Authentication method for client certificate, server and client
An authentication method and client-side technology, applied in the client certificate authentication method, server and client fields, can solve the problems of client loss, digital certificate and password leakage, and achieve the effect of avoiding identity misidentification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
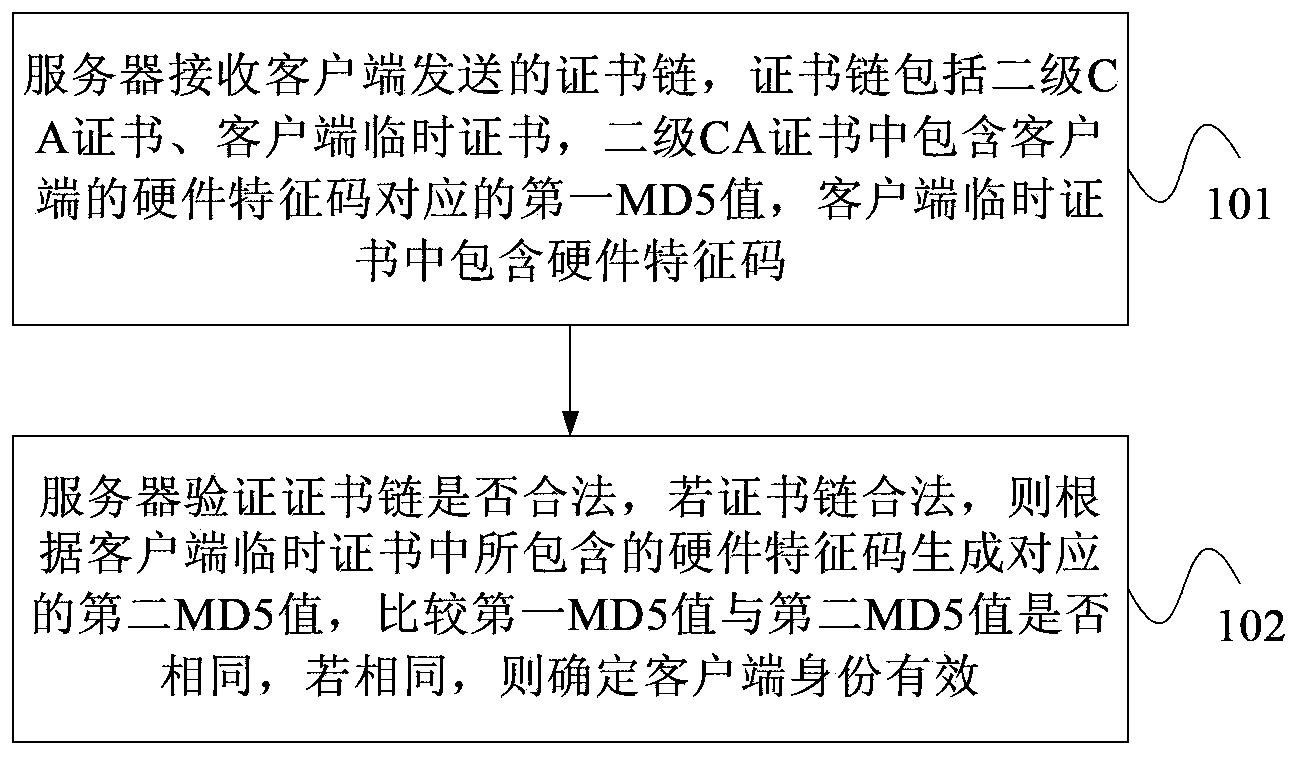
[0039] figure 1 It is a flow chart of Embodiment 1 of the client certificate authentication method of the present invention, as shown in figure 1 As shown, the method provided in this embodiment includes the following steps:
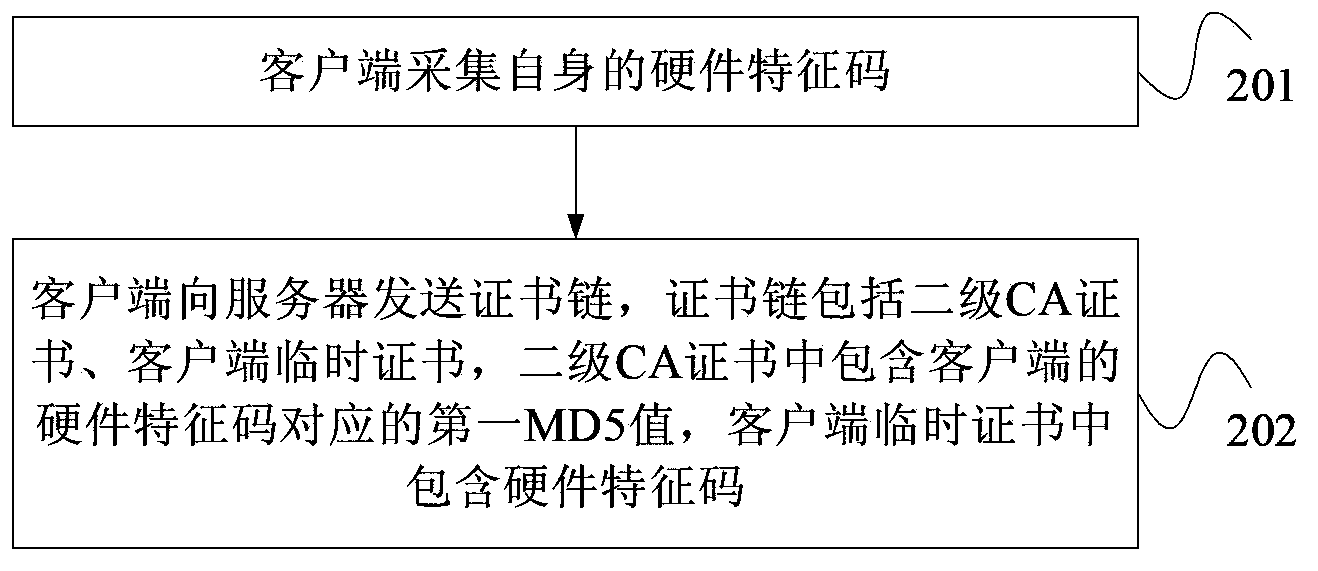
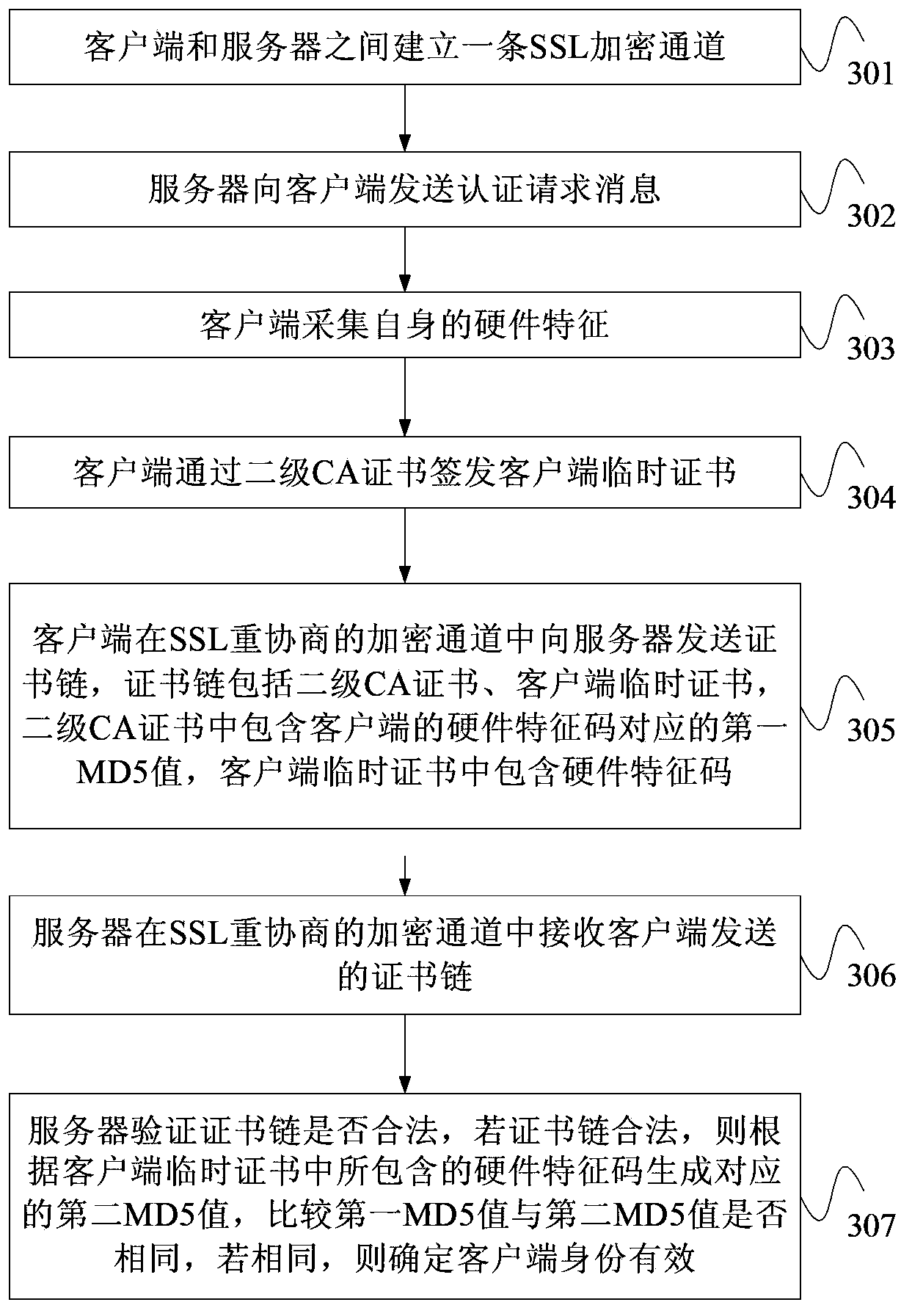
[0040] Step 101. The server receives the certificate chain sent by the client. The certificate chain includes a secondary CA certificate and a temporary client certificate. The secondary CA certificate contains the first MD5 value corresponding to the hardware signature of the client. feature code.
[0041] Among them, the client temporary certificate is issued by the secondary CA certificate, and the secondary CA certificate is issued by the primary CA certificate. When the server needs to verify the identity of the client, the client issues a client temporary certificate through the local secondary CA certificate. The validity period of the client temporary certificate is very short, such as 1 minute or 30 seconds. A temporary client certificate is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com