Patents
Literature
57 results about "CA protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
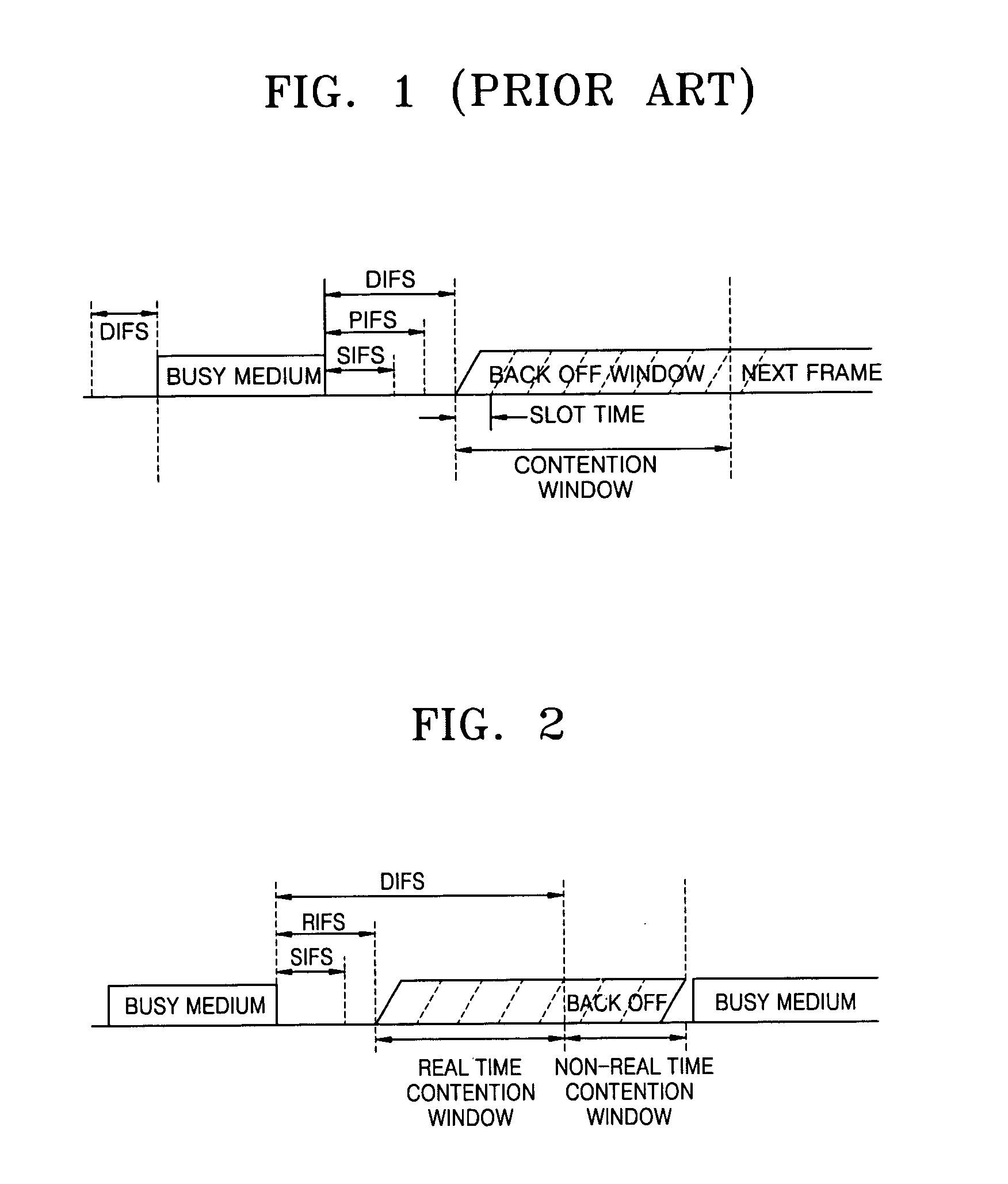
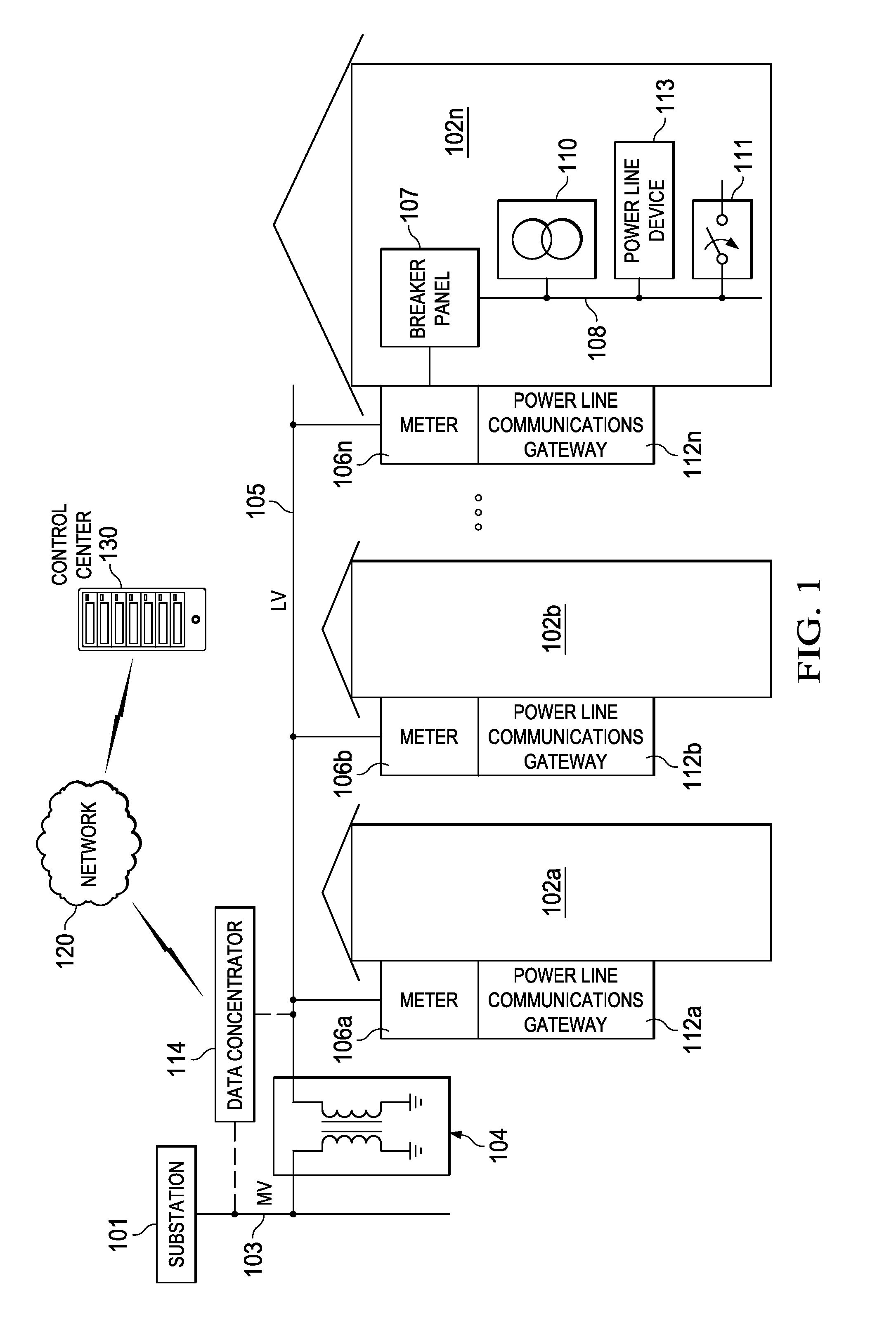
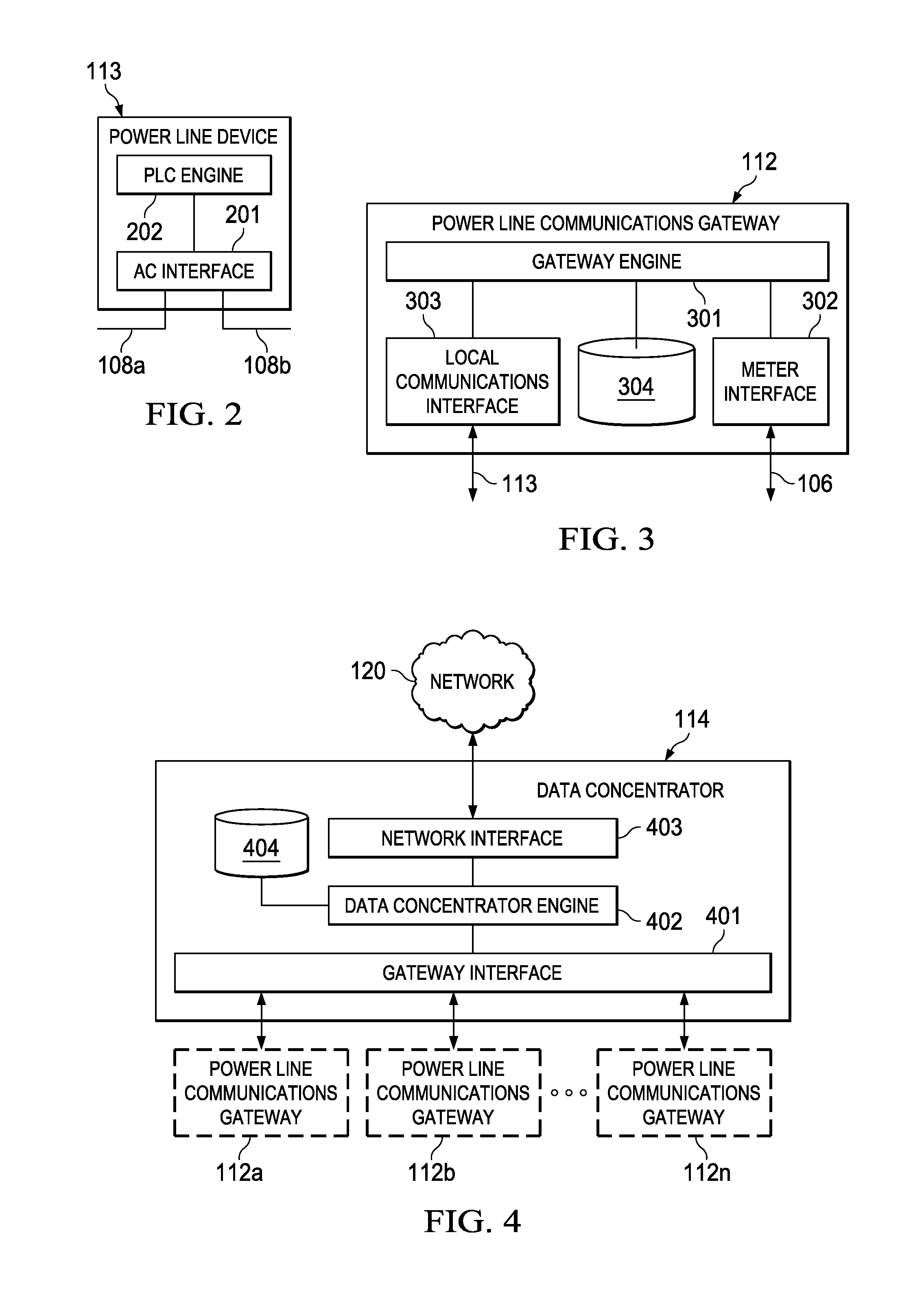
The CAN bus protocol is defined by the ISO 11898-1 standard and can be summarized like this: The physical layer uses differential transmission on a twisted pair wire. A non-destructive bit-wise arbitration is used to control access to the bus.
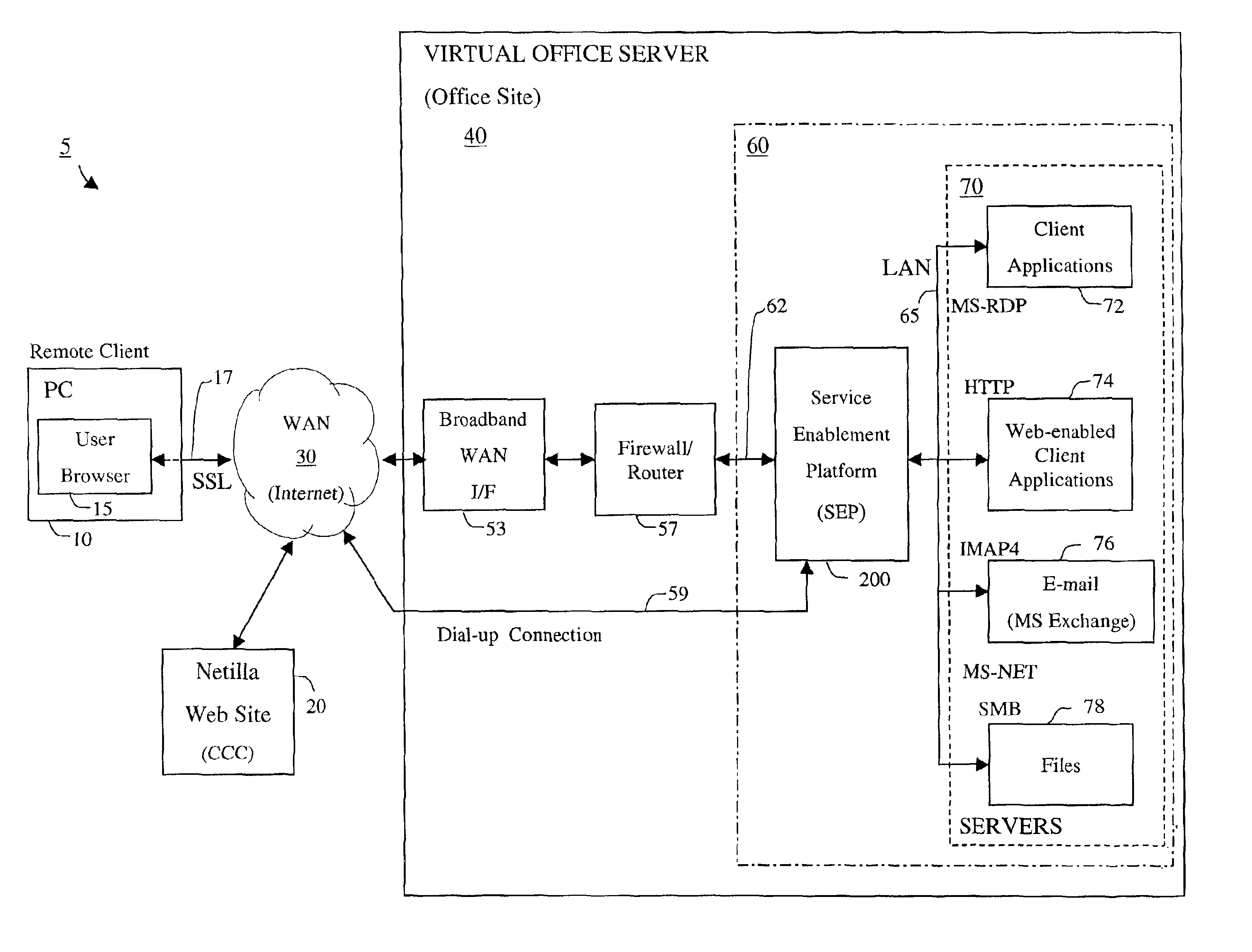
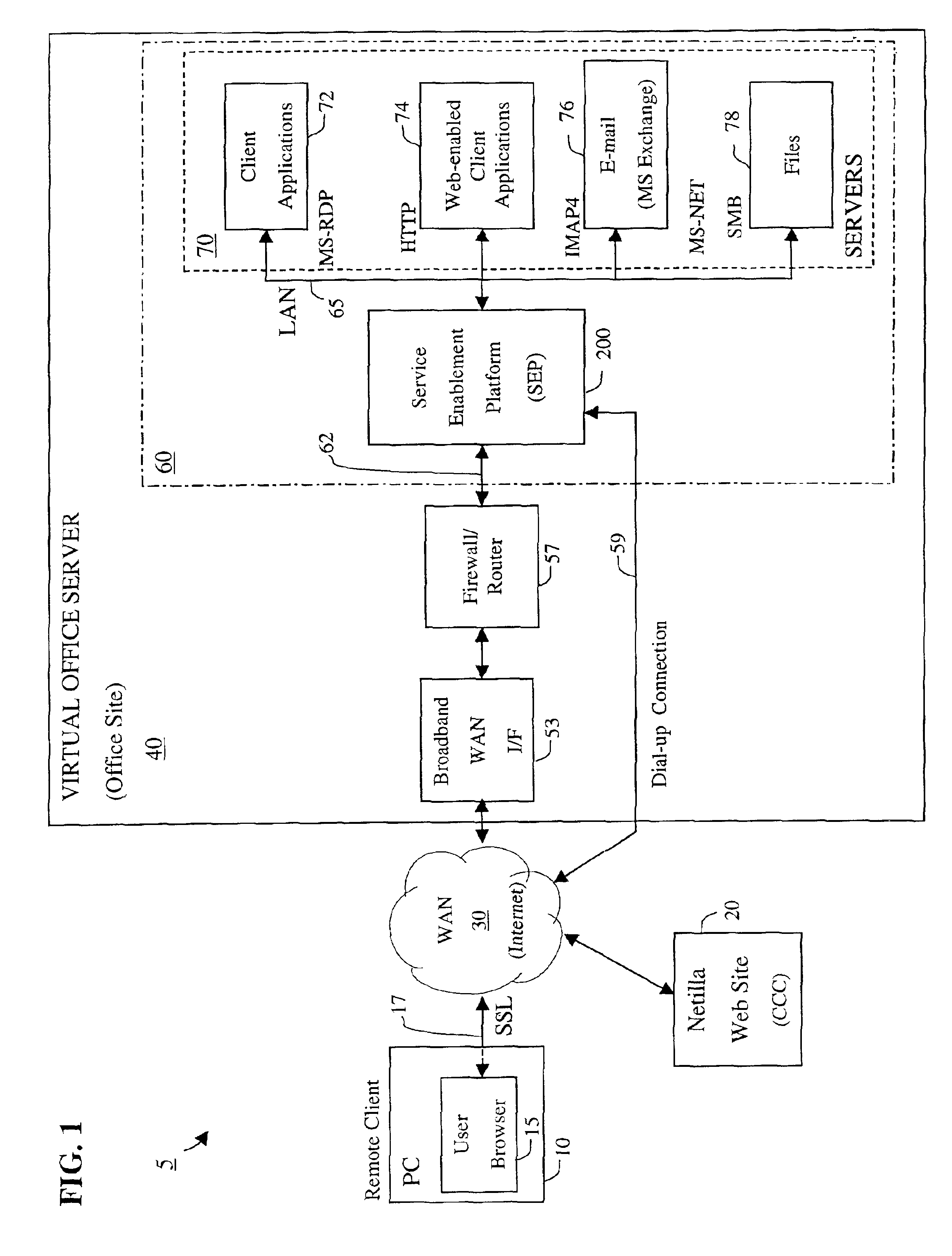
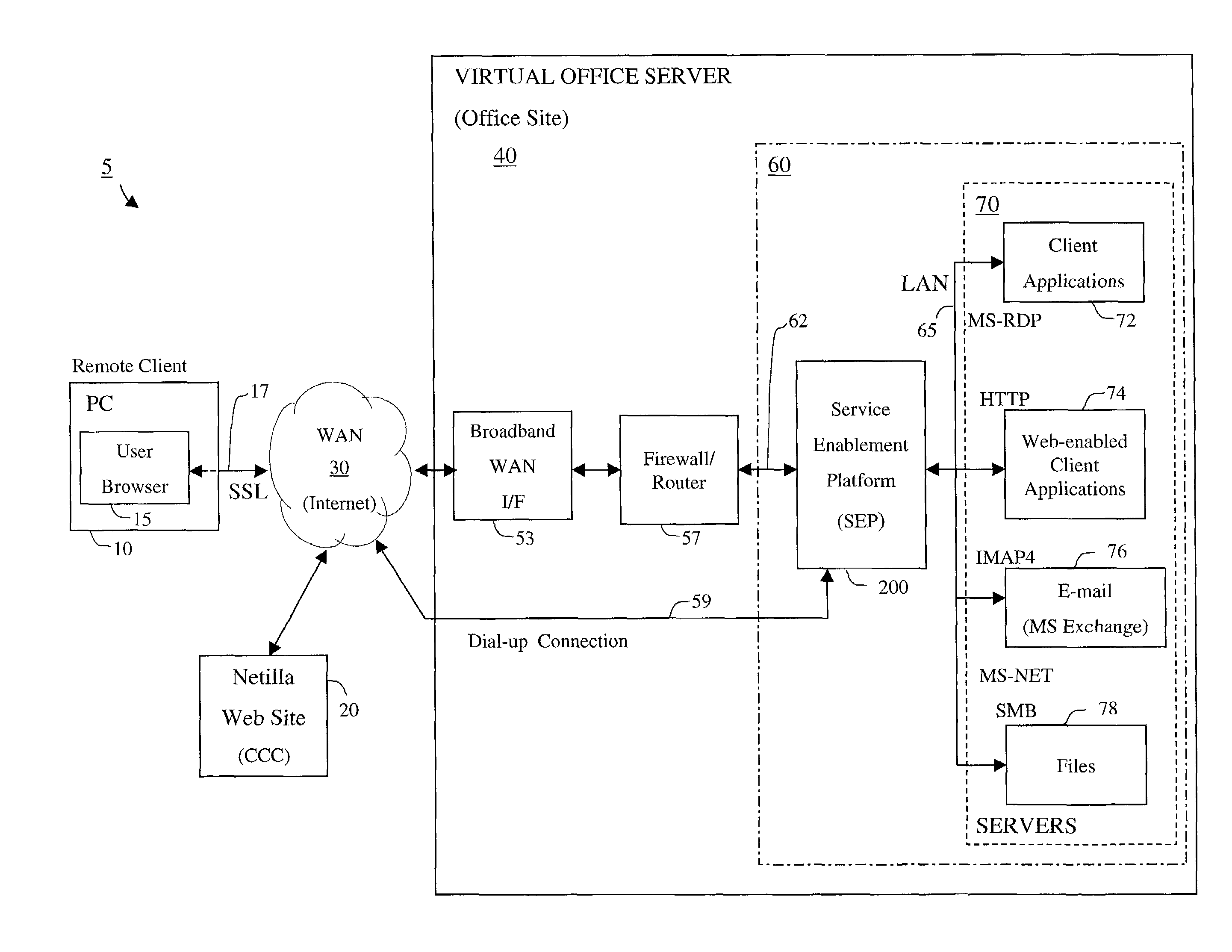
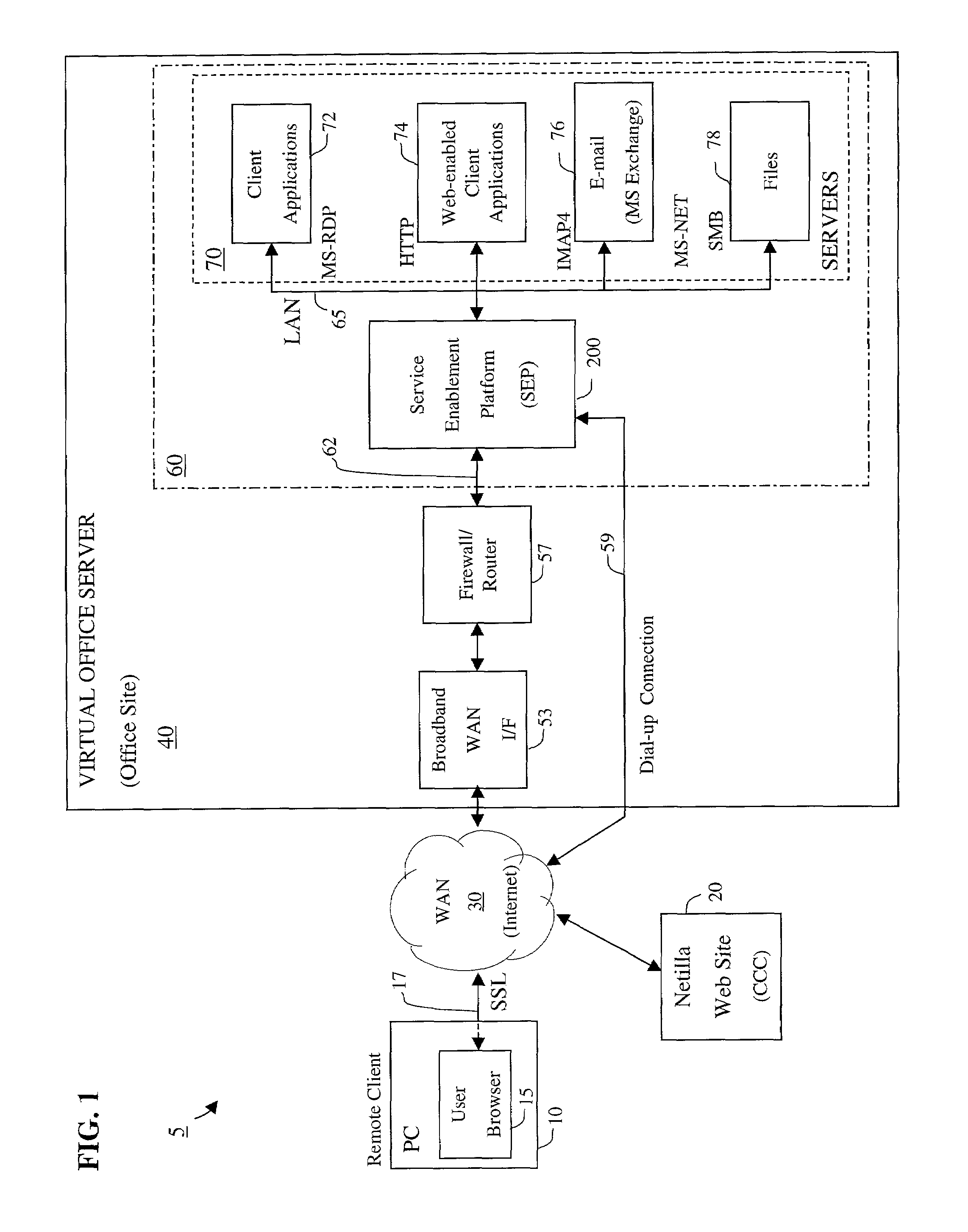
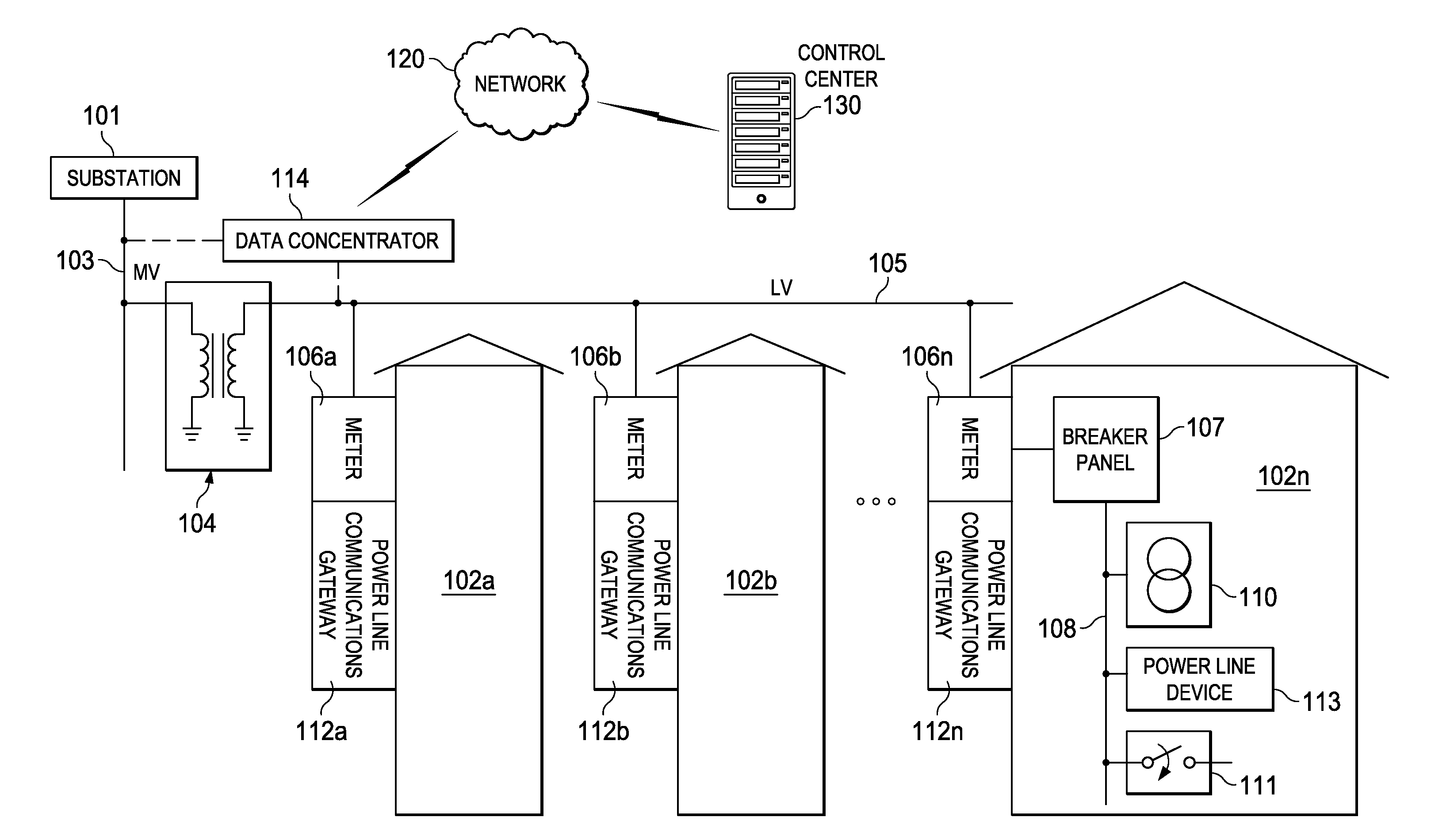
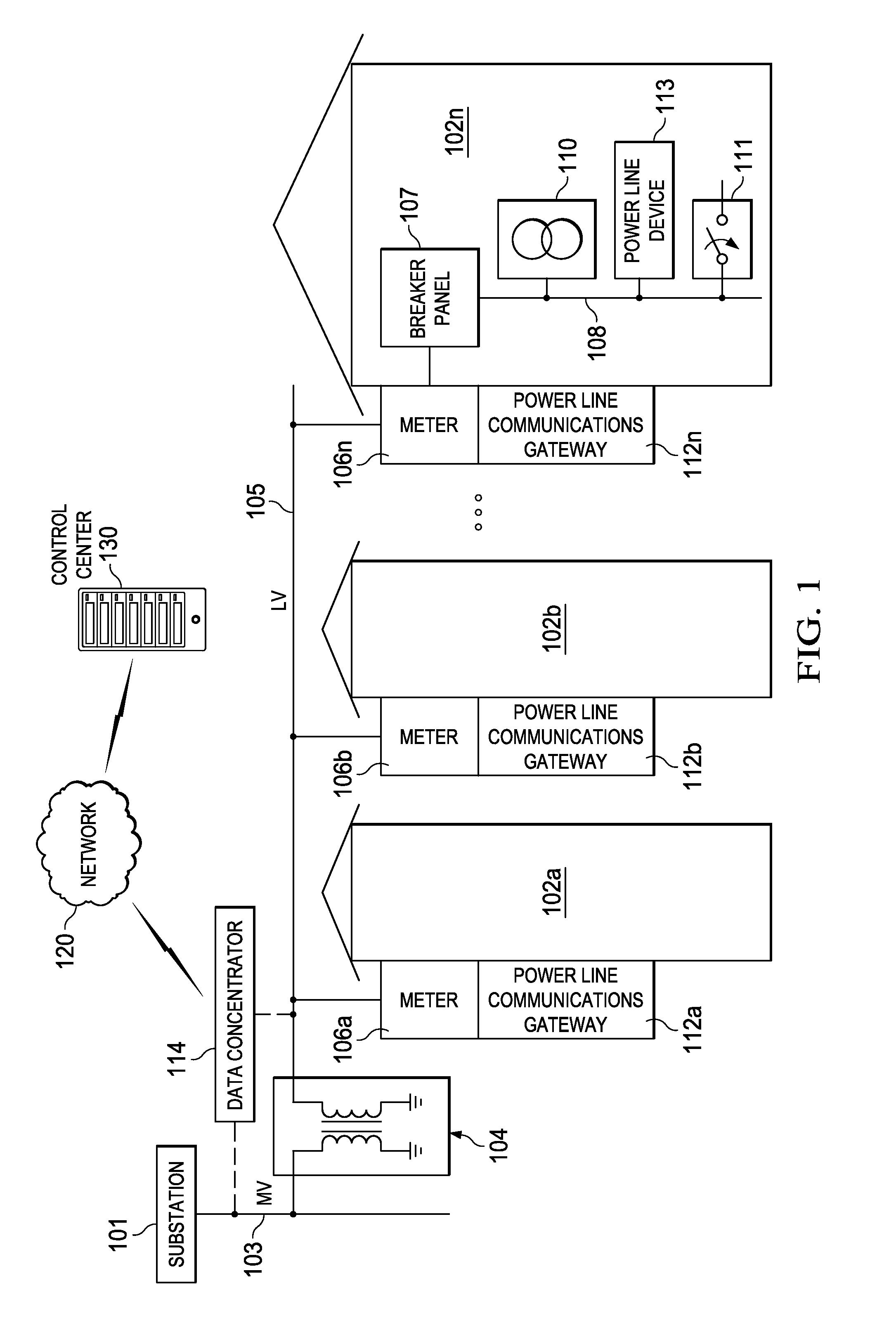
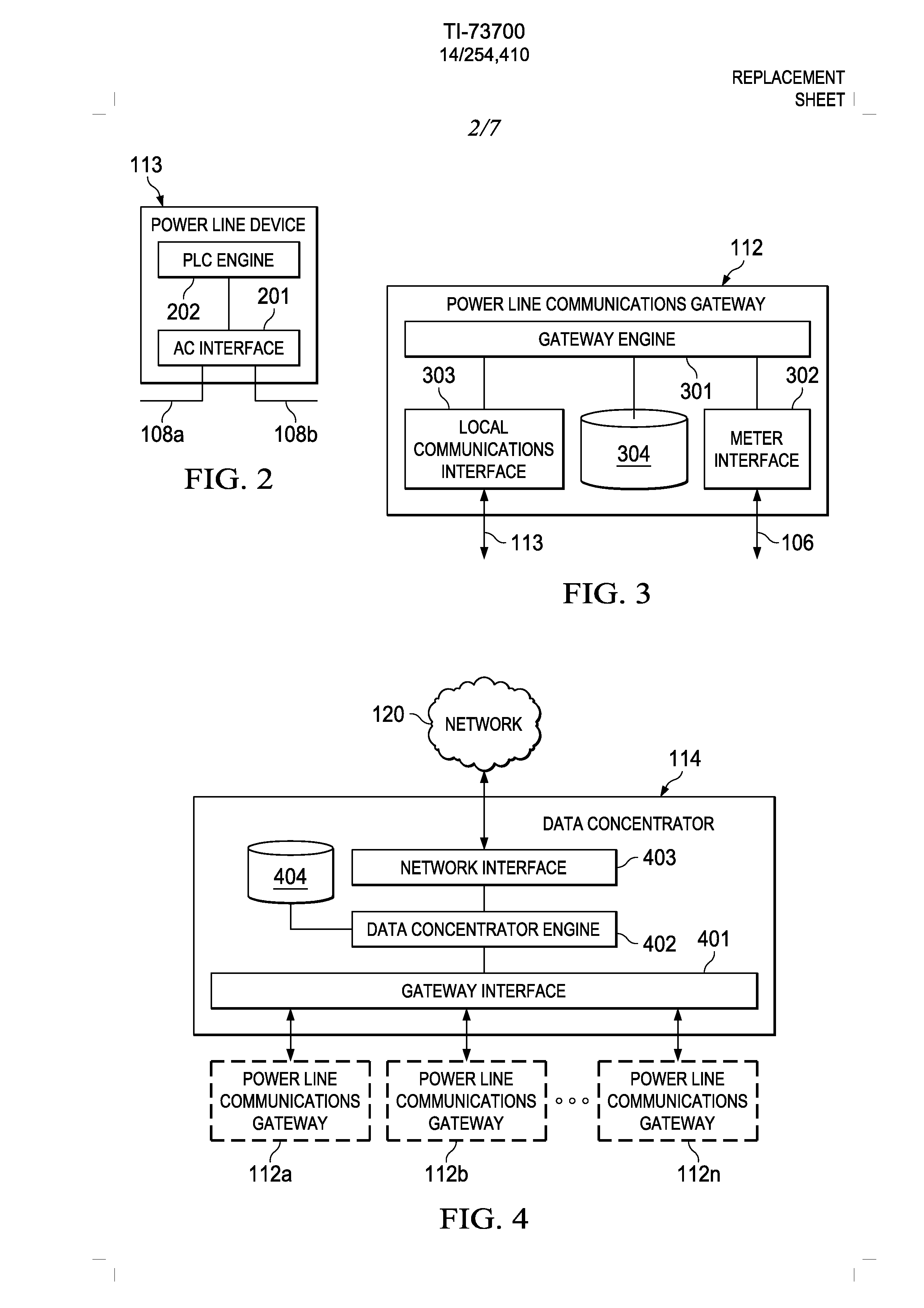
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6920502B2Readily and easily accommodateExpanding processing and storage capacityMultiple digital computer combinationsProgram controlCA protocolNetwork connection
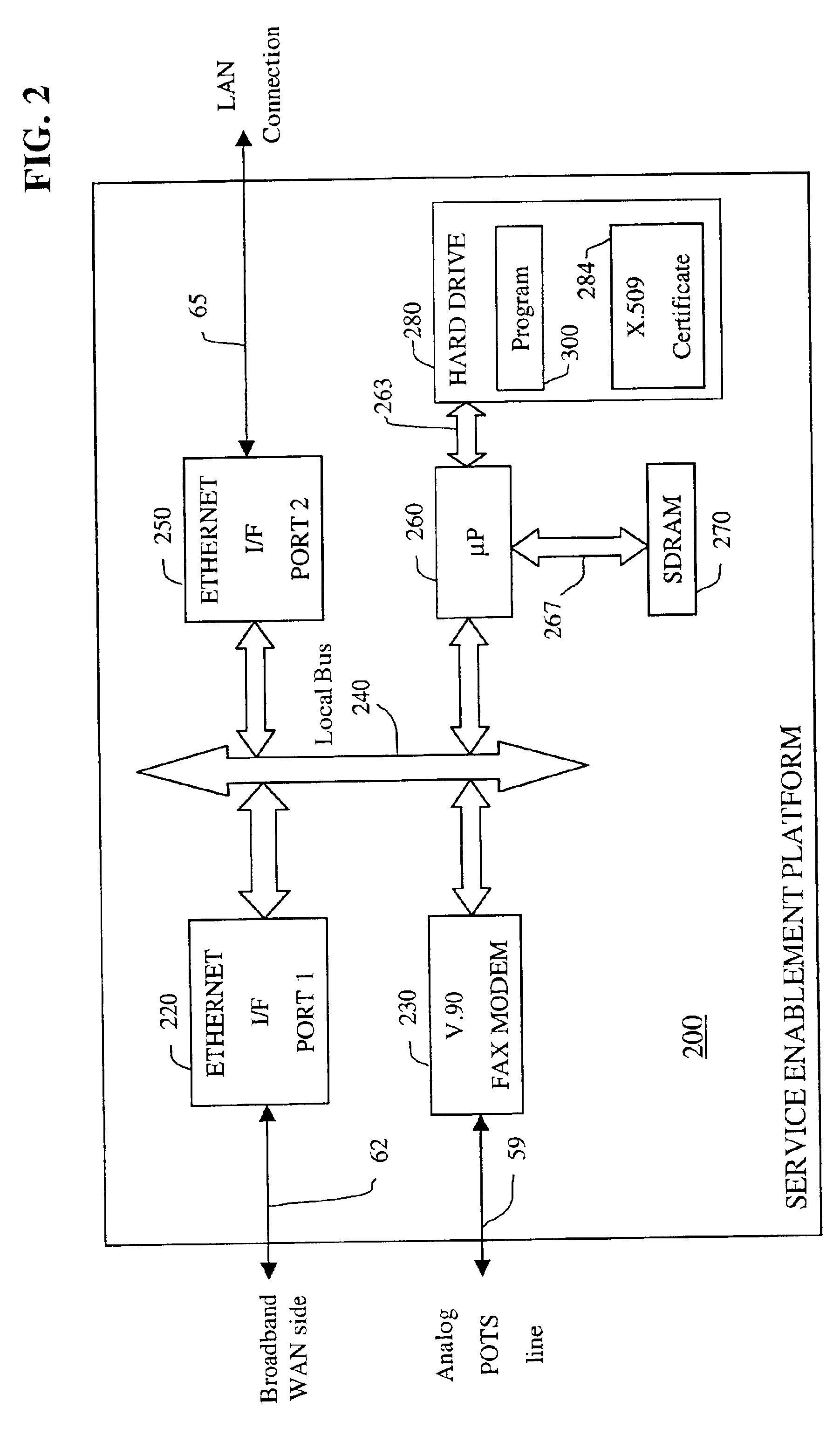
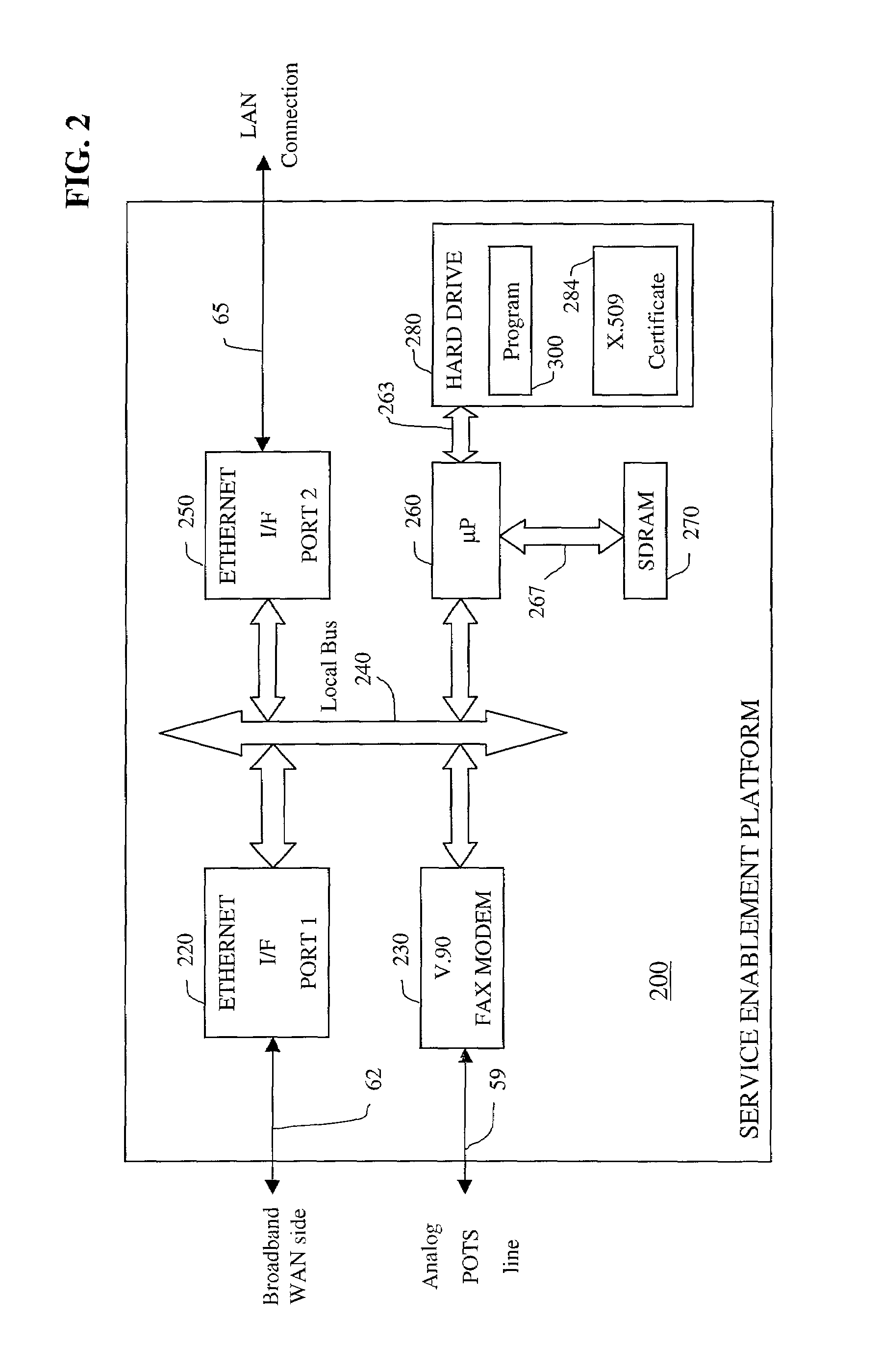
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6981041B2Expanding processing and storage capacityEasy to scaleMultiple digital computer combinationsData switching networksCA protocolNetwork connection
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
Outdoor wireless communication system based on LoRa ad-hoc network
ActiveCN105813099ASolve the problem of poor mobile network signalReduce power consumptionNetwork topologiesWireless commuication servicesCA protocolWireless mesh network
