Patents
Literature
116 results about "Sequence ID" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Sequence Identifiers. Many sequences have two types of identification numbers, GI and VERSION.The two identifier types differ in format , and were implemented at different times. GI numbers. A GI number (for GenInfo Identifier, sometimes written in lower case, " gi") is a simple series of digits that are assigned consecutively to each sequence record processed by NCBI.
Method and apparatus for operating resources under control of a security module or other secure processor
InactiveUS6226749B1Improve operational flexibilityDigital data processing detailsDigital data protectionComputer hardwareSequence ID
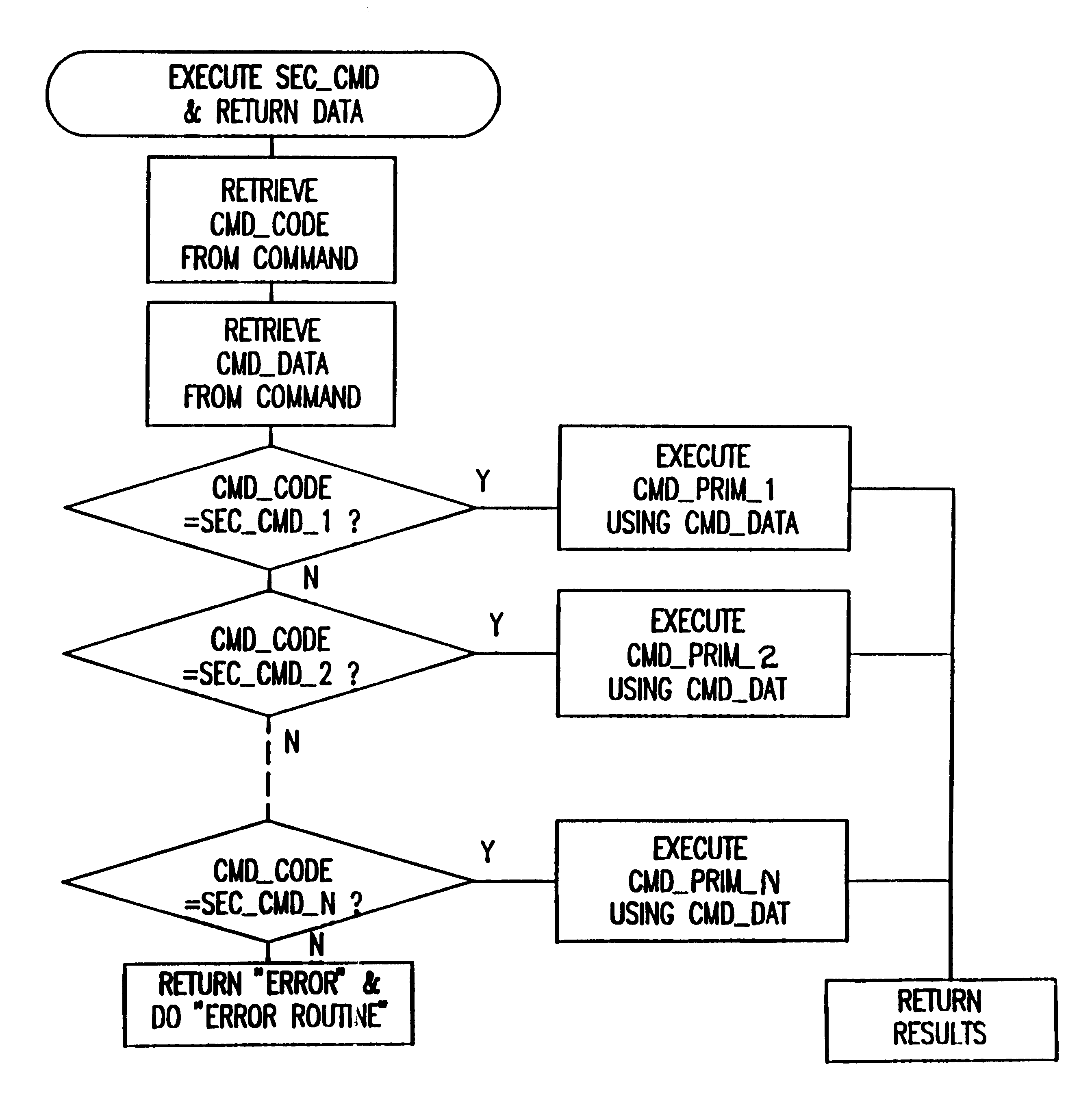
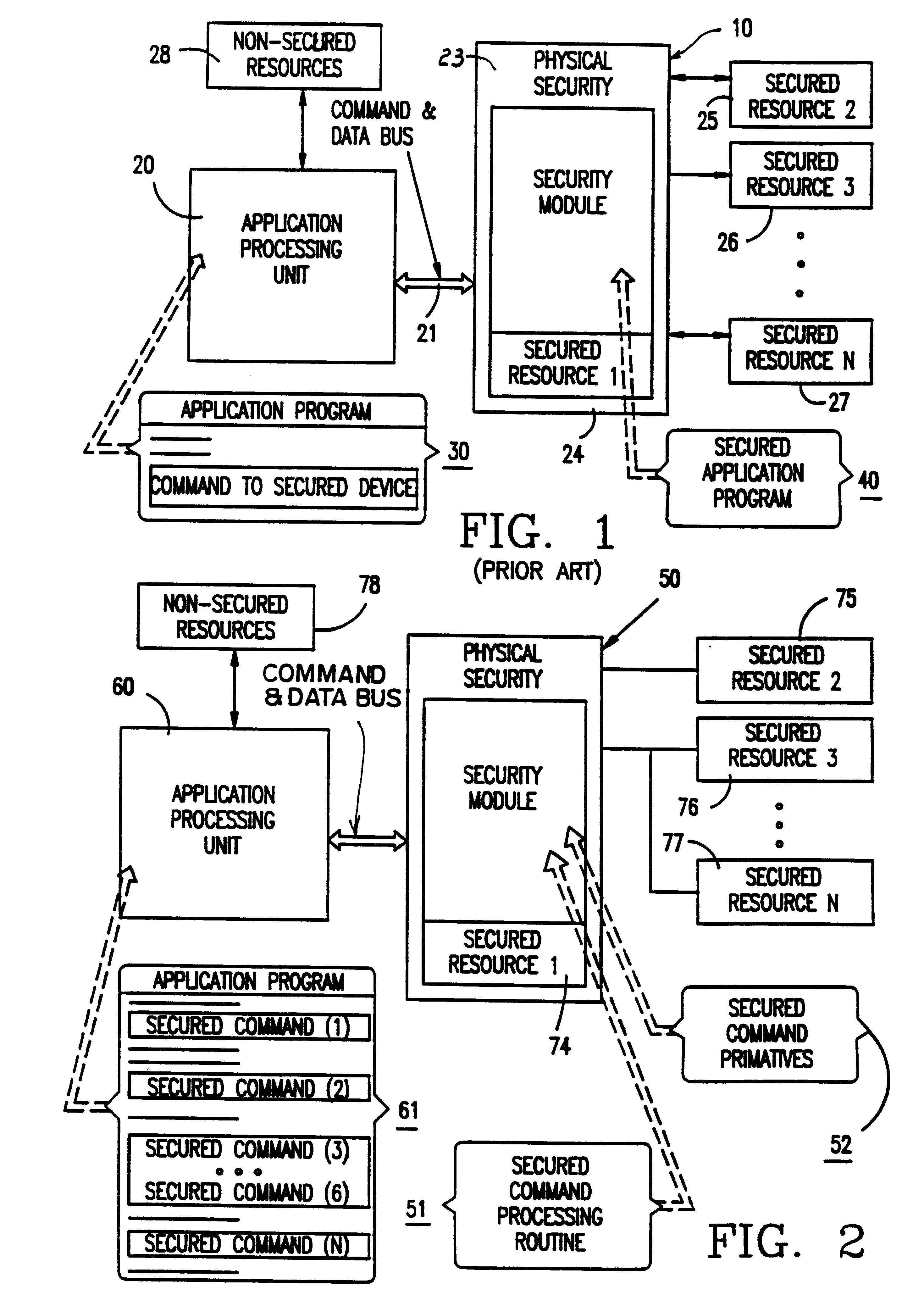
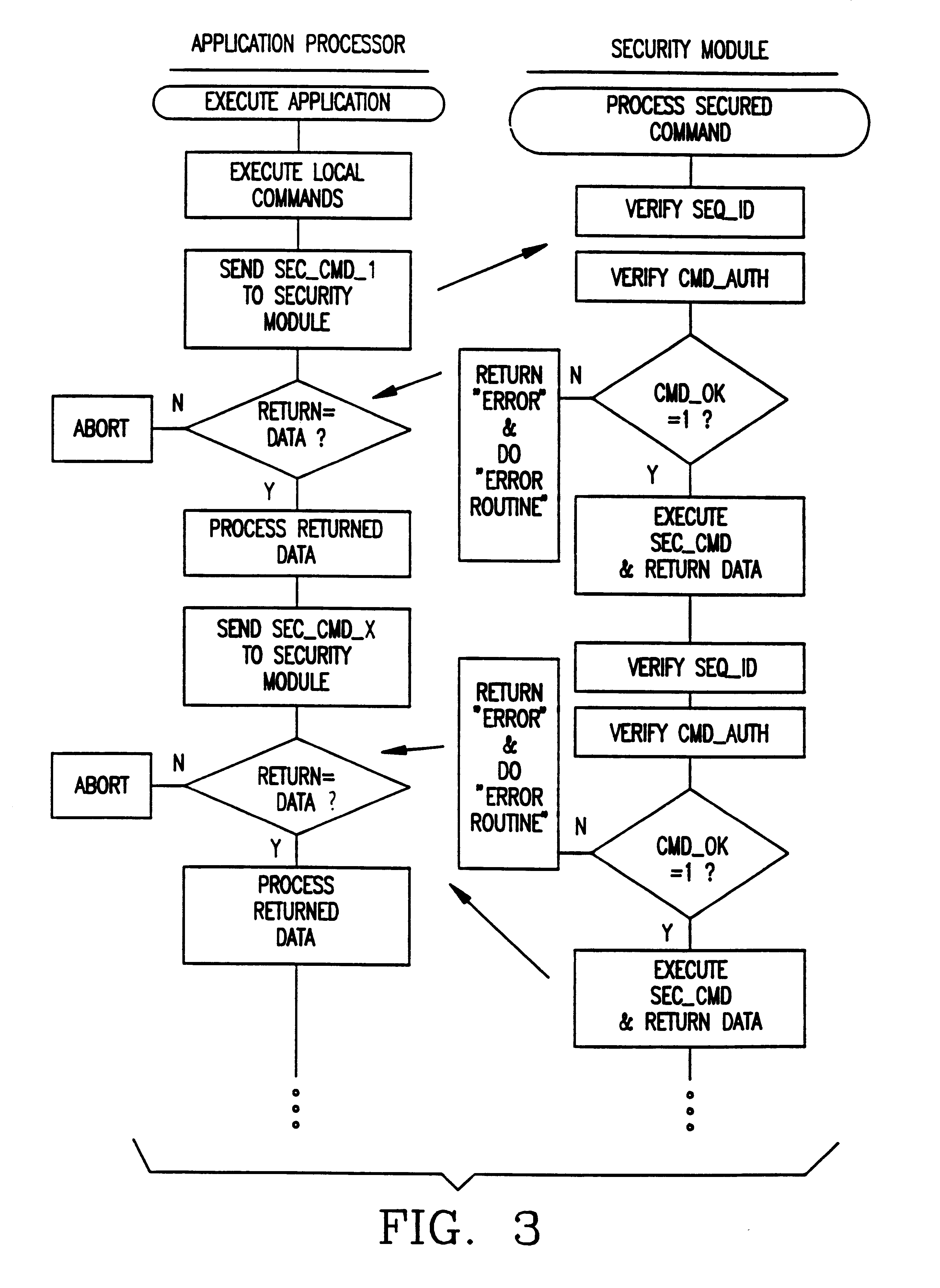
A method and apparatus for operating a set of resources under the control of a secure processor, e.g. security module, having a command authentication means and a command execution means, to achieve secure control of the resources. The secure processor stores a set of command primitives for functional control of the resources. A set of defined commands for invoking command primitives has either a secured command format including a command sequence ID, a command code, and a set of command data items or a non-secured command format including a command code and a set of command data items. The secure processor stores a command set up table including command type flags to designate each command as a secured command or a non-secured command. An application program running in an external device includes a plurality of the defined commands in either secured command format or the non-secured command format and these are sent one at a time to the secure processor for execution. The secure processor looks up each received command in the command set up table, and if the command is a non-secured command it immediately executes associated command primitives. If the command is a secured command, the secure processor tests both its authenticity and regularity and only executes the associated command primitives if the command passes both tests.
Owner:HEWLETT PACKARD DEV CO LP
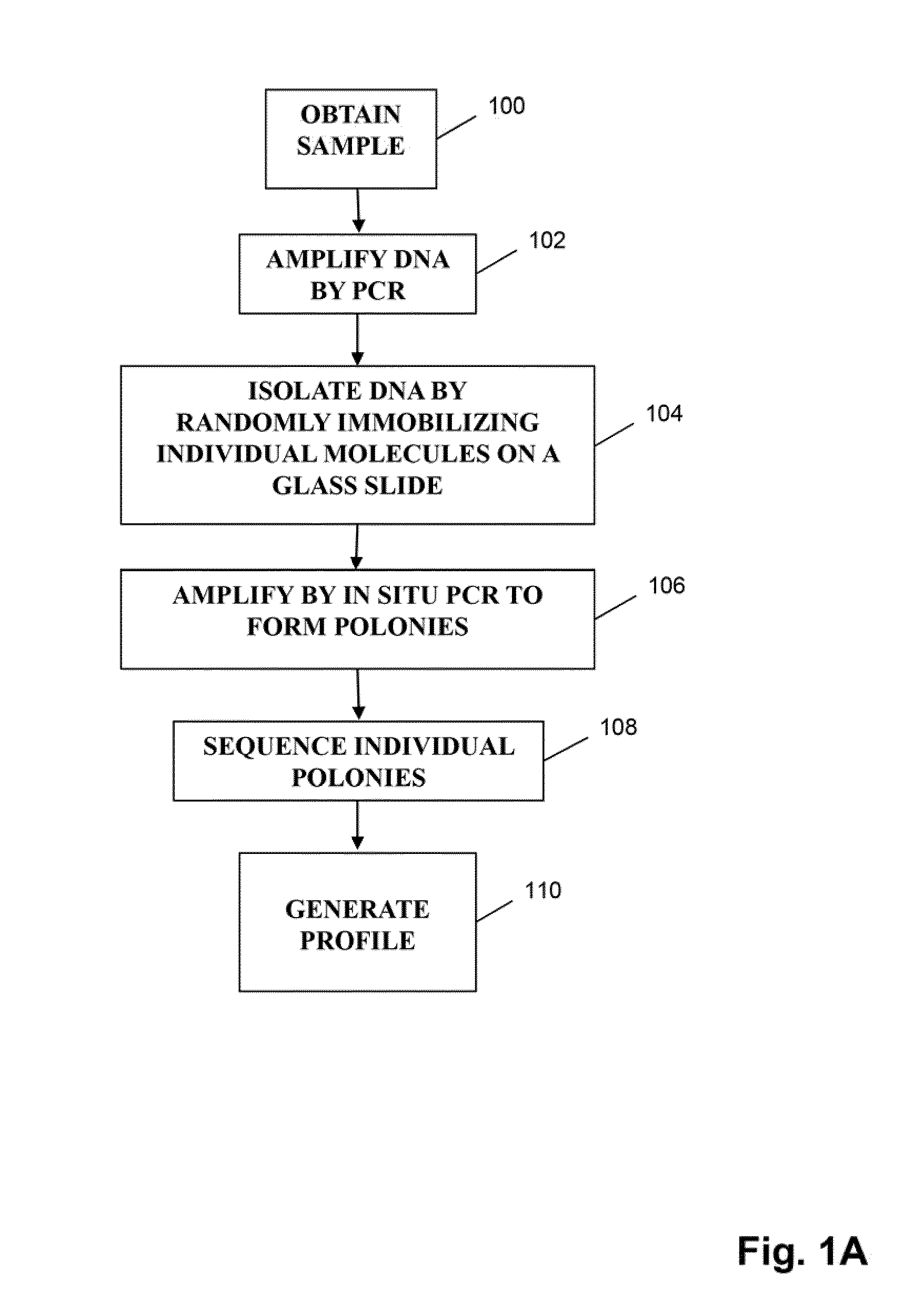
Sequence analysis of complex amplicons
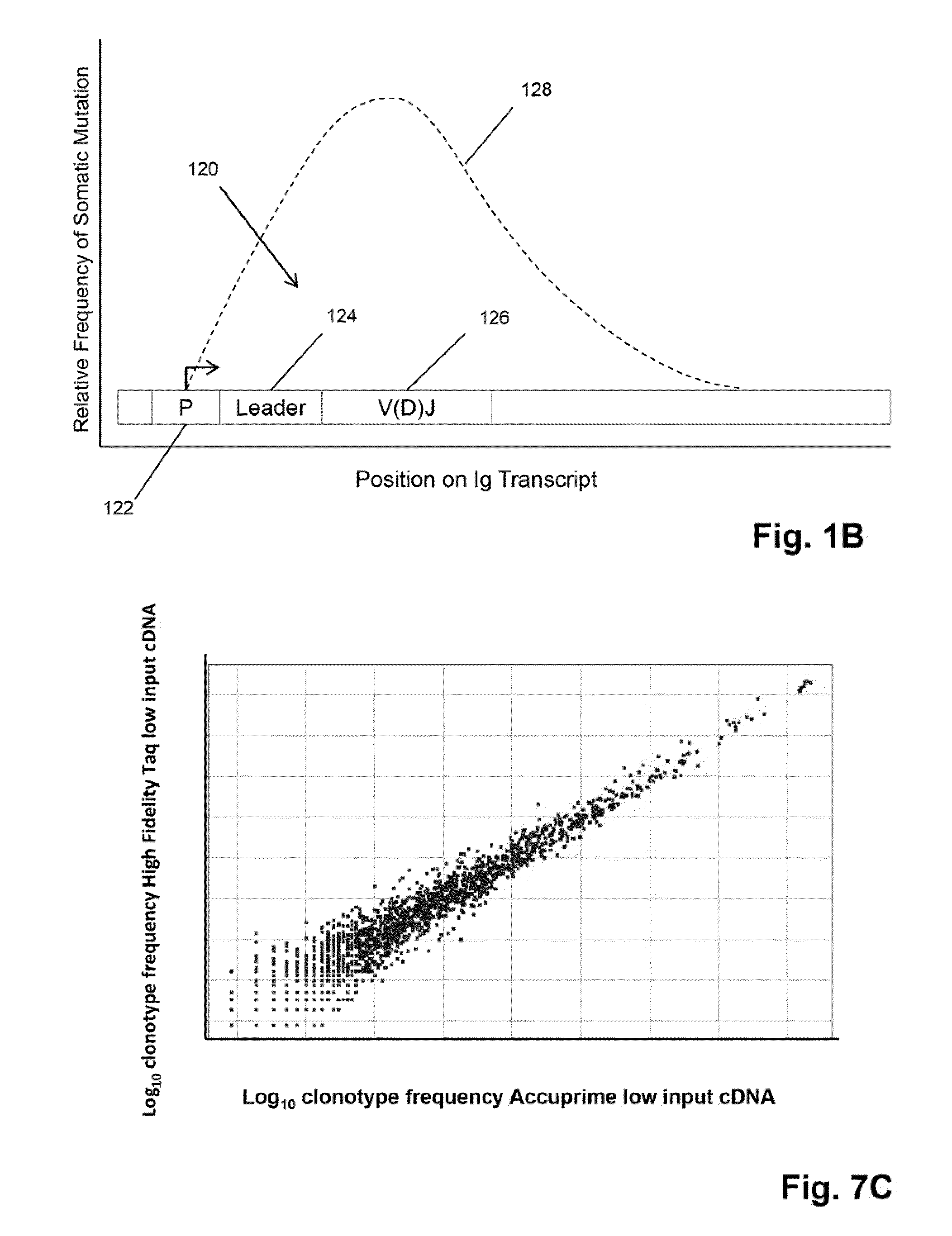
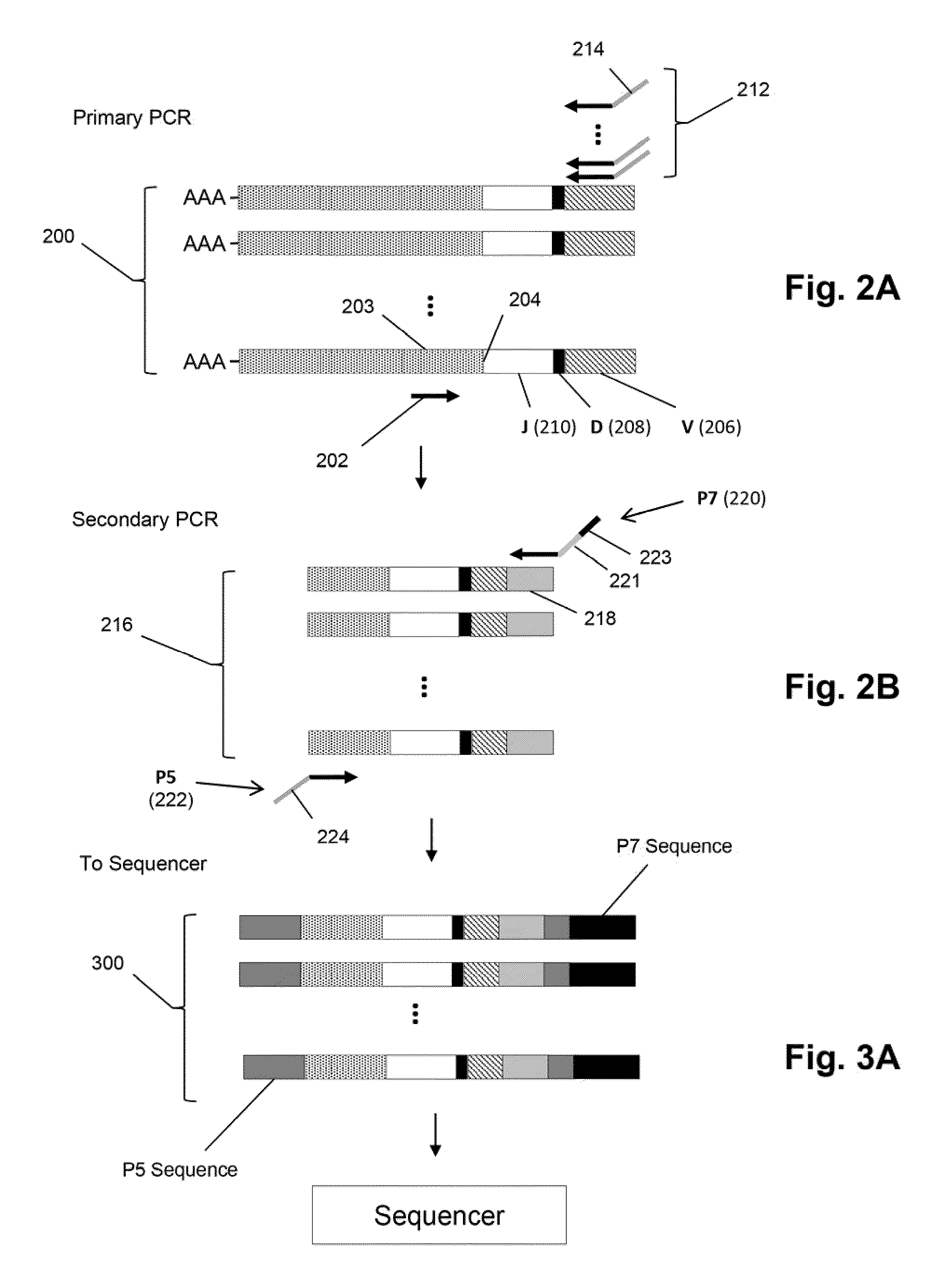
The invention is directed to methods of generating sequence profiles of populations of nucleic acids, whose member nucleic acids contain regions of high variability, such as populations of nucleic acids encoding T cell receptors or B cell receptors. In one aspect, the invention provides pluralities of sets of primers for generating nested sets of templates from nucleic acids in such populations, thereby insuring the production of at least one template from which sequence reads are generated, despite such variability, or dispite limited lengths or quality of sequence reads. In another aspect, members of such populations are bidirectionally sequenced so that further sequence information is obtained by analyzing overlapping sequence reads in the zones of highest variability.
