Sharing internal memory management method and apparatus
A shared memory and management method technology, applied in the field of shared memory management methods and devices, can solve problems such as memory leaks, troubleshooting difficulties, over-deletion or over-writing, and achieve the effect of eliminating residual memory blocks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
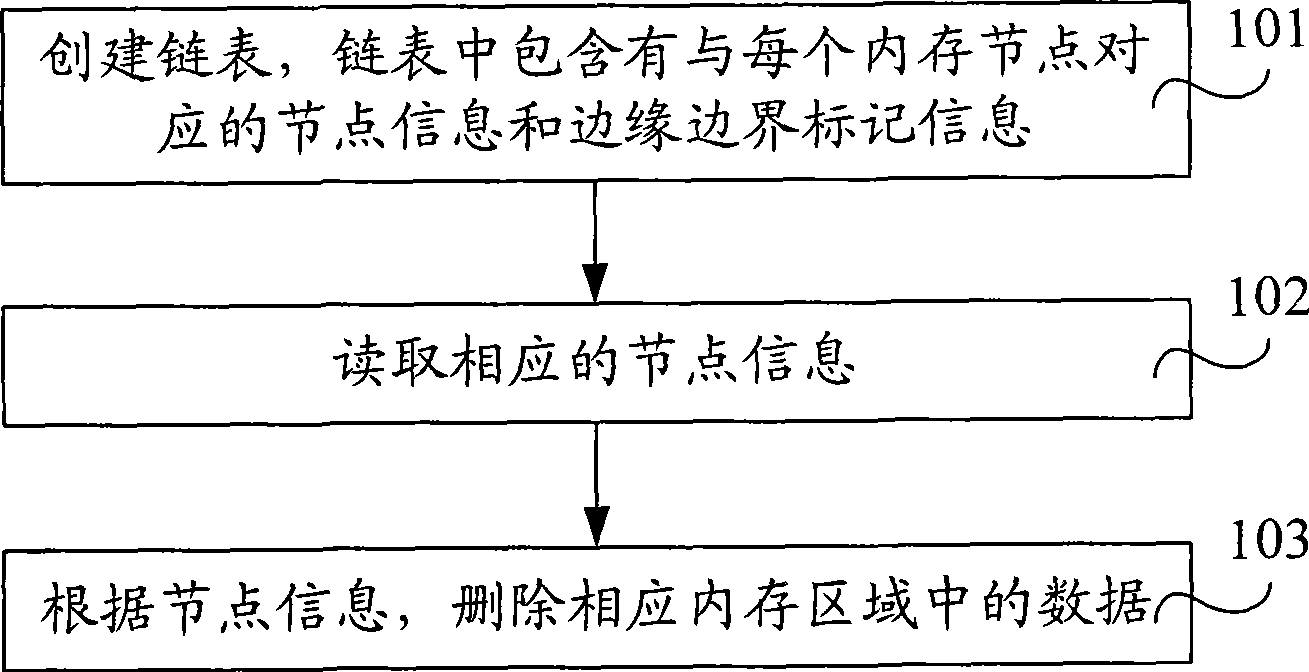
[0037] Such as figure 1 As shown, it is a flow chart of the first embodiment of the shared memory management method of the present invention, and the shared memory management method is specifically as follows:
[0038] Step 101, create a linked list, the linked list contains node information, data information and edge boundary marker information corresponding to each memory block, the node information is located in the node area, the data information is located in the data area, the edge boundary The tag information is located in the tag area, and the node information includes at least the size of the data area, a status tag for indicating whether there is data information in the data area, an address of a forward memory block, and an address of a backward memory block;
[0039] Step 102, reading corresponding node information;
[0040] Step 103, delete the corresponding memory block according to the node information.
[0041] In the first embodiment of the shared memory man...
no. 4 example
[0089] Such as Figure 8 As shown, it is a flow chart of the fourth embodiment of the shared memory management method of the present invention, and the shared memory management method is specifically as follows:
[0090] Step 801, start the main process.
