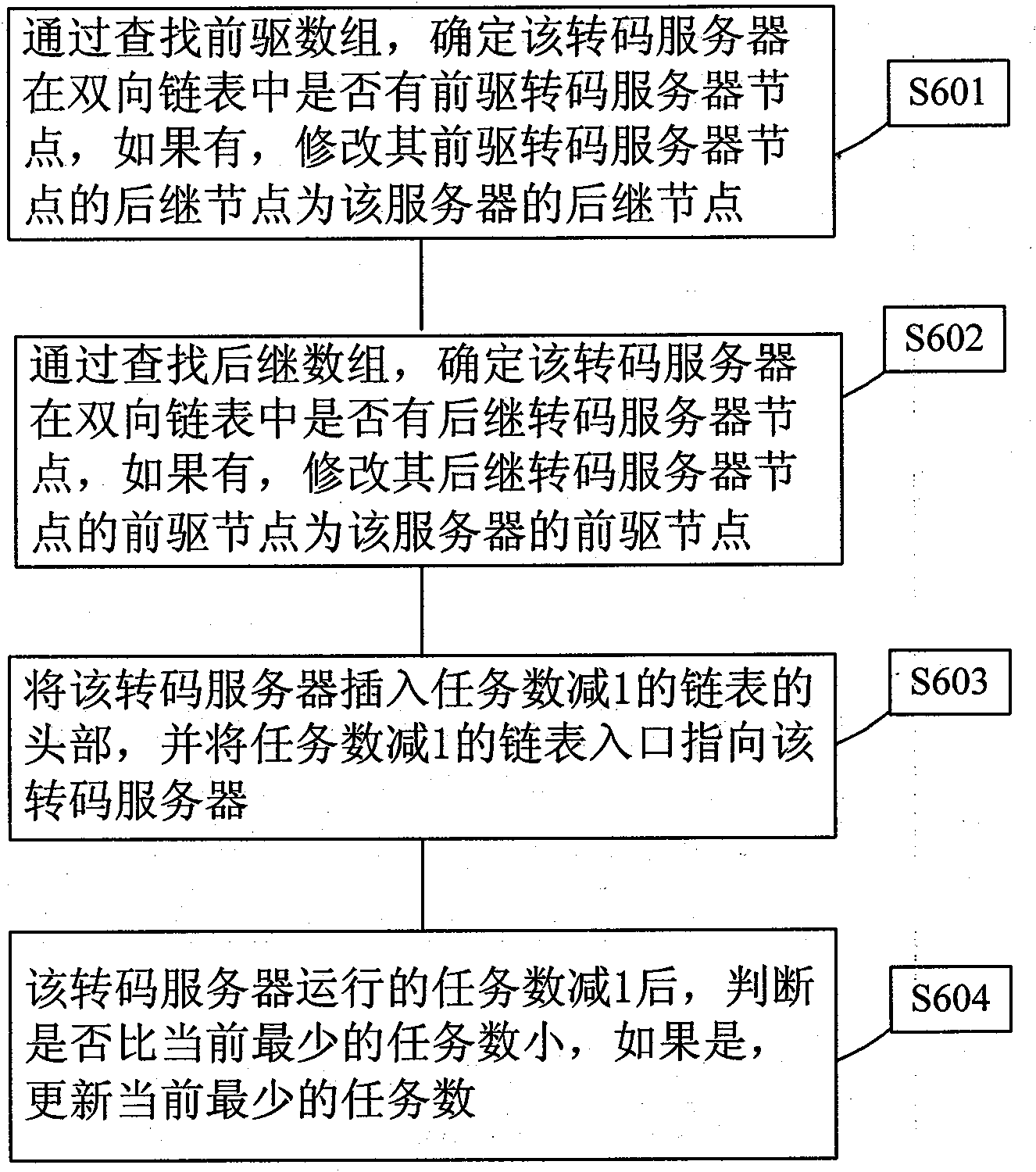
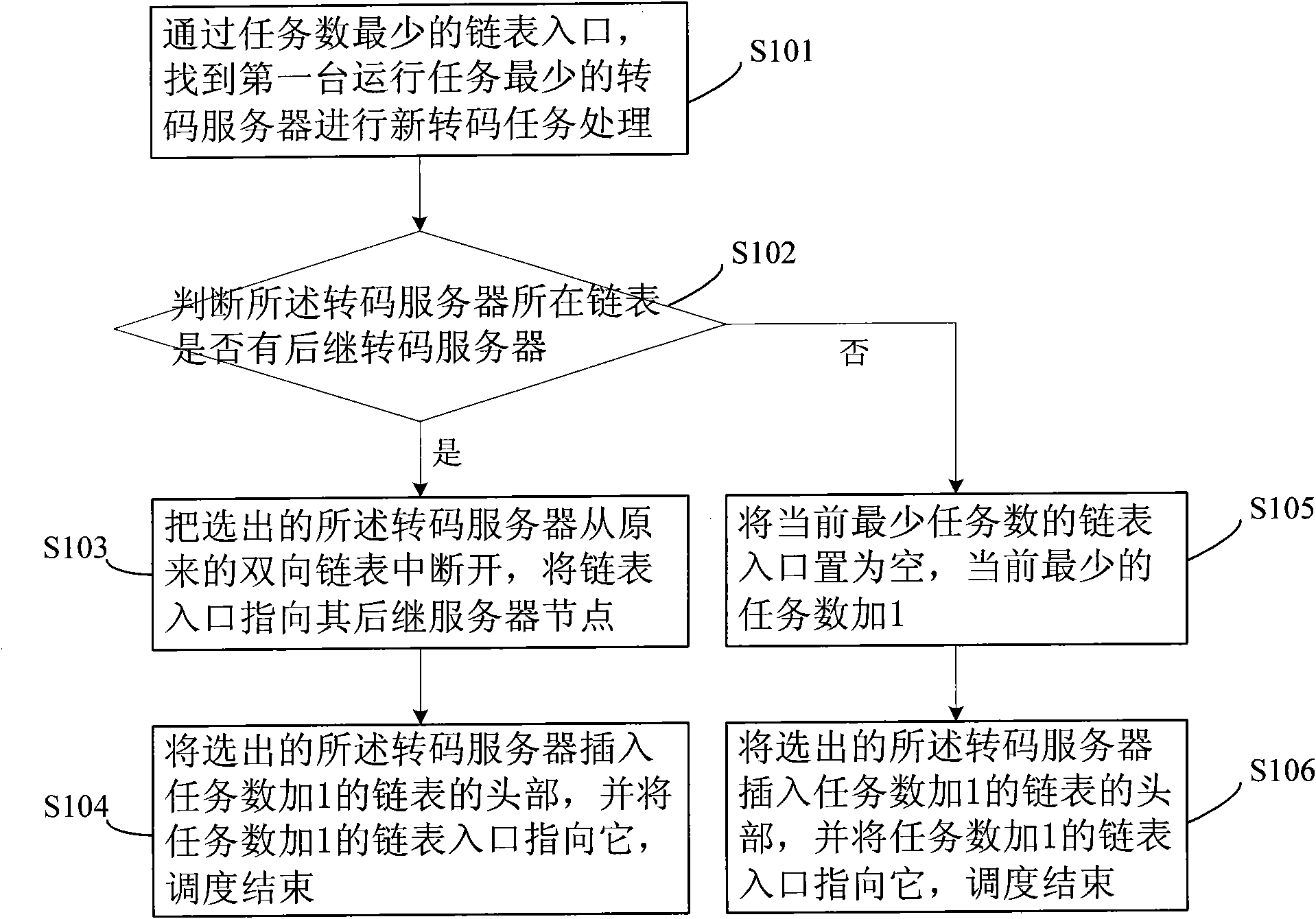
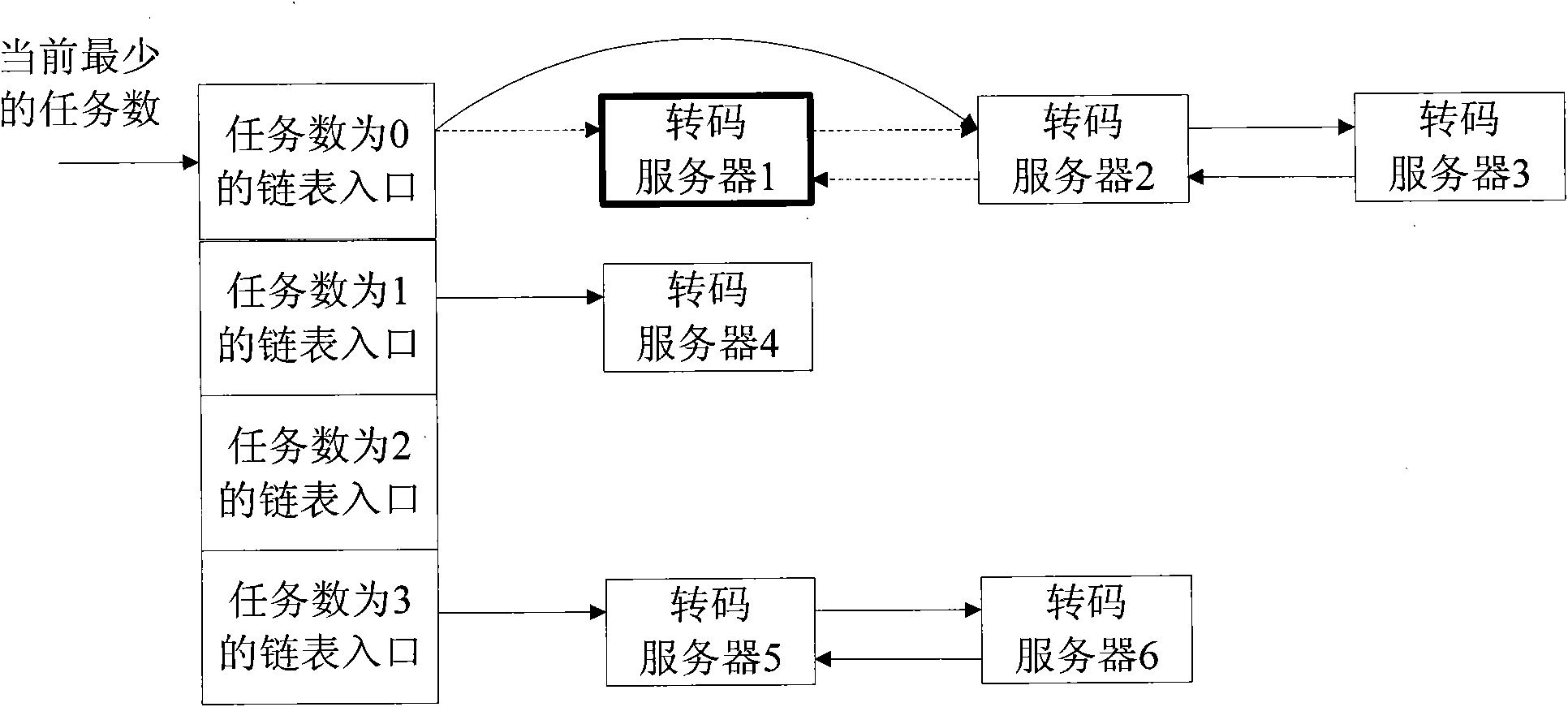
The invention discloses a distributed video transcoding scheduling method. Servers with the same number of running tasks are stored in a double linked list; two arrays of which the length is equal to the total number of the servers are used for describing the double linked list, one array indicates subsequent server nodes of the servers in the double linked list, and the other array indicates precursor server nodes of the servers in the double linked list; a linked list entry table is used for storing double linked list head nodes of each task number; and a variable is used for storing the current smallest task number. When a new transcoding task arrives, a first server with the smallest