Owner:ADAPTIVE BIOTECH
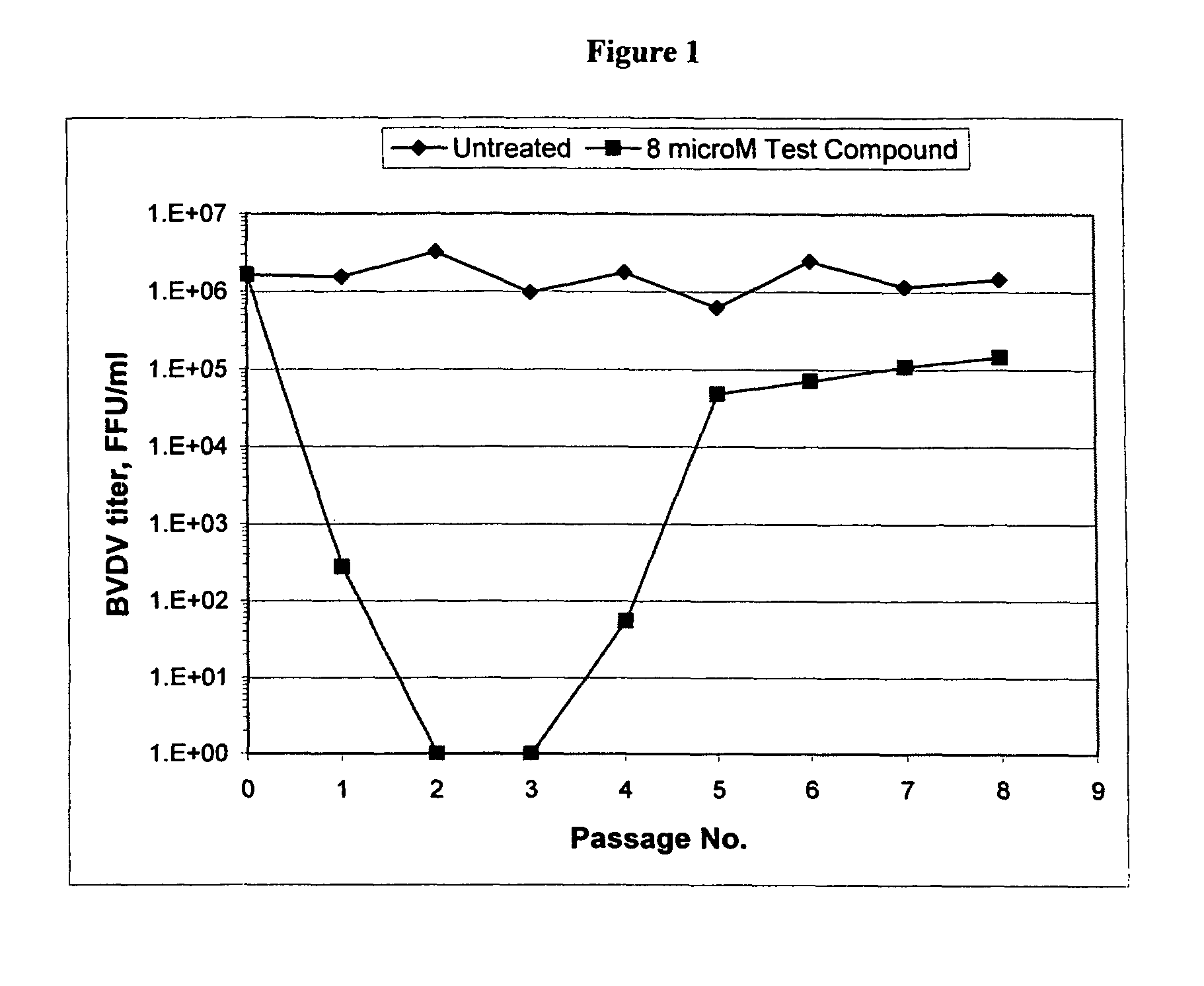
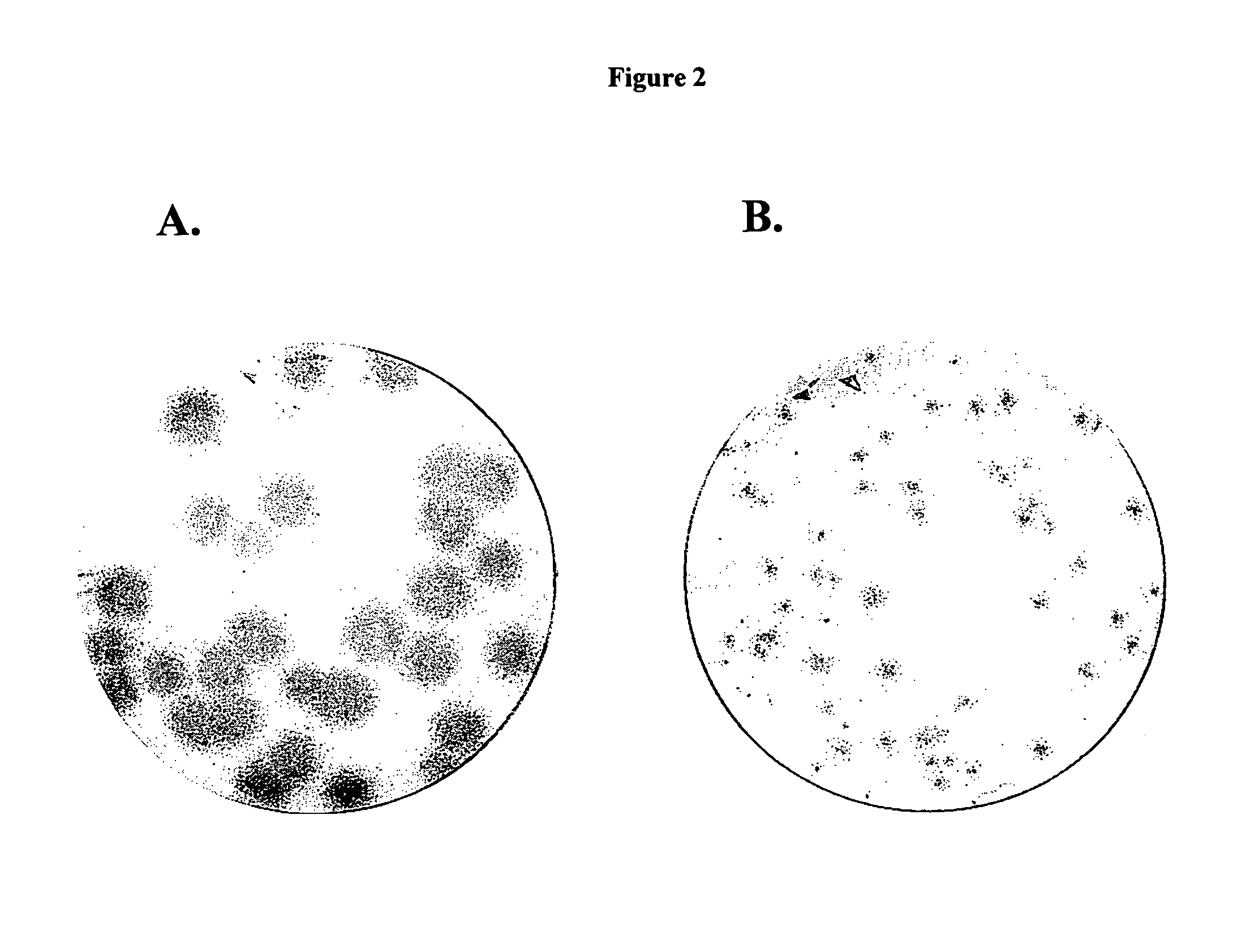
2′-branched nucleosides and Flaviviridae mutation
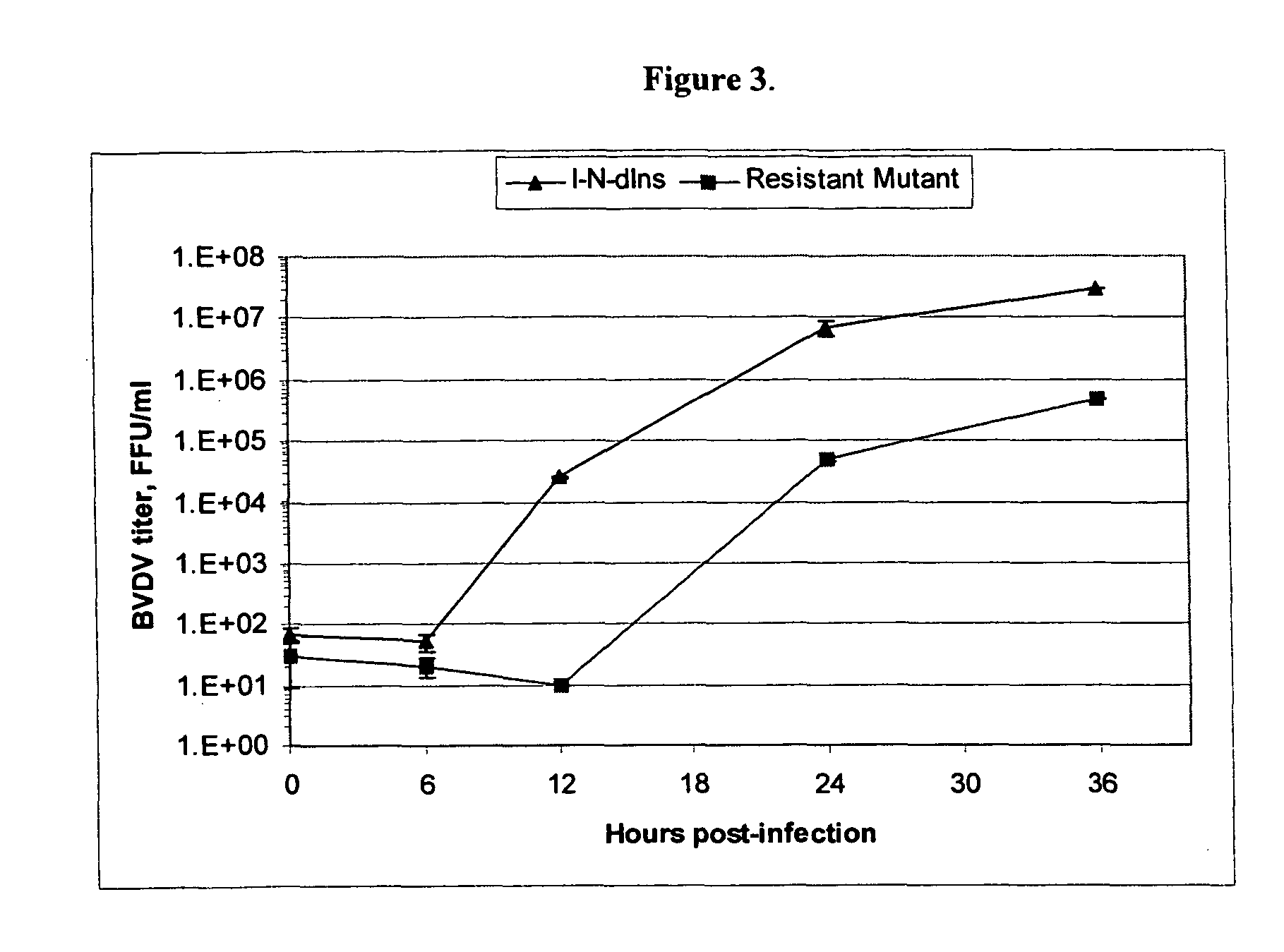
ActiveUS7824851B2High sensitivityReduce Flaviviridae infectionBiocideSsRNA viruses positive-senseAmino acidMutant strain
The present invention discloses a method for the treatment of Flaviviridae infection that includes the administration of a 2′-branched nucleoside, or a pharmaceutically acceptable prodrug and / or salt thereof, to a human in need of therapy in combination or alternation with a drug that directly or indirectly induces a mutation in the viral genome at a location other than a mutation of a nucleotide that results in a change from seine to a different amino acid in the highly conserved consensus sequence, XRXSGXXXT (Sequence ID No. 63), of domain B of the RNA polymerase region, or is associated with such a mutation. The invention also includes a method to detect a mutant strain of Flaviviridae and a method for its treatment.
Owner:INDENIX PHARM LLC
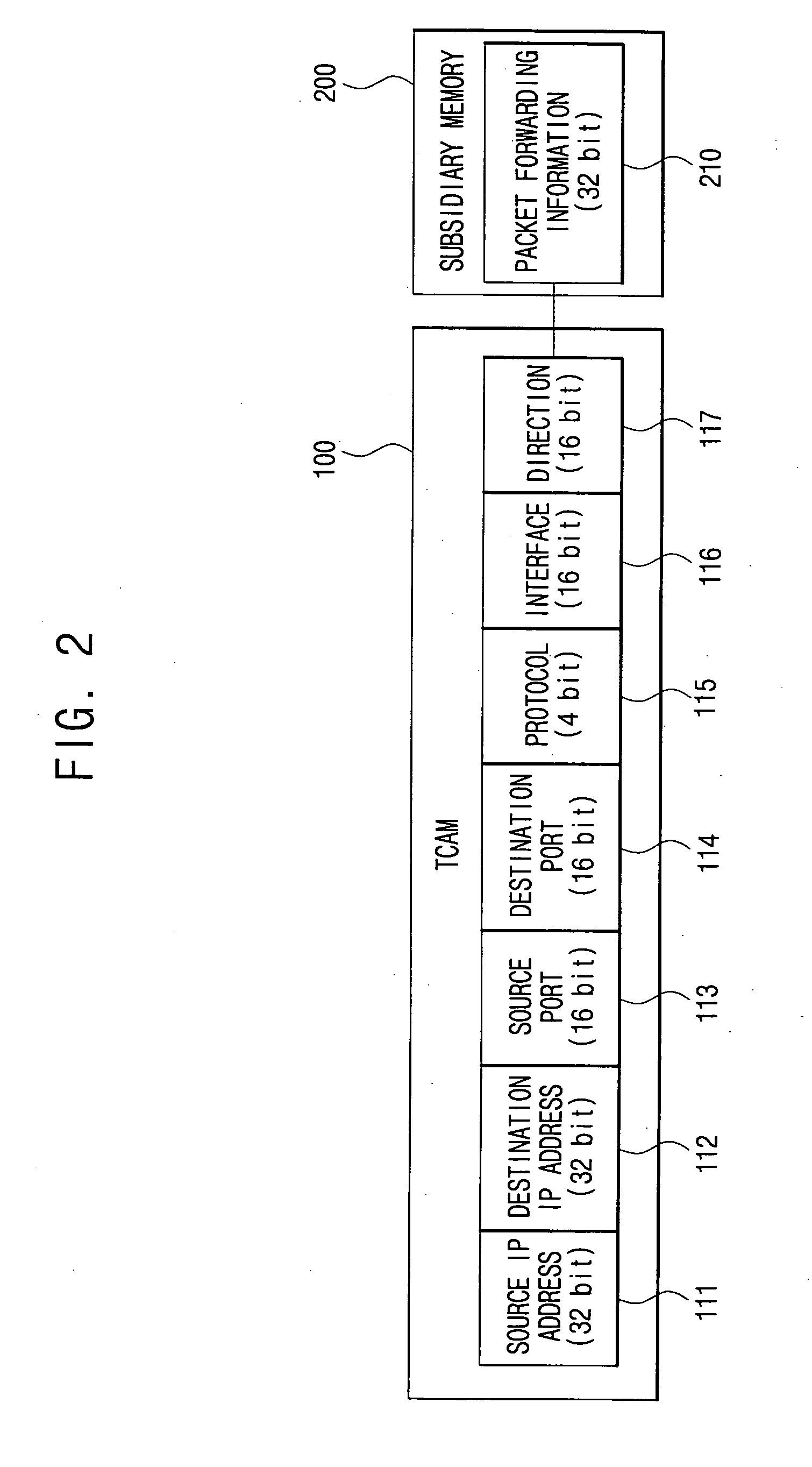
Routing system and method for managing rule entries of ternary content addressable memory in the same
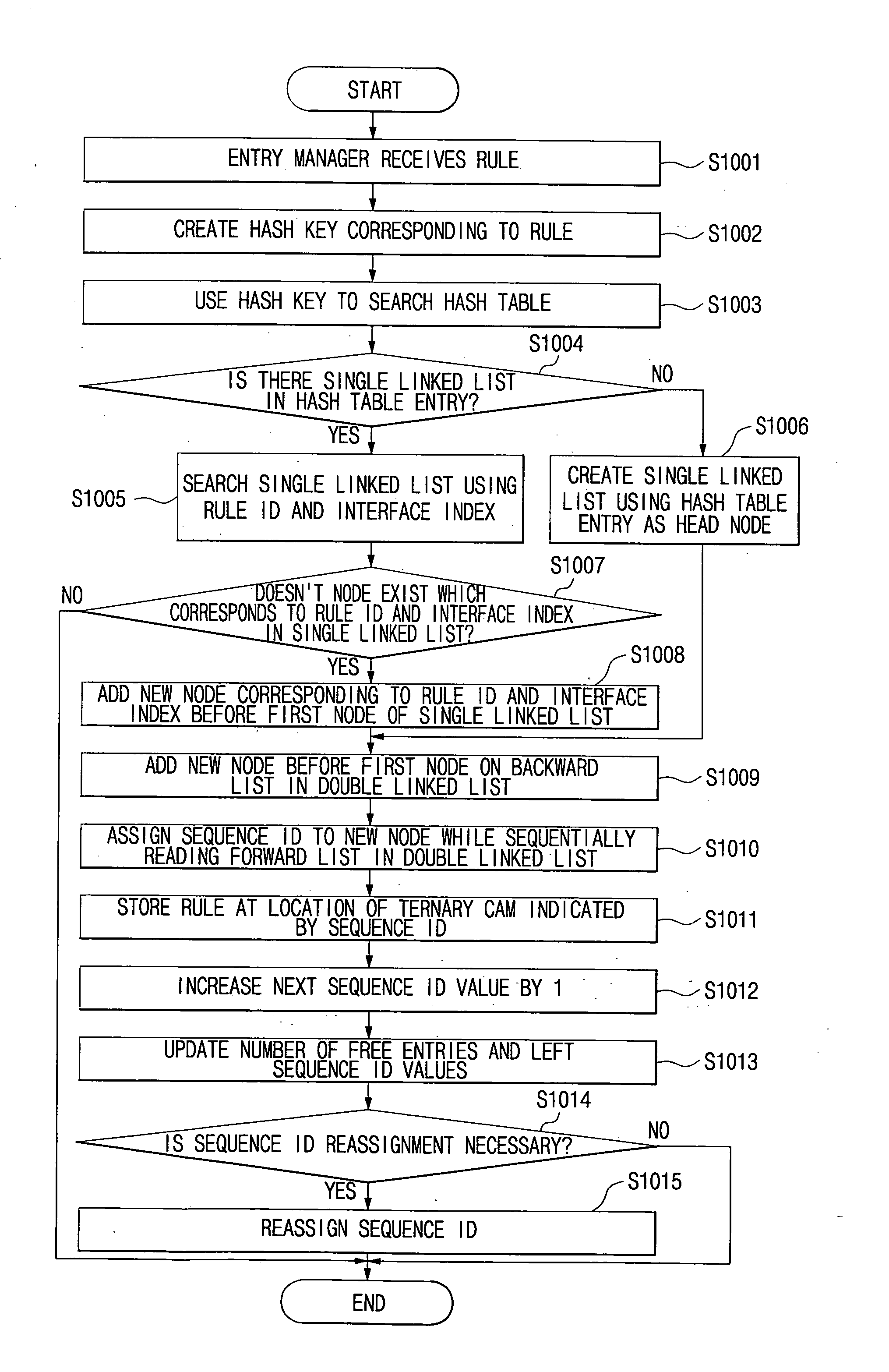
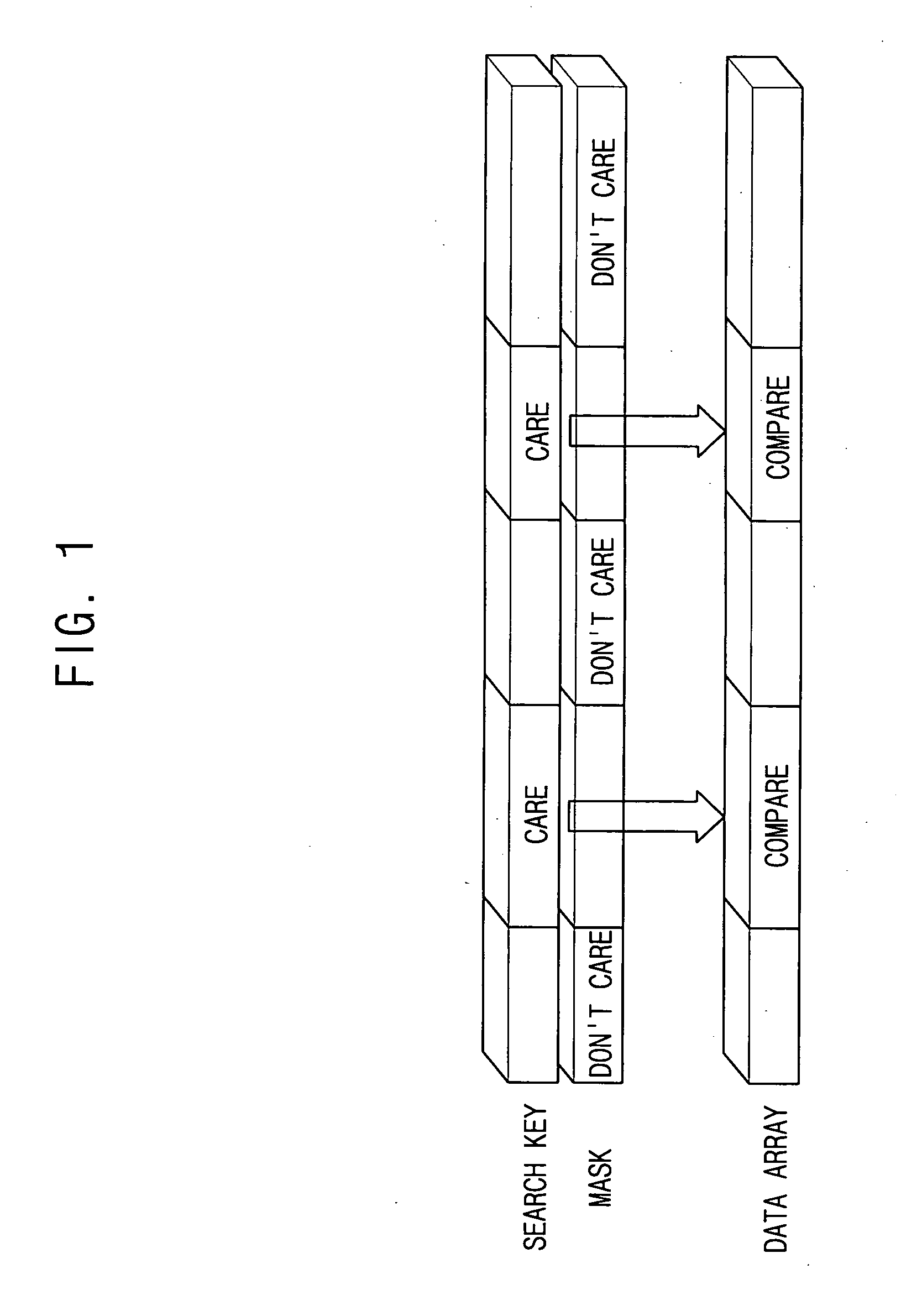
InactiveUS20080192754A1Easy to addEasy to deleteData switching by path configurationData packSequence ID
A method of managing rule entries of a Ternary Content Addressable Memory (TCAM) in a routing system includes: creating a hash table having a hash key corresponding to each entry; creating a single linked list for linking nodes, the single linked list using the entry of the hash table as a head node and including rule IDs and sequence IDs assigned according to a rule input order; and a double linked list having an independent head node, the double linked list bidirectionally linking the nodes constituting the single linked list according to an order of the sequence IDs. Thus, the packet classifying / filtering rule can be easily added to the TCAM or deleted from the TCAM only with minimal information. Also, the sequence ID reassignment process, required for storing as many rules in the TCAM as possible according to the priority of the rules, is performed when a certain time elapses following rule addition or deletion, thereby reducing a latency that may be caused upon setting the packet classifying / filtering rule.
Owner:SAMSUNG ELECTRONICS CO LTD
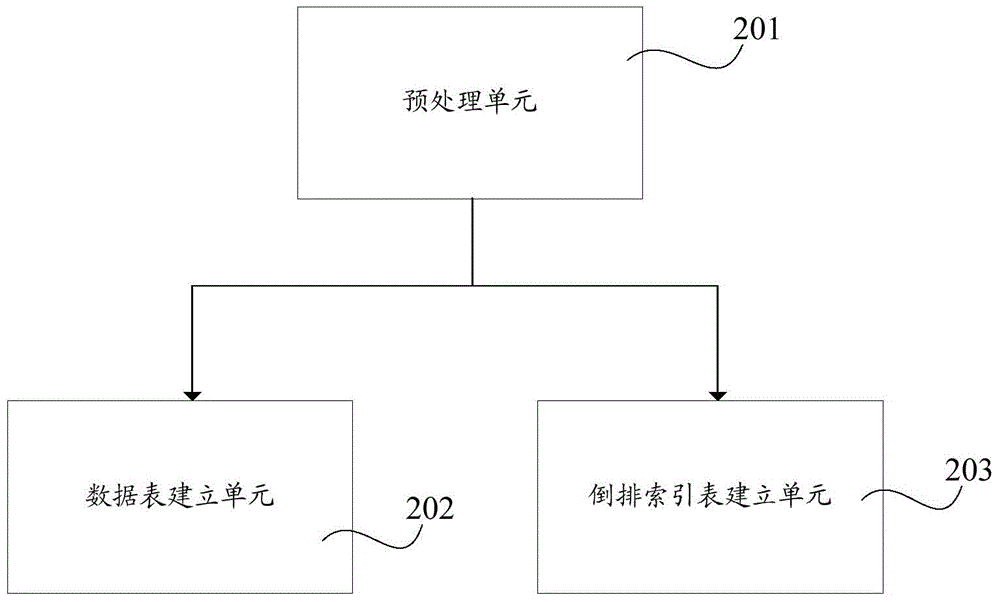
Method and device for establishing NoSQL database index for semi-structured data
ActiveCN104794123AImprove query efficiencyImprove update efficiencySemi-structured data indexingSpecial data processing applicationsSemi-structured dataSequence ID
Semi-structured source data is preprocessed to obtain text partitions to be stored into a data table with a first combined primary key including a structure thread primary key and a sequence value primary key. The structure thread primary key identifies a structure thread that is segmented into several consecutive intervals according to a determined or predetermined sequence. An inverted index table, created for the preprocessed text partitions, includes a second combined primary key including the structure thread primary key and a keyword primary key. Corresponding to values of the primary keys in the second combined primary key, related text partition sequence IDs are recorded as index values of the inverted index table. Index values having a same keyword primary key value but different structure thread primary key values are located in different rows in the inverted index table. The present techniques improve query efficiency of database index and facilitate updating.
Owner:ALIBABA GRP HLDG LTD
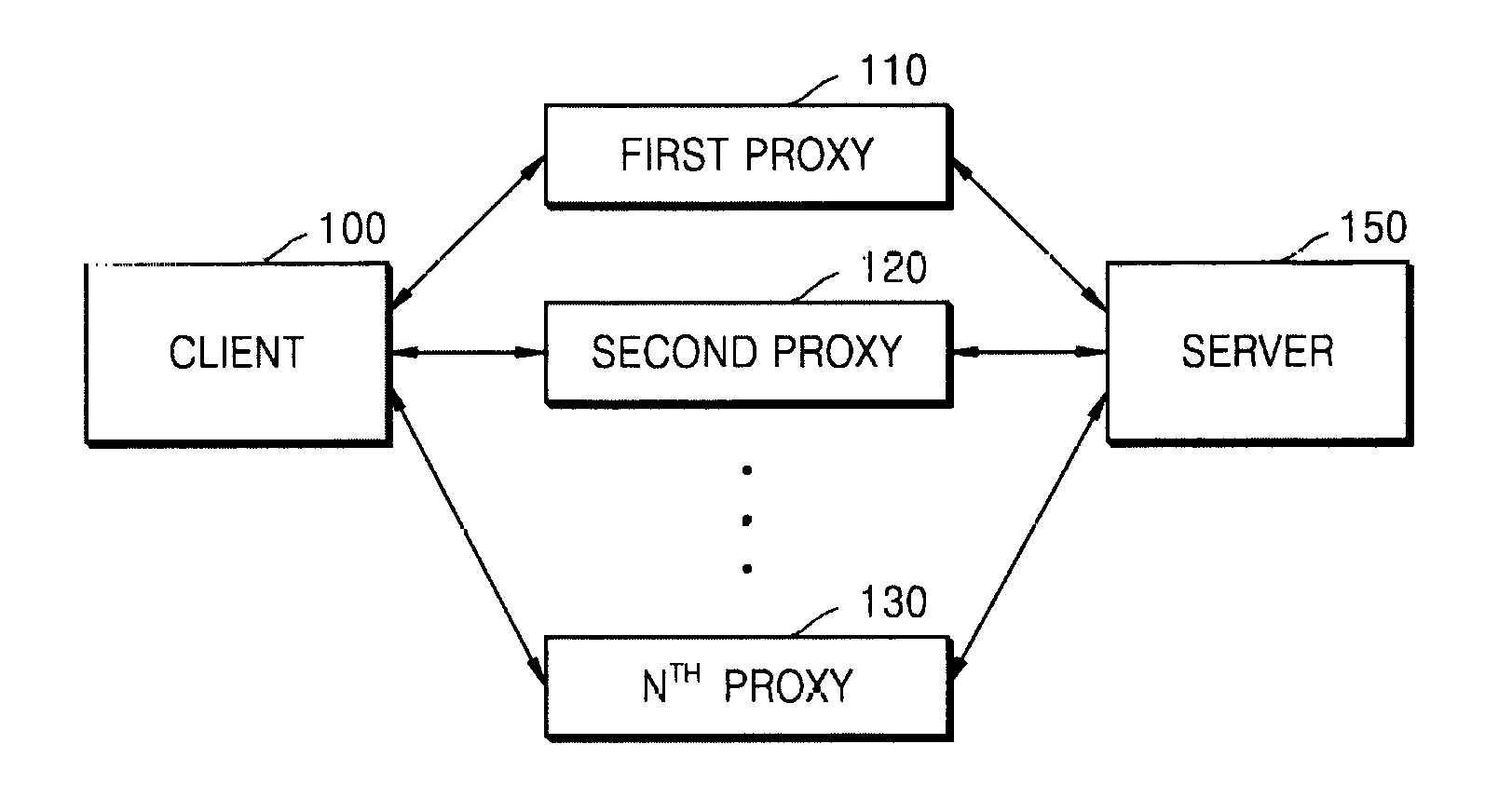
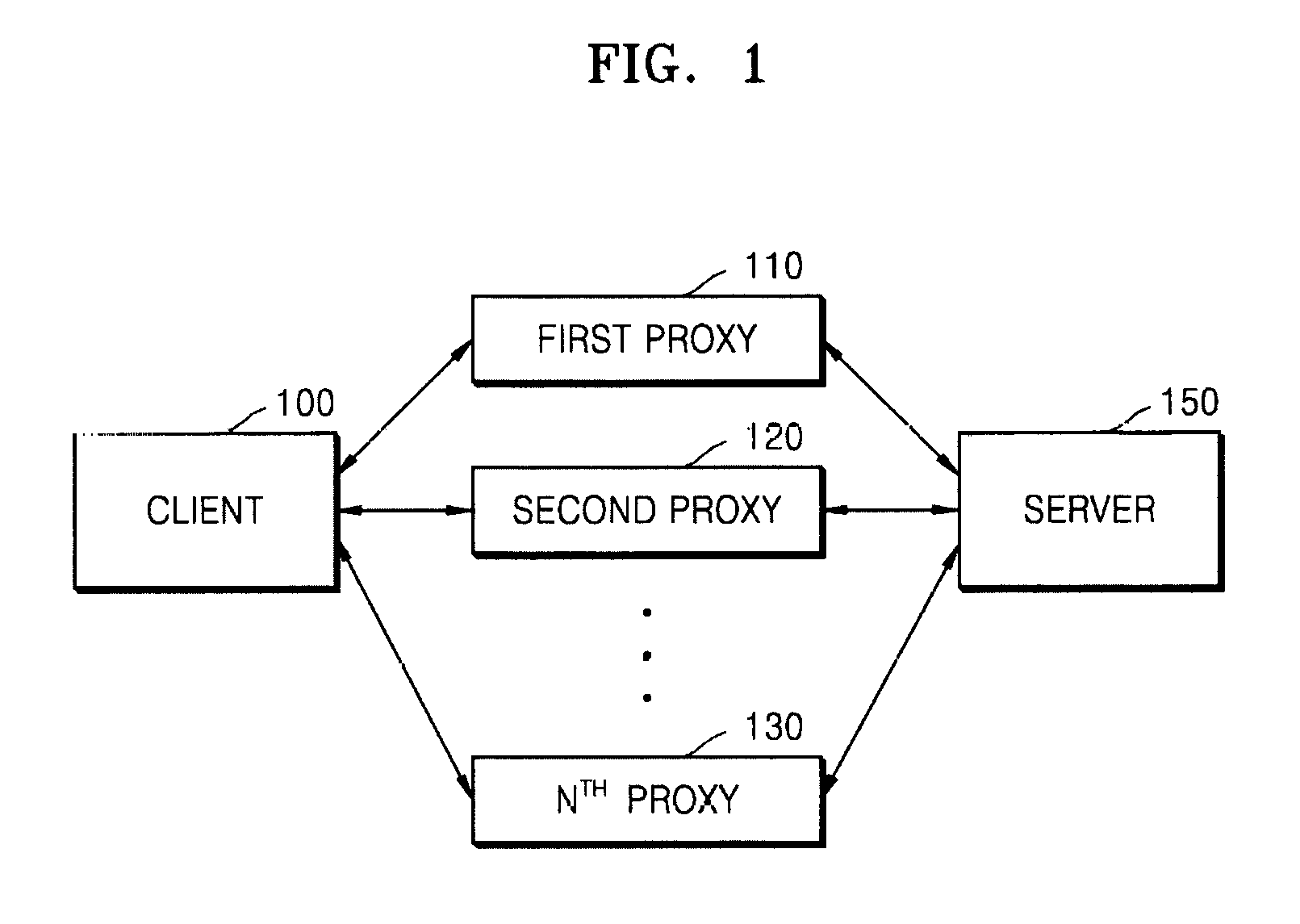
Multi-connection system and method for service using internet protocol
ActiveUS20160173452A1Strengthen the connection structureCommunicate seamlesslyData switching by path configurationMultiple digital computer combinationsInternet protocol suiteSequence ID
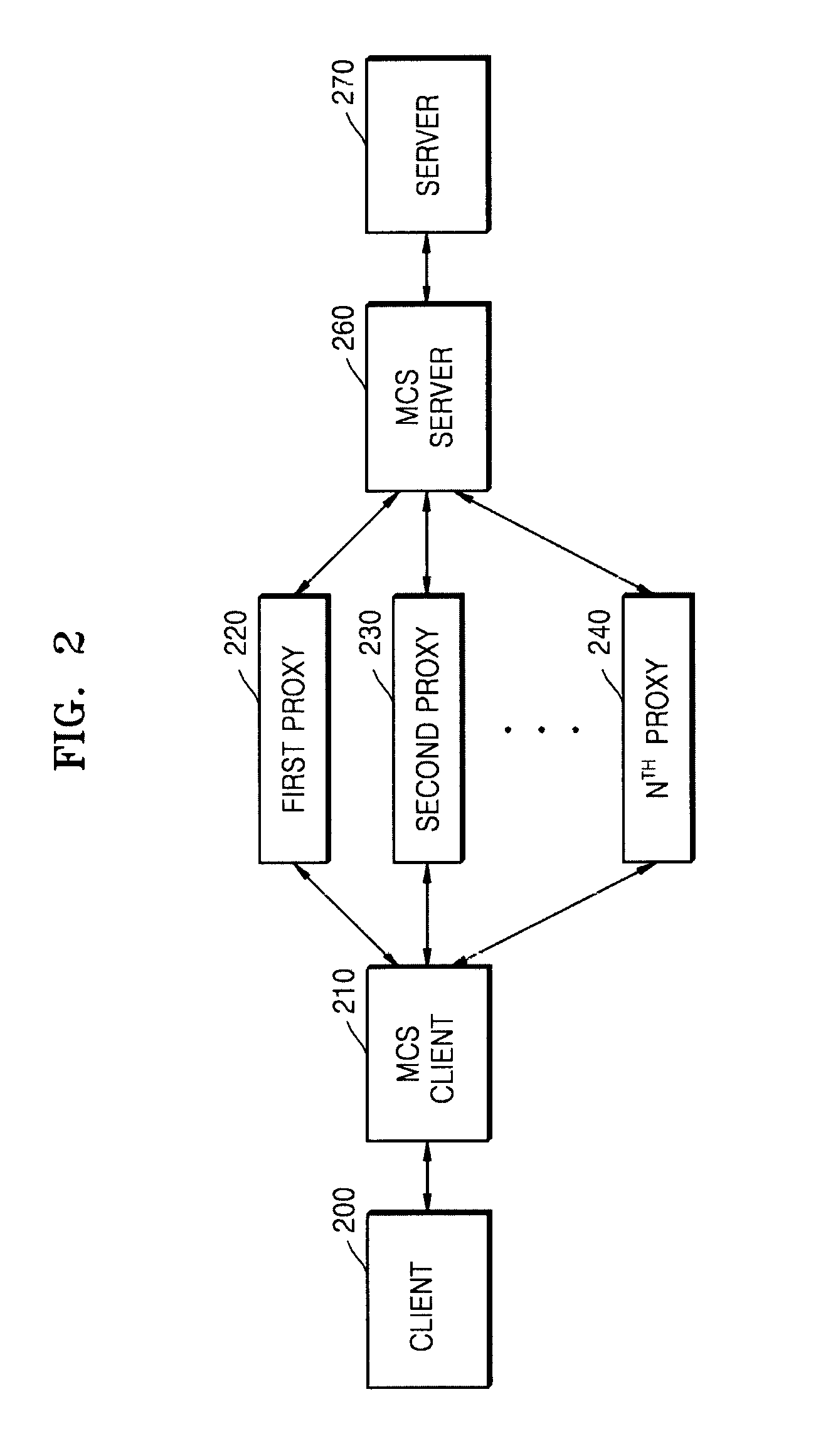
Disclosed are a multi-connection system (MCS) and method for a service using an Internet protocol. The MCS includes a plurality of proxies; an MCS client to receive a packet to be transmitted from the client to the server, generate MCS packets by adding an MCS sequence identification (ID) to the packet, and sequentially and respectively transmit the MCS packets to the plurality of proxies, wherein a number of MCS packets corresponds to a number of pieces of proxy access information connected to the plurality of proxies or a set number of pieces of proxy access information; and an MCS server to respectively receive the MCS packets from the plurality of proxies; extract the MCS sequence IDs from the MCS packets, compare the extracted MCS sequence IDs with MCS sequence IDs stored beforehand; store the extracted MCS sequence IDs, generate server-receivable packets from the MCS packets, and transmit the server-receivable packets to the server when the extracted MCS sequence IDs are not identical to the stored MCS sequence IDs; and block the MCS packets from being transmitted to the server when the extracted MCS sequence IDs are identical to the stored MCS sequence IDs.