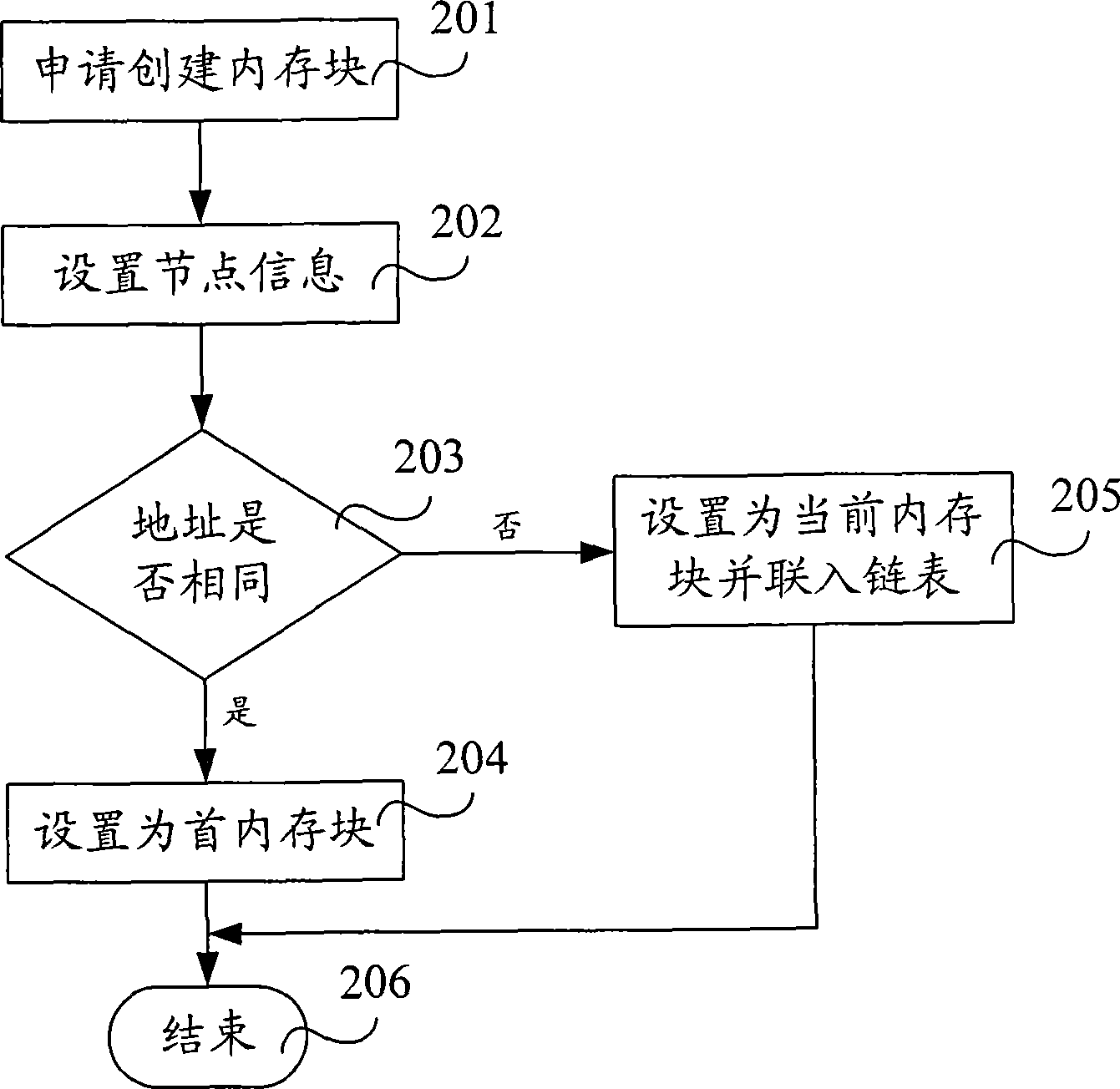
[0091] Step 802 , judging whether the instruction value of creating a sub-process corresponding to the main process is to generate a sub-process; if it is necessary to generate a sub-process, perform step 803 . In the implementation process, if the value of the create child process command is set to "0", it is necessary to generate a child process, and when the value of the create child process command is set to "1", it is set to not need to generate a child process, that is, to create a child process command When the value is "0", step 803 is executed.