number of running tasks is found through a linked list entry with the smallest task number so as to perform new transcoding task processing; the server is deleted from the original double linked list, and is inserted into the head of a double linked list with the task number plus one; and when a certain server completes a transcoding task, the server is deleted from the original double linked list and is inserted into a double linked list with the task number minus one. The time complexity for video transcoding scheduling is lower.
Owner:融创天下(上海)科技发展有限公司
Memory leak detecting method and memory leak detecting device
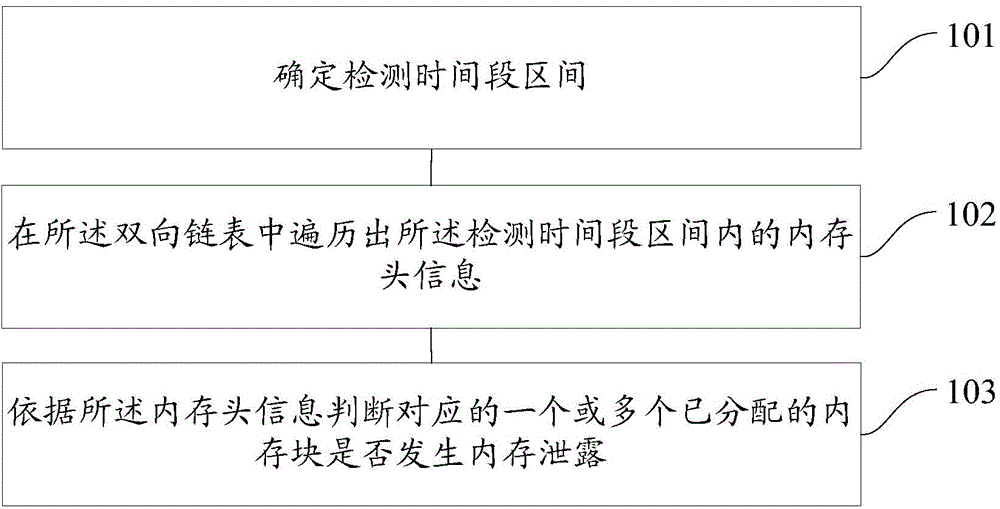
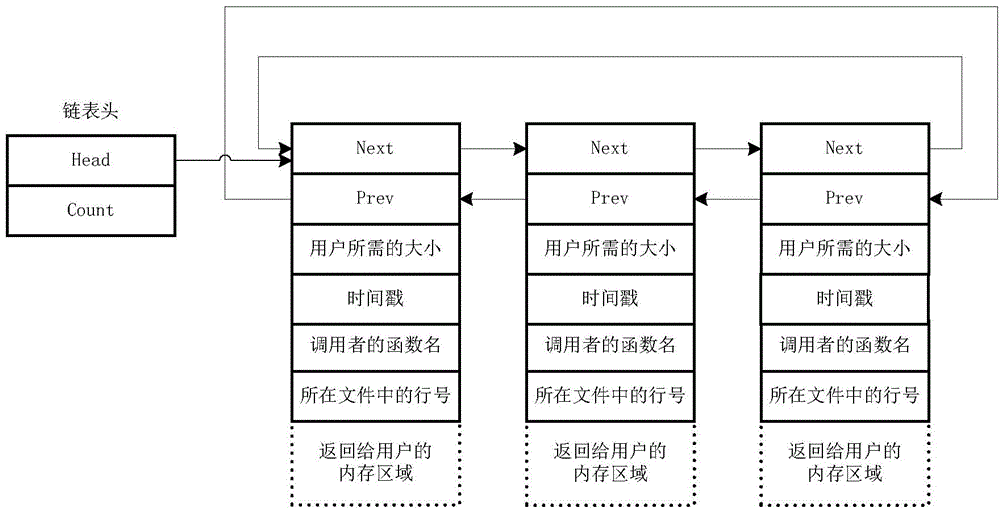
InactiveCN104572460AImprove accuracySmall scaleSoftware testing/debuggingMemory leakDoubly linked list