Owner:SEO +1
Configuration Method for Channel State Information Feedback Signal and Base Station and Termination
ActiveUS20150098346A1Enhances self-adaptive capabilityImprove performanceSpatial transmit diversityFrequency-division multiplex detailsSequence IDEngineering
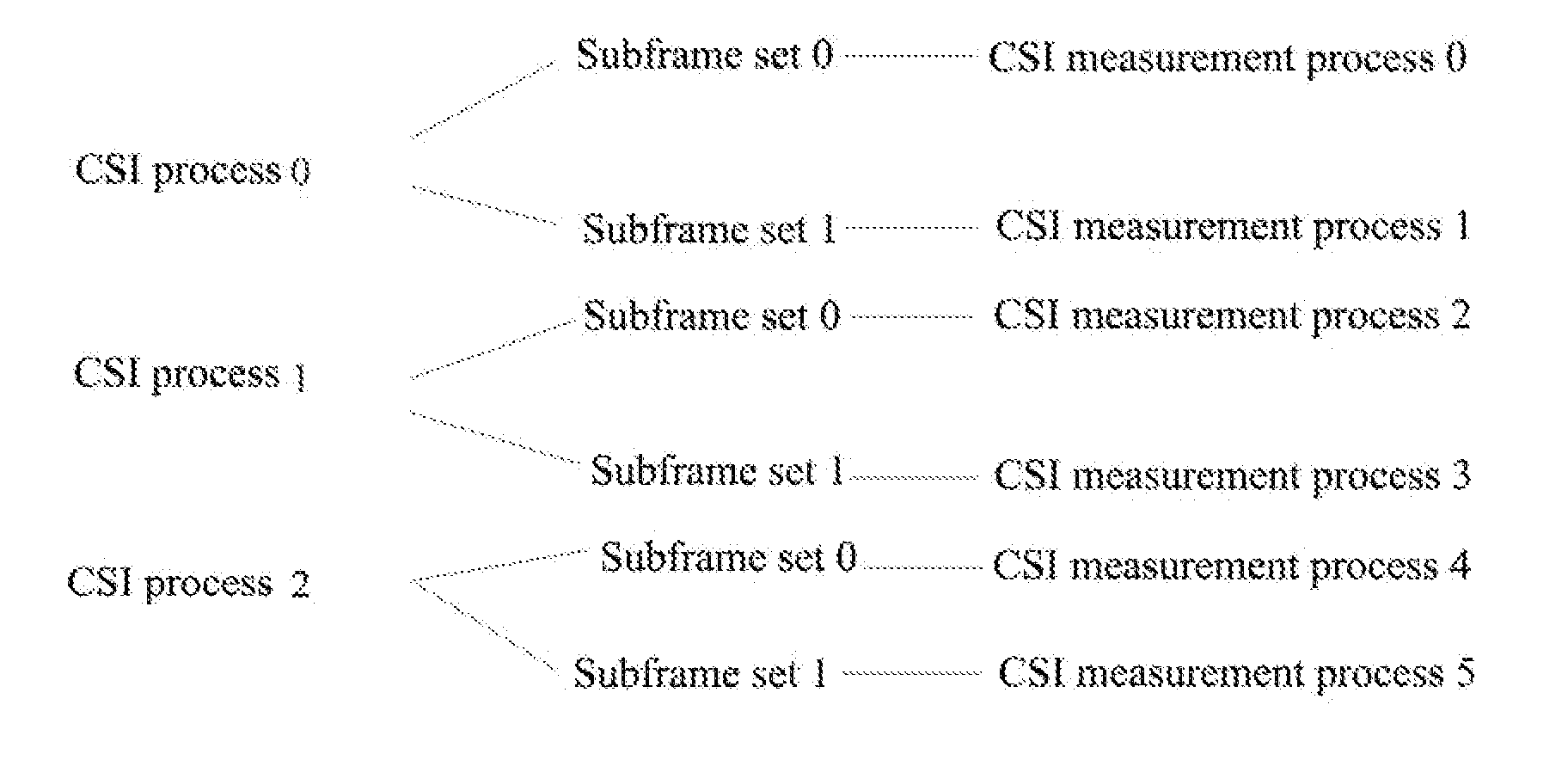
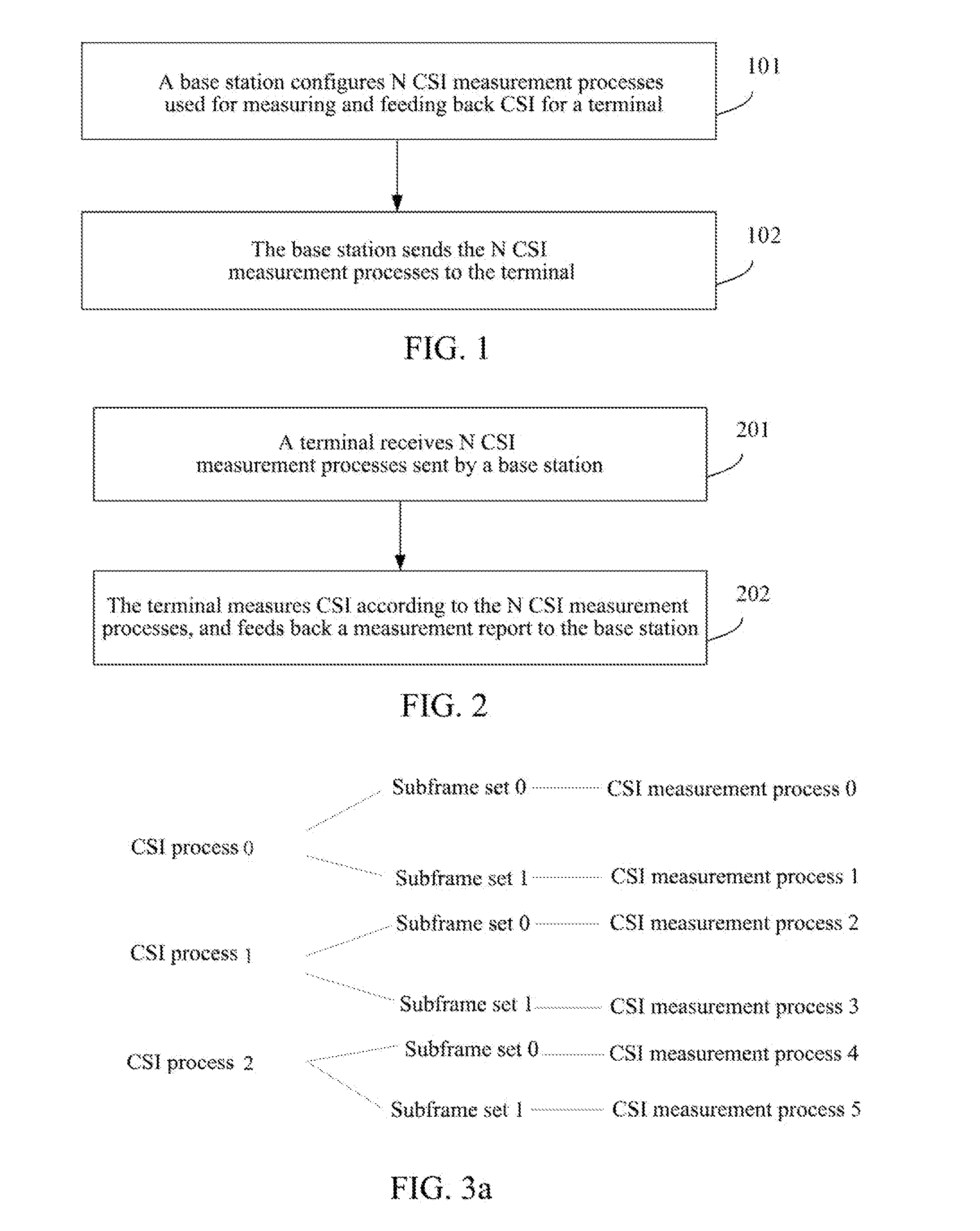
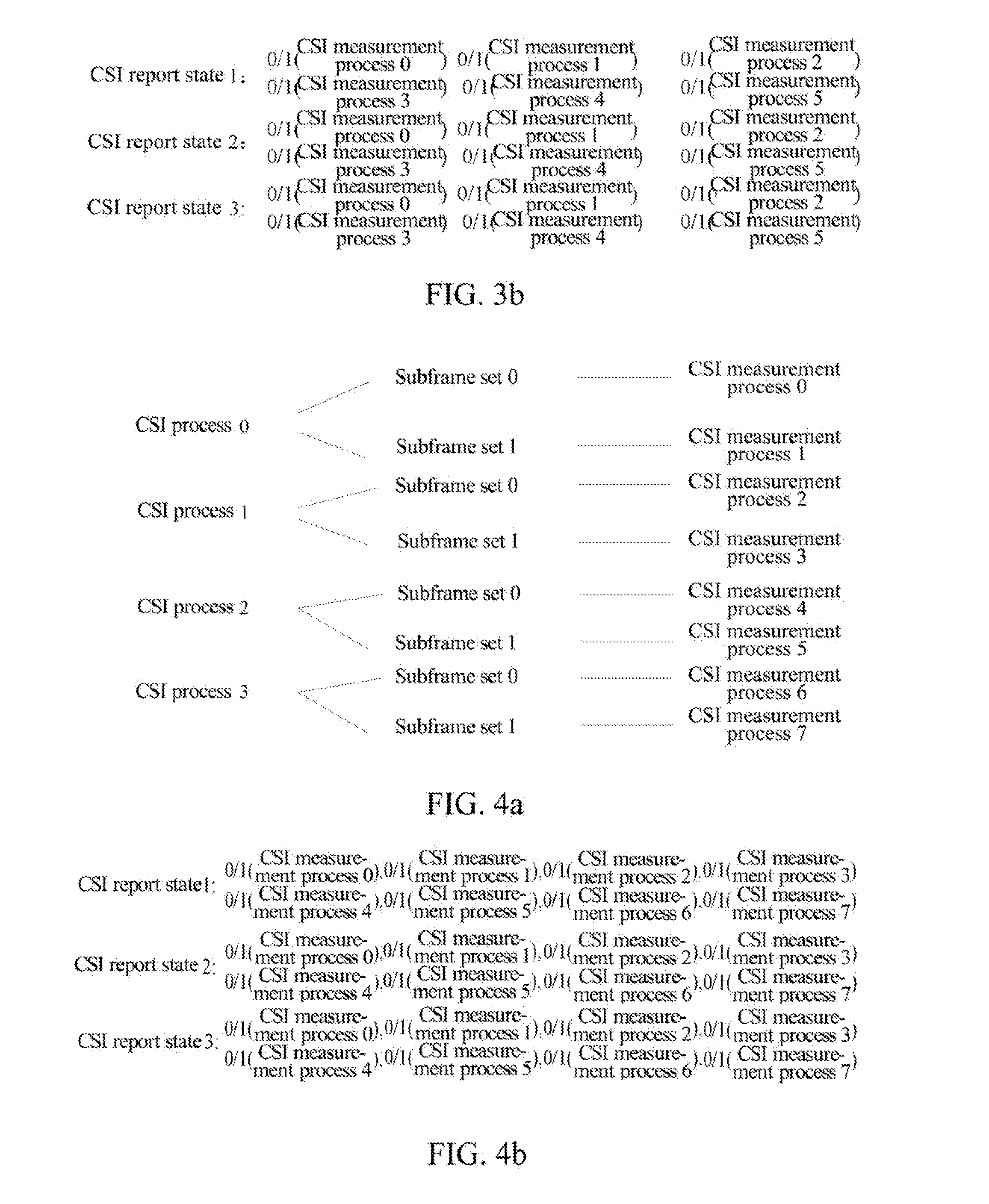
Methods for configuring Channel State Information (CSI) feedback signalings, feeding back CSI, configuring data demodulation, data demodulating, configuring antenna port information, obtaining antenna port information, base stations and terminals are disclosed. The method for configuring CSI feedback signalings includes: the base station configuring N CSI measurement processes for measuring and feeding back CSI for the terminal, each of them being independently configured with one or more of the following through terminal dedicated higher layer signaling: codebook subset restriction, PMI-RI-Report, PMI feedback-enabled, RI feedback-enabled, RI feedback-enabled according to reference process, PMI feedback-enabled according to reference process, sub-band feedback-enabled according to reference process, feedback mode, resource location fed back by PUCCH corresponding to CSI measurement process, subframe offset and cycle fed back by PUCCH corresponding to CSI measurement process, and initialization sequence ID of PUCCH corresponding to CSI measurement process; the base station sending the N CSI measurement processes to the terminal.
Owner:XIAN ZHONGXING NEW SOFTWARE
Method and device for efficiently retransmitting packets in wired/wireless network
ActiveUS20080082891A1Improve transfer rateError prevention/detection by using return channelTransmission systemsNetwork packetSequence ID
Owner:ELECTRONICS & TELECOMM RES INST
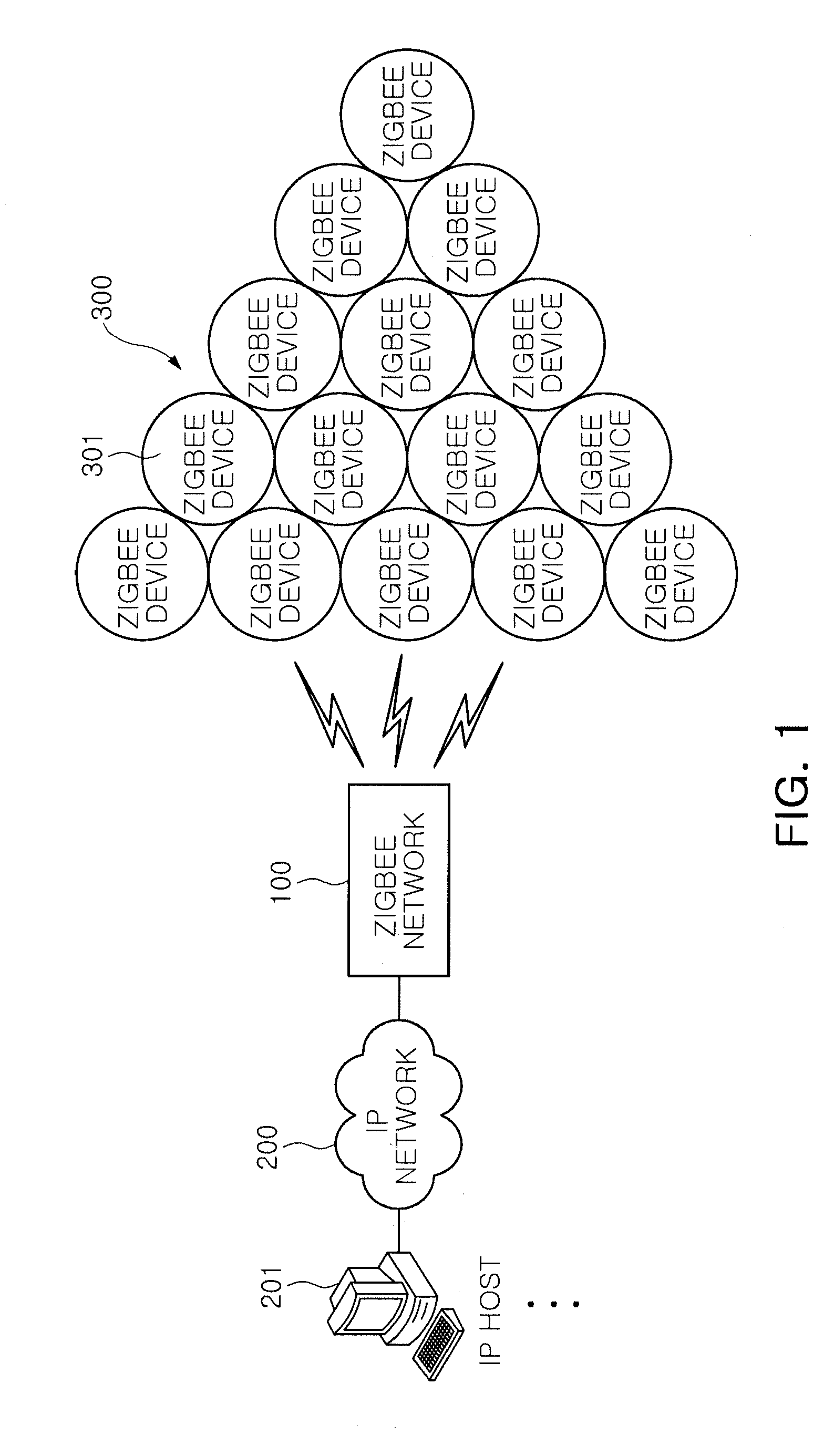
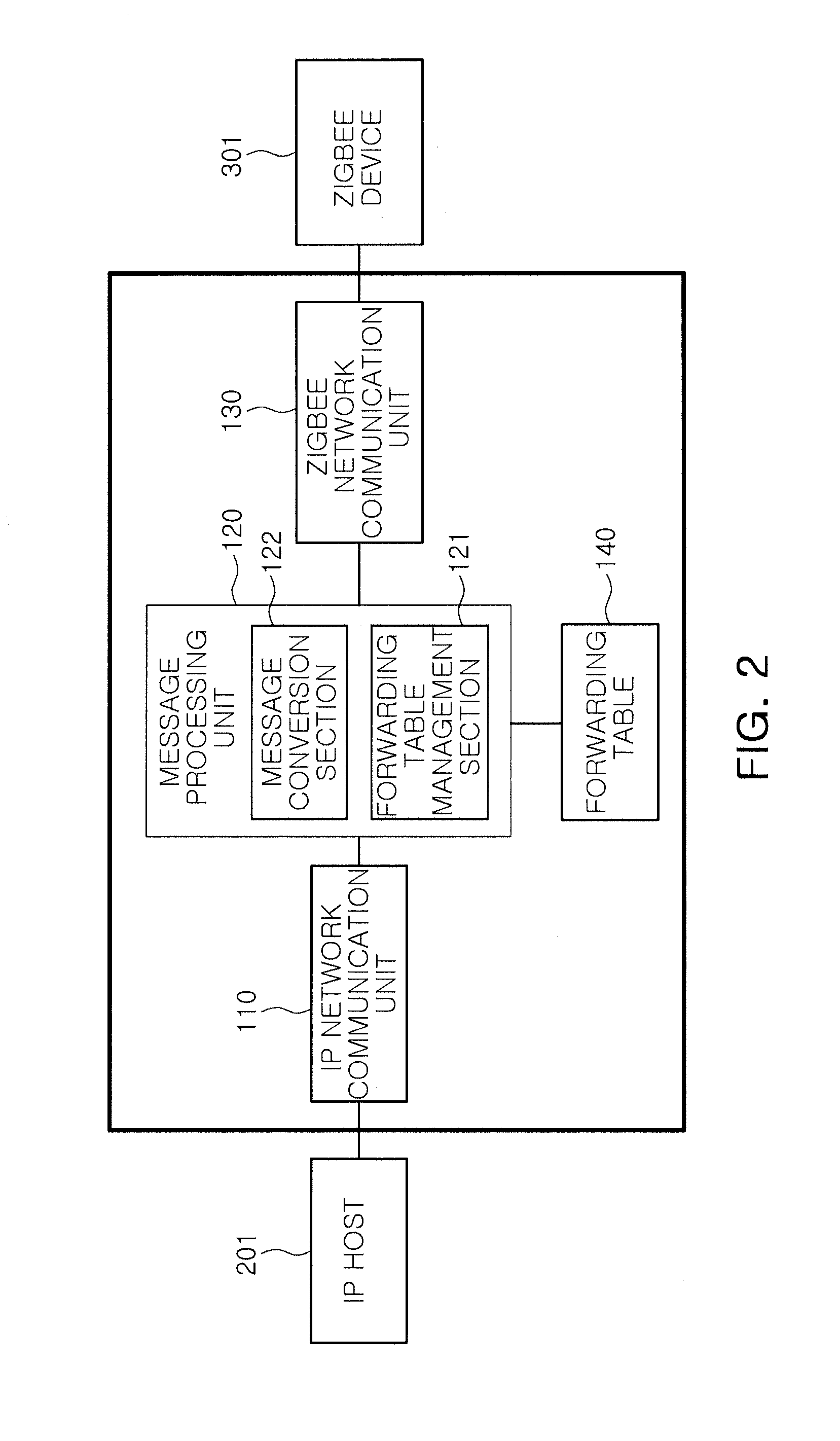
Zigbee gateway and message identification method of the same
InactiveUS20110149932A1Improve identityNetwork topologiesRadio transmission for post communicationSequence IDMessage processing
A ZigBee gateway includes: an IP network communication unit supporting communications with an IP network; a ZigBee network communication unit supporting communications with a ZigBee network; and a message processing unit generating a forwarding entry containing a service request ID and a transaction sequence ID corresponding to a service request message, when the service request message is received from the IP network, and performing a forwarding operation between the service request message and a response message transmitted from the ZigBee network in response to the service request message, by referring to the forwarding entry.
