Patents
Literature
32 results about "WebID" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
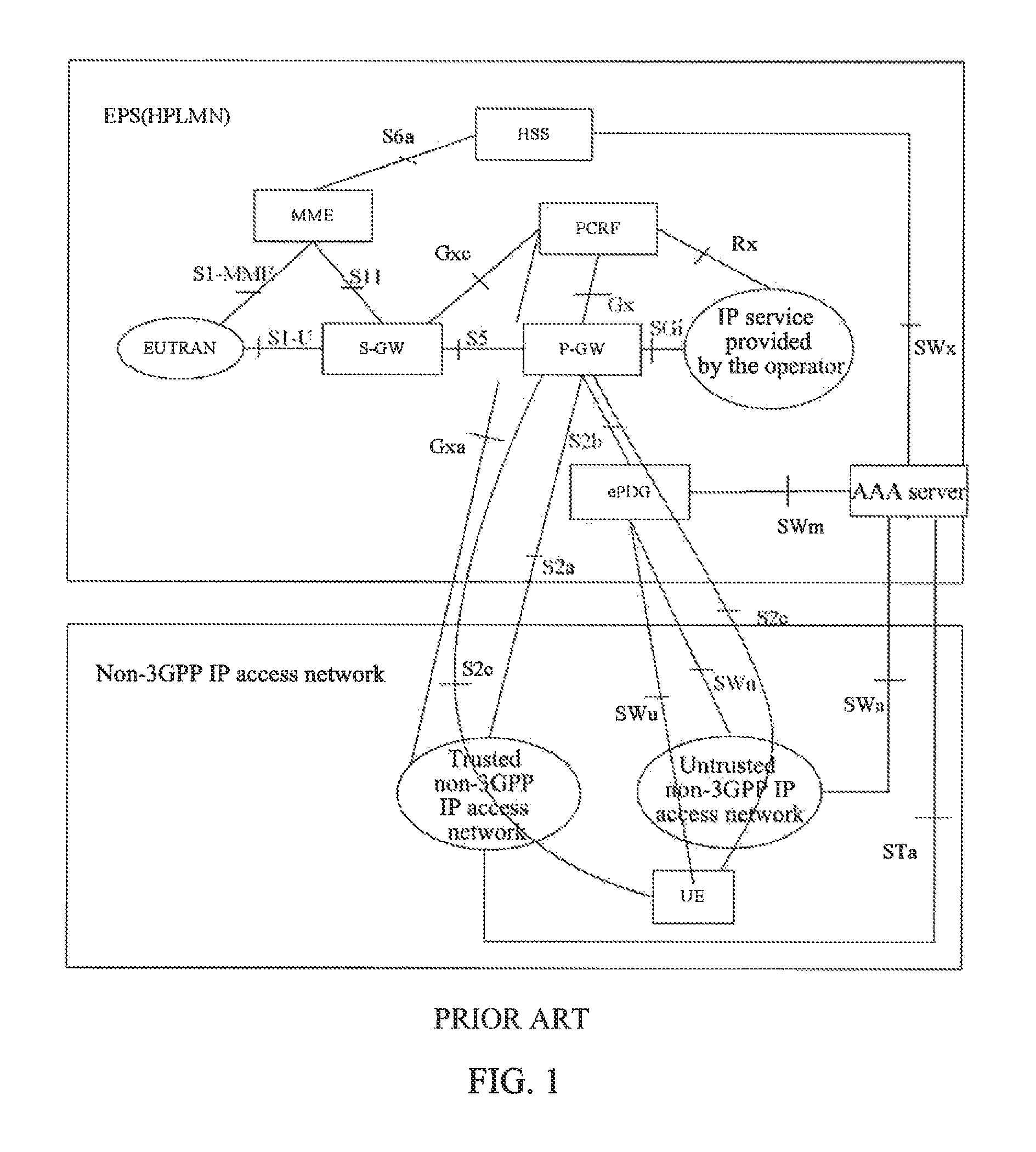
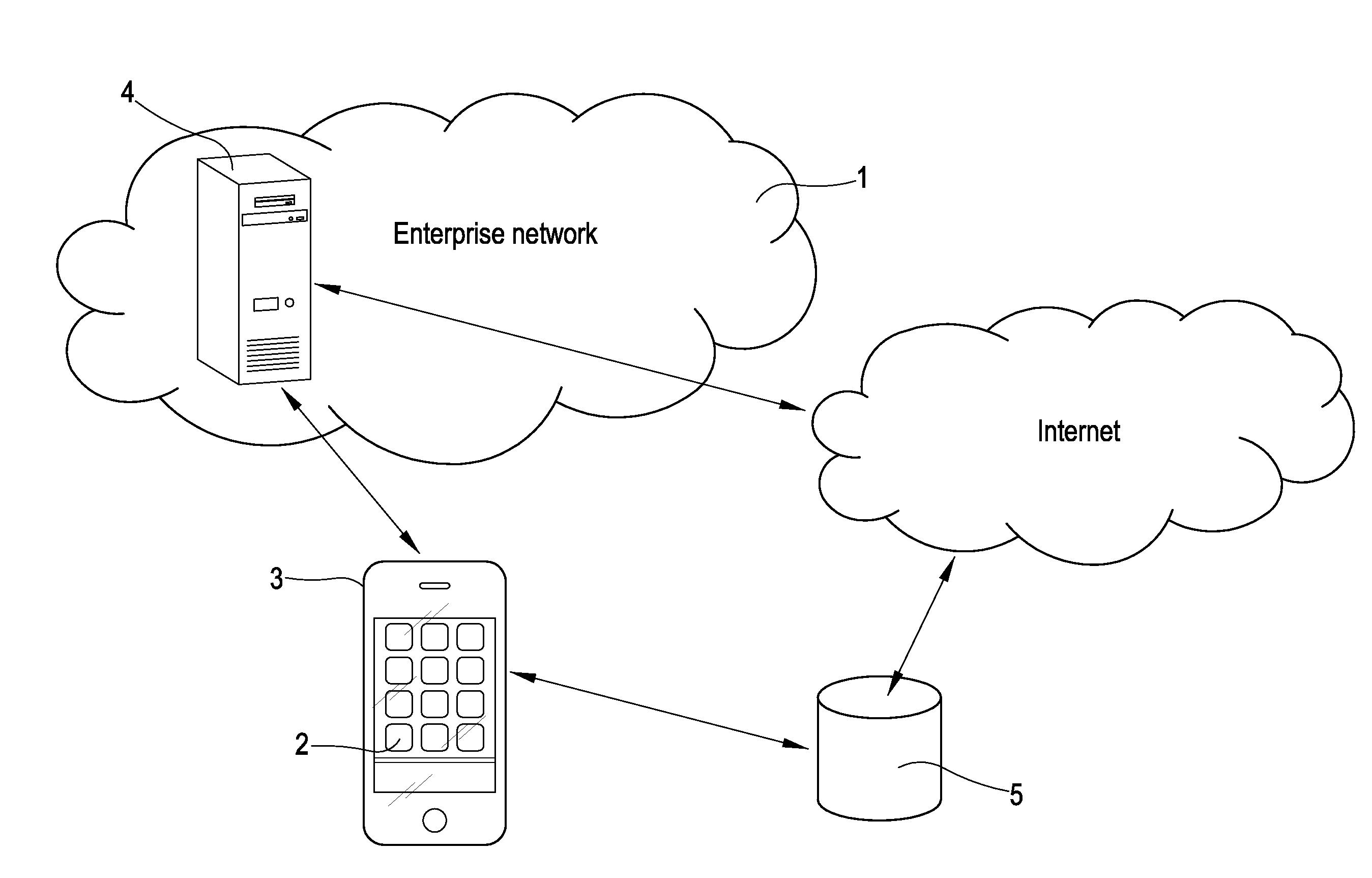
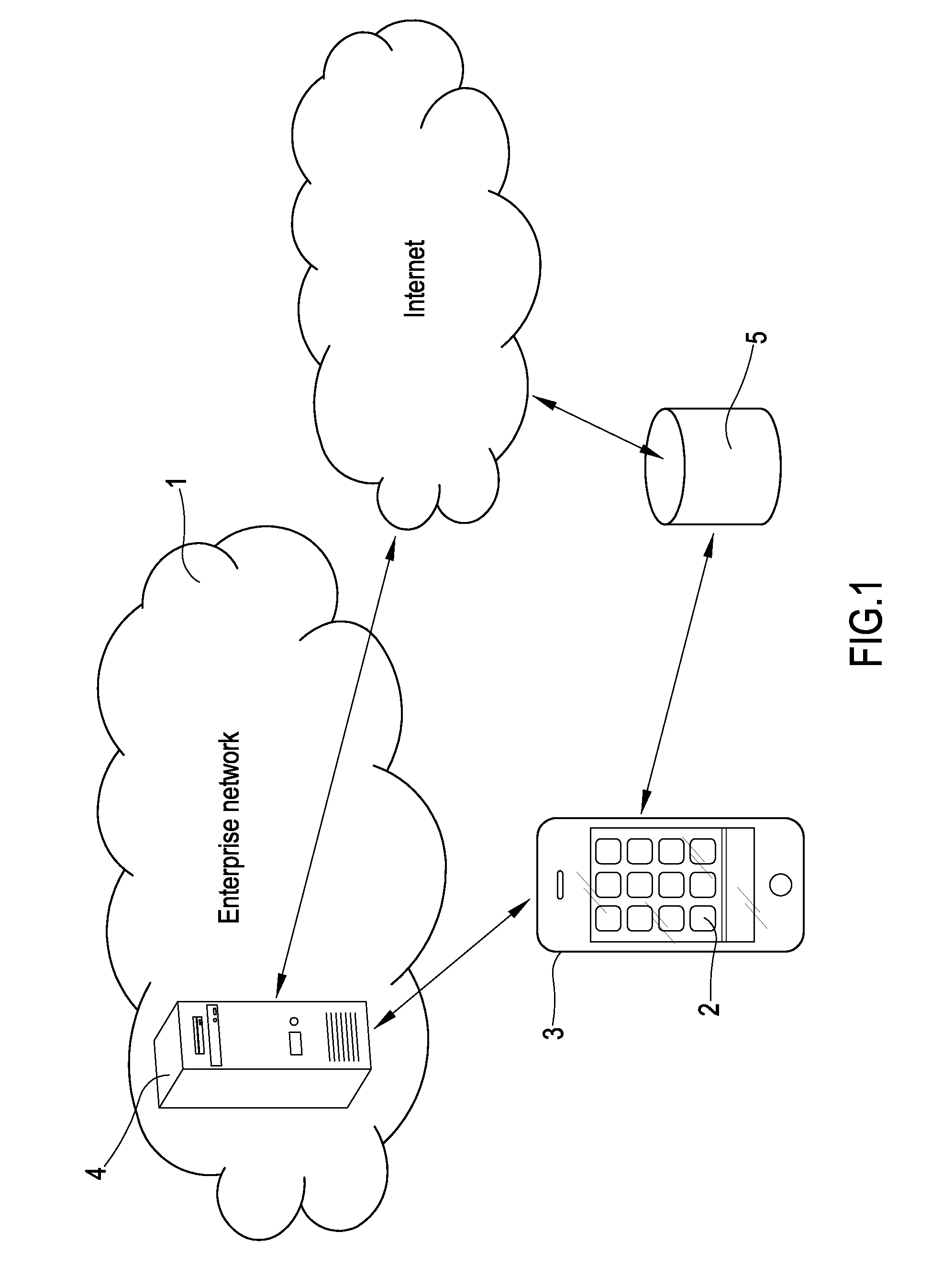
WebID is a method for internet services and members to know who they are communicating with. The WebID specifications define a set of editor's drafts to prepare the process of standardization for identity, identification and authentication on HTTP based networks. WebID-based protocols (WebID-OIDC, WebID-TLS, WebID-TLS+Delegation) offer a new way to log into internet services. Instead of using a password, for example, the member refers to another web address which can vouch for it. WebID is not a specific service or product.
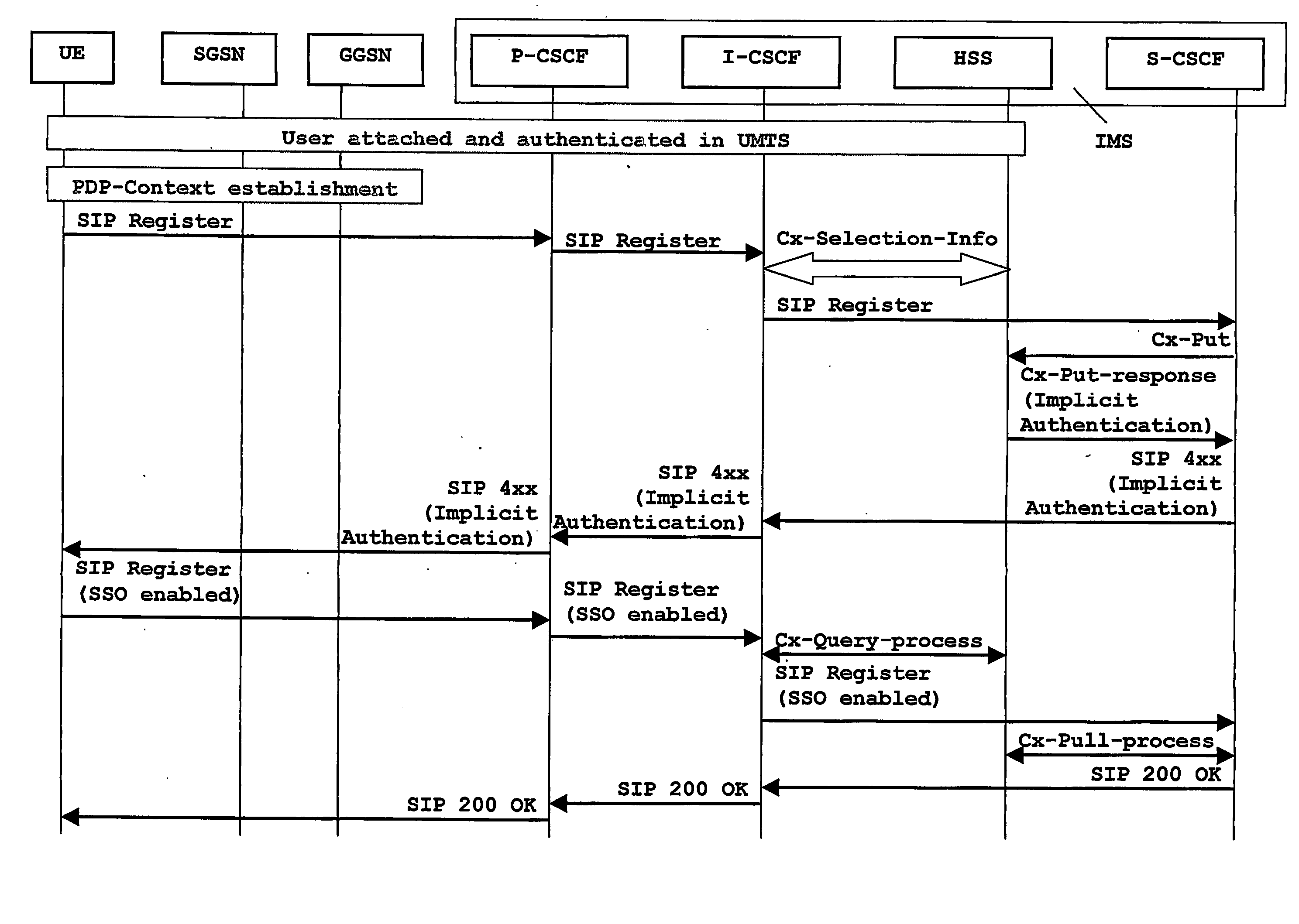
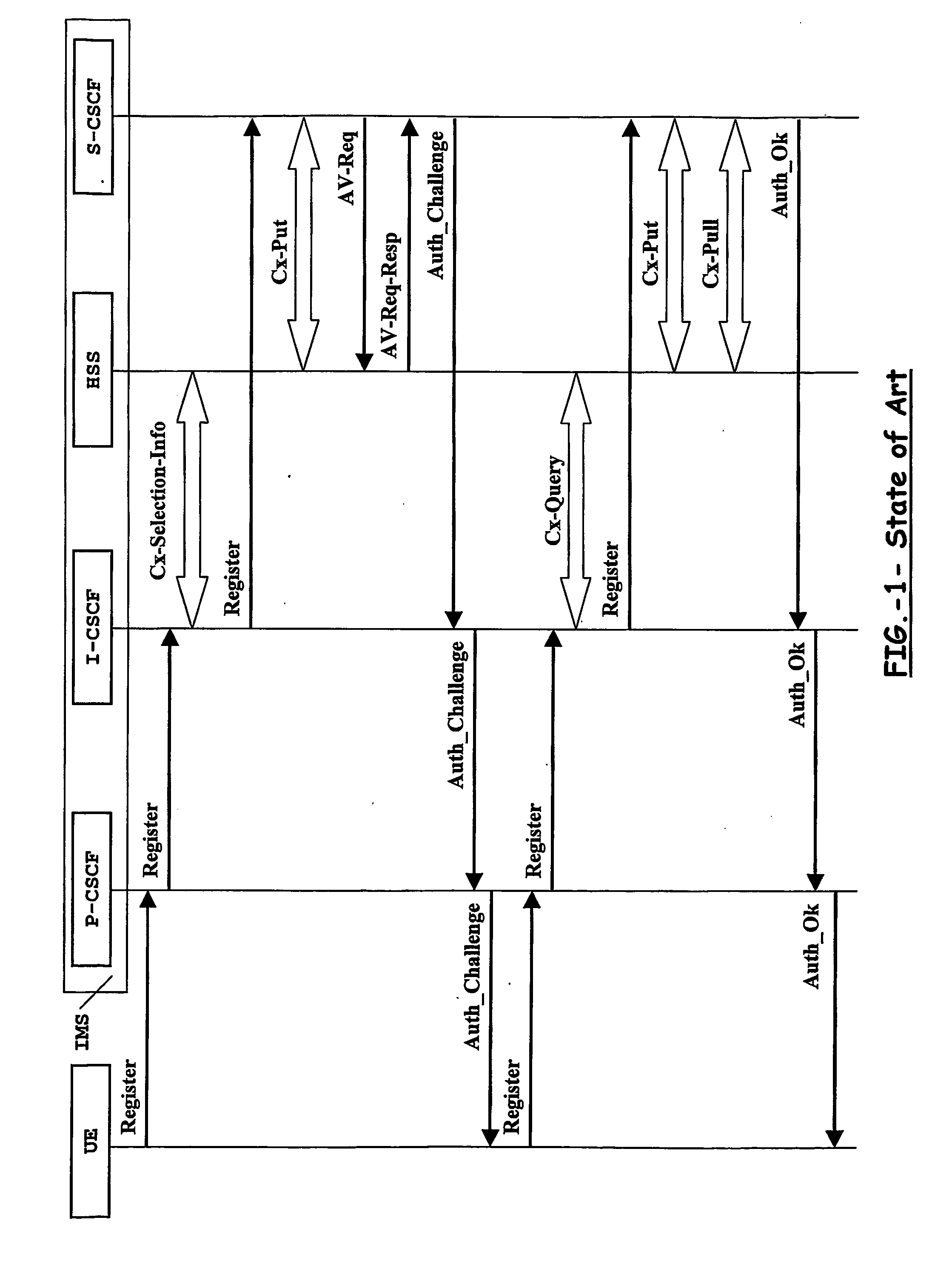
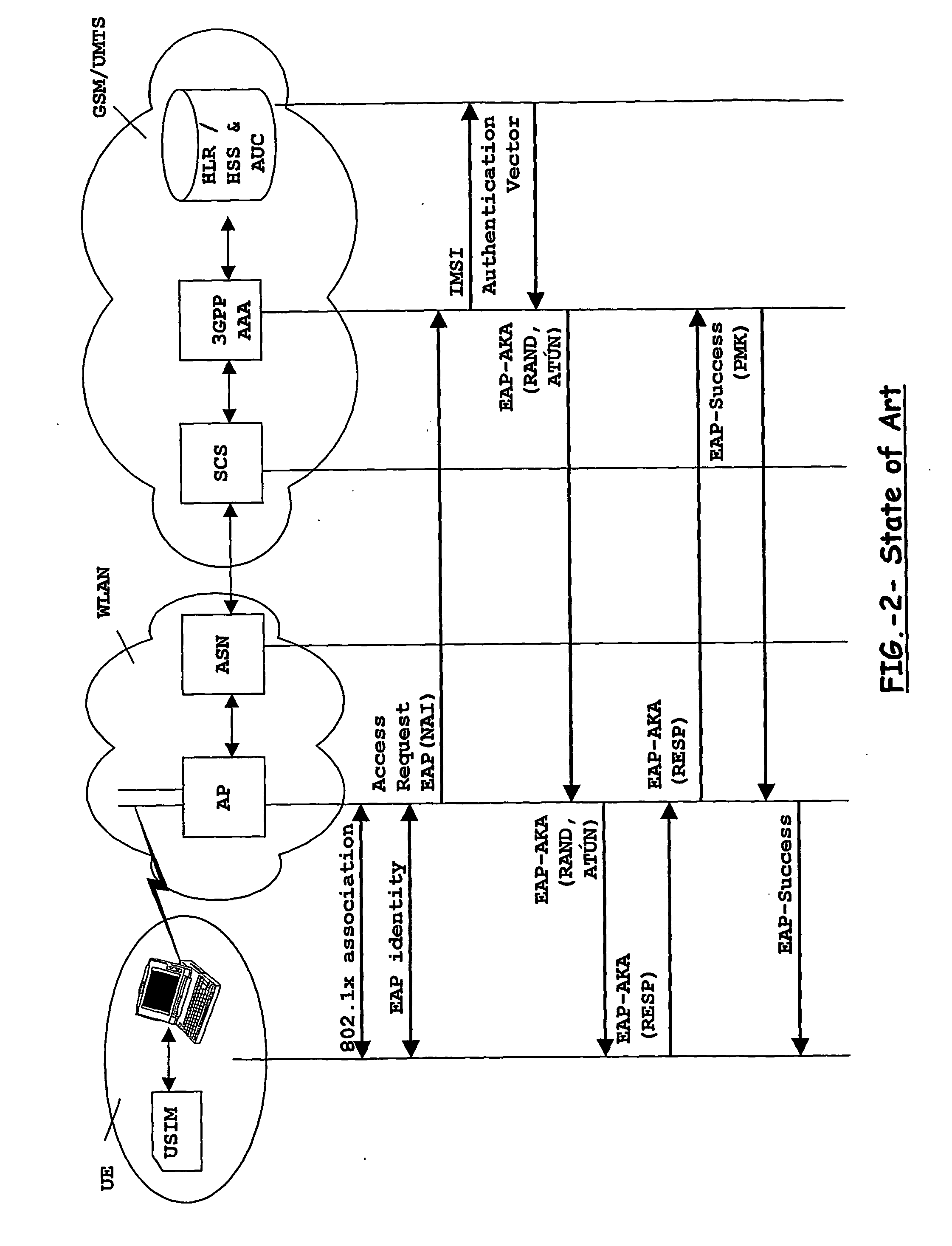
Apparatus and method for authenticating a user when accessing to multimedia services
An inter-domain authentication mechanism is provided for carrying out a cross-domain authentication for a given user between an access network domain and a Multimedia domain. The authentication mechanism is applicable where a user has been authenticated by the access network and may be implemented as a dedicated Multimedia Authentication device in close co-operation with a subscriber server, or be fully integrated in the subscriber server. The authentication mechanism is arranged for re-using authentication data between different networks, or between different technological domains, and with help from other entities of a Multimedia domain according to present standards.
Owner:TELEFON AB LM ERICSSON (PUBL)
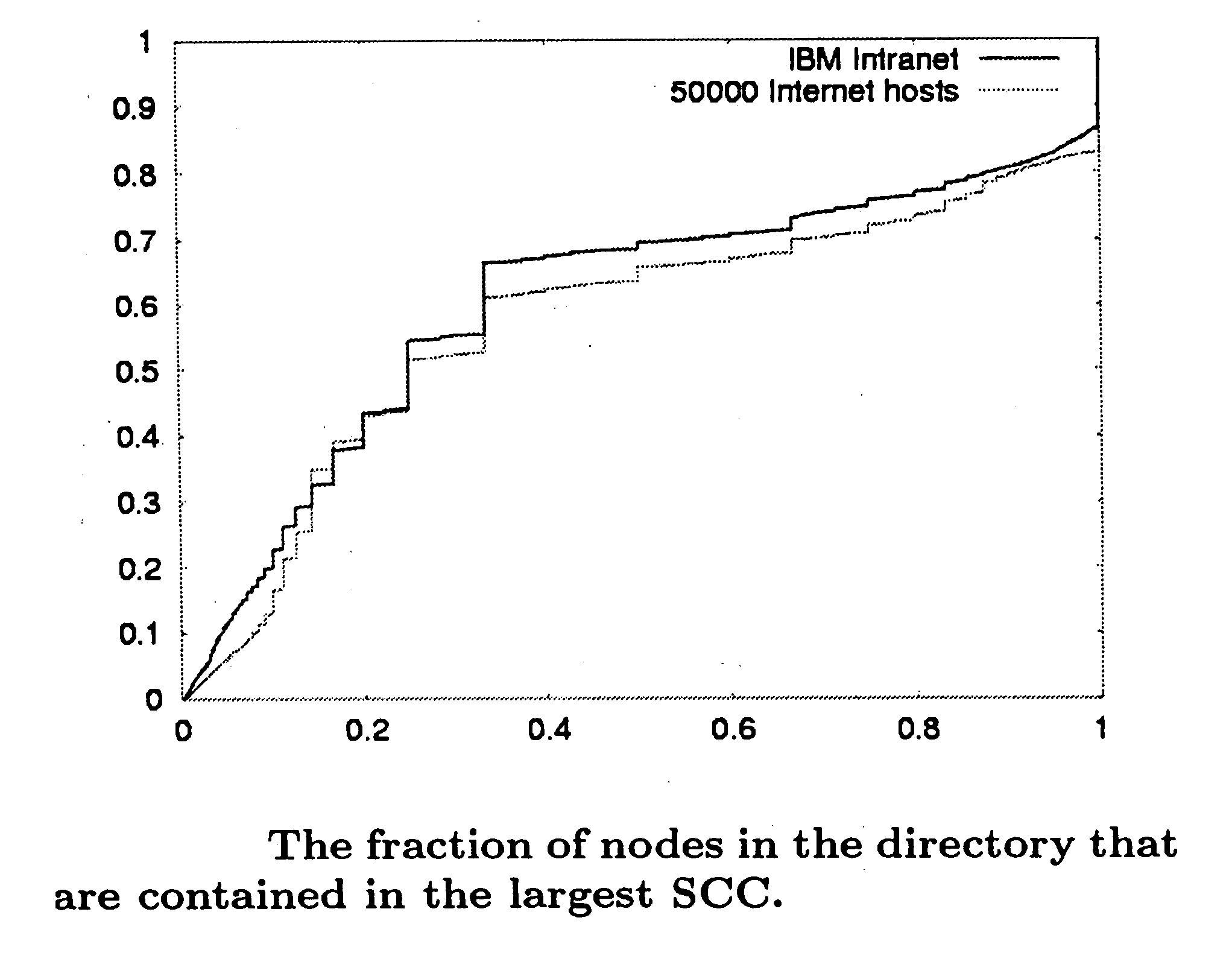
System, method, and computer program product for identifying multi-page documents in hypertext collections
InactiveUS20050071310A1Precise definitionBetter quality toolDigital data information retrievalDigital data processing detailsWebIDEntry point
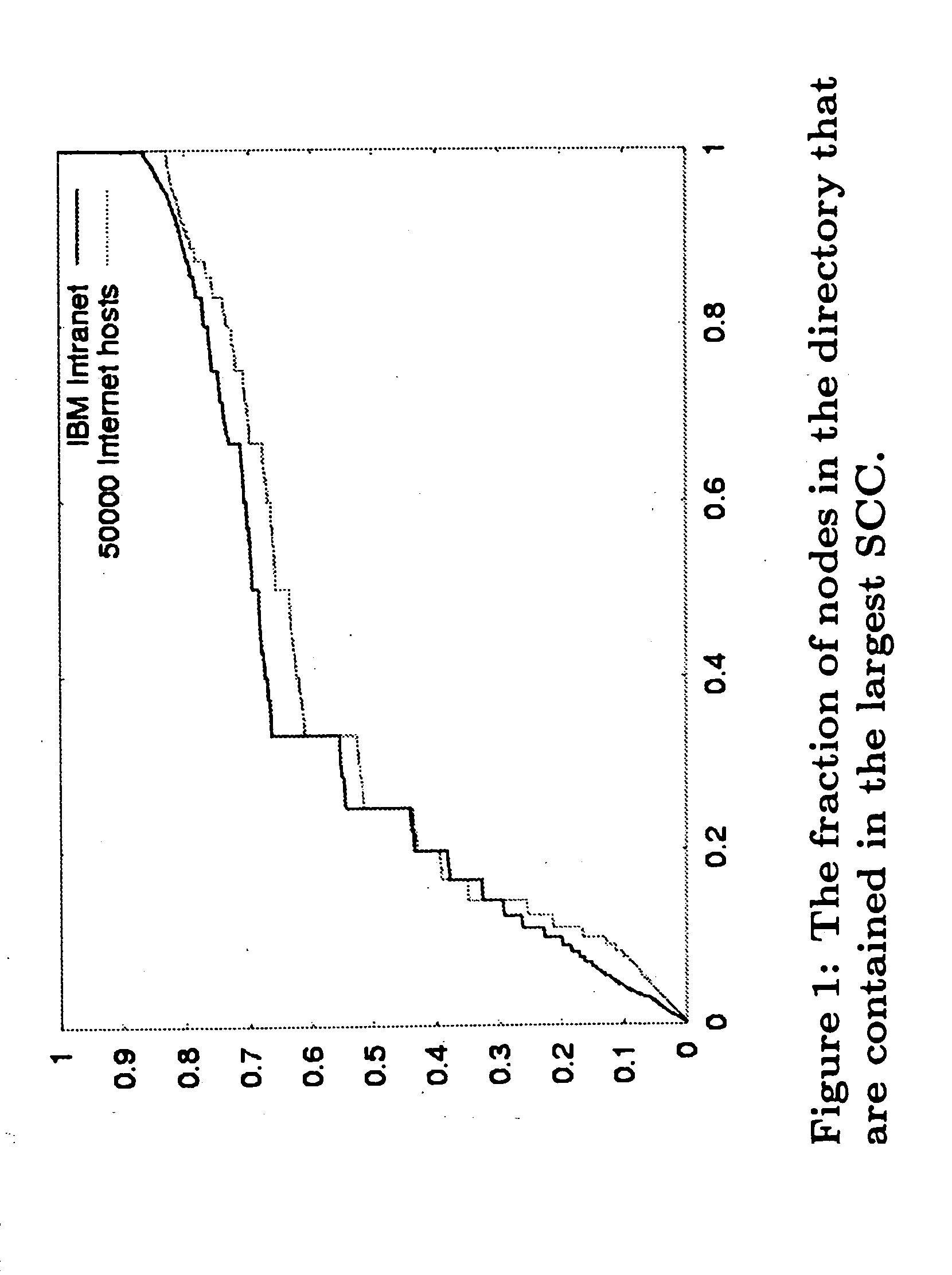
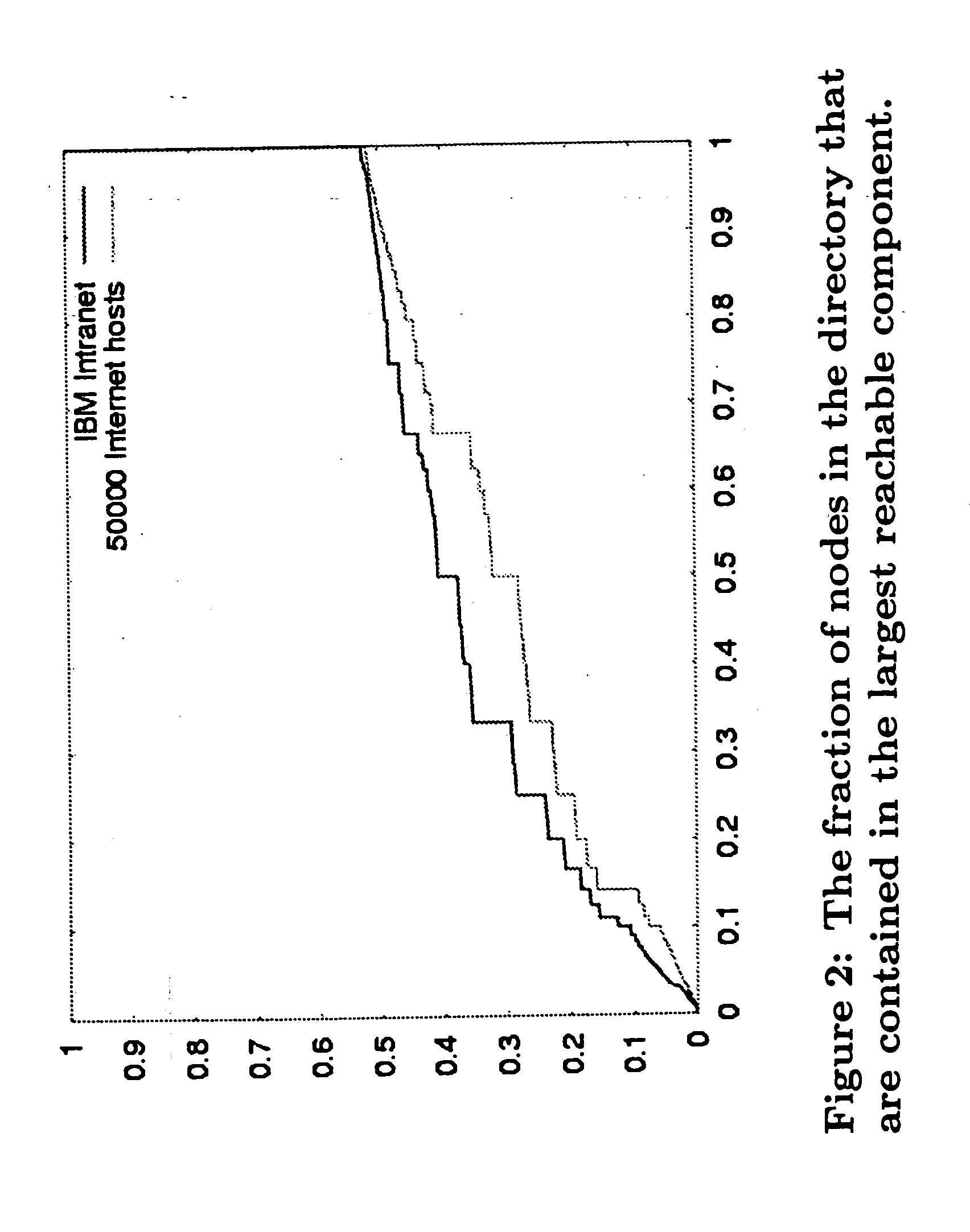
A system, method, and computer program product for identifying compound documents as a coherent body of hyperlinked material on a single topic as created by an author or collaborating authors, analyzing the content and structure of the compound documents and related hyperlinks, and responsively selecting a preferred entry point at which to begin processing such documents. The body of material may include the internet, an intranet, or other digital library that typically has content distributed over several separate pages or URLs, sometimes in a hierarchical directory structure. The processing may include creating at least one taxonomy, as well as searching or indexing the compound documents. The identification and analysis schemes include a observation of a number of heuristics run on component documents in the compound documents.
