Secure web page tag library system supported by multiple strategies
A security label, multi-policy technology, applied in instruments, computing, electrical digital data processing, etc., can solve the problems of no control-level fine-grained access control, lack of policy integration support, inability to meet security levels, etc., to achieve reusability Strong, flexible authentication method, convenient secondary development effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
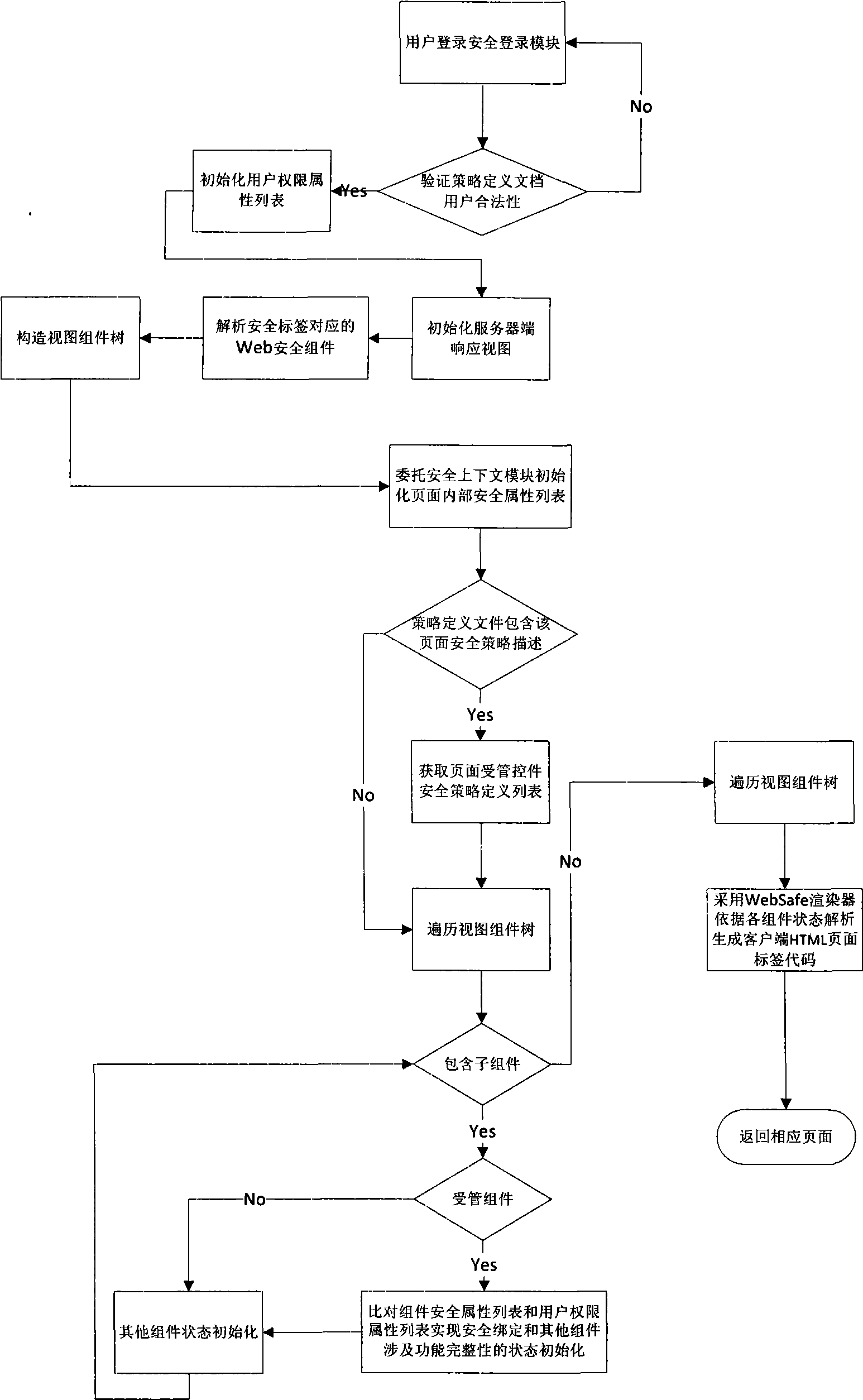
[0033] Below in conjunction with accompanying drawing and example the present invention is described in further detail.