Owner:ELECTRONICS & TELECOMM RES INST
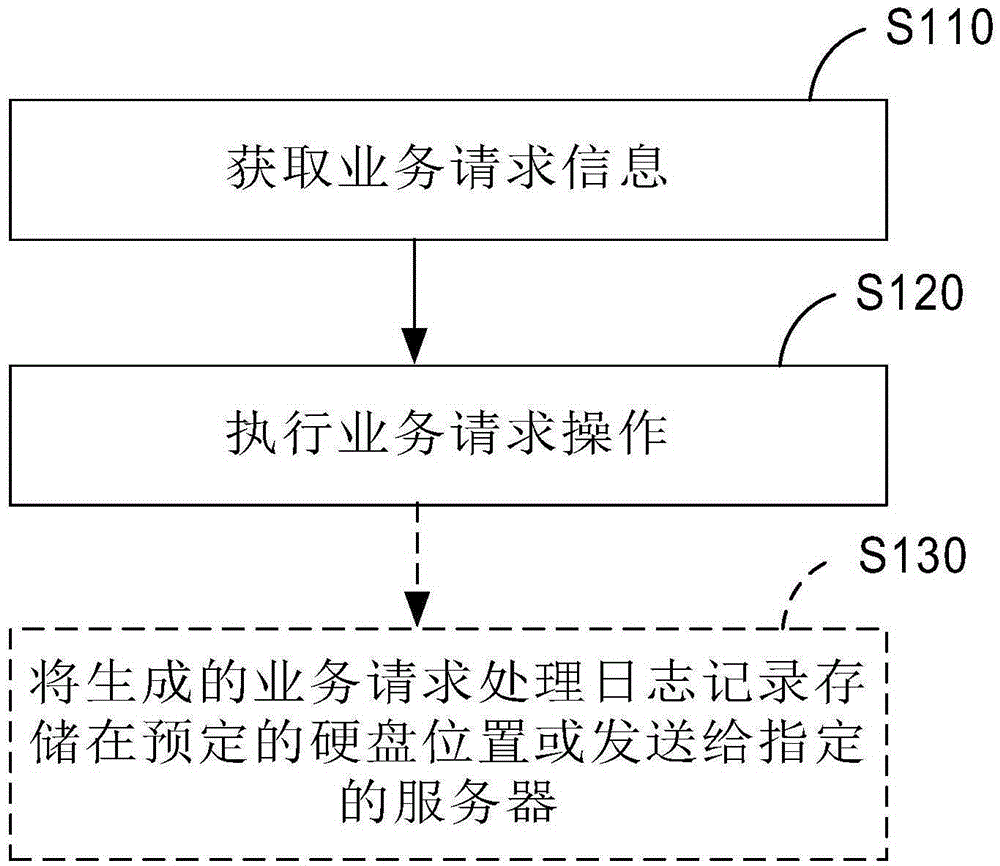
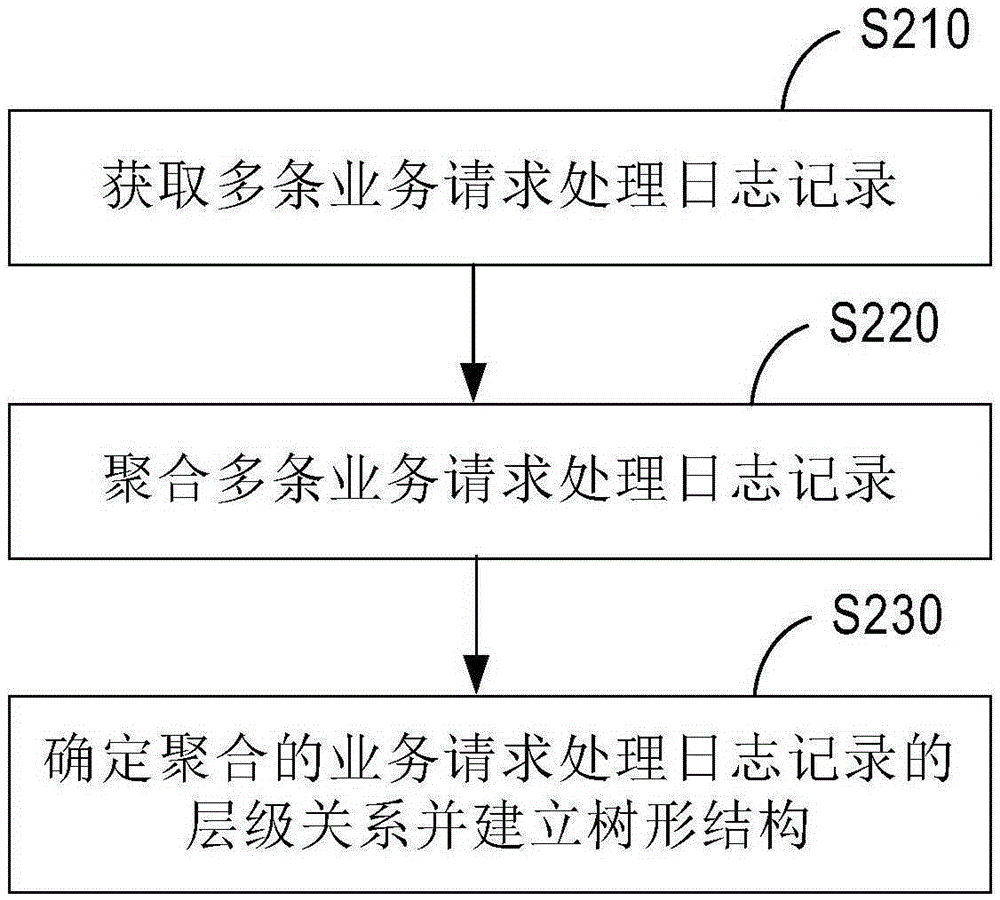
Service request processing method, log processing method and service request processing device
ActiveCN105391772AFast and accurate analysisQuick stop lossData switching networksRelationship - FatherSequence ID
An embodiment of the invention provides a service request processing method, a log processing method and a service request processing device, wherein the service request processing method comprises the steps of acquiring service request information; and executing a service request operation according to the service request information, wherein a service request processing log record which comprises a service request ID, a first log sequence ID and a second log sequence ID according to the service request information; the first log sequence ID is the ID of the current log, and the second log sequence ID is the ID of a current log father node. The service request processing method, the log processing method and the service request processing device provided by the embodiment of the invention can quickly and accurately analyze and position key information which causes a service request abnormity and / or key information that causes other online faults, thereby quickly stopping loss and reducing cost.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Multi-rotor drone autonomous landing method based on monocular vision and fuzzy control
InactiveCN109885084AHigh accuracy of pose detectionLarge detection distance rangePosition/course control in three dimensionsAdaptive controlMathematical modelSequence ID
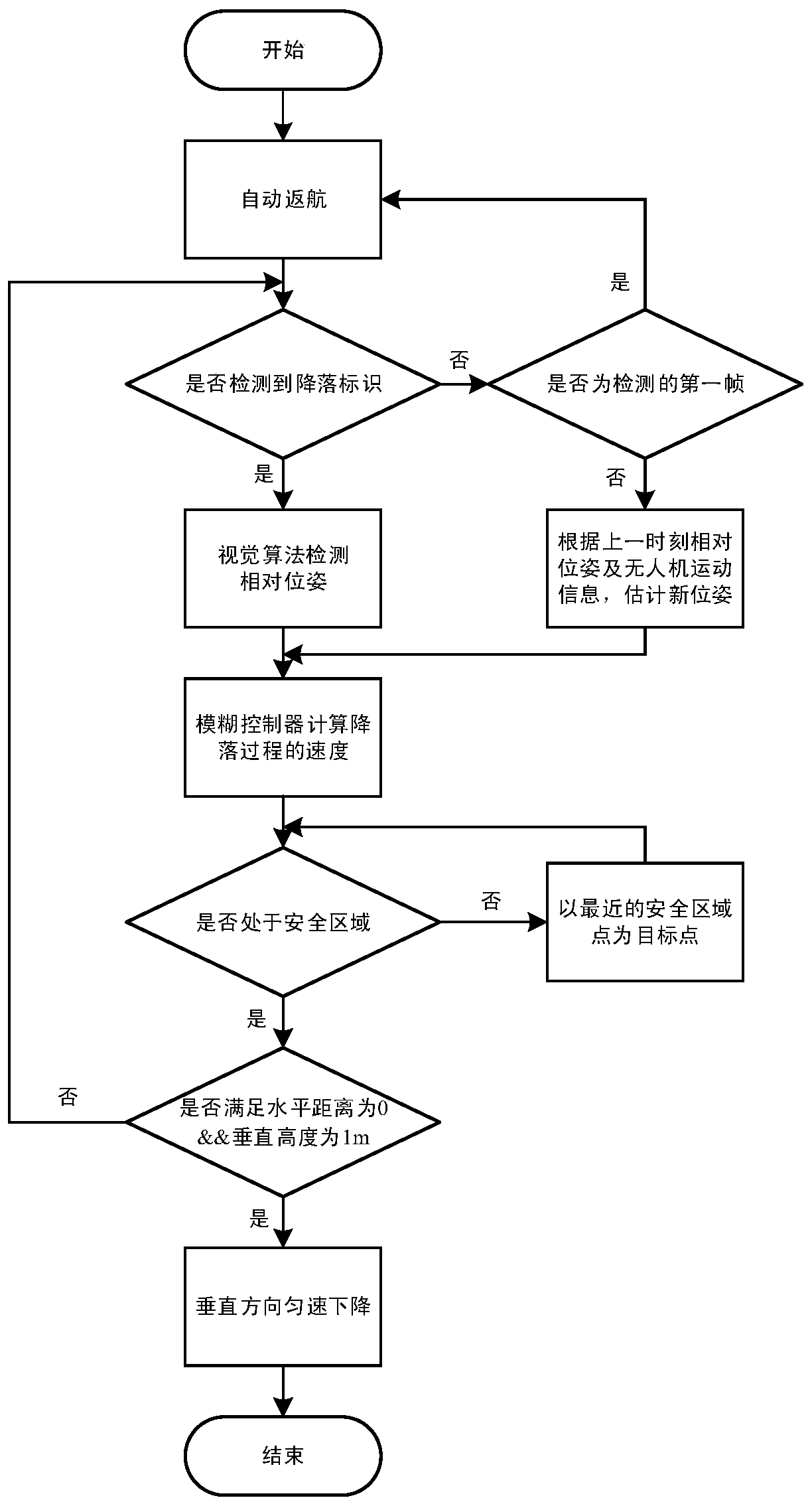
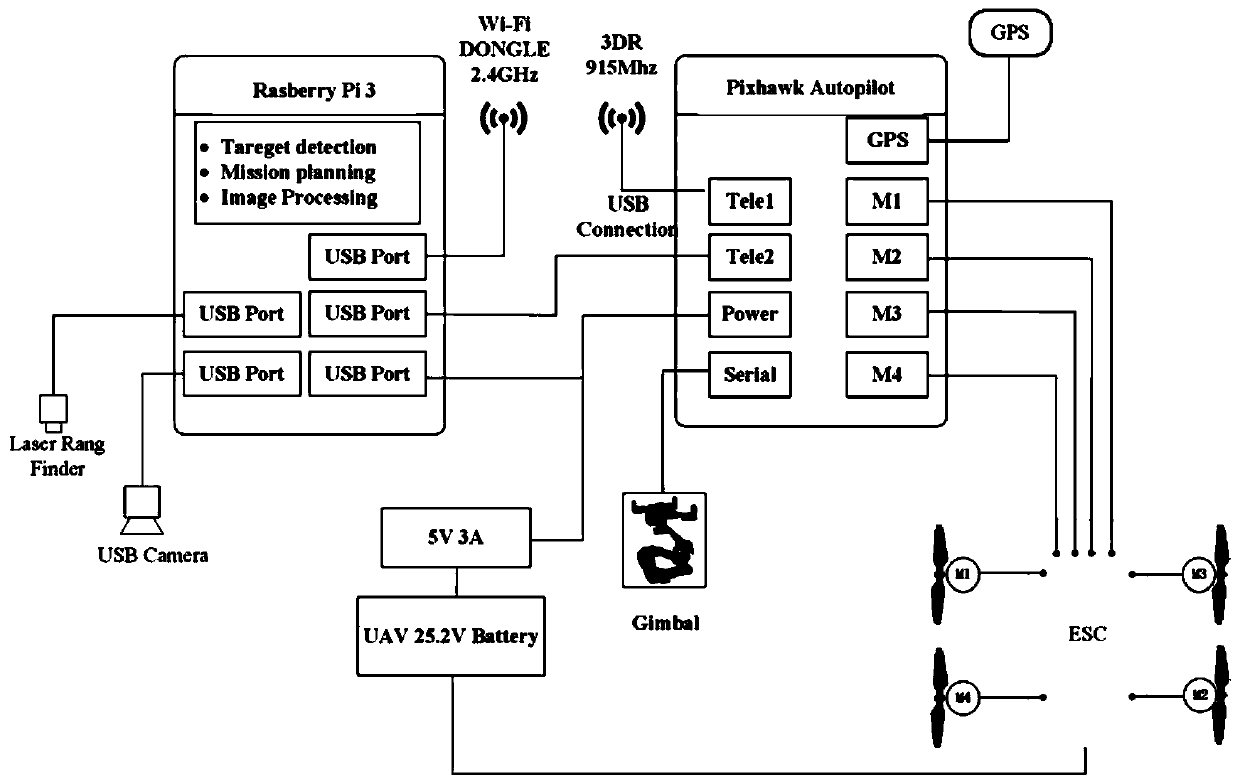
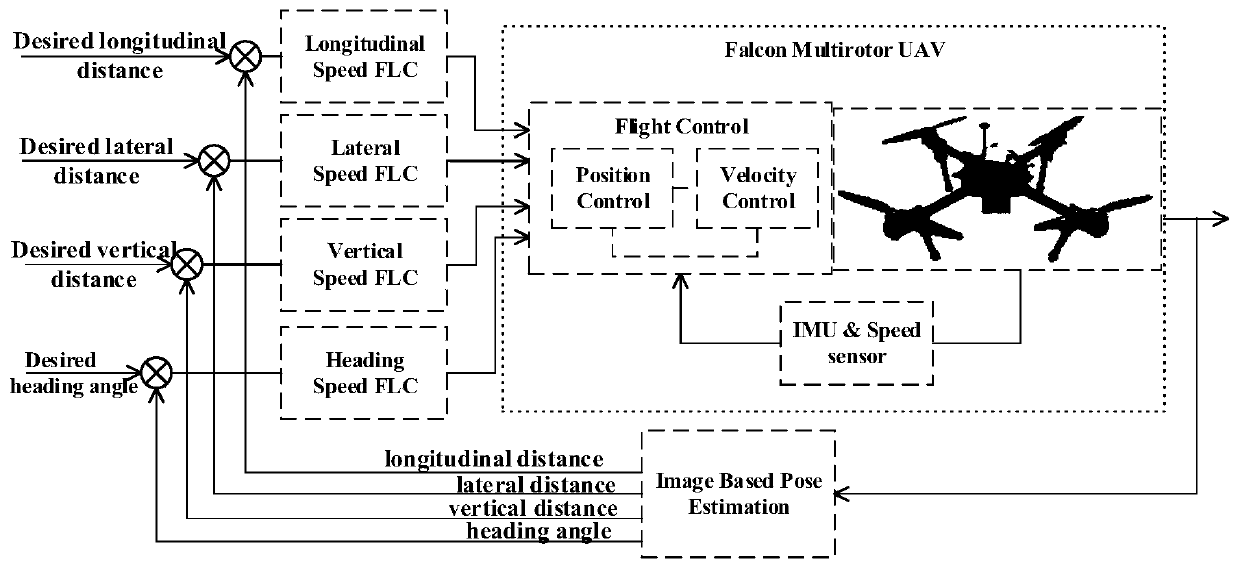
The invention discloses a multi-rotor drone autonomous landing method based on monocular vision and fuzzy control. A landing gear printed with a two-dimensional code identifier is deployed in a targetlanding area of the drone, the drone returns to the vicinity of the target area by means of GPS navigation and searches and detects the identifier based on the monocular visual information to obtainan identifier relative spatial pose and a two-dimensional code identifier sequence ID value. Based on the fuzzy control method and visual image feedback information, autonomous landing planning and control is carried out for the drone. In order to ensure the safety in the narrow takeoff and landing space, the inverted cone safety area is designed as the space position constraint of the drone landing. The drone is smoothly and safely landed on the landing gear where the target identifier is located in a smooth and efficient manner. The method overcomes the defect that the landing accuracy is insufficient due to the GPS positioning alone, has low cost, overcomes the problem of overshoot and relying on the accurate mathematical model common in PID control by fuzzy control, is safe and reliable in flight area and convenient in application, and has important engineering value.
Owner:NANKAI UNIV
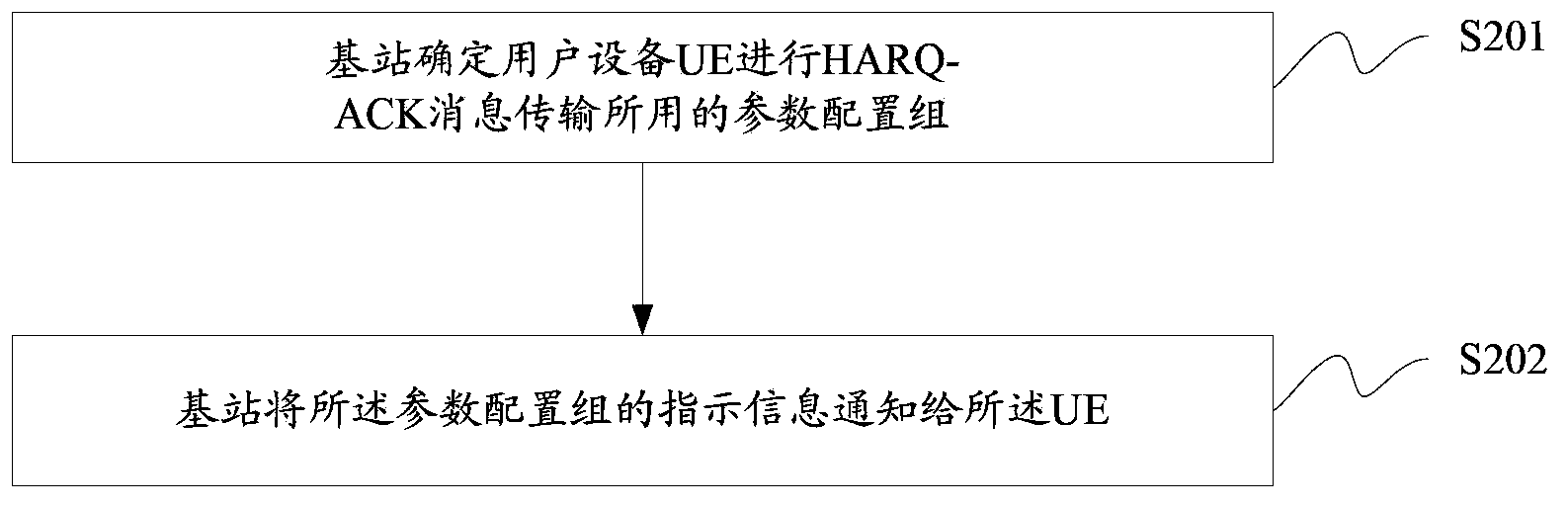
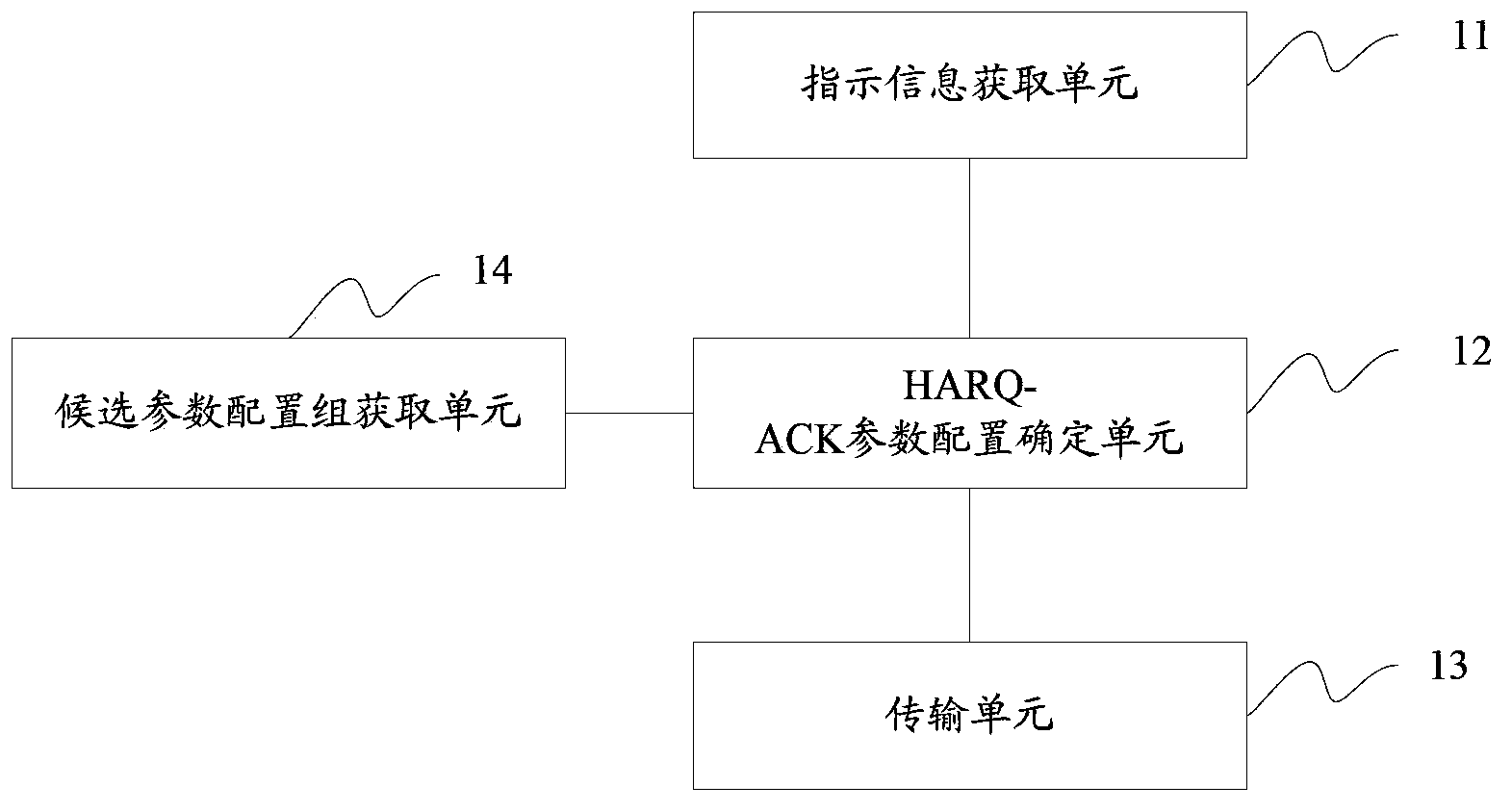
Transmission method for HARQ-ACK message and control method and device thereof
ActiveCN103490864ARealize transmissionImplement transmission schedulingError prevention/detection by using return channelComputer hardwareSequence ID
The invention discloses a transmission method for a HARQ-ACK message and a control method and device thereof, so transmission of the HARQ-ACK message through UE under different scenes is more flexibly achieved. The transmission method for the HARQ-ACK message includes the steps that the UE obtains indicating information sent by a base station and used for HARQ-ACK message transmission of a parameter configuration group, and the parameter configuration group comprises HARQ-ACK resource allocation used for HARQ-ACK message transmission and / or sequence ID configuration generating HARQ-ACK transmission sequences; the parameter configuration group used for the HARQ-ACK message transmission is determined through the UE according to the indicating information, and HARQ-ACK parameter configuration in the parameter configuration group is determined; the UE carries out HARQ-ACK message transmission according to the HARQ-ACK parameter configuration.
Owner:DATANG MOBILE COMM EQUIP CO LTD
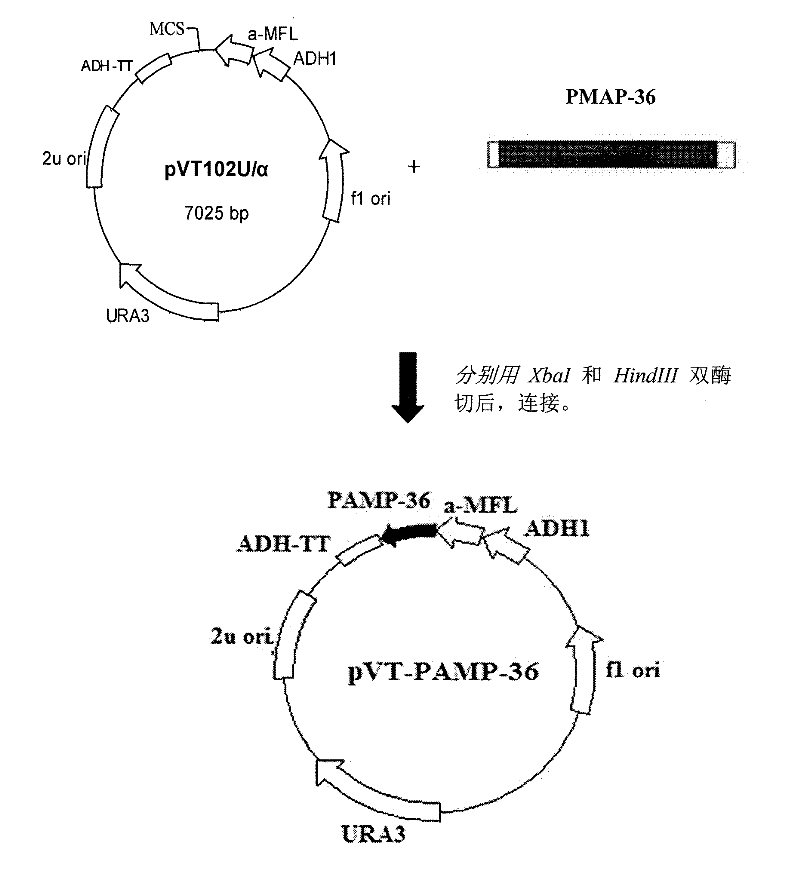
Recombinant antimicrobial peptide (AMP) as well as genetic engineering preparation method and application thereof
InactiveCN102220255AHigh antibacterial activityExpress system securityAntibacterial agentsBiocideBiotechnologyDisease
The invention provides a preparation method and application of a recombinant antimicrobial peptide (AMP) and belongs to the technical field of biological genetic engineering. The method comprises: amplification of an antibacterial peptide gene, gene cloning, transformation of beer yeast and efficient expression and purification of recombinant protein. The recombinant AMP provided by the invention is AMP-36 of the porcine Cathelicidins family, and the protein of the recombinant AMP contains short peptide shown by the sequence ID No.2. By utilizing the method provided by the invention, the prepared recombinant AMP can be used for producing a feed additive, a veterinary medicine and a preservative and preparing Gram-negative bacteria, Gram-positive bacteria and medicaments for diseases caused by fungi or virus.
Owner:SHENZHEN SUNSMILE BIOTECH
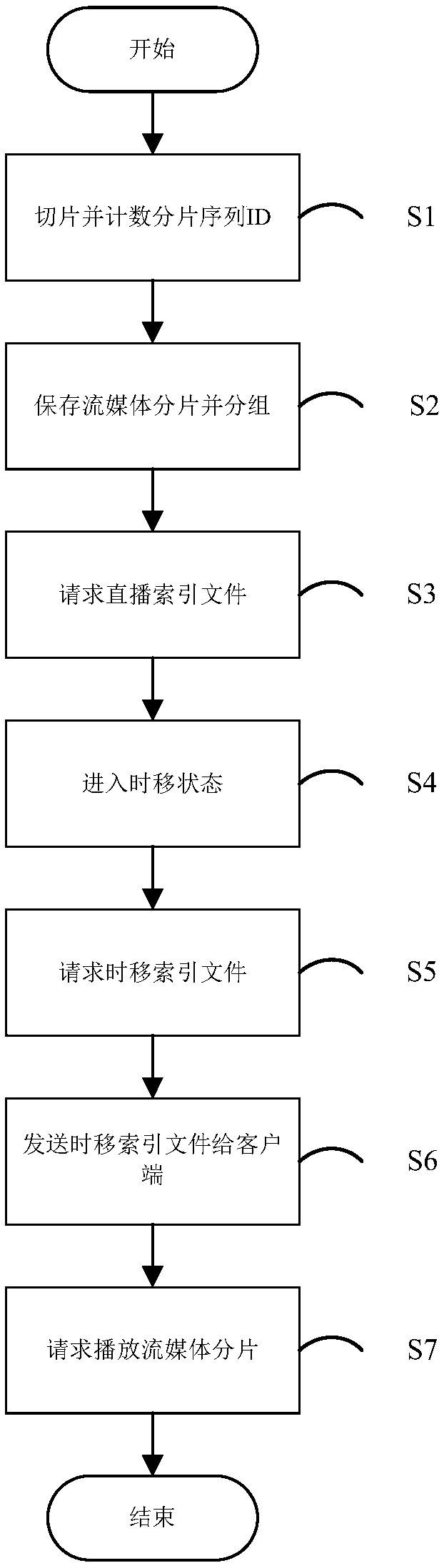
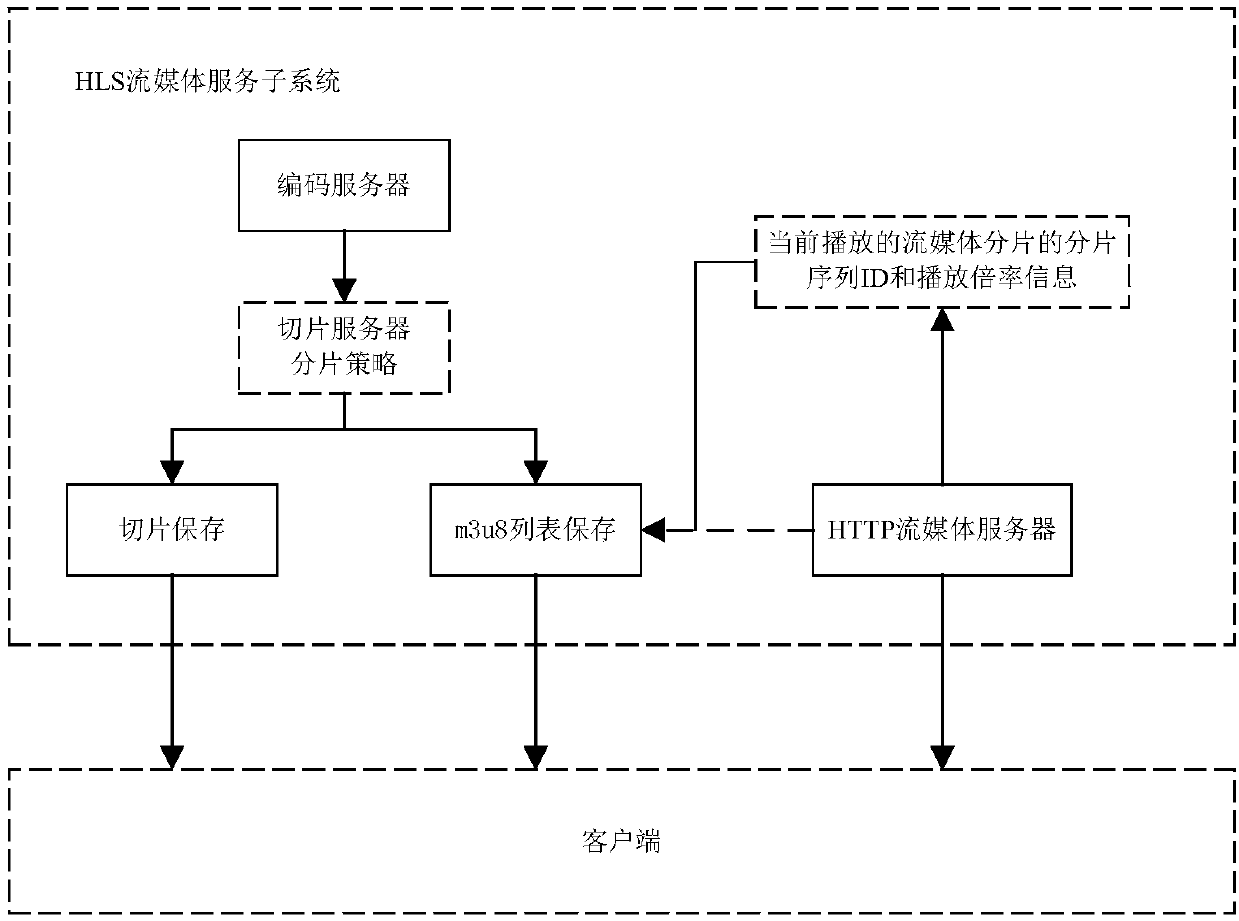
Time shifting optimization method and system based on HLS protocol
InactiveCN107707937AReduce bandwidthReduce time spentSelective content distributionSequence IDMedia server
The invention discloses a time shifting optimization method and system based on the HLS protocol, and relates to the field of Internet multimedia. The method includes the following steps: starting from a preset time point, with a media segment time length with a fixed length as a fragment length, counting a fragment sequence ID of each streaming media fragment; storing all streaming media fragments within a time shifting range, grouping the streaming media fragments, dividing every continuous N streaming media fragments into one group, wherein each group of streaming media fragments forms a time shifting index file; causing an HLS live broadcast program into a time shifting state by a client via a broadcast control operation, adding time shifting additional information on the address of the live broadcast index file, and sending the time shifting index file to an HTTP streaming media server; analyzing, by the HTTP streaming media server, the time shifting additional information, and sending the corresponding time shifting index file to the client; and requesting and playing, by the client, the received streaming media fragments. By adoption of the time shifting optimization methodand system, the bandwidth and time consumed by the transmission of the time shifting index file are reduced, which is conducive to improving the playing speed.