Owner:IBM CORP
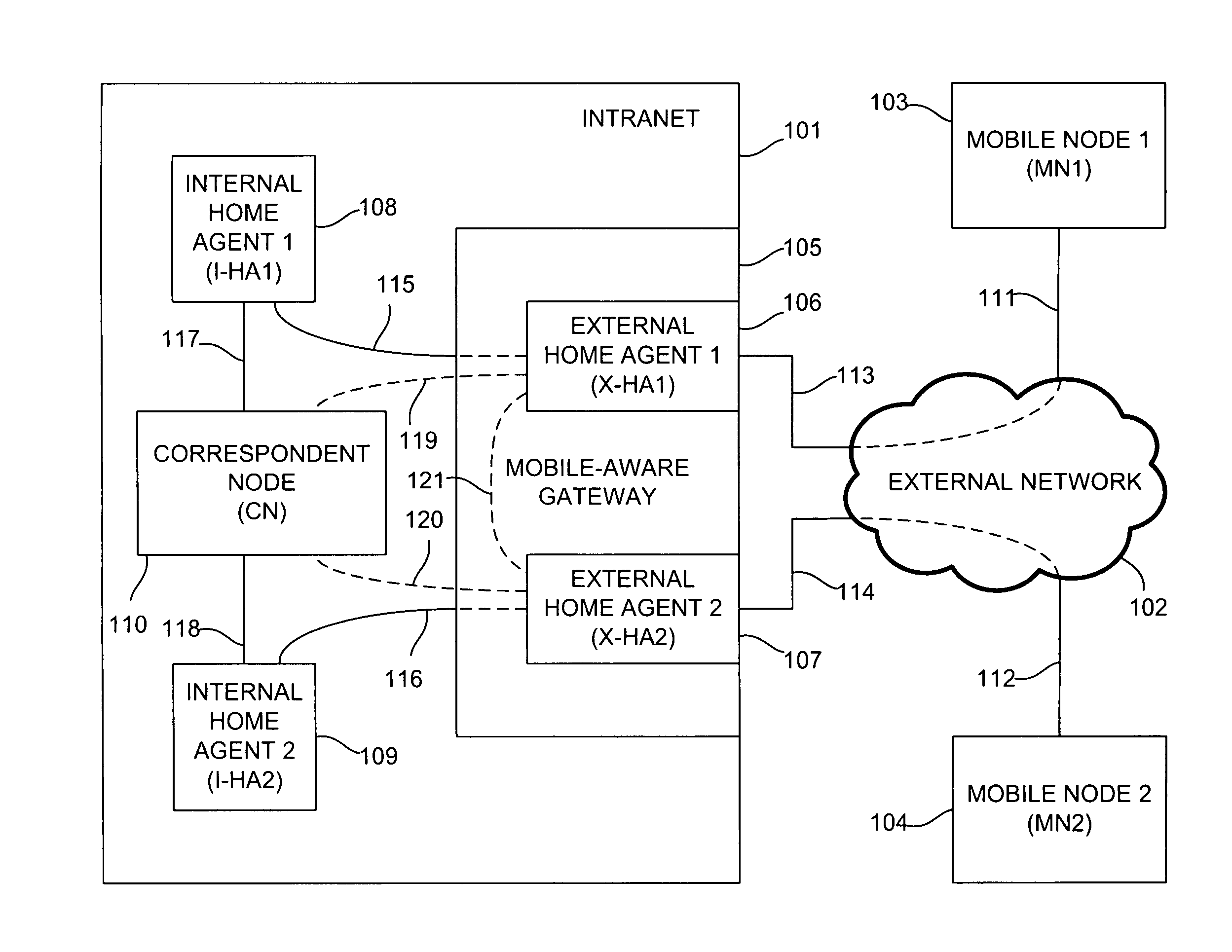
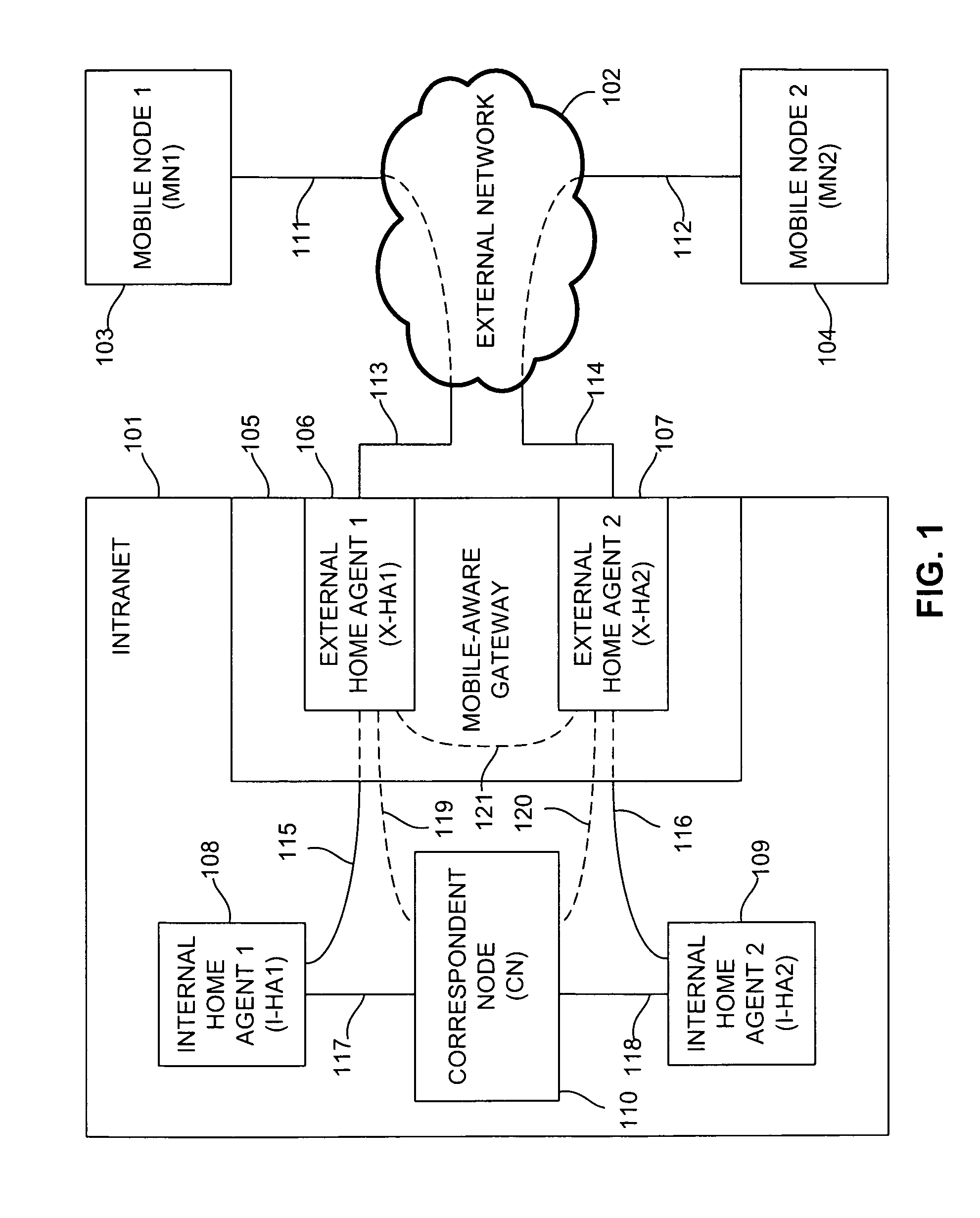
Method and apparatus for providing low-latency secure session continuity between mobile nodes
InactiveUS20060268901A1Connection managementData switching by path configurationWebIDConfidentiality
Owner:ALCATEL LUCENT SAS
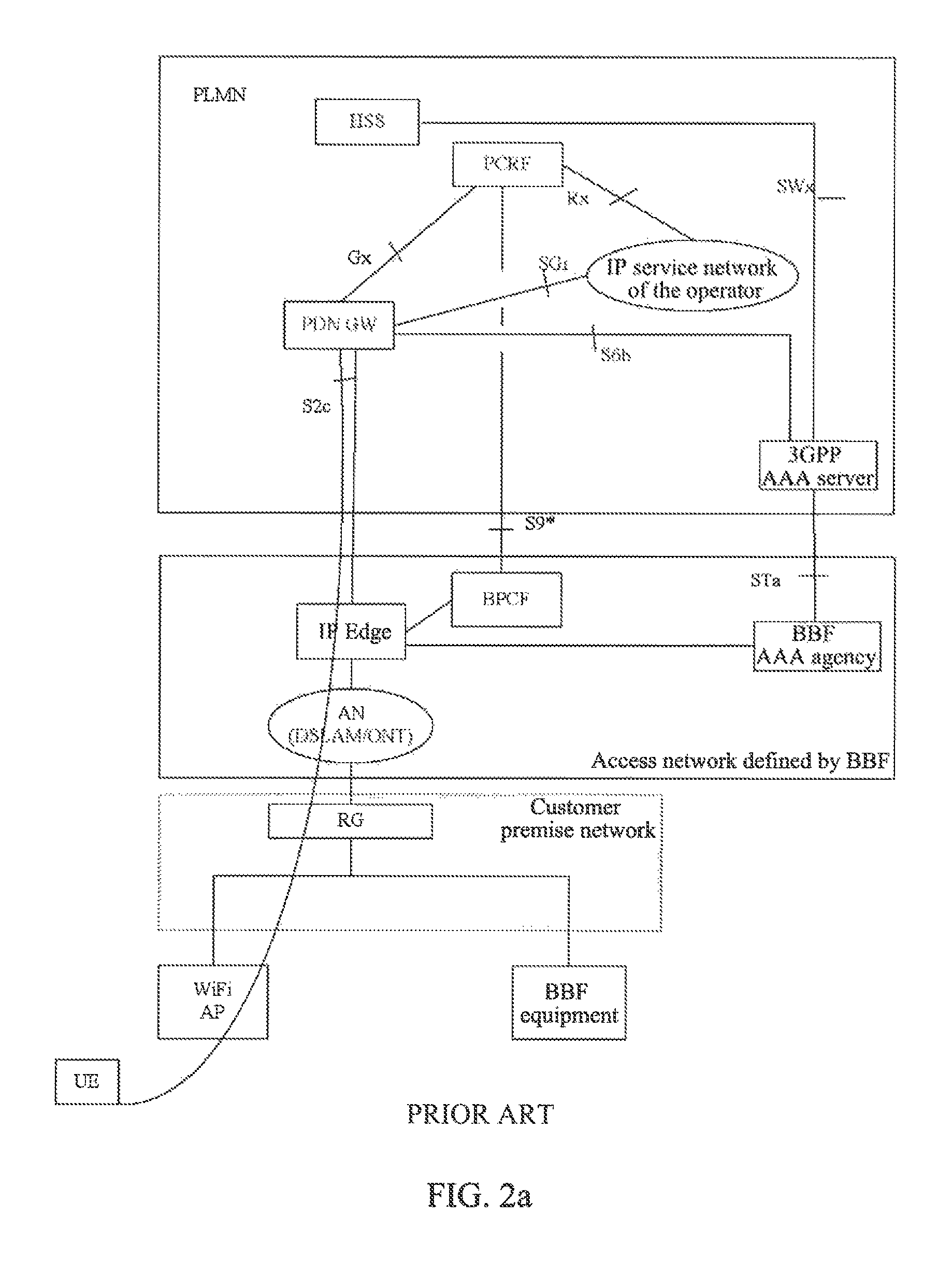
Systems and Methods of Providing An Intranet Internet Protocol Address to a Client on a Virtual Private Network
ActiveUS20080046994A1Efficiently assigningEfficient managementDigital data processing detailsAnalogue secracy/subscription systemsClient agentWebID
The intranet IP address management solution of the appliance and / or client described herein provides an environment for efficiently assigning, managing and querying virtual private network addresses, referred to as intranet IP (IIP) addresses of virtual private network users, such as a multitude of SSL VPN users on an enterprise network. The appliance provides techniques and policies for assigning previously assigned virtual private network addresses of a user to subsequent sessions of the user as the user logs in multiple times or roams between access points. This technique is referred to IIP stickiness as the appliance attempts to provide the same IIP address to a roaming VPN user. The appliance also provides a configurable user domain naming policy so that one can ping or query the virtual private network address of a user by an easily referenceable host name identifying the user. The appliance and / or client agent also provide techniques to allow applications to seamlessly and transparently communicate on the virtual private network using the virtual private network address of the user or client on the private network.
Owner:CITRIX SYST INC
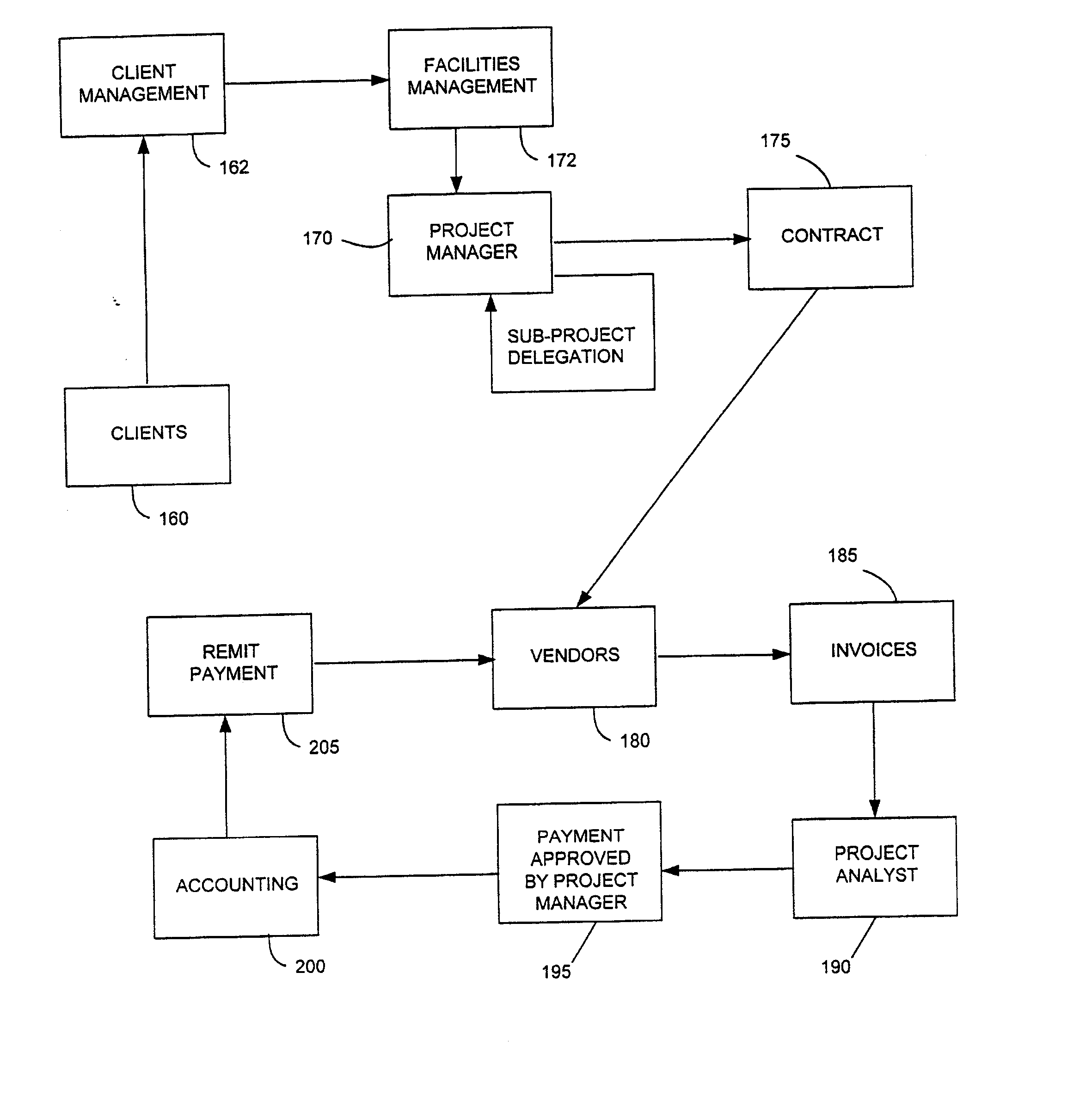
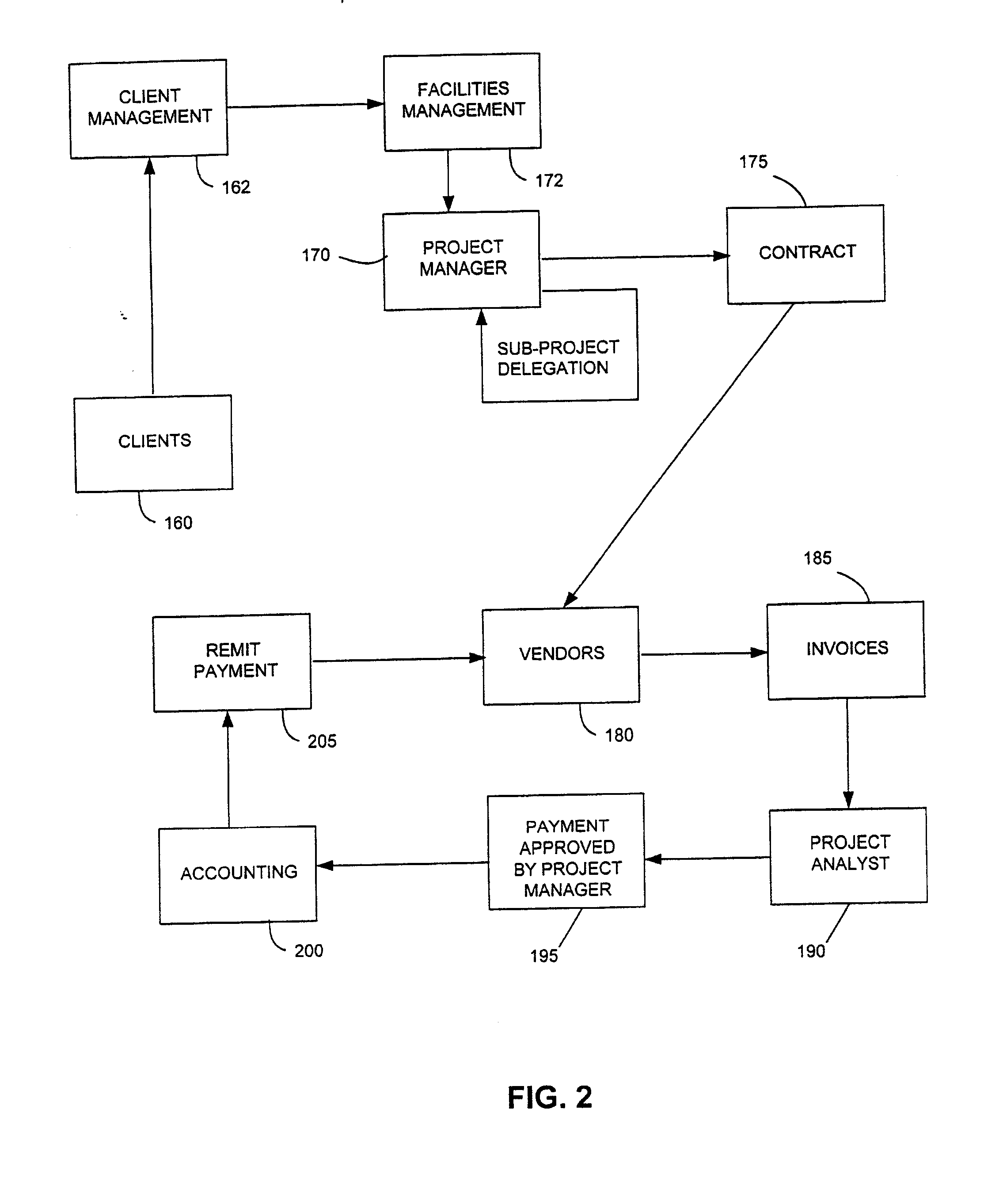
System and method for automatic financial project management
InactiveUS20080027861A1Reduce deliveryMaximal functionalityFinancePayment architectureAutomatic controlWebID
A system and method for providing project management tools to support construction, renovations, maintenance and other projects. The system automates the creation, processing and approval cycles of the numerous documents involved with each project. The system provides standardized work processes through processing templates. The system provides automated control and management of the process. The system allows project initiation and funding approval by clients throughout the corporation via a desktop browser coupled to a corporate Intranet. A software application embodying the present invention and its underlying technology are appropriate for a paper intensive area. It reduces the approval cycle of projects. It automates the creation, processing and approval cycle of documents by routing documents electronically for on-line approval.
Owner:JPMORGAN CHASE BANK NA
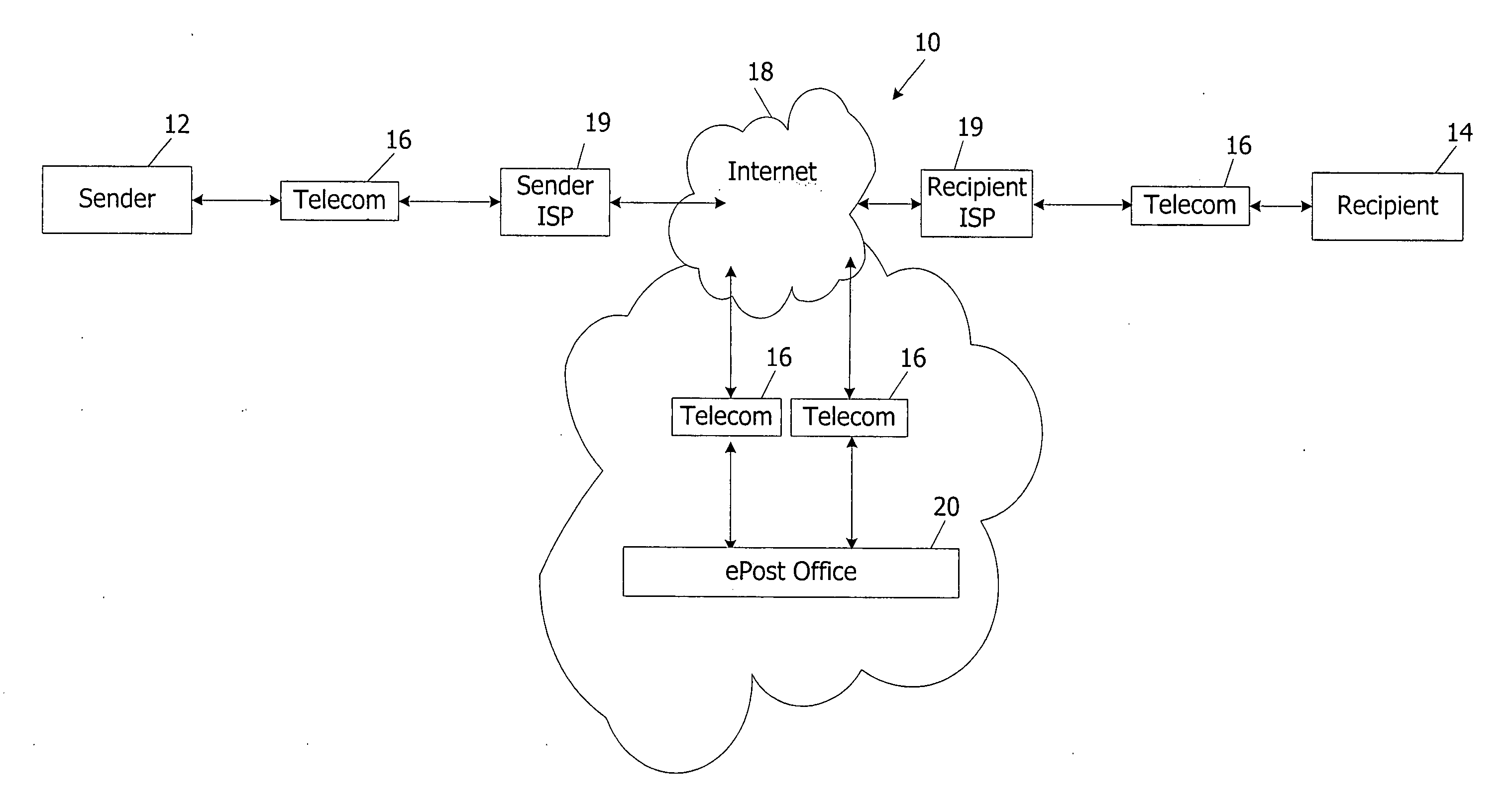
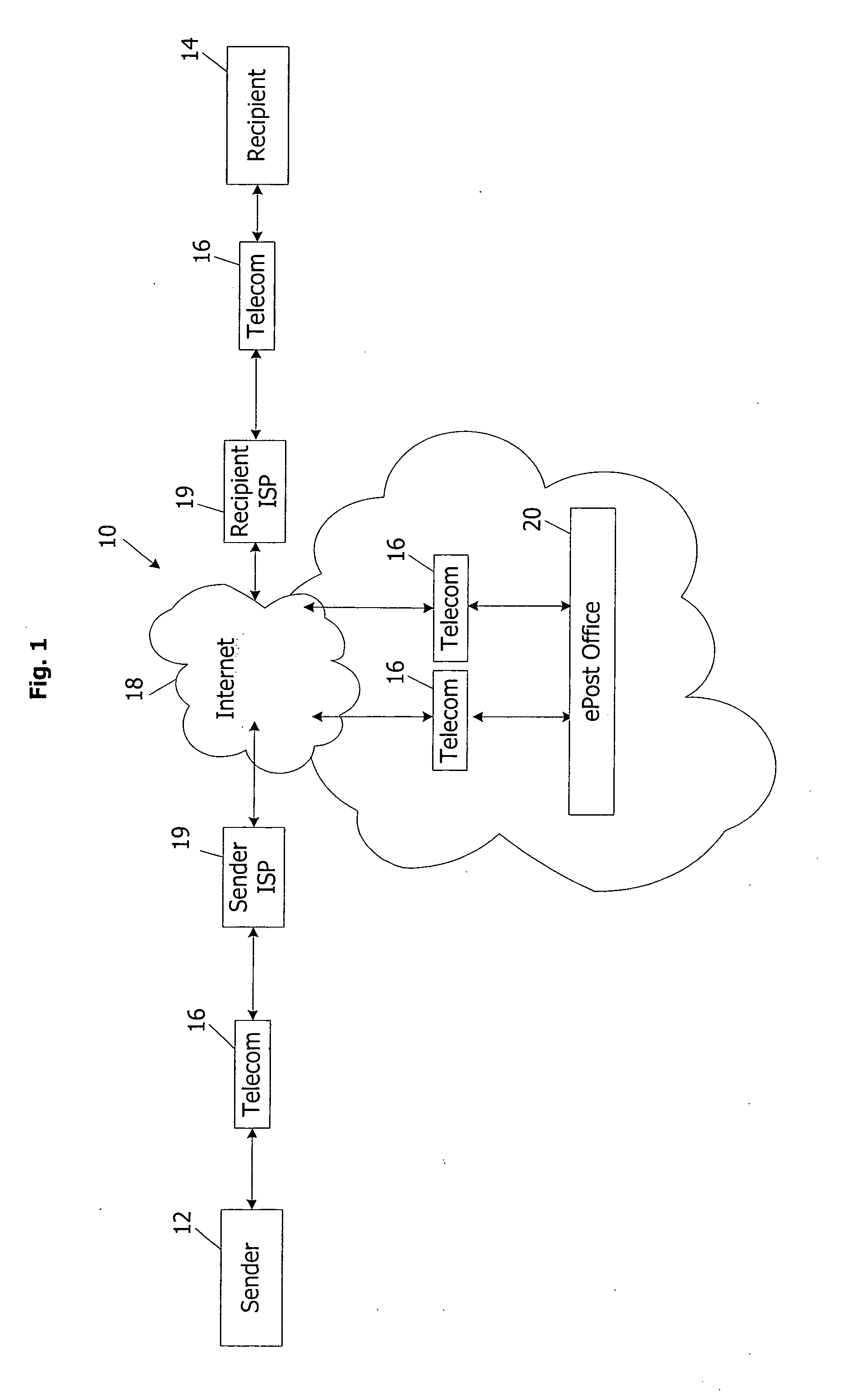
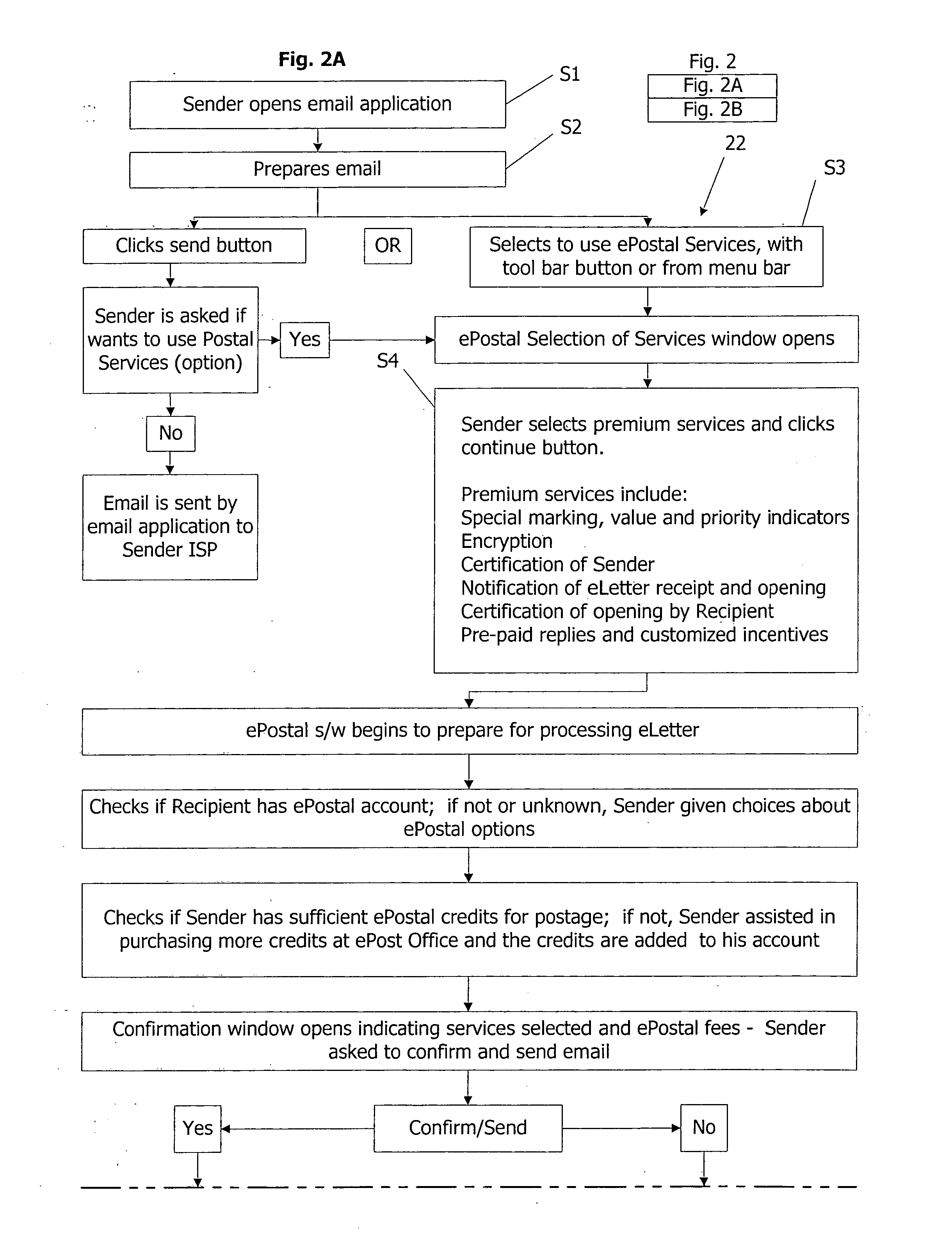
Messaging and document management system and method
InactiveUS20060168074A1Increase opportunitiesGood serviceMultiple digital computer combinationsData switching networksPaymentWebID
A communication system and method transmits electronic mail among multiple users that are senders or recipients of the mail, or both. The system and method use and augment the Internet with a postal server and software linked to the Internet. The sender and recipient have terminals also linked to the Internet. The sender uses postal sender software to select transmission with certain premium services. The system and method include payment and accounting functions for use of the premium services. The system and method can operate with plural postal servers at one or more locations. Communications can utilize the postal server and software only for processing data about the message and / or its transmission. Communications among the Sender, Recipient, and postal server can create virtual intranet-like qualities. Transmitted electronic mail uses message data to identify the Sender, authenticate and verify the email, and direct its processing.