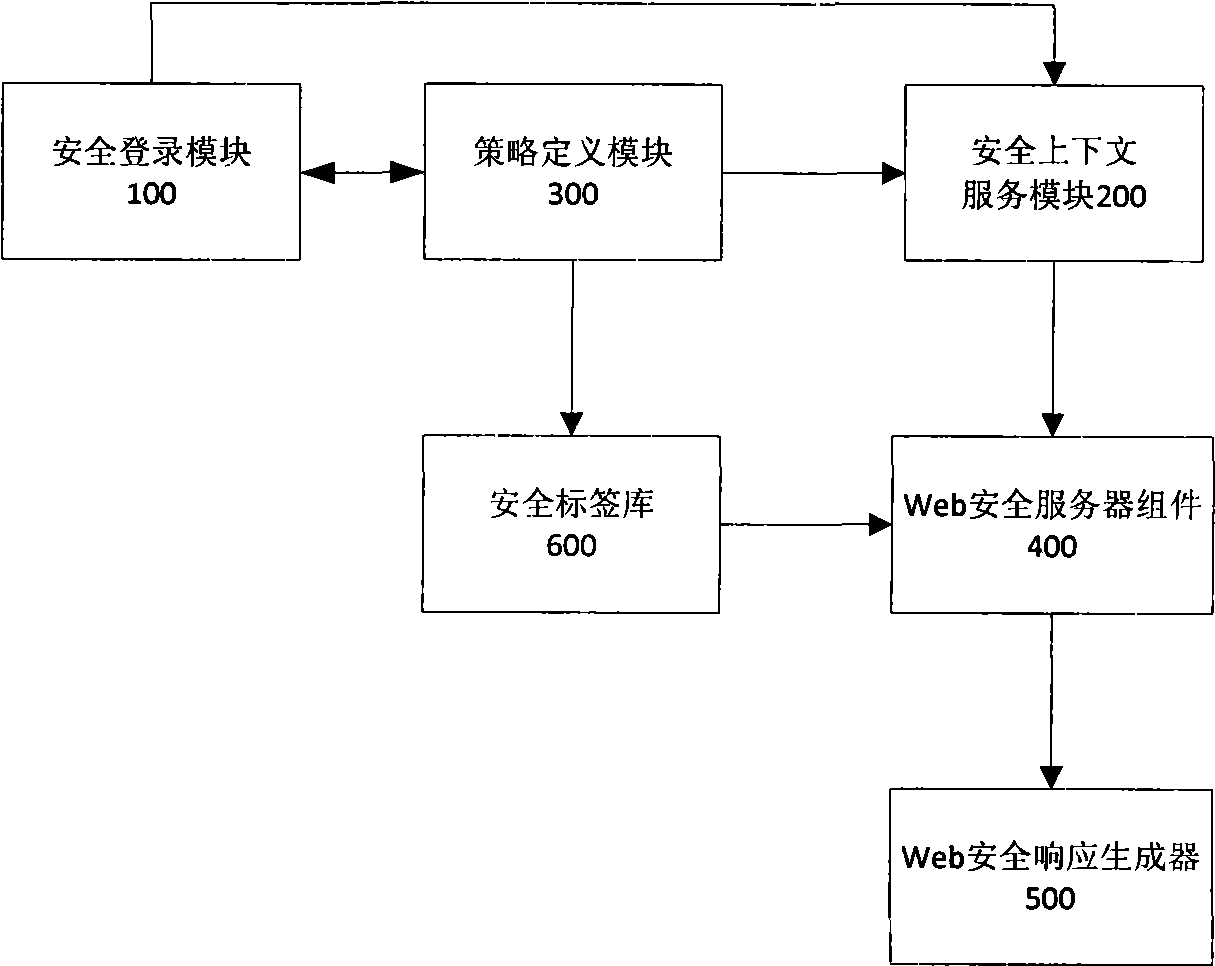
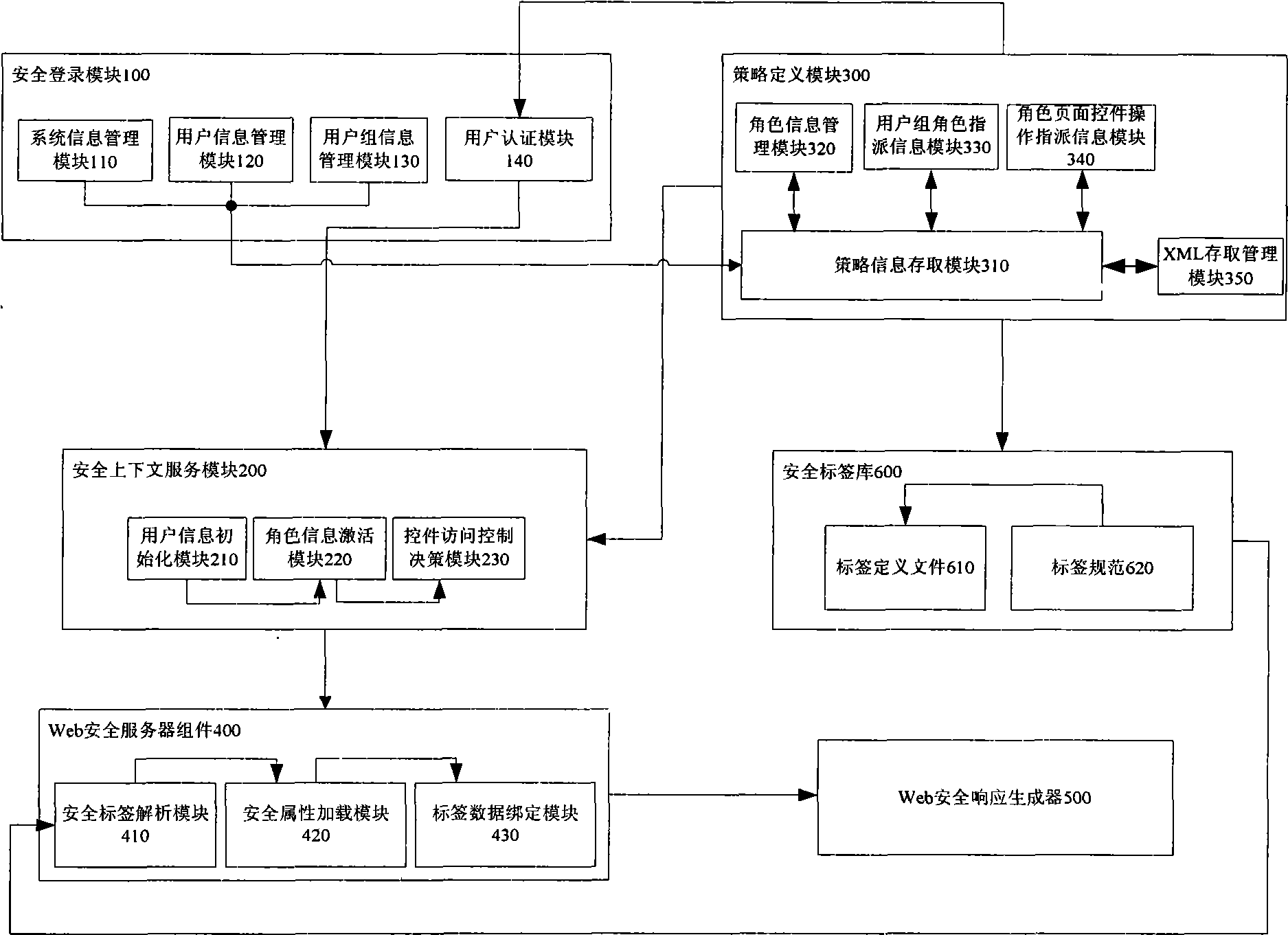
[0034] Such as figure 1As shown, the secure Java Web application page label library system that provides multi-policy support provided by the present invention includes a secure login module 100, a security context service module 200, a policy definition module 300, a Web security server component 400, a Web security response generator 500 and Security tag library 600 .
[0035] The security tag library 600 defines a set of security tags that can be imported in various Java Web pages. By directly defining the security components corresponding to the tag library in the page, developers can quickly and intuitively develop security components that meet various practical engineering requirements. The required web application module, and by setting the unique security ID of each security label in the policy document, can easily define various security rules bas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com