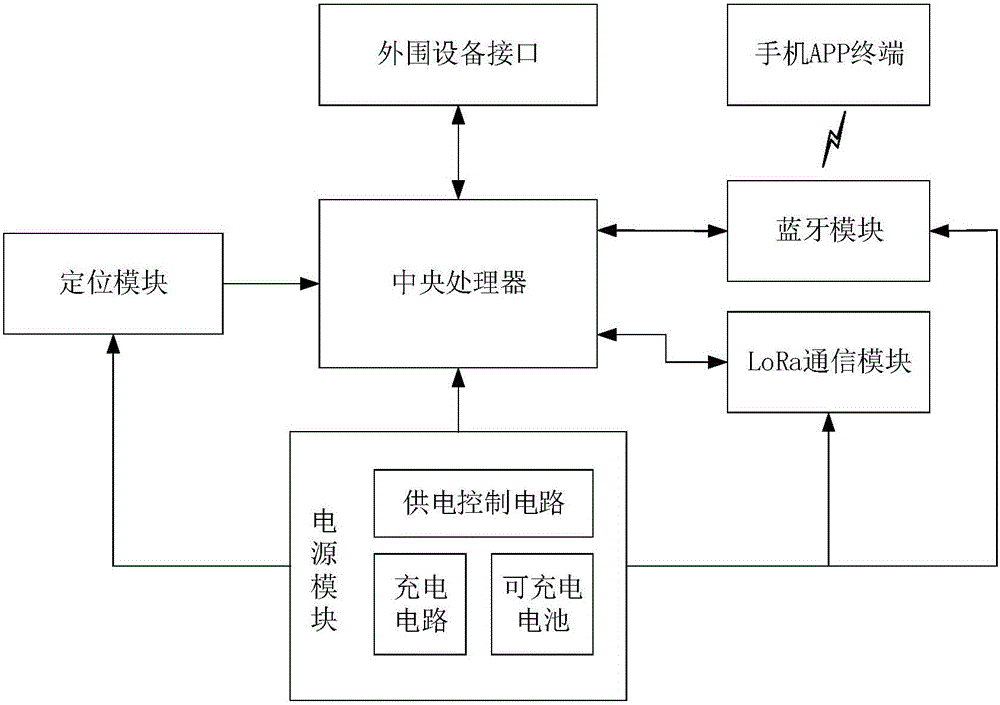
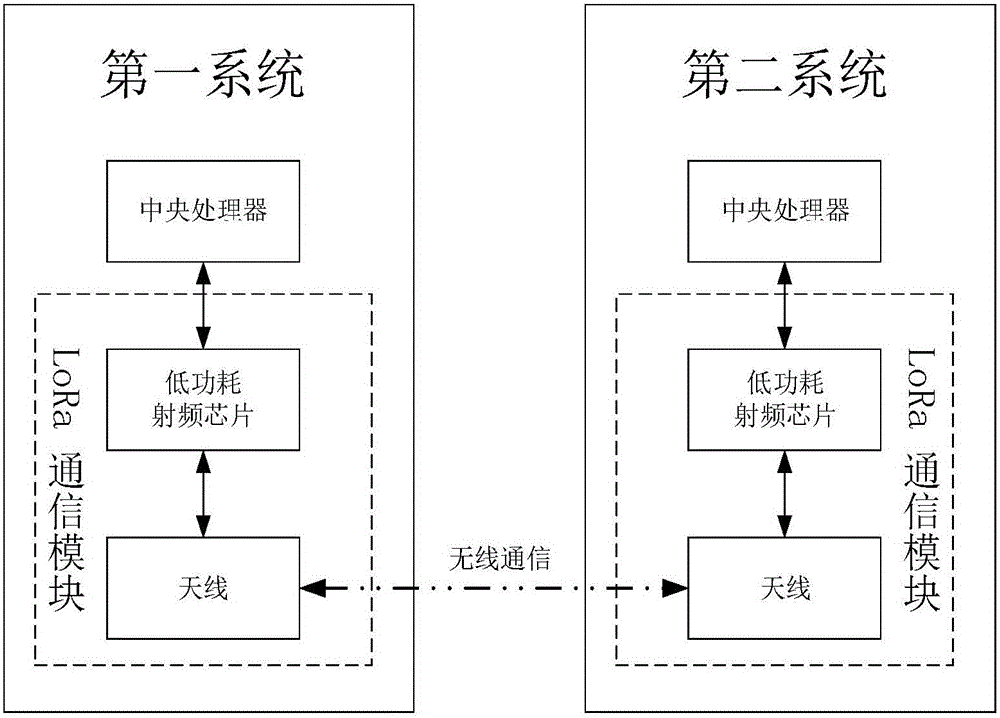
The invention provides an outdoor wireless communication system based on a LoRa ad-hoc network, which is used for solving technical problems of poor mobile network signals in severe environment, short transmission distance and absence of an interactive interface for information sharing of the existing outdoor wireless communication system. The outdoor wireless communication system based on the LoRa ad-hoc network comprises a central processing unit, a positioning module, a Bluetooth module, a peripheral interface, a power supply module, a LoRa communication module and a mobile phone APP terminal; the central processing unit is respectively connected with the positioning module, the Bluetooth module, the peripheral interface, the power supply module and the LoRa communication module; the LoRa communication module constructs a wireless Mesh network with the LoRa communication modules of other systems, and performs reliable data communication through a CSMA / CA protocol and an AODV routing algorithm; and the mobile phone APP terminal and the Bluetooth module perform data exchange through the Bluetooth. The outdoor wireless communication system based on the LoRa ad-hoc network performs communication without the mobile network, has long transmission distance, has the interactive interface for information sharing, and can be applied to the fields, such as the Internet of Vehicles and the Internet of Things.