Owner:EPOSTAL SERVIES INC
Systems and methods for resolving resource names to IP addresses with load distribution and admission control
InactiveUS20080147885A1Locally resolveQuick fixMultiple digital computer combinationsTransmissionLoad SheddingWebID
Systems and methods are disclosed for resolving URIs to IP addresses and port numbers in an intranet, in which the host processors of the intranet individually maintain a data store with entries indicating the status of service application ports provided by the other hosts of the intranet, and URIs within the intranet are resolved at the host processing nodes without DNS server consultation by local address resolution components that provide load shedding and load balancing according to the data store entries.
Owner:LUCENT TECH INC
Systems and Methods for a Real-Time Workflow Platform
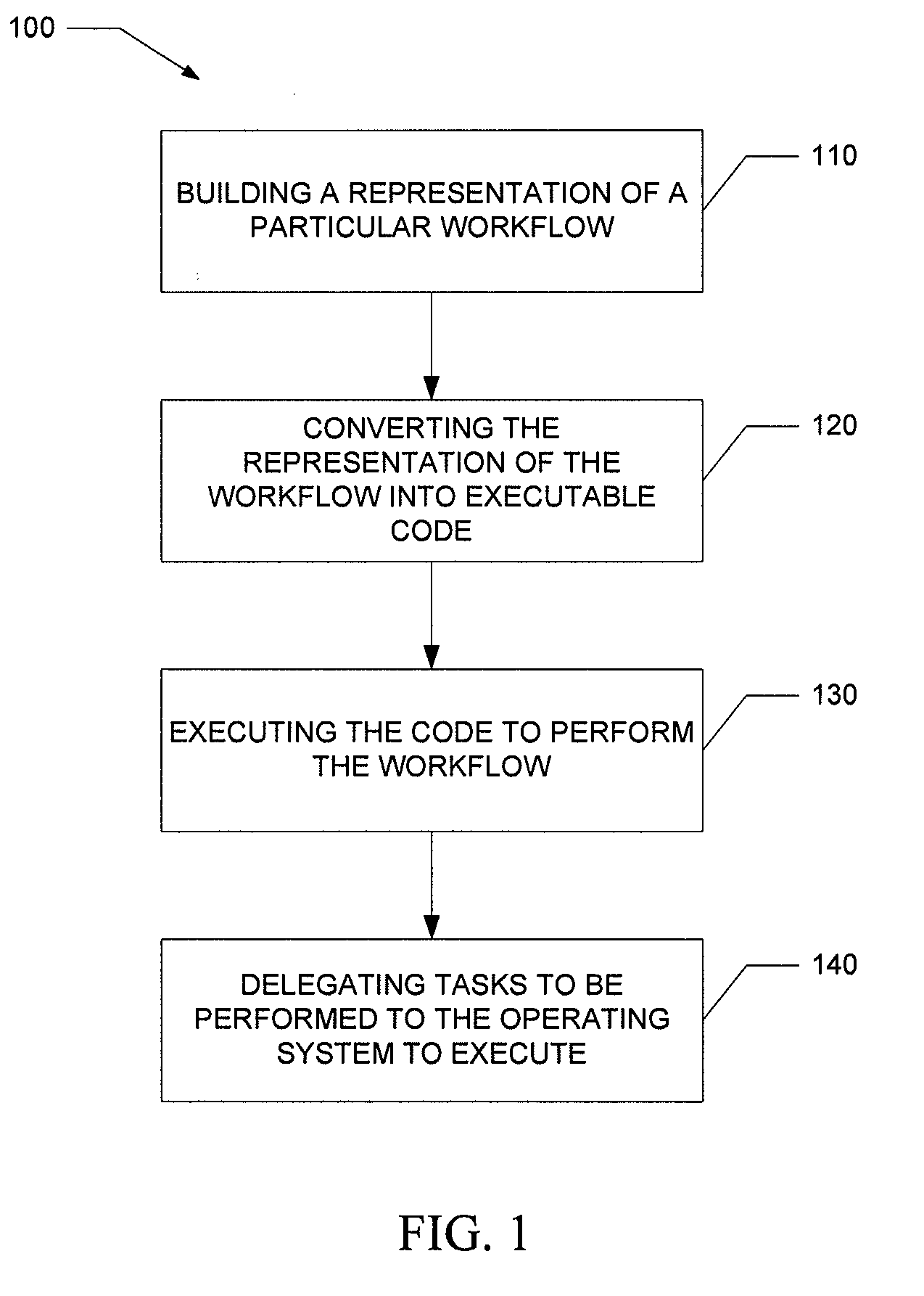
ActiveUS20100280865A1Computation using non-denominational number representationResourcesAbstraction layerOperational system
Various embodiments of the present invention provide systems and methods for enabling design, generation, and execution of real-time workflows. Such embodiments provide a graphical designer including a plurality of shapes representing the various objects of a workflow that are used to model the workflow. In addition, various embodiments of the graphical designer provide shapes to model aspects of the workflow not found in previous graphical designers. Various embodiments also provide a code generator that converts the representation of the workflow into executable code for multiple target languages. Various embodiments also provide a workflow engine based on a Petri net model responsible for executing the workflow and for delegating tasks to be performed for the workflow to an operating system. In various embodiments, the workflow engine further includes a platform abstraction layer that provides a transition layer from the Petri net language to the operating system language.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
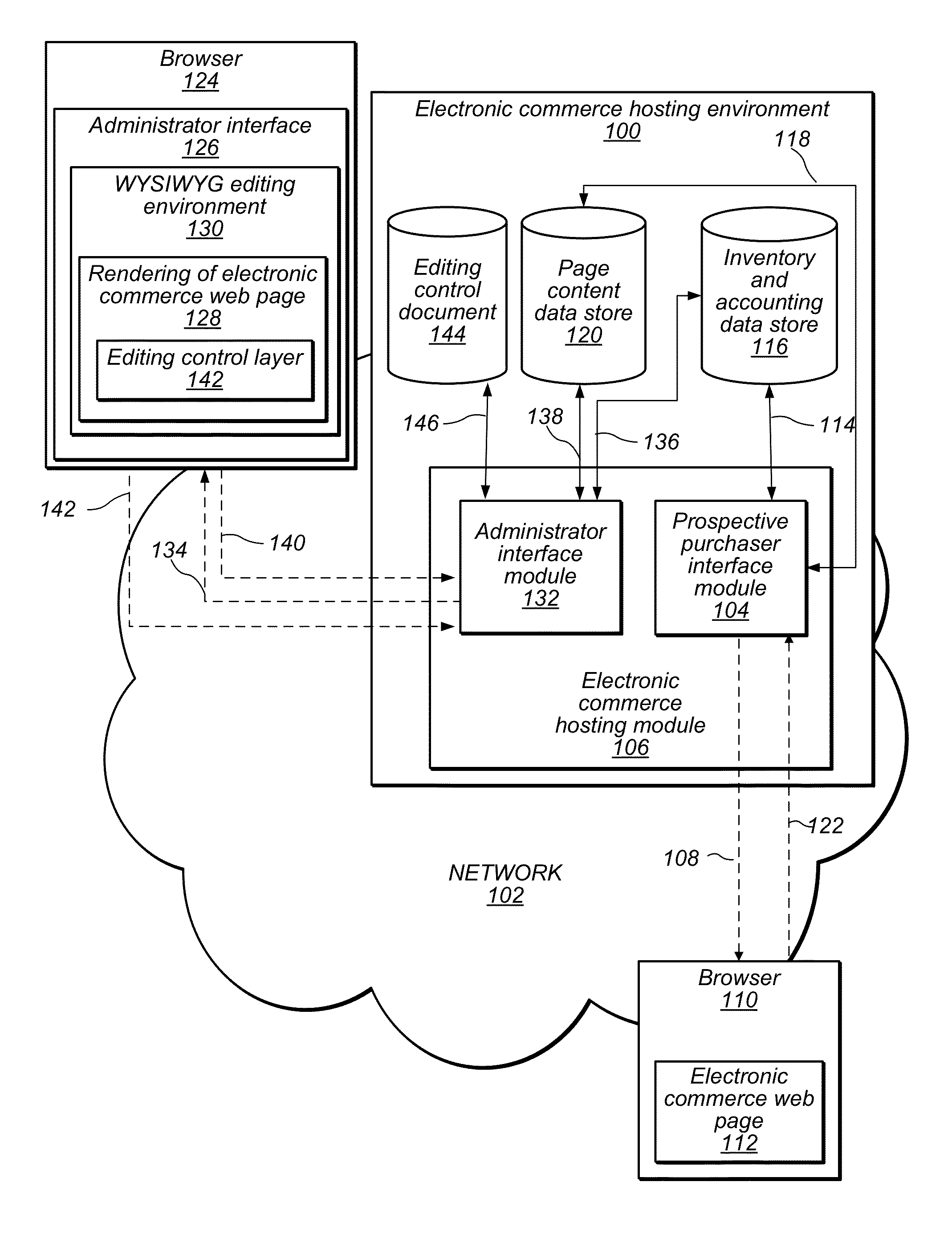
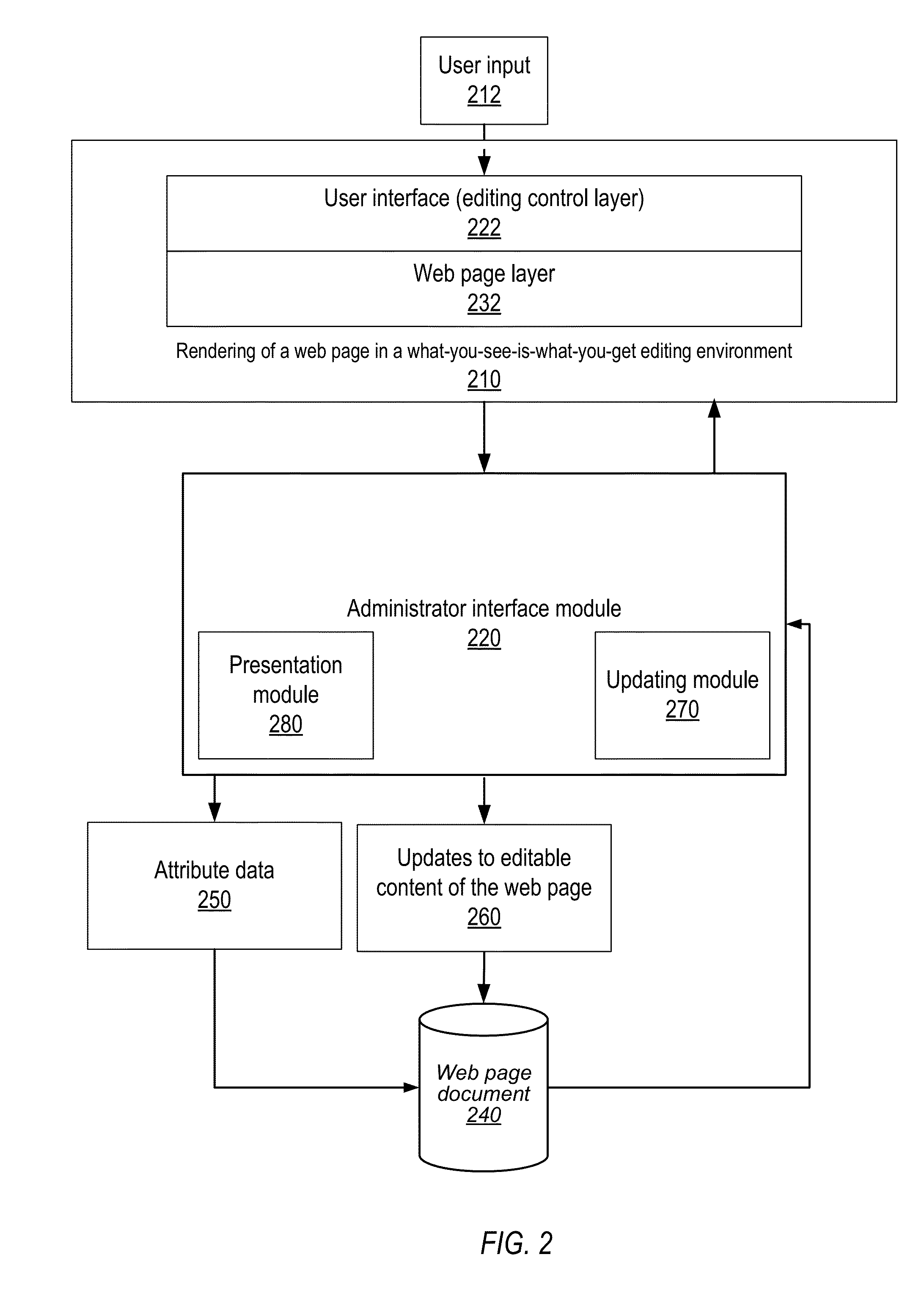
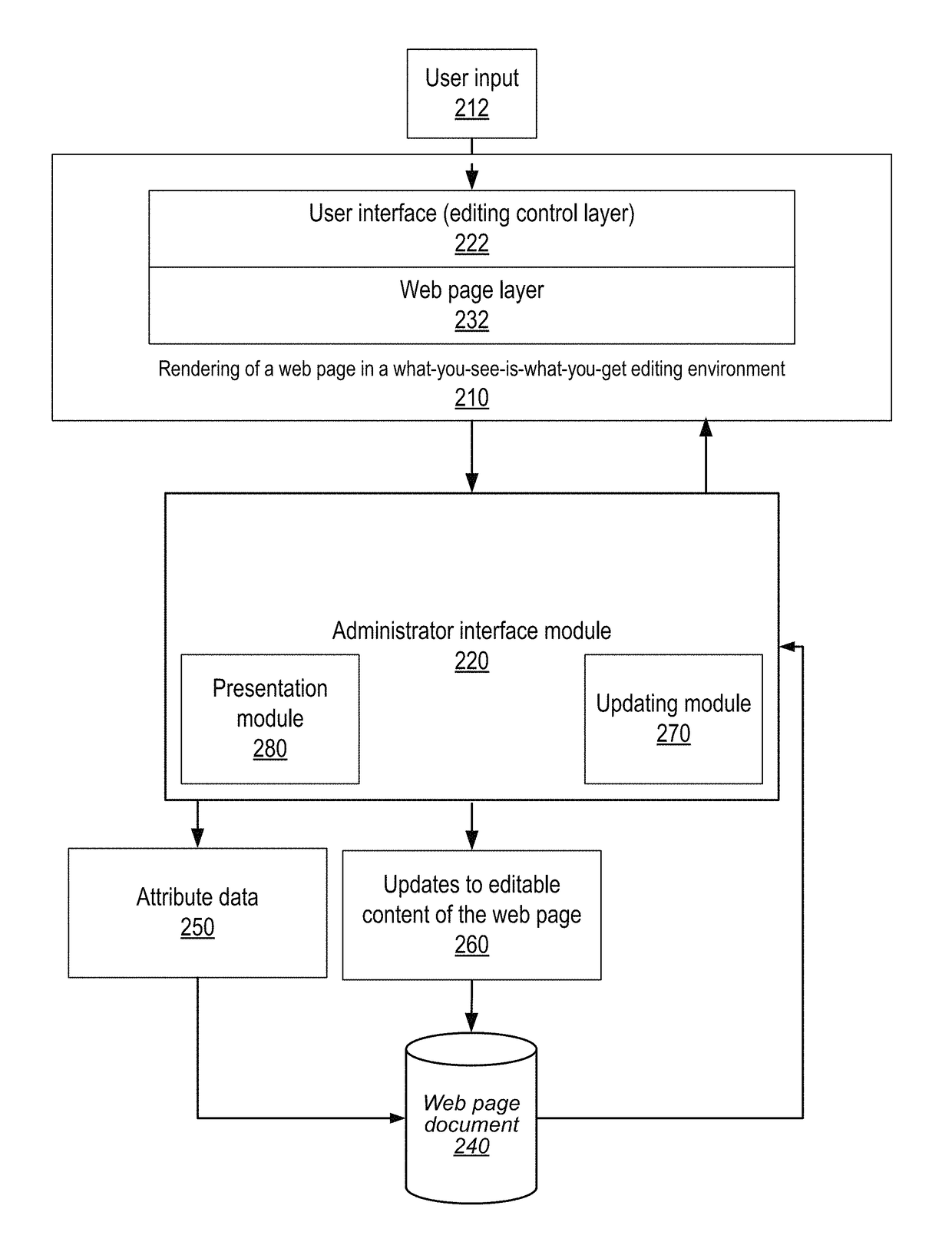
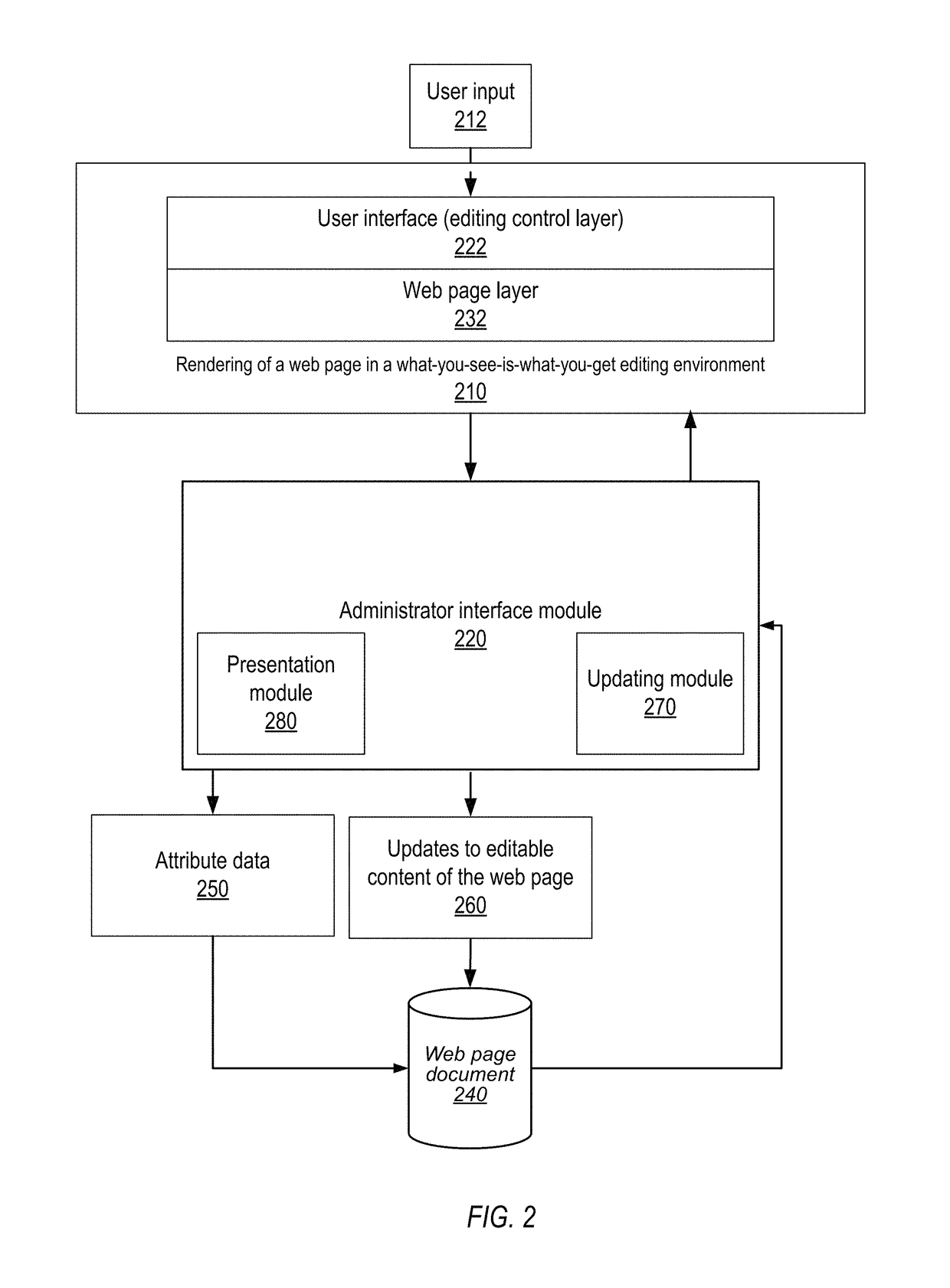
Methods and apparatus for in-line editing of web page content with reduced disruption of logical and presentational structure of content
InactiveUS8522134B1Reduce disruptionNatural language data processingWebsite content managementControl layerWebID
Owner:KIBO SOFTWARE INC
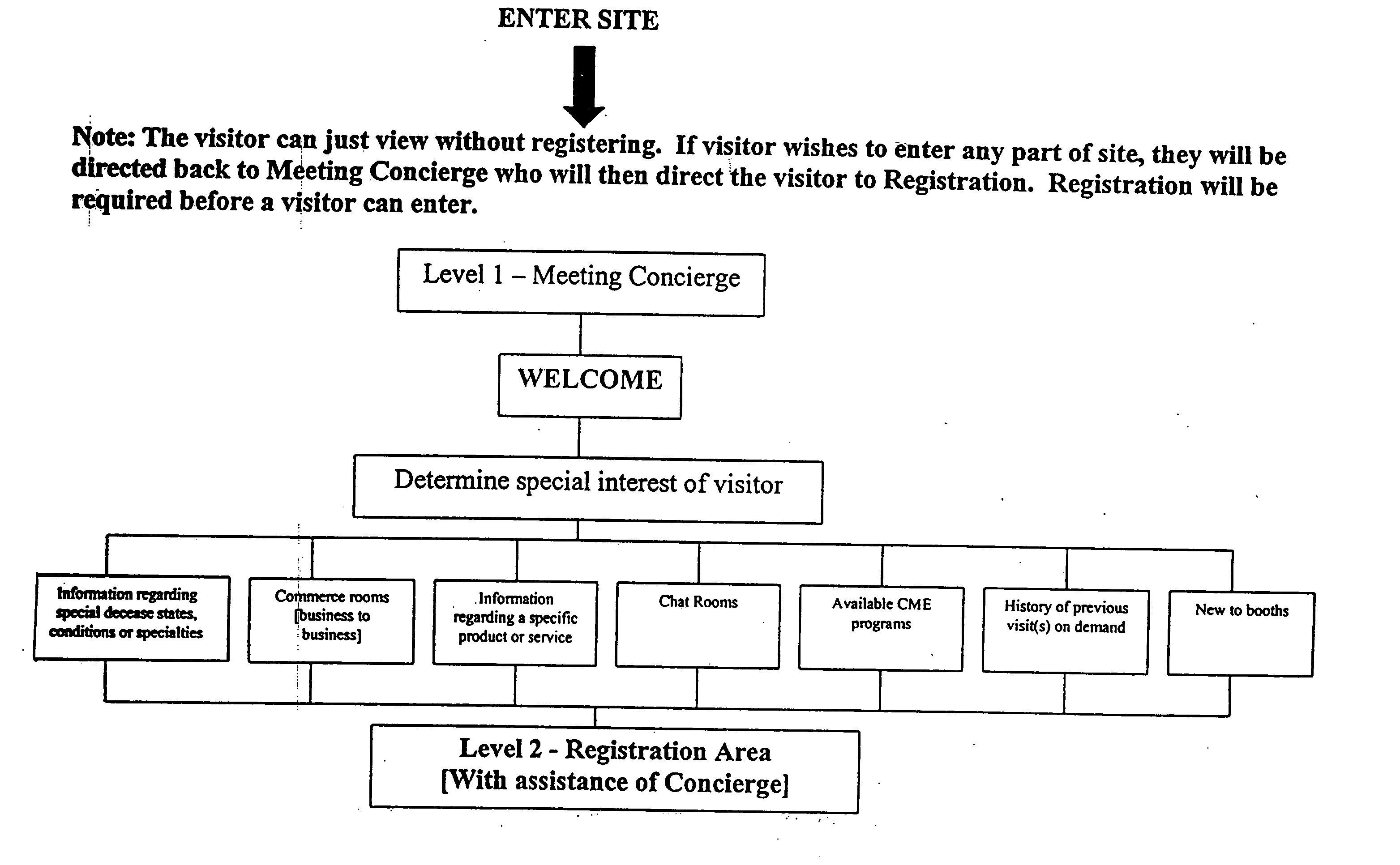
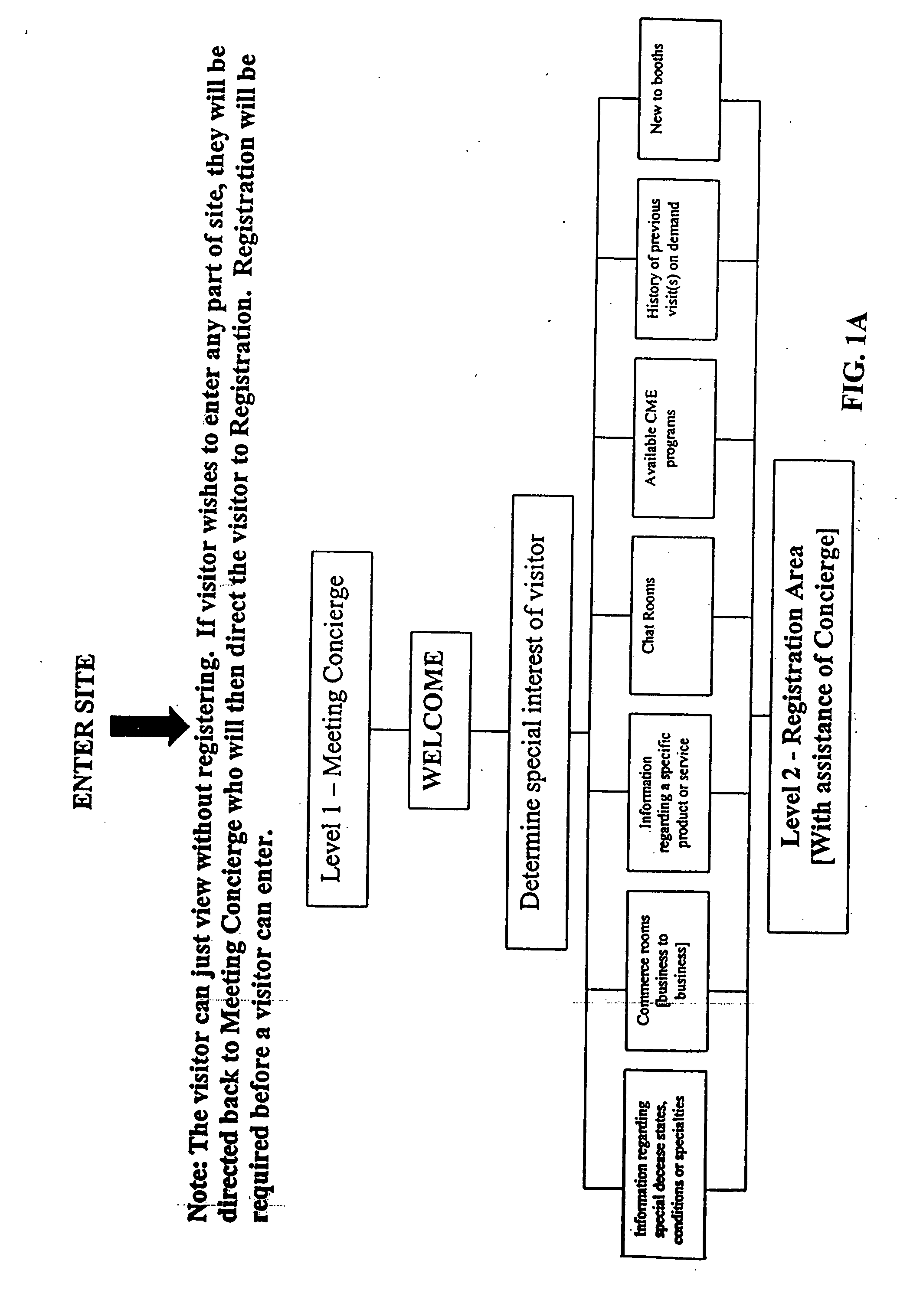
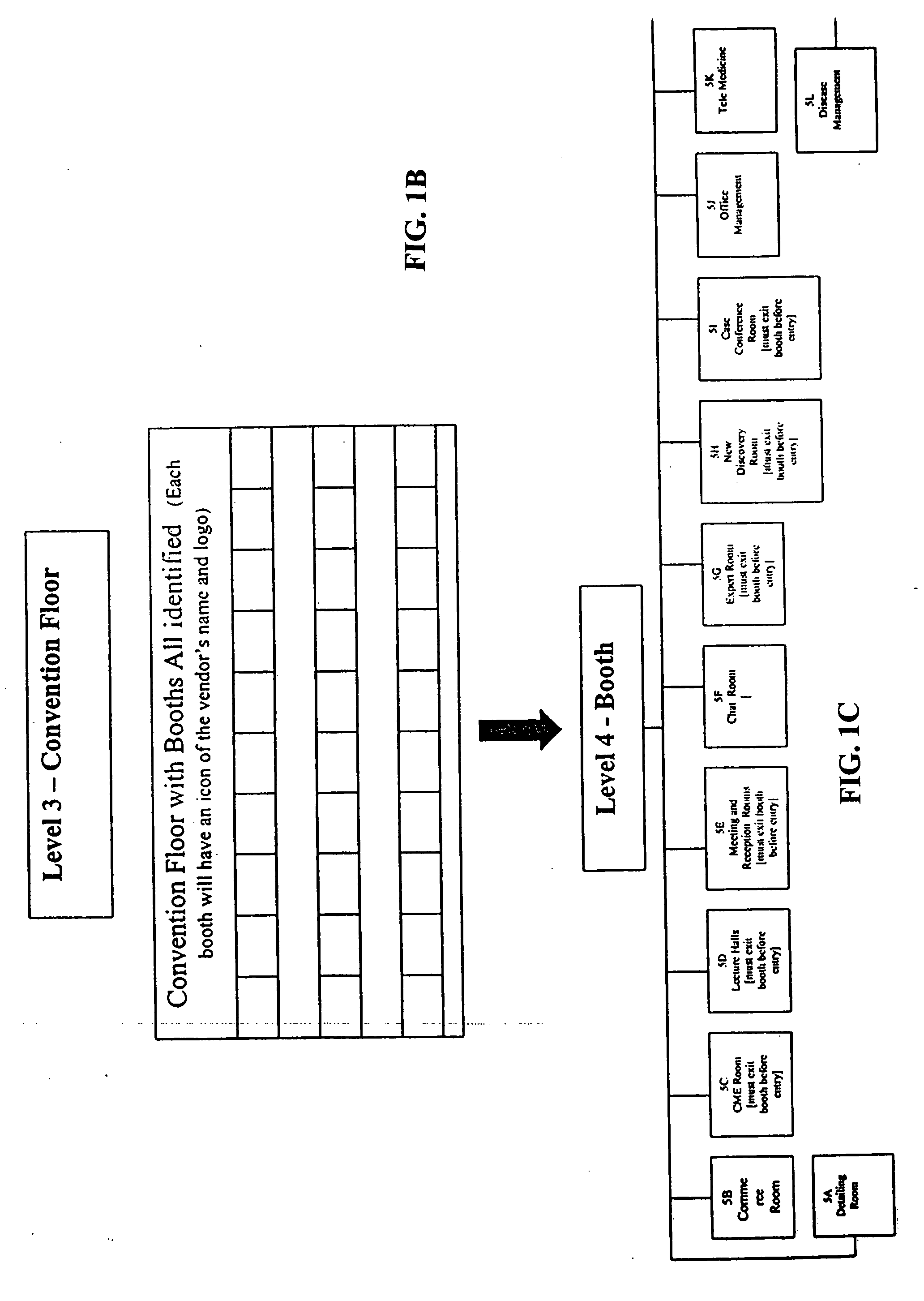
System and methods for providing a healthcare industry trade show via internet
A system or method for providing a 3-D virtual healthcare industry trade show via internet including at least one server computer for collecting, assembling, storing, correlating, or otherwise processing information desired by a participant of the healthcare industry, and at least one other computer used by the participant of the healthcare industry connected via internet or intranet to conduct transactions with other participants or exhibitors of the healthcare industry trade show. Other embodiments include means for leaving any facility or any activity in progress and then return to at the same location, timing to continue without starting from the beginning of the visit or activity, means for creating a 3-D virtual Continuing Education facility, and means for disseminating FDA permitted off-label product promotions which are scientific and educational in nature to medical community as delivered by independent third parties in the formats of clinical trials, special studies, and grand rounds.
