Cross-trust-domain identity authentication method
An identity authentication and trust domain technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of inconvenient subnet information sharing and interaction, information barriers, etc., and achieve the effect of simplifying the development process of identity authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The invention is based on:
[0019] 1. PKI's digital signature technology realizes the signature of identity tokens, ensures the validity of identity tokens, and provides the basis for cross-domain authentication.
[0020] 2. The XML language specification realizes the encapsulation of identity tokens and realizes cross-platform, cross-language, and extensible tokens.
[0021] 3. WebService technology to realize cross-software and hardware platforms and cross-language identity token verification services.
[0022] 4. OPENID technology realizes the standardization of identity authentication protocols.
[0023] 5. COM technology, realizing the token interface call of the Window platform.
[0024] 6. The FireFox plug-in technology realizes the calling of the token interface of the Linux platform.
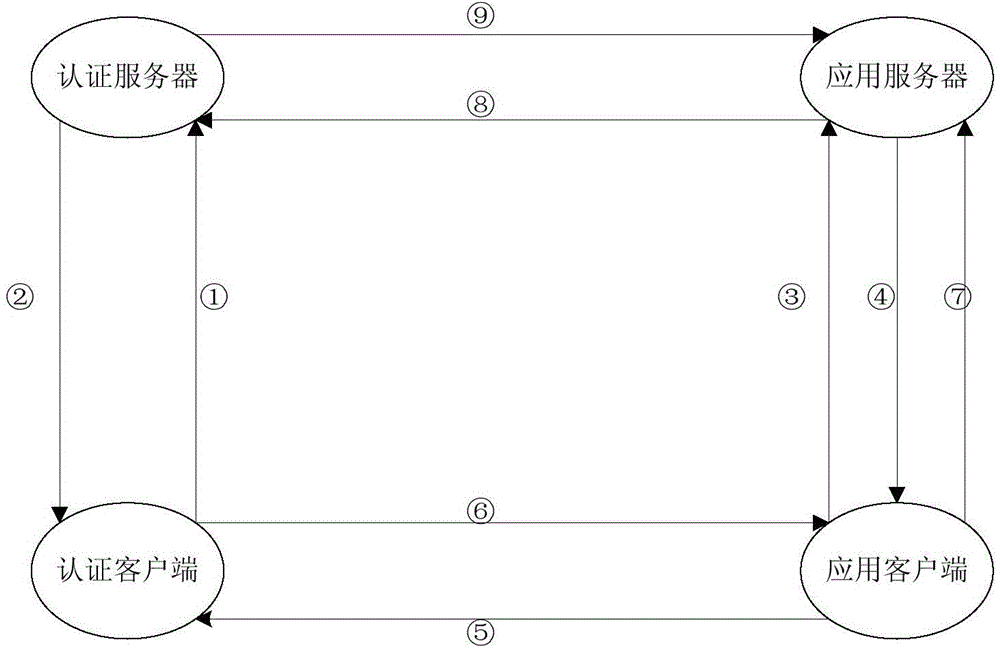
[0025] An identity authentication method across trust domains, including: identity token issuing service and token verification service of identity authentication server; ide...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com