Owner:XIDIAN UNIV
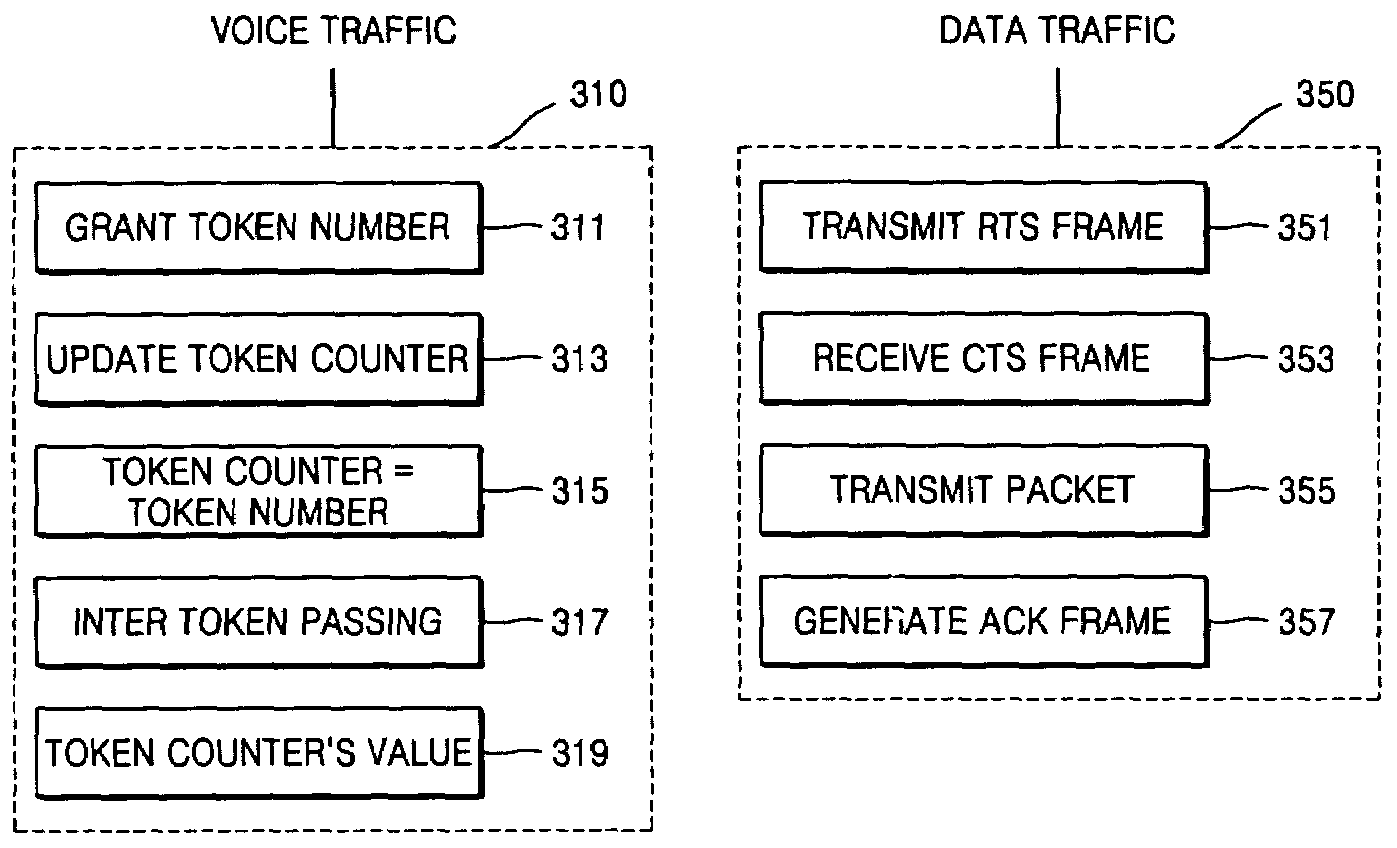
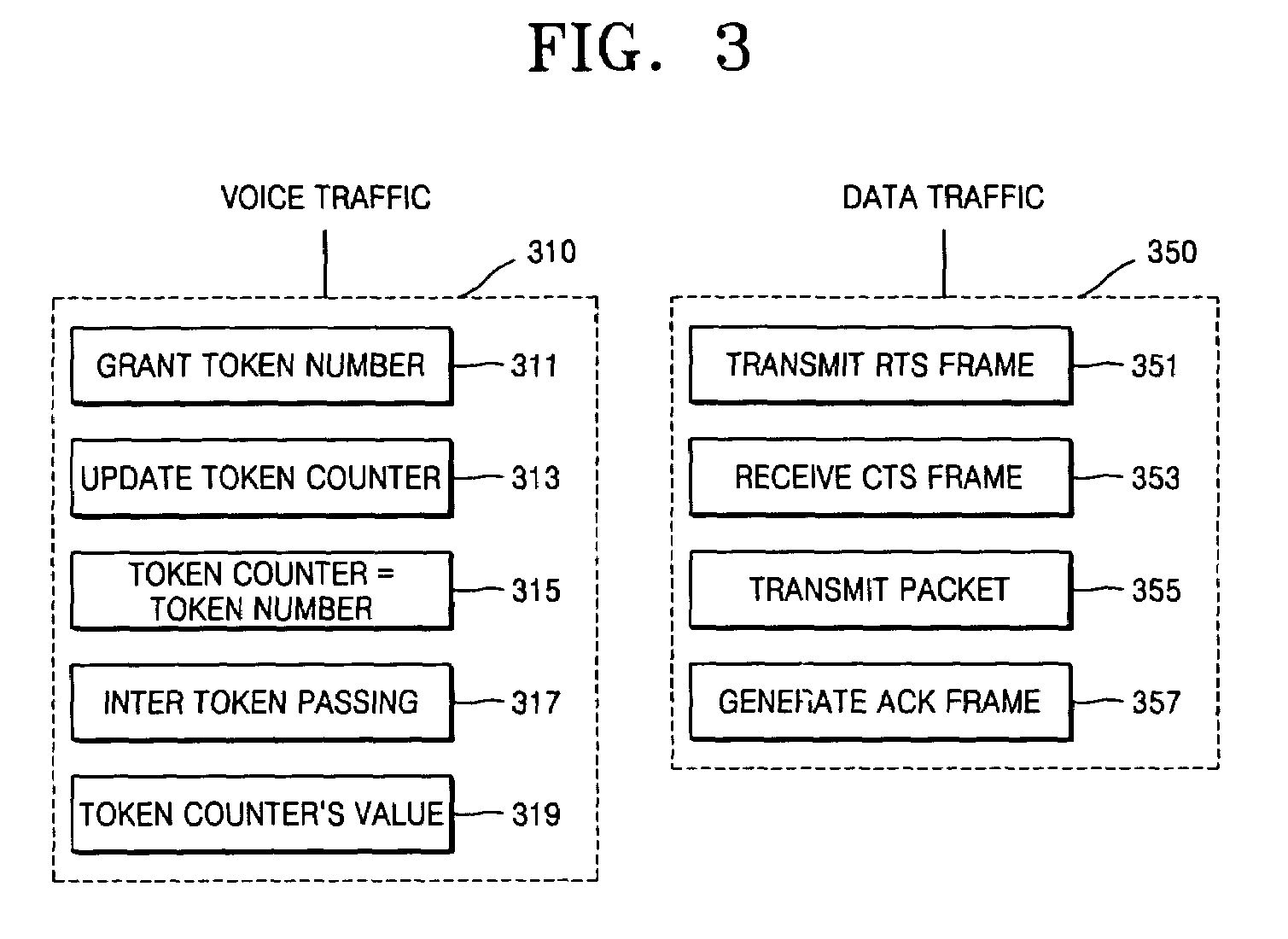
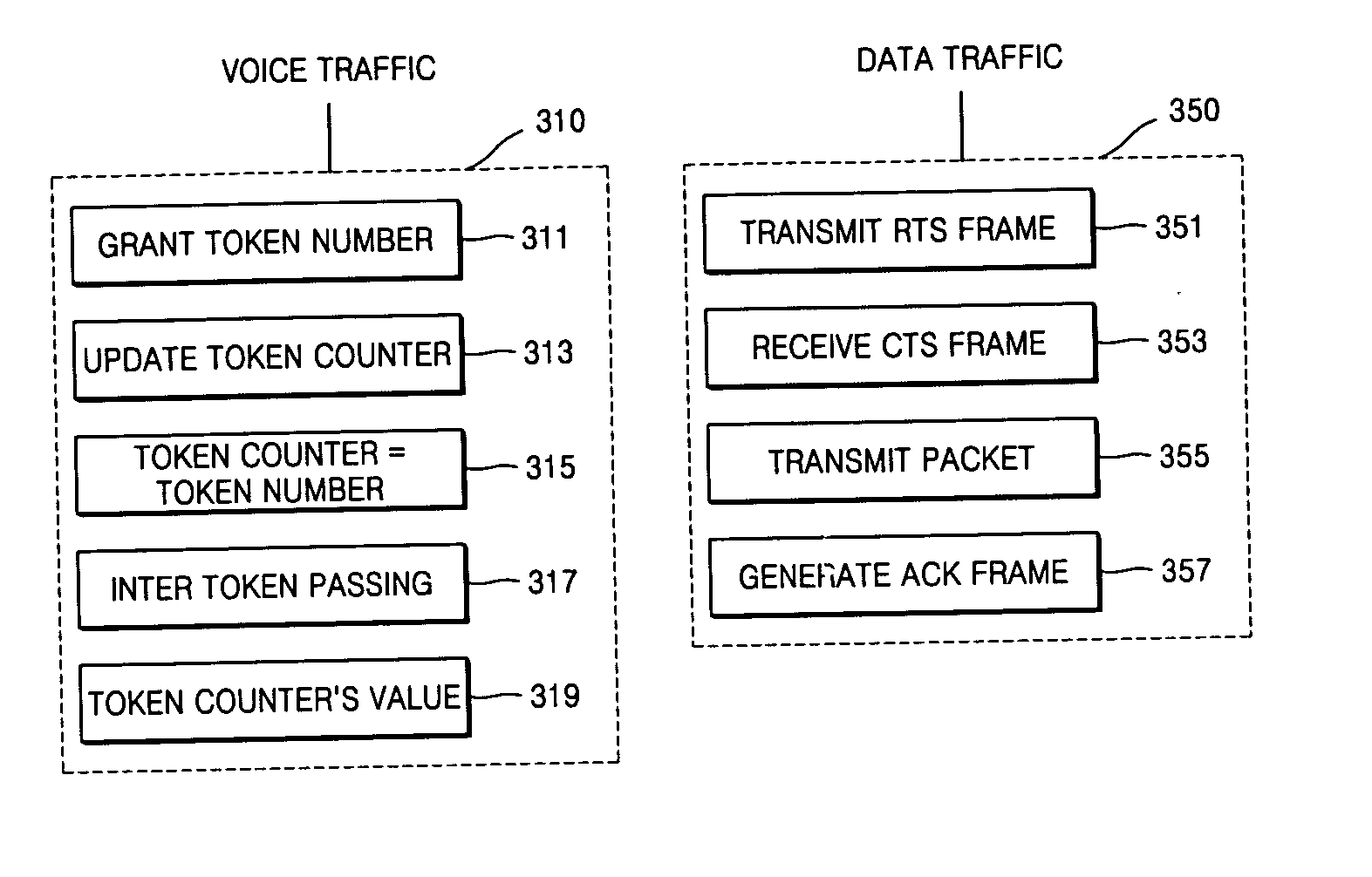
Hybrid implicit token carrier sensing multiple access/collision avoidance protocol
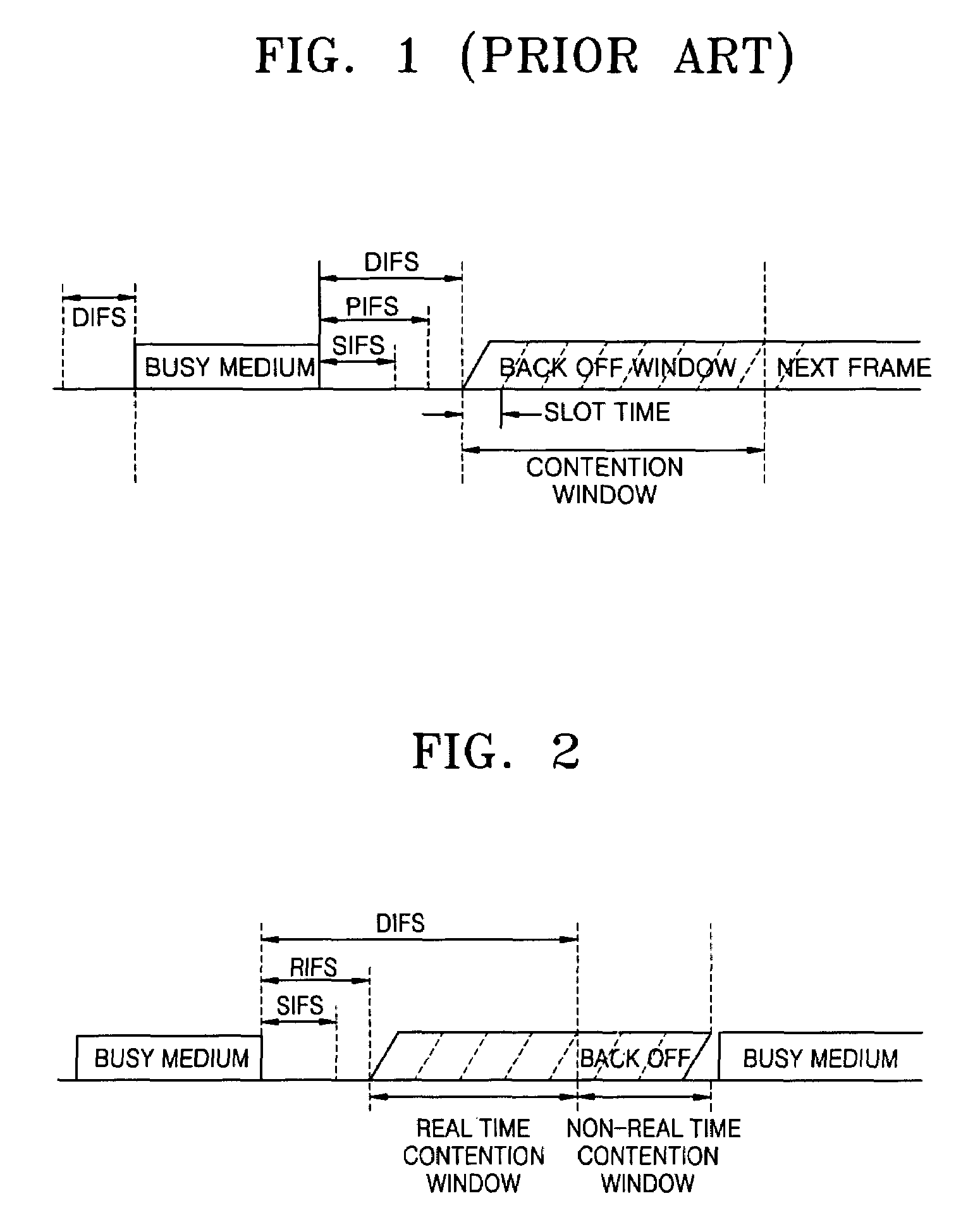
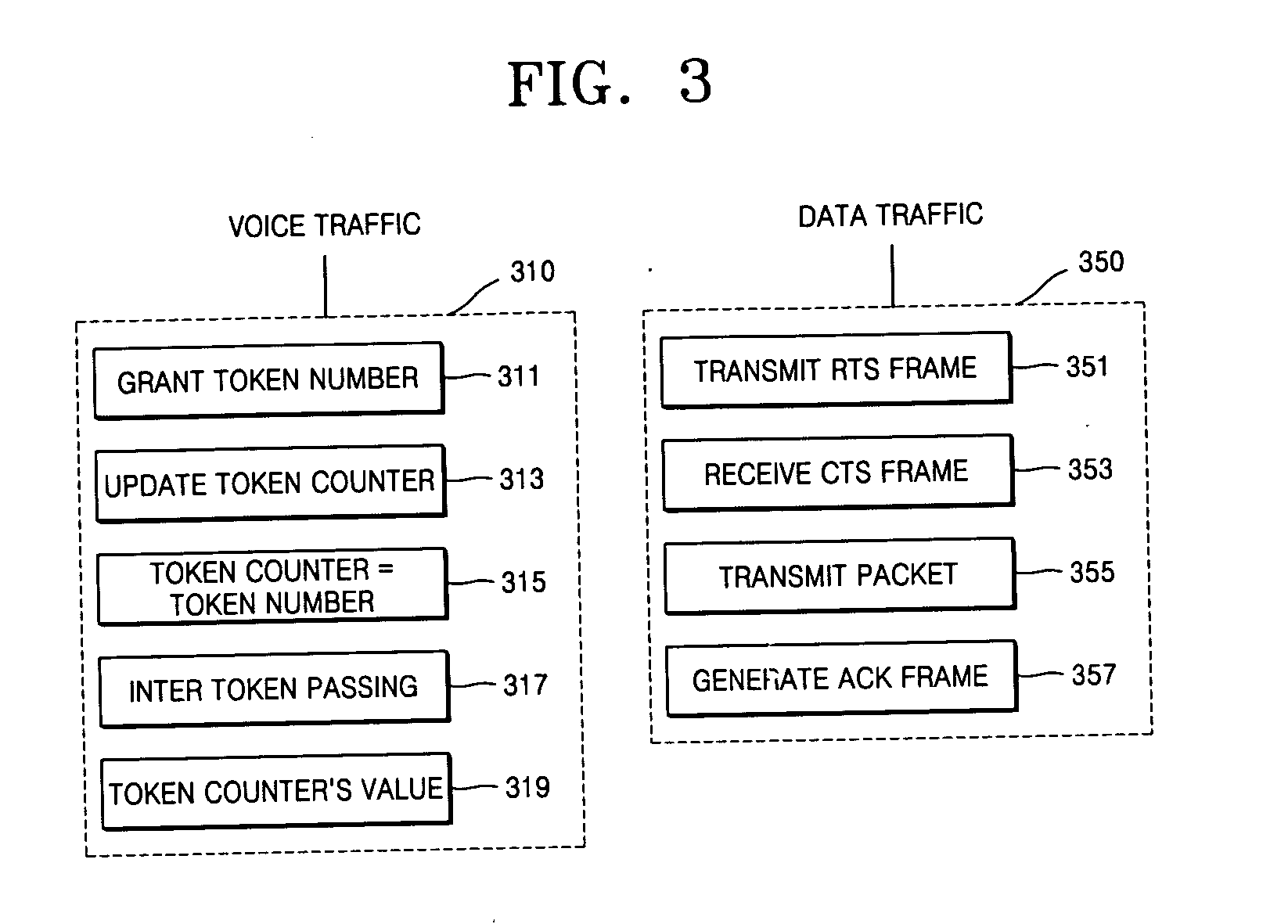
Provided is a distributed and asynchronous implicit token carrier sense multiple access / collision avoidance (CSMA / CA) protocol guaranteeing quality of service for both real time and non-real time traffic. The implicit token CSMA / CA protocol allocates a band in an entire bandwidth to voice traffic and allows the remaining bands to be used for data traffic. The implicit token CSMA / CA protocol includes applying a token passing protocol to transmit voice traffic in real time by having a band in an entire bandwidth allocated using a predetermined data frame and applying a CSMA / CA mechanism to transmit data traffic in non-real time by employing remaining bands not allocated to the voice traffic using another predetermined data frame.
Owner:ELECTRONICS & TELECOMM RES INST
Efficient Fairness Allocation in Powerline CSMA/CA Protocols
ActiveUS20140307658A1Transmission path divisionImproving S/N for transmission/receivingCA protocolCarrier signal
Transmission over a communication channel using carrier sense multiple access collision avoidance (CSMA / CA) may be performed by determining for each frame if the communication channel is busy after a backoff time proportional to a randomly generated number within a contention window (CW). When the channel is not busy, a frame of data may be transmitted. When the channel is busy, the device may periodically determine if the communication channel is busy after subsequent backoff times. The value of CW is adjusted for each subsequent backoff time using a fairness protocol, in which the value of CW is increased until the value of CW reaches a maximum CW value; and then the value of CW is held until a fairness number of backoff repetitions reaches a fairness threshold; then the value of CW is reduced incrementally until the value of CW reaches a minimum CW value.
Owner:TEXAS INSTR INC
Hybrid implicit token carrier sensing multiple access/collision avoidance protocol
Provided is a distributed and asynchronous implicit token carrier sense multiple access / collision avoidance (CSMA / CA) protocol guaranteeing quality of service for both real time and non-real time traffic. The implicit token CSMA / CA protocol allocates a band in an entire bandwidth to voice traffic and allows the remaining bands to be used for data traffic. The implicit token CSMA / CA protocol includes applying a token passing protocol to transmit voice traffic in real time by having a band in an entire bandwidth allocated using a predetermined data frame and applying a CSMA / CA mechanism to transmit data traffic in non-real time by employing remaining bands not allocated to the voice traffic using another predetermined data frame.
Owner:ELECTRONICS & TELECOMM RES INST
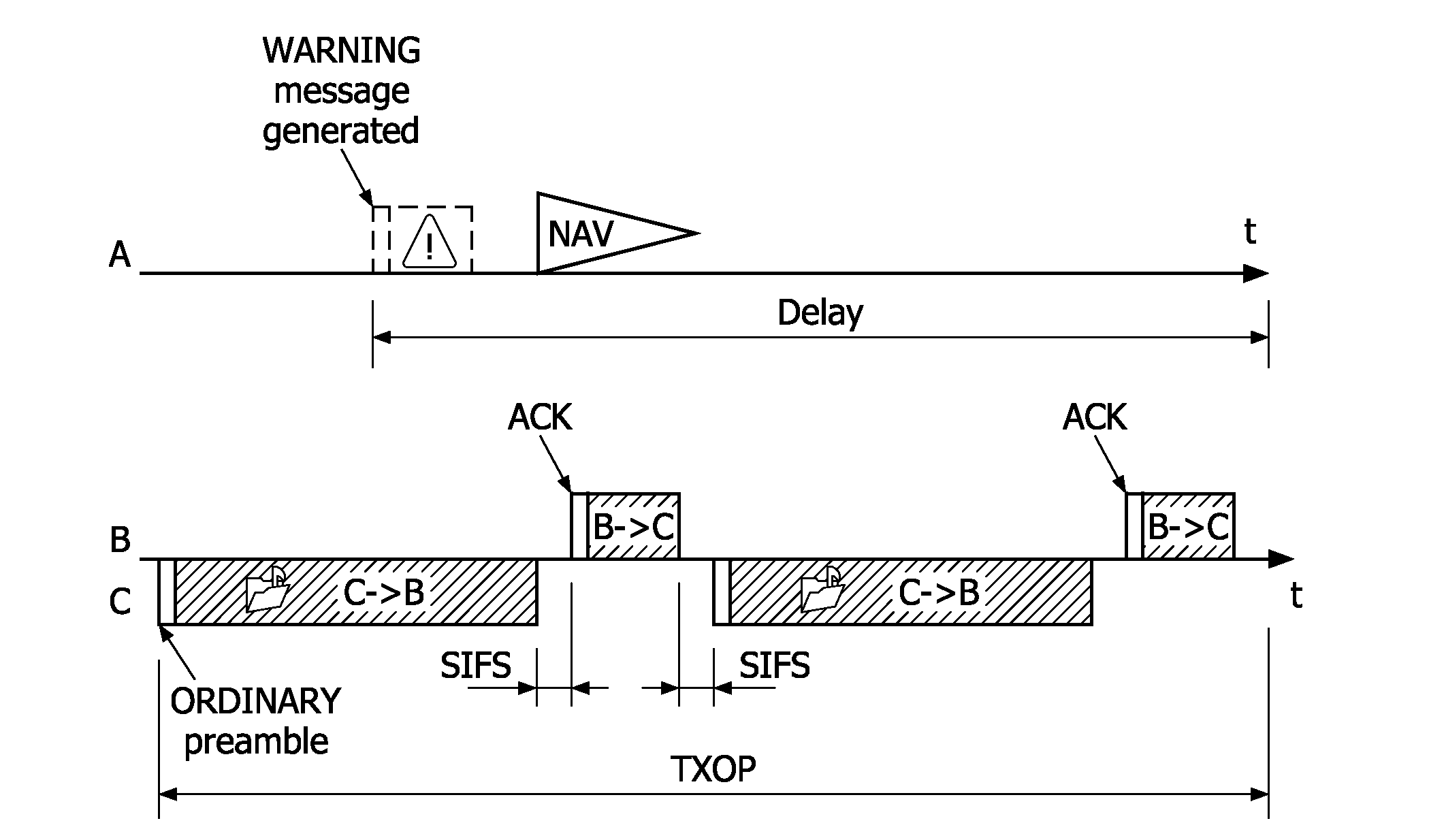
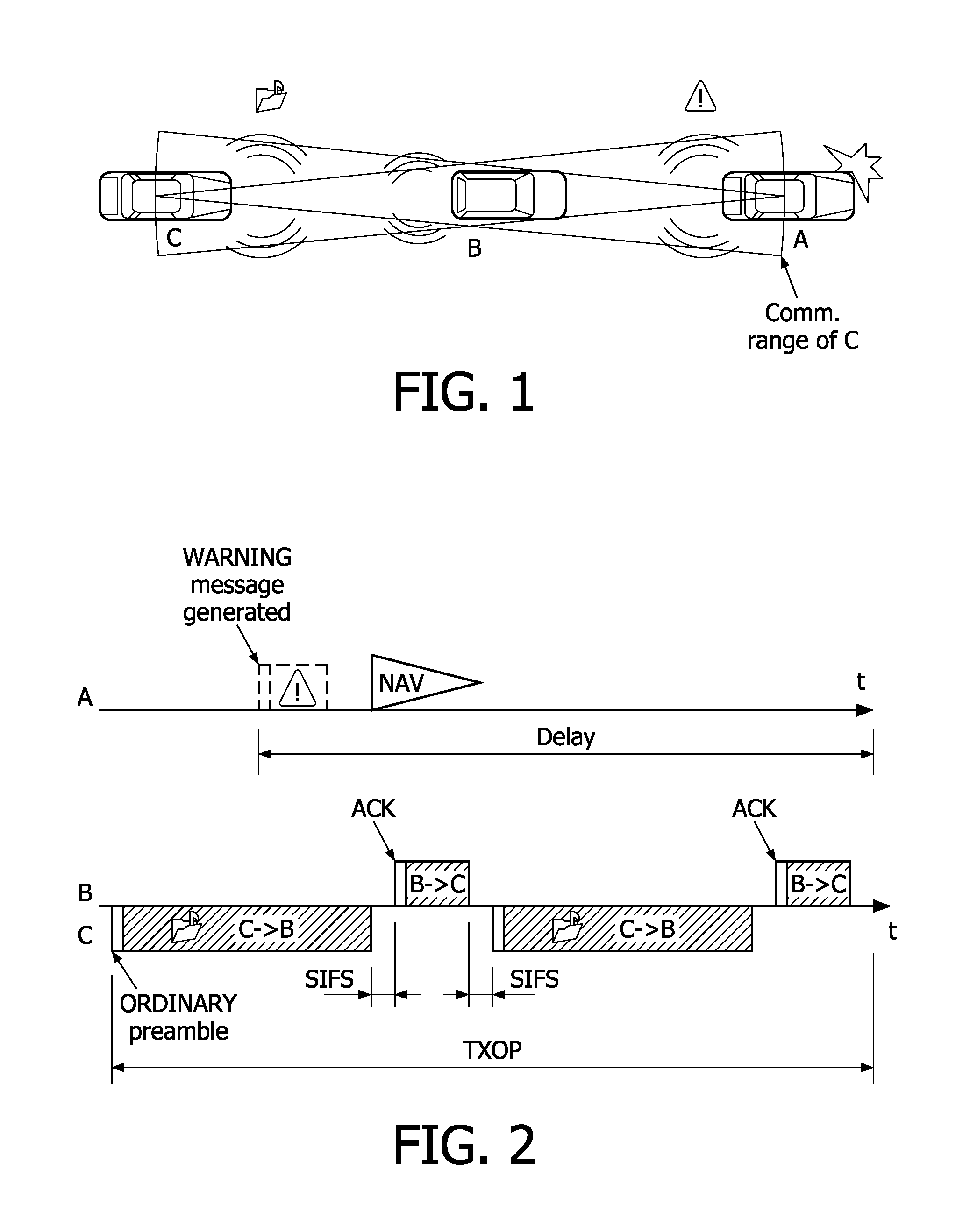
Visible light full duplex continuous transmission random access method based on channel reservation mechanism
ActiveCN107046733AResolve hidden nodesFix performance issuesClose-range type systemsWireless communicationCA protocolHidden node problem
The invention discloses a visible light full duplex continuous transmission random access method based on a channel reservation mechanism. Different from the CSMA / CA protocol in the existing IEEE802.15.7 standard, after a user executes idle channel estimation and detects that the channel is in an idle state, the user does not directly send a data frame, but firstly sends a RTS frame to reserve the channel, and sends the data frame after successfully reserving the channel. A full duplex visual light access point needs to broadcast busy tone to eliminate the hidden nodes when receiving the RTS frame or the data frame. Moreover, the user can directly execute CCA without executing random evasion again after successfully transmitting the data frame, therefore the conflict of the data frame is prevented, the time slot resources consumed by the random evasion mechanism are reduced, and the throughput and delay performance are improved. By adoption of the visible light full duplex continuous transmission random access method, the visible light hidden node problem is effectively solved, and meanwhile, the throughput and the delay performance of the visible light CSMA / CA protocol is optimized at the same time.
Owner:SUN YAT SEN UNIV
Inter-satellite networking communication method for small satellite cluster
The invention provides an inter-satellite networking communication method for a small satellite cluster. The method comprises the following steps that: (1) a center node and an ordinary node are set; (2) a physical channel is divided into a networking channel and a data channel, and each satellite node shares the physical channel through a CSMA / CA mode of an IEEE802.11 protocol; (3) the center node sends a networking beacon frame by using the networking channel, the ordinary node carries out monitoring, and after the reception, a request association frame is sent to the center node if the access to a network is decided; (4) after the center node receives the request association frame, whether the access of an ordinary node into the network is allowed or not is judged according to the identity verification and network capacity information, the corresponding association application feedback information is sent to the ordinary node, after the networking is completed, each ordinary node employs a roll polling mode to carry out measurement and control data communication under the control of the center node, and after the measurement and control data communication is completed, each ordinary node employs a CSMA / CA protocol of IEEE802.11 to carry out data communication.
Owner:AEROSPACE DONGFANGHONG SATELLITE
Method and apparatus for data communication in radio network
InactiveUS20110268012A1Reduce in quantityAvoid excessive loadsBroadcast transmission systemsWireless network protocolsCA protocolRadio networks
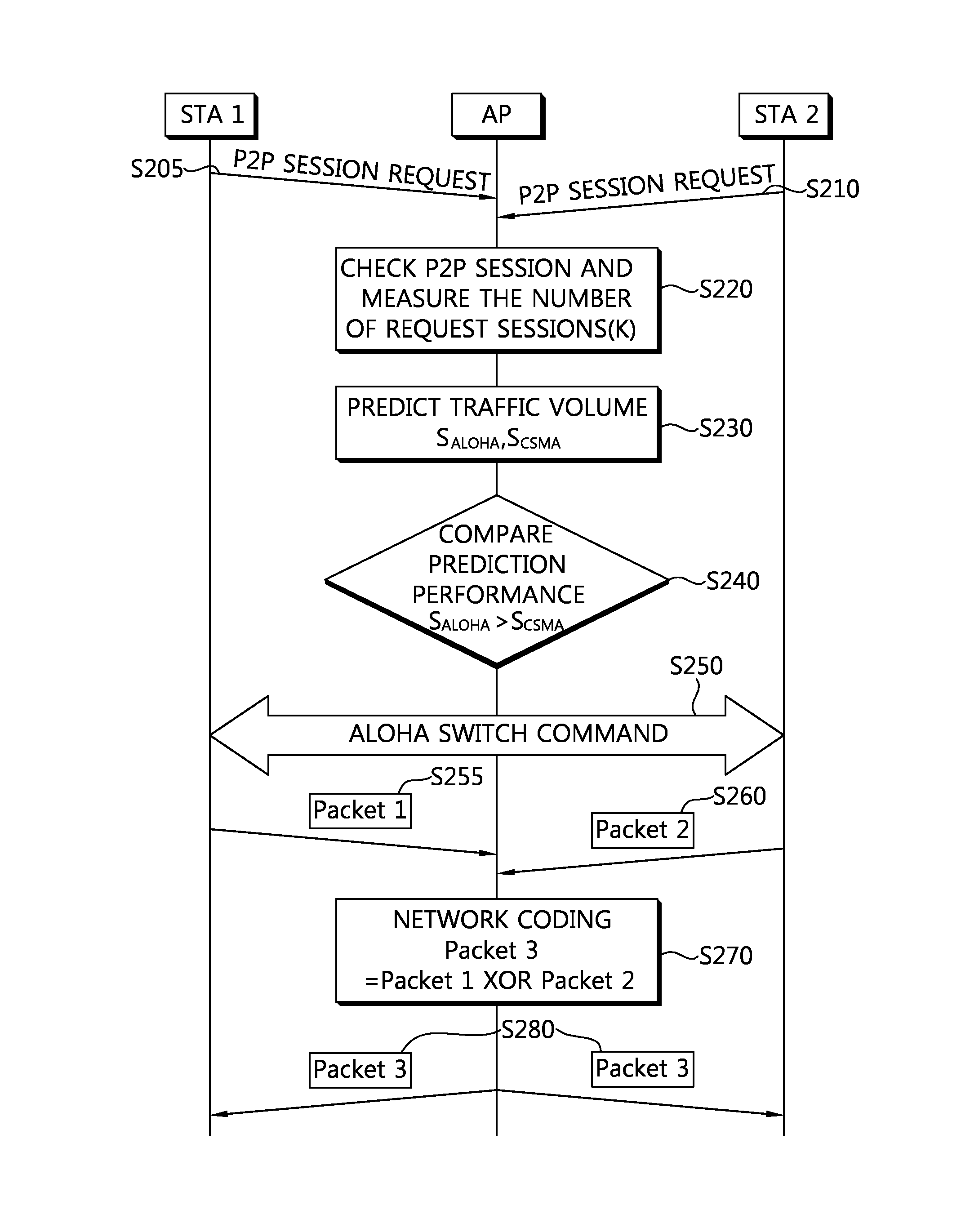
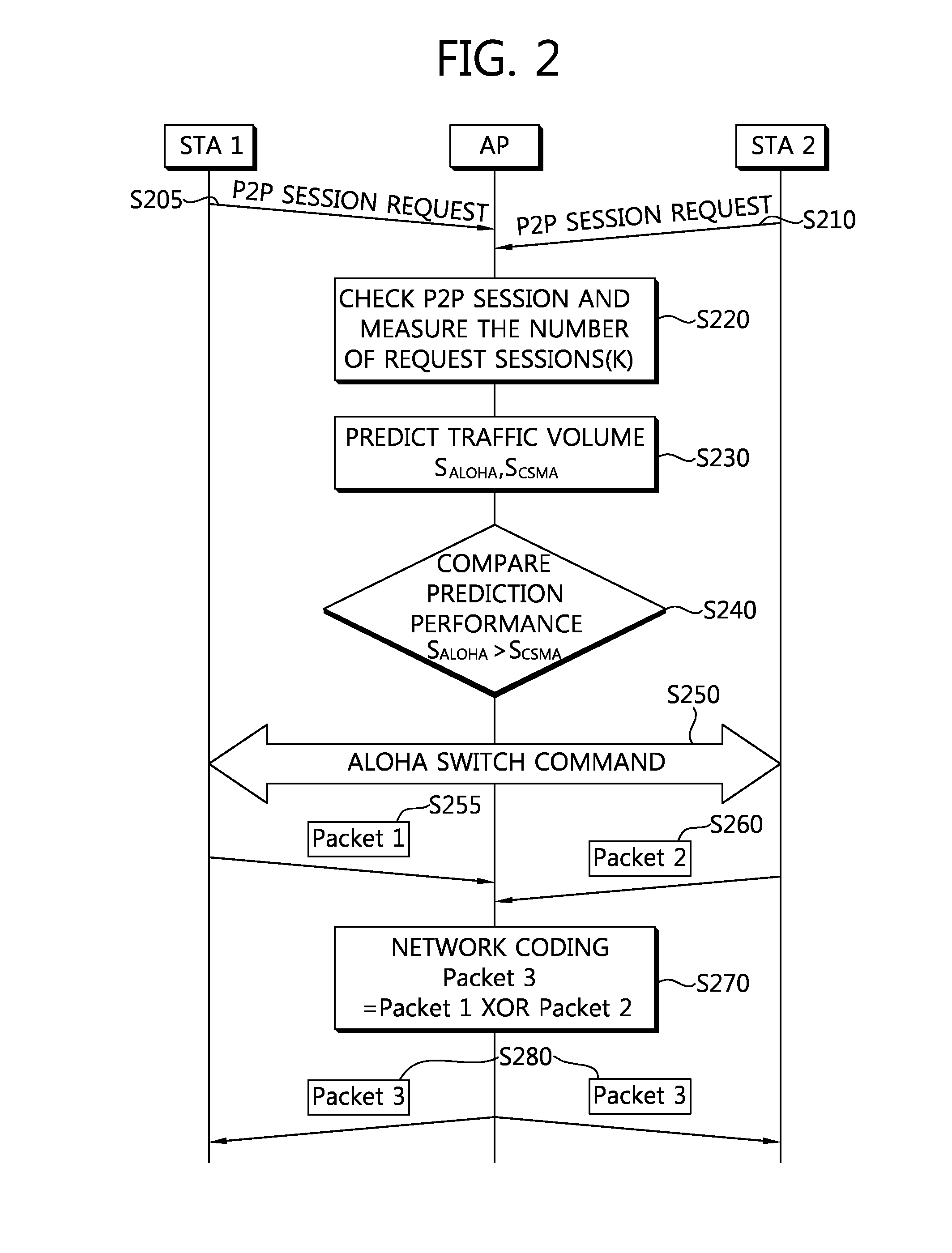
Disclosed is a method for data communication in a radio network, including calculating an expected value of transmission efficiency of a Carrier Sense Multiple Access / Collision Avoidance (CSMA / CA) protocol and an expected value of transmission efficiency of a Slotted ALOHA protocol, comparing the two expected values, switching a mode into the mode of the protocol having the larger expected value from among the expected value of transmission efficiency of the CSMA / CA protocol and the expected value of transmission efficiency of Slotted ALOHA protocol, and broadcasting, to stations (STAs), a message for indicating the STAs to switch a protocol into the protocol having the larger expected value of transmission efficiency, and transmitting data by using the protocol having the larger expected value of transmission efficiency.
