Domainname-based unified identification mark and authentication method
A technology of identity authentication and authentication method, which is applied in the directions of user identity/authority verification, transmission system, digital transmission system, etc. It can solve problems such as interoperability difficulties, host mobile characteristics, protocol encryption characteristics, complex problems, and the inability to quickly determine the person in charge, etc. achieve good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
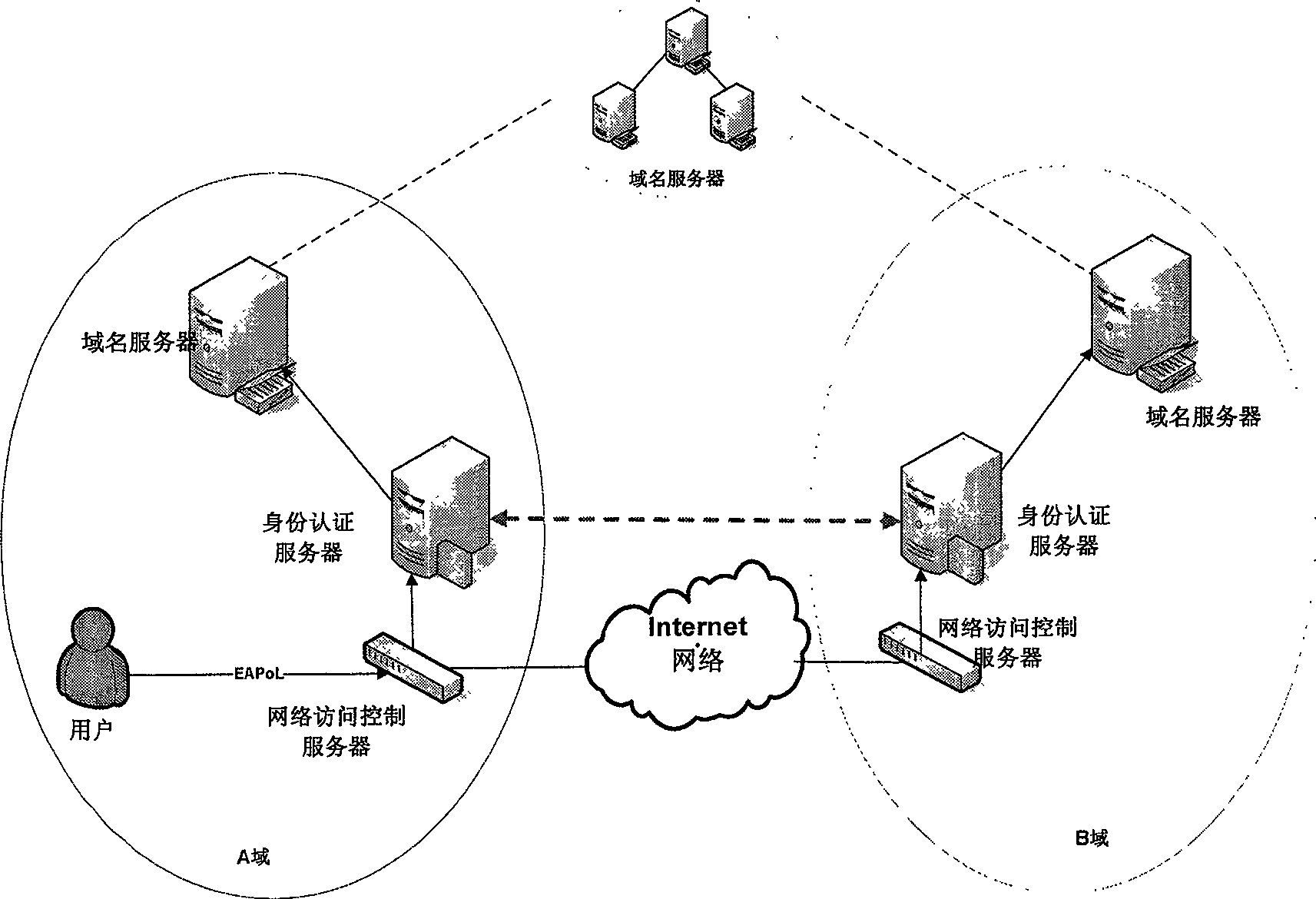
[0064] System structure such as figure 1 Shown: Two administrative domains A and B are shown. Each of these domains contains:
[0065] ● Identity authentication server;
[0066] ●Network access control server;
[0067] ●Domain name server.