Owner:SHELTON JOHN S +1
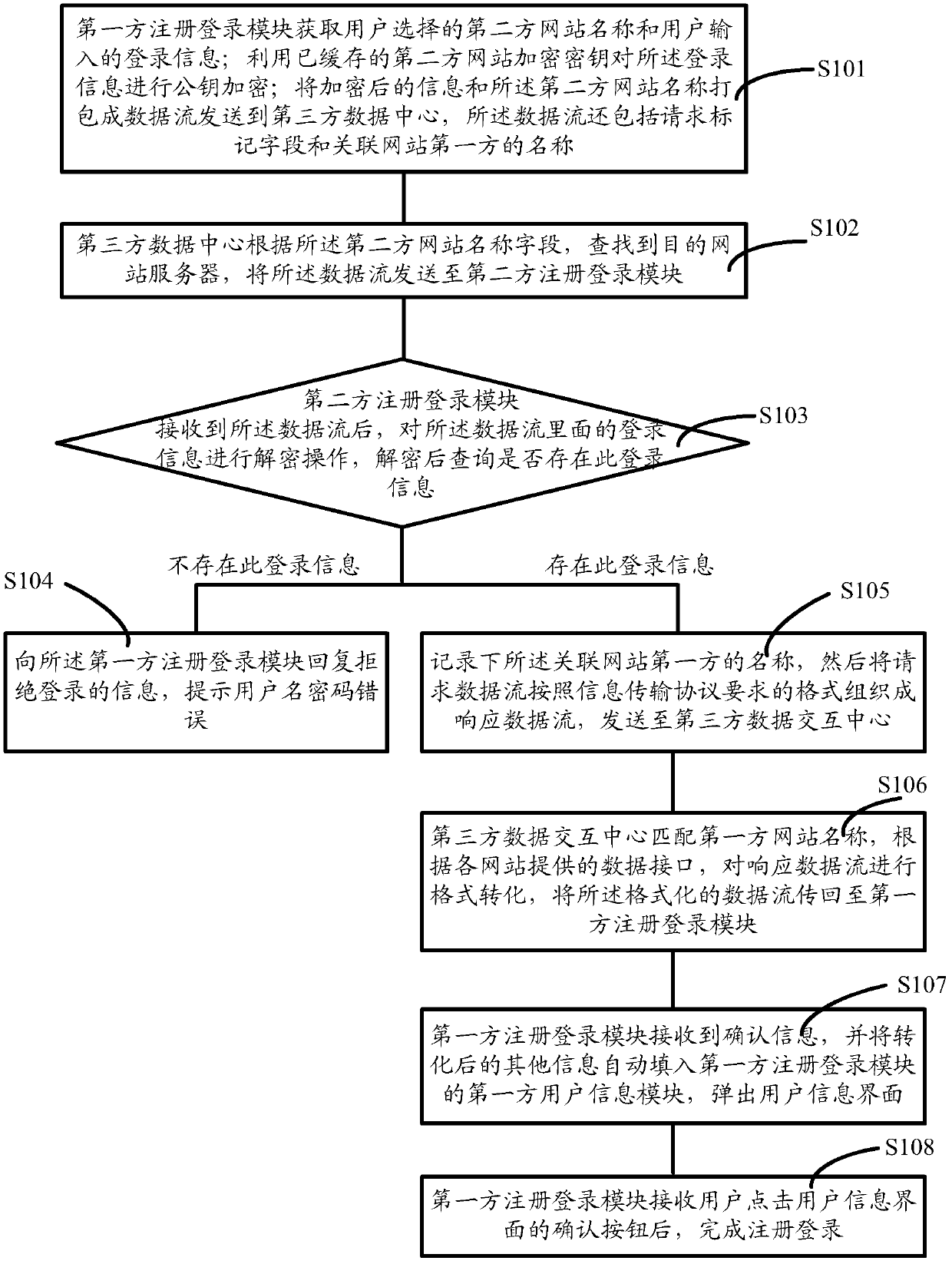
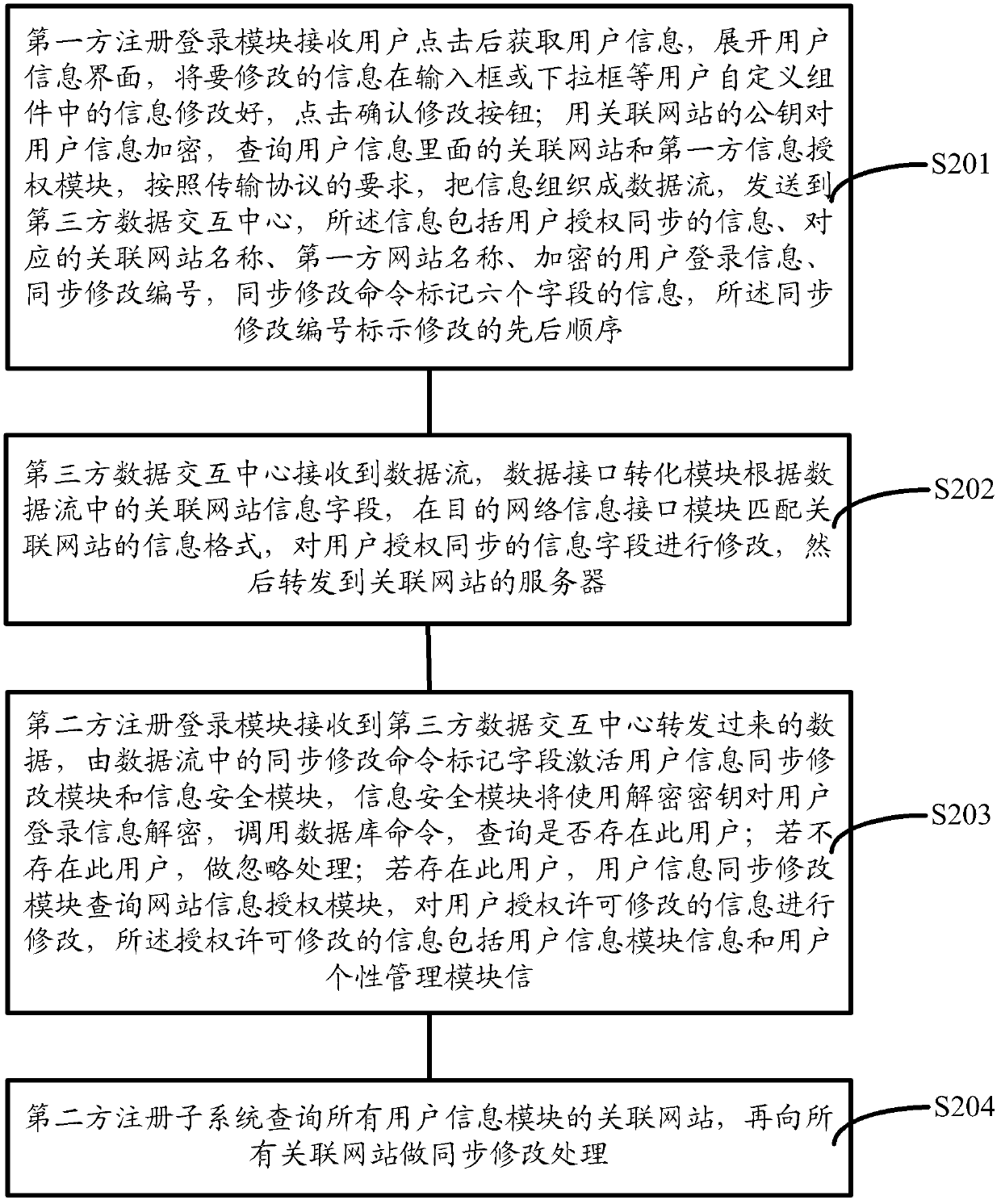
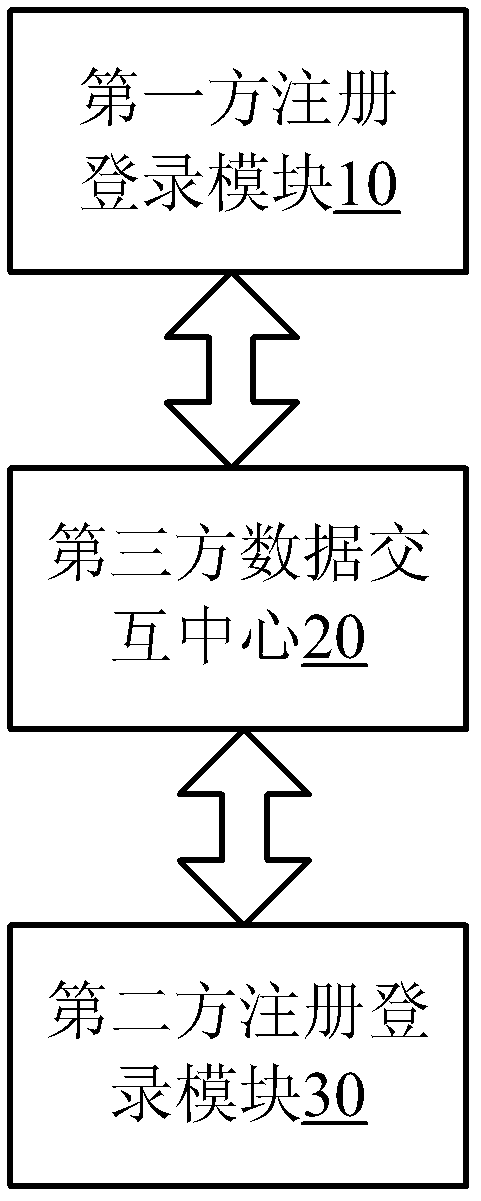
Method and system for carrying out whole-network login authentication by utilizing registered website user information
ActiveCN102624728ASolve the problem of different login information that is difficult to rememberImprove user experienceTransmissionWeb siteThird party
The invention discloses a method and a system for carrying out whole-network login authentication by utilizing registered website user information. The method of the embodiment of the invention includes the following steps that: the second-party website name selected by a user and the login information inputted by the user are acquired by a first-party registered login module; the encrypted information and the second-party website name are packaged into a data stream which is sent to a third-party data interaction center; according to the second-party website name field, the third-party data interaction center finds a destination website server, and sends the data stream to a second-party registered login module; after receiving the data stream, the second-party registered login module queries whether the login information exists; if the login information does not exist, login-denying information is returned to the first-party registered login module, and 'username or password is incorrect' is promoted; and if the login information exists, the first-party registered login module fulfills registered login after the user clicks the 'OK' button of a user information interface.
Owner:ZHEJIANG UNIV CITY COLLEGE
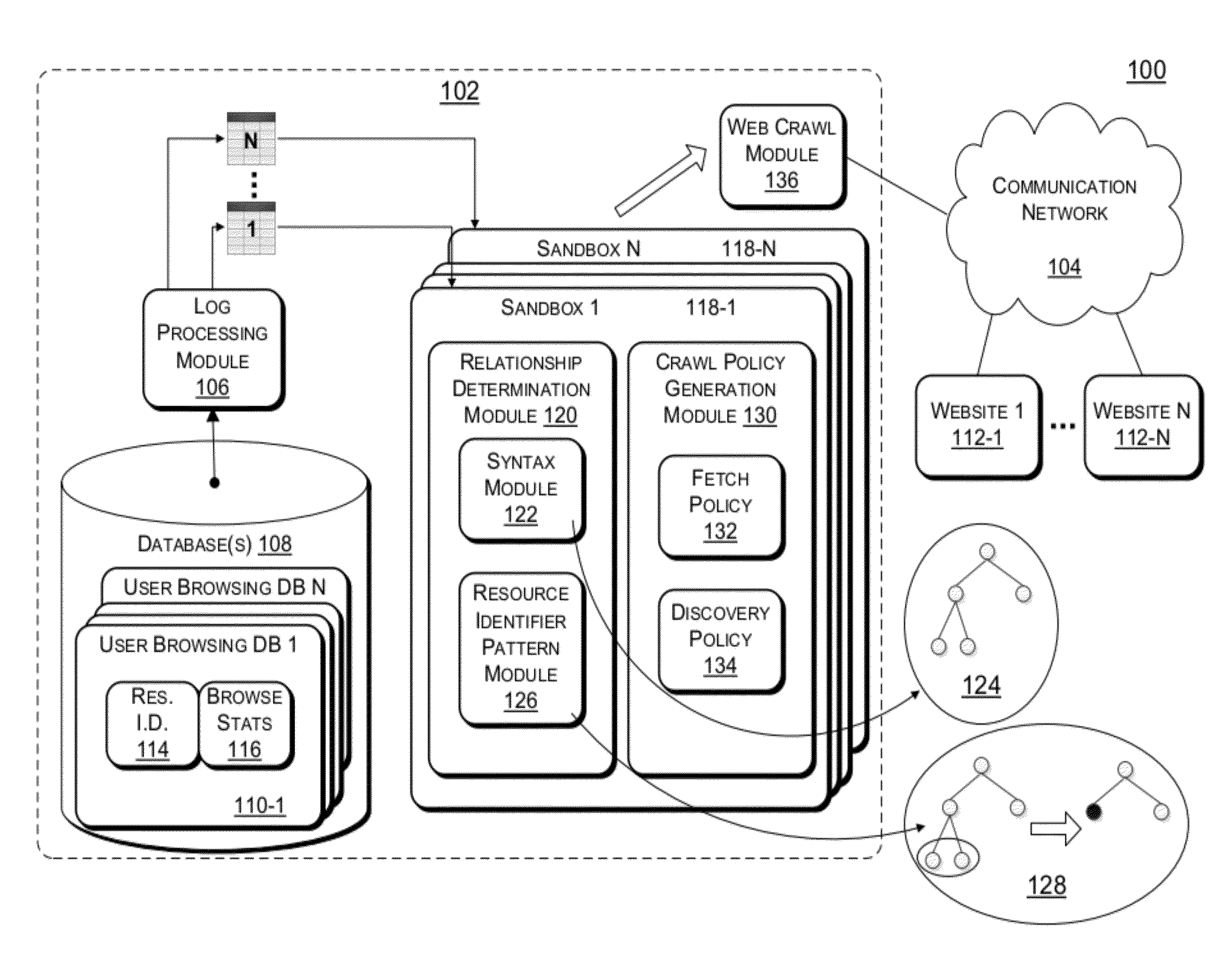
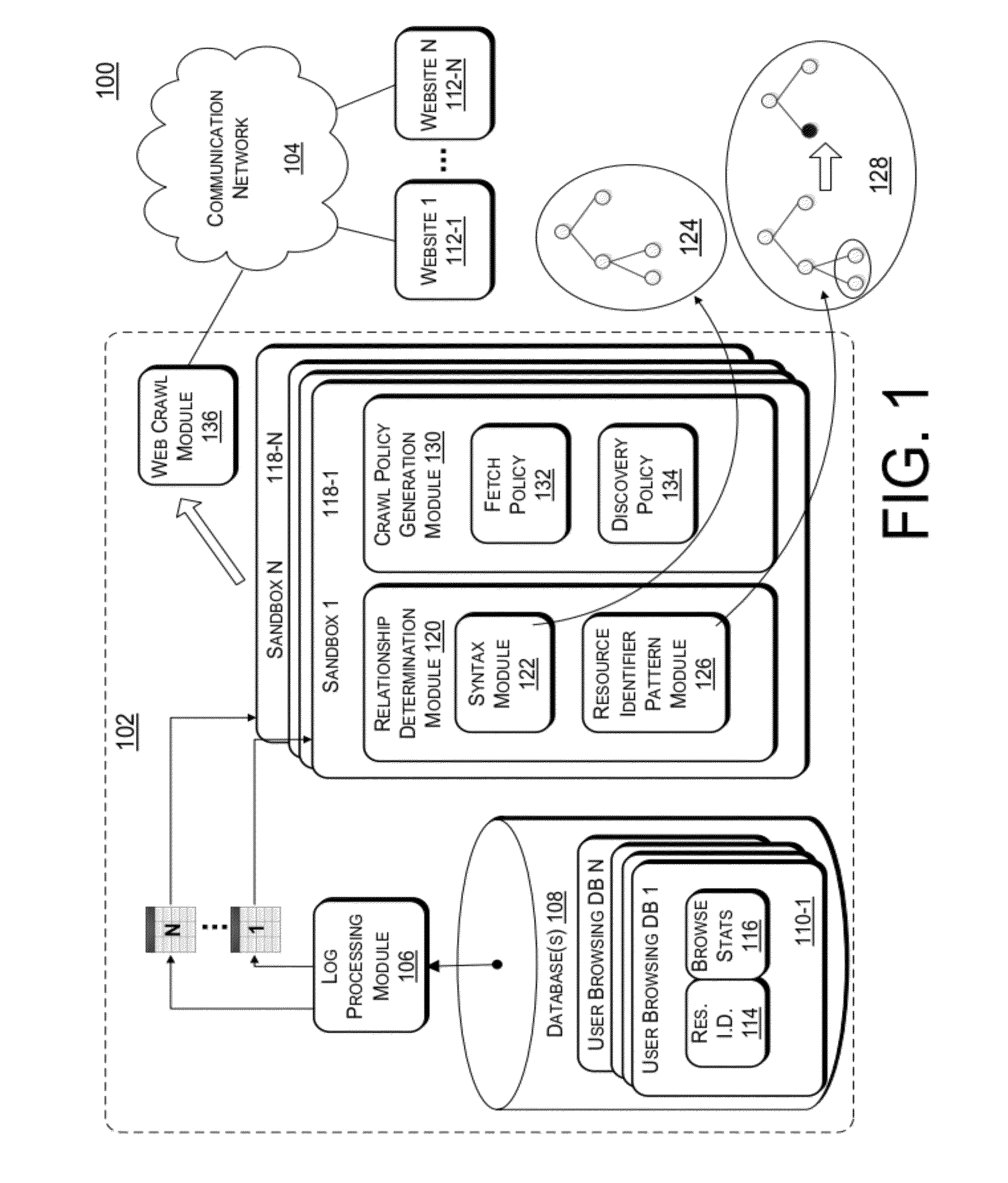
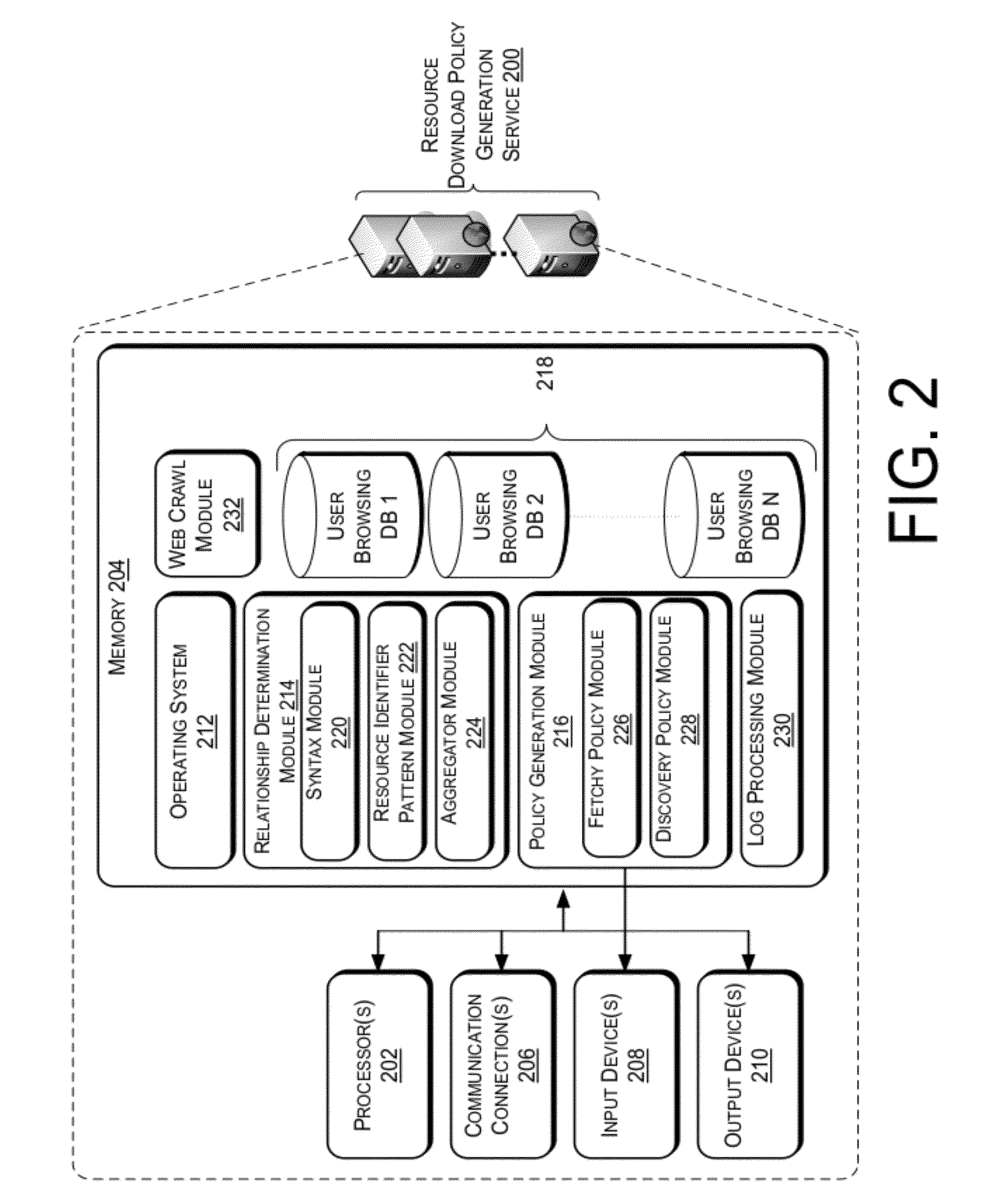
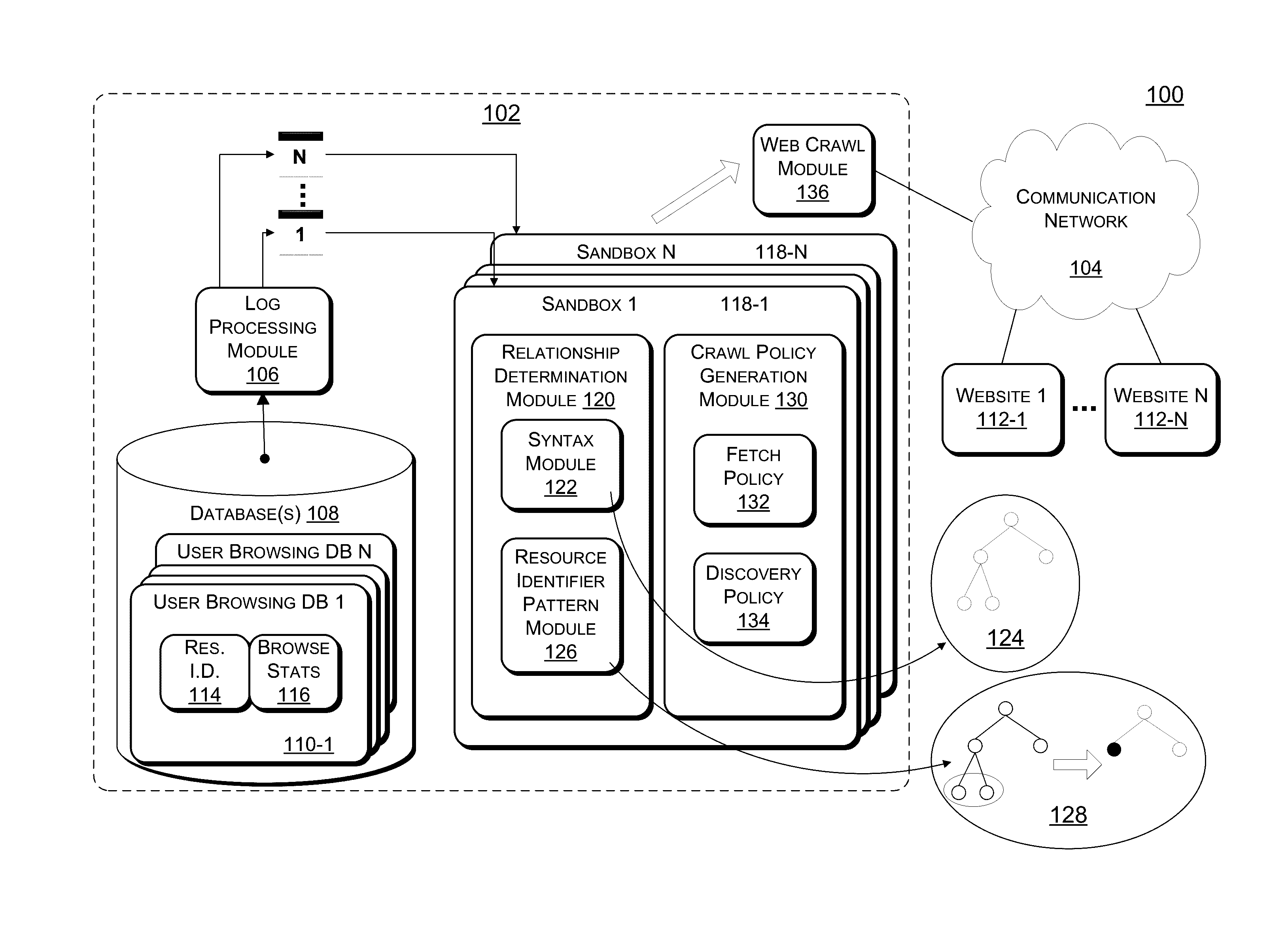
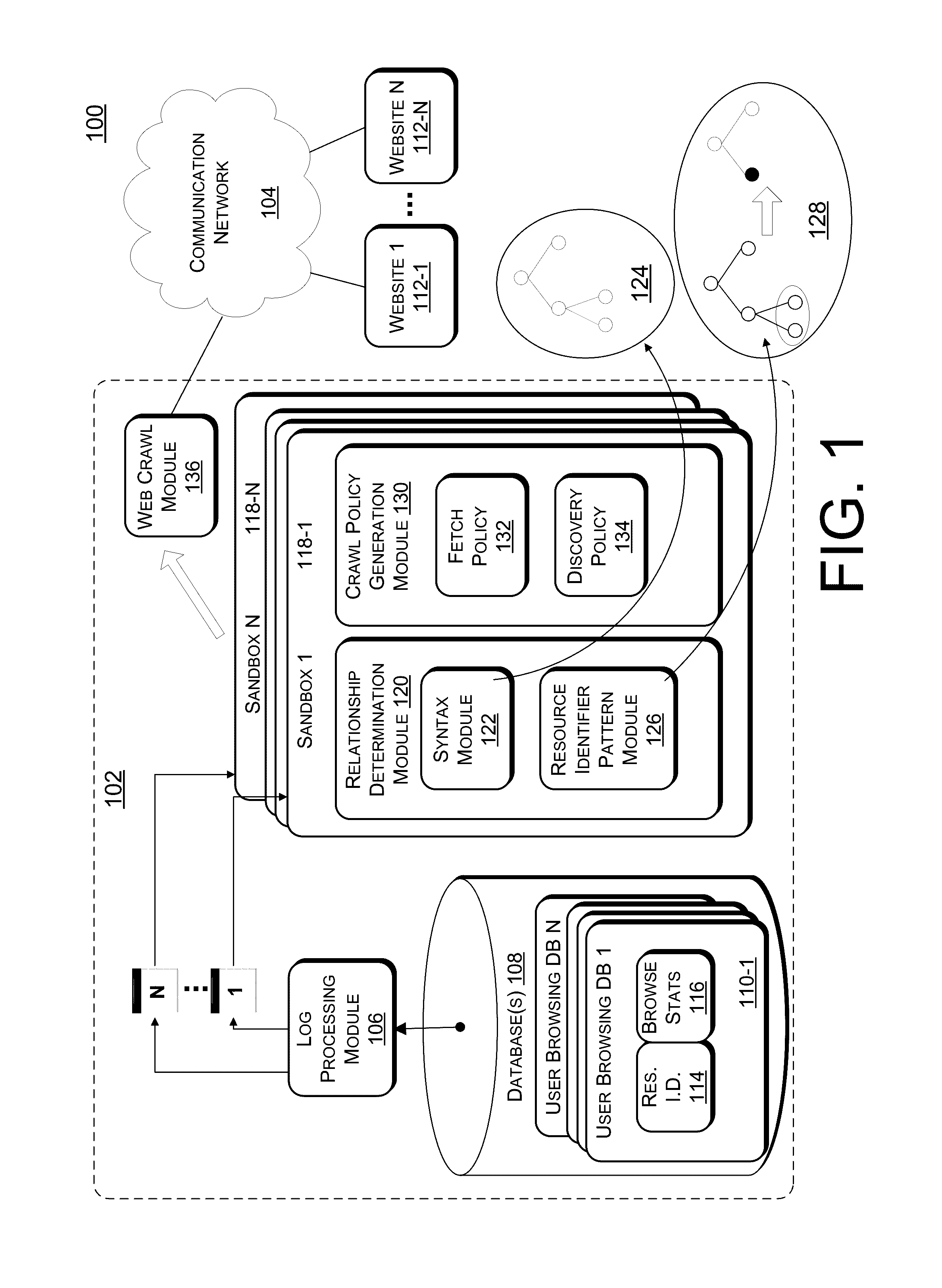
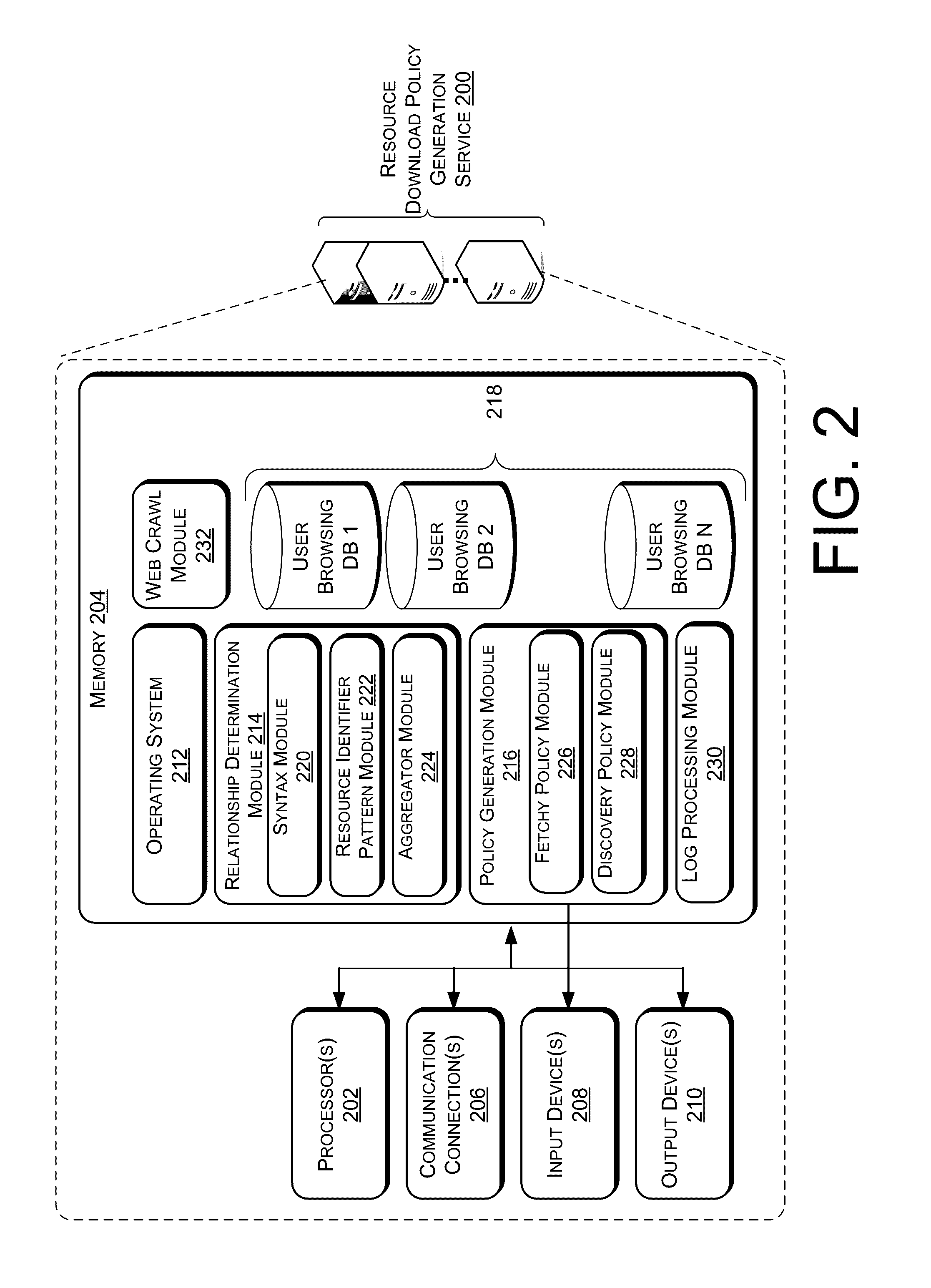
Resource Download Policies Based On User Browsing Statistics
ActiveUS20120303606A1Simple conceptLess computationally complexWeb data indexingDigital data processing detailsWeb siteWebID
Web crawling polices are generated based on user web browsing statistics. User browsing statistics are aggregated at the granularity of resource identifier patterns (such as URL patterns) that denote groups of resources within a particular domain or website that share syntax at a certain level of granularity. The web crawl policies rank the resource identifier patterns according to their associated aggregated user browsing statistics. A crawl ordering defined by the web crawl polices is used to download and discover new resources within a domain or website.