Owner:LG ELECTRONICS INC +1
Wireless communication method and wireless communication system
ActiveUS20130250836A1Solve problemsBroadcast transmission systemsBroadcast service distributionCA protocolCommunications system
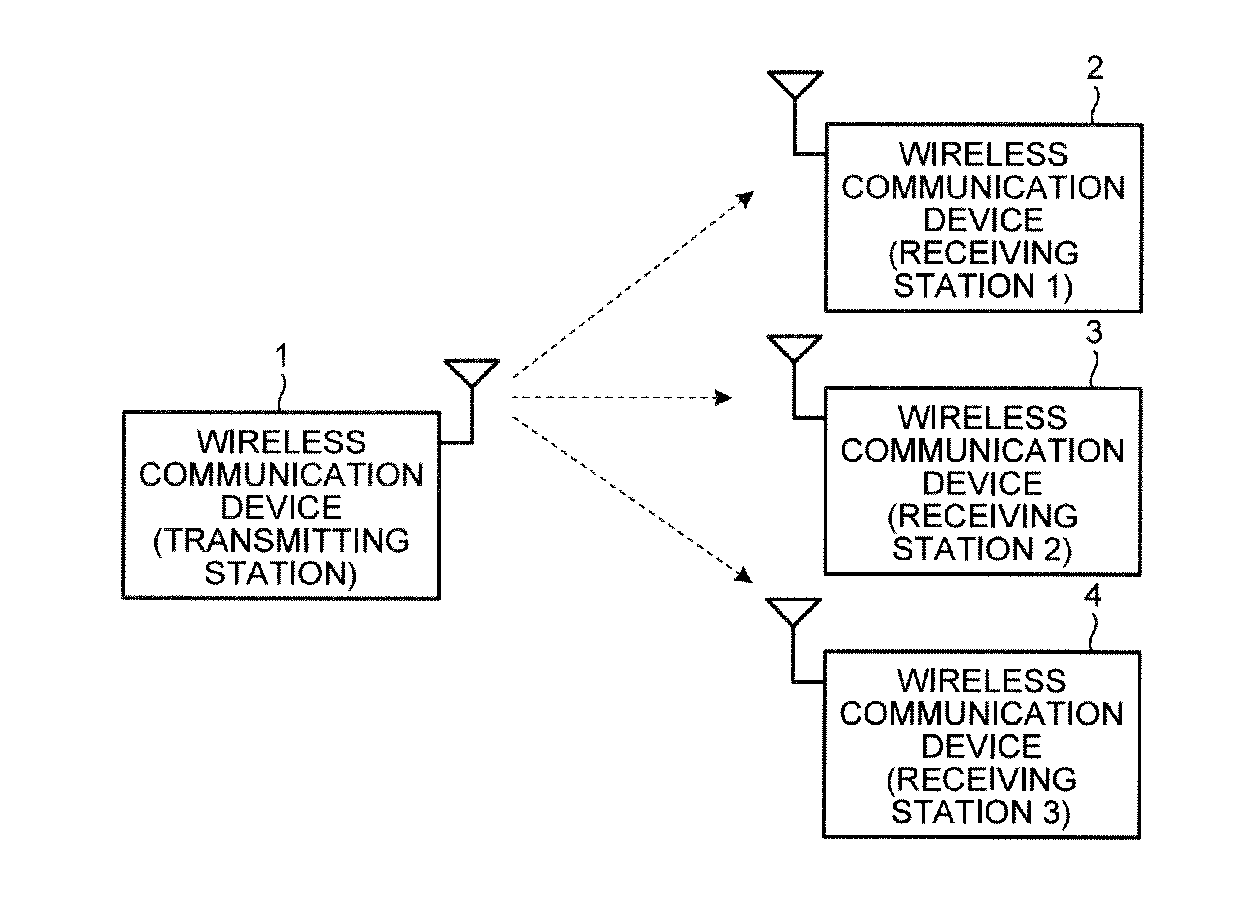
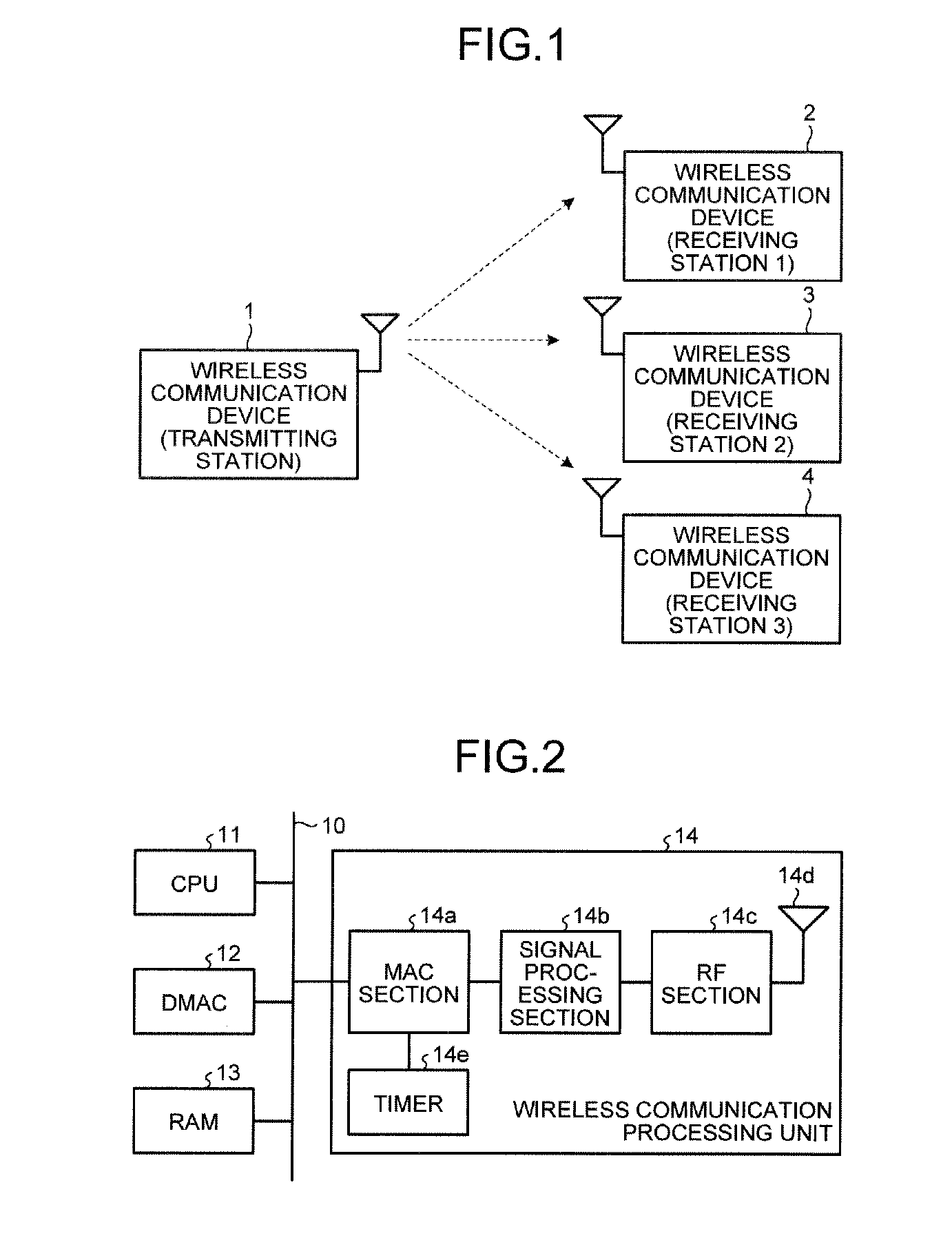
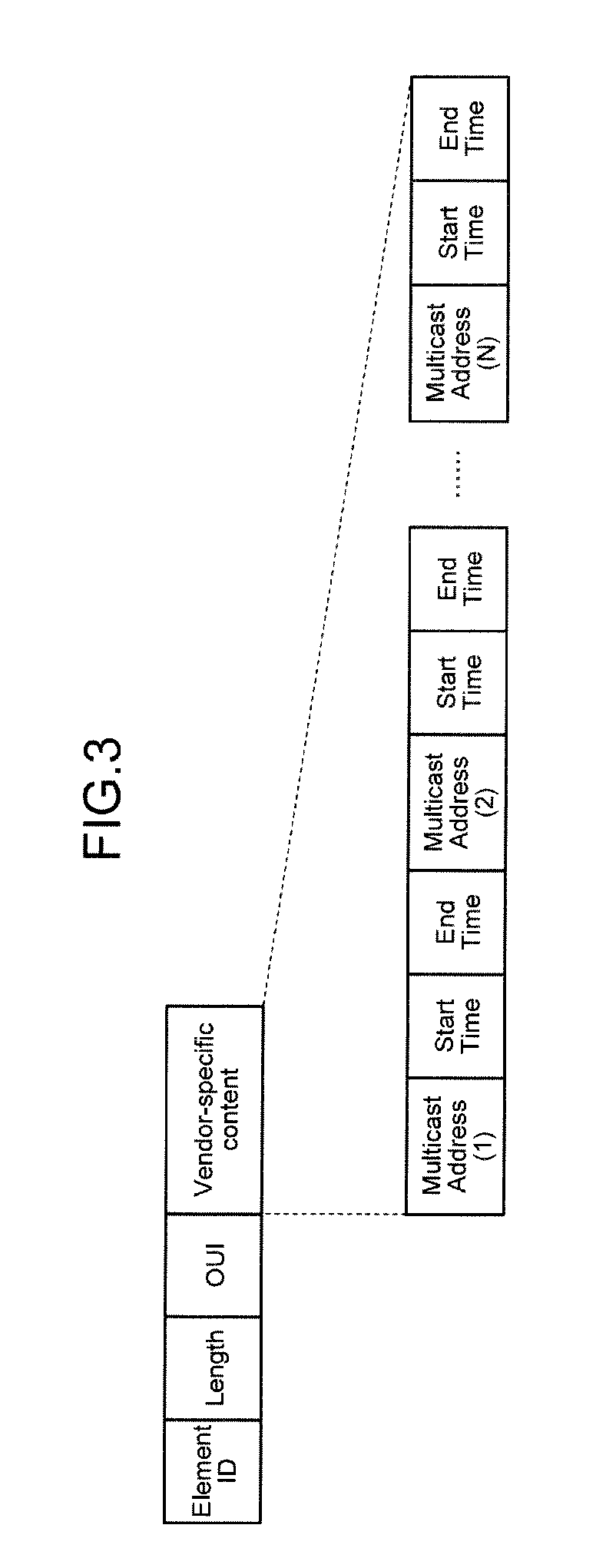
In the invention, wireless communication devices transmit beacon frames in an order in compliance with a CSMA / CA protocol. A wireless communication device as a transmitting station of a multicast frame uses one of the beacon frames to notify wireless communication devices as receiving stations of the multicast frame that an ACK frame is to be transmitted when the multicast frame is received. On receipt of the multicast frame, the wireless communication devices as the receiving stations transmit ACK frames in order of transmitting the beacon frames at SIFS intervals.
Owner:RICOH KK
Dynamic power line carrier communication channel allocation method based on TDMA and CSMA/CA
InactiveCN107919951AAdaptableImprove network performancePower distribution line transmissionTransmission path sub-channels allocationCA protocolIdle time
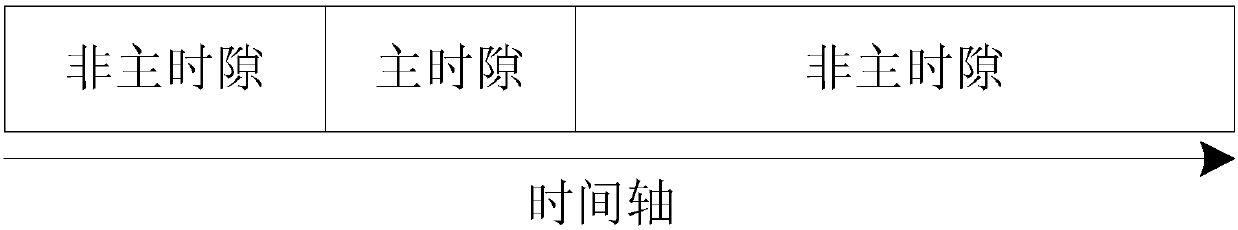
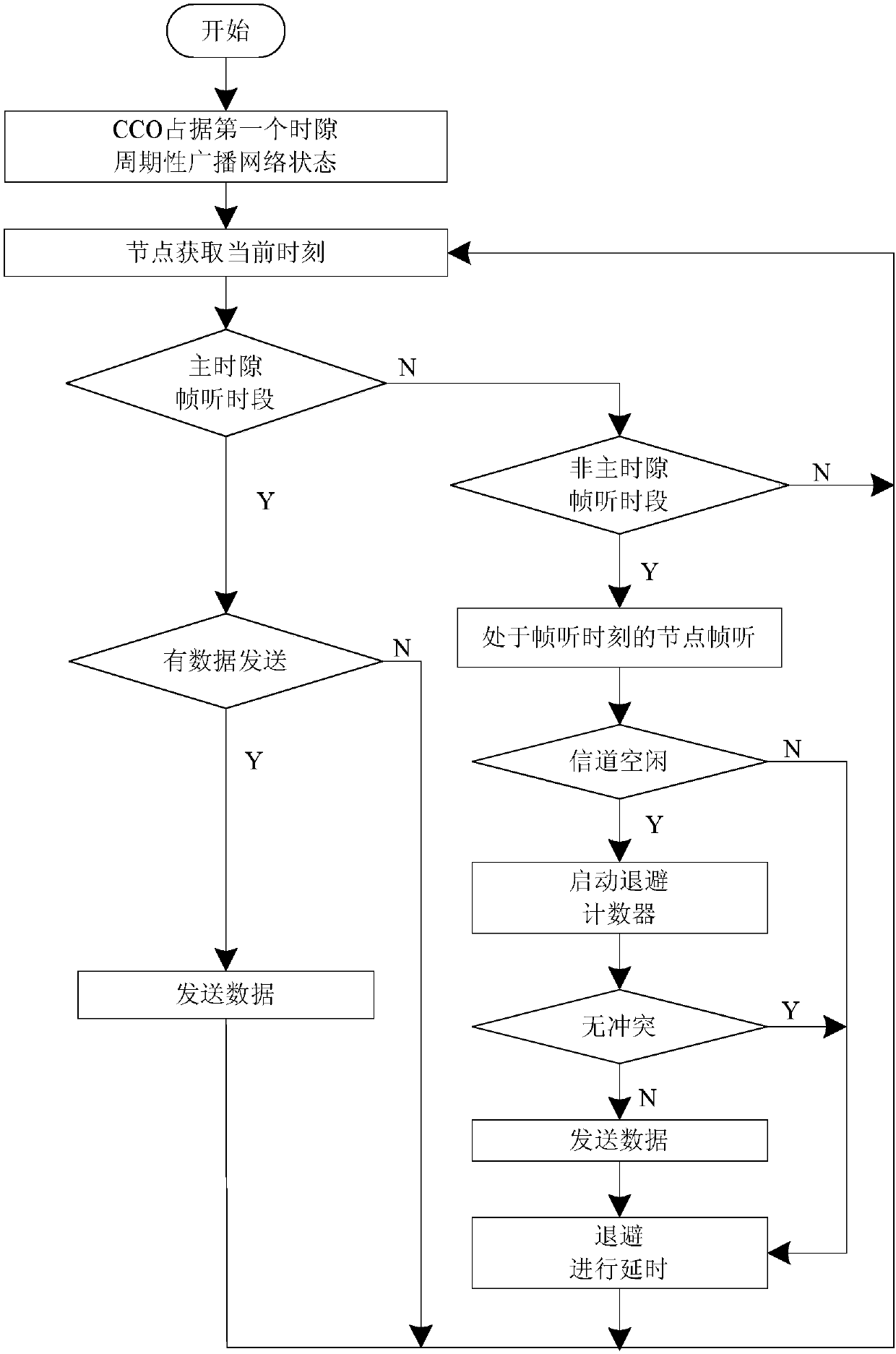
The invention provides a dynamic power line carrier communication channel allocation method based on TDMA and CSMA / CA, and relates to the communication field. The method is used for solving the problems that an existing power line carrier communication channel allocation method is poor in adaptivity and low in channel utilization rate. According to the dynamic power line carrier communication channel allocation method, the TDMA protocol is utilized to allocate channels to all nodes in a communication network, and when an idle time slot is generated after channel allocation is completed, the CSMA / CA protocol is utilized to allocate channels to non-main nodes. The advantages of TDMA and the advantages of CSMA / CA are combined, and the channel utilization rate is increased in the real-time changing process of the network load while network conflicts are reduced. The dynamic power line carrier communication channel allocation method can be applied to multiple fields such as smart home, building automation and rail traffic.
Owner:HARBIN INST OF TECH
Long distance CSMA/CA protocol with QoS assurance
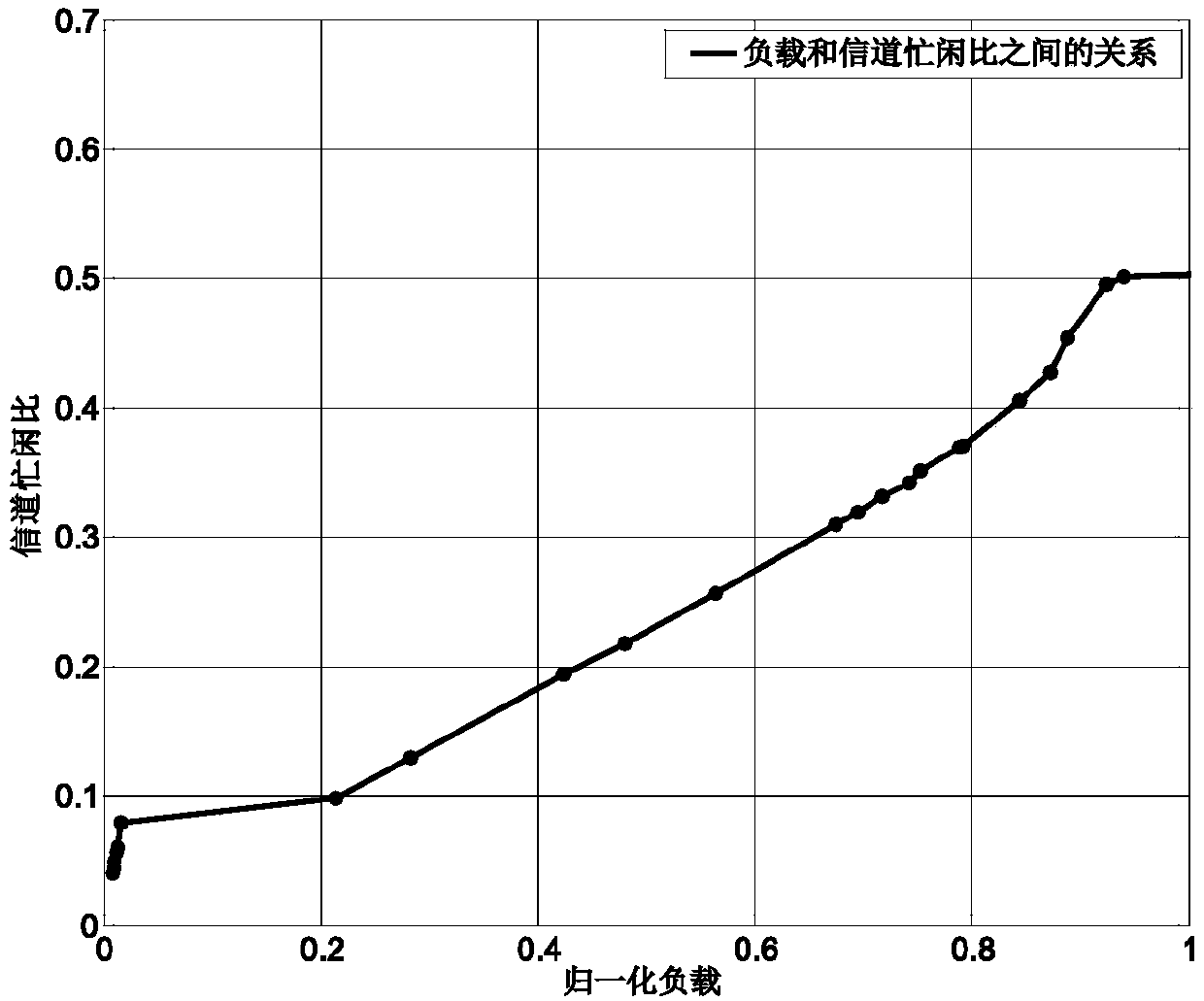
The invention discloses a long distance CSMA / CA (Carrier Sense Multiple Access with Collision Avoidance) protocol with QoS (Quality of Service) assurance, a node in a communication channel executes the following steps: (1) entering a backoff stage after sending of the previous data packet is finished in a sending queue; (2) according to priority conditions of the data packets in the existing sending queue, extracting the data packet with the highest priority and arranging the extracted data packet at the head of the sending queue; (3) calculating a channel busy-to-idle ratio and a priority threshold corresponding to the data packet of the head of the sending queue; (4) after the backoff stage is ended, detecting the busy-to-idle ratio of the current channel, and comparing the priority threshold corresponding to the data packet of the head of the sending queue with the busy-to-idle ratio of the current channel, if the busy-to-idle ratio of the current channel is less than the priority threshold corresponding to the data packet, enabling the data packet to be accessed to the channel and sending the data packet, and returning back to the step (1). According to the long distance CSMA / CA protocol with QoS assurance provided by the invention, performance requirement of the data packet with high priority is satisfied through delay of access of the data packet with low priority, and hereby, a collision probability is reduced and a throughput is improved.
Owner:CHINESE AERONAUTICAL RADIO ELECTRONICS RES INST +1
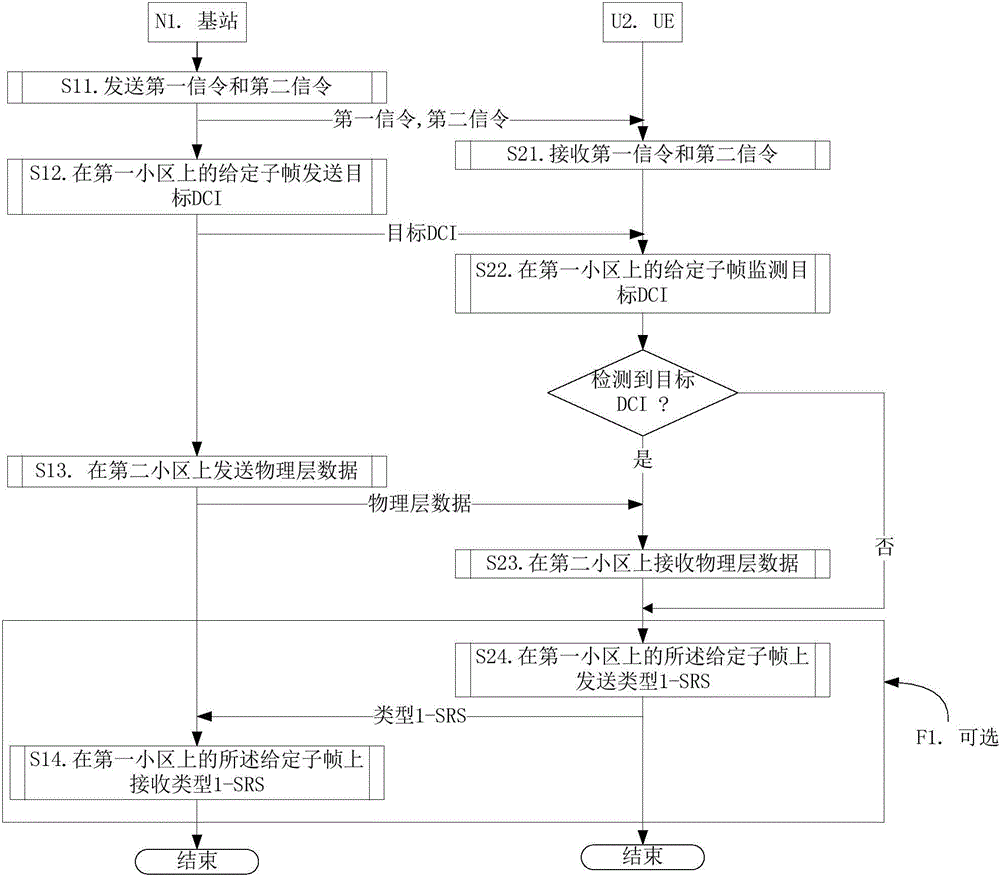
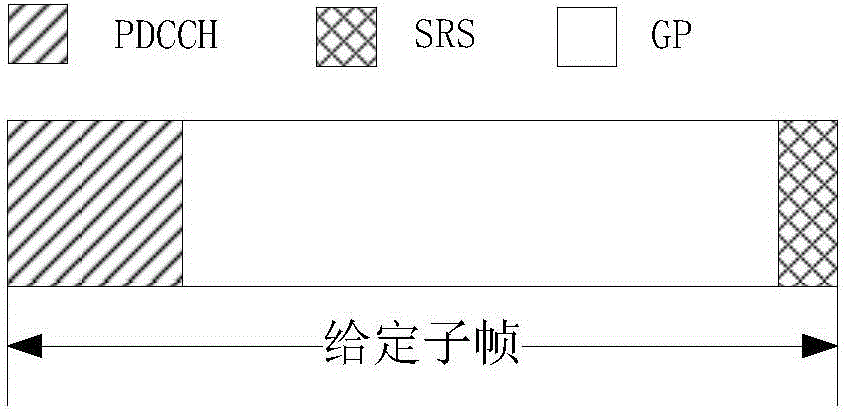
LAA transmission method and device
ActiveCN105306184AAvoid discardingReduce power consumptionTransmission path multiple useCA protocolPhysical layer
The invention provides a LAA transmission method and device. UE firstly receives a first signaling to determine that a given frame of a first cell is set to be a first TDD UL / DL frame structure, and receives a second signaling to obtain a second TDD UL / DL frame structure; a target DCI of a given sub-frame of the given frame in the first cell is monitored; wherein the given sub-frame corresponds to an uplink sub-frame of the first TDD UL / DL frame structure and an un-uplink sub-frame of the second TDD UL / DL frame structure, and the second signaling is a high-layer signaling or a physical-layer signaling. By adopting the technical scheme provided by the invention, the power consumption of the UE is saved, and meanwhile, unnecessary SRS abandonment is avoided; in addition, the invention is compatible with the existing eIMTA and CA protocols and has excellent compatibility.
