Backup and recovery method of computer system, device and computer system
A computer system and backup technology, which is applied in the field of computer security, can solve the problems of poor compatibility, low security of backup and restoration methods, etc., and achieve good security, save backup time, and save disk space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
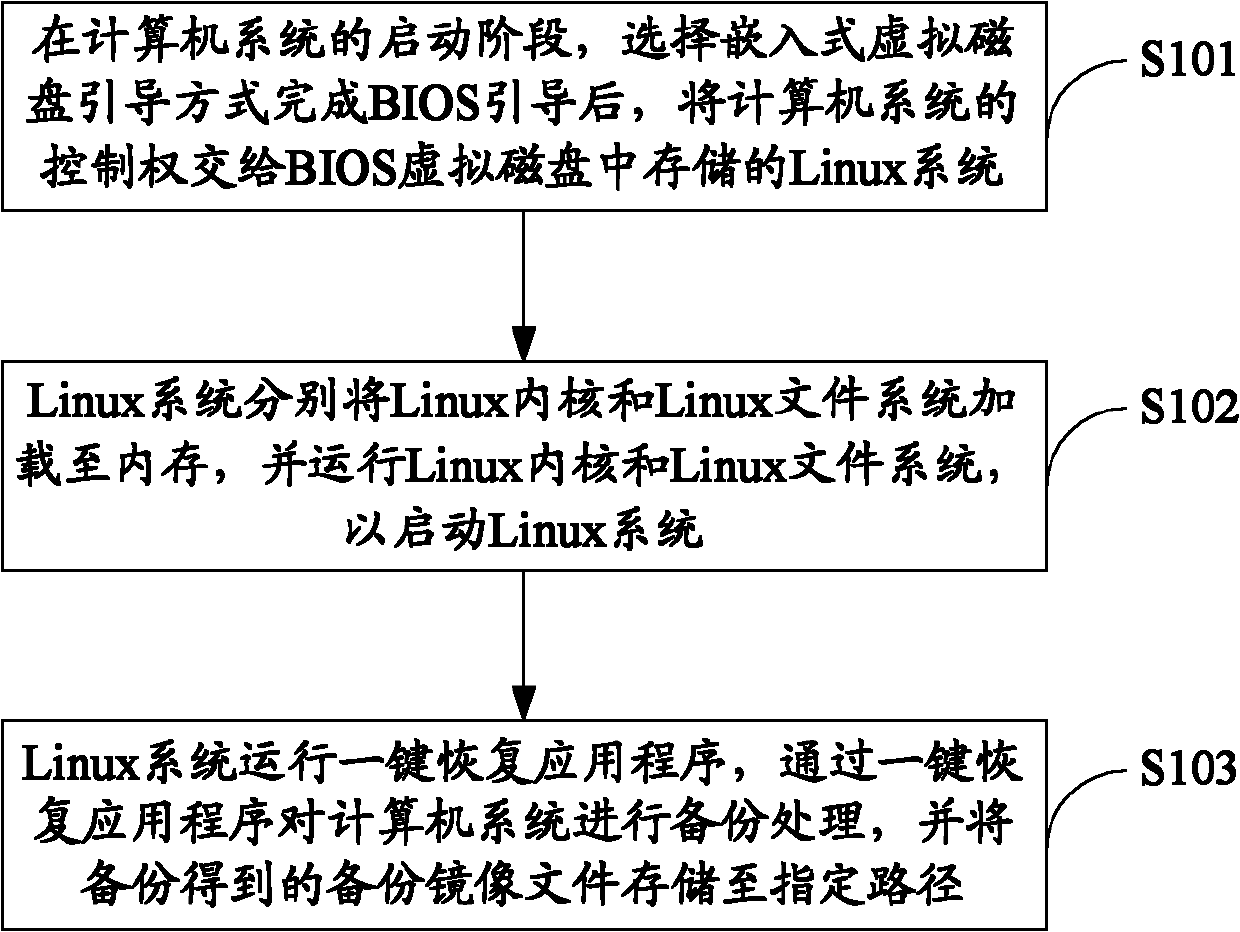
[0036] figure 1 The implementation process of the computer system backup method provided by the first embodiment of the present invention is shown, and the details are as follows:
[0037] In step S101, in the startup stage of the computer system, after selecting the embedded virtual disk boot mode to complete the BIOS booting, the control right of the computer system is transferred to the Linux system stored in the BIOS virtual disk.
[0038] In the embodiment of the present invention, after the computer system is powered on, enter the BIOS setup (Setup) interface through the function key. In the BIOS Setup interface, by selecting the embedded virtual disk (Embedded Virtual Disk, EVD) boot mode, the BIOS can be The virtual disk performs BIOS booting. After the BIOS boot is completed through the BIOS virtual disk, the control of the computer system is transferred to the Linux system stored in the BIOS virtual disk.