The embodiment of the invention provides a memory leak detecting method and a memory leak detecting device. A memory comprises a doubly linked list of an allocated memory; and the doubly linked list comprises memory header information of one or more allocated memory blocks. The method comprises the steps of: determining a detection time interval; traversing the header information in the detection time interval in the doubly linked list; and in accordance with the memory header information, determining whether the corresponding one or more allocated memory blocks are subject to memory leak. By the memory leak detecting method and the memory leak detecting device, memory leak can be visually detected in real time, the software performance is improved, and manual operation is reduced or avoided, so that the method and the device are labor-saving and time-saving, the operation difficulty is reduced, the working efficiency is improved, the cost is reduced, the accuracy of the detection of memory leak is improved, and the leaked memory can be recycled in the entity life cycle.
Owner:DATANG MOBILE COMM EQUIP CO LTD
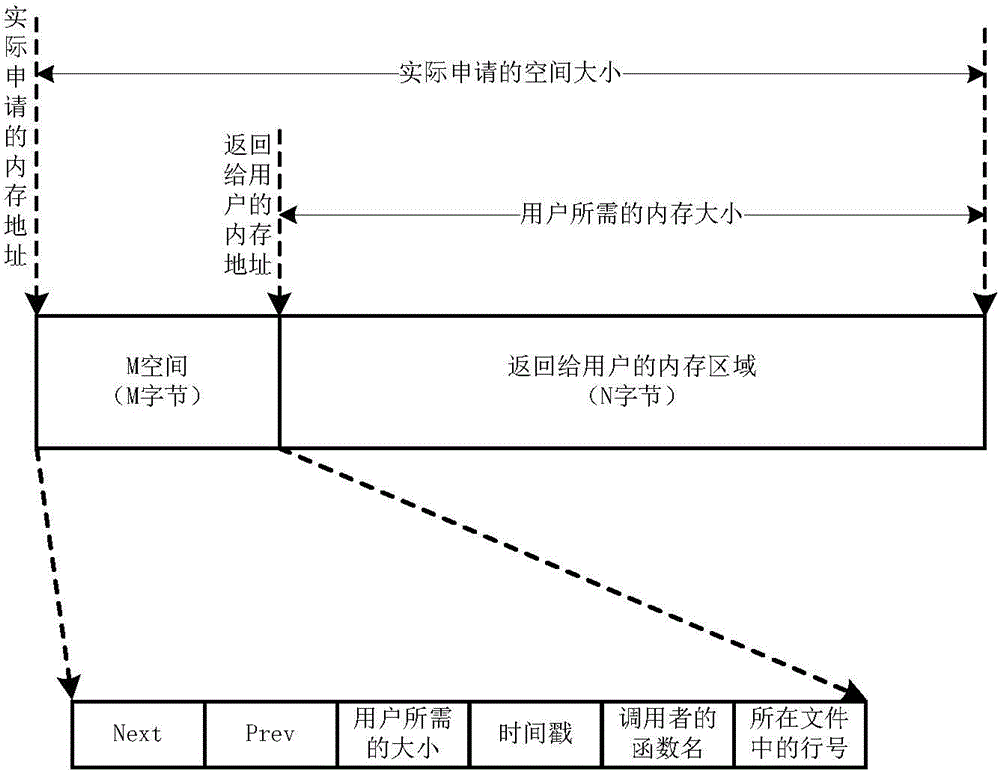
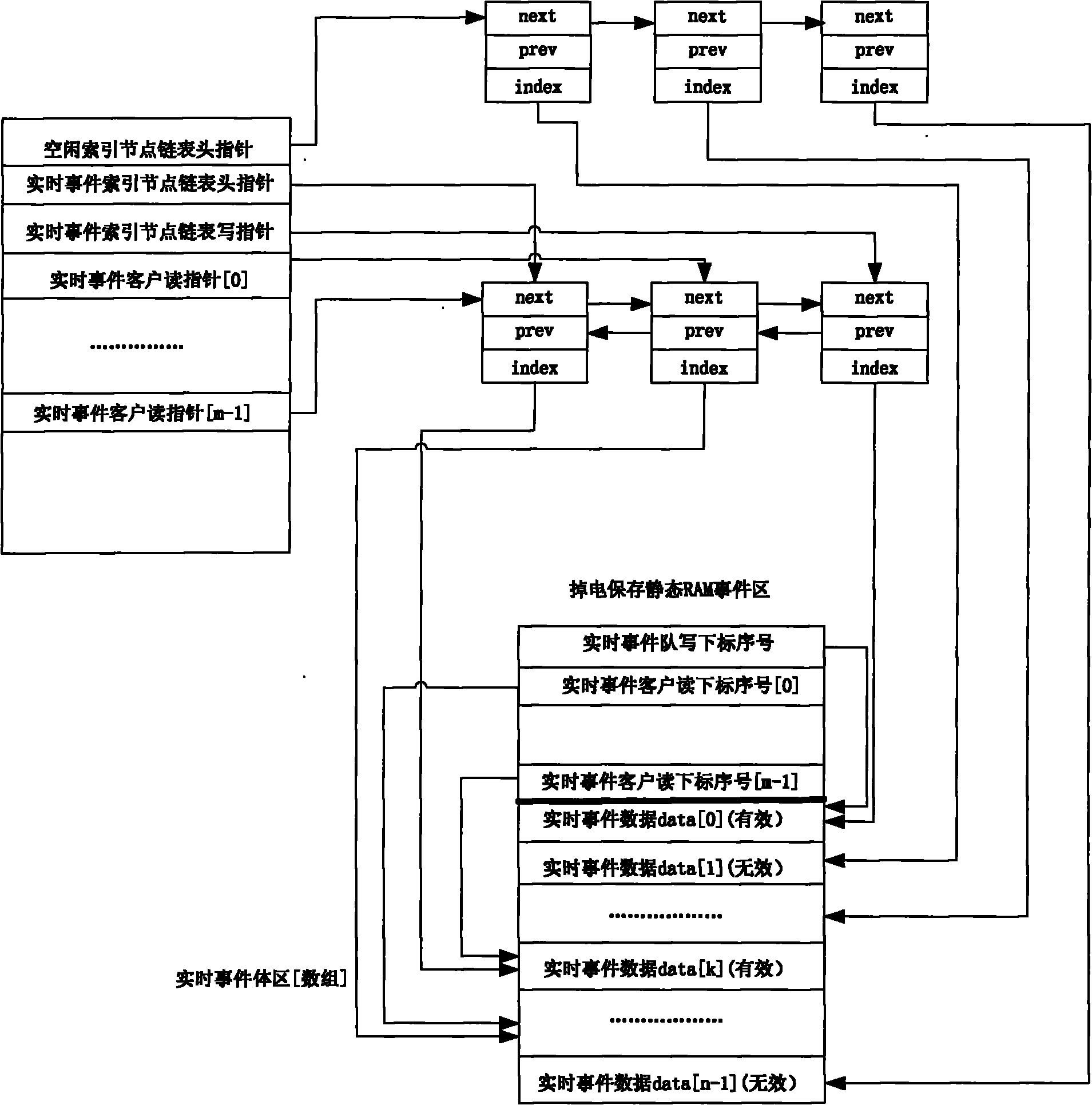
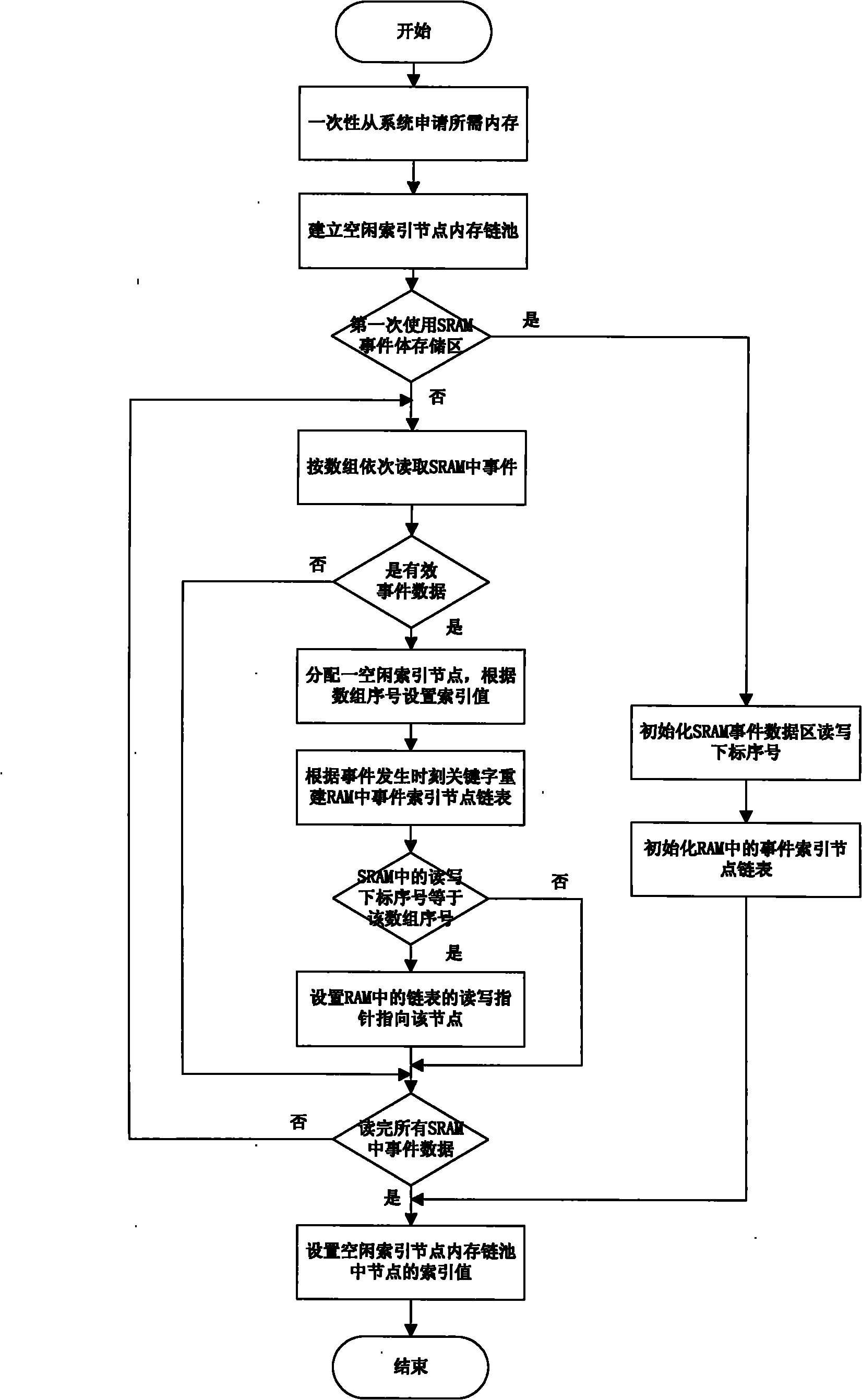
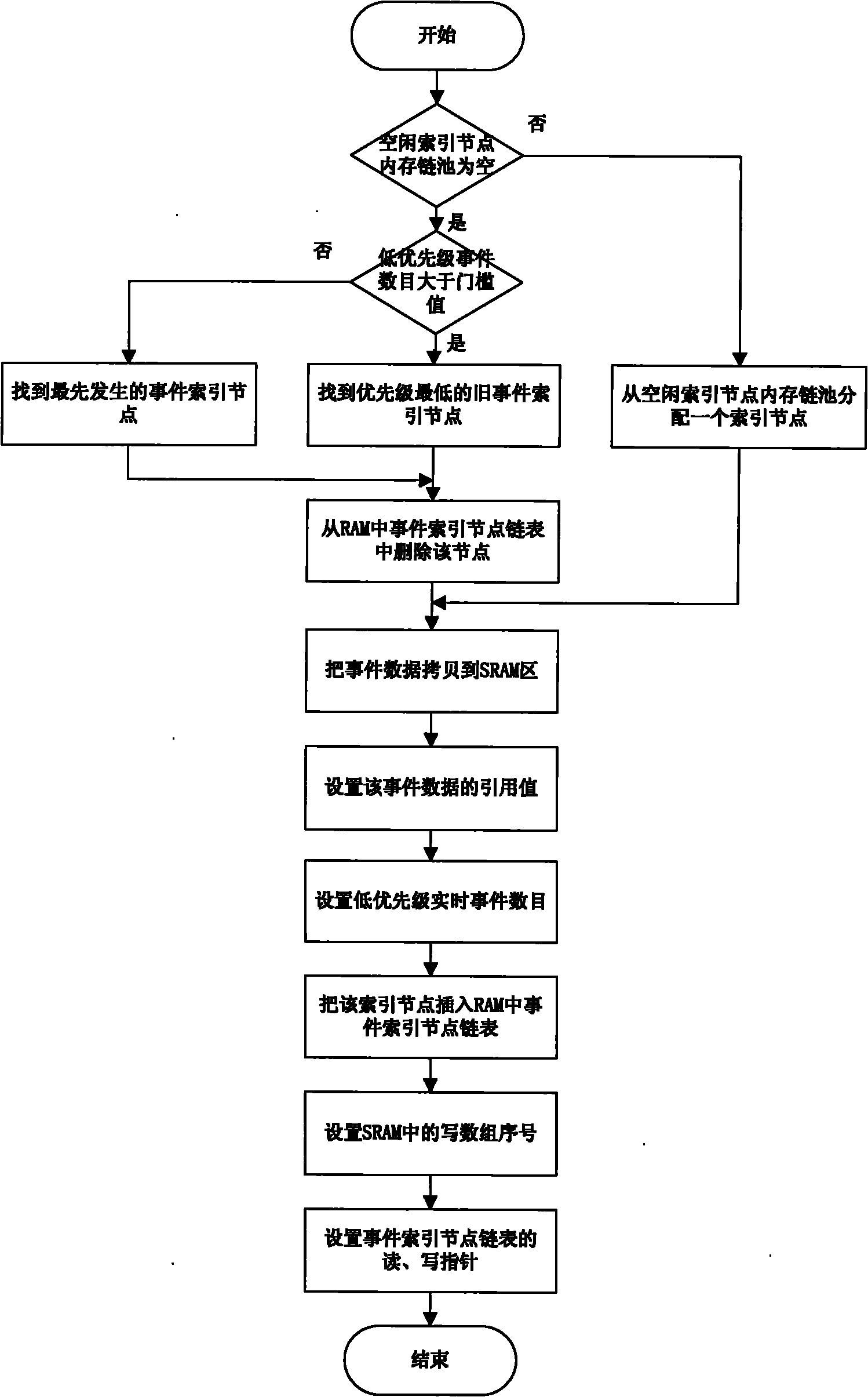
Real-time event management method for intelligent electronic equipment
ActiveCN101944119AAddress management deficienciesIncrease delaySpecial data processing applicationsOperational systemData entity
The invention relates to a real-time event management method for intelligent electronic equipment. The method comprises the following steps of: 