Owner:SHANGHAI LANGBO COMM TECH CO LTD
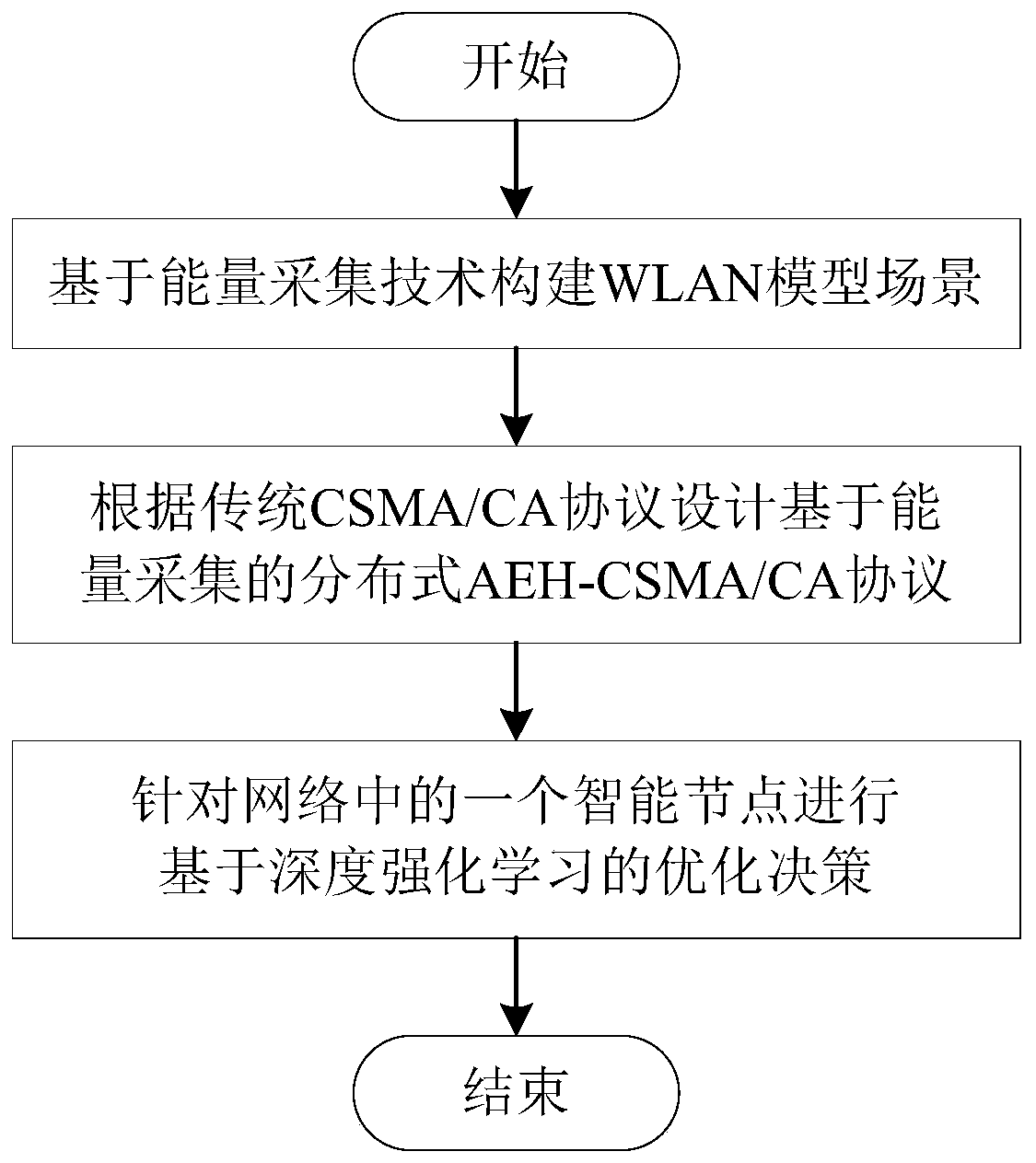
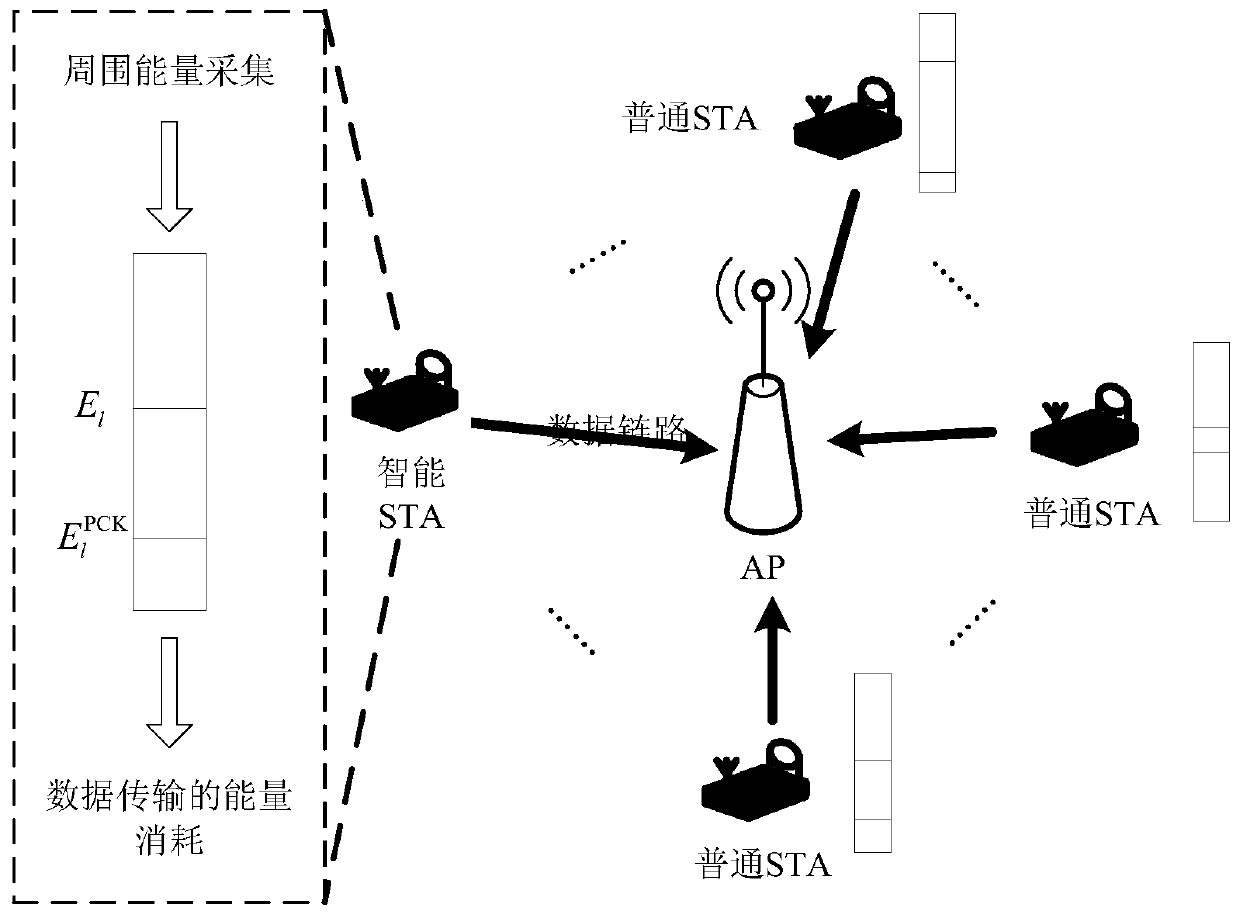
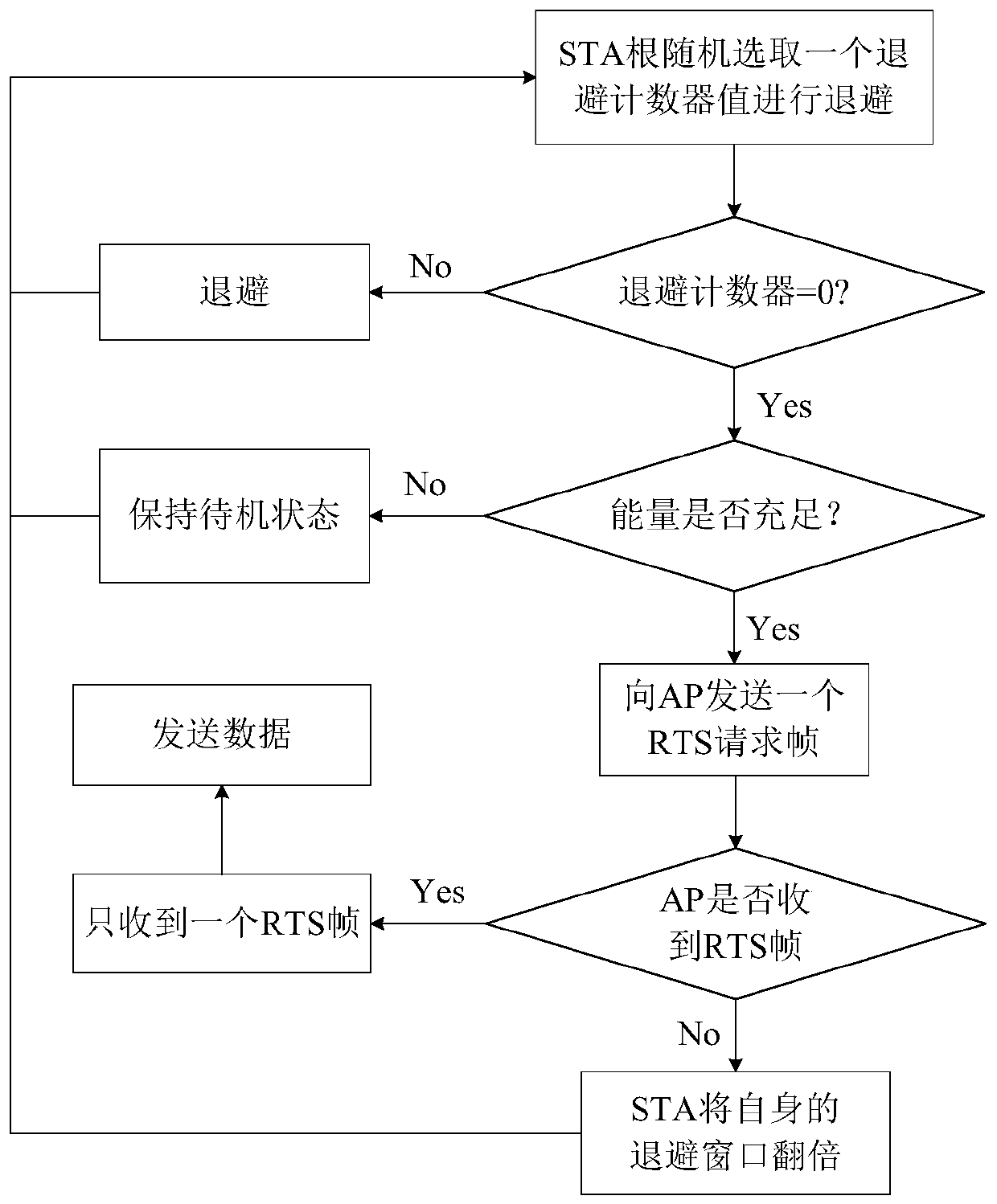
WLAN protocol design and optimization method based on energy collection and deep reinforcement learning
ActiveCN111278161ASolve energy supplyIncrease sending volumeMachine learningNeural architecturesCA protocolProtocol design
The invention discloses a WLAN protocol design and optimization method based on energy collection and deep reinforcement learning. The method comprises the following steps: S1, constructing a WLAN model scene based on an energy collection technology; S2, designing a distributed AEH-CSMA / CA protocol based on energy collection according to a traditional CSMA / CA protocol; S3, performing optimizationdecision based on deep reinforcement learning for the intelligent STA in the network. According to the invention, the energy collection technology and the wireless communication technology are combined, the problem of energy supply of mass equipment of the Internet of Things in the future is effectively solved, and the willingness of a green network is realized. Meanwhile, based on the deep reinforcement learning technology, intelligent decision making is carried out on the intelligent STA in the network, so that the energy outage probability of the intelligent STA is reduced, the data sendingamount is increased, and the wireless network is more intelligent.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
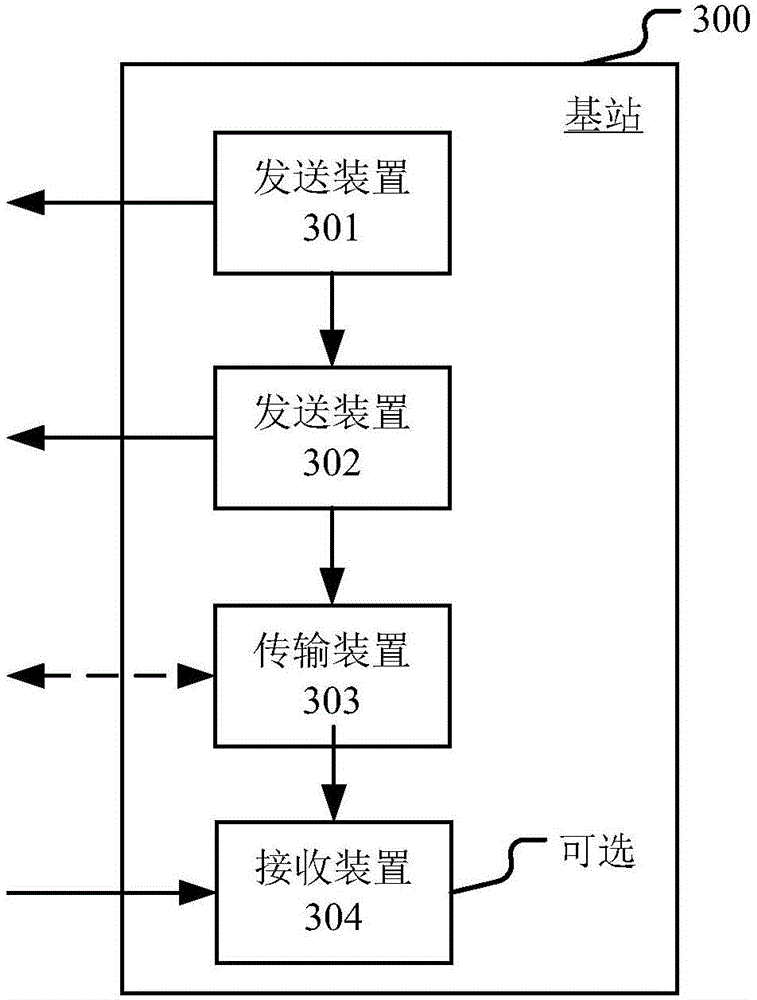
Congestion control in a communication network based on the csma/ca protocol
ActiveUS20100260046A1Raise priorityEnhanced congestion controlError preventionTransmission systemsCA protocolStructure of Management Information
The present invention relates to a congestion control method for a communication system supporting layered radio channel structure for communication between at least a first communication device and a second communication device, the layered structure comprising at least a physical layer and a medium access layer. The communication system is arranged to offer a first type of service with a first priority order and a second type of service with a second priority order, in the communication system messages comprising a preamble and a payload can be transmitted between devices, each message being separated by at least a period corresponding to a minimum allowable period between two messages. In the method the first communication device first (a) generates (301) a physical layer message pertaining to the first type of service; (b) senses (303) the radio channel idle for at least a period corresponding to the minimum allowable period between two messages; and (c) transmits (305) the physical layer message comprising a special preamble indicative of the type of service the message pertains, wherein the content of the preamble is arranged to be detected by the second communication device within a communication range irrespective of the decoding state of the payload of the transmitted message.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
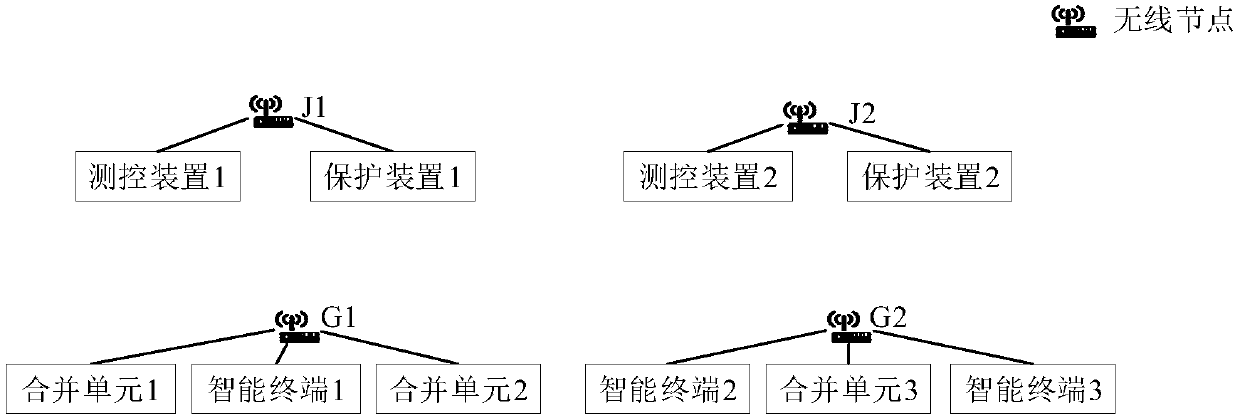
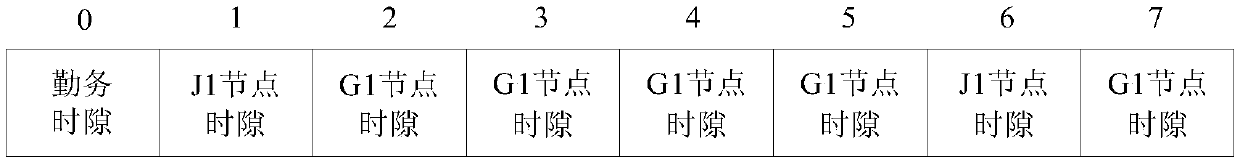
Low delay intelligent substation wireless communication mechanism
InactiveCN109548165AImprove resource utilizationGuaranteed Priority DeliveryWireless communicationCA protocolBusiness requirements
The invention discloses a low delay intelligent substation wireless communication mechanism. The problem that message transmission delay is instable in an intelligent substation wireless network is mainly solved. The scheme comprises the fact that through utilization of a TDMA protocol, according to SV (Sampled Value) and GOOSE (Generic Object Oriented Substation Event) periodic business requirements of a substation, fixed time slots are allocated to all nodes in a communication network based on a periodic fair allocation method; and when leisure occurs in the fixedly allocated time slots, through utilization of a CSMA / CA protocol and through importing of message priorities, and channels are competed for sudden business such as barring business or other uncertain business. The invention provides a wireless communication mechanism for intelligent substation equipment. According to the low delay intelligent substation wireless communication mechanism based on TDMA and CSMA / CA mixture, delay stability of periodic messages in the intelligent substation wireless network is ensured, transmission of sudden messages is ensured, and a channel utilization rate is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM +1
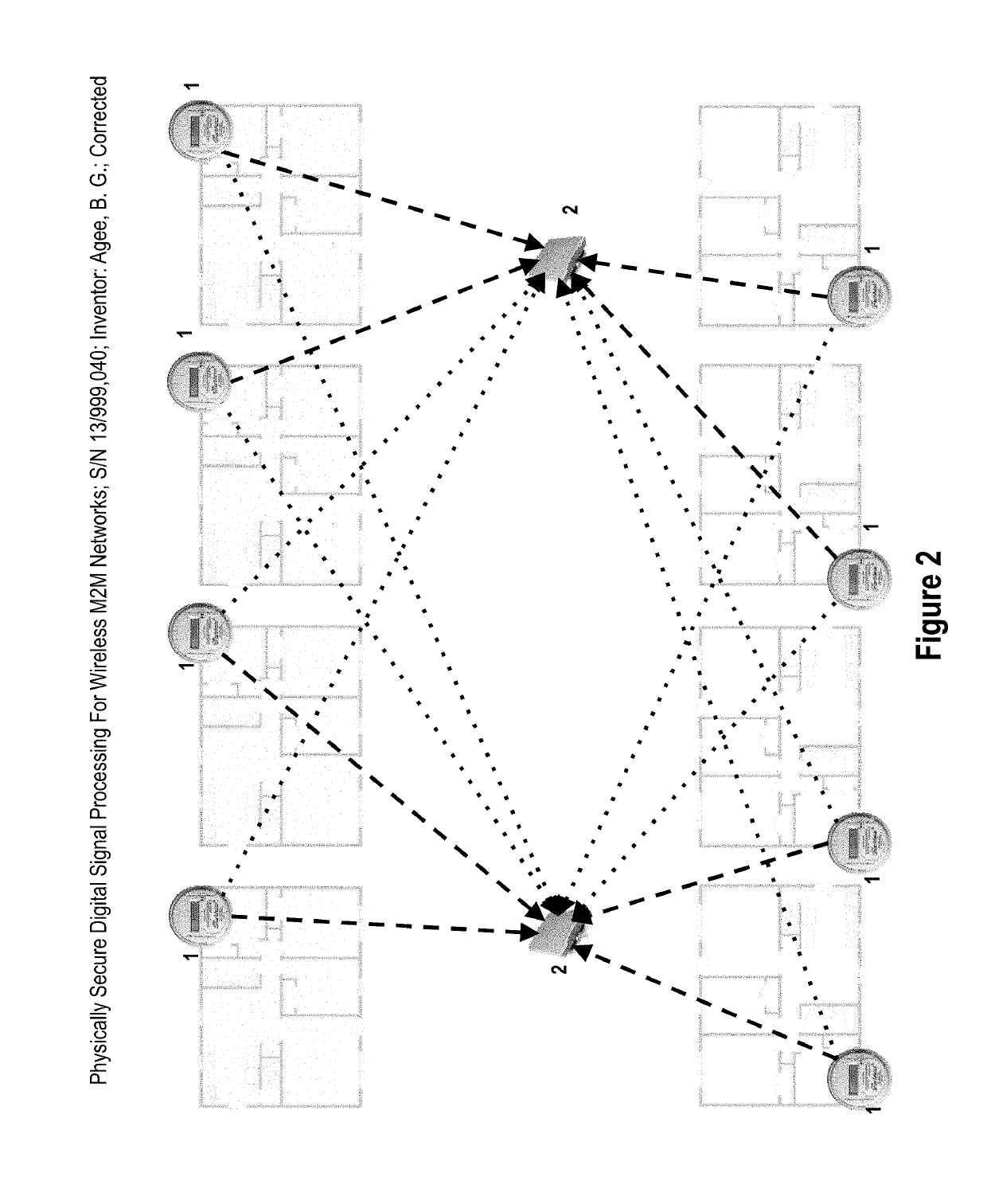
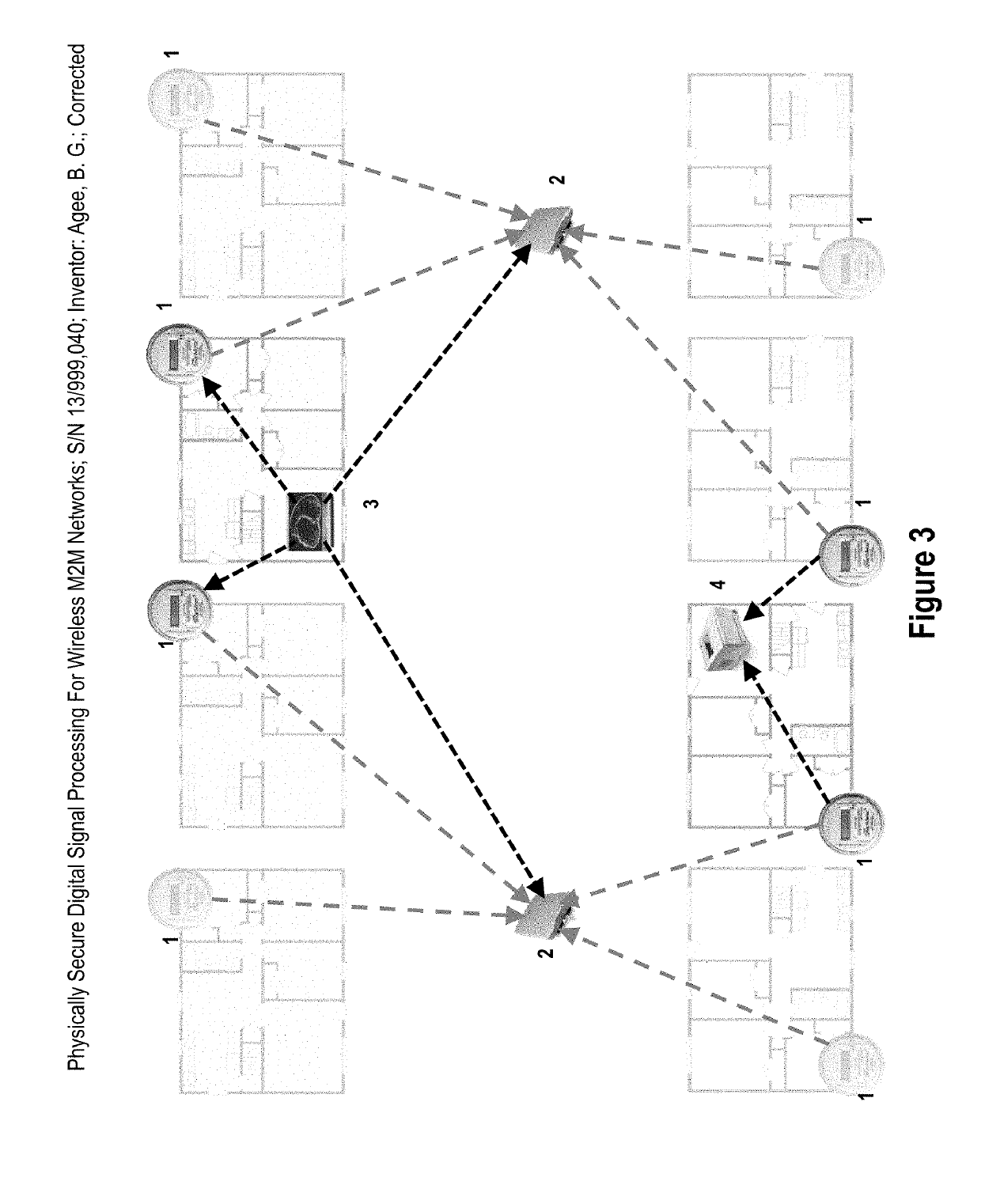
Generation of signals with unpredictable transmission properties for wireless M2M networks
ActiveUS20190320303A1Avoid overheadReduce data transferTransmissionMultiplex code typeCA protocolWireless mesh network
A method and apparatus for generation of signals with unpredictable transmission properties allowing physically secure, unscheduled and interference-resistant communication over machine-to-machine (M2M) networks is claimed. A physical dwell structure comprising time slots and frequency channels is established, and a combination of unpredictable physical dwells, spread spectrum modulation formats employing unpredictable spreading vectors, and additional physical properties allowing unpredictable selection of intended receivers is described. These unpredictable transmission properties enable receivers employing blind detection and signal separation techniques to detect and extract transmissions intended for the receive, and excise transmissions not intended for the receiver, as part of the despreading procedure, and even if those transmissions are received at a much higher power level than the intended transmissions. The resultant system eliminates the ability for an adversary to predict and override M2M transmissions; allows reception of ad-hoc transmissions in dense environments without scheduling, CSMA / CA protocols, or feedback paths enabling scheduling, and allows macrodiverse reception of transmissions at networks of connected receivers, thereby providing additional efficiency and security improvements by exploiting the route diversity of the network.