Owner:MICROSOFT TECH LICENSING LLC
System for creating/providing individual learning plan for learner using communication network
InactiveCN1383534AImprove learning enthusiasmData processing applicationsElectrical appliancesWebIDNetwork connection
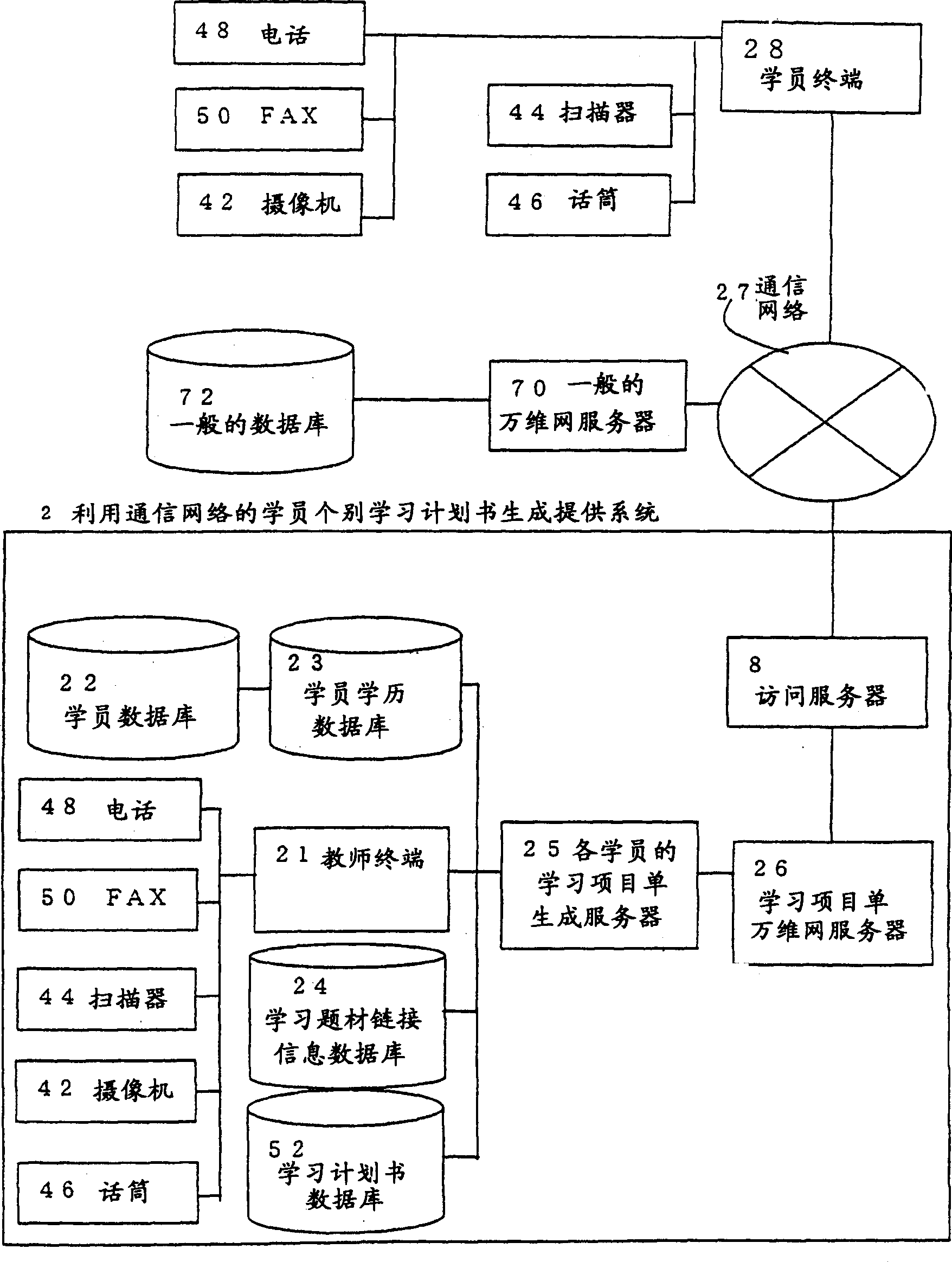
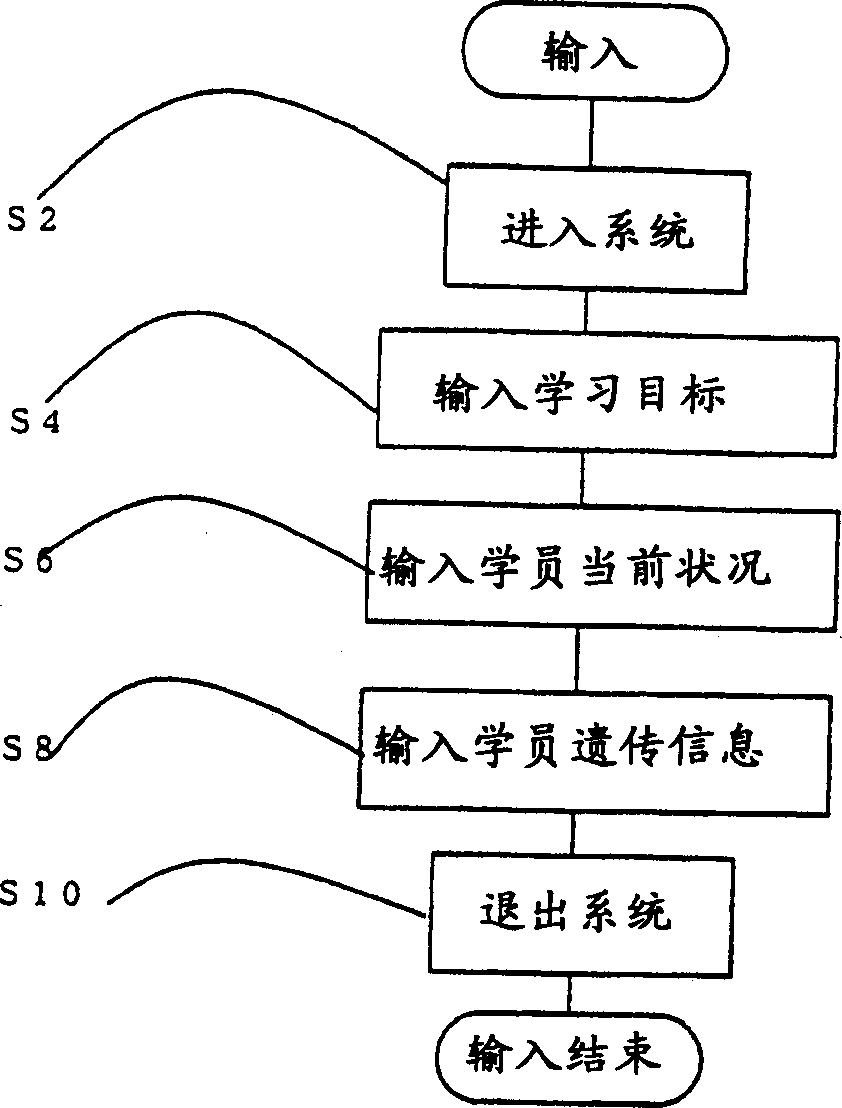
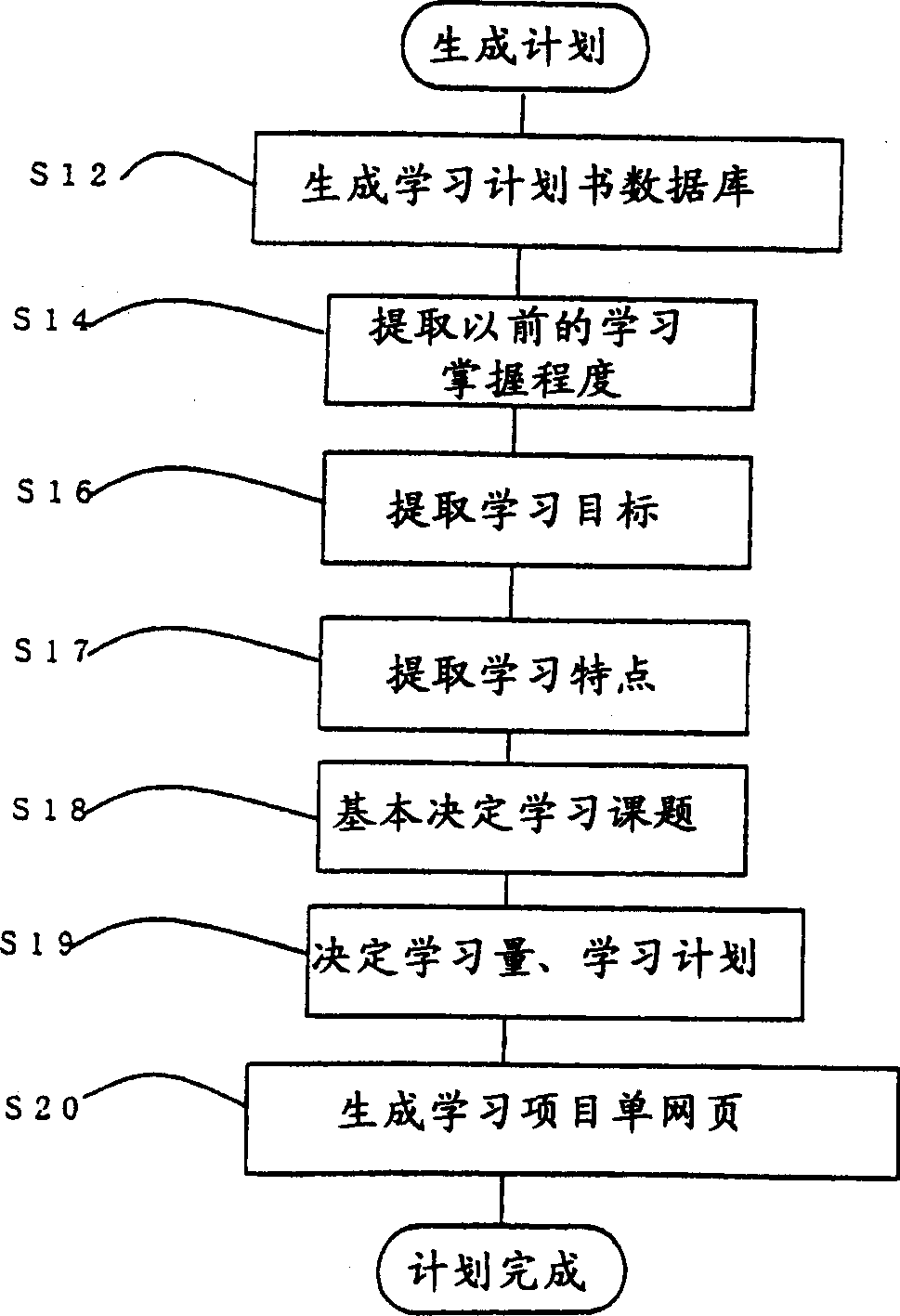
The invention relates to a student individual study plan generation and provision system that supports teachers to provide students with clear goals corresponding to changes in the development stage of learning, and a student individual study plan generation and provision system, comprising: an access server connected to a communication network and an access server electrically The learning item list web server, the learning item list generating server for each student electrically connected to the learning item list web server, the student academic qualification database electrically connected to the learning item list generating server for each student, the student database electrically connecting with the student academic qualification database, and the The teacher terminal that is electrically connected to the learning item list generation server of each student, the learning subject link information database that is electrically connected to the learning item list generation server of each student, the learning plan database that is electrically connected to the learning item list generation server of each student, and the electrical connection to the teacher terminal. Connected telephones, fax machines, scanners, cameras, microphones.
Owner:伊利斯股份有限公司
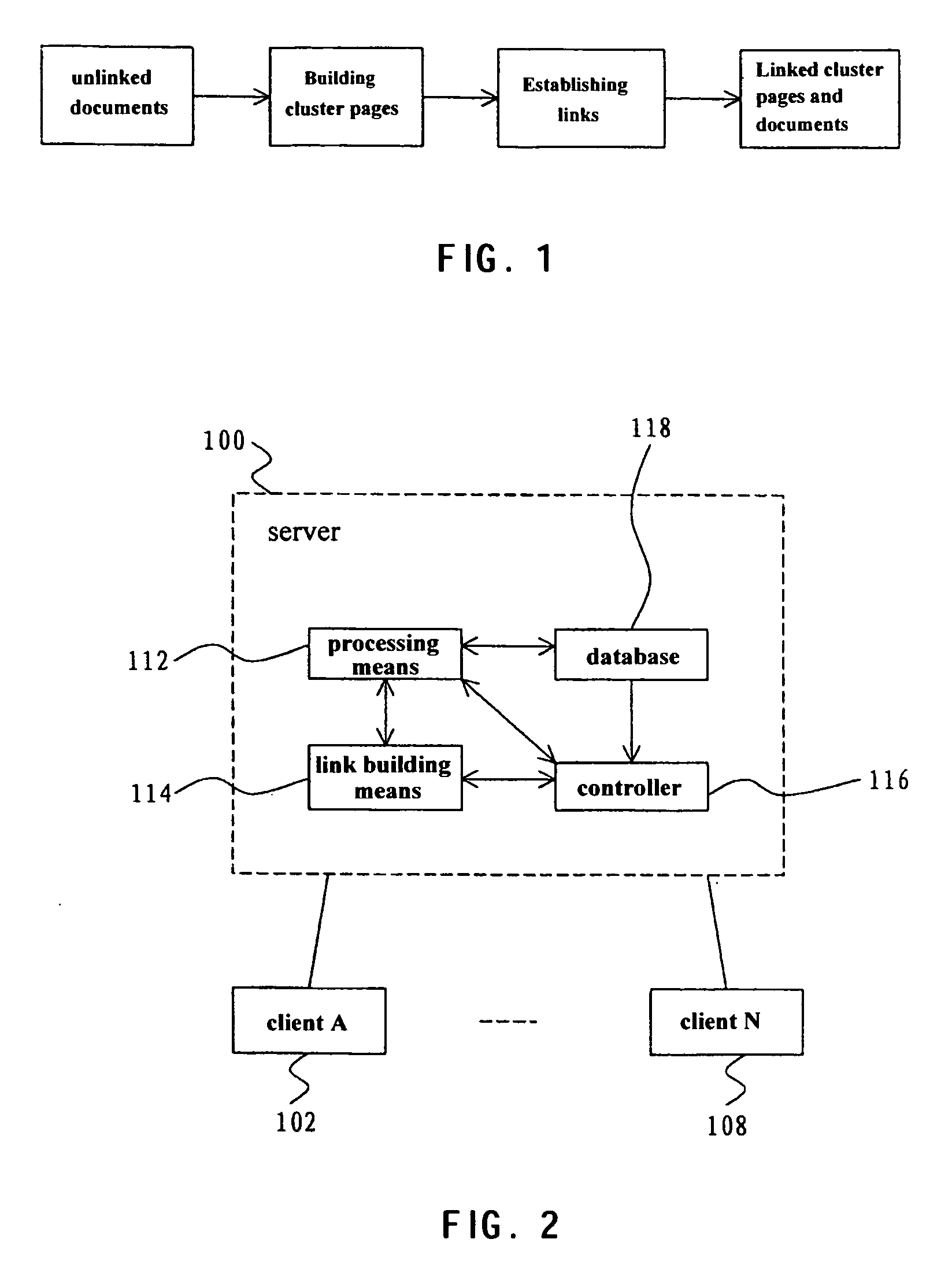
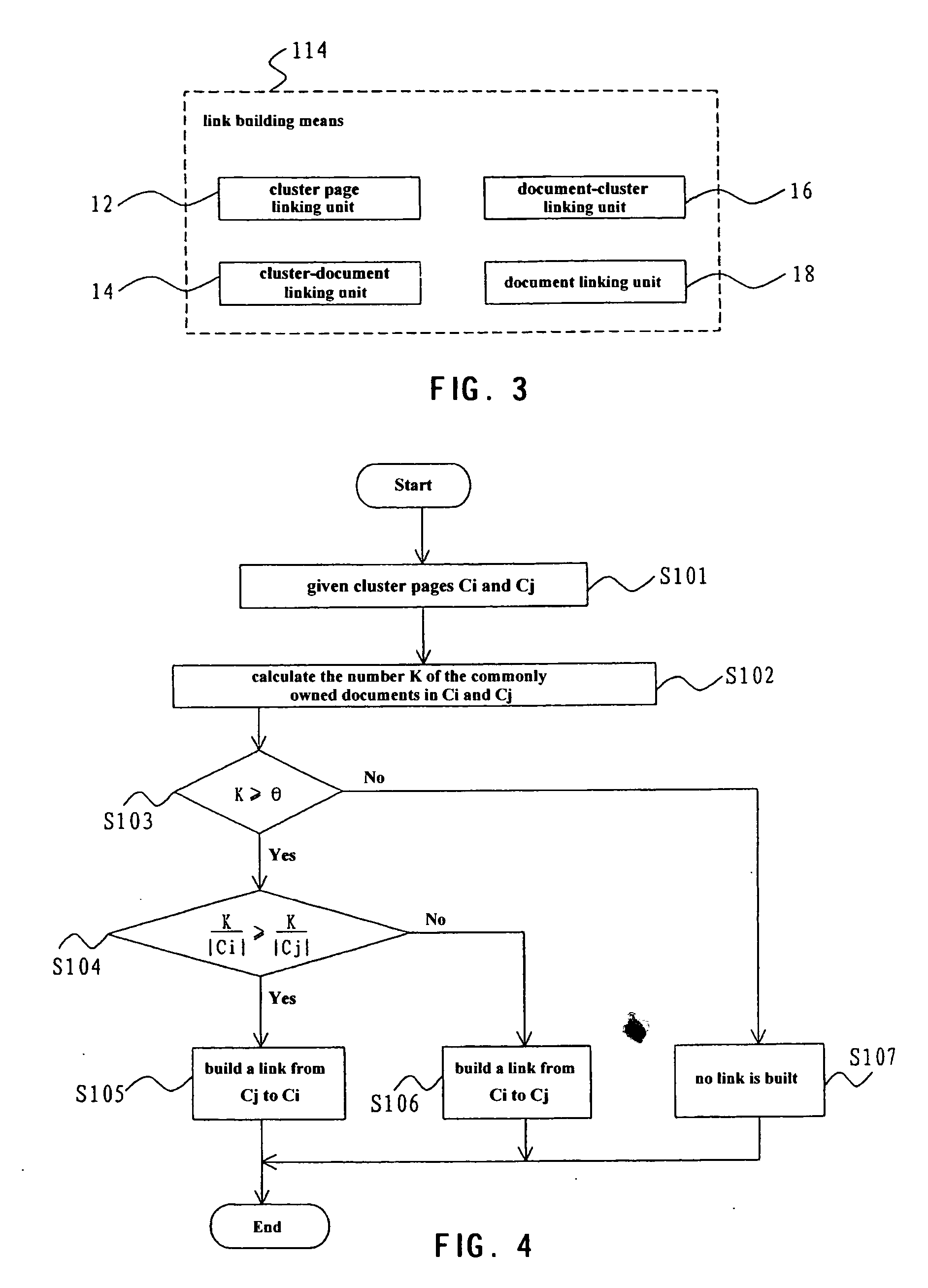
Method, apparatus, and system for linking documents
InactiveUS20060271536A1Improve search capabilitiesEfficient conductionData processing applicationsWeb data indexingWebIDPaper document
A method, apparatus and system for linking documents, the method comprising the steps of providing a plurality of clusters in an enterprise intranet, each cluster consists of one or more documents; building a cluster page for each cluster to present the documents in the cluster; and building links between the cluster pages, between the documents, and between the cluster page and the document, based on analysis of the contents of the clusters and the documents. The present invention is useful for building the links between separate documents and may apply a link analyzing algorithm to the search for these documents to implement better search performance within the enterprise intranet.
Owner:IBM CORP
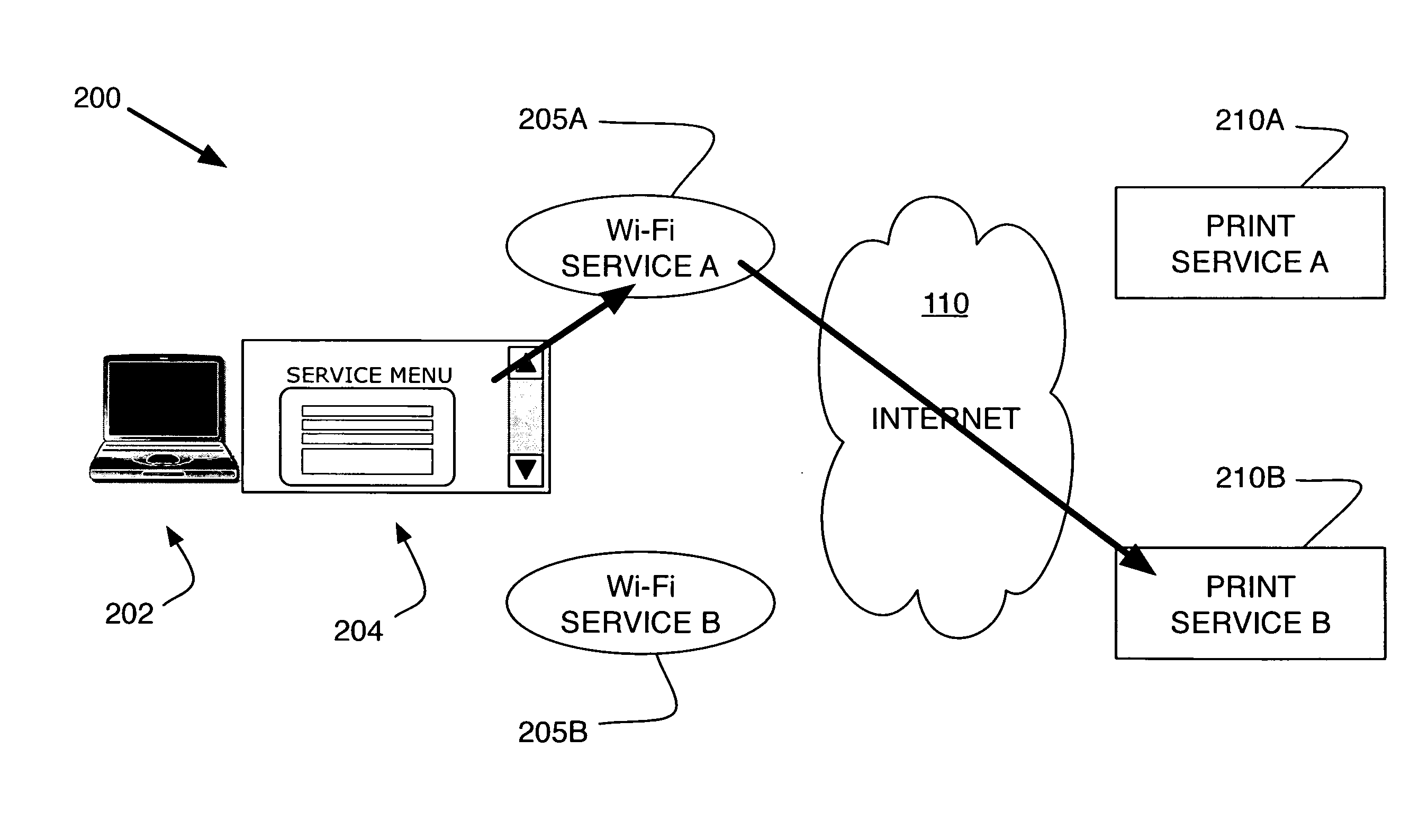
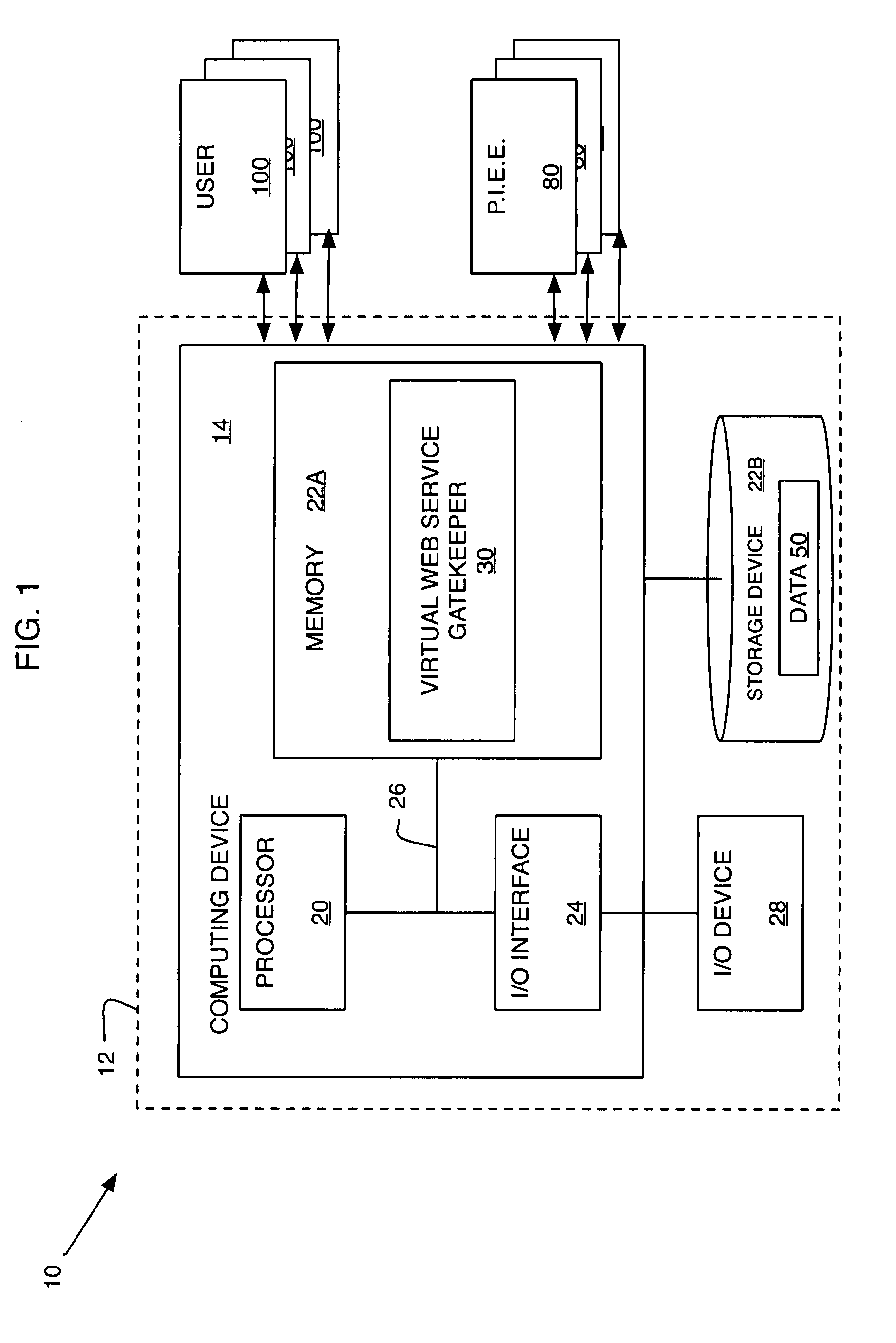
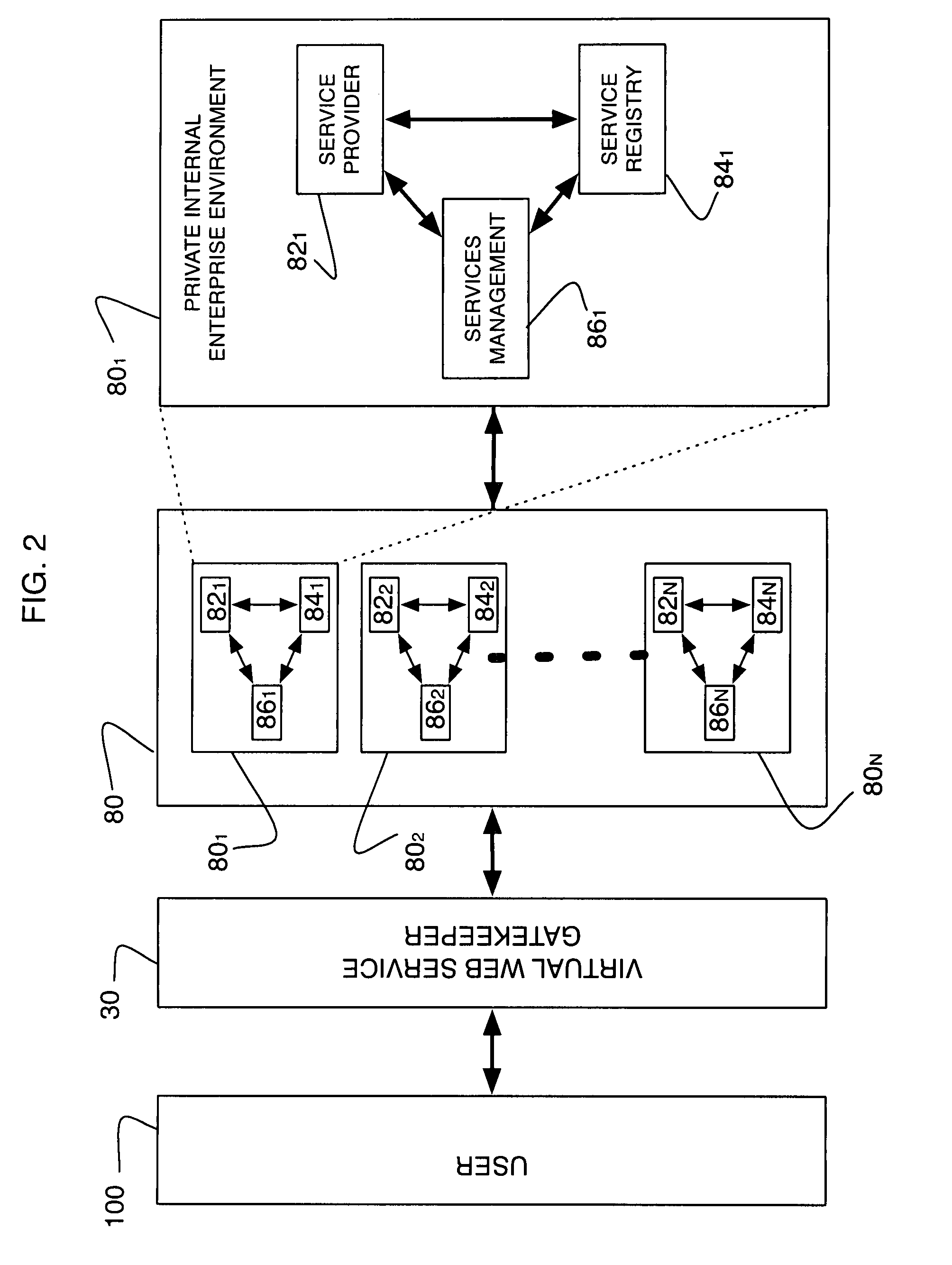
Virtual web service
ActiveUS20090190601A1Easy to solveData switching by path configurationMultiple digital computer combinationsWebIDWeb service
An improved solution for Web services is provided. In an embodiment of the invention, a method for providing a virtual Web service includes: providing a Web service gatekeeper, where the gatekeeper acts as an access point to multiple private internal enterprise environments; and then the gatekeeper receives a request for access to one, or more, of these private internal enterprise environments.