[0039] The BIOS virtual disk is made through the following steps:
...
Embodiment 2
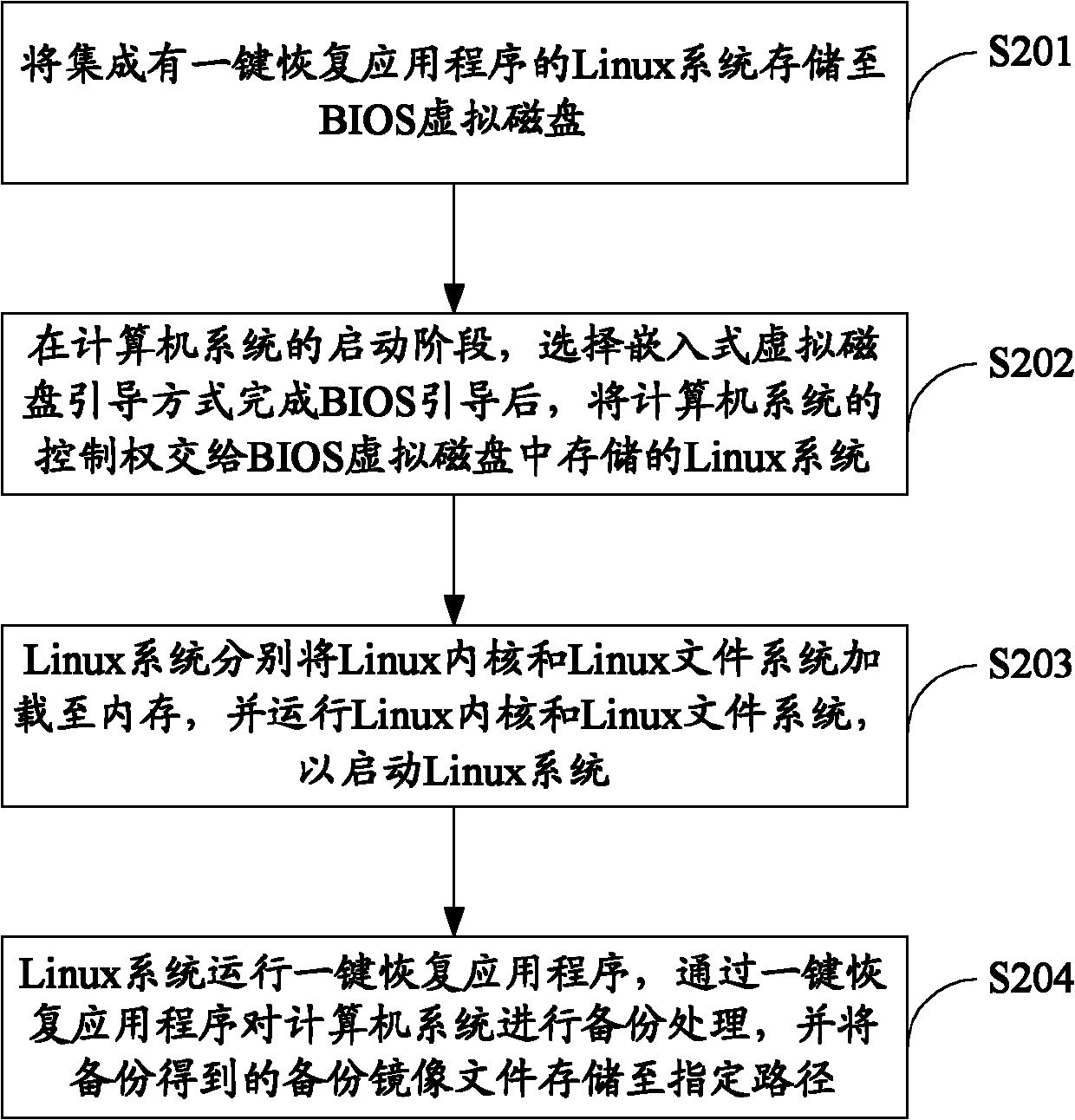
[0062] figure 2 Shows the implementation process of the computer system backup method provided by the second embodiment of the present invention, in which step S202 to step S204 are figure 1 Steps S101 to S103 are the same, the only difference is that it also includes the following steps:
[0063] In step S201, the Linux system integrated with the one-key recovery application is stored in the BIOS virtual disk. The specific steps are as follows:
[0064] a. Reserve a continuous storage space in the BIOS Flash chip as a BIOS virtual disk. The specific steps are as described above and will not be repeated here.
[0065] b. Integrate a one-key recovery application in the Linux system.
[0066] In another embodiment of the present invention, in order to save the storage space of the BIOS Flash chip to the utmost extent, this step can be replaced by: customizing a compact Linux system and integrating a one-key recovery application in the compact Linux system.