Owner:AGEE BRIAN G
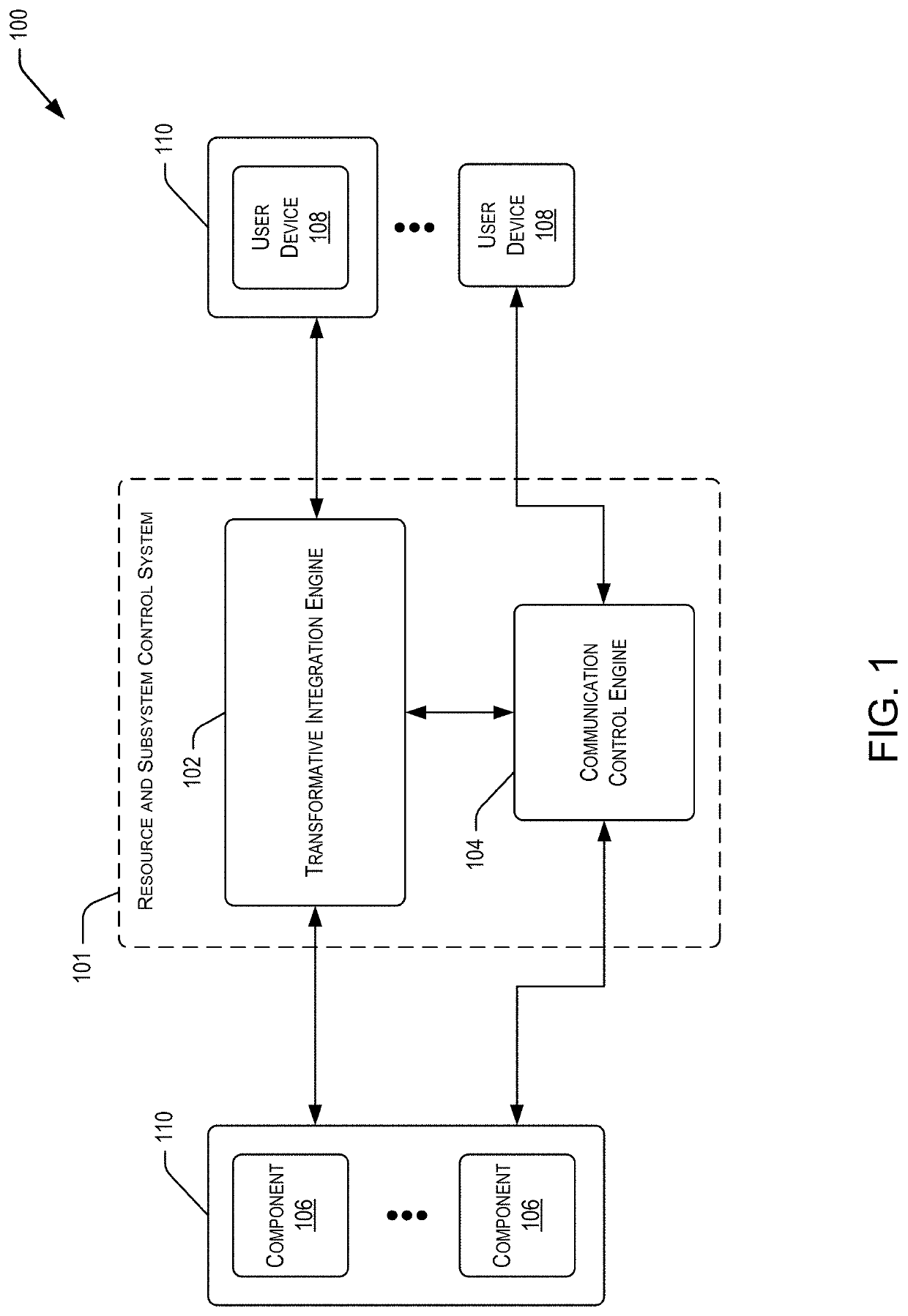
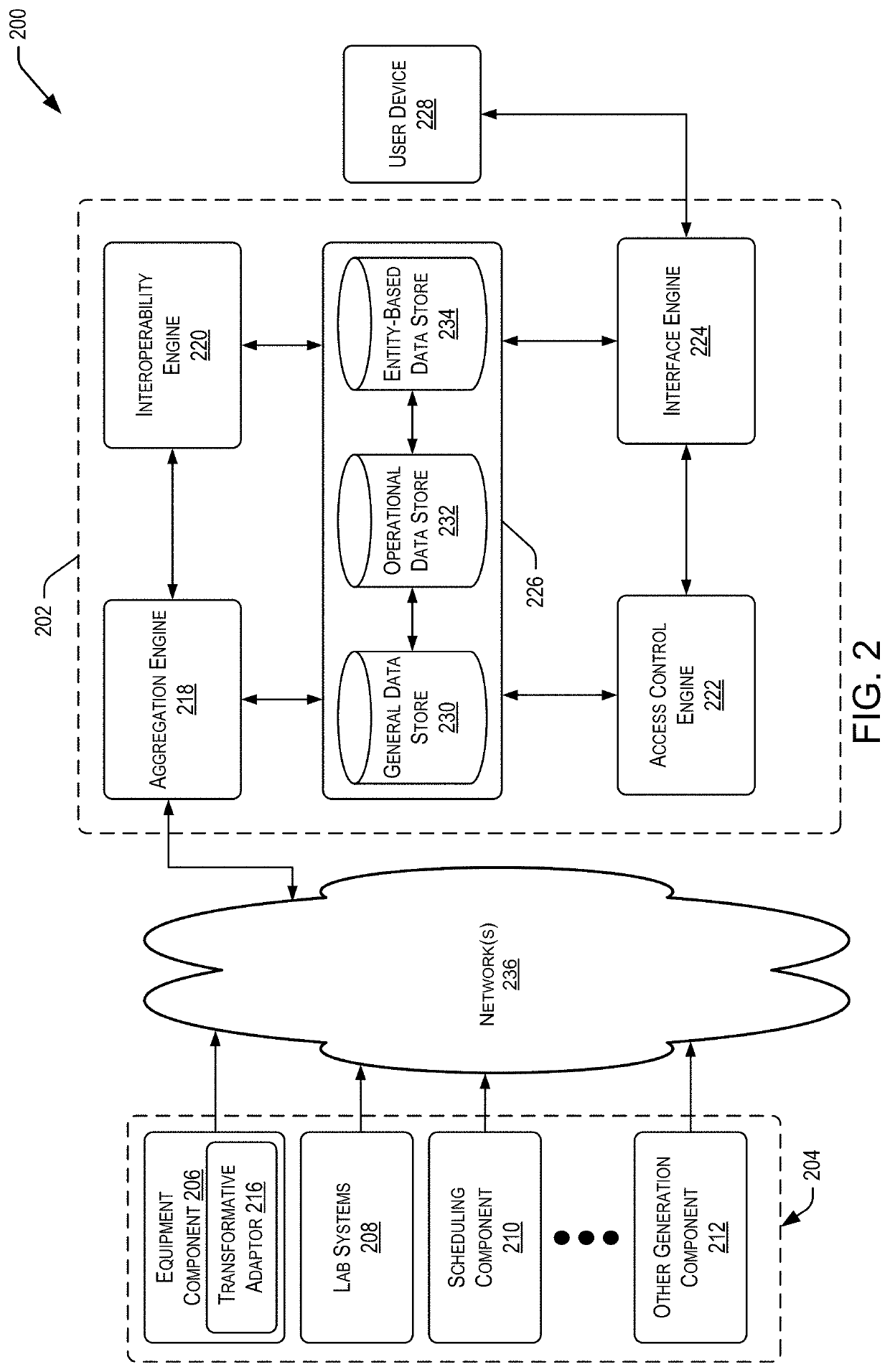
Systems and methods for multi-tier resource and subsystem orchestration and adaptation
Systems, methods, and machine-readable media to orchestrate process-performing resources and process protocols particularized to individual resources and loads are provided. Data changes in the data streams may be detected and identified. Data items from the data streams may be aggregated. Protocols that include parameter constraints according to specifications of process performance and / or operation performance may be identified. Operation-performing resources may be modeled with metrics being a function of protocols and consolidated data portions. A composite may be created that specifies a configuration a subsystem. The composite may be transmitted, and allocation of operation-performing resources to perform the defined process in accordance with the selected protocols may be controlled.
Owner:CHCA
Method and system for realizing TCP (Transmission Control Protocol) full-offload IP (Internet Protocol) cores for multi-connection management
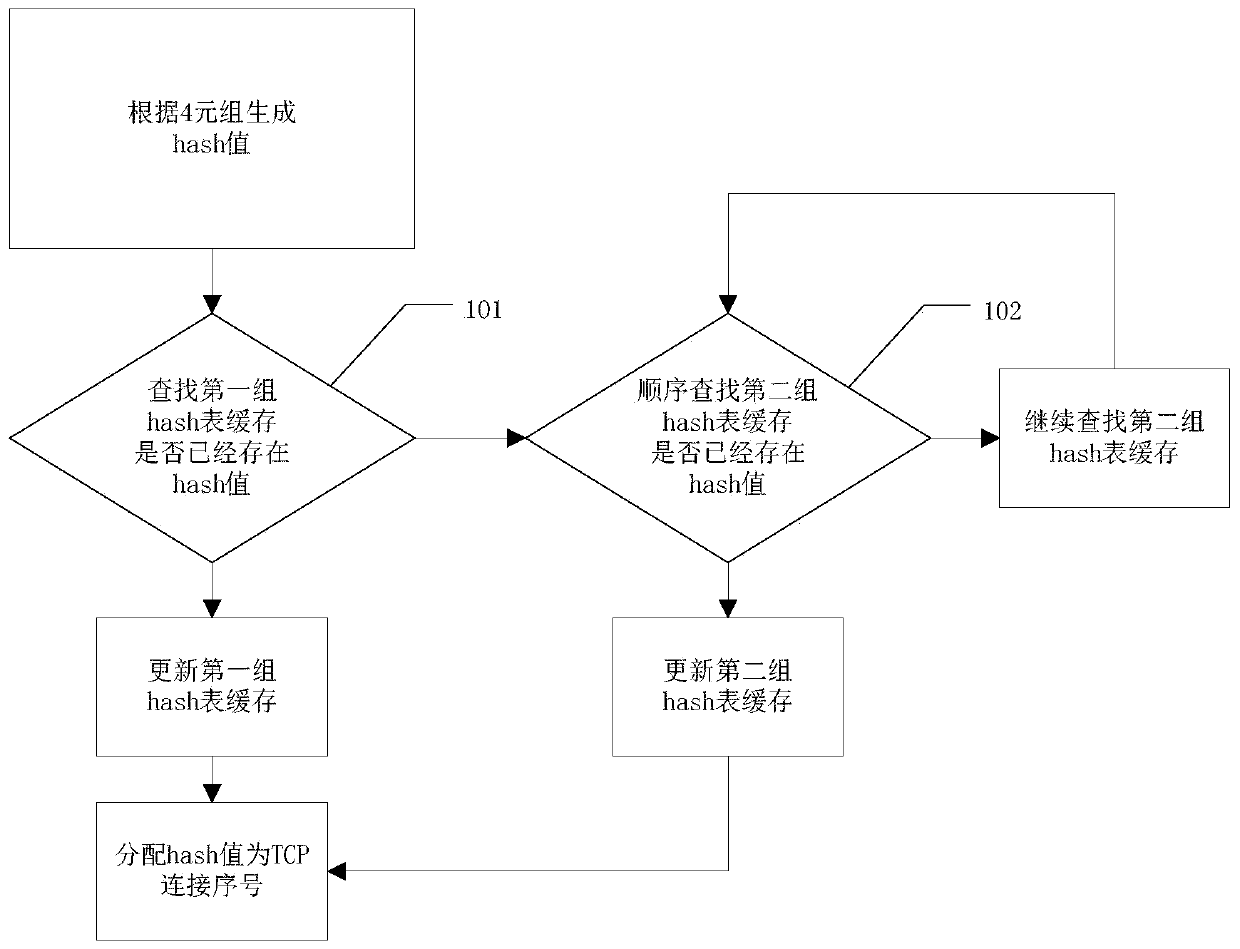
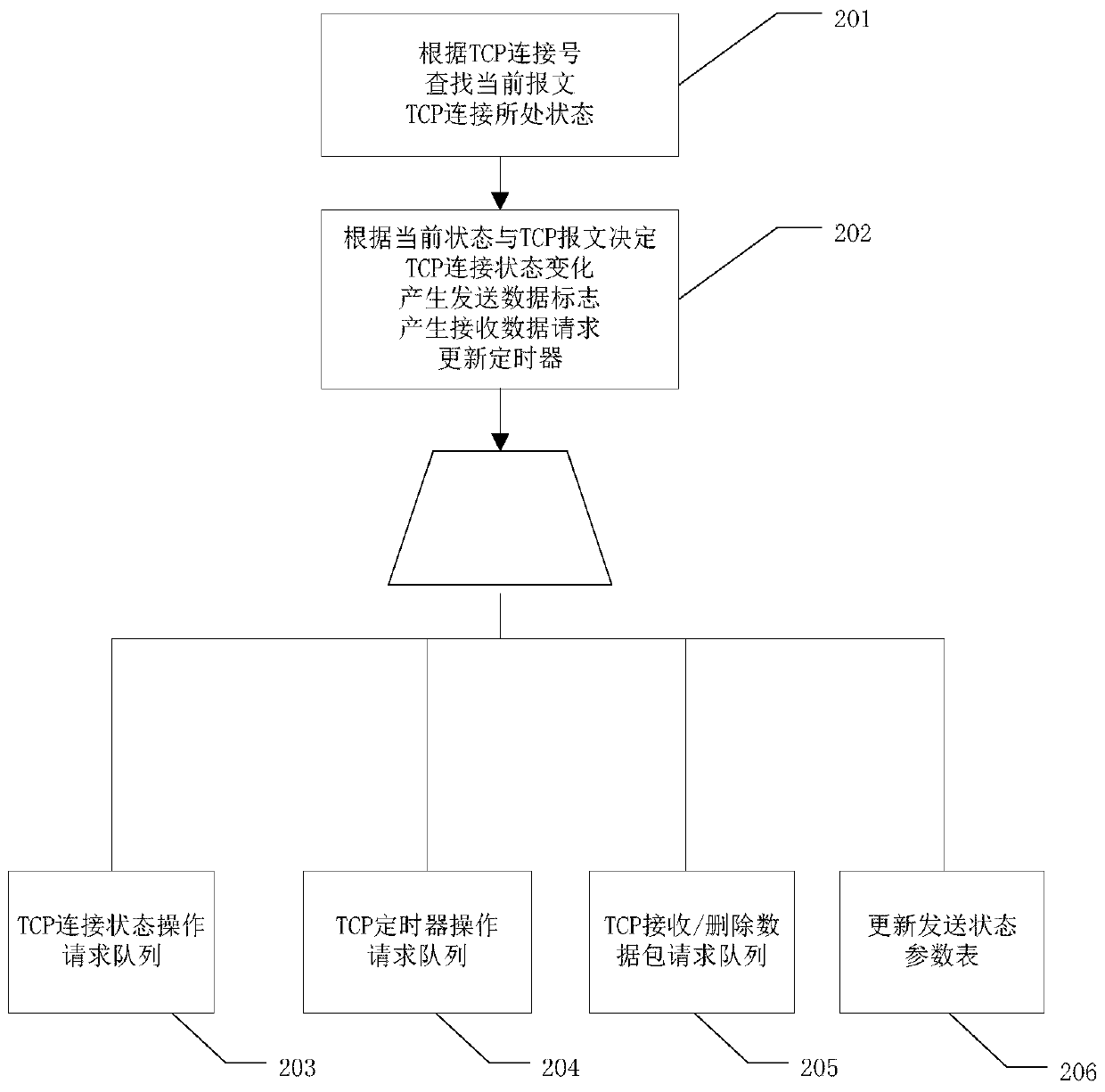
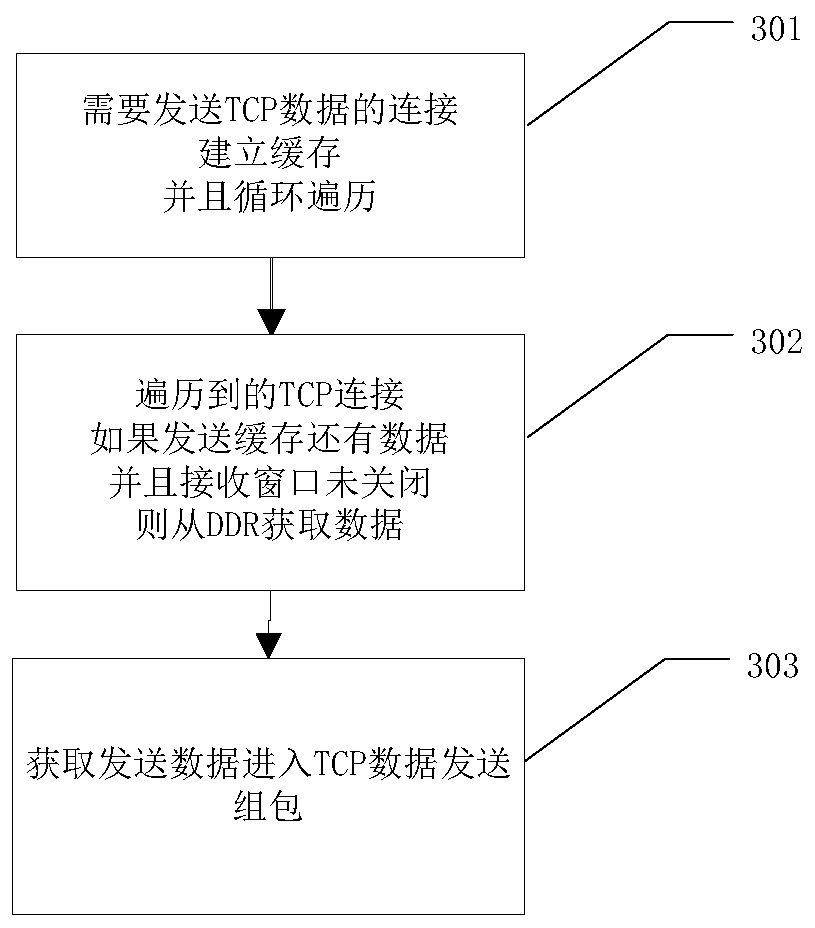
The invention provides a method and a system for realizing TCP (Transmission Control Protocol) full-offload IP (Internet Protocol) cores for multi-connection management. The method comprises a hash value generation step, a connection management step, a sending management step and a timer management step. The IP core for realizing TCP unloading can be connected with different types of buses to serve as a protocol processor; by means of the IP core, TCP network data can be obtained on FPGA hardware, and the function of supporting network control and data receiving and sending is achieved throughthe data connection algorithm acceleration module, the dynamic reconstruction module and the like.
Owner:EAST CHINA INST OF COMPUTING TECH
Protocol message forwarding method and communication equipment
ActiveCN102316022AGuaranteed uptimeOvercome issues affecting normal protocol packetsData switching networksCA protocolCommunication device
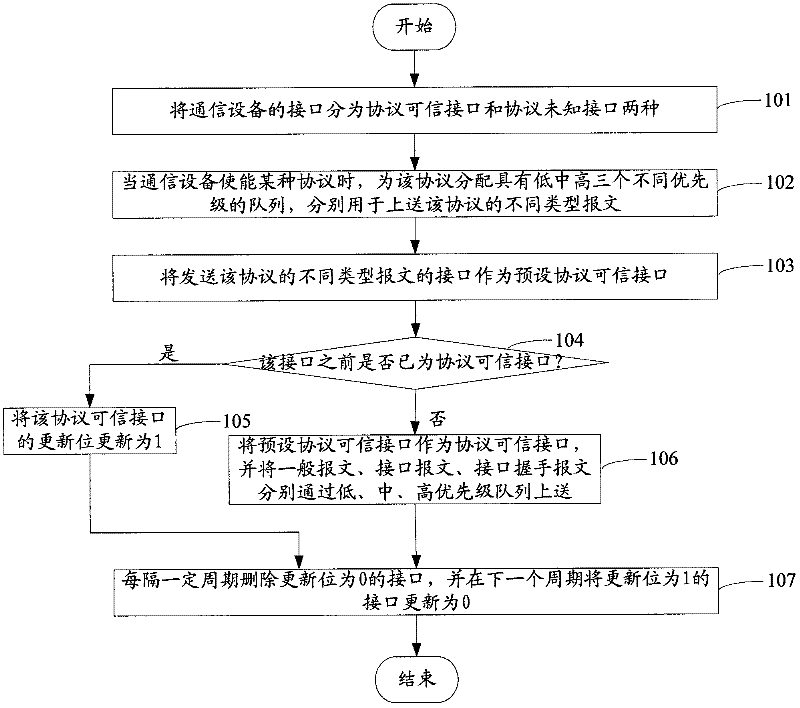
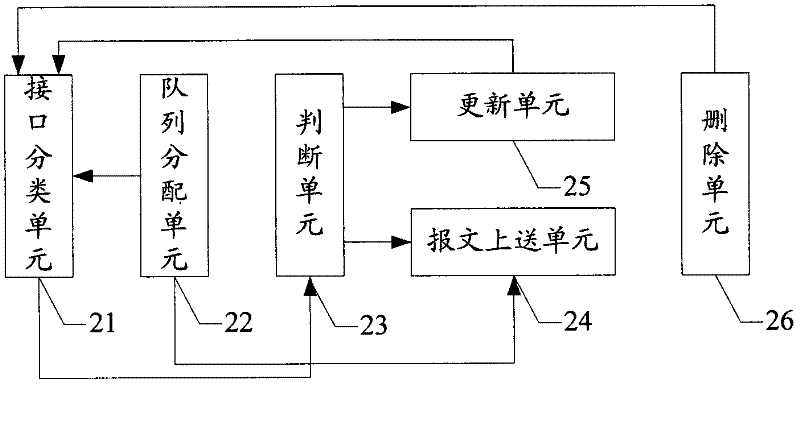
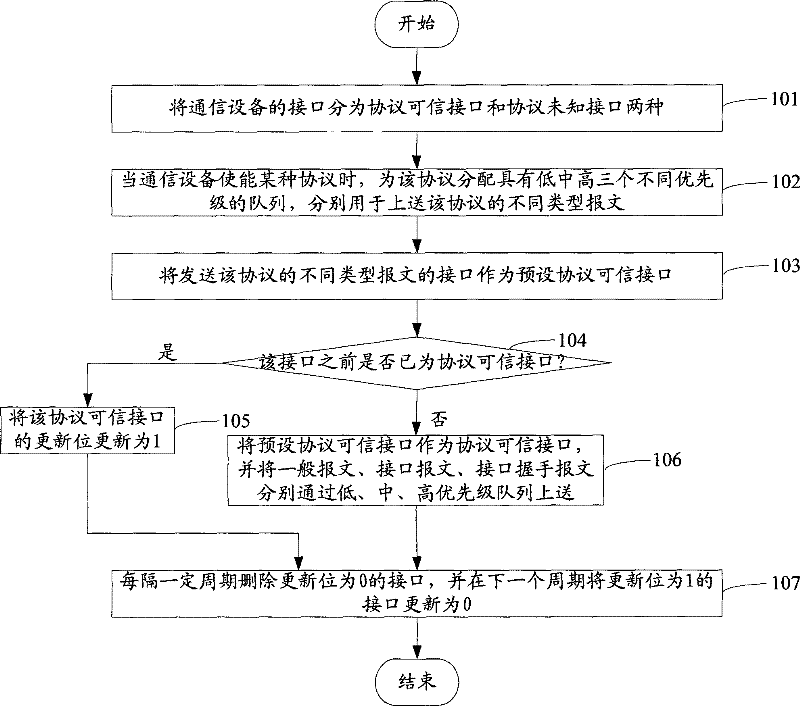
The invention discloses a protocol message forwarding method. The method is characterized in that: dividing interfaces of communication equipment into a trustworthy protocol interface and an unknown protocol interface, wherein the trustworthy protocol interface is the interface which establishes protocol interaction; when the communication equipment enables a protocol, distributing queues with n different priorities for the protocol, wherein the queues are used to push different types of messages of the protocol and the n is a natural number which is great than or equal to two; taking the interface which sends the different types of messages of the protocol as the preset trustworthy protocol interface; determining whether the preset trustworthy protocol interface is the trustworthy protocol interface; if the preset trustworthy protocol interface is not the trustworthy protocol interface, taking the preset trustworthy protocol interface as the trustworthy protocol interface and pushing the different types of messages of the protocol respectively from the n different priority queues. The invention also discloses the communication equipment used in the protocol message forwarding. By using the method and the equipment of the invention, abnormal operation of the communication equipment caused by forging the protocol messages can be avoided.
Owner:NEW H3C TECH CO LTD
Design method of CSMA/CA protocol for M2M network
ActiveCN104394599AHigh frequencyEarly energy-saving operationPower managementHigh level techniquesCA protocolHigh energy
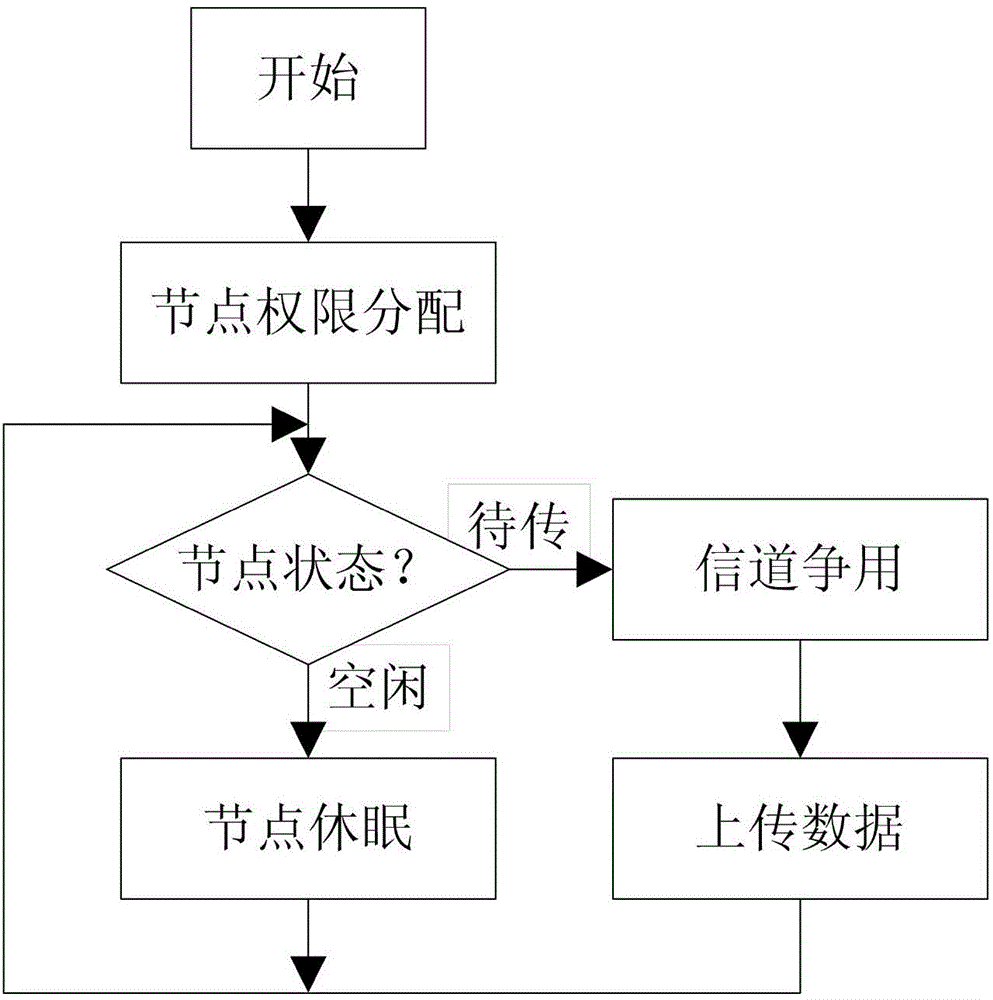
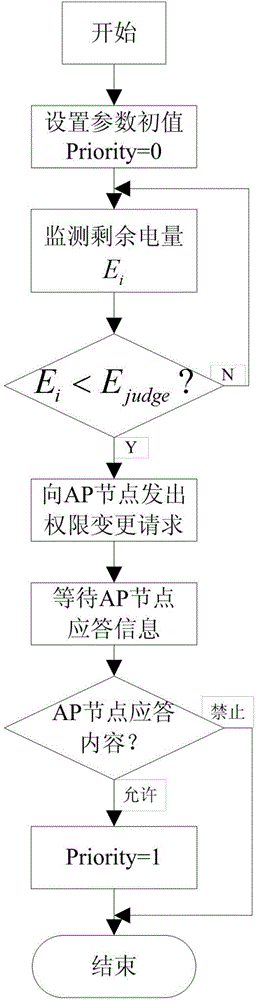
The invention discloses a design method of a CSMA / CA (carrier sense multiple access / collision avoidance) protocol for a M2M network, and the method is characterized in that energy consumption of a node with high energy consumption is reduced in the M2M network, and the transmission reliability of data in the M2M network can be ensured when the life cycle of the mentioned node is prolonged, thus the method can be applied to the CSMA / CA protocol of the M2M network. The method comprises steps of: step 1: assigning permission to the monitoring point in the M2M network; step 2: periodically detecting the operation status of the monitoring node in the M2M network, performing step 3 under the idle state of the monitoring node, and performing step 4 under the to-be-transmitted data state of the monitoring node; step 3: performing dormancy operation to the monitoring node, and performing the step 2 after some interval of time; step 4: performing signal channel contention operation to the M2M network, acquiring signal channel use right by the monitoring node, and performing step 5; step 5: uploading the data to the monitoring node, and performing the step 2 after uploading the data.