Owner:FENGHUO COMM SCI & TECH CO LTD
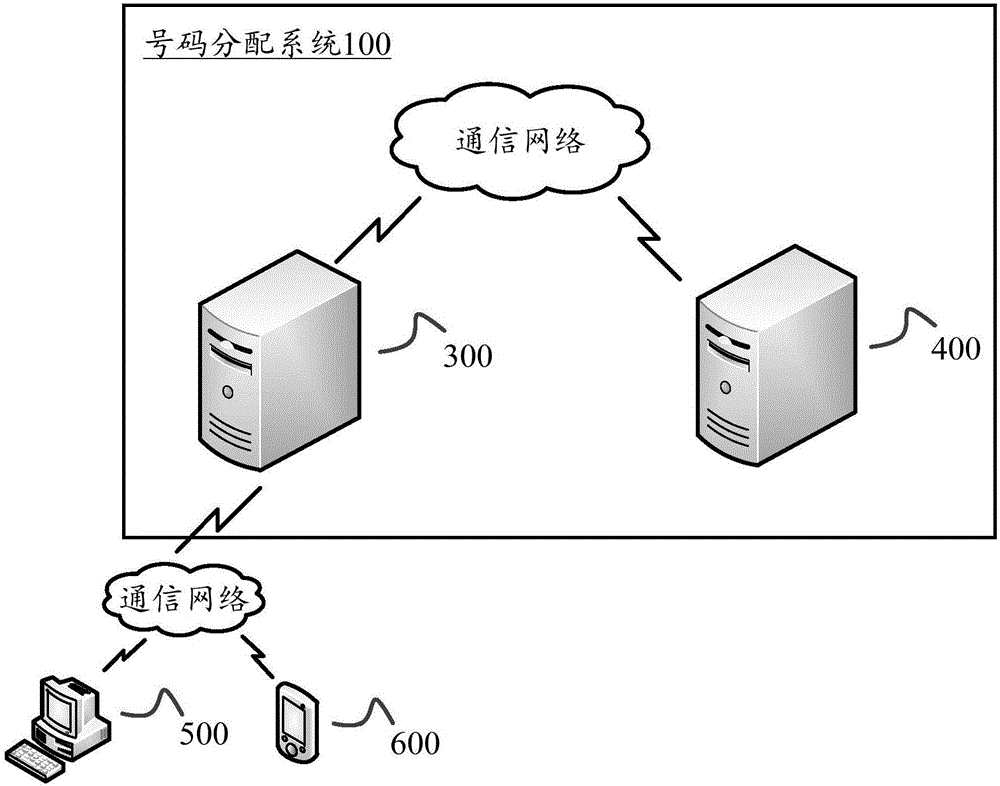
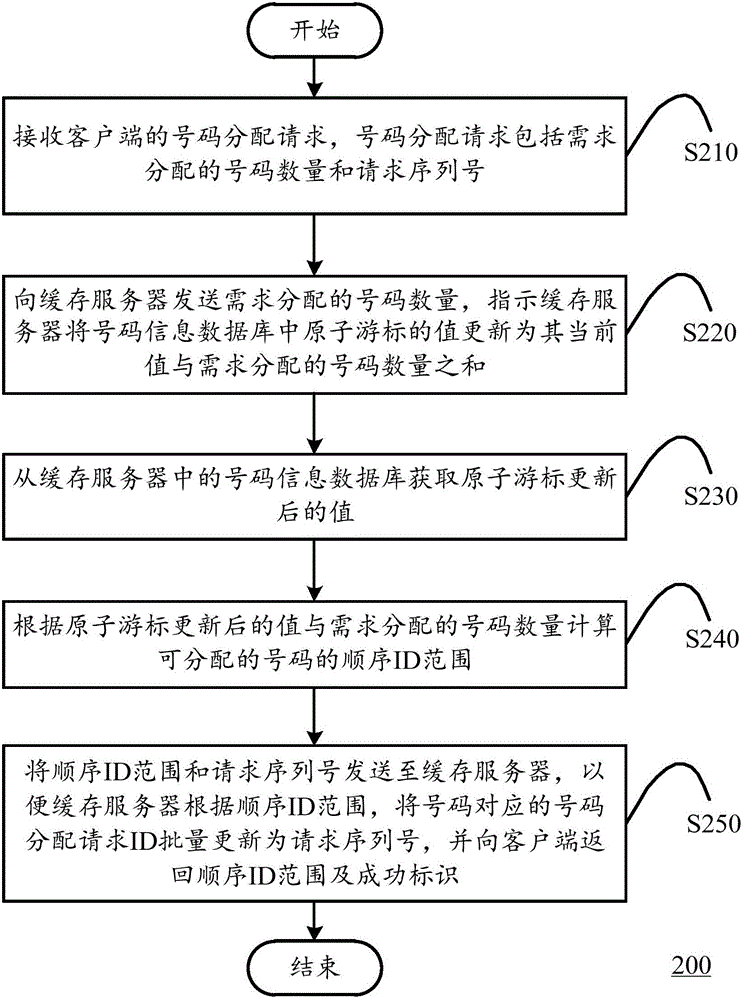
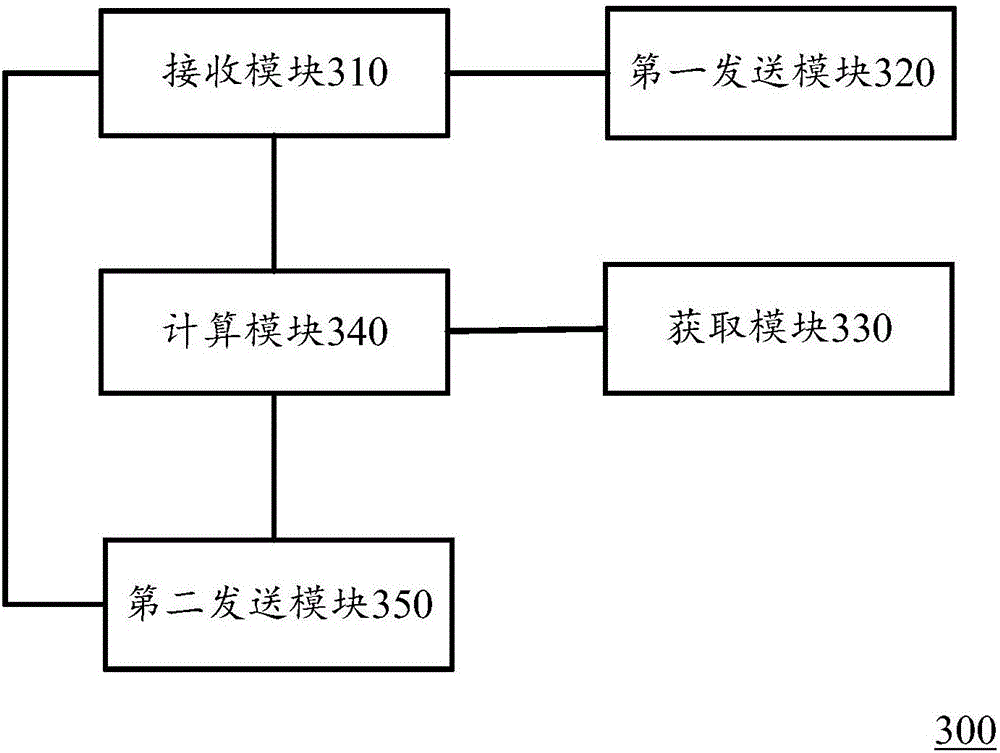
Number distribution method, server and system
Owner:北京科摩仕捷科技有限公司
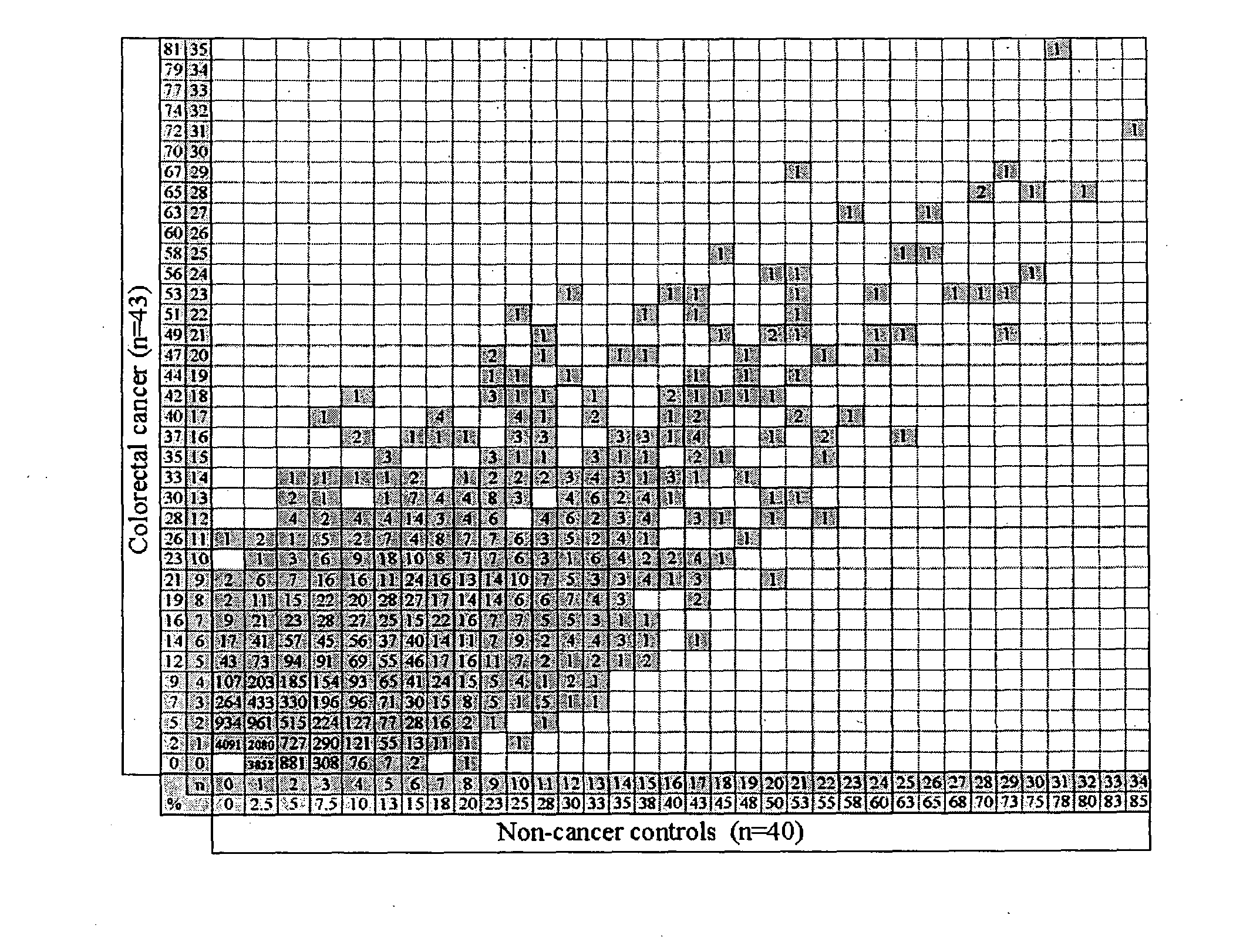
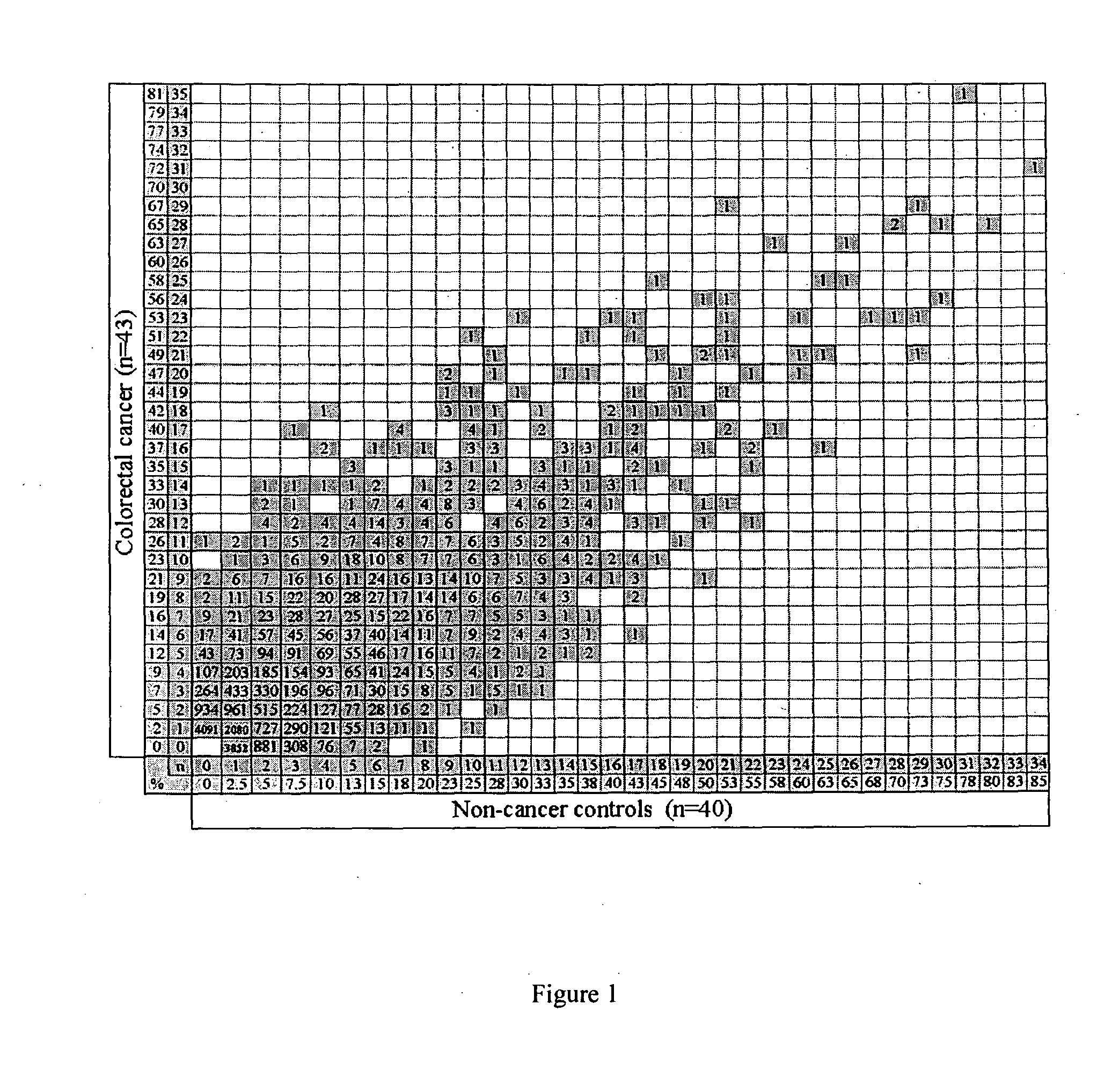
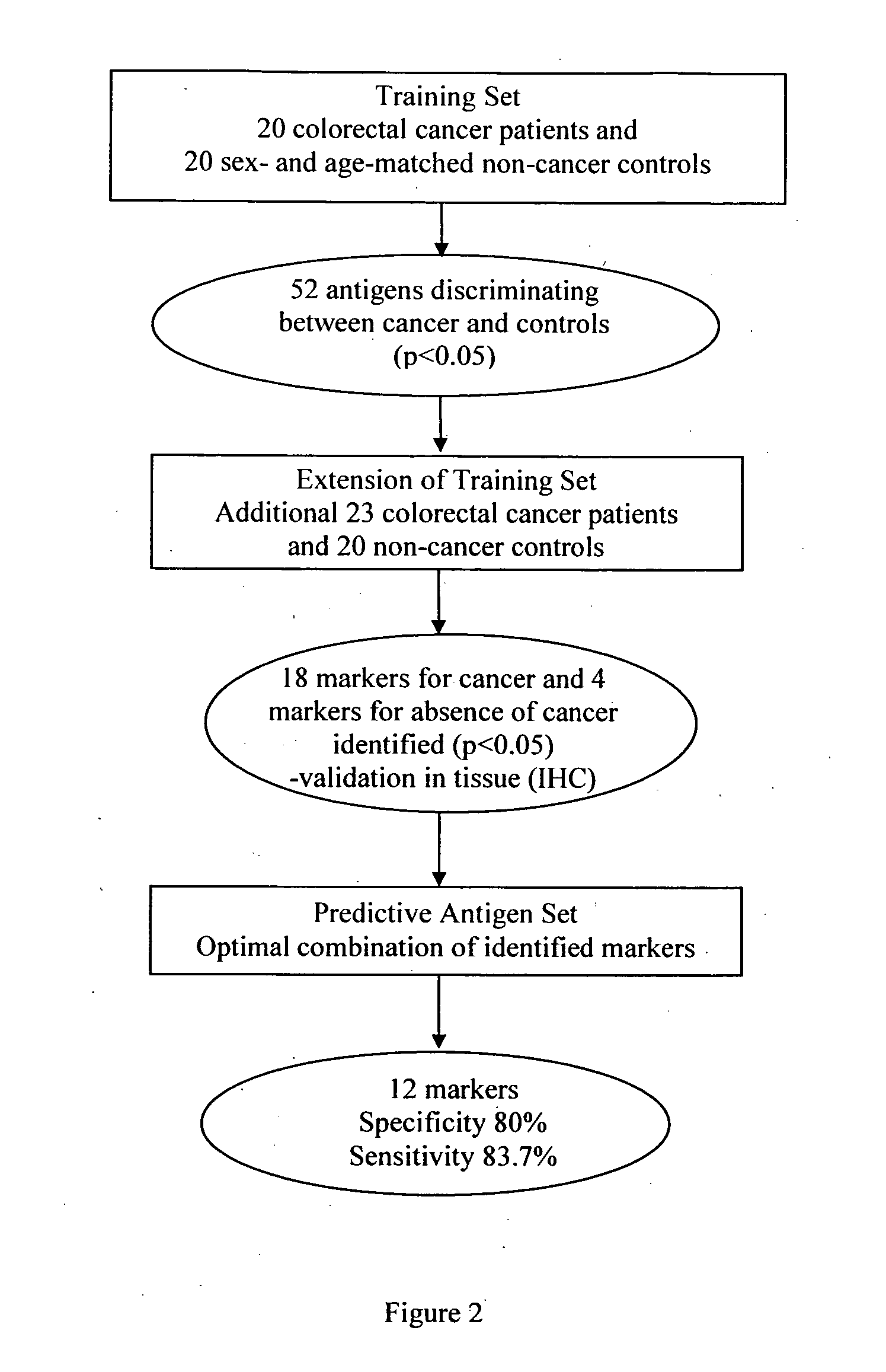
Method of assessing colorectal cancer status in an individual
InactiveUS20100304410A1Reduce in quantityAssisted identificationMicrobiological testing/measurementBiological testingAutoantibodySequence ID
The invention relates to a method of screening a patient to identify and quantify risk of colorectal cancer, and thereby identify patients suitable for further invasive investigation such as a colonoscopy. The method employs auto-antibodies that are shown to correlate with colorectal cancer risk method and involves of assaying a biological sample from the individual for a combination of a plurality of biomarkers selected from SEQUENCE ID NO's: 1 to 12, where the combination of biomarkers is chosen such that detection of all biomarkers in the patient correlates to at least a 50% risk of the patient being positive for colorectal cancer. Detection of all of the combination of biomarkers indicates that the patient should undergo a colonoscopy. Kits for performing the method of the invention are also provided.
Owner:ROYAL COLLEGE OF SURGEONS & IRELAND
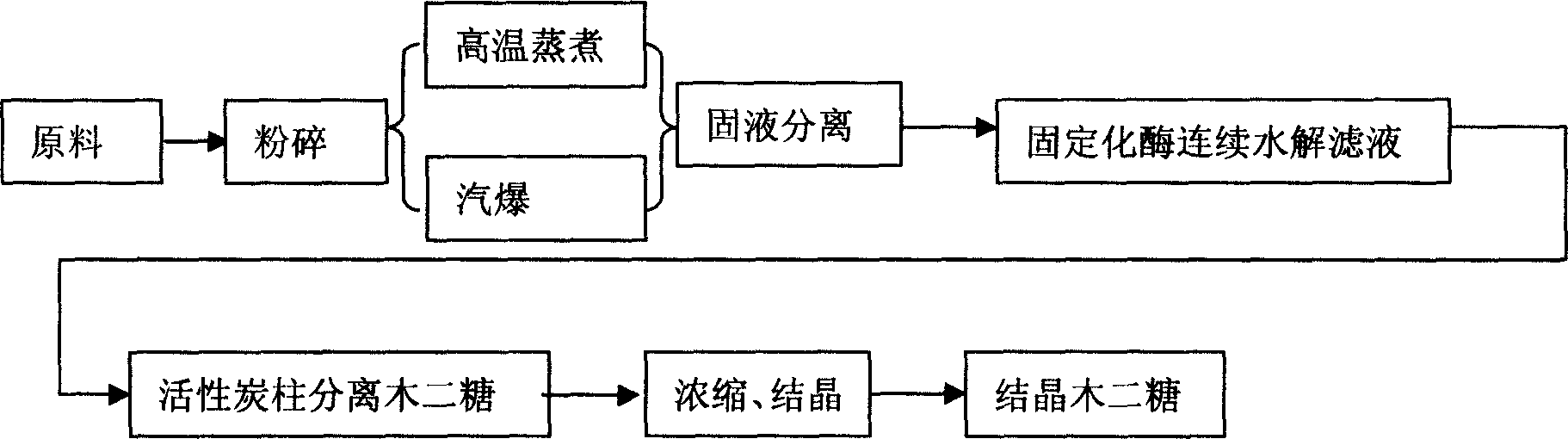
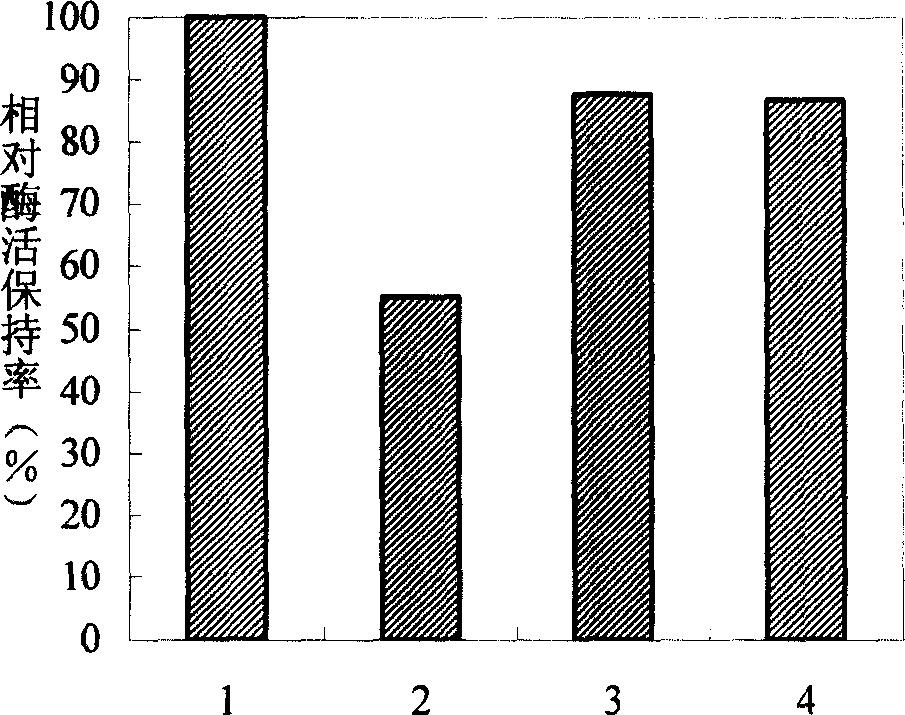
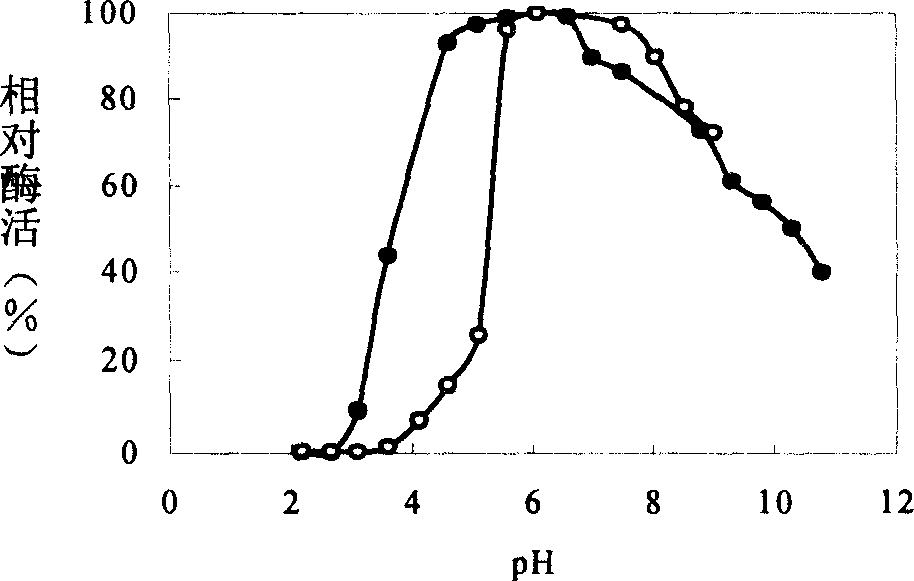
Method for producing xylobiose, and dedicated immobilized enzyme
Owner:CHINA AGRI UNIV
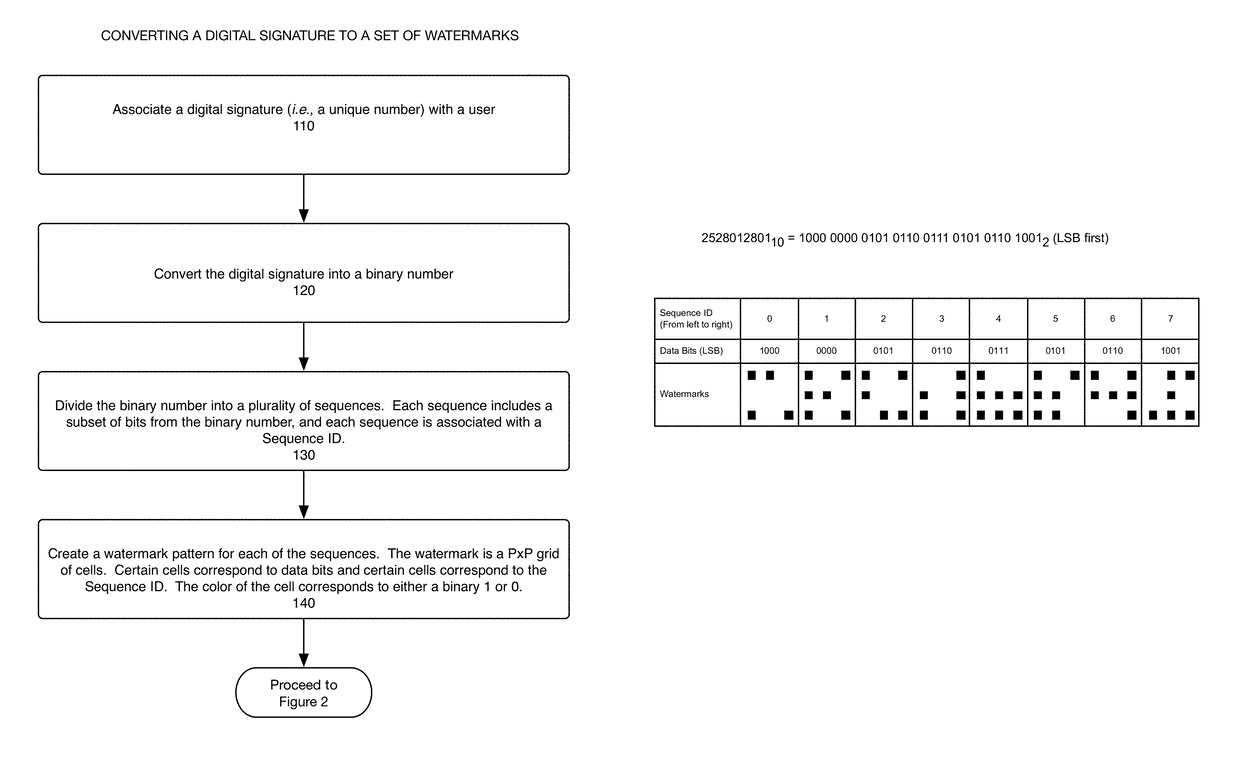
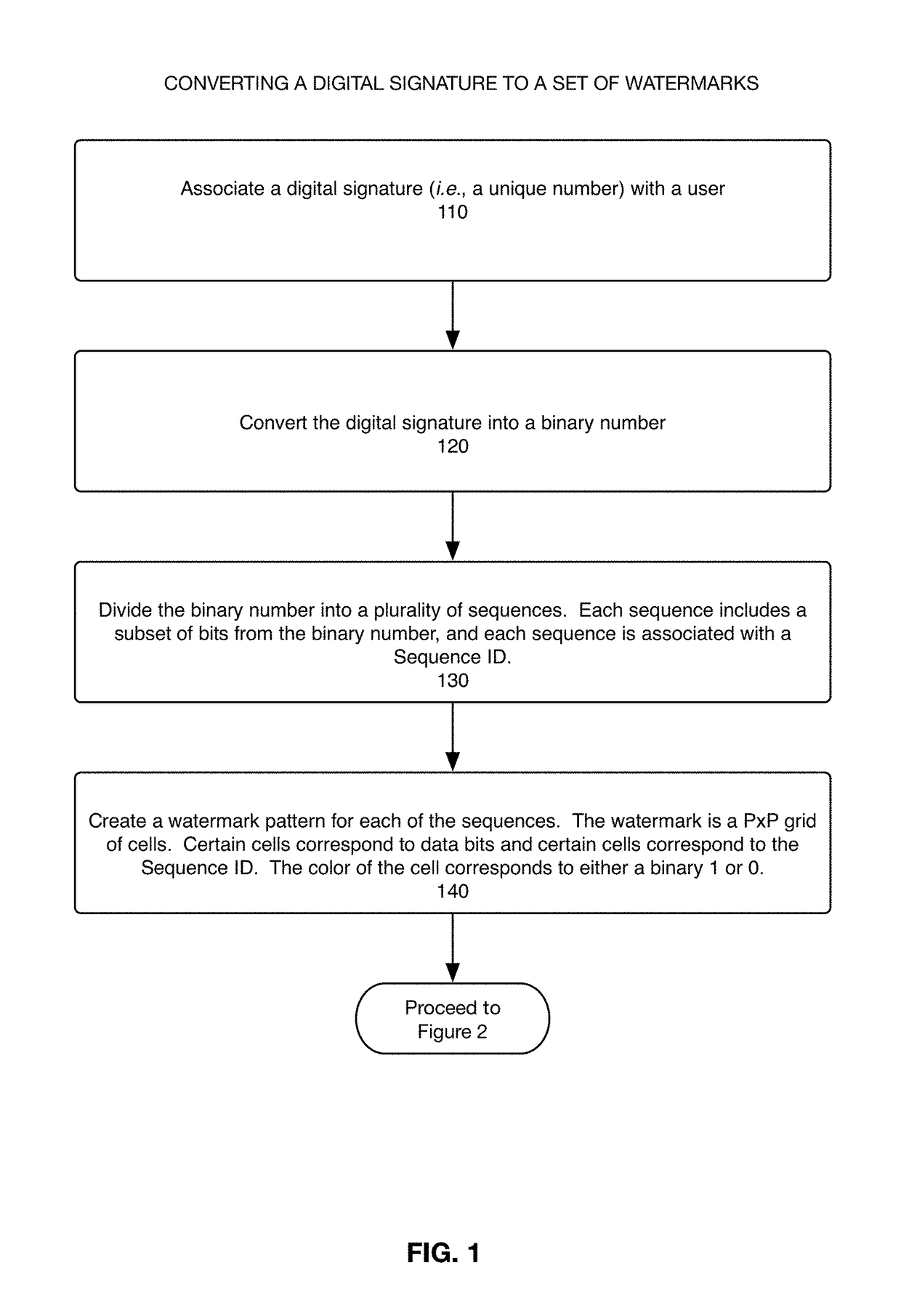
System, method, and computer program for encoding and decoding a unique signature in a video file as a set of watermarks
ActiveUS9959586B1Image data processing detailsDigital video signal modificationComputer hardwareDigital signature
The present disclosure describes a system, method, and computer program for encoding and decoding a unique signature for a user in a video file, wherein the digital signature is substantially invisible to the viewer of the video, easy to detect during the coding process, does not require specialized equipment for playback of the video, and is resilient to transcoding, video editing, and high compression encoding. A numeric digital signature is converted into a binary number. The binary number is then divided into sequences, where sequence includes a subset of data bits from the binary number. Each sequence is also associated with a sequence ID that enables the data bits in the sequence to be later combined in the correct order to recreate the binary number. A watermark is created for each of the sequences and embedded within suitable areas of a color channel.
