Method for distributing key using public key cryptographic technique and on-line updating of the public key
A technology of key distribution and public key cryptography, which is applied in the field of key distribution and online public key update, and can solve the problems of forward secrecy without key perfection, large security risks, and threats to system security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
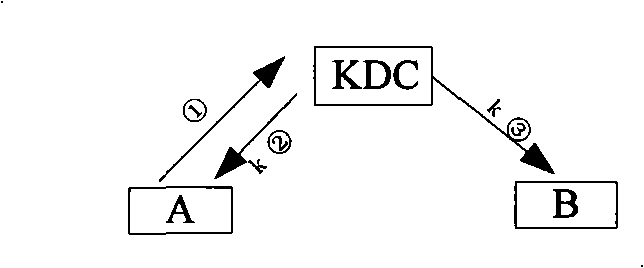
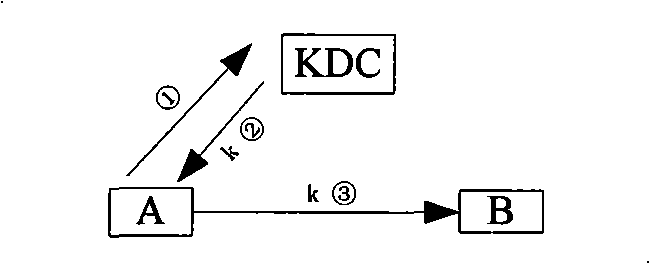
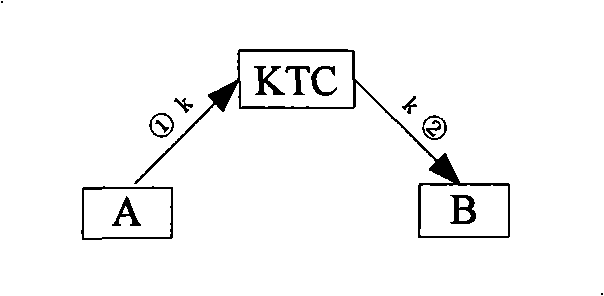
[0037]The key distribution center has a pair of public-private key pair x and Px, and the communication entity should obtain the public key Px of the key distribution center before communication and store it locally. When the first entity A and the second entity B need to conduct secure communication, the communication session key is obtained through a key distribution protocol.
[0038] see Figure 5 , the steps of the key distribution method utilizing public key cryptography of the present invention are as follows:
[0039] 1) The first entity A generates a pair of temporary public-private key pair a and Pa, and sends a key request message to the key distribution center, and the key request message contains the temporary public key Pa of the first entity A;
[0040] 2) After the key distribution center receives the key request message sent by the first entity A, it generates the communication session key k between the first entity A and the second entity B, and the key dist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com