Owner:NANJING UNIV OF POSTS & TELECOMM
Safety certification method for smart grid AMI system
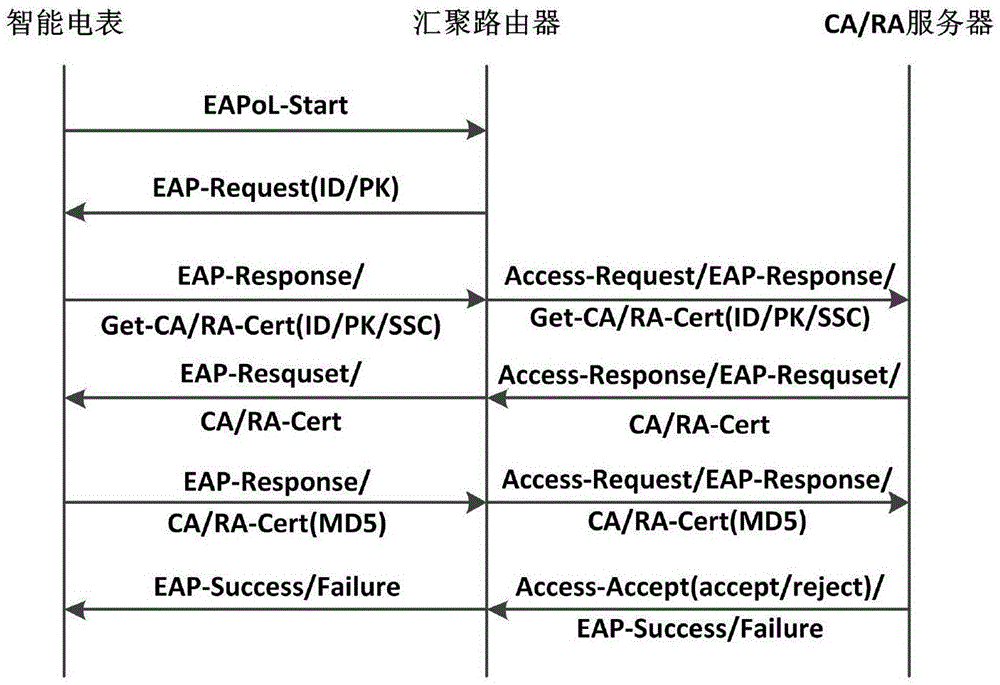
InactiveCN105656633AImprove efficiencyHigh speedUser identity/authority verificationComputer hardwareSmart grid
The invention relates to a safety certification method for a smart grid AMI system. The safety certification method is suitable for the IEEE802.1x protocol certification method based on SCEP expansion of the smart grid AMI system, the SCEP is used as the certification mode of a smart grid terminal for accessing the AMI system and is used as an IEEE802.1x protocol expansion certification mode, namely, under the control of the IEEE802.1x protocol, SCEP certification can be only carried out on the non-certificated smart grid terminal by an uncontrolled port of the IEEE802.1x protocol; and the certificated smart grid terminal can access the AMI system through a controlled port of the IEEE802.1x protocol. The safety certification method provided by the invention is suitable for simple certificates and is used for guaranteeing to completely isolate the AMI system resources before the smart terminal is authorized to access the AMI system.
Owner:TIANJIN UNIV
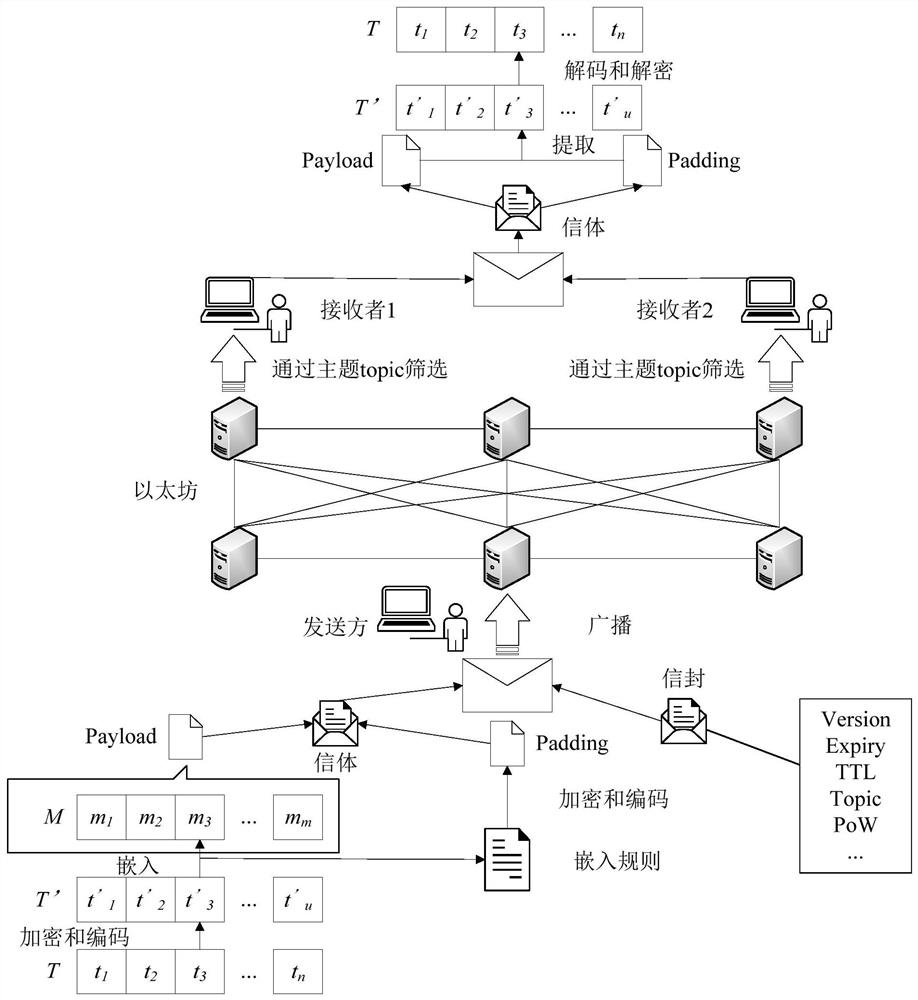
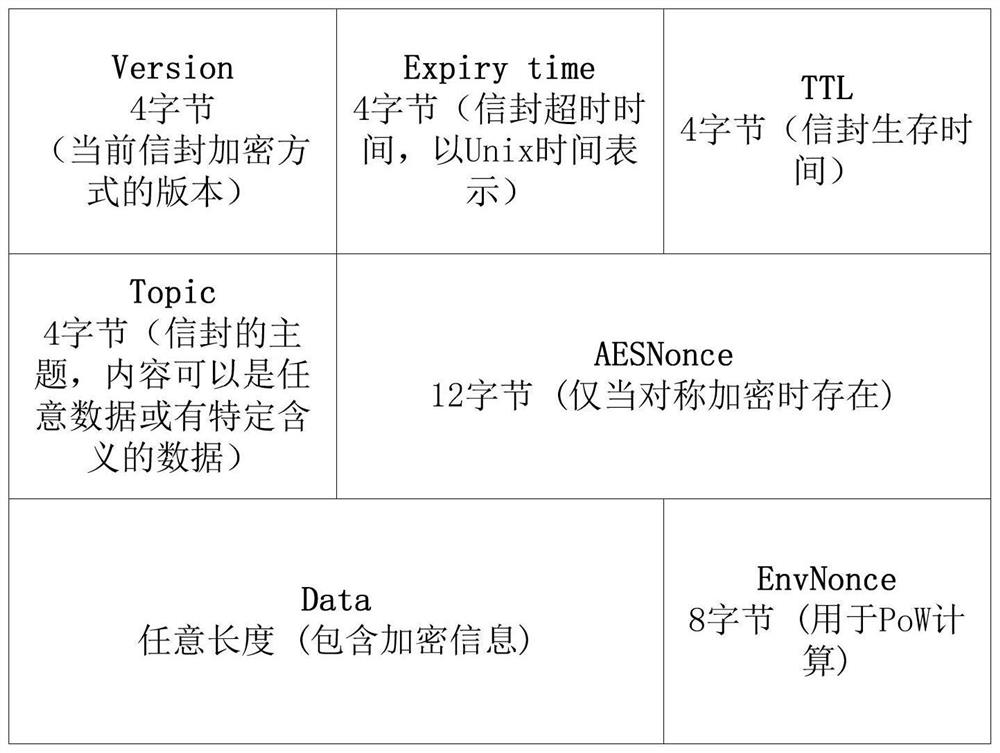
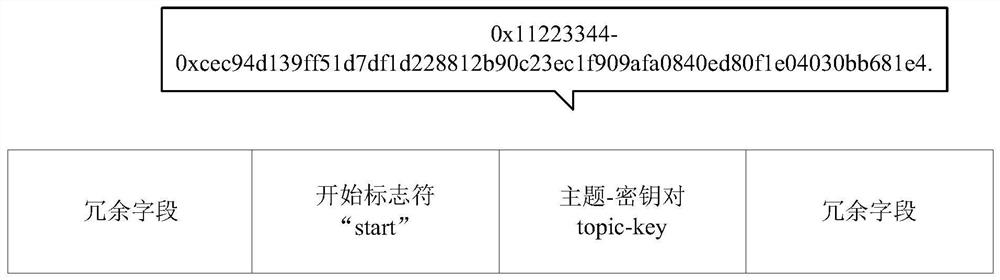
Ethereum covert communication method based on whisper protocol
The invention discloses an Ethereum covert communication method based on a whisper protocol. The method comprises the steps: coverting and interacting a subject-key pair; encrypting and encoding the message T to be transmitted to obtain T '; randomly generating a statement as an effective carrier payload of a message body in a whisper protocol; carrying out character matching on the T' and a carrier, and recording index information of matched characters; encrypting the index information, and expanding the index information to enable the total length of the message to be a multiple of 256 bytesand serve as an expanded part padding of a message body in a whipper protocol; setting structure information of the whisper letter, setting a theme of the letter as an interactive theme, and encrypting the interactive theme; broadcasting letters to achieve information transmission; enabling the receiver to screen letters through the theme, and decrypt the letters by using the corresponding secretkeys to obtain payload and padding; and decrypting the padding to obtain decrypted information, namely an index, and performing information restoration in combination with the effective carrier. Themethod provided by the invention is high in security, has good anti-interference performance, tamper resistance and detection resistance, and avoids unnecessary consumption when a receiver screens data packets in combination with a theme mechanism of the whisper.
Owner:YANGZHOU UNIV
Data transmission method and system in wireless fidelity network
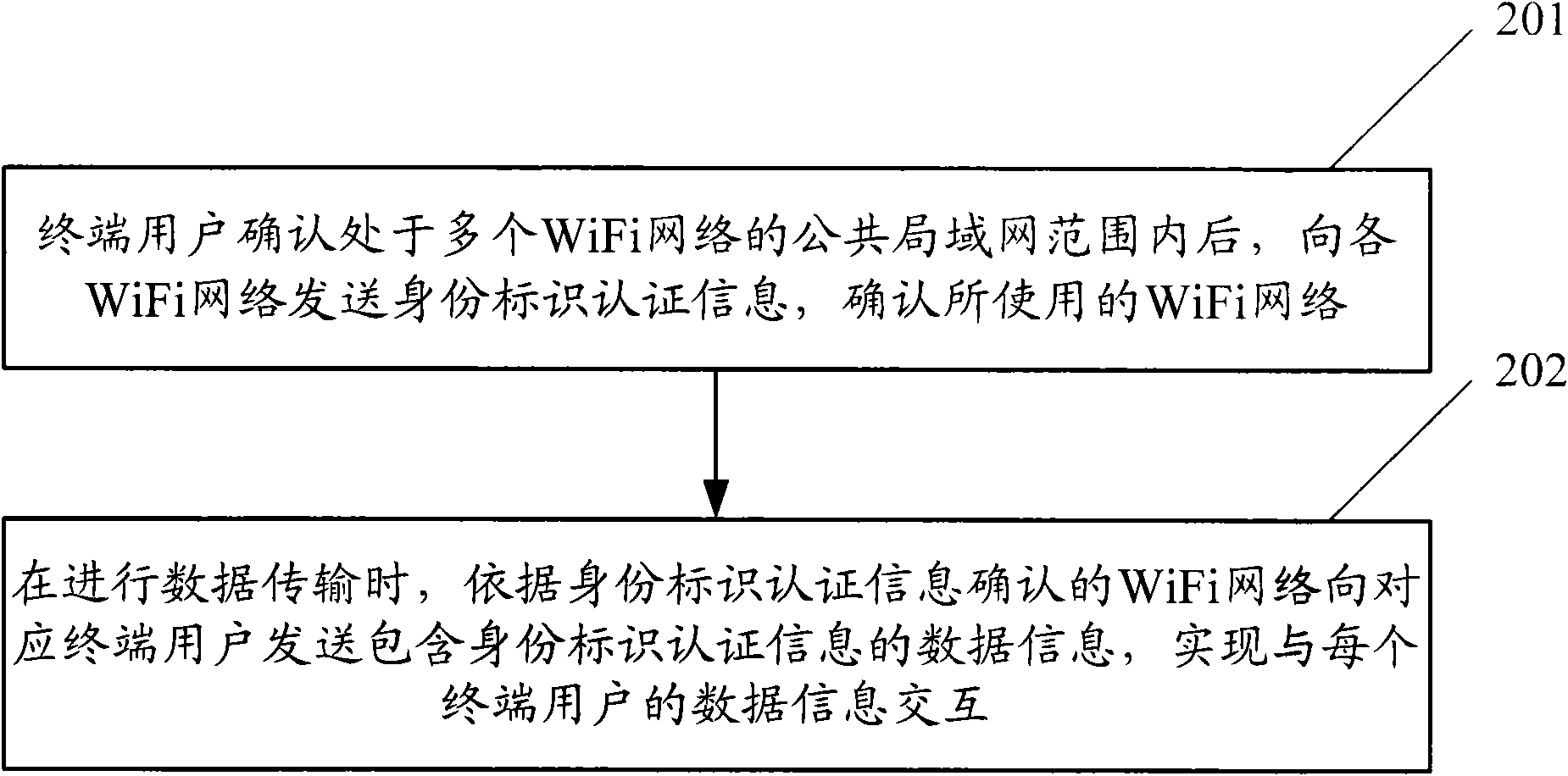
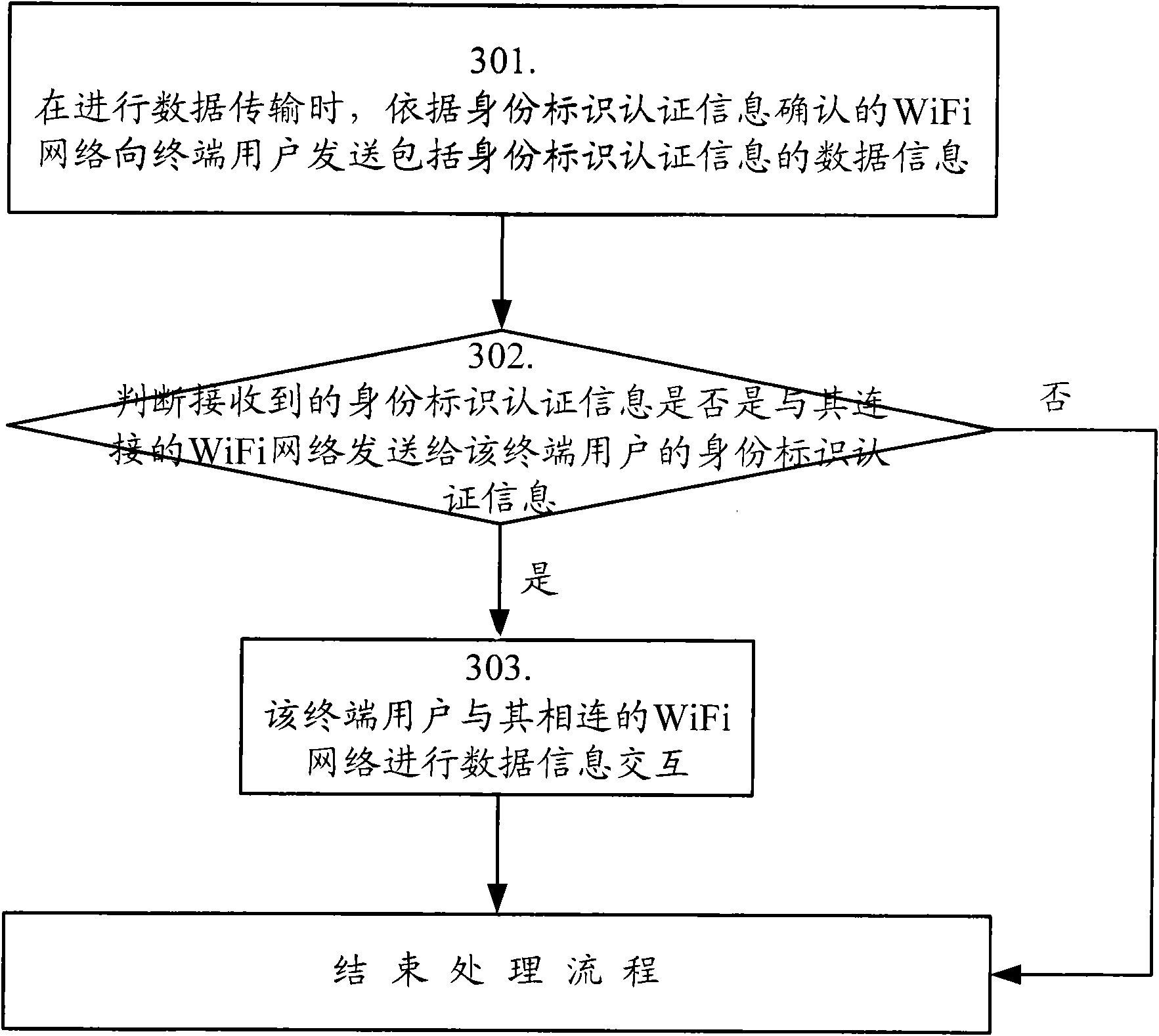
ActiveCN101820304AAvoid conflict collisionImprove interaction efficiencyNear-field transmissionSecurity arrangementCA protocolData information
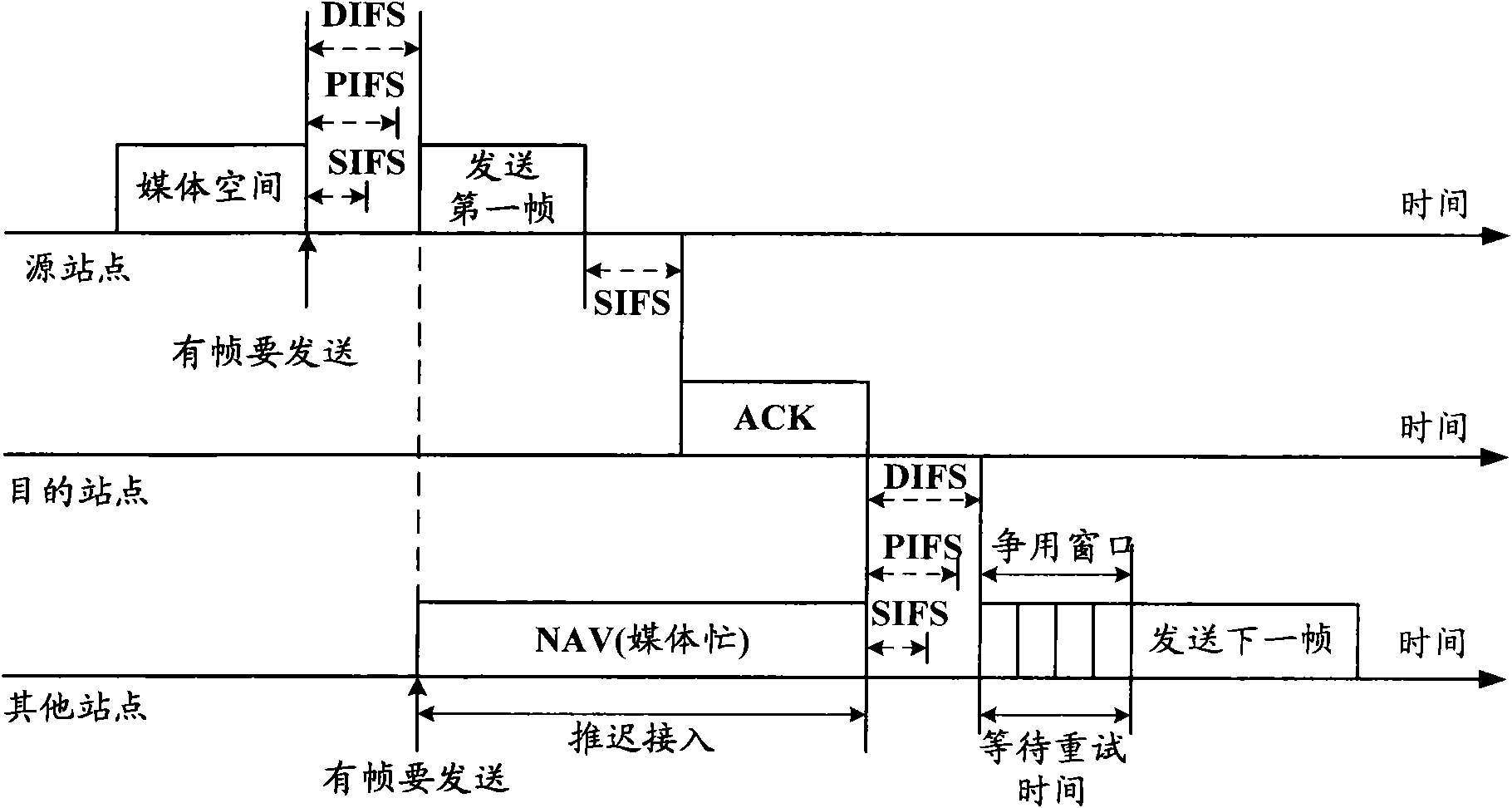
The invention discloses a data transmission method in a WiFi network, which comprises the following step: when data transmission is carried out, sending data information comprising identity authentication information to a corresponding terminal user according to a WiFi network confirmed by the identity authentication information. Meantime, the invention also discloses a data transmission system in the WiFi network. The method and system of the invention can effectively avoid collision in the WiFi network, and can solve the problem of avoiding data collision depending on increasing interframe space in the working process of a CSMA / CA protocol, thereby improving the interactive efficiency between a network side and a user terminal.
Owner:ZTE CORP
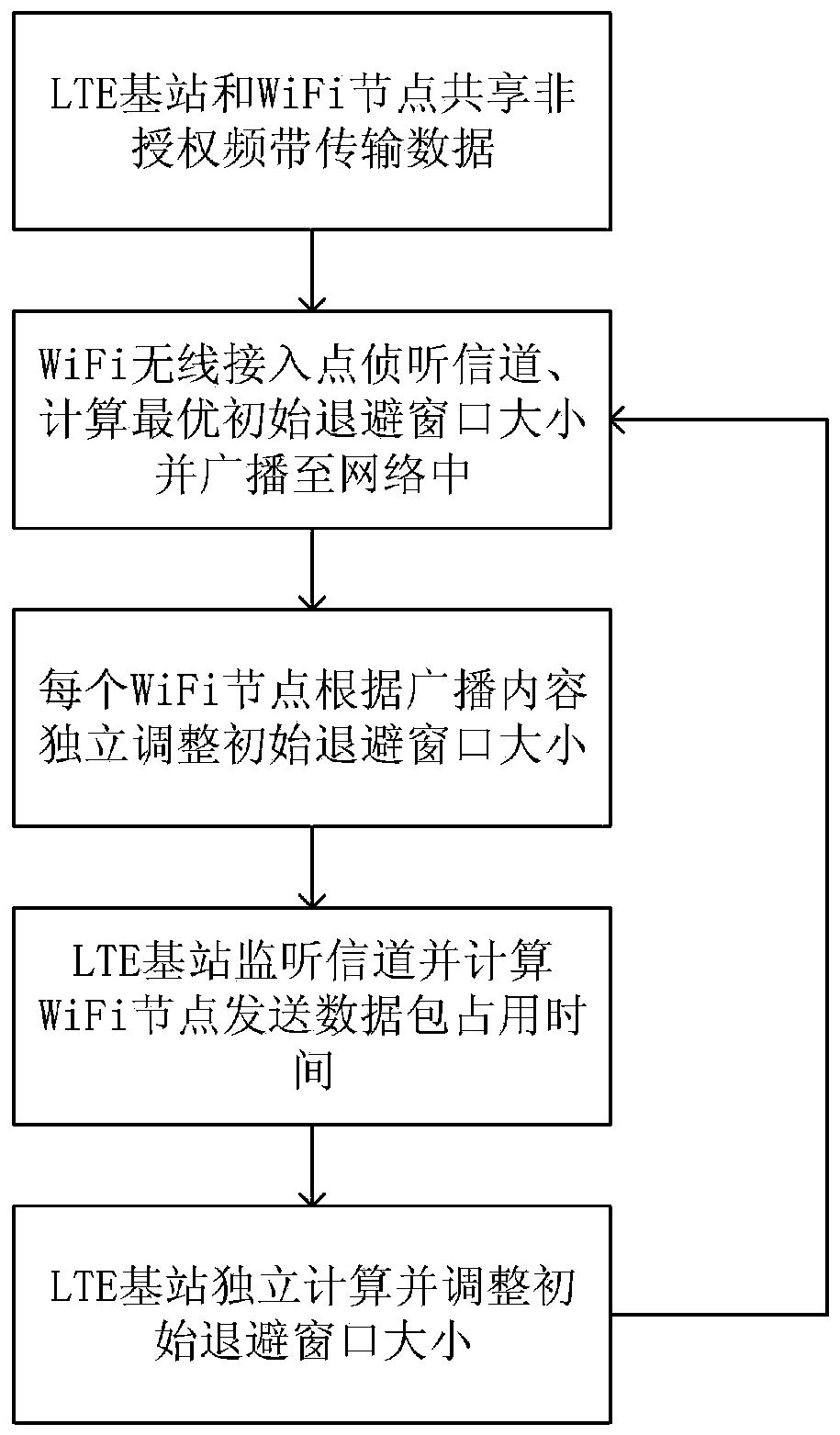
Backoff window distributed adjustment method for LTE and WiFi coexisting network
The invention discloses a distributed adjustment method for a node initial back-off window when an unlicensed frequency band is shared by LTE and WiFi. The LTE base station and the WiFi node share anunlicensed frequency band; the WiFi nodes comprise a WiFi wireless access point and a WiFi user node; the WiFi node accesses a channel by using a CSMA / CA protocol; and the LTE base station accesses the channel by using an LBT and backoff mechanism, and the LTE base station and the WiFi node adjust respective initial backoff window sizes in a distributed manner according to respective observed information so as to maximize the throughput of the LTE and WiFi coexisting network under the condition of meeting 3GPP fair limitation.
Owner:SUN YAT SEN UNIV
Method for network congestion control of power line carrier communication
InactiveCN106817150AGuaranteed priorityGuaranteed reliabilityPower distribution line transmissionData switching networksCA protocolSuccessful transmission
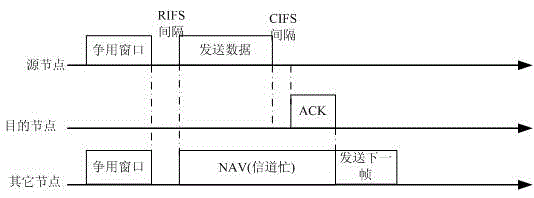
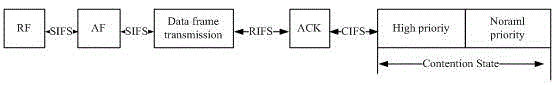
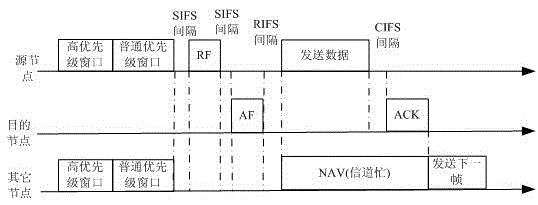
The invention discloses a method for network congestion control of power line carrier communication. Considering the security of important data, an original CSMA / CA protocol applied to power line carrier communication is improved, data is divided into high-priority data and ordinary-priority data, and the important data is set to be at high priority. In order to ensure the security and reliability of the high-priority data, a special high-priority competition channel is opened, so as to ensure the priority in transmission of the high-priority data. The ordinary-priority data can only be transmitted after the transmission of the high-priority data is completed, thereby preventing the important data from being discarded due to competition failure. In addition, in order to ensure data security, an RF / AF handshaking signal is added before transmission of the high-priority data, and a data packet is transmitted after successful transmission and reception of the handshaking signal. An RF frame has a channel reservation function, the transmission of the original ordinary-priority data is interrupted when high-priority data to be transmitted is found, and the high-priority data is transmitted preferentially.