Owner:KYNDRYL INC
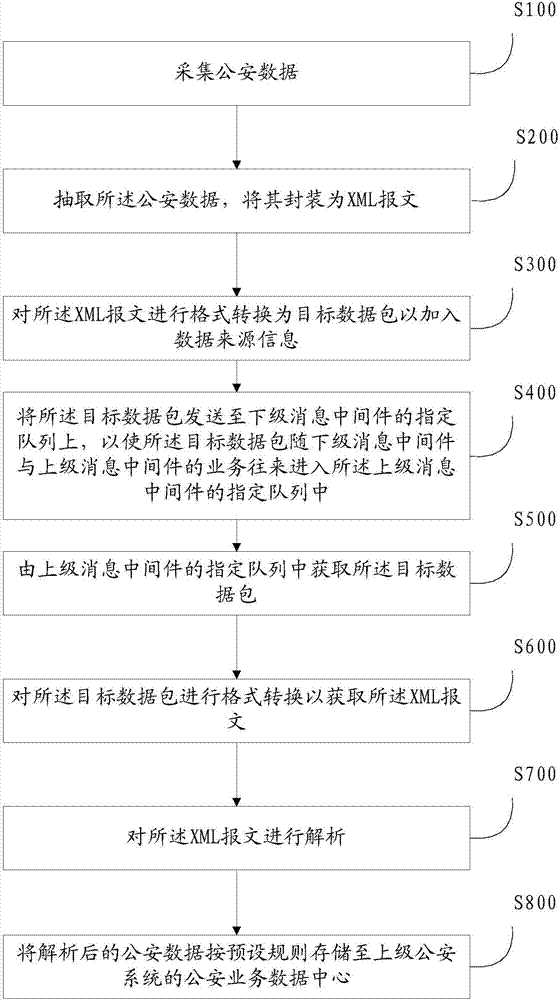
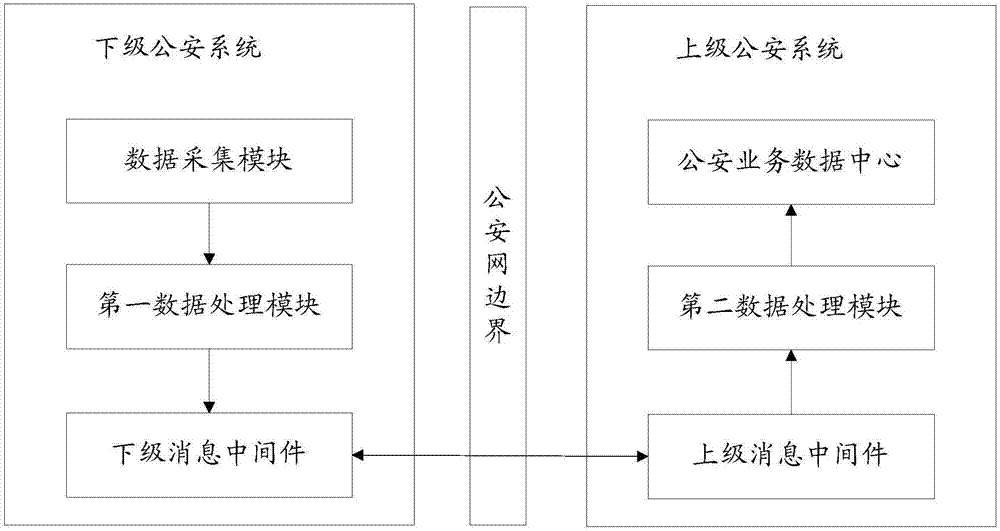
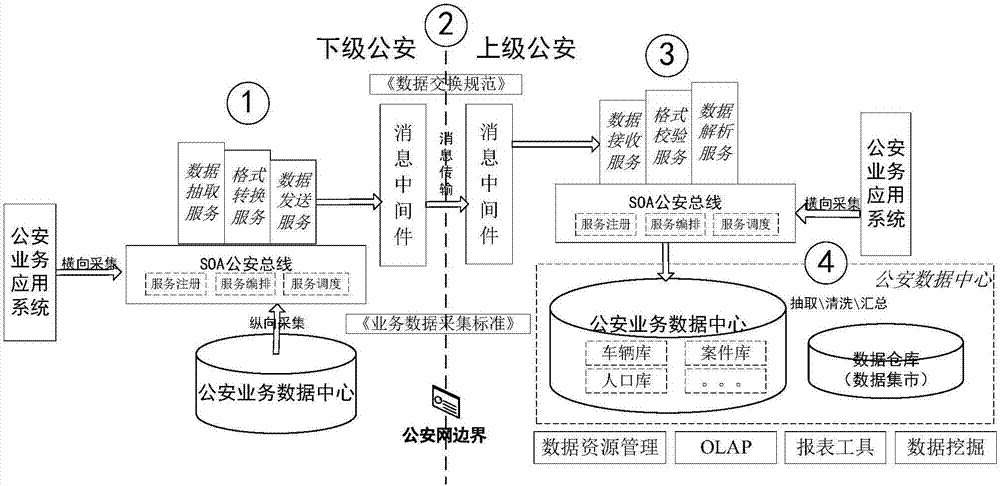
Integration method and system for public security business data
InactiveCN107194853ARealize the integrated exchangeAchieve comprehensivenessData processing applicationsInterprogram communicationWebIDData center
The invention discloses an integration method and system for public security business data. The method comprises the steps that public security data is collected; the public security data is extracted and encapsulated into an XML message; format conversion is performed; a target data packet is made to enter superior message-oriented middleware along with a business transaction between inferior message-oriented middleware and the superior message-oriented middleware; the target data packet is acquired; format conversion is performed to acquire the XML message; the XML message is analyzed; and the public security data obtained after analysis is stored into a public security business data center of a superior public security system according to preset rules. The system comprises an inferior public security system and the superior public security system, wherein the inferior public security system comprises a data collection module, a first data processing module and the inferior message-oriented middleware, and the superior public security system comprises the superior message-oriented middleware and a second data processing module. According to the integration method and system, the data transaction between different public security systems is realized through the message-oriented middleware, and the problem that inter-network cross-platform public security business data integration and exchange are difficult is solved.
Owner:北京一零科技有限公司
Methods and apparatus for in-line editing of web page content with reduced disruption of logical and presentational structure of content
InactiveUS10013400B1Reduce disruption and disruptionNatural language data processingWebsite content managementControl layerWebID
Owner:KIBO SOFTWARE INC
User-activity-based routing within a website
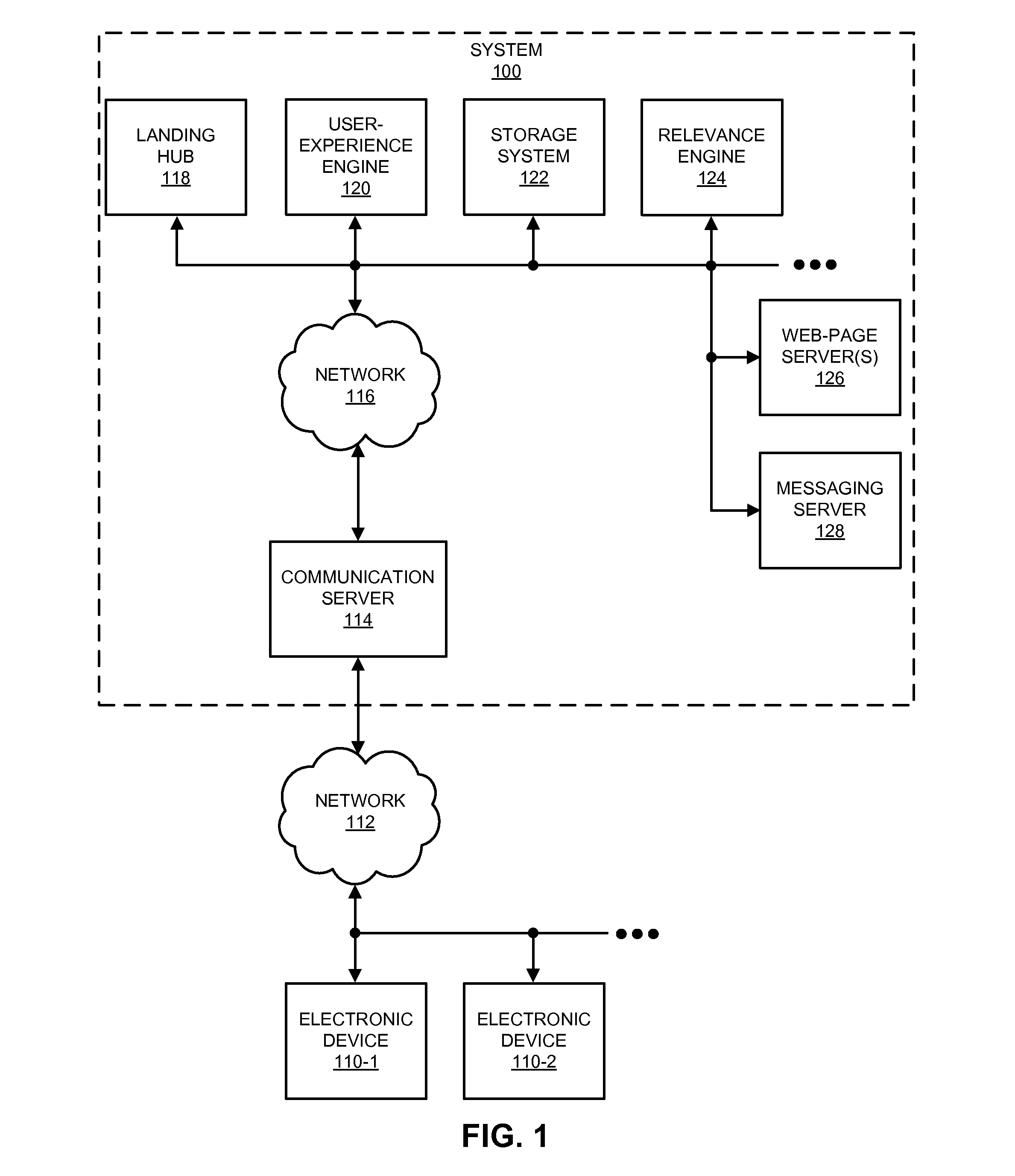
When a user of a social network accepts an invitation message to connect with another user of the social network, a system may use a history of user activity to determine where the user is subsequently directed within the social-network website. In particular, based on the history of user activity associated with an in-network page with recommendations for possible connections for the user within the network of users, the system may determine whether or not there have been too many impressions of the in-network page. If not, the system may present the in-network page with a recommendation for a possible in-network connection for the user within the network of users. Then, if the system receives a user selection of the possible in-network connection, the system may provide an invitation message inviting the possible in-network connection to connect with the user by activating a link in the invitation message.
Owner:MICROSOFT TECH LICENSING LLC
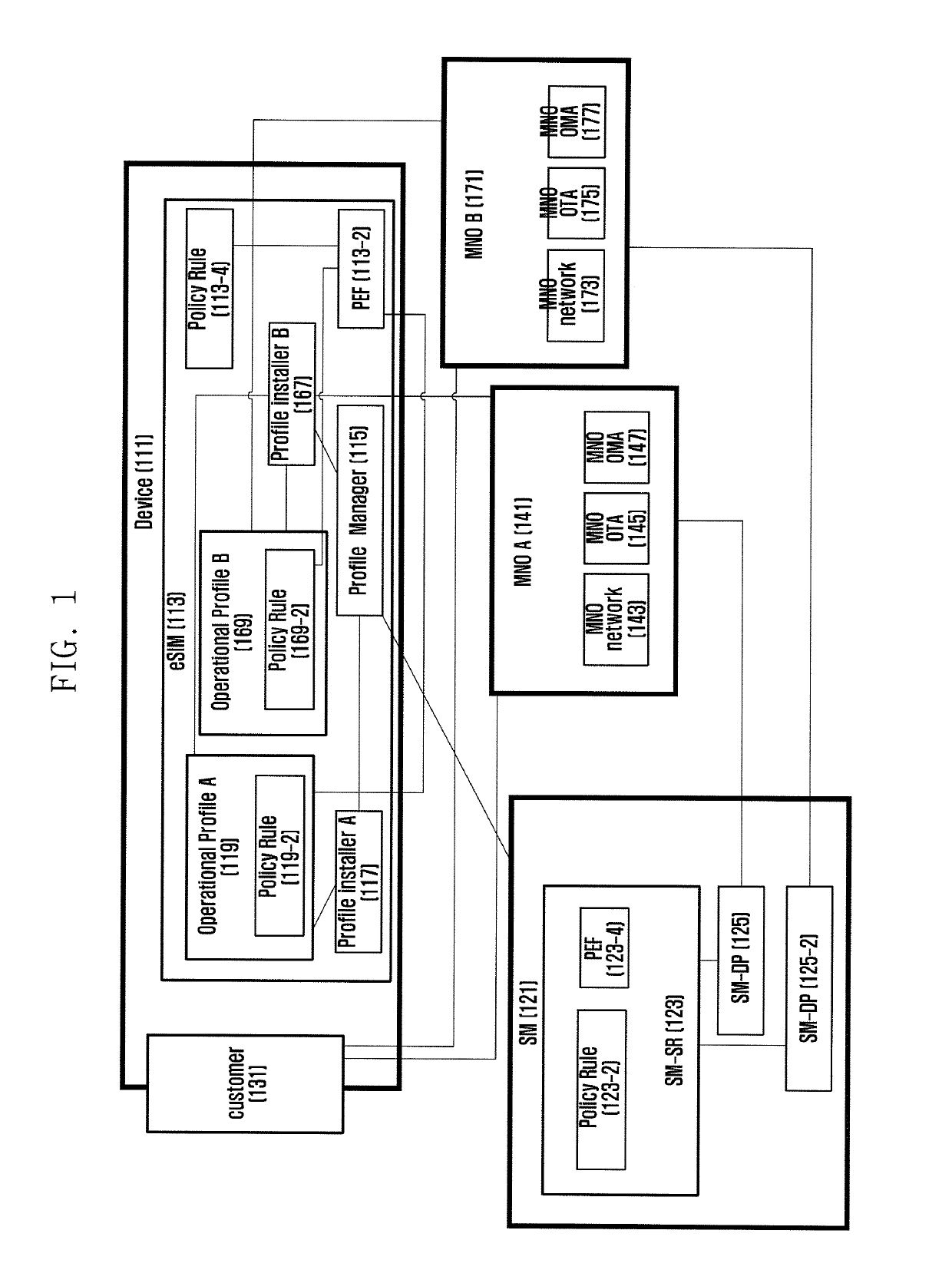
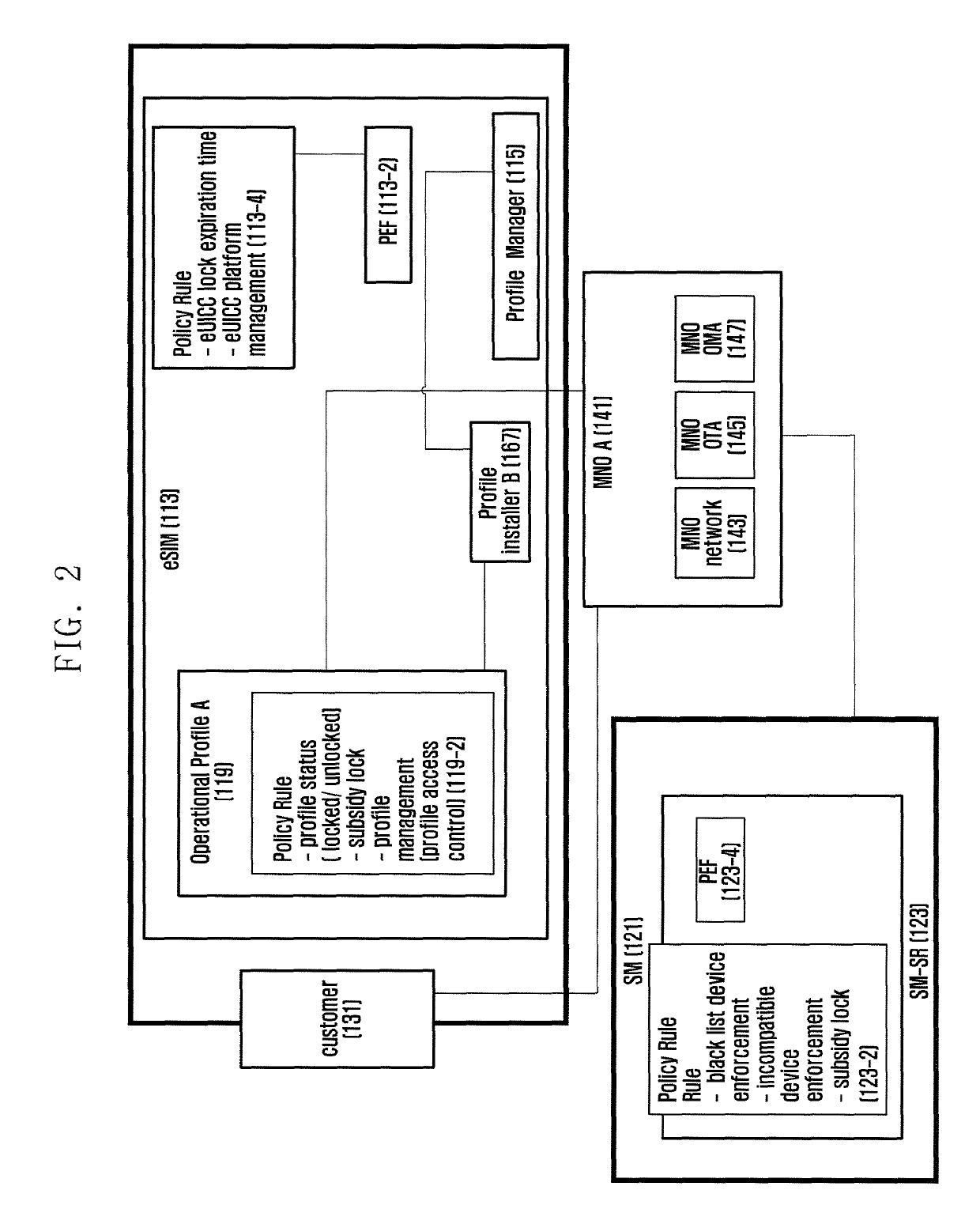
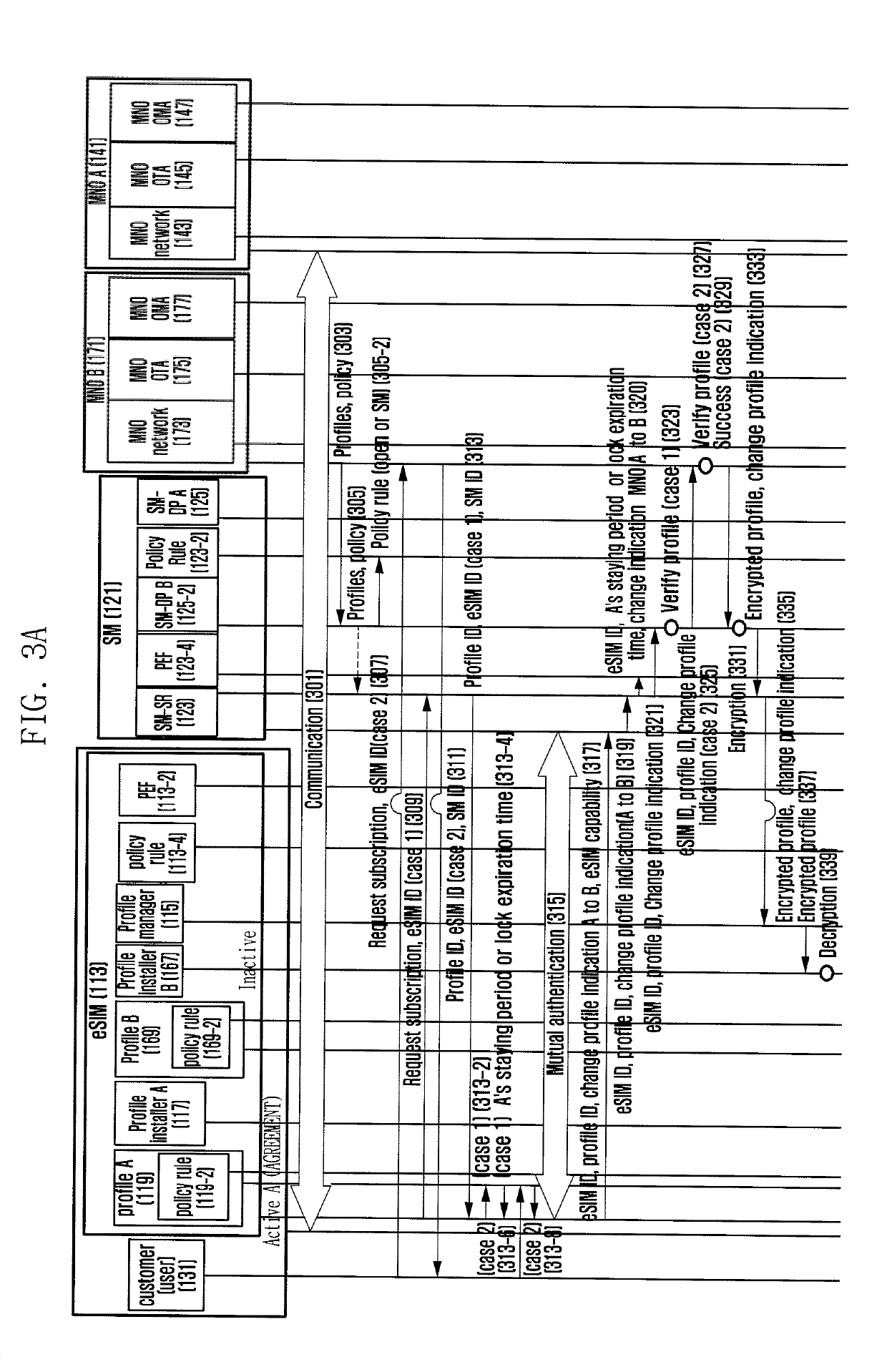
Method for supporting subscriber's service provider change restriction policy in mobile communications and apparatus therefor
The present invention relates to a method and an apparatus for employing an embedded subscriber identity module (hereinafter referred to as eSIM) to apply a policy such as a subsidy policy to, activate, deactivate, add to, update, and delete a user profile in a mobile communications network. The present invention enables a mobile device to determine whether to host the policy of a new service provider when it changes the present service provider or to perform a lock for prohibiting the policy change, and to change the profile related to the determination. The present invention also enables a mobile device to replace the policy related to the service provider by applying the policy, or to employ eSIM so as to activate, deactivate, revise, add, or delete the rules of the policy related to the service provider. The present invention provides various examples of hosting and applying the policy and various examples of activating, deactivating, revising, adding, deleting the policy rules so as to make eSIM identify the subscriber as the existing subscriber identity module. The invention also enables the device or eSIM to be reused when changing the service provider throughout the life cycle thereof without limiting the use of eSIM to a single service provider. The invention also provides a method for locking the policy applied per service provider, and the use of eSIM when changing to another service provider by the policy per service provider. The present invention also provides a method for checking the criteria of decision and verifying the power of decision when administering the policy rules and eSIM through deleting, adding, revising, activating, and deactivating the profile management plan and policy rules by applying the service provider's policy. Thus the present invention enables the device to host a new service provider's policy for communicating therewith when changing from the existing service provider to the new service provider, or when the government changes the service provider for an M2M device related to the electricity, infrastructure, etc. under an environment such as EUTRAN (Evolved Universal Terrestrial Radio Access Network) or UTRAN (Universal Terrestrial Radio Access Network) / GERAN (GSM / EDGE Radio Access Network). The present invention also is advantageous in that if the change of a service provider is not allowed according the policy of the existing service provider, the information related to communication and the security information are set revised safely by locking, thus enhancing the communication efficiency and security. The present invention also enables the device to verify the power of the user or to revise safely the information of eSIM for adding, revising, deleting, activating, and deactivating the policy rules for managing the operation profile for administration of the policy of the service provider under an environment such as EUTRAN (Evolved Universal Terrestrial Radio Access Network) or UTRAN (Universal Terrestrial Radio Access Network) / GERAN (GSM / EDGE Radio Access Network), thus enhancing the communication efficiency and security.