[0067] c. Embed the Linux sy...
Embodiment 3
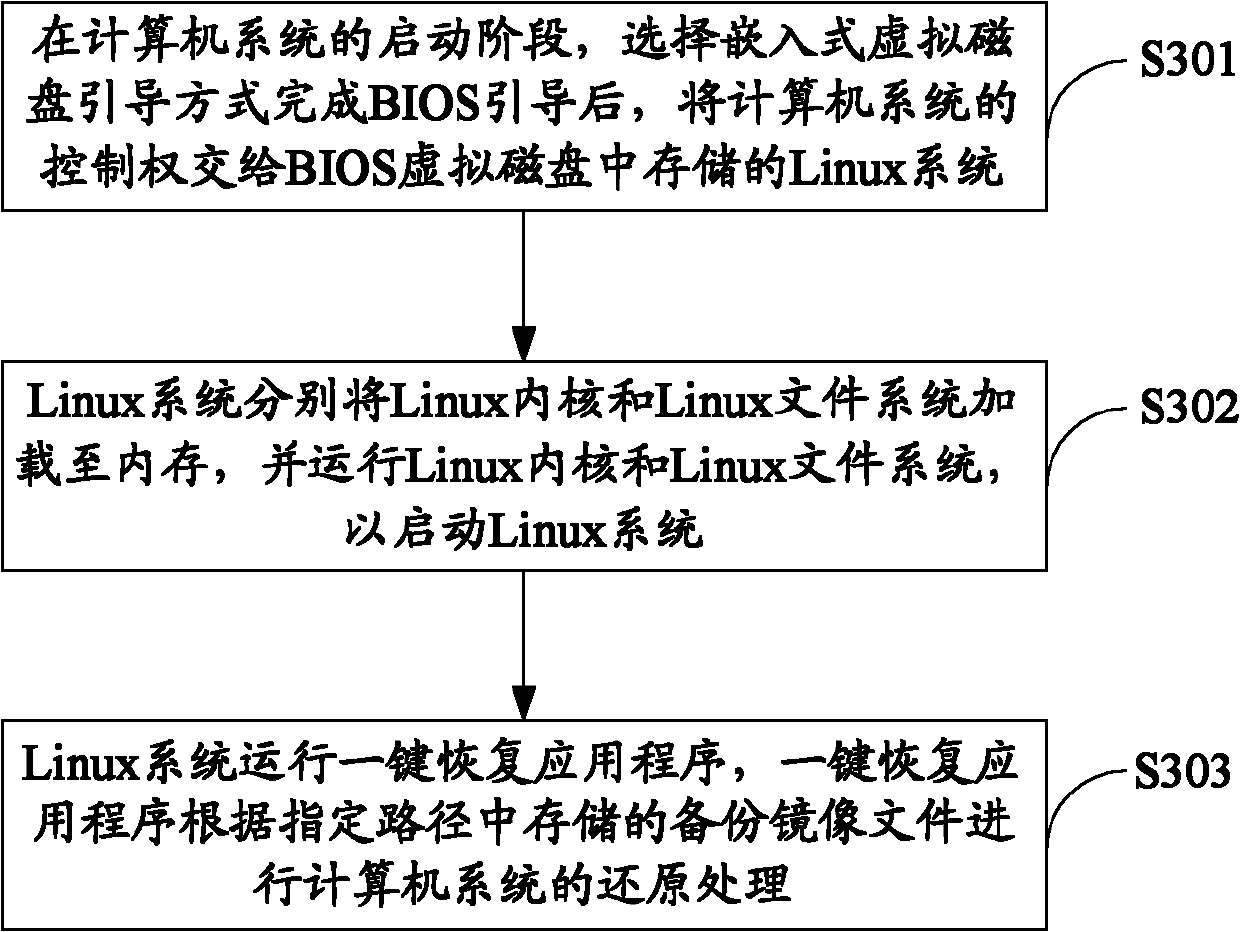
[0071] image 3 The implementation process of the computer system restoration method provided by the third embodiment of the present invention is shown, and the details are as follows:
[0072] In step S301, in the startup stage of the computer system, after selecting the embedded virtual disk boot mode to complete the BIOS booting, the control right of the computer system is transferred to the Linux system stored in the BIOS virtual disk.
[0073] The ways to choose to boot from the embedded virtual disk include but are not limited to the following: one is to choose to boot from the embedded virtual disk through a key action on the keyboard; the other is to define a timer through the BIOS to periodically start from the embedded virtual disk Boot; The third is to use General Purpose InputOutput (GPIO hardware switch settings) to draw a trigger interface from the hardware, and select to start from the virtual disk through this interface.
[0074] In step S302, the Linux system loads t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com