Method for realizing switch-over between open call/secrete call in end-to-end voice telecommunication
A technology for voice communication and encrypted call, which is applied to secure communication devices and key distribution, can solve the problems of inconvenient use of encrypted communication