Owner:SAMSUNG ELECTRONICS CO LTD
Secret key management method for multi-network platform
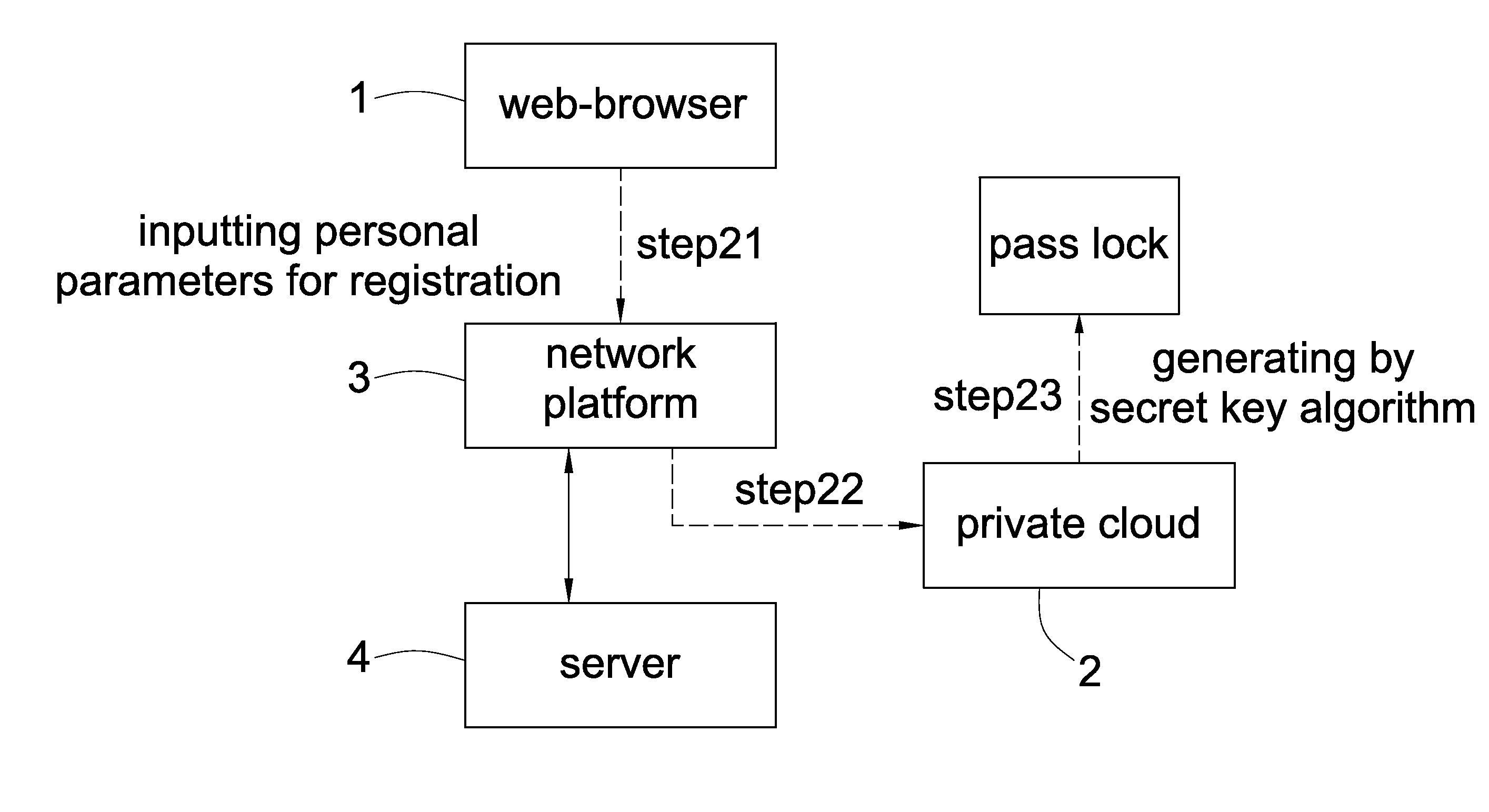
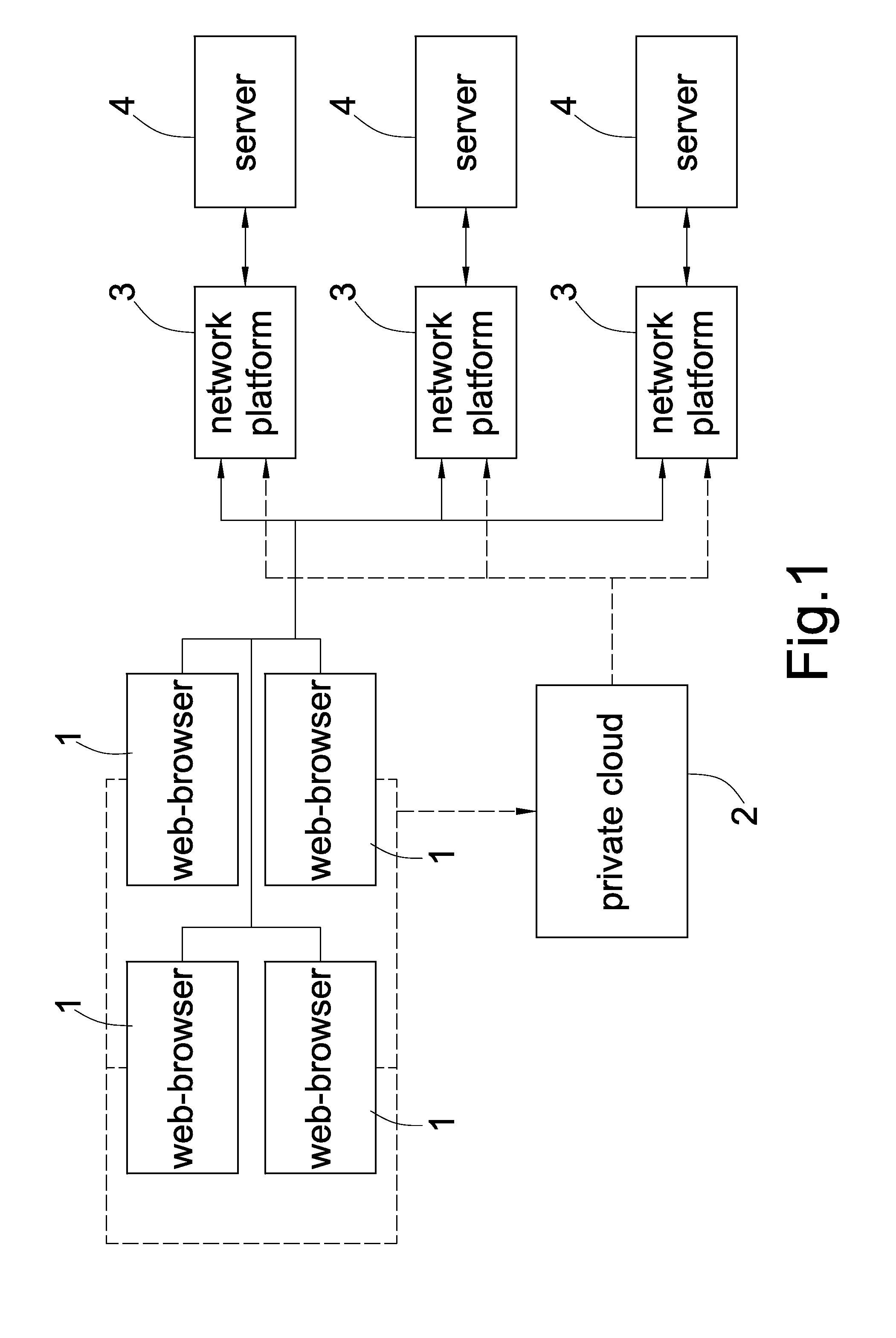
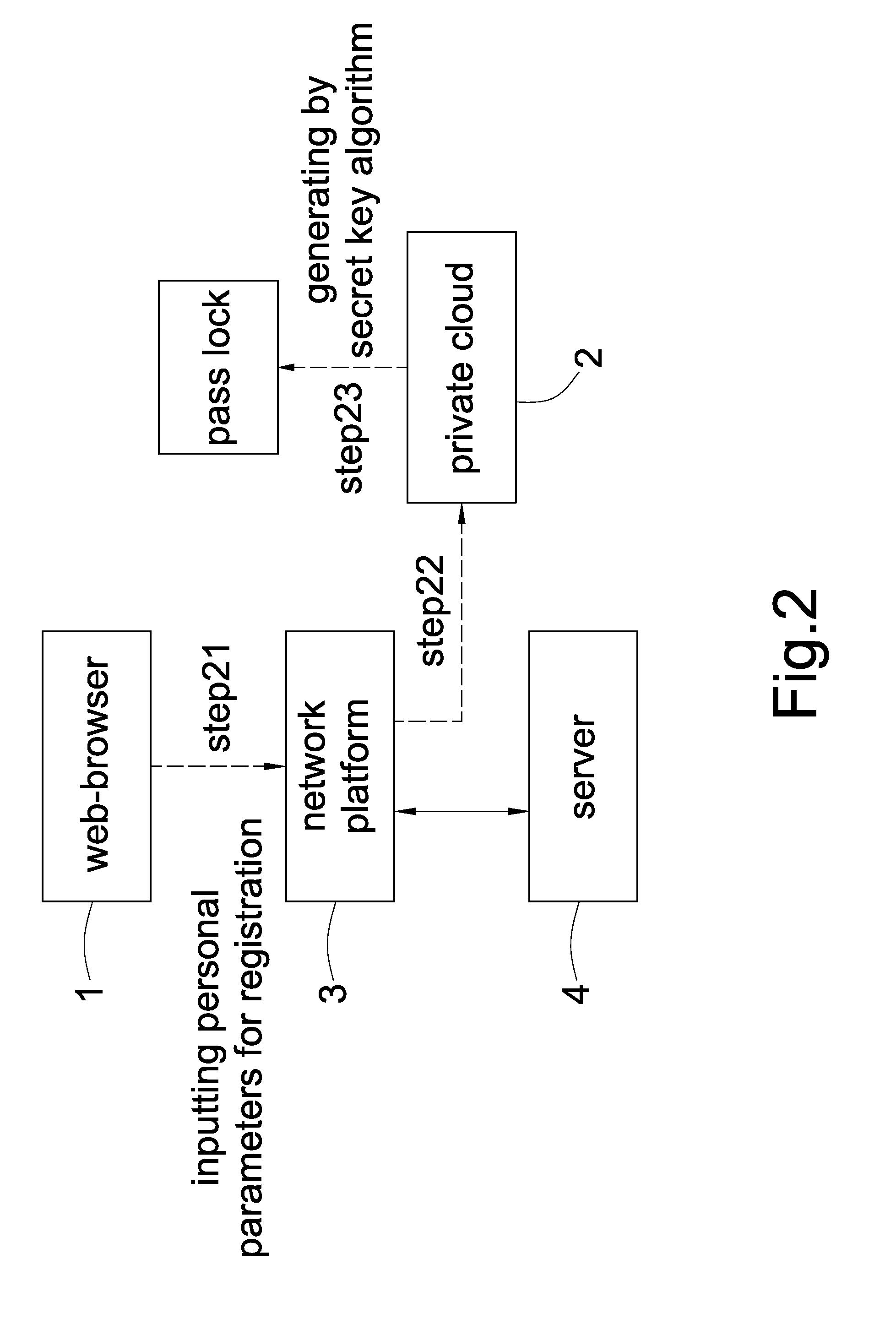
InactiveUS20140325219A1Assisted identificationKey distribution for secure communicationUser identity/authority verificationWeb browserWebID
In a secret key management method for multi-network platform, when the user logs in any network platform via arbitrary web-browser, the network platform links to the private cloud by Hypertext Transfer Protocol Daemon (HTTPD), and the private cloud shows a timeliness operational parameter on the web-browser for the user inputting personal parameters, and when the user inputs personal parameters within the predetermined time period, the private cloud then generates a pass key; the pass key generated by the private cloud is adapted to cooperate with the pass lock which is generated by the private cloud when the user registered to identify the user, and the identification result is transmitted to the network platform, and the network platform is configured to use the pass lock and pass key to identify the user.
Owner:WANIN INT
Resource download policies based on user browsing statistics
Web crawling polices are generated based on user web browsing statistics. User browsing statistics are aggregated at the granularity of resource identifier patterns (such as URL patterns) that denote groups of resources within a particular domain or website that share syntax at a certain level of granularity. The web crawl policies rank the resource identifier patterns according to their associated aggregated user browsing statistics. A crawl ordering defined by the web crawl polices is used to download and discover new resources within a domain or website.
Owner:MICROSOFT TECH LICENSING LLC
Information transmission method, packet data gateway, and policy and charging rules function
ActiveUS9369292B2Accurate identificationMetering/charging/biilling arrangementsWireless network protocolsWebIDInformation transmission
Owner:ZTE CORP
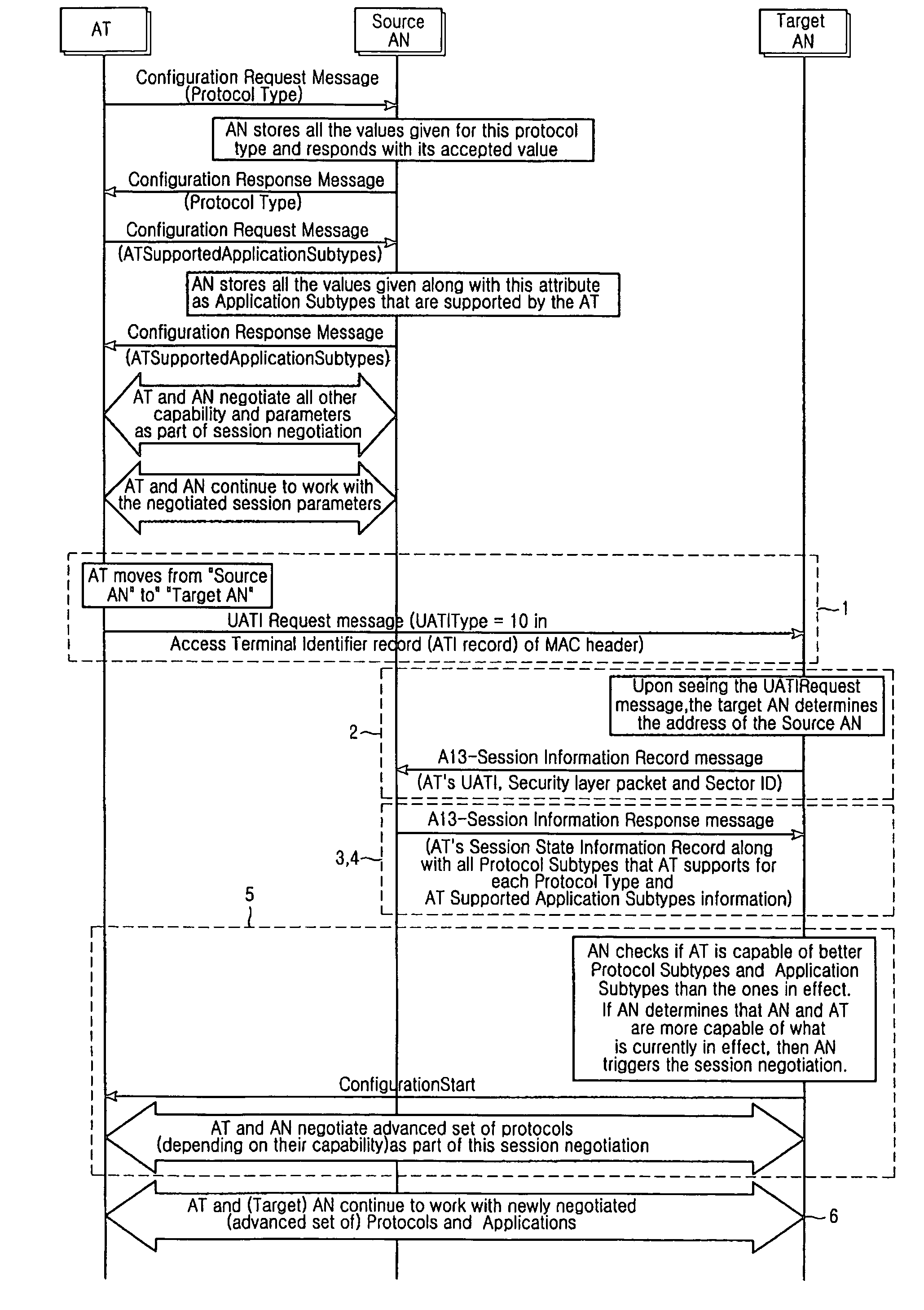
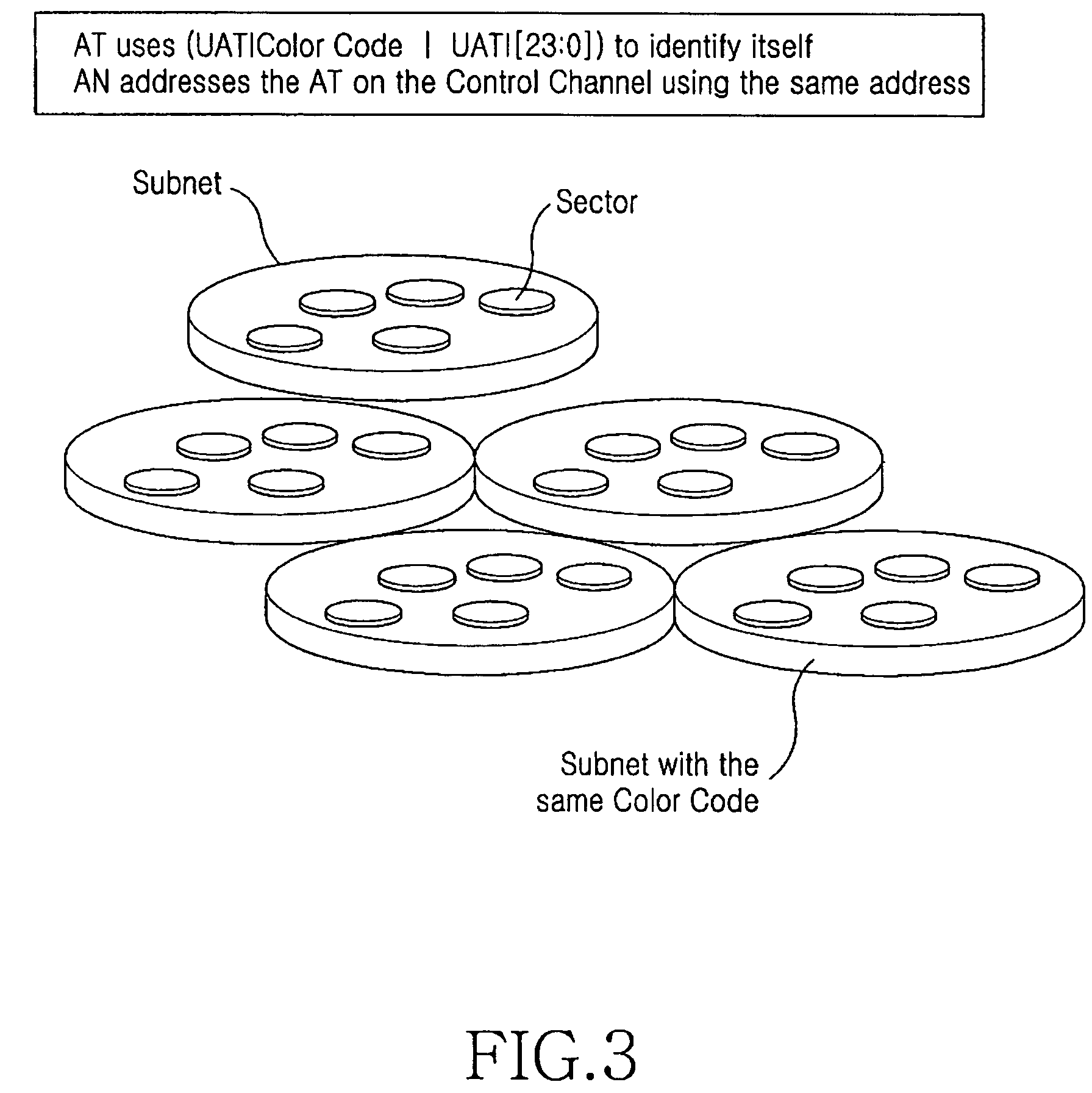
Apparatus and method for triggering session re-negotiation between access network and access terminal in a high rate packet data system
ActiveUS7725722B2Easy transferNetwork traffic/resource managementAssess restrictionAccess networkHigh rate
The invention relates to a method for triggering re-negotiation of a session when an Access Terminal moves from one access network (source AN) to another access network (target AN) having different capabilities in high rate packet data system. According to an exemplary embodiment of the invention, the source AN is allowed to store all the protocol subtypes, protocols and applications that AT is capable of and also allowing the AT to send this information in priority order during session negotiation and hence facilitating the transfer of this information from source AN to target AN during session transfer when AT moves from one AN to another AN. An alternate embodiment is to let the AT send the protocol subtypes, protocols and applications and other AT capable information to target AN after it moves to a new AN or by letting the Rev-A capable AN query the AT's capability information and then the AT providing this information. In another exemplary embodiment, the invention includes re-negotiation by introducing a revision (like Protocol revision) information in overhead information messages that an AN broadcasts to all ATs.
Owner:SAMSUNG ELECTRONICS CO LTD
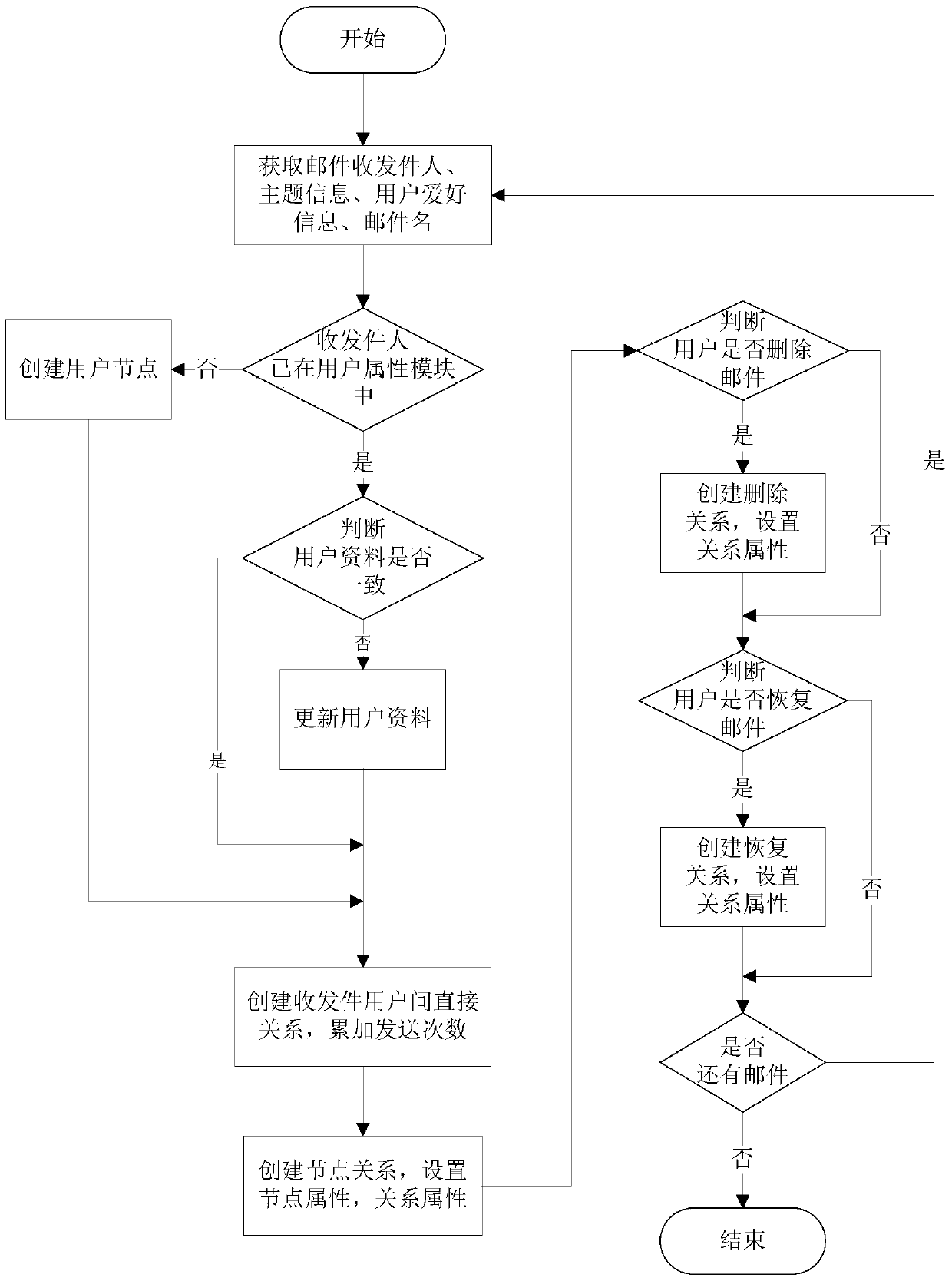
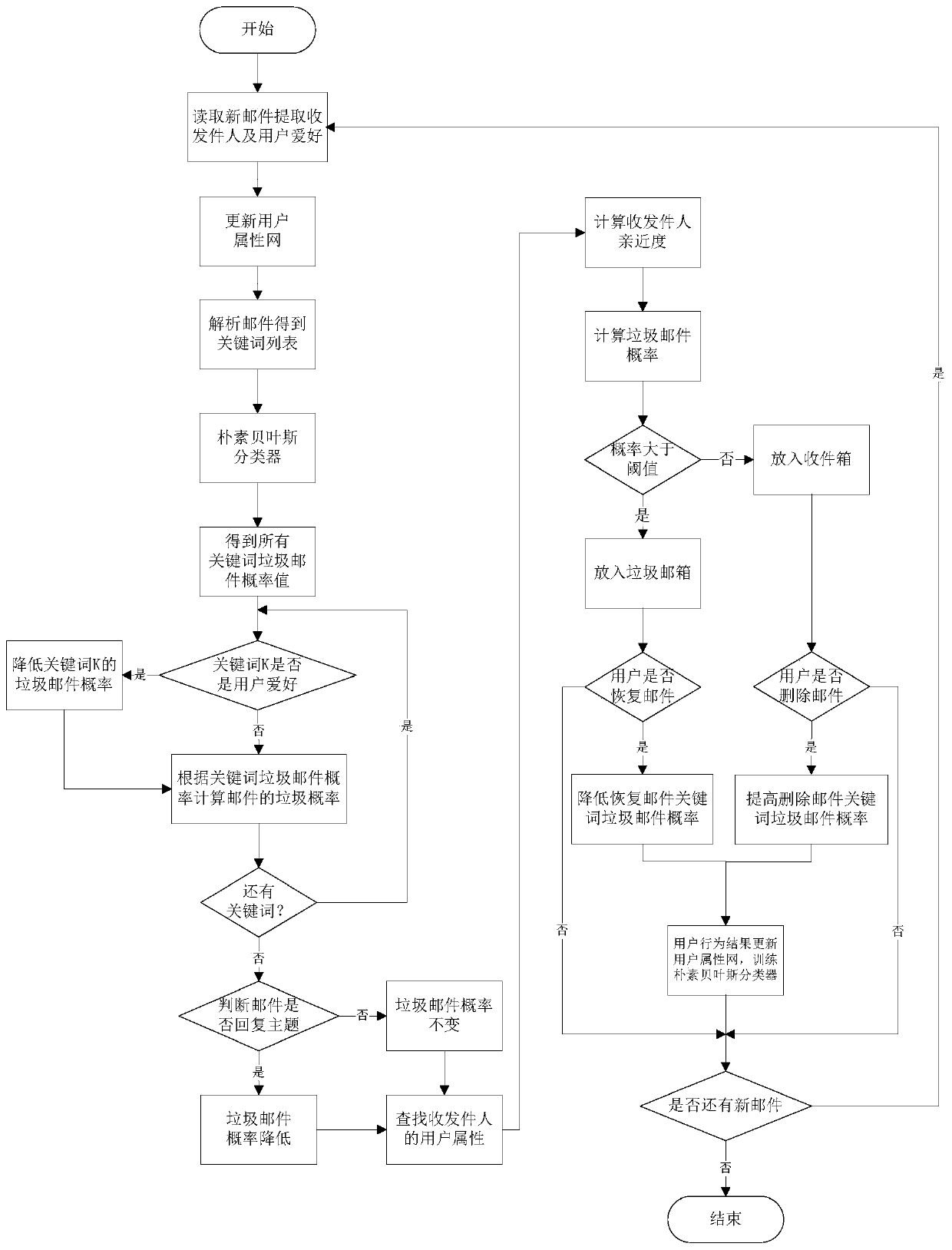
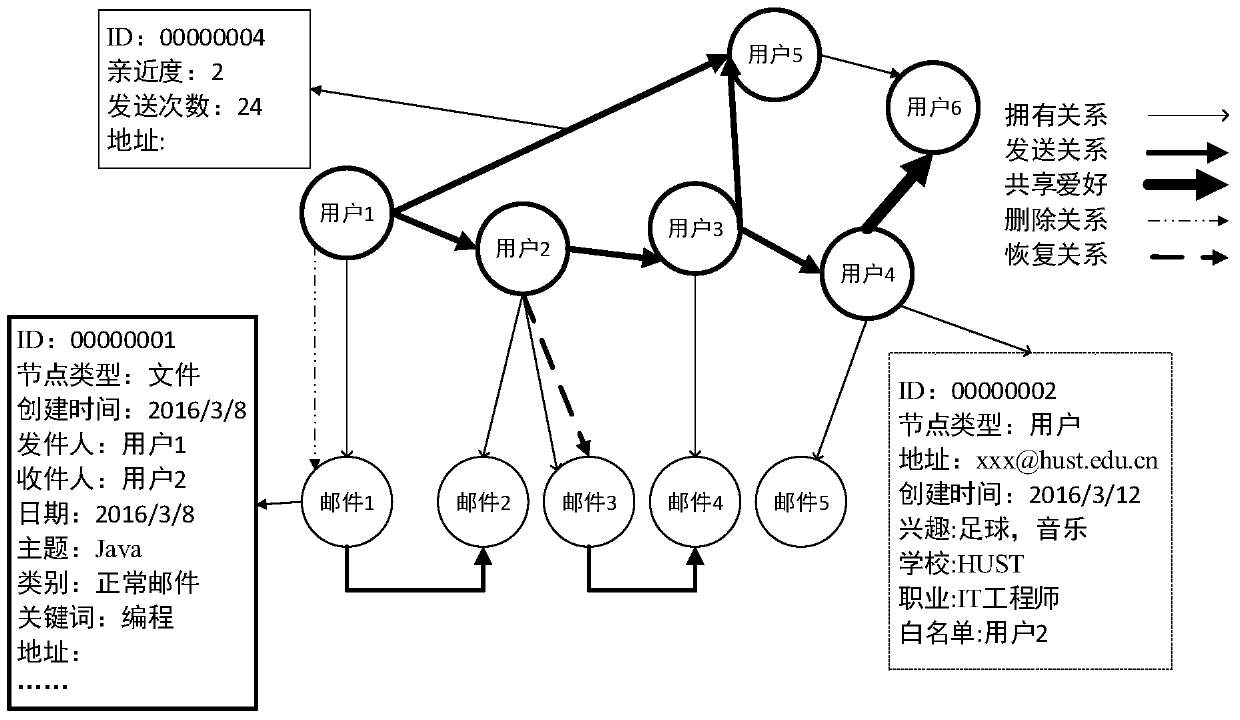
A mail classification method and system combining user attributes
ActiveCN106230690BImprove accuracy performanceOffice automationData switching networksWebIDEmail spam
The invention discloses a mail classification method and system combined with user attributes, which belong to the technical field of data mining. First, a classifier is used to initialize the probability of new mail spam, and then the user preference attribute of the new mail is matched in the built user attribute network. , email subject attribute, user intimacy attribute and user behavior attribute, and then use the influence of user preference attribute, mail subject attribute, user intimacy and user behavior attribute on spam probability to update the spam probability of email. The present invention also provides a system for implementing the above method. The present invention improves the accuracy of the existing mail classification technology by classifying and determining the mail in combination with the user attributes.
