Method and system for detecting memory occupancy state of embedded system
An embedded system, memory occupation technology, applied in the direction of software testing/debugging, can solve the problems of system crash, large system resource requirements, small embedded system memory, etc., to achieve the effect of convenient detection and strong versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to describe the technical content, structural features, achieved goals and effects of the present invention in detail, the following will be described in detail in conjunction with the embodiments and accompanying drawings.
[0037] In information technology, computer memory usage often affects the performance of a system, especially when a memory leak seriously affects the system, which will not only lead to waste of space, lower system performance, but also cause complex memory exhaustion. Furthermore, a memory The leaked program may use up a lot of memory and cause errors in other programs, but the user does not know where the error comes from. In addition, a seemingly harmless memory leak may be a harbinger of another problem. Therefore, try to avoid memory leaks. Occurrence of leakage.
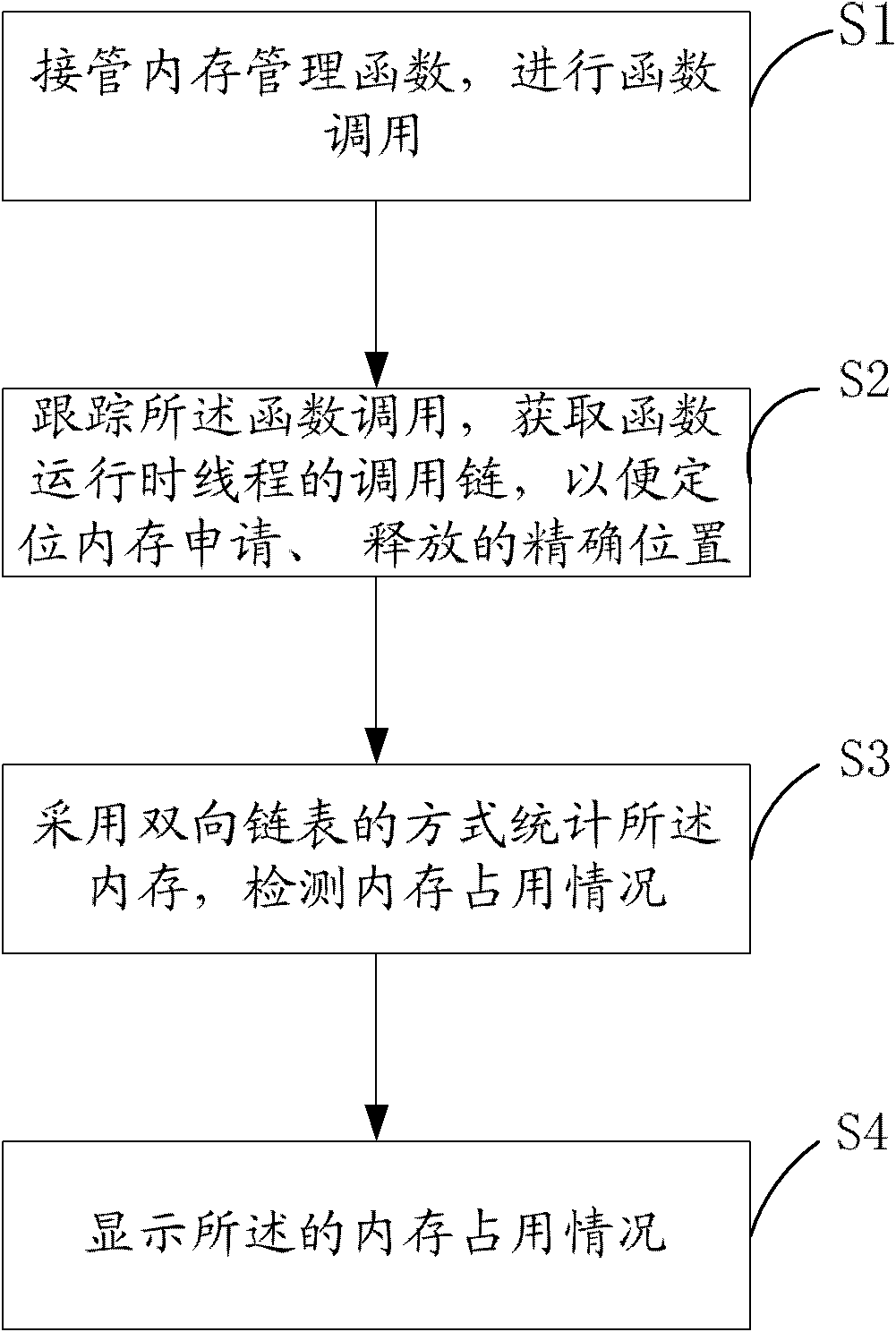
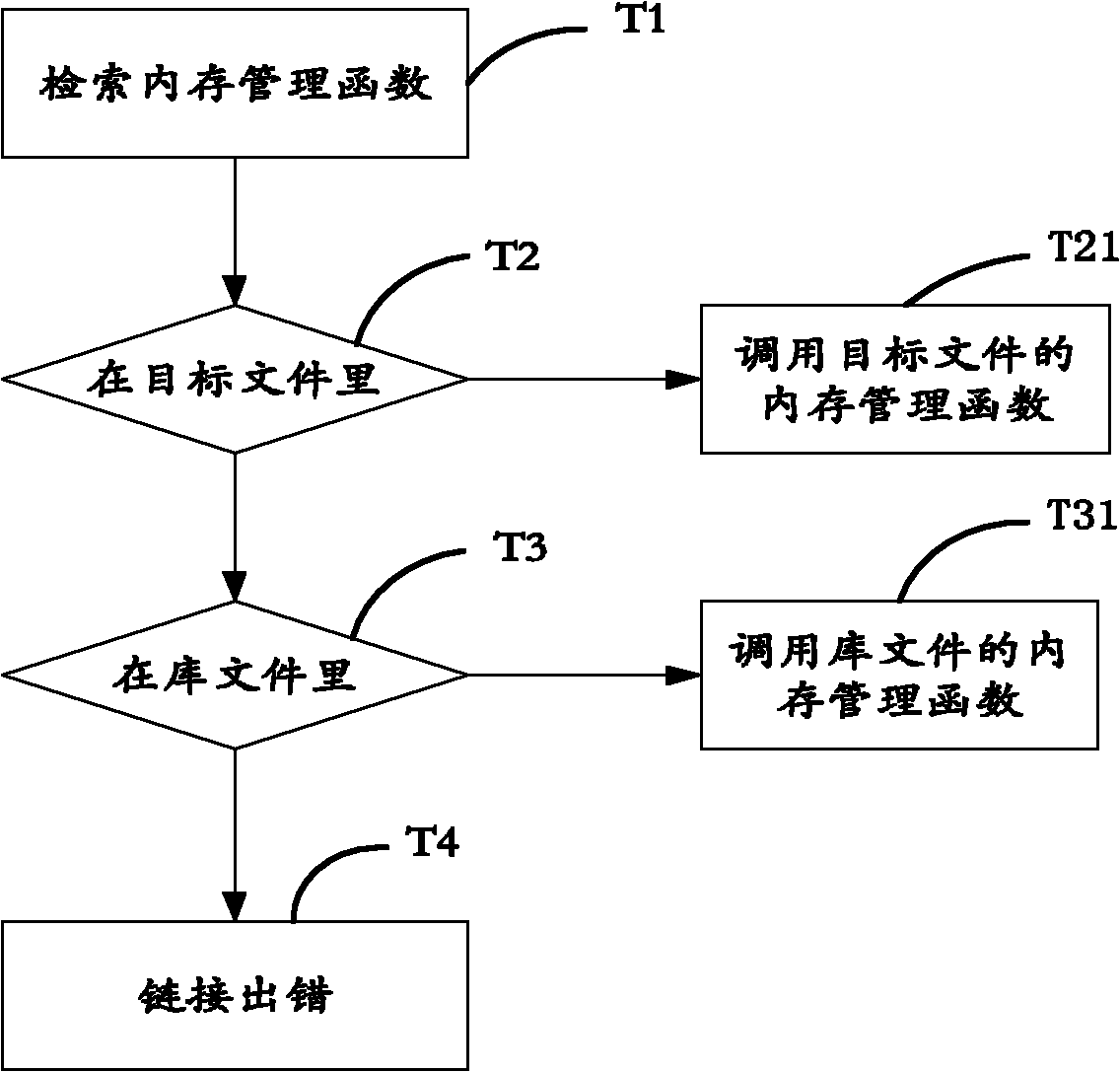
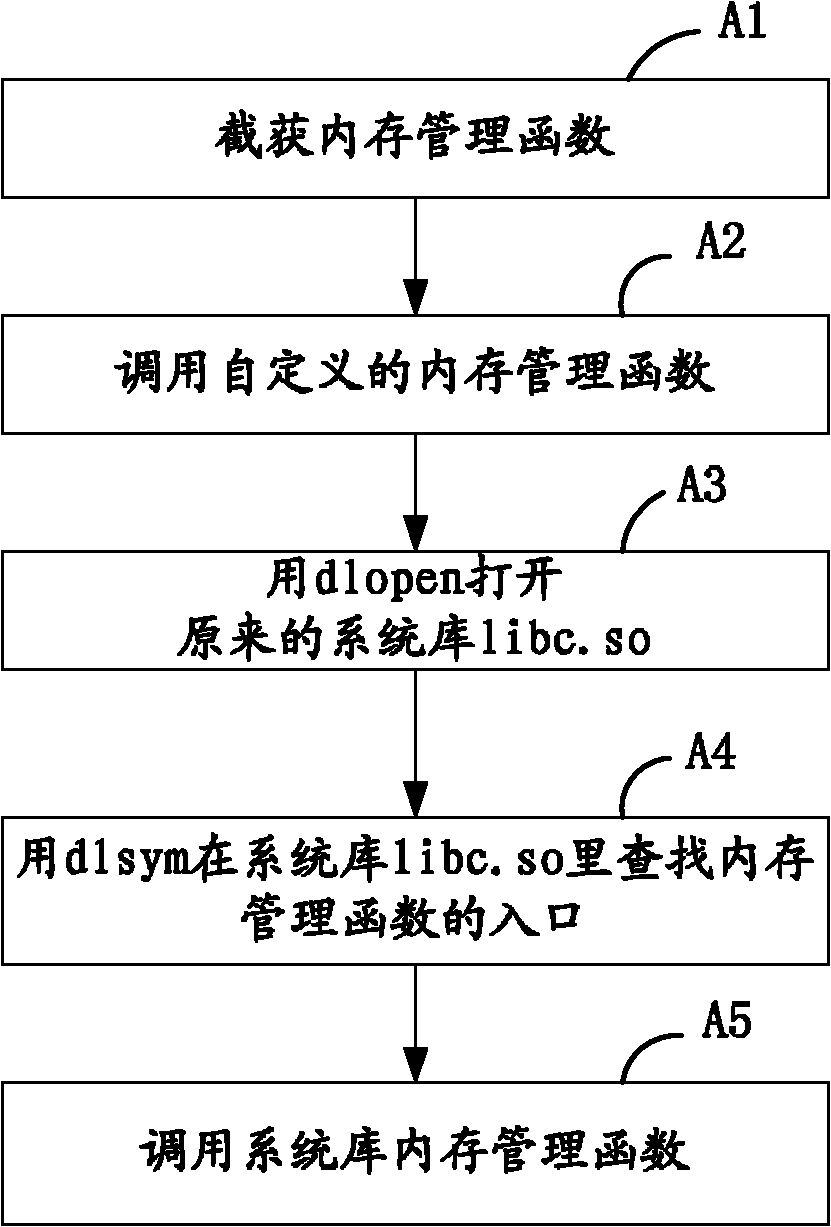
[0038] see figure 1 , in the first embodiment of the present invention, the embedded system memory occupation status detection method of the present invention comprises: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com