Owner:GOANIMATE INC
Monoclonal antibodies against N-Terminus proBNP
Monoclonal antibodies having high affinity for N-terminus pro brain natriuretic peptide (NT-proBNP) are described. The monoclonal antibodies are prepared against a synthetic peptide having the Sequence ID No. 1. Specifically, the monoclonal antibodies described are produced from two hybridoma cell lines, 6G11-F11-D12 and 1C3-E11-R9, deposited with the American Type Culture Collection under Accession Numbers PTA-4844 and PTA-4845 respectively. The monoclonal antibody antibodies can be used as reagents in an immunoassay system to identify blood, serum or plasma levels of NT-proBNP. Such an immunoassay system can be used for diagnosing and quantifying congestive heart failure (CHF).
Owner:OTTAWA HEART INST RES
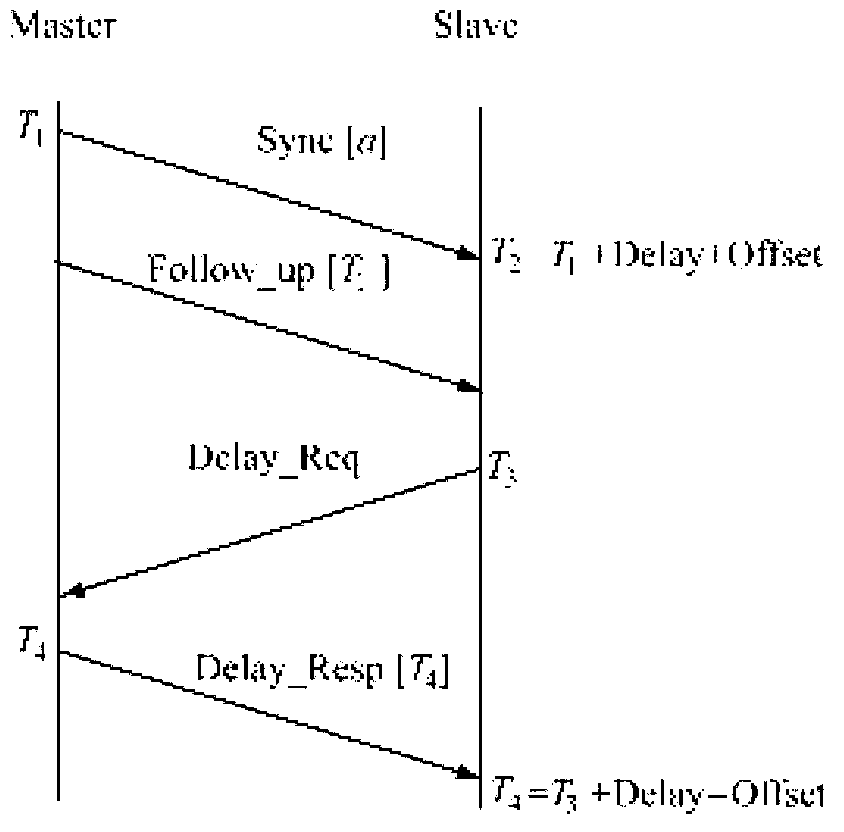
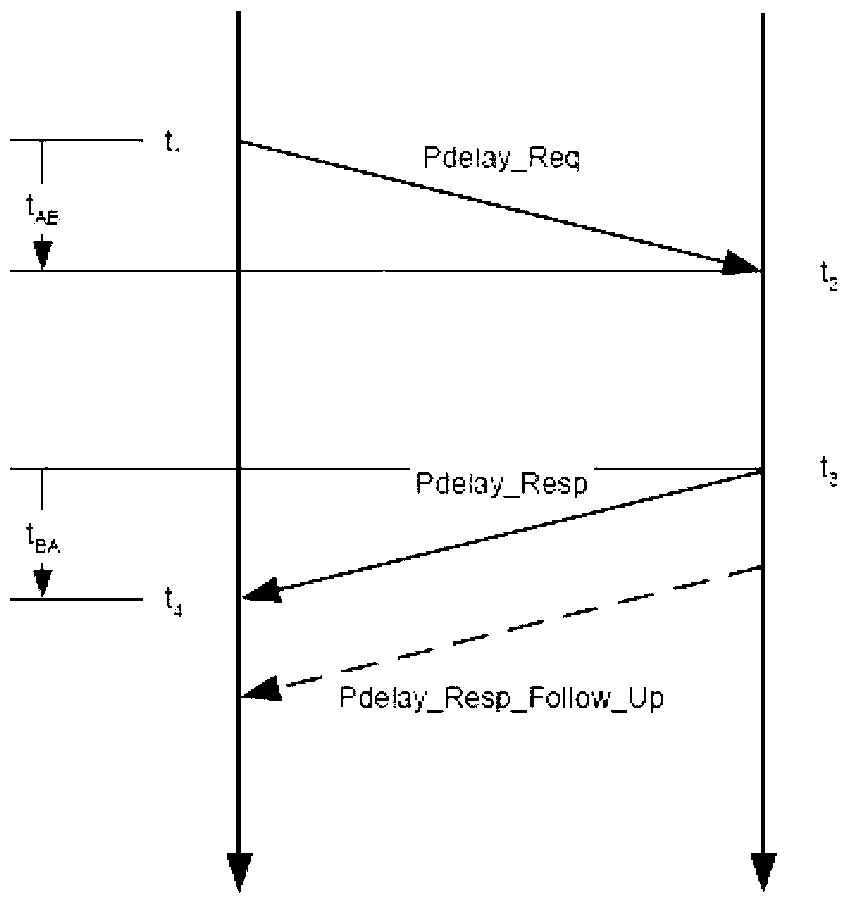
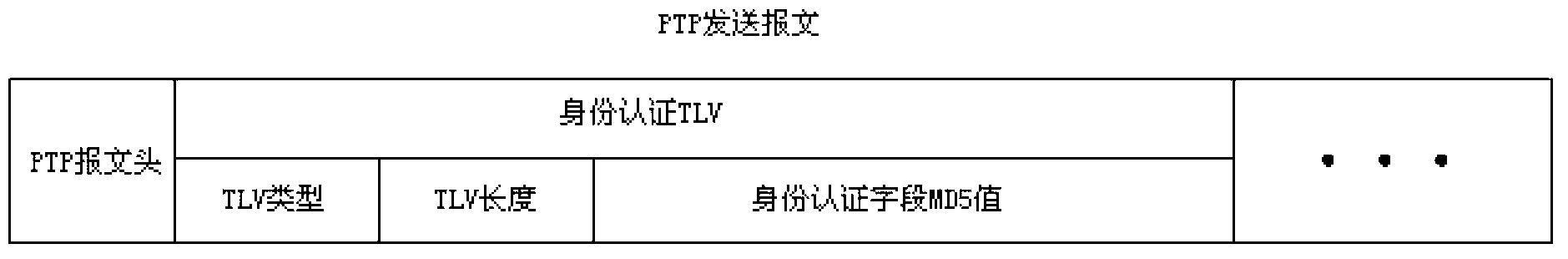
Method for setting security authentication in precision time protocol (PTP)
InactiveCN102801733AEnsure communication securityNot vulnerable to malicious attacksTransmissionCommunications securitySequence ID
The invention discloses a method for setting security authentication in a precision time protocol (PTP). The method comprises the following steps of: setting keys on a time synchronous source and time synchronous equipment in advance, and adding an identity authentication field in the transmitted PTP message when the time synchronous source transmits synchronous information to the time synchronous equipment, wherein the field comprises a first MD5 value, and the MD5 value consists of a sequence ID field and key logic operation; performing corresponding logic operation on the sequence ID field in the message and a locally preset key when the time synchronous equipment receives the PTP message to obtain a second MD5 value; comparing the two MD5 values, passing the PTP authentication if the PTP messages are the same, otherwise discarding the messages. Thus, the communication safety of PTP is guaranteed, so that equipment for operating the PTP is hardly influenced by hostile attack from an internet.
Owner:SUZHOU CENTEC COMM CO LTD
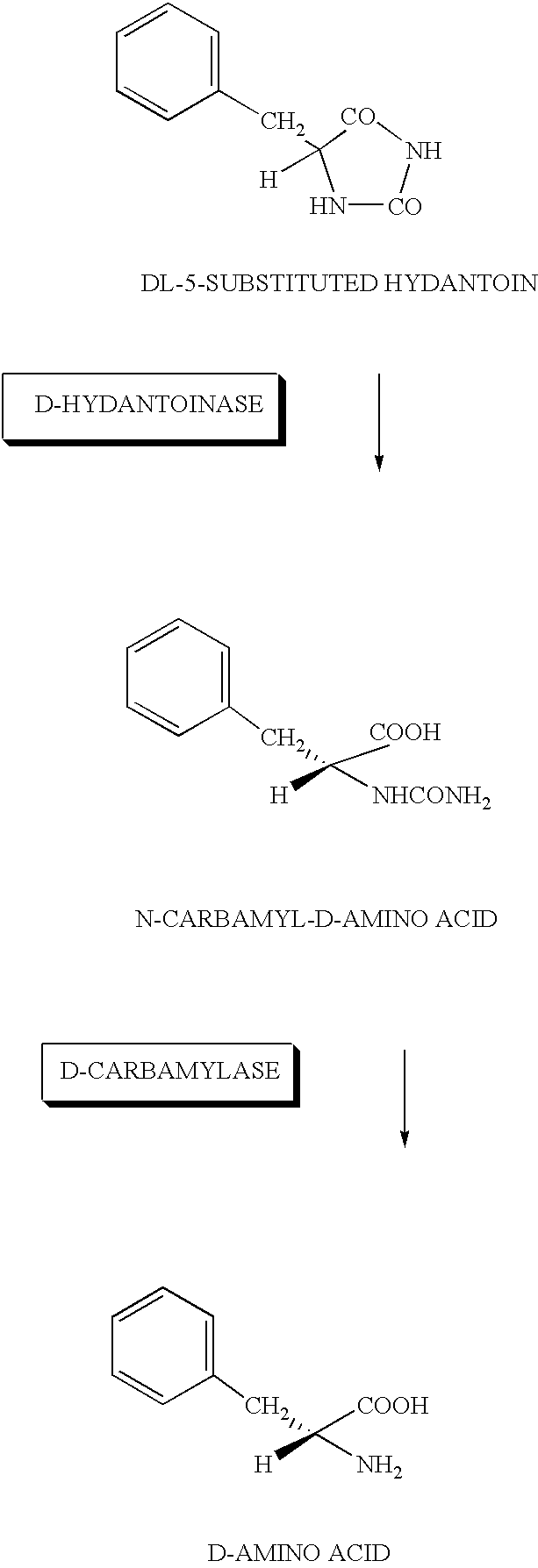
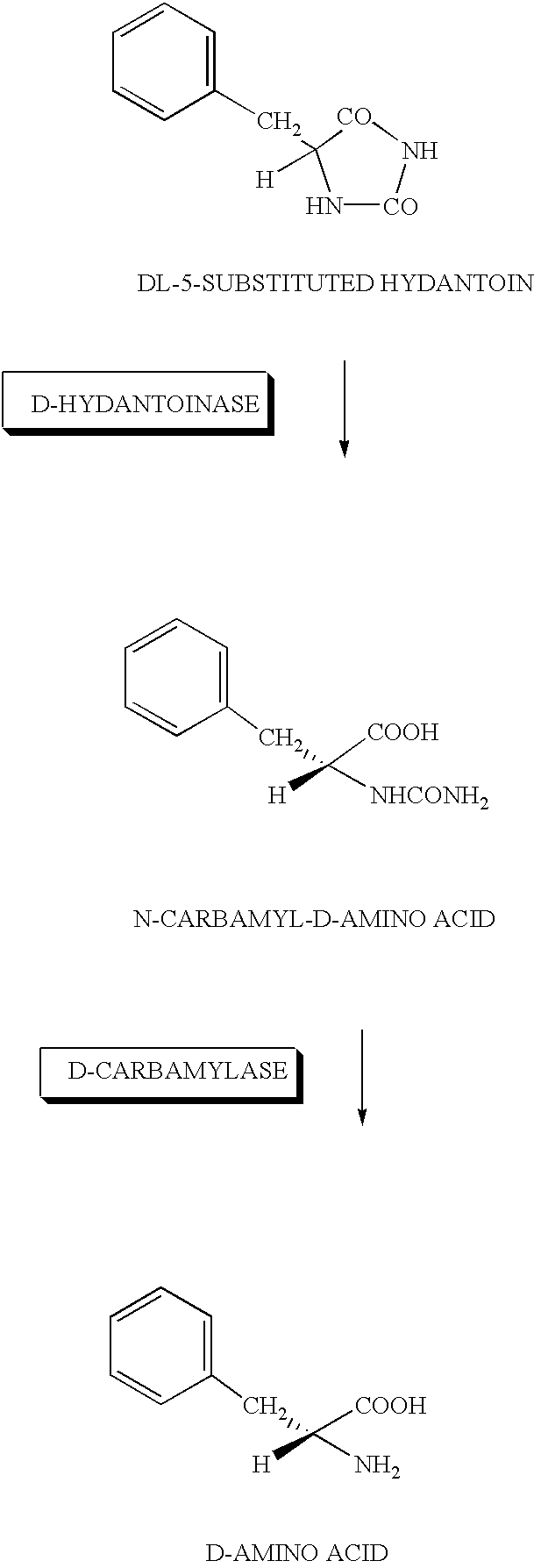
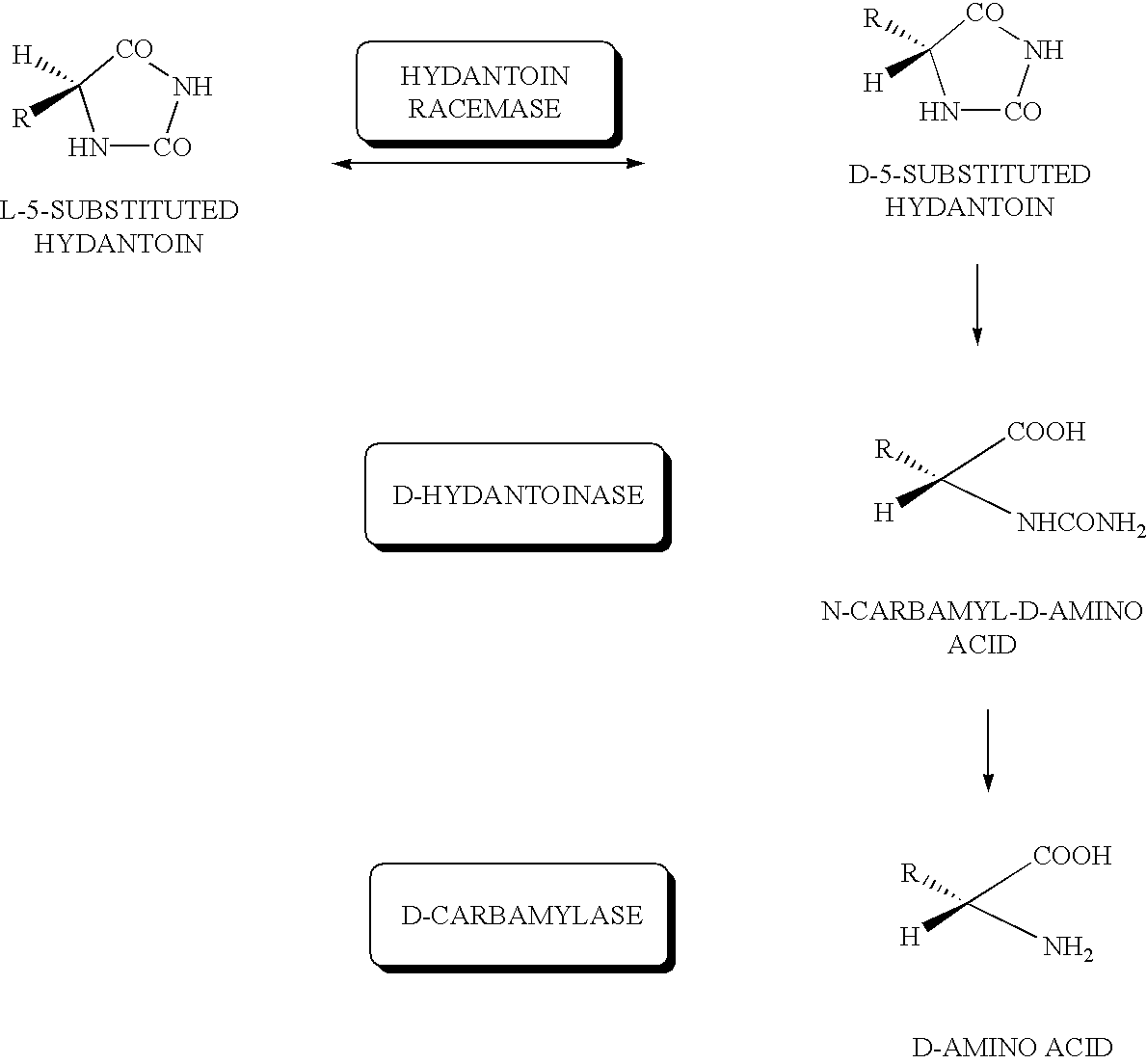
DNA for encoding D-hydantoin hydrolases, DNA for encoding N-carbamyl-D-amino acid hydrolases, recombinant DNA containing the genes, cells transformed with the recombinant DNA, methods for producing proteins utilizing the transformed cells and methods for producing D-amino acids
DNA for encoding a protein having D-hydantoinase activity which has a base sequence represented by Sequence ID No. 1 in the Sequence Listing. DNA for encoding a protein having D-carbamylase activity which has a base sequence represented by Sequence ID No. 3 in the Sequence Listing.