Owner:HUAZHONG UNIV OF SCI & TECH
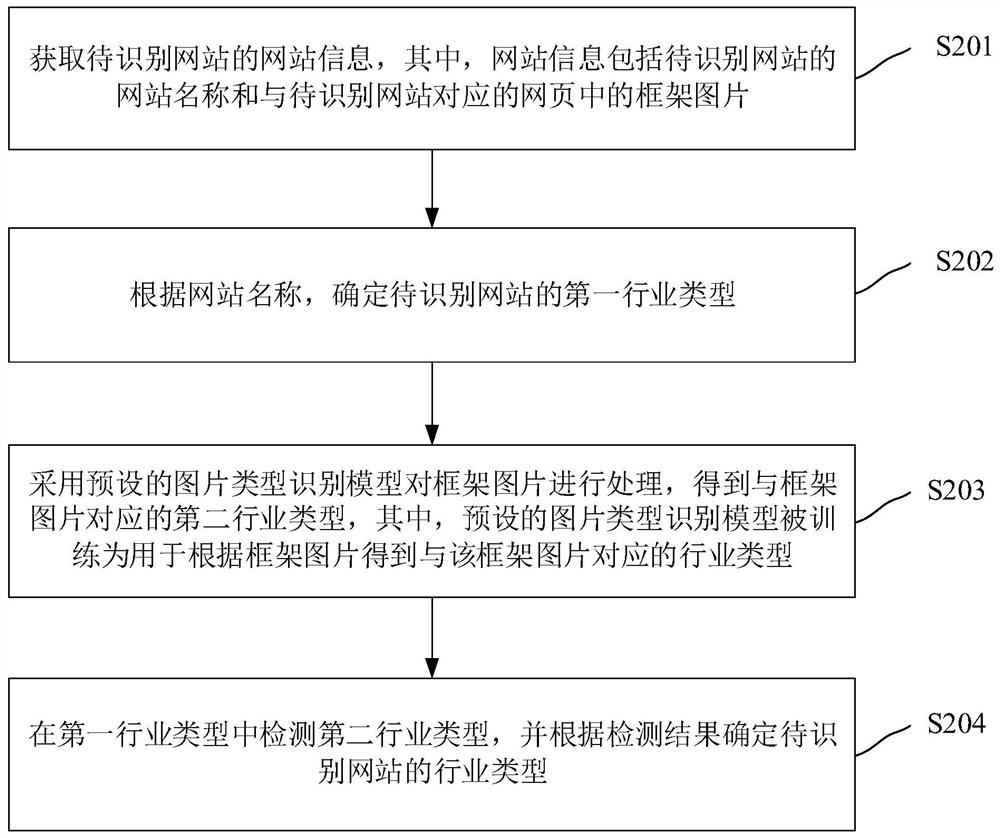
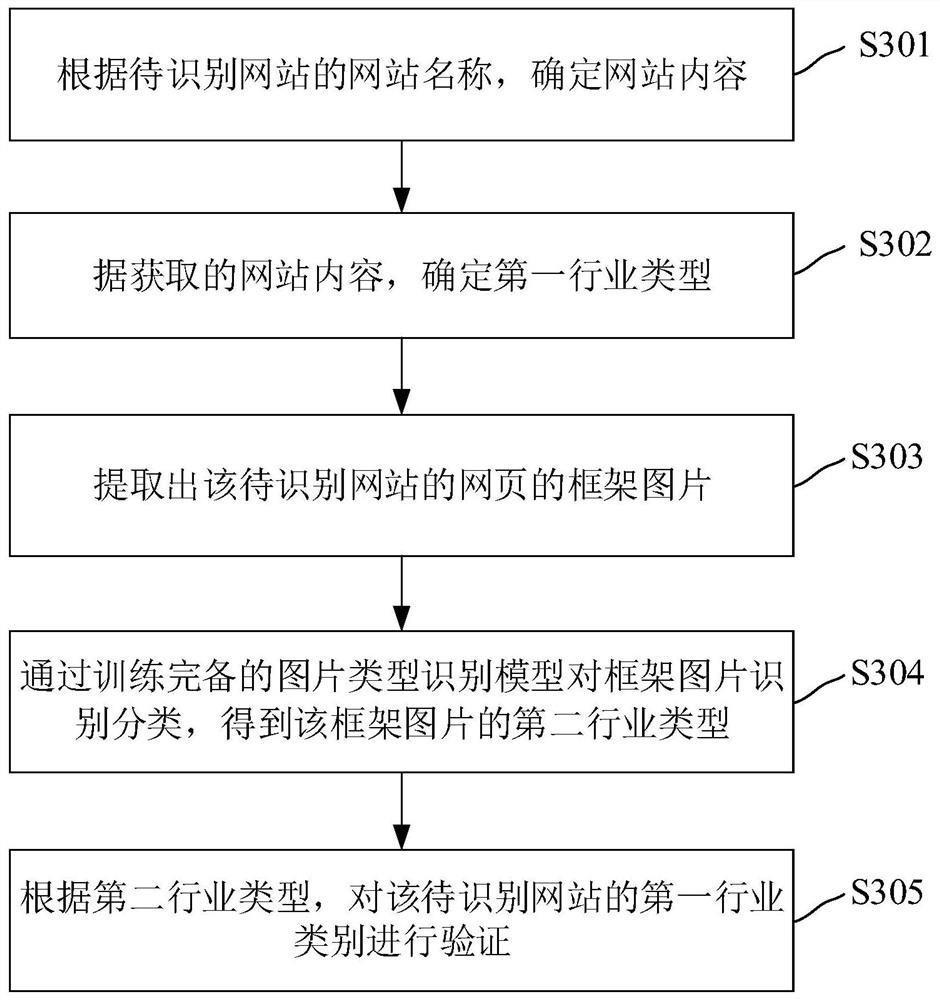
Classification method, device, electronic device and storage medium of website industry type
ActiveCN113268691BSolve the low recognition rateImprove recognition rateCharacter and pattern recognitionWebsite content managementWeb siteWebID
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
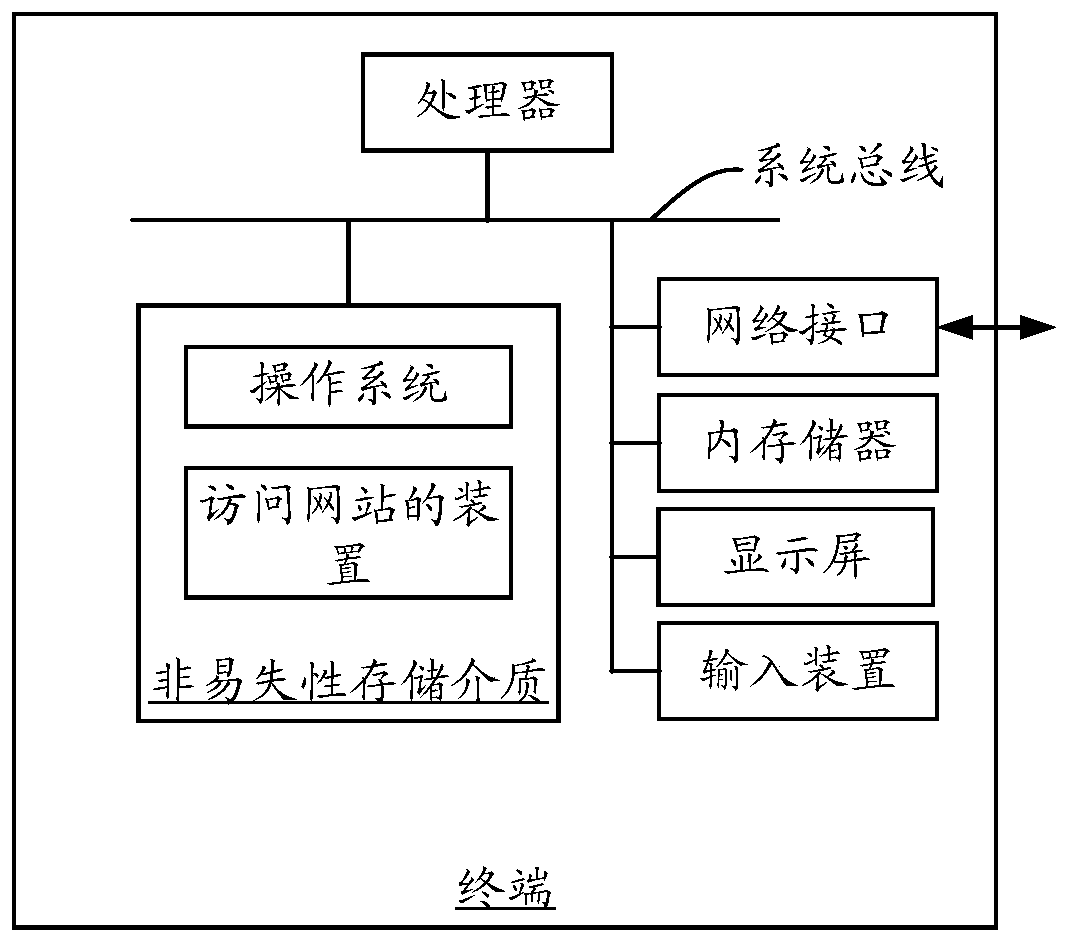
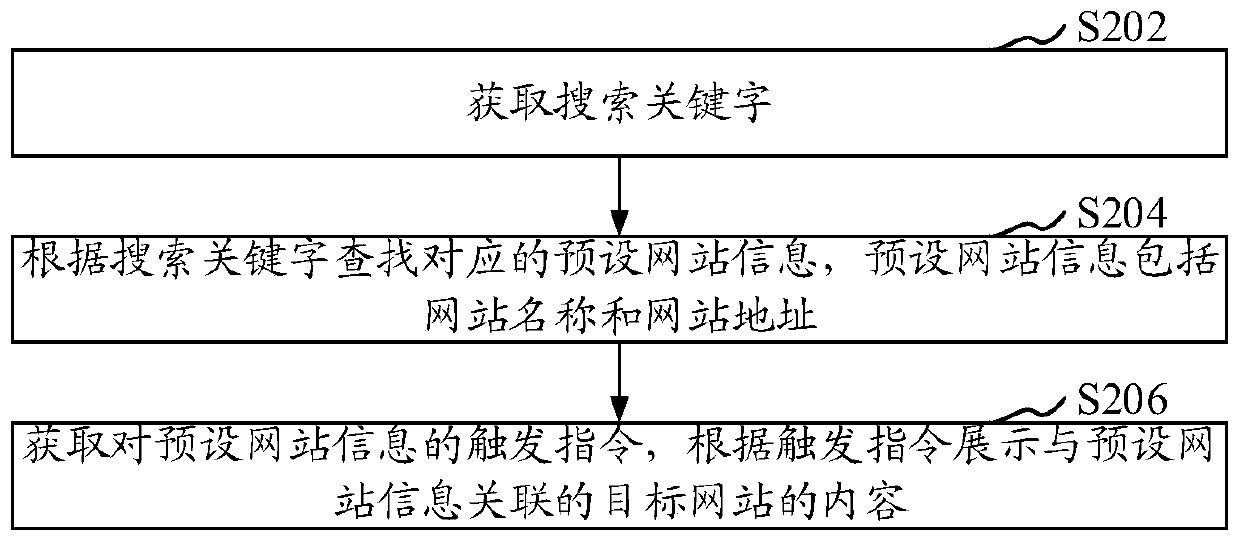
Method and device for accessing the website
ActiveCN106934019BHigh trafficFast access to trafficWeb data indexingWebsite content managementWeb siteWebID
The present invention relates to a website access method and apparatus. The method comprises: obtaining a search keyword; searching corresponding preset website information according to the search keyword, wherein the preset website information comprises a website name and a website address; and obtaining a trigger instruction for the preset website information, and according to the trigger instruction, displaying content of the target website associated with the preset website information. According to the website access method disclosed by the present invention, by obtaining the search key word, searching the preset website information corresponding to the search keyword, and clicking the preset website information, the content of the target website associated with the preset website can be displayed in the preset website; and relying on the top ranking of the preset website in the search engine, the content of the target website associated with the preset website can obtain higher access traffic, and the content of the target website can obtain the access traffic at a faster speed.
Owner:深圳市商舟网科技有限公司
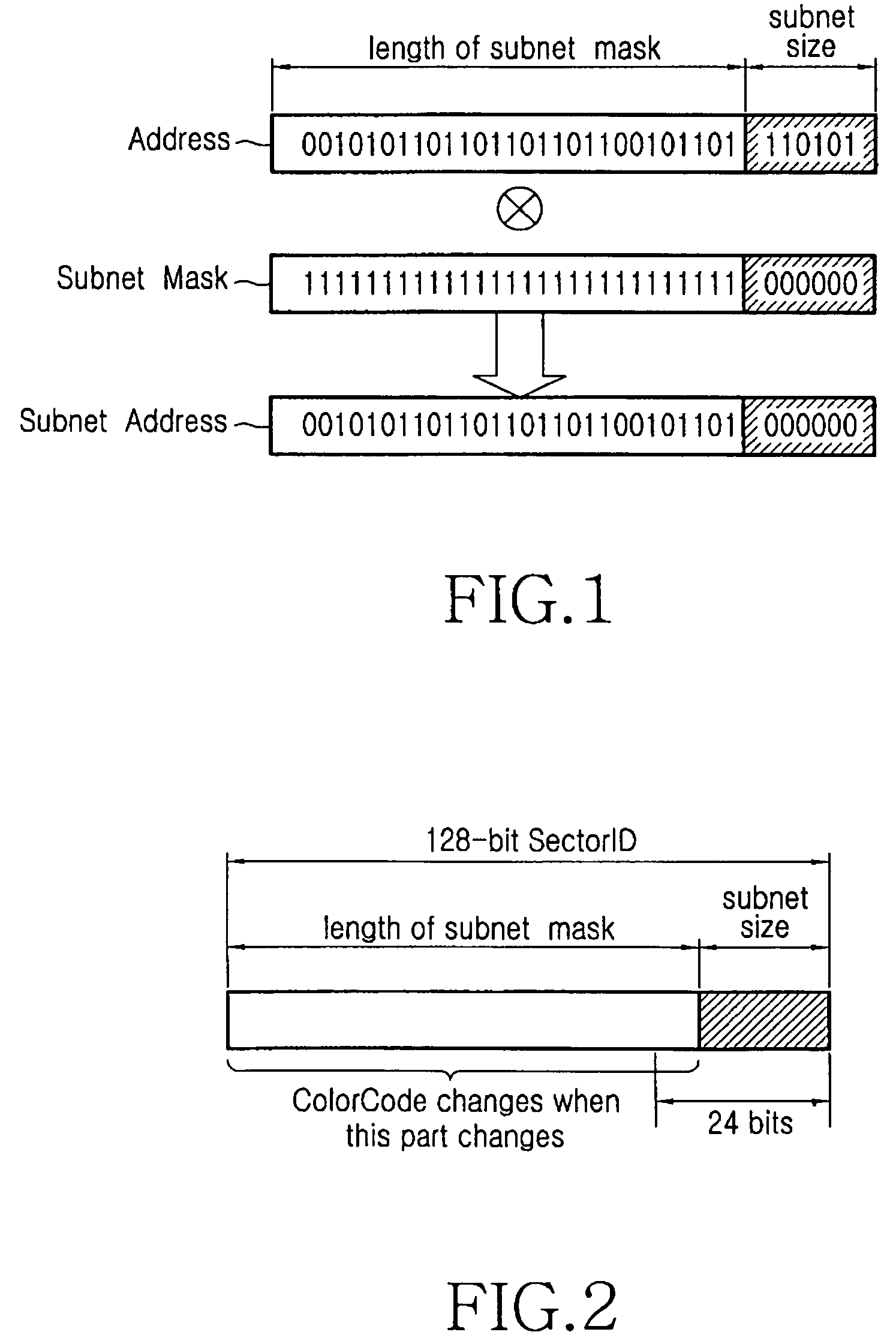
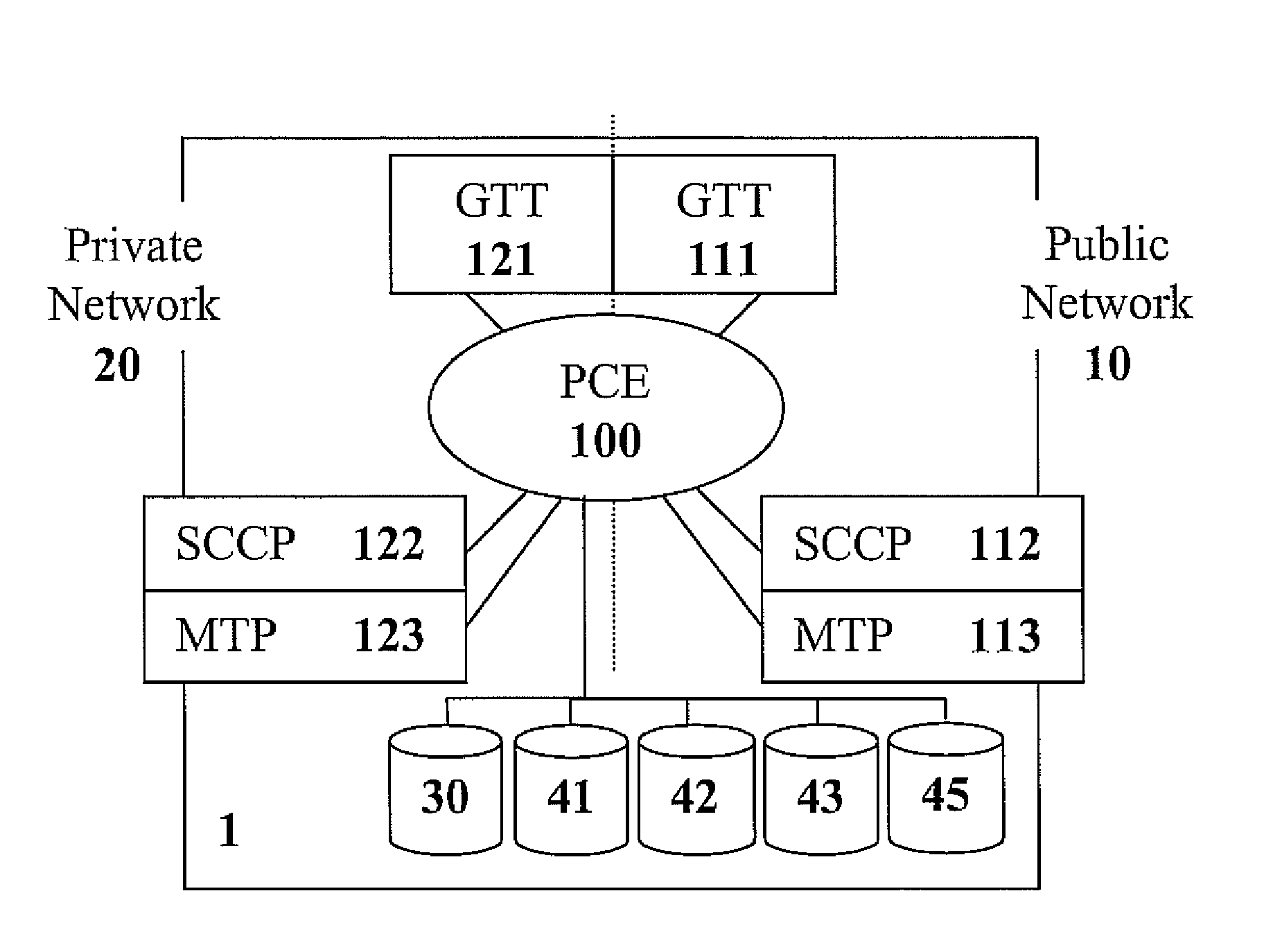
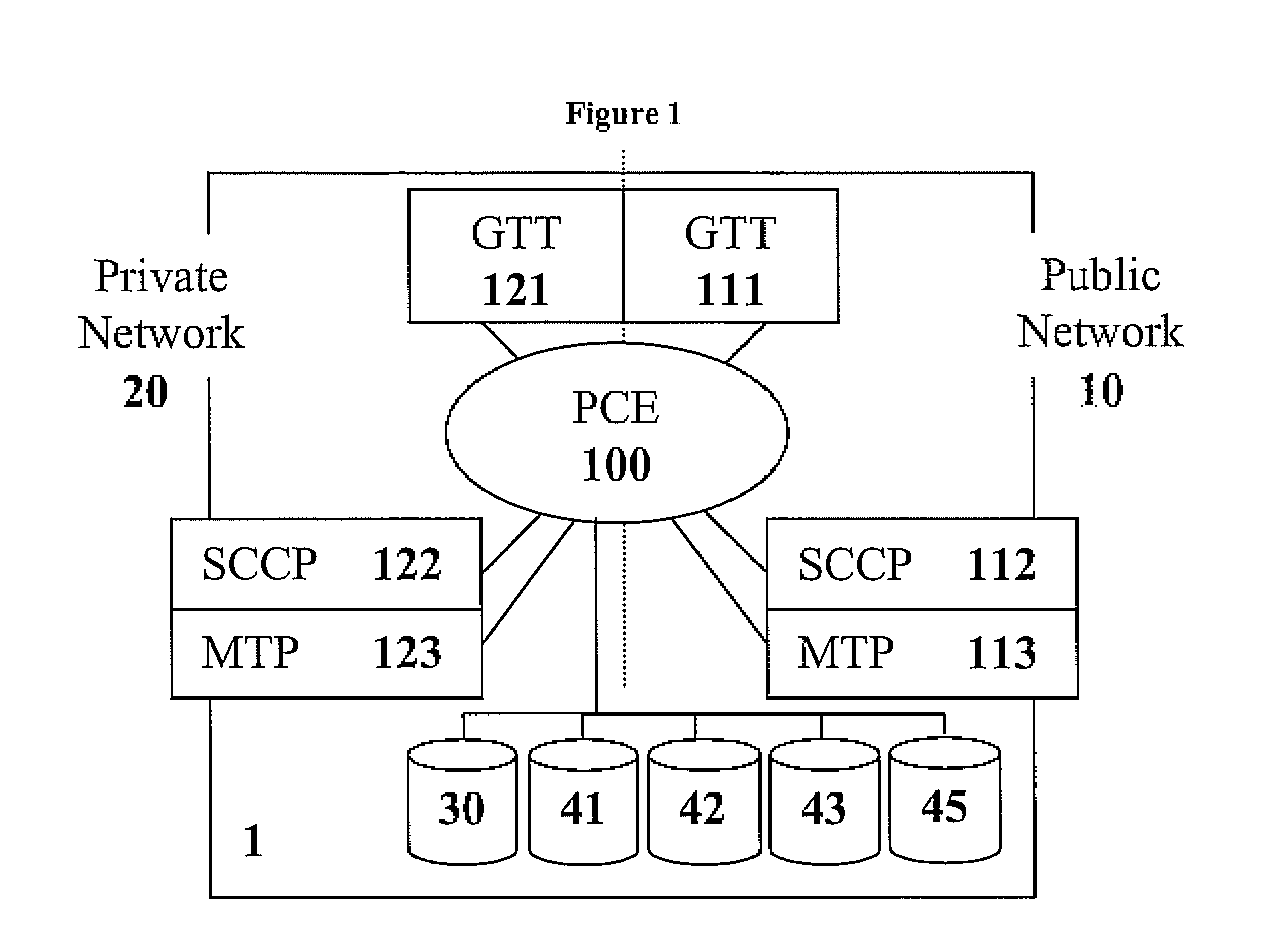
Point code emulation for common channel signaling system No. 7 signaling network
ActiveUS8452890B2Expanding and extending networkOvercome limitationsDigital data processing detailsMultiple digital computer combinationsWebIDSignaling network
Owner:RIBBON COMM OPERATING CO INC
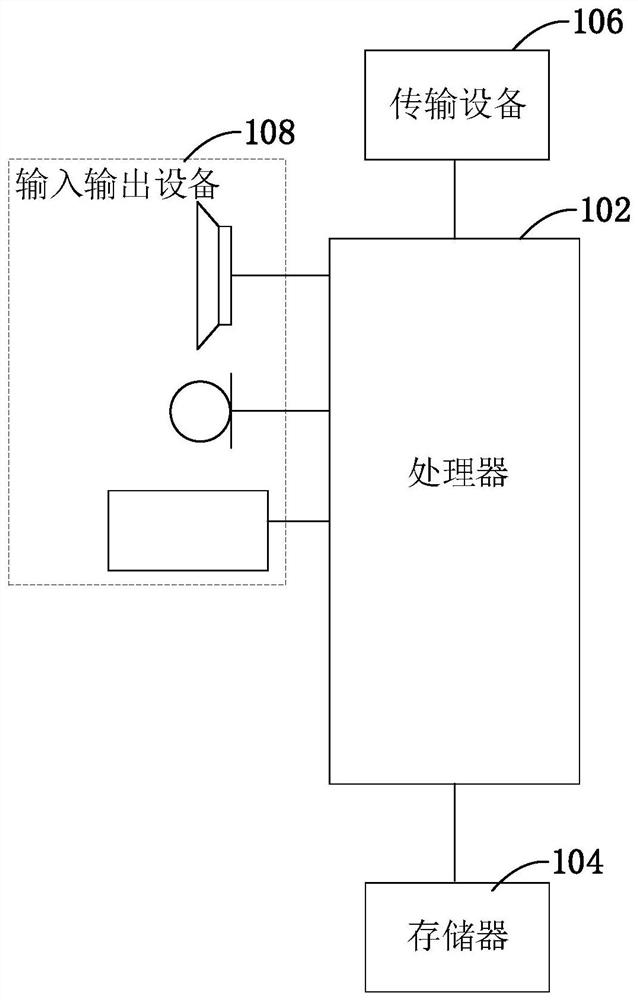
Website industry type classification method and device, electronic device and storage medium
ActiveCN113268691ASolve the low recognition rateImprove recognition rateCharacter and pattern recognitionWebsite content managementWeb siteWebID
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Managment system of the resources of an access connection provided by an enterprise
InactiveUS20160261518A1Data switching networksSoftware simulation/interpretation/emulationComputer networkWebID
the present invention relates to system of electronic apparatuses and devices for the management of an access connection, as internet and / or intranet connection, provided by an enterprise as a chain of stores, for example based on the specific services enquires in a specific moment, contrary to the statistic approach of the communication provider service company
Owner:GUERRI GIOVANNI +1
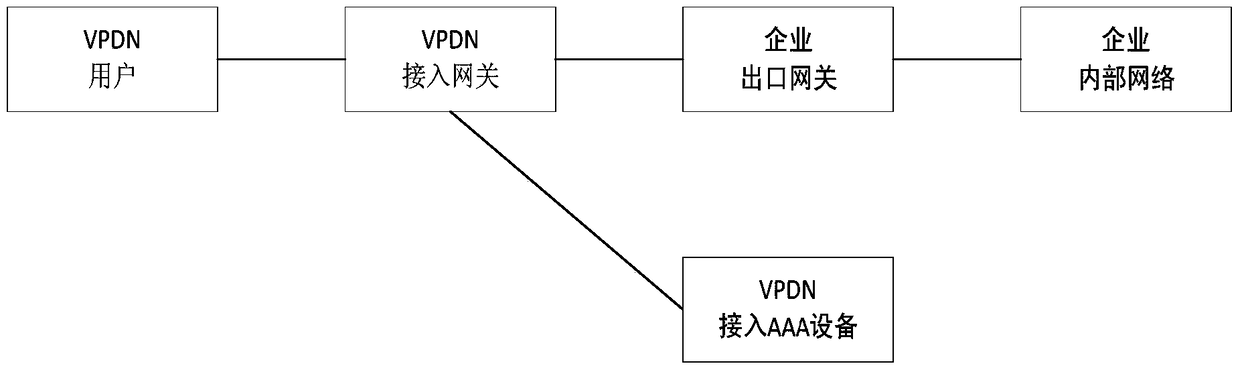
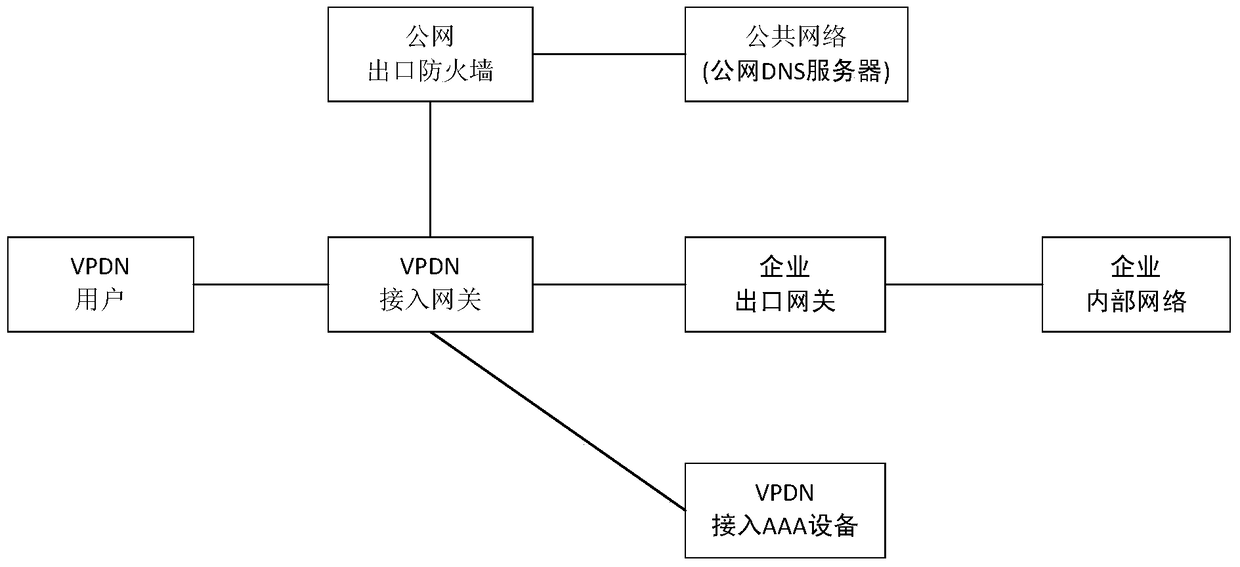
Control device and method for wireless vpdn network users to access specific public website
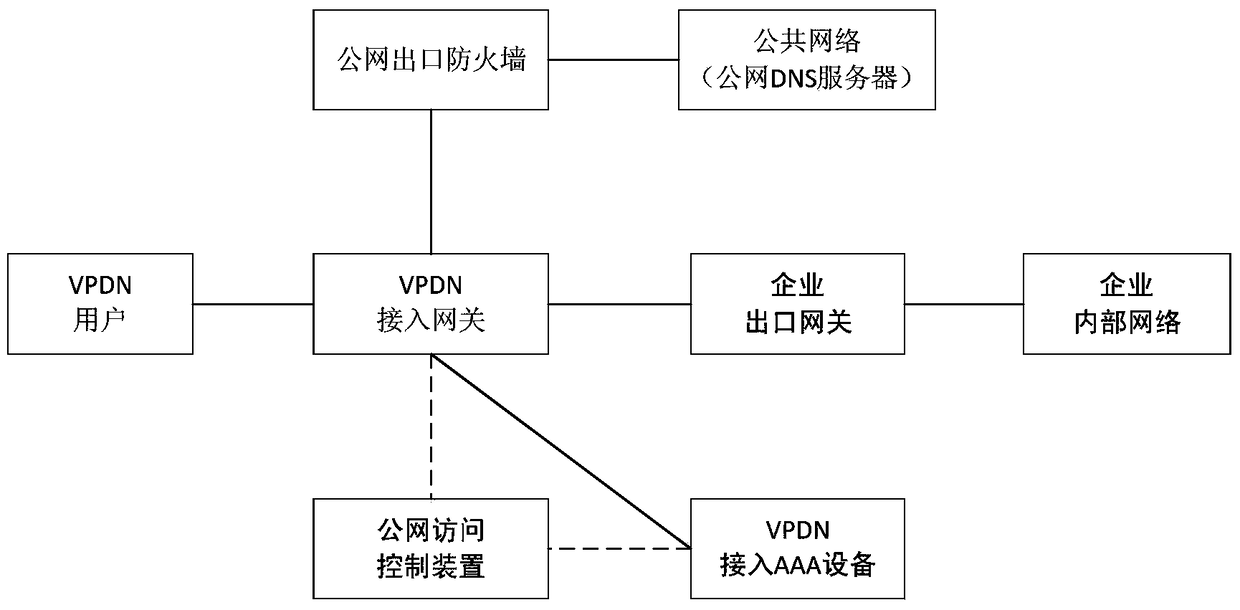
ActiveCN105553987BTroubleshoot access control issuesEasy to carry outTransmissionWireless communicationIt innovationWebID
A control device and method for a wireless VPDN user to access a specific public website, the device is used to control the user to only be able to access authorized public websites in the VPDN network environment on the basis of the existing VPDN network architecture and without changing the current business process point. The key to its innovation is to use the online IP address of the VPDN user recorded in the AAA device to identify the user, and obtain the list of public websites authorized by the user to legally visit, and then judge the legitimacy of the user's access to the target public website according to the list of public websites allowed to visit . The present invention has little modification to the existing network, does not affect the existing business operation process of the existing network, and has high applicability and implementability. For operators, it can promote the development and promotion of new services, and broaden users and revenue channels. For VPDN users, the list of allowed public networks can be flexibly set and adjusted, and cloud computing and other application services of specific public networks can be safely used to improve the user experience of specific services, increase user stickiness and loyalty, and have broad application space.
Owner:BEIJING CAPITEK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com