Owner:JIANGSU LINYANG ENERGY CO LTD
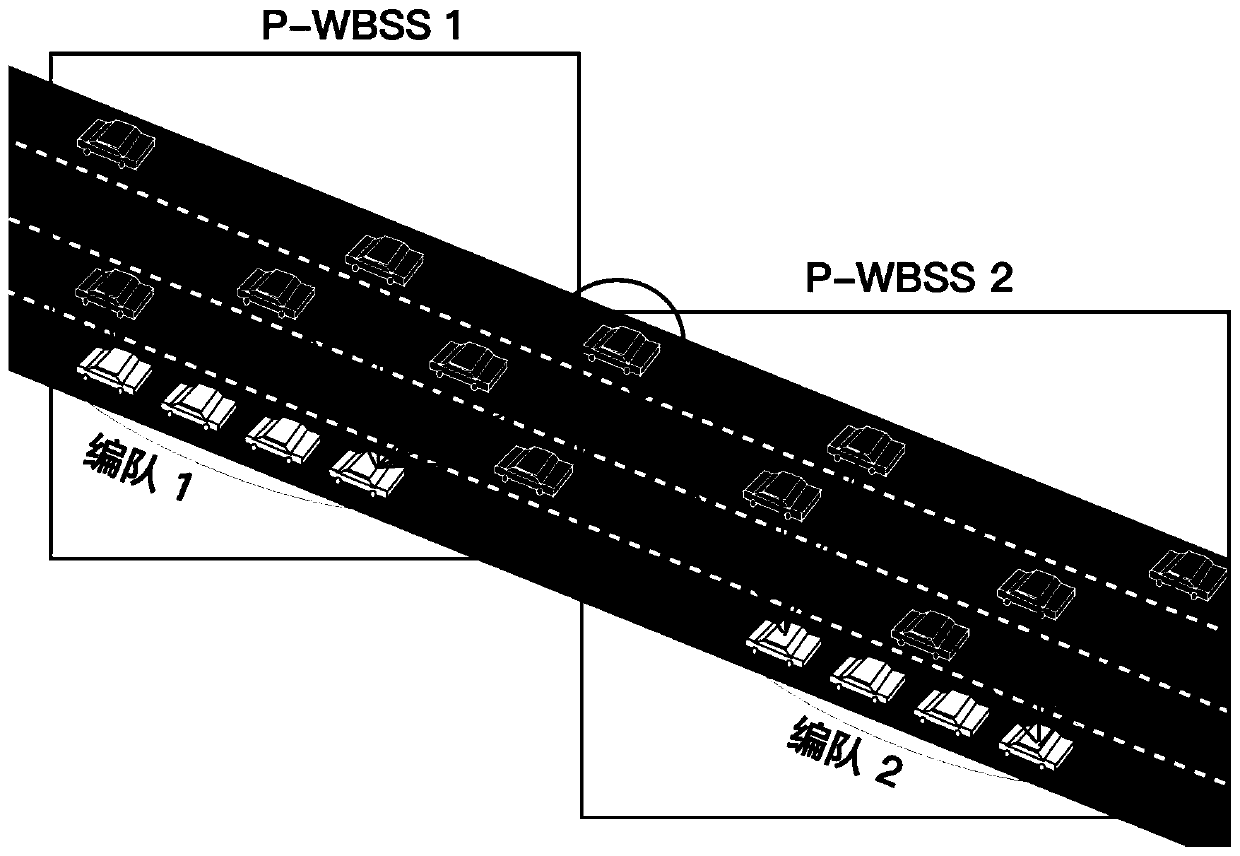
Reliable broadcasting method for hybrid traffic system with formation as center
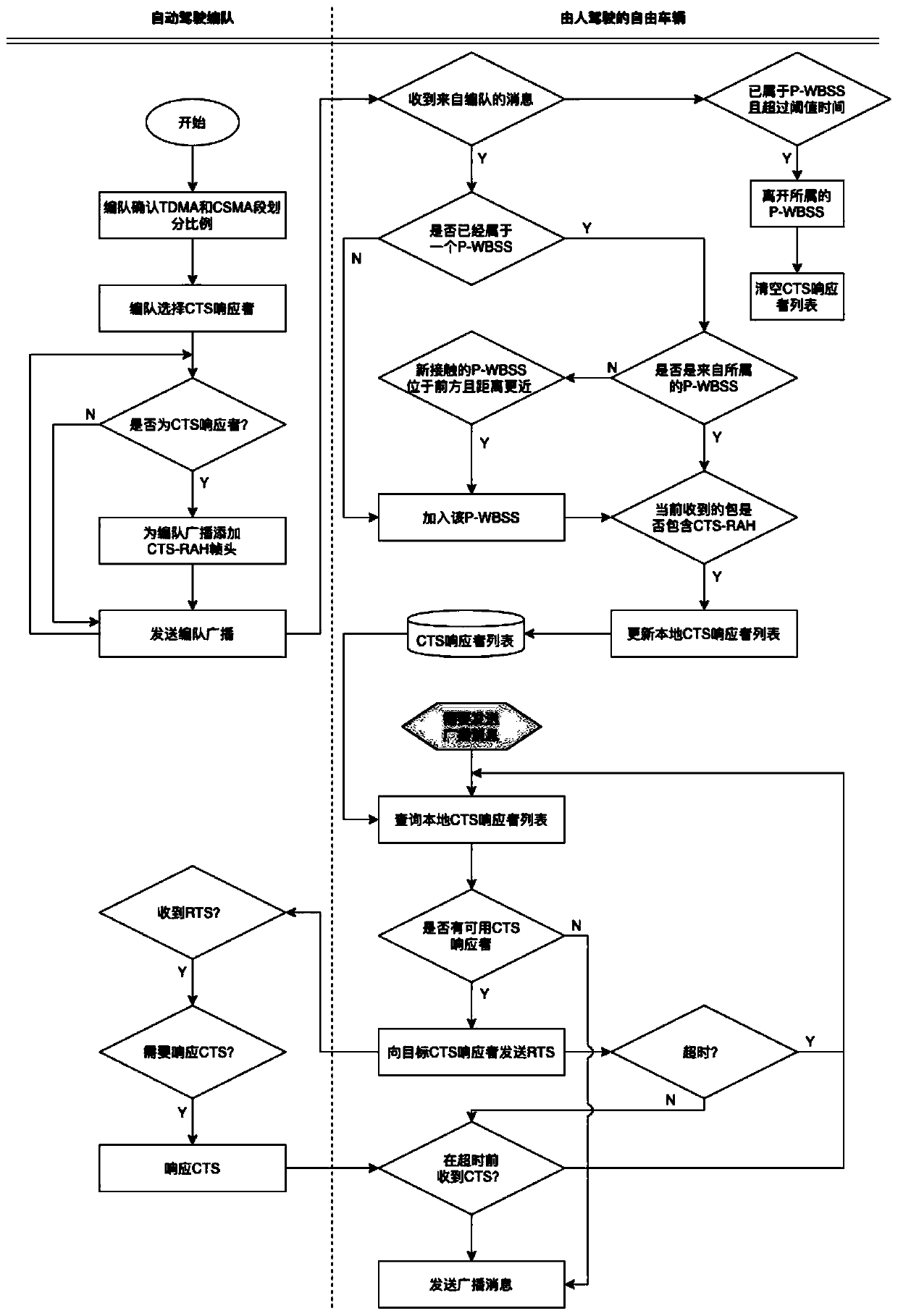
ActiveCN111417081AImprove reliabilityImprove throughput efficiencyNetwork traffic/resource managementParticular environment based servicesCA protocolEngineering
The invention relates to the field of communication, in particular to a reliable broadcasting method for a hybrid traffic system with formation as the center. According to the method disclosed in theinvention, a wireless basic service set is formed by taking unmanned formation as a center. Formation vehicles use a TDMA protocol, and other vehicles use a CSMA / CA protocol. According to the method disclosed in the invention, a part of formation members are selected as CTS responders in a basic service set; the RTS / CTS function is realized for broadcast communication of a free vehicle driven by aperson, an RTS / CTS mechanism is introduced for broadcast communication, so that the broadcast communication can have a retransmission capability, and the reliability of the broadcast communication isimproved. According to the method, the topological structure characteristics in the hybrid traffic system are fully utilized, the performance loss caused by collision in wireless communication can begreatly reduced, and therefore the network communication efficiency is improved.
Owner:TSINGHUA UNIV
CSMA/CA multiple access method based on threshold service
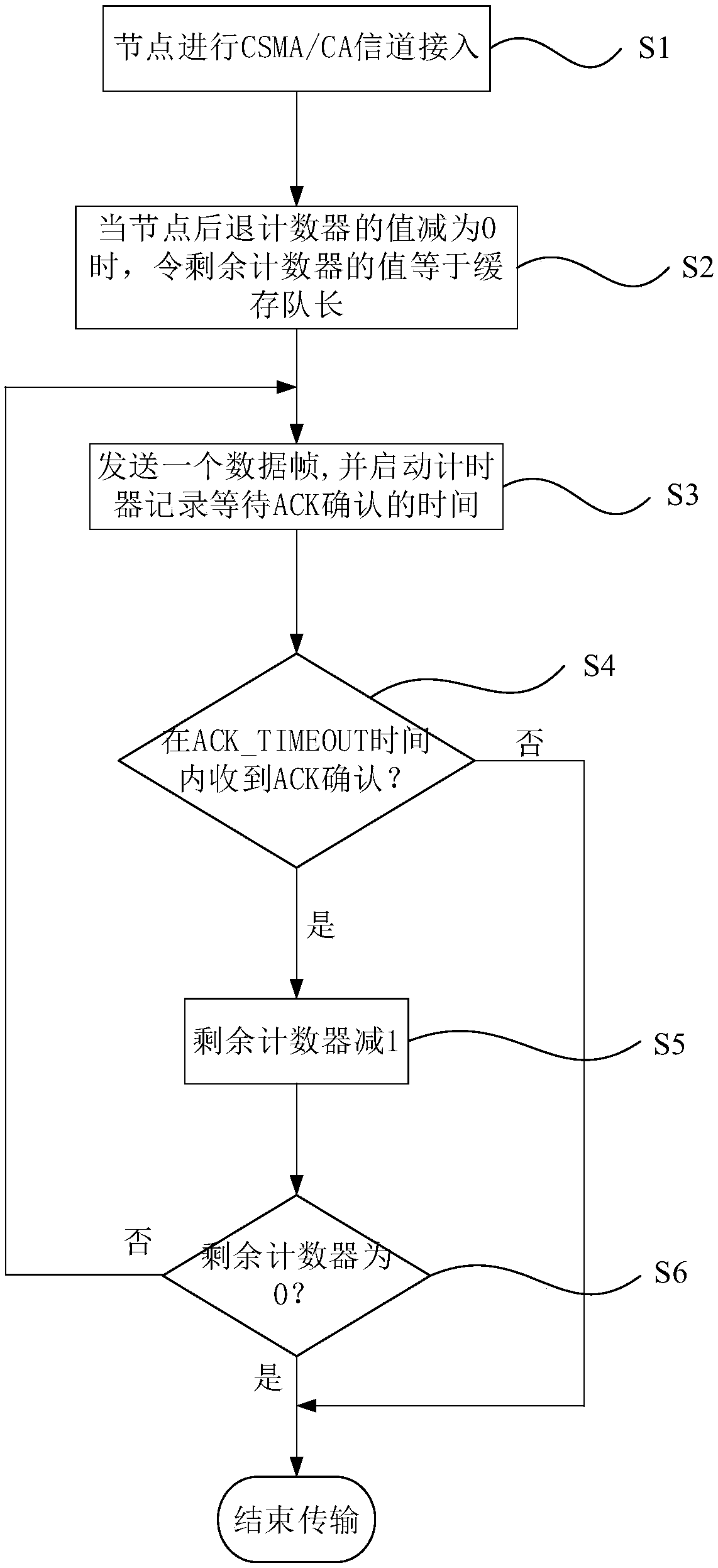
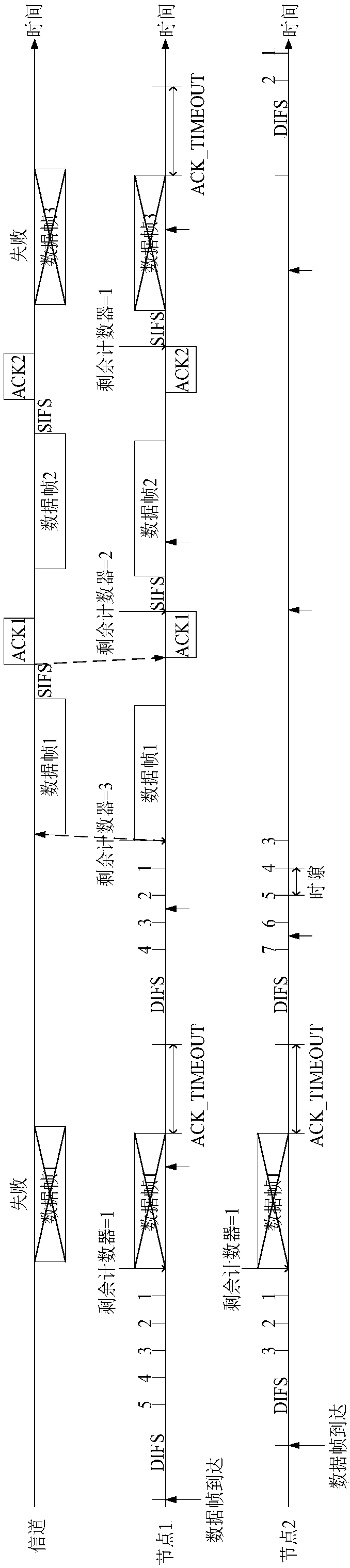
InactiveCN108541076AShorten contention delayIncrease profitWireless communicationCA protocolAccess method
The invention provides a CSMA / CA multiple access method based on a threshold service. The method comprises the following steps that a node needing to be accessed into a channel preempts the channel according to a CSMA / CA protocol; when a value of a backoff counter is reduced to 0, the node checks the length of a cache queue, and sets a value of the residual counter as the length of the cache queue; the node sends a data frame and starts the timer to record the time for waiting for ACK confirmation; whether the node receives the ACK confirmation in the ACK-TIMEOUT time or not is judged, and ifyes, the data frame is sent successfully. According to the method, the competition time delay of the node can be greatly reduced, and the data frame can be sent out once as soon as possible, so that the network throughput is improved, the average time delay and the delay jitter of the data frame are reduced, and the system stability is enhanced.
Owner:SHANGHAI JIAO TONG UNIV
Efficient fairness allocation in powerline CSMA/CA protocols
ActiveUS9198198B2Transmission path divisionPower distribution line transmissionCA protocolCarrier signal
Transmission over a communication channel using carrier sense multiple access collision avoidance (CSMA / CA) may be performed by determining for each frame if the communication channel is busy after a backoff time proportional to a randomly generated number within a contention window (CW). When the channel is not busy, a frame of data may be transmitted. When the channel is busy, the device may periodically determine if the communication channel is busy after subsequent backoff times. The value of CW is adjusted for each subsequent backoff time using a fairness protocol, in which the value of CW is increased until the value of CW reaches a maximum CW value; and then the value of CW is held until a fairness number of backoff repetitions reaches a fairness threshold; then the value of CW is reduced incrementally until the value of CW reaches a minimum CW value.
Owner:TEXAS INSTR INC
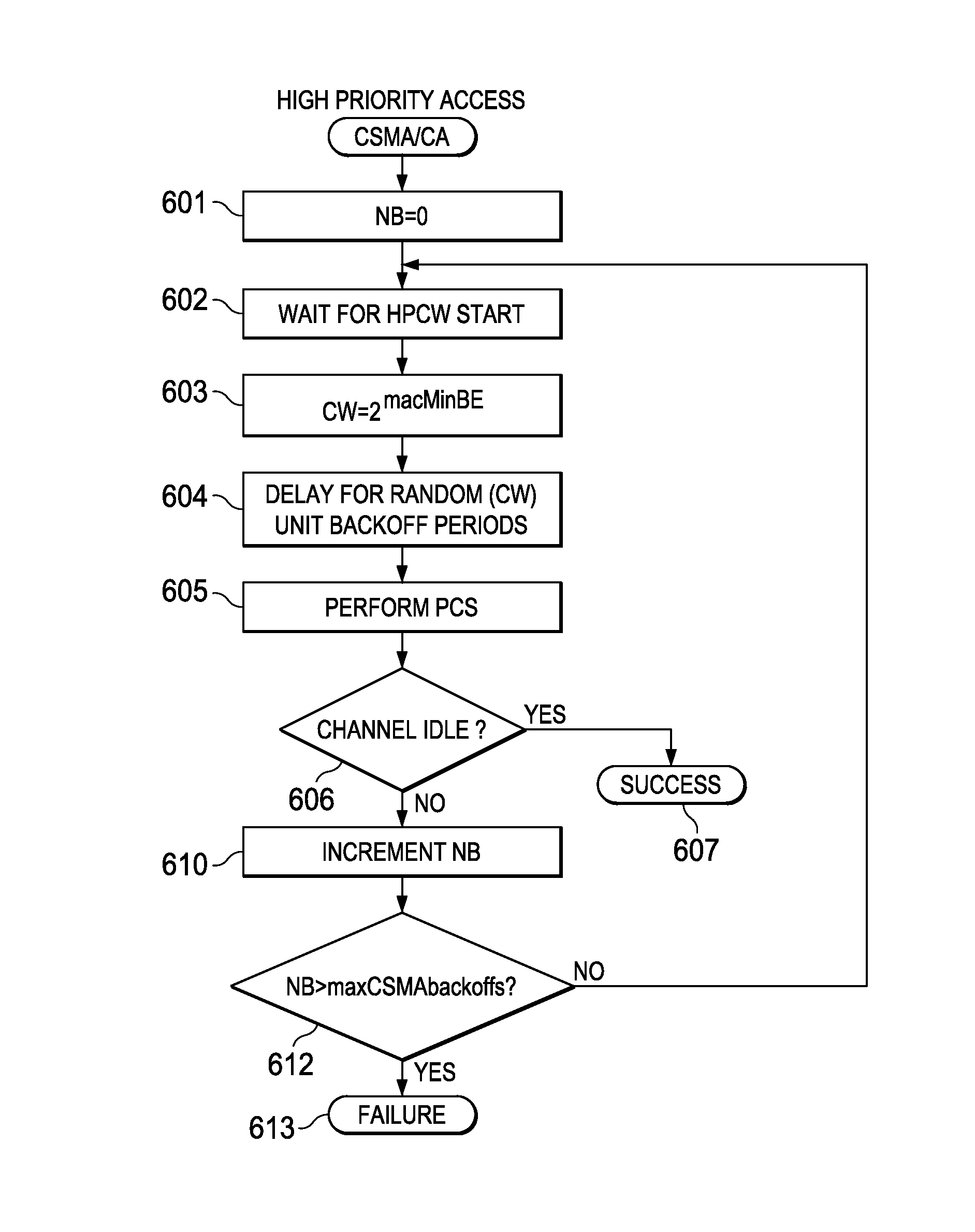
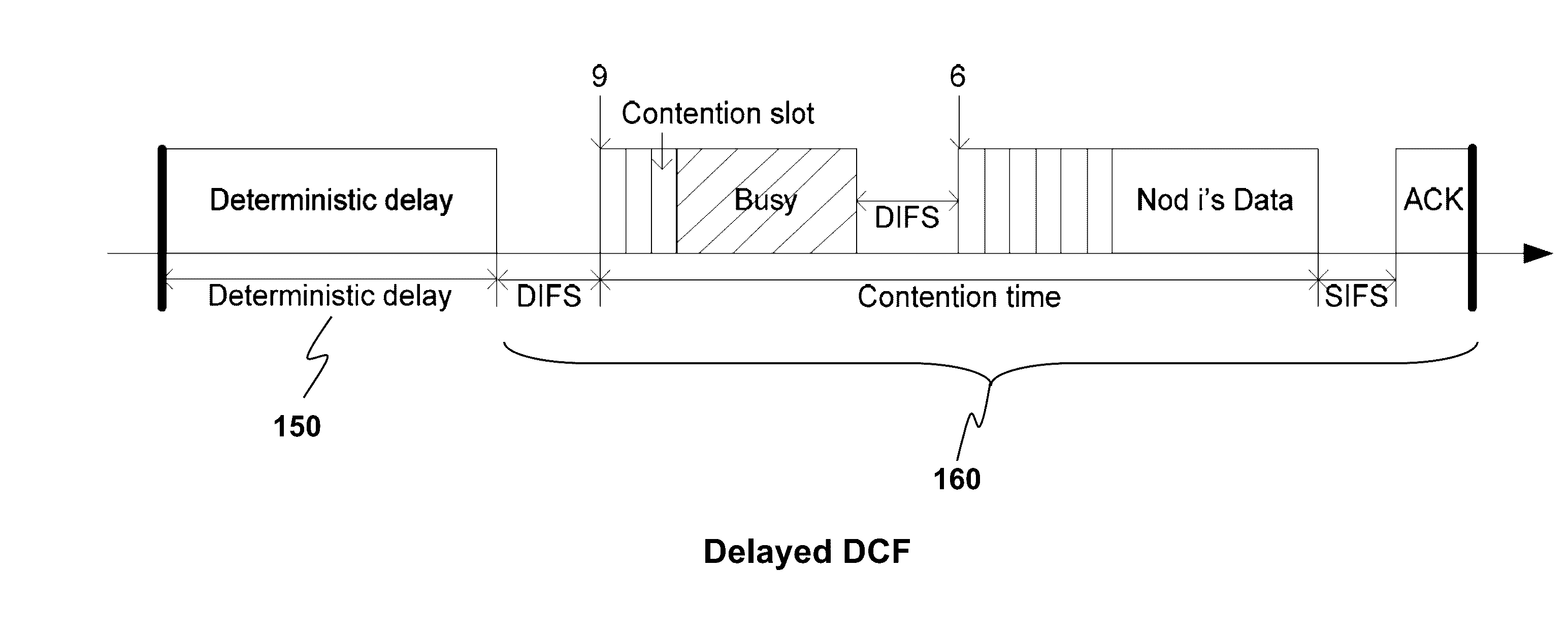
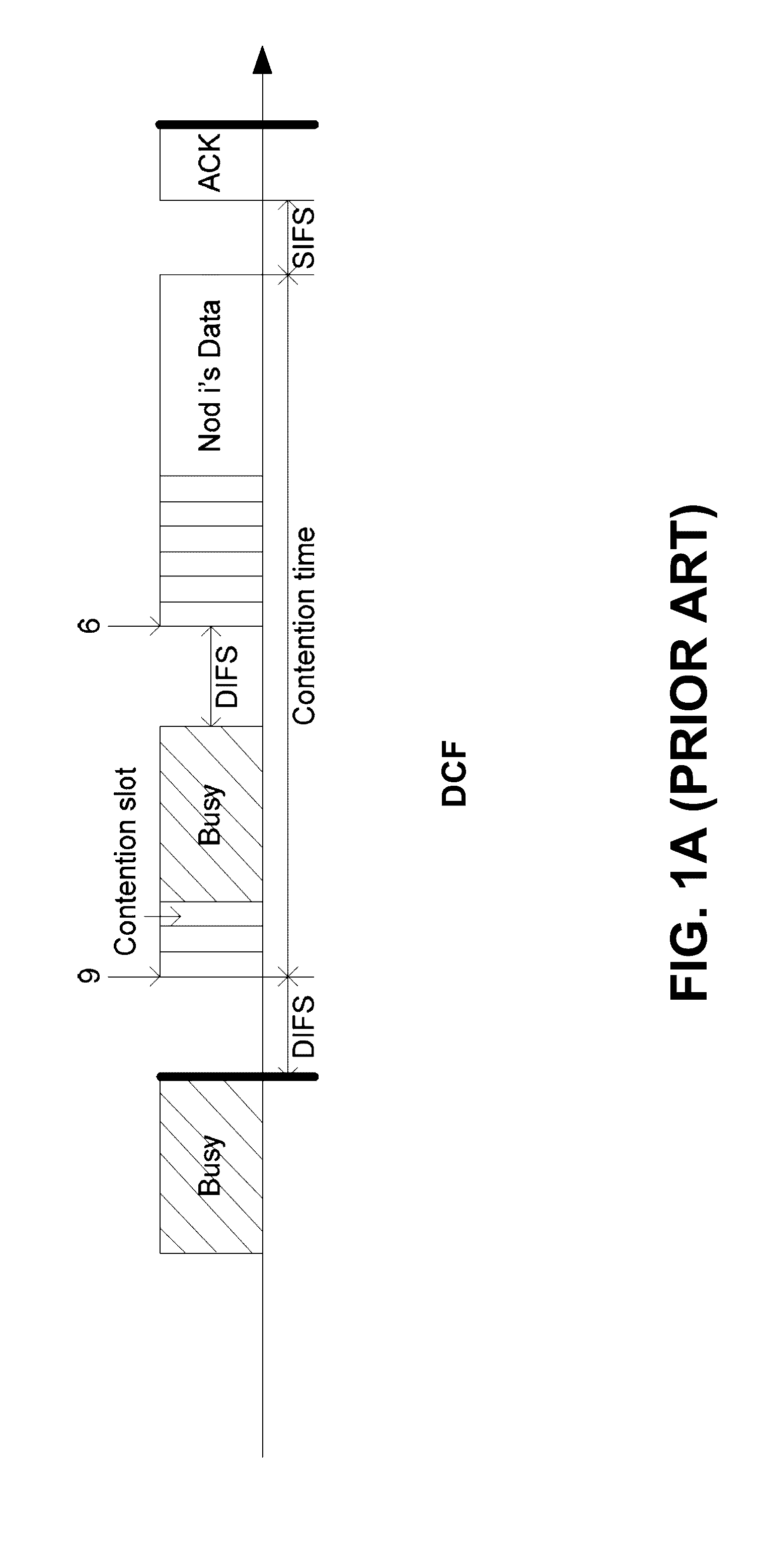
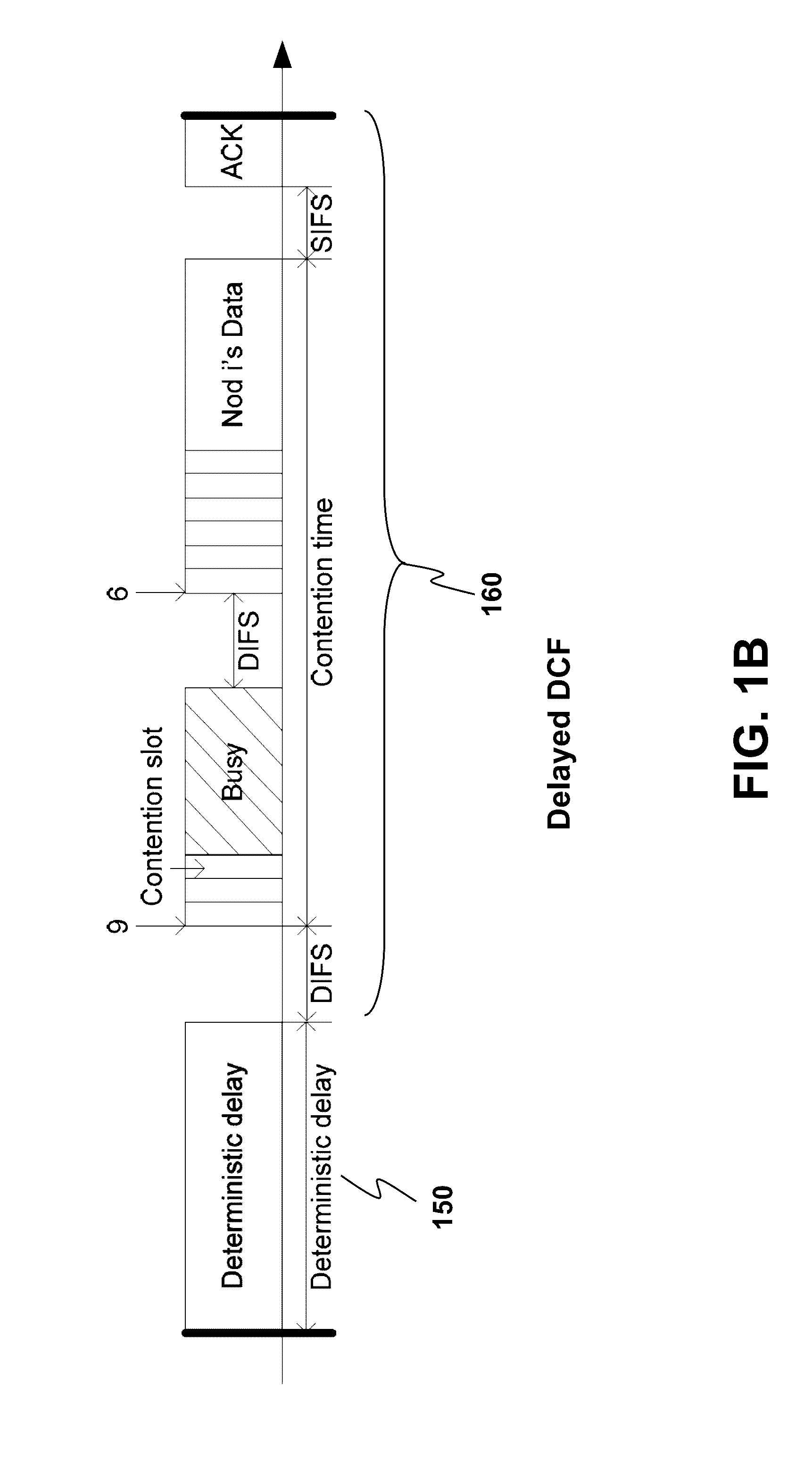
System Parameter Optimization for Delayed Channel Access Protocol
A method for enabling one or more nodes to communicate with an access point (AP) according to a CSMA / CA protocol is provided. In one embodiment of the method, when the individual node enters into a state of having at least one packet of data to be transmitted to the AP, the individual node waits for a non-zero deterministic delay so that any packet arrived during the delay is allowed to be aggregated and transmitted upon one transmission opportunity, thereby improving channel utilization. The delay is determined such that a predicted system throughput is maximized. It is found that the system throughput is significantly affected by the relationship between the delay and the number of the one or more nodes. Hence, the delay is advantageously determined according to the number of the one or more nodes. After the delay expires, the individual node initiates a contending procedure.
Owner:MACAU UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com