Owner:AJINOMOTO CO INC
Method and device for efficiently retransmitting packets in wired/wireless network
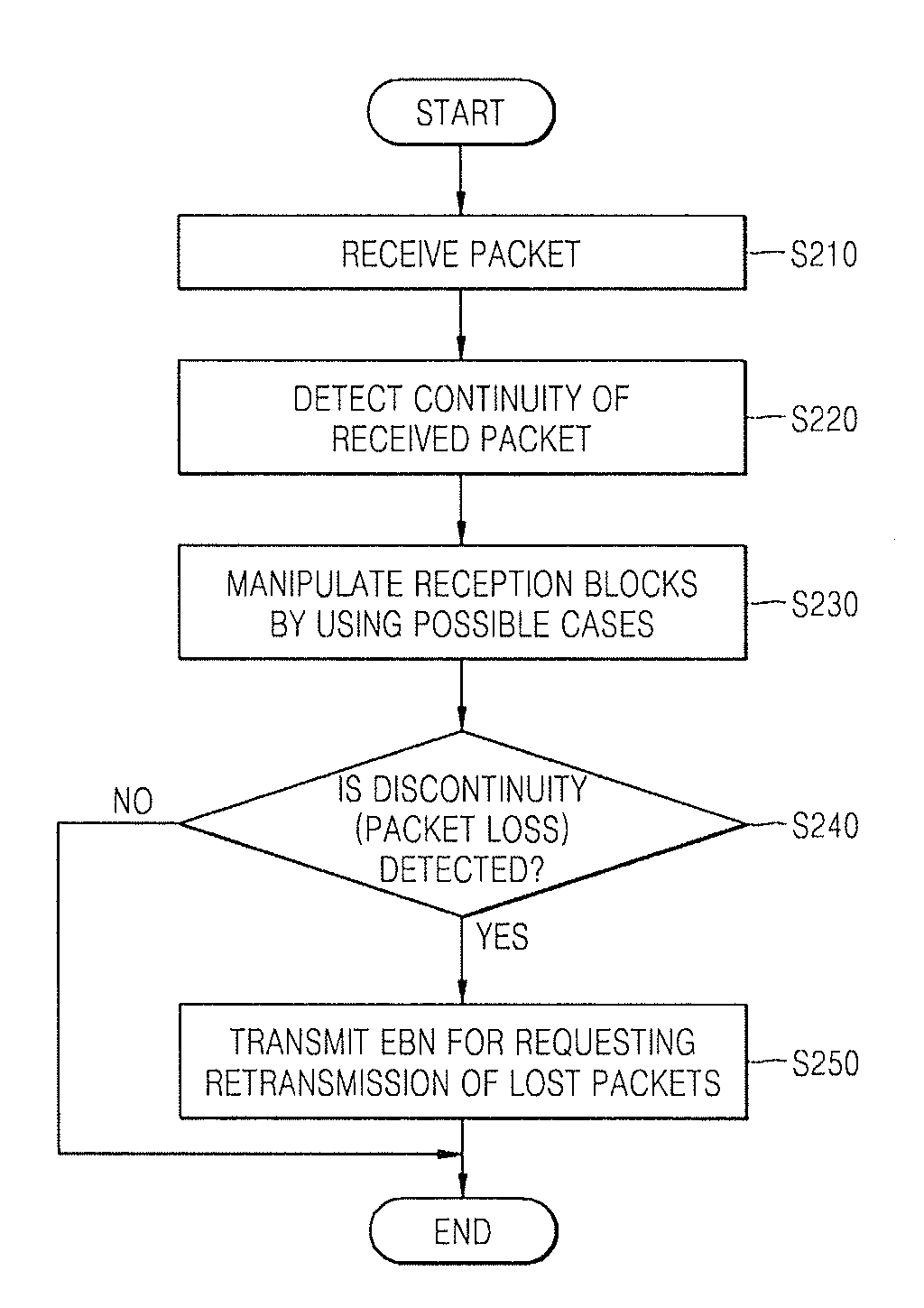
ActiveUS8042016B2Improve transfer rateReduce overheadError prevention/detection by using return channelTransmission systemsWireless mesh networkNetwork packet
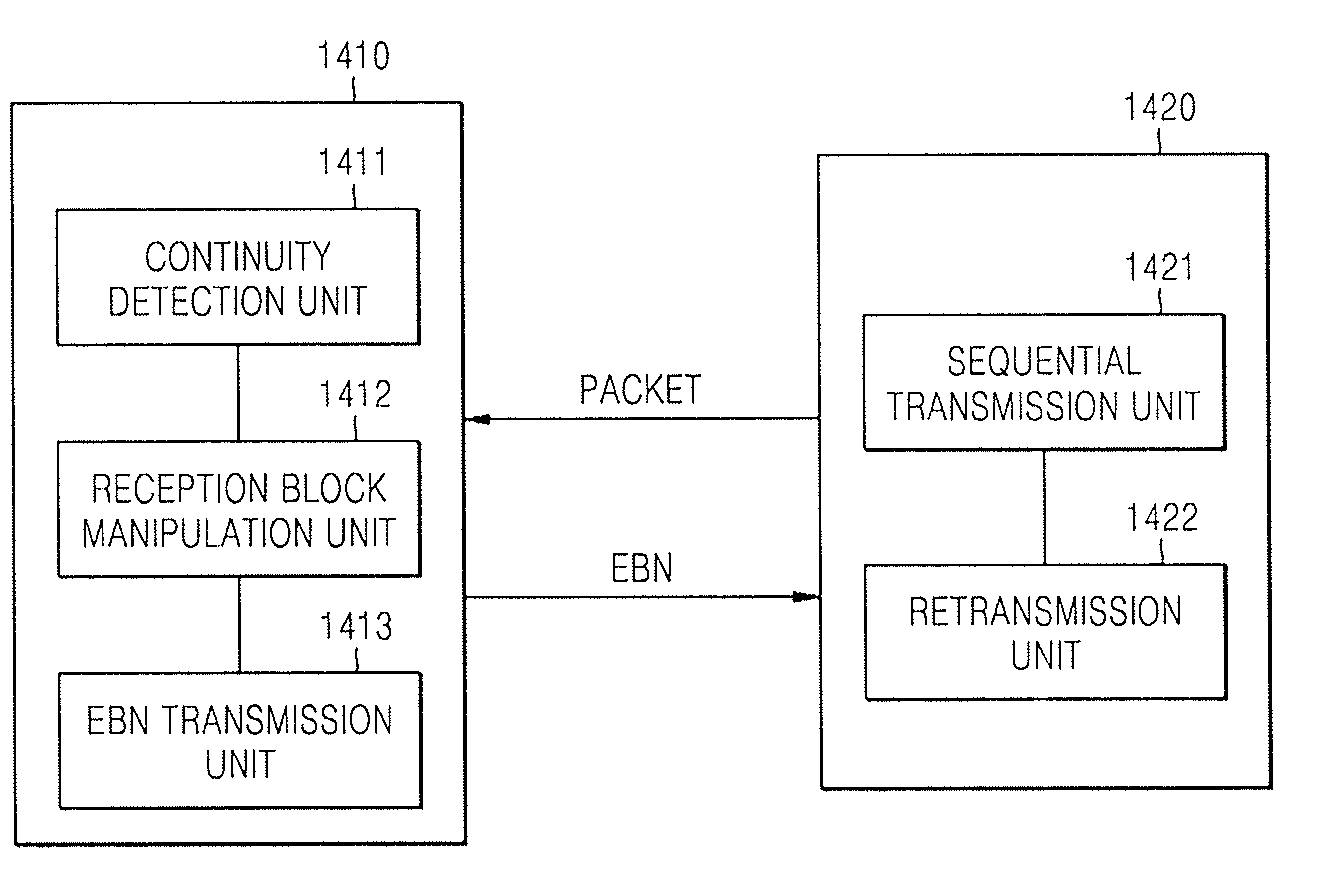
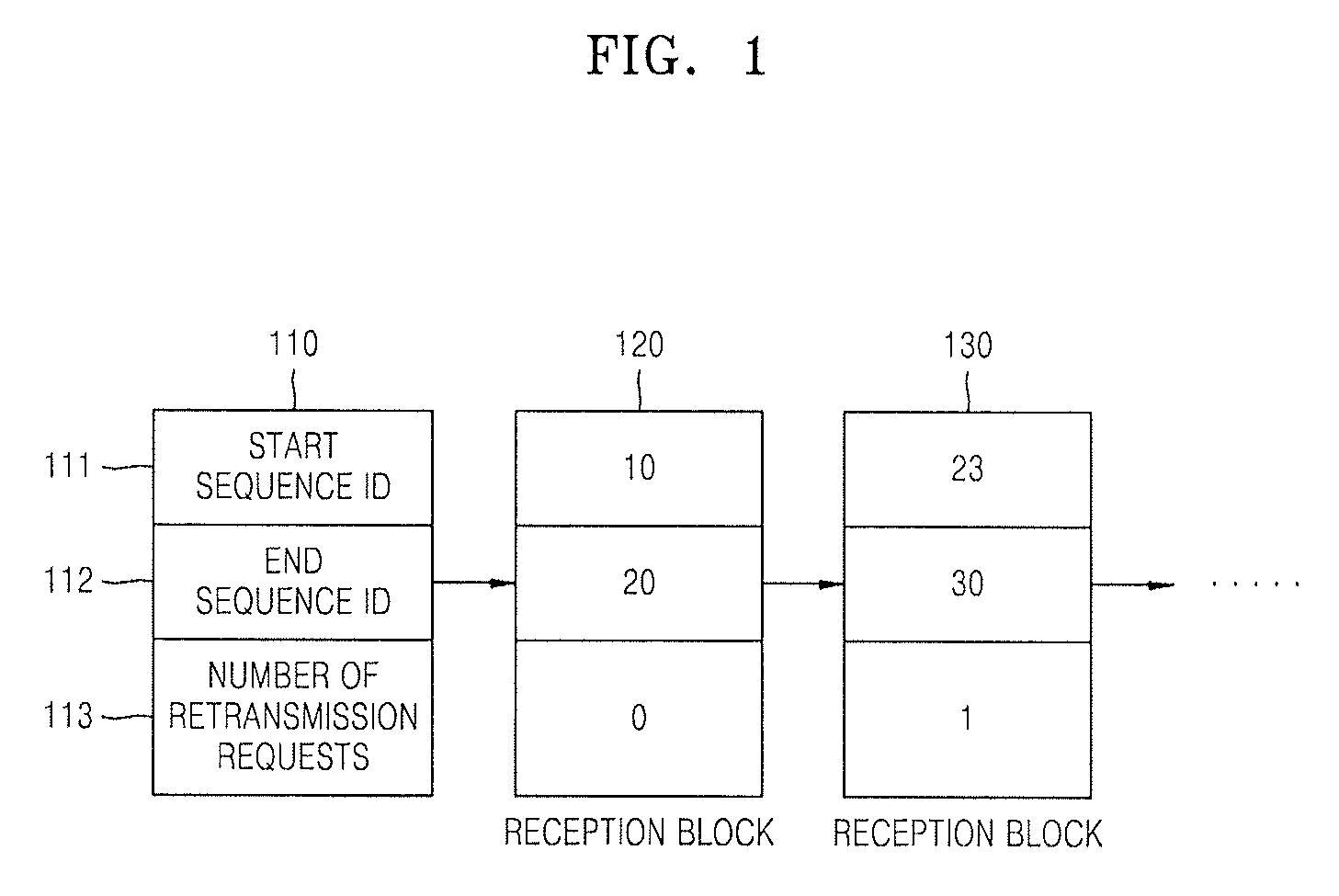
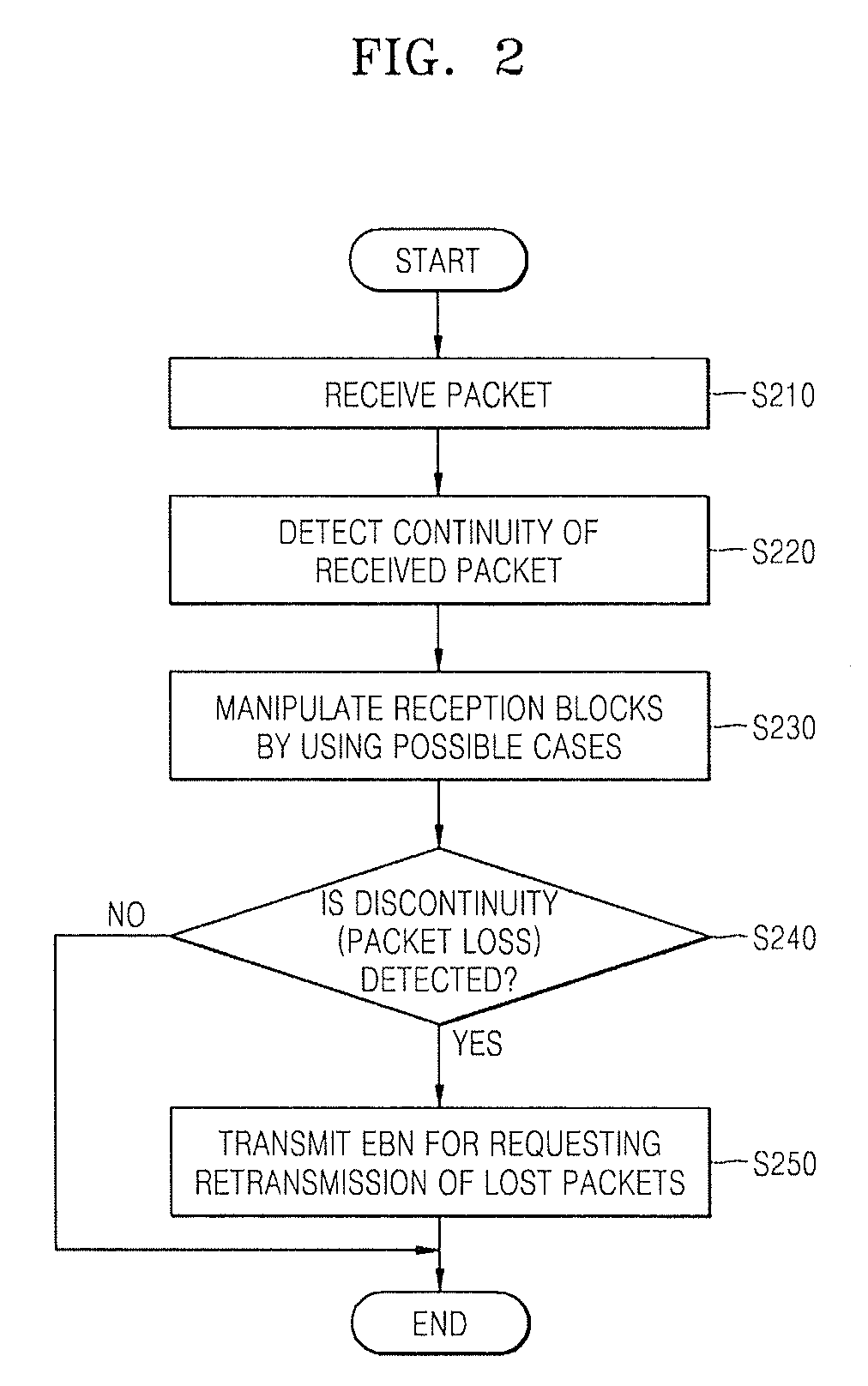
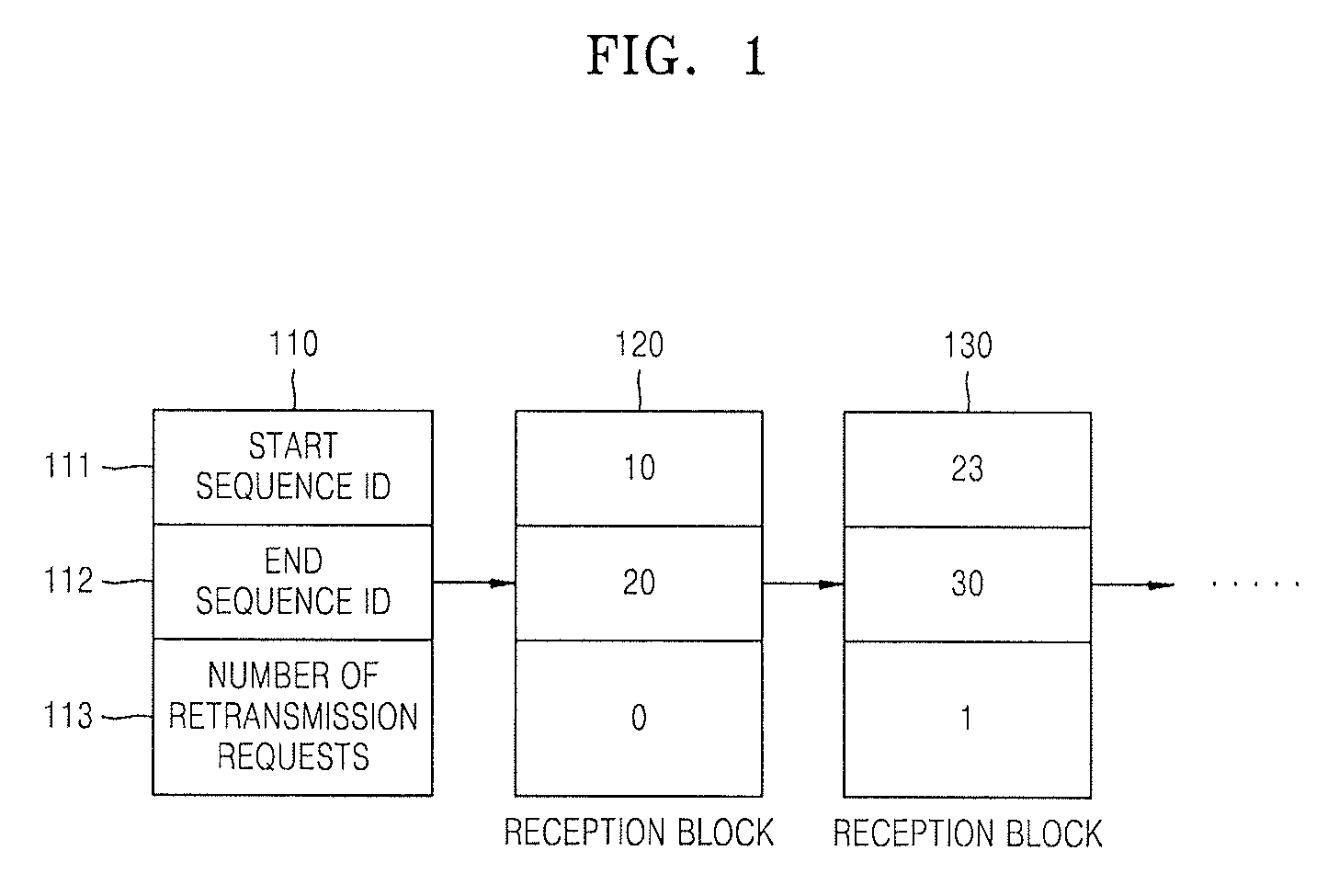
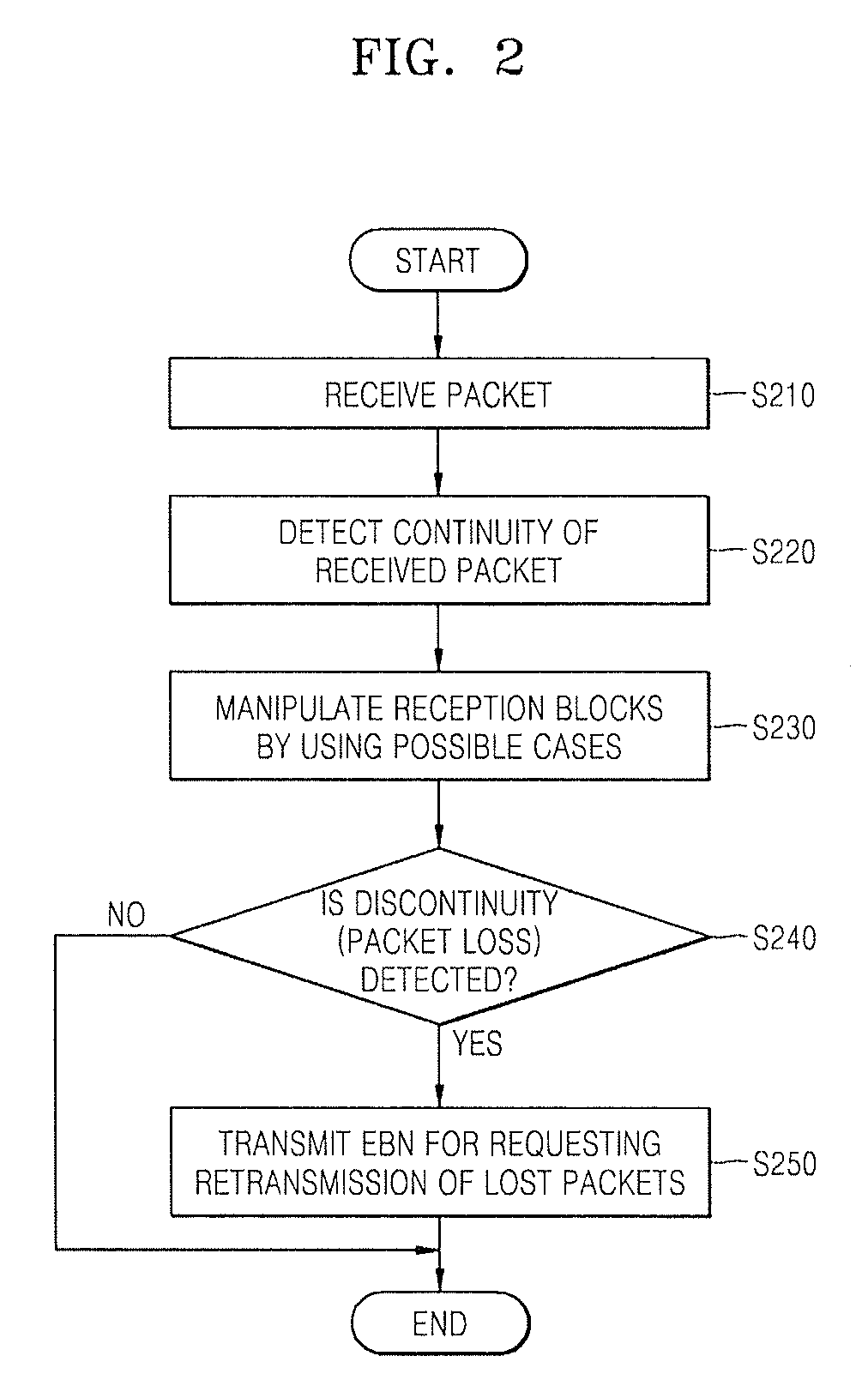
Provided a method and device for efficiently retransmitting packets of which transmissions failed in wired / wireless network including detecting continuity by detecting whether or not a sequence ID of a received packet is continuous with a start sequence ID or an end sequence ID of packets included in reception blocks which are generated in advance of the received packet; depending on the result of the detection, manipulating reception blocks to renew or delete the reception blocks or generate a new reception block by using the sequence ID of the received packet; and transmitting an EBN (Explicit Block NACK) for requesting retransmission of lost packets in units of a block when discontinuity is detected.
Owner:ELECTRONICS & TELECOMM RES INST
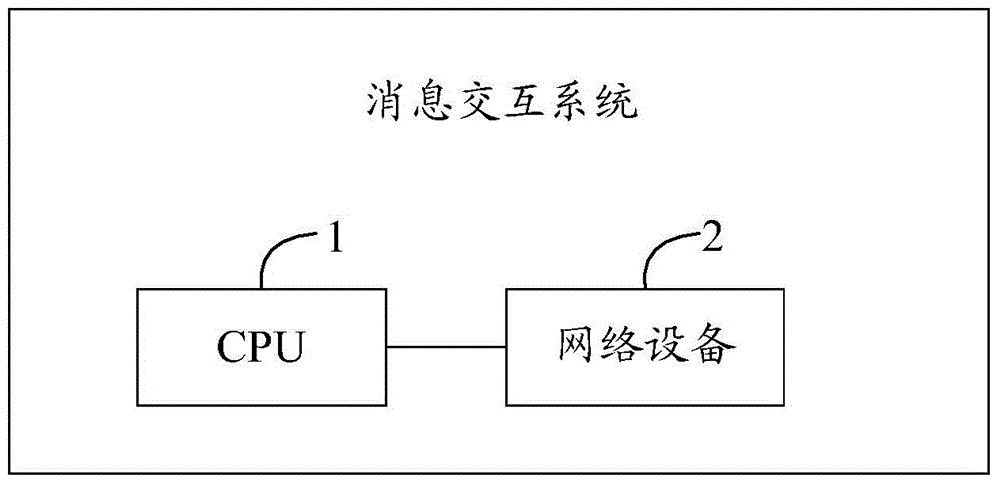
Method and system for message interaction between CPU and network equipment
ActiveCN105610730AMeet performance requirementsAvoid sending and receiving confusionData switching networksComputer hardwareSequence ID
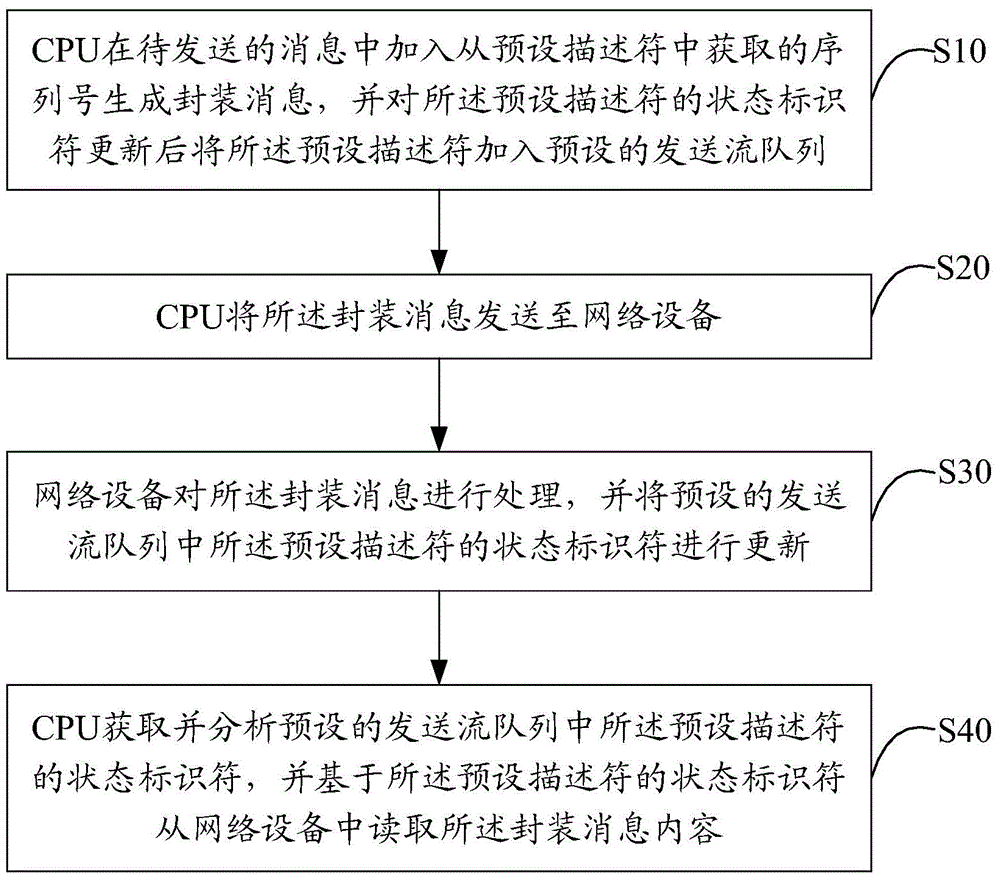
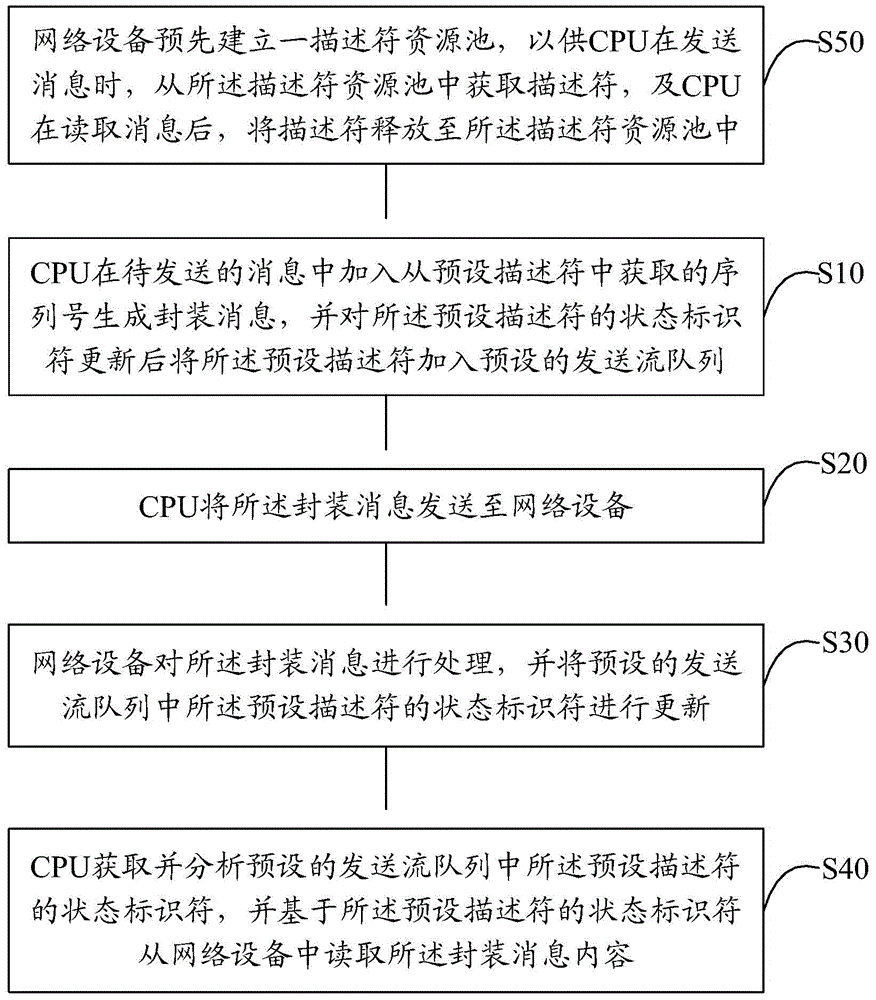
The invention discloses a method for message interaction between a CPU and network equipment, comprising the following steps: a CPU adds a sequence ID generation package message acquired from a preset descriptor to a message to be sent, and adds the preset descriptor to a preset sending flow queue after updating the state identifier of the preset descriptor; the CPU sends the package message to network equipment; the network equipment processes the package message, and updates the state identifier of the preset descriptor in the preset sending flow queue; and the CPU acquires and analyzes the state identifier of the preset descriptor in the preset sending flow queue, and reads the content of the package message from the network equipment based on the state identifier of the preset descriptor. The efficiency of message transmission is improved, and the performance requirement for interaction of a large number of messages between the CPU and the network equipment is satisfied.
Owner:ZTE CORP
EST-SSR primer group developed on basis of transcriptome sequences of hemarthria compressa and hemarthria altissima and application of EST-SSR primer group
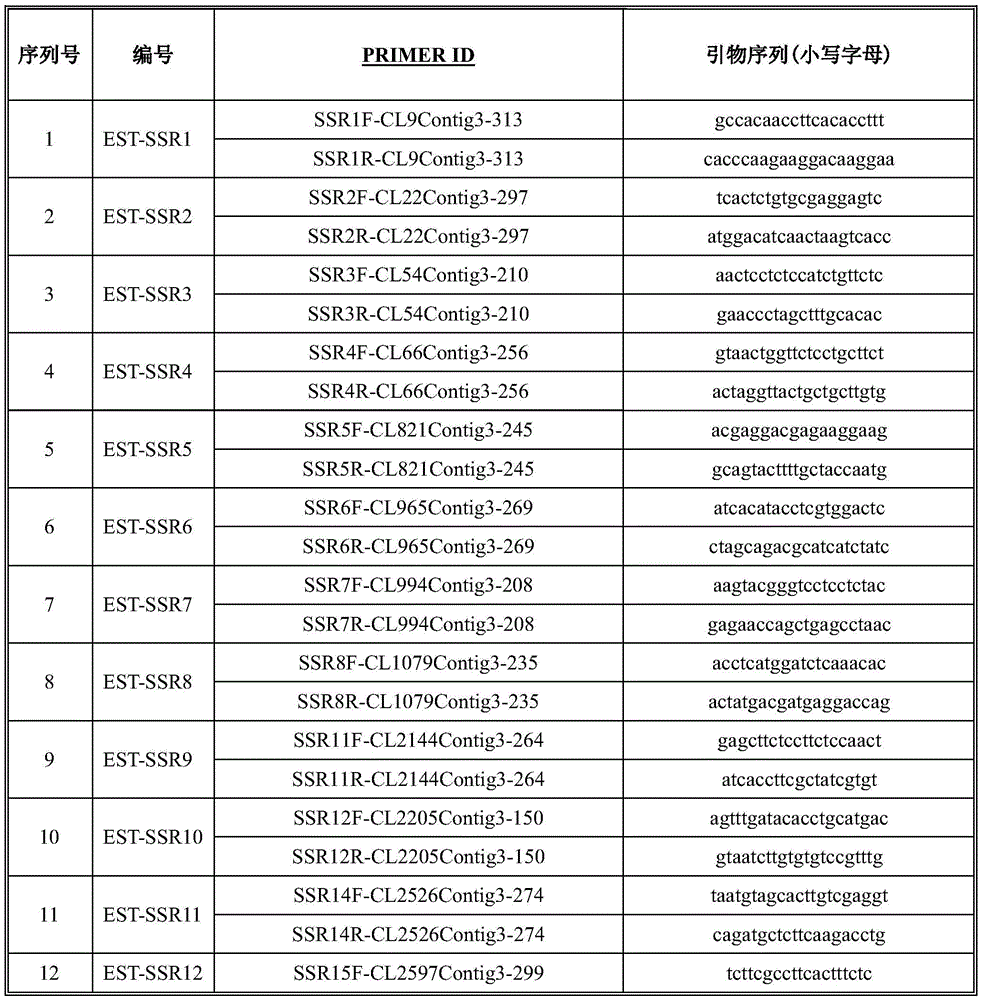
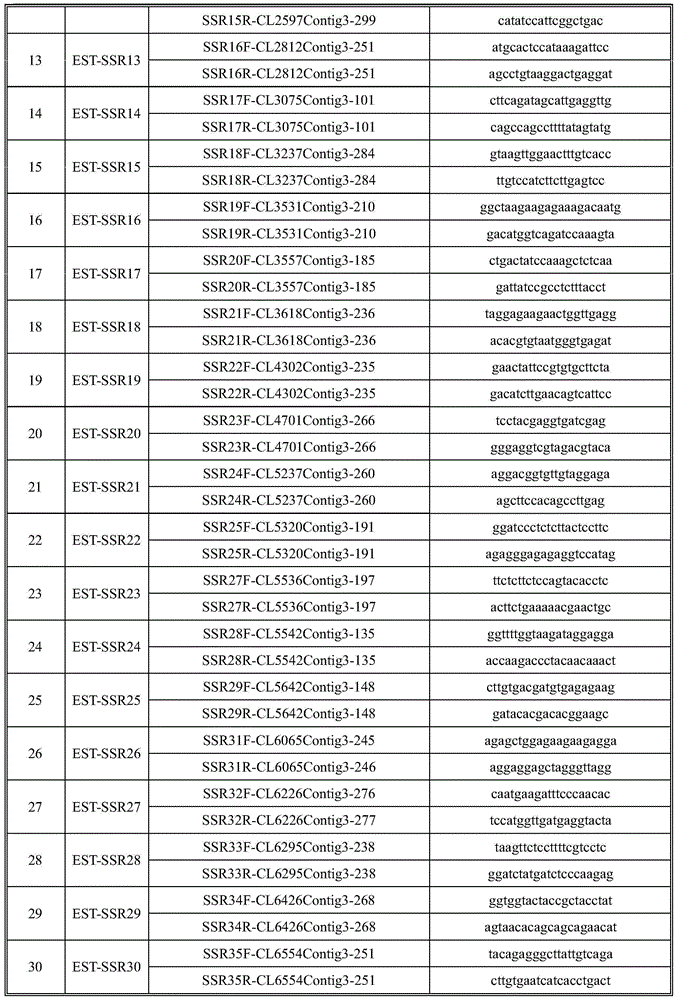
InactiveCN105586338AA large amountPolymorphism richMicrobiological testing/measurementDNA/RNA fragmentationGermplasmGenetics
The invention discloses an EST-SSR primer group developed on the basis of transcriptome sequences of hemarthria compressa and hemarthria altissima. The EST-SSR primer group comprises 52 pairs of primers, and nucleotide sequences of the primers are represented as sequence tables SEQUENCE ID NO.1-104. The invention further relates to an application of the EST-SSR labeled primers in the aspects of genetic diversity analysis of hemarthria sibirica and transferability of the hemarthria sibirica in gramineae species. The 52 pairs of primers in the EST-SSR primer group developed on the basis of the transcriptome sequences of hemarthria compressa and hemarthria altissima have the advantages of abundant polymorphism, stable amplification, good repeatability, convenience in counting and the like, can be effectively applied to research fields such as hemarthria sibirica germ resource genetic diversity analysis, variety identification, fingerprinting construction, molecular marker assisted breeding and the like and are applied to correlational research of other gramineae forage species.