1) separately storing and processing a data entity and a logical relationship of a real-time event; 2) managing an idle index node by using a chain pool mechanism; 3) adopting a doubly linked list structure with one write pointer and a plurality of read pointers; 4) processing the logical relationship among real-time events by using two keywords, namely event occurrence time and event priority; 5) fully and correctly reestablishing the whole doubly linked list in the process of initialization according to a generation time keyword stored in an SRAM event data entity; and 6) establishing a process list and event management routine interface for connecting an operation system. The method has the advantages of capacity of managing various real-time events in a converting station, adapting to various real-time operation systems, simplifying the complexity of managing the real-time events by multiple kinds of intelligent electronic equipment, particularly analyzing, calculating and processing the real-time events.
Owner:STATE GRID ELECTRIC POWER RES INST
Method for forwarding Linux kernel protocol stack network bridge data
ActiveCN102780627AGuaranteed stabilityGuaranteed scalabilityNetworks interconnectionStore and forwardLinux kernel
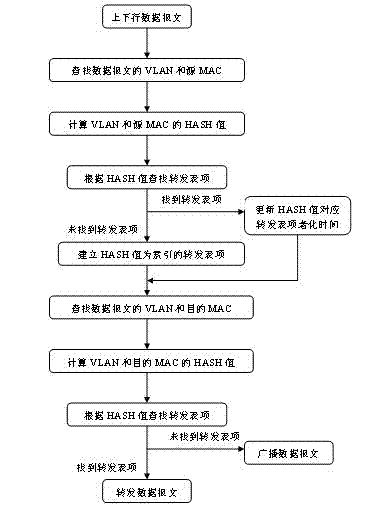
The invention provides a method for forwarding Linux kernel protocol stack network bridge data, when an LINUX kernel protocol stack is established, a double lined list which stores a forwarding table is initialized, when the data message enters a kernel protocol stack network bridge, an HASH value is computed through a virtual local area network (VLAN) and a multi-access computer (MAC), and is taken as an index to establish the forwarding table to be inserted into the double lined list which stores the forwarding table, and for the MAC addresses from one source, the forwarding tables which correspond to a plurality of different output equipment can be learnt. The method has the beneficial effects that the whole process is simple to realize and easy to carry out, ensures the stability and the expansibility of an LINUX kernel, and is very suitable for the requirement on network bridge data forwarding of embedded devices which are based on an LINUX system.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Method and apparatus for traversing a multiplexed data packet stream
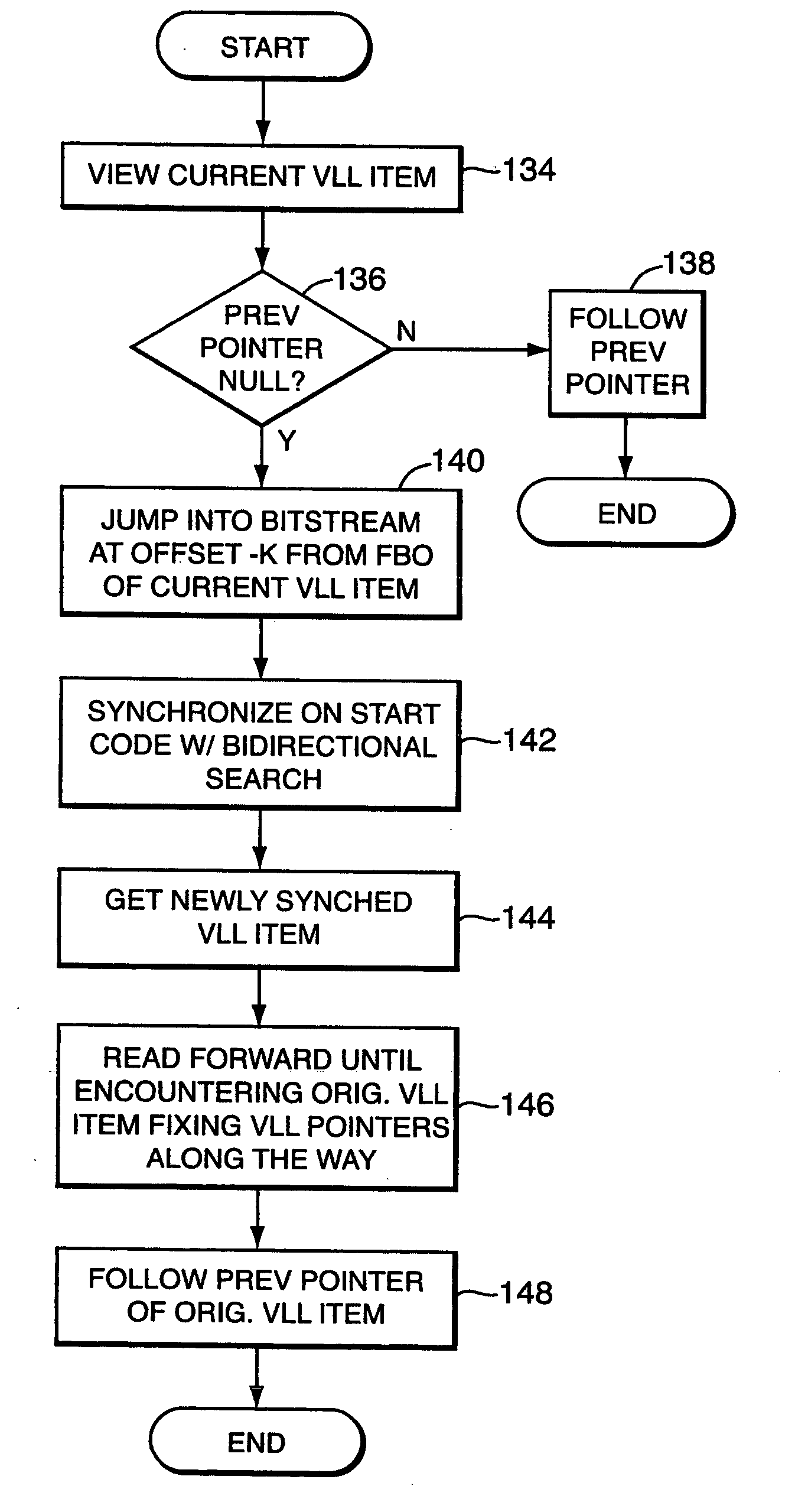
InactiveUS20050019009A1Simple working processTelevision system detailsRecording carrier detailsMultiplexingBidirectional search
A method for traversing a multiplexed data packet stream including choosing a starting location in a multiplexed data packet stream, making a bi-directional search from the starting location to locate a nearest system stream object; and traversing the system stream as a doubly-linked list of objects. Traversing the system stream preferably includes traversing object links of the doubly-linked list of objects. The objects are further preferably cached with an LRU process. Multiple disjoint locations in the system stream can be accessed with a virtual linked list. The virtual linked list can be used to search forwardly, backwardly, or both forwardly and backwardly.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com