[0092] Step 803, generate an empty stack, the sub-process corresponds to a memory doubly linked list, the memory doubly linked list contains node information, data inform...
no. 6 example
[0105] Such as Figure 10 As shown, it is a flowchart of the sixth embodiment of the shared memory management method of the present invention, and the shared memory management method specifically includes the following:
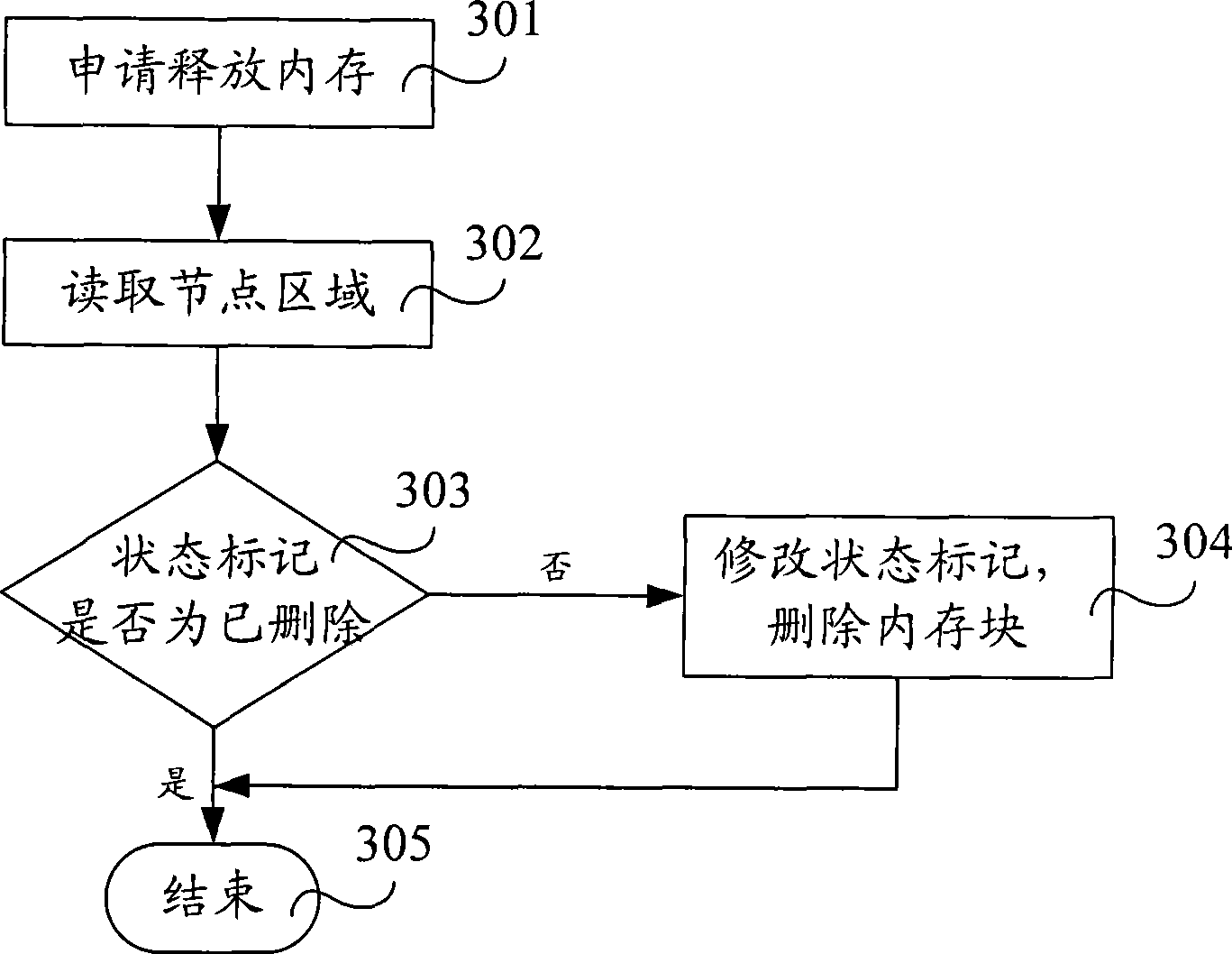
[0106] Step 1001, the execution of the main process is completed, and step 1002 is executed; the main process corresponds to at least one sub-process, and the memory doubly-linked list corresponding to the sub-process is located in a stack, and the memory doubly-linked list contains information related to each memory block Corresponding node information, data information and edge boundary label information, the node information is located in the node area, the data information is located in the data area, the edge boundary label information is located in the label area, and the node information includes at least the data area The size of the data area, the status flag used to indicate whether there is data information in the data area, the address of the forw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com