Owner:SICHUAN AGRI UNIV +1
Identifier generation method, system and device based on distributed system and medium
PendingCN112199923AImprove production efficiencyAvoid duplicationNatural language data processingComputer networkSequence ID
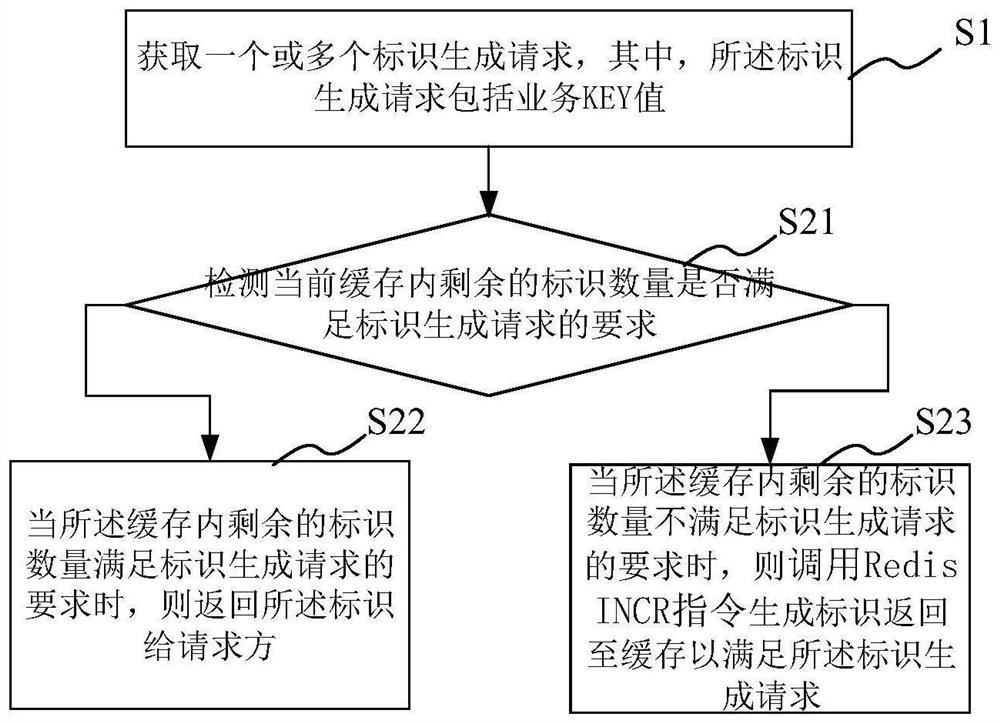
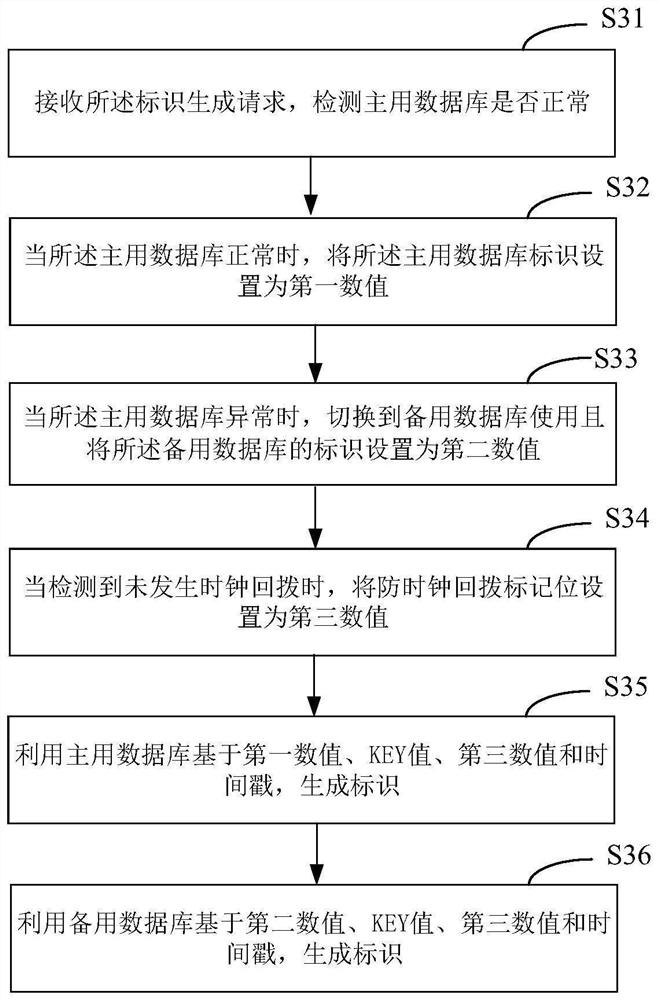
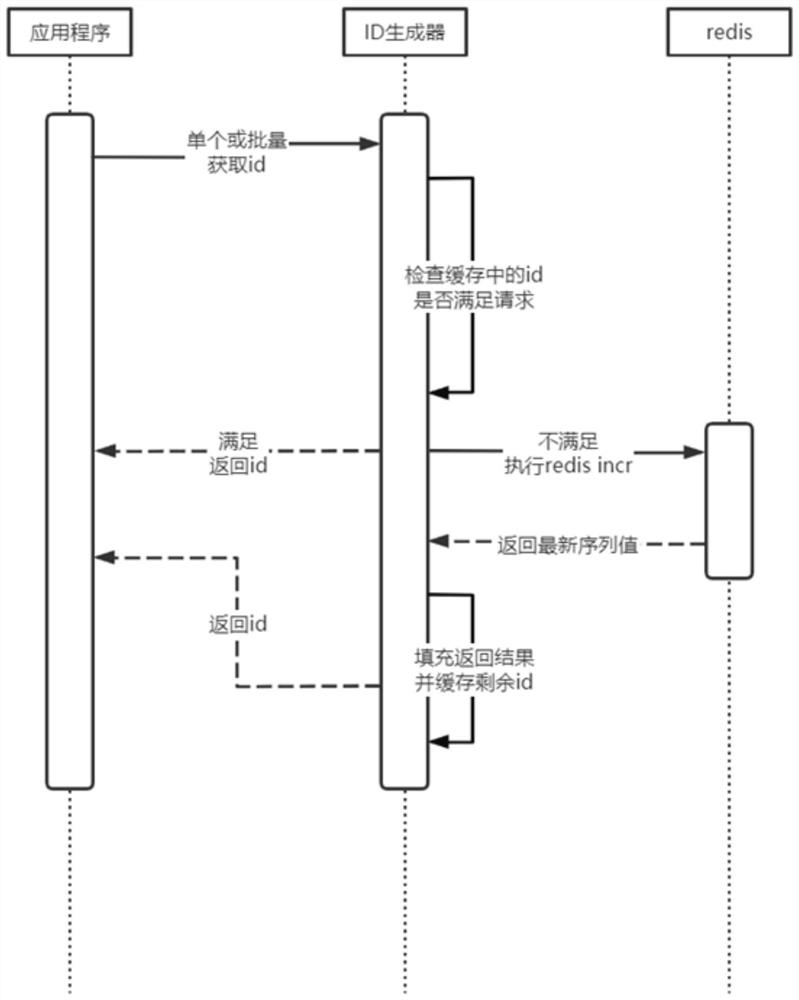
The invention provides an identifier generation method, system and device based on a distributed system and a medium, and the method comprises the steps: obtaining one or more identifier generation requests, and enabling the identifier generation requests to comprise a business KEY value; detecting whether the number of the remaining identifiers in the current cache meets the requirements of the identifier generation request or not; when the number of the remaining identifiers in the cache meets the requirement of an identifier generation request, returning the identifiers to a requester; whenthe number of the remaining identifiers in the cache does not meet the requirement of an identifier generation request, calling a Redis INCR instruction to generate an identifier, and returning the identifier to the cache to meet the identifier generation request; and obtaining the maximum value of the sequence by utilizing the Redis INCR, reversely calculating the initial values to be sequentially increased or decreased to generate identifiers, and determining the generation quantity of the identifiers according to the quantity of the remaining identifiers in the cache and the requirements of identifier generation requests. According to the invention, the identifier generation efficiency is improved; the ID repetition phenomenon is avoided through the sequence IDs generated in sequence,and subsequent capacity expansion is facilitated.
Owner:重庆紫光华山智安科技有限公司
Method for sequencing unknown flanking sequence at both sides of known sequence
ActiveCN103667481ALower quality requirementsAvoid mutationMicrobiological testing/measurementA-DNAInsertion sequence
A method for sequencing an unknown flanking sequence at both sides of a known sequence comprises library construction, flanking sequence capturing and sequencing. The method comprises: employing a site directed mutagenesis PCR process, designing an appropriate primer on the known sequence (without mutation sites), taking the constructed library as the template, screening numerous plasmids in the library to obtain a DNA fragment containing the known sequence sites, screening out target sites in the plasmid library by employing the PCR process, and further obtaining an insertion sequence 2 Kb-5 Kb and a plasmid library containing the known sequence, and taking the plasmid library as the target point to obtain the flanking sequence at the both sides of the known sequence. The provided sequencing method helps to realize full view acquisition of genome, helps to solve the technological restriction that researchers cannot describe the full view of a gene and consequently cannot precisely research the functions of the gene when carrying out comprehensive research on the gene, and is beneficial to improve the efficiency of related researches.
Owner:重庆巴斯德生物医药科技有限公司
Scanning and integration verification comparison method for encrypted product
InactiveCN106528208AMeet high-volume testing requirementsReduce work stationsElectronic circuit testingCo-operative working arrangementsSequence IDByte
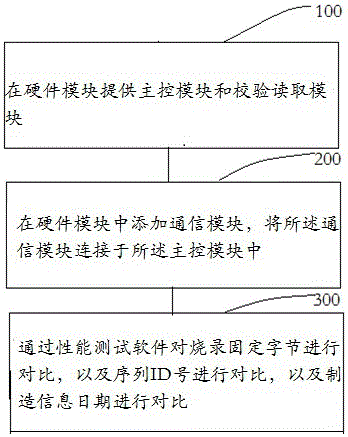
The present invention provides a scanning and integration verification comparison method for an encrypted product. The method is characterized by comprising: providing a main control module and a calibration reading module in a hardware module; adding a communication module in the hardware module, and connecting the communication module into the main control module; and comparing burning fixed bytes, sequence ID numbers and manufacturing information dates by means of performance test software. Our company realizes a burning verification performance test scheme for BQ2022A series encrypted IC products, which adopts a 20 channel parallel burning calibration-verification integrated test method and a 20 channel performance complex verification test method. The current device test scheme saves stations for complex verification, and integrates a function of complex verification into device performance tests.
Owner:HUIZHOU BLUEWAY ELECTRONICS
Face recognition method based on central point tracking model
ActiveCN112541434AImprove recognition accuracyReduce the probability of tracking errorsCharacter and pattern recognitionMachine visionSequence ID
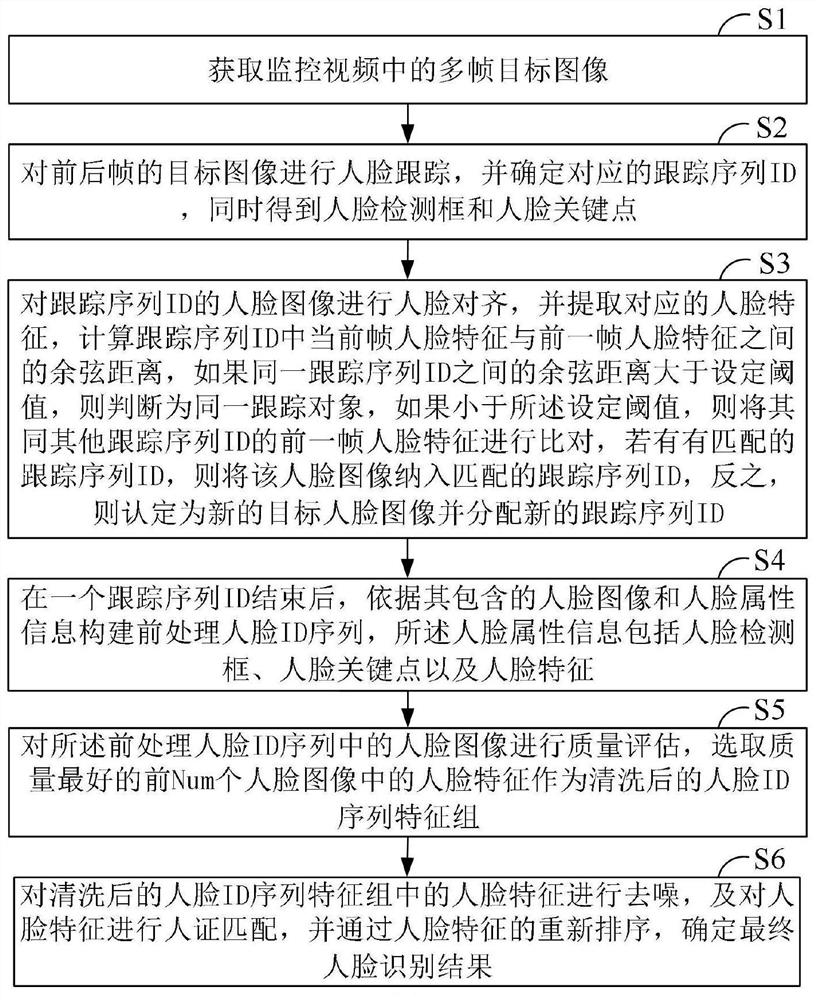
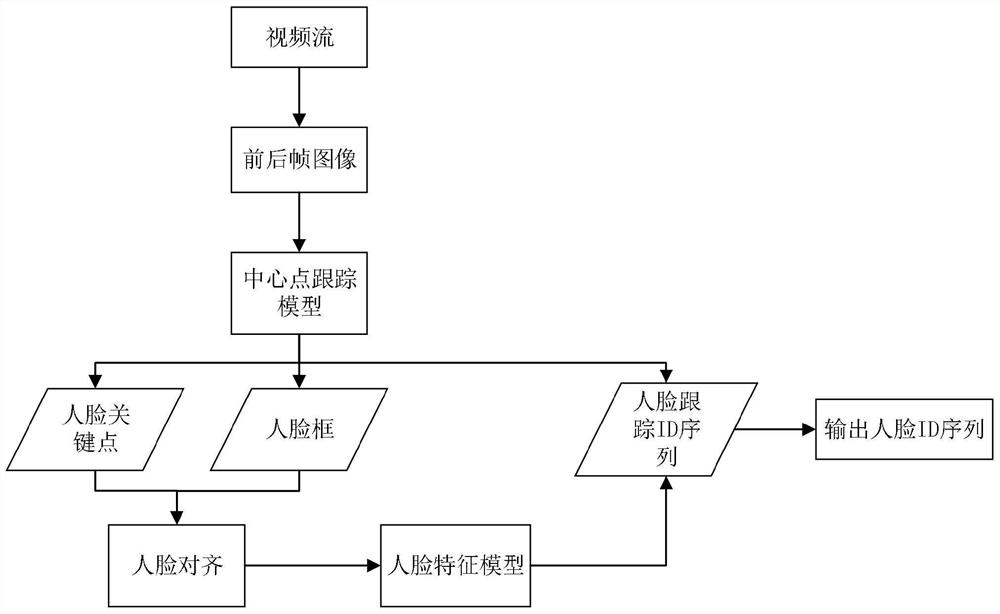
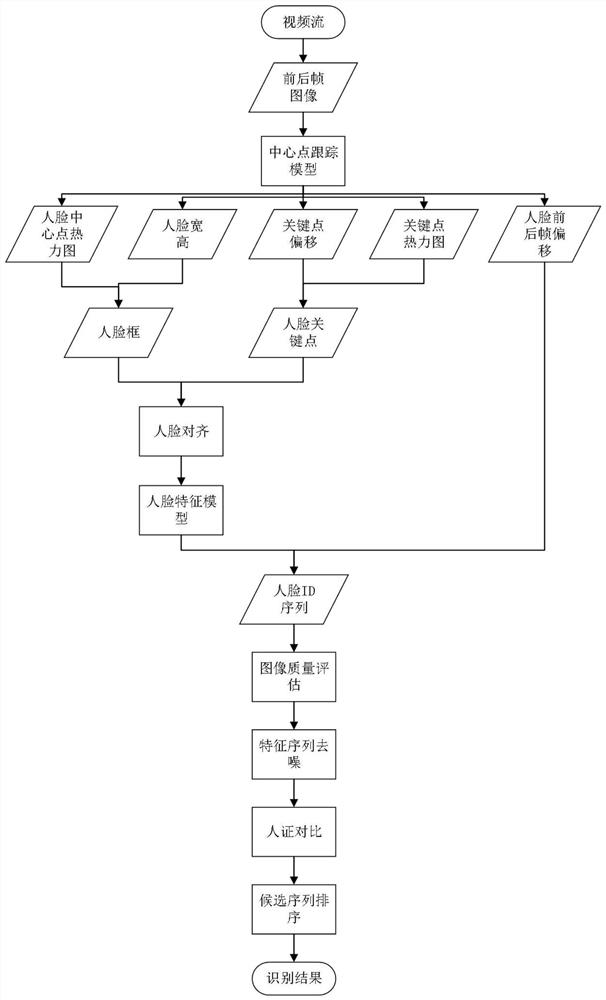
The invention relates to the technical field of machine vision, and specifically discloses a face recognition method based on a central point tracking model, and the method comprises the steps: obtaining a plurality of frames of target images; performing face tracking on the target images of the front and back frames, and determining a corresponding tracking sequence ID; performing face alignmenton the face image of the tracking sequence ID, and extracting corresponding face features; after one tracking sequence ID is finished, constructing a pre-processing face ID sequence; performing quality evaluation on the face images in the pre-processed face ID sequence, and selecting face features in the first Num face images with the best quality as a cleaned face ID sequence feature group; and denoising face features in the face ID sequence feature group, and determining a final face recognition result through reordering of the face features. According to the method, the influence of factorssuch as illumination, pedestrian flow shielding and face angles on the face recognition effect in a dynamic video environment can be reduced, and the face recognition precision is improved.
Owner:无锡锡商银行股份有限公司
Spatial-contiguity-considered vector space data coding method
ActiveCN106649425AConsider spatial proximityAvoid repetitionSpecial data processing applicationsPoint objectHyperrectangle
The invention discloses a spatial-contiguity-considered vector space data coding method. The spatial-contiguity-considered vector space data coding method includes the steps that whether a given object P is a point object or not is judged; if the space object P is a non-point object, the maximum order k where a grid capable of completely containing a minimum external-containing hyperrectangle is obtained through calculation, and then k+1 pieces of ZG(P)<j*> from the zero order to the k order are calculated, wherein ZG(P)<j*> represents the coded value of the space object P in the j* order; the k+1 pieces of ZG(P)<j*> are coded according to the coding rule of a space filling curve, and Geocode(f.geometry)* is obtained; then coding is carried out according to the formula that Rowkey(f)* is equal to the sum of Geocode(f.geometry)* and FID(f)*. Based on the layered coding of the space filling curve, in the same space division, different space objects have same prefix codes, then unique sequence ID values are added to serve as postfix codes, the space proximity of the vector space objects is considered, and Rowkey can also be prevented from being repeated. In this way, Rowkey has the features of a spatial index, and direct spatial querying in a database becomes possible.
Owner:武汉兆图科技有限公司
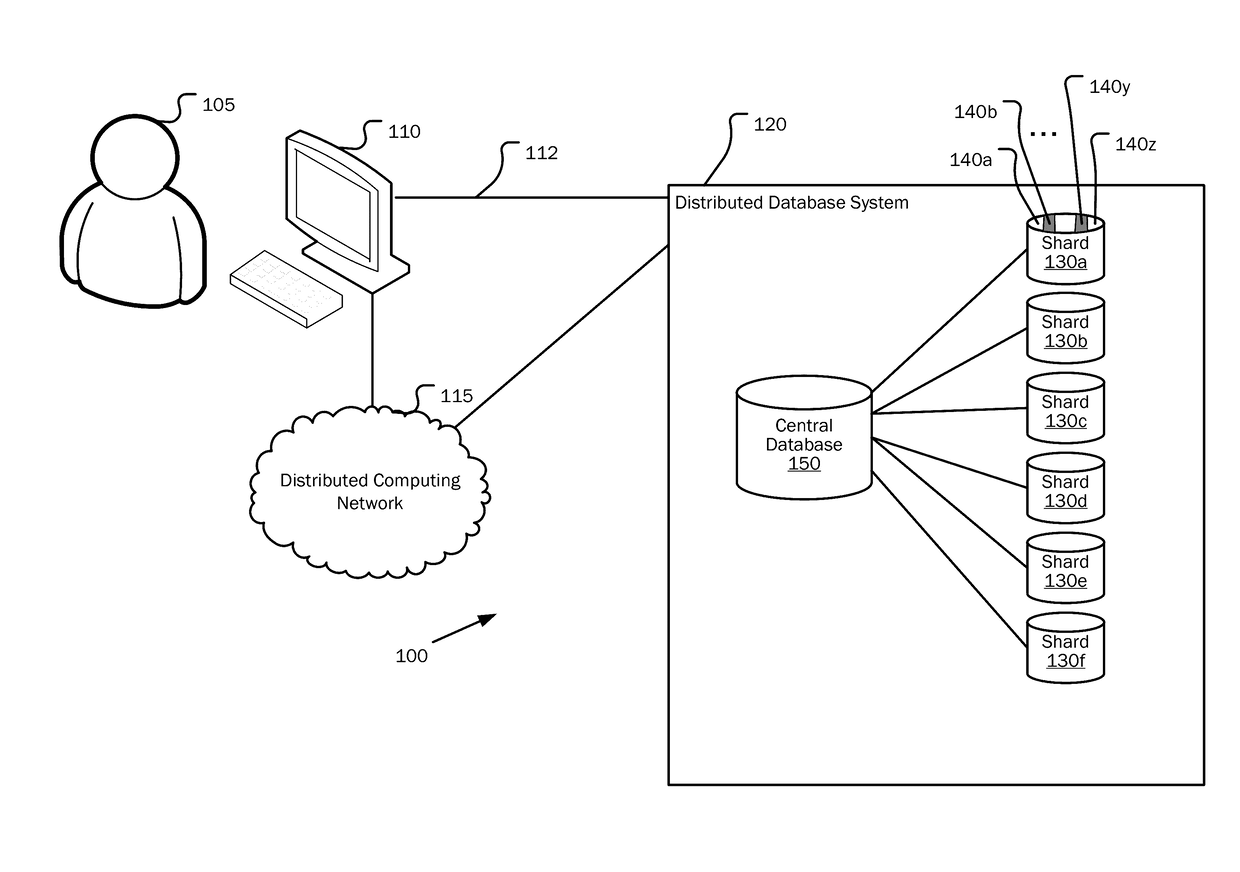
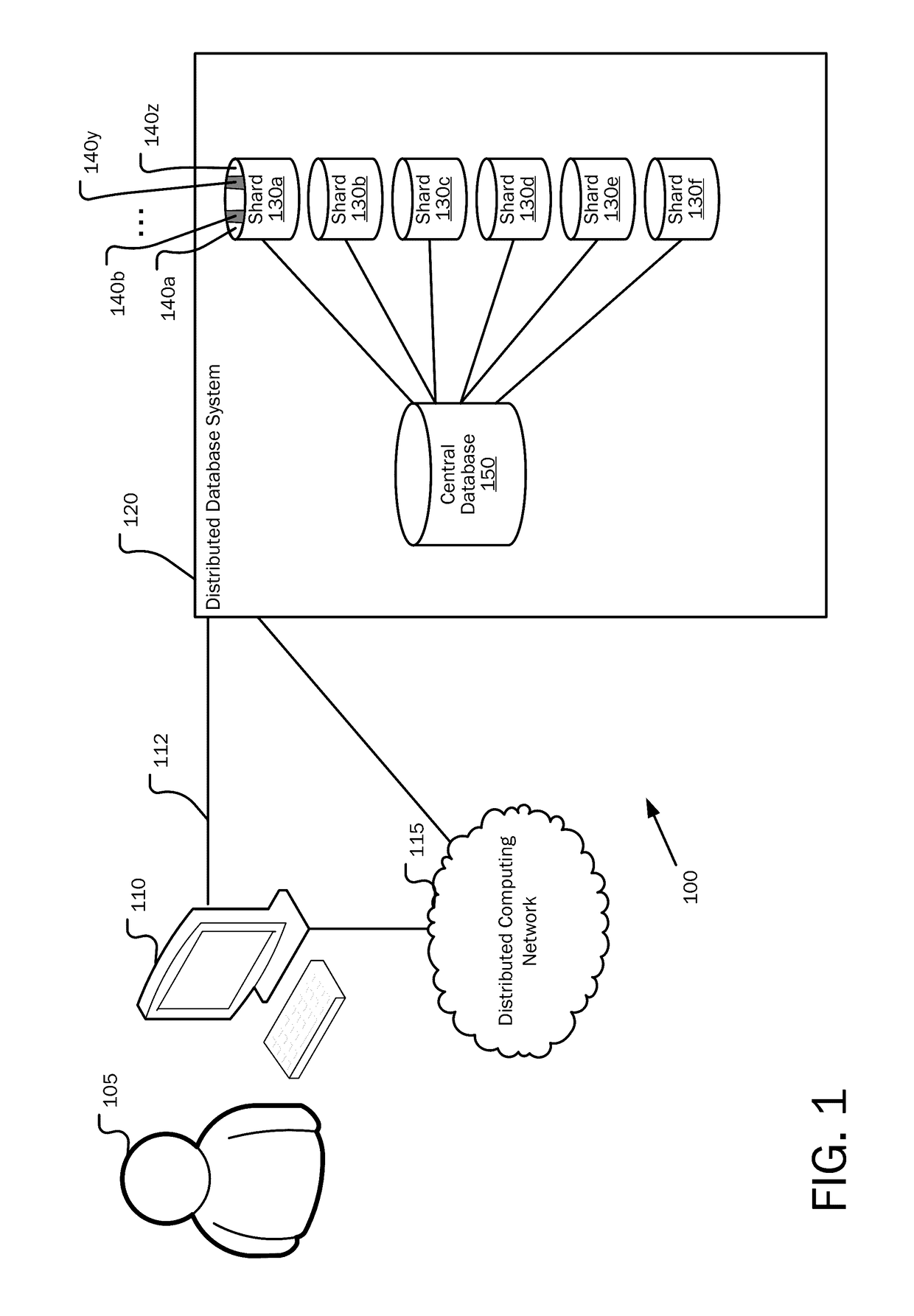
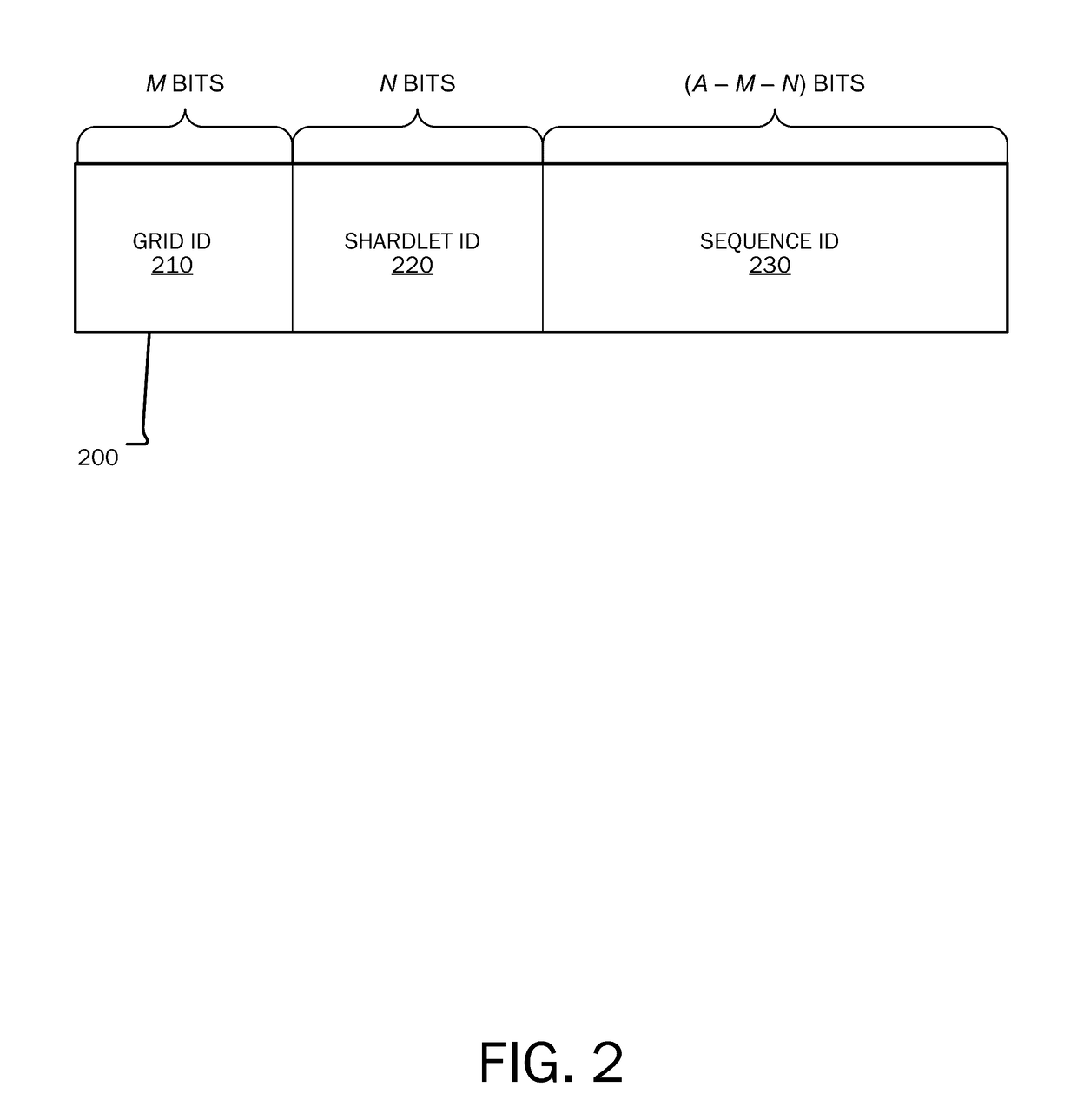
Partitioning of geographic data
Improving the efficiency of distributed database systems in providing geographically related information is provided by generating a data object identifier (ID) in association with geographical data. A geographical data object is received for storage in the distributed database system. A grid ID is generated based on spatial information contained in the geographical data object, a shardlet ID is generated indicating a shardlet location in a given shard on which the geographical data object is stored, and a sequence ID is generated indicating data placement within the shardlet location. The data object ID is assigned to the geographical data object, the data object ID comprising the grid ID, the shardlet ID, and the sequence ID.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com