[0068] ID
[0069] Aiming at the difficulty of memorizing and managing IPv6 addresses in the next generation Internet and various problems existing in the existing identity identification mechanism, the present invention proposes to use personal domain names to identify users.
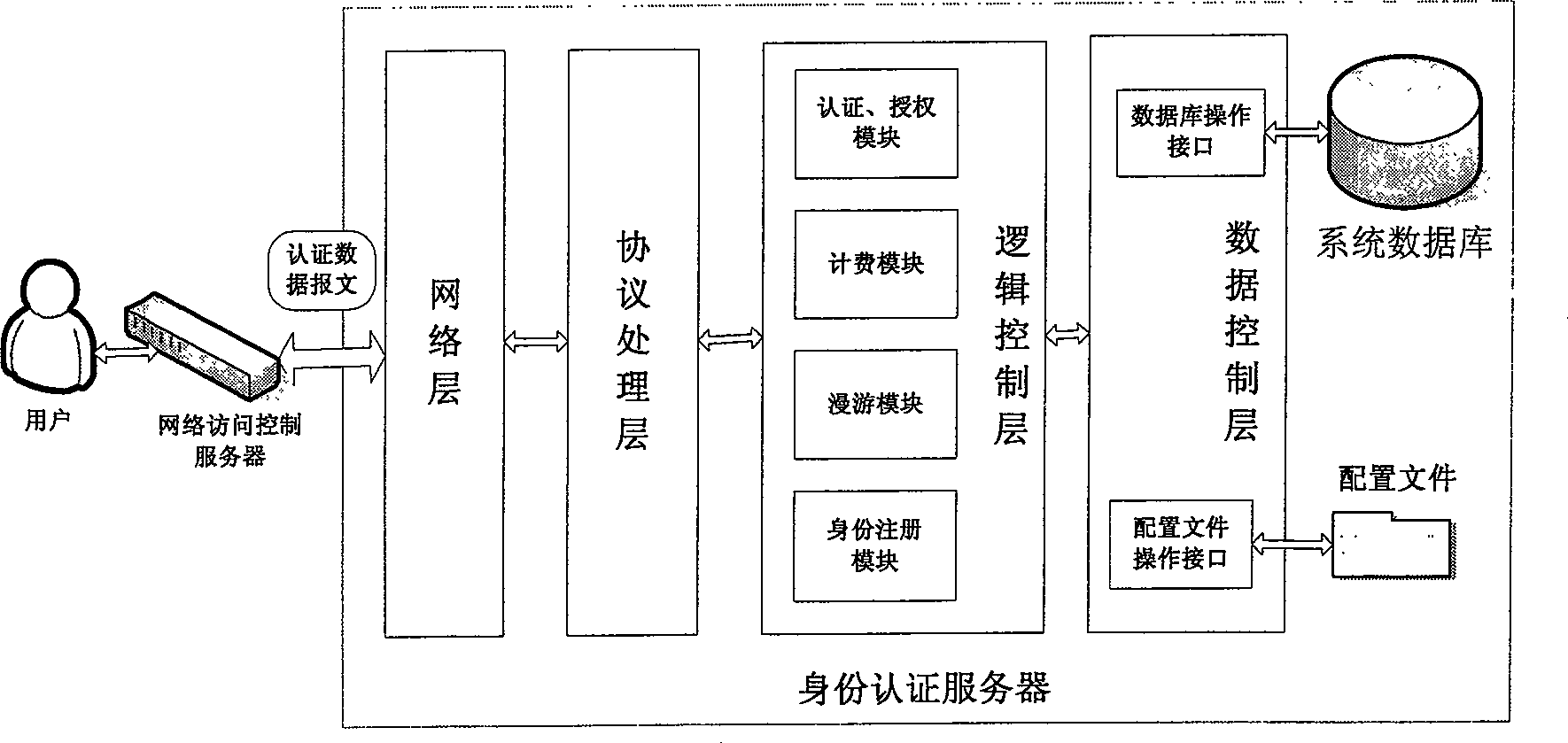
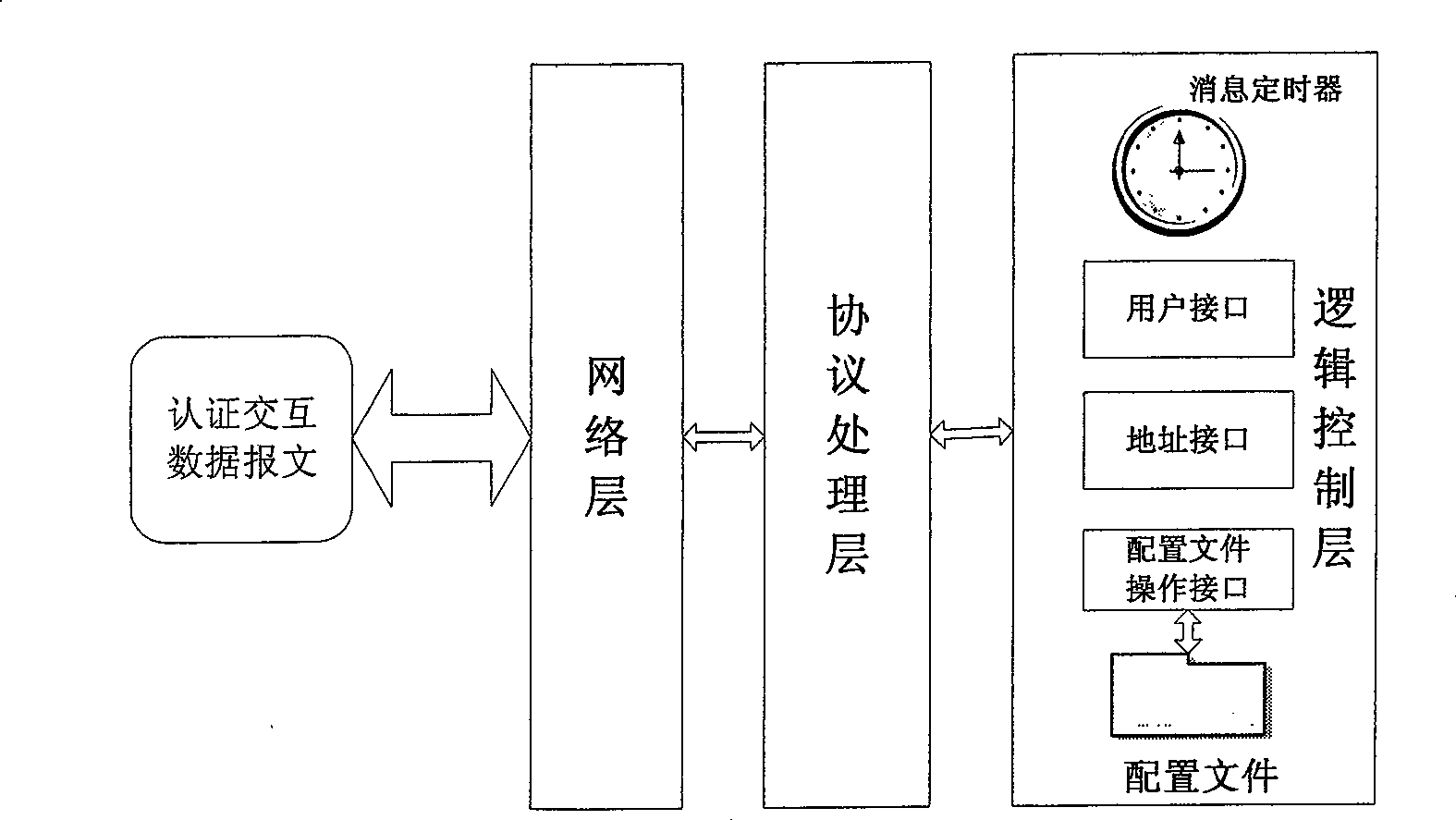
[0070] Personal domain name PDN refers to a network-wide unique identity assigned to a user, which corresponds to the user's current IPv6 address and is used to address the user. A personal domain name takes the form of Username@Domainname similar to an email address, meaning that the user belongs to an administrative domain. After the user has successfully authenticated, the identity authentication server will register the corresponding relationship between ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com