Processing method supporting calling of various safety devices
A security device and processing method technology, applied in the processing field that supports calling multiple security devices, can solve the problems of different API interfaces, functions and algorithms of security service providers, etc., and achieve the effect of large scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
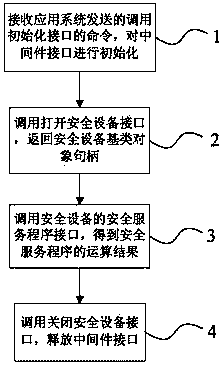
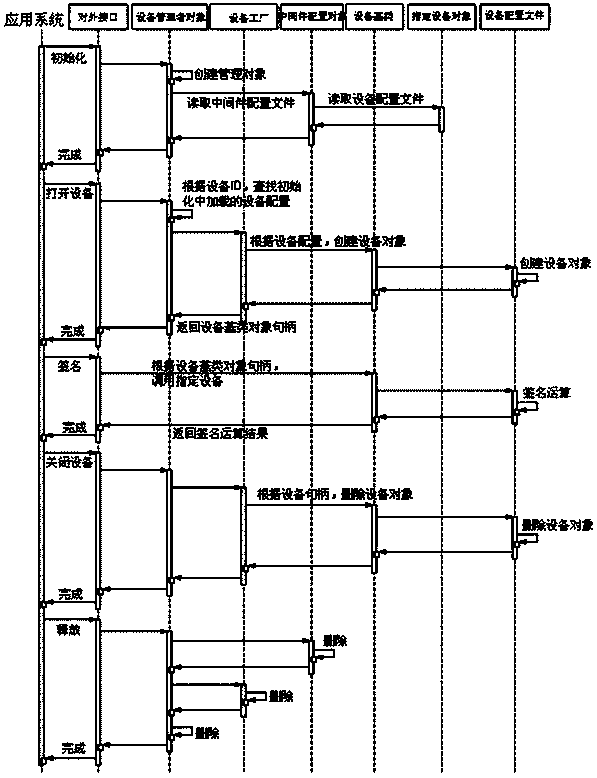
[0032] A processing method that supports invoking multiple security devices is used in the connection and communication between a device (such as a computer) installed with an application program and the security device. In principle, the method of the present invention adopts the factory model, and abstracts the functions of security equipment to obtain the equipment base class. The security equipment inherits from the equipment base class. The equipment worker configures the production equipment according to the algorithm, and the manager manages the factory production according to the middleware configuration. The flow chart and sequence diagram of this method are as follows figure 1 , figure 2 As shown, it specifically includes the following steps:
[0033] Step 1. Receive the command to call the initialization interface sent by the application system, and initialize the middleware interface.
[0034] In this step, the process of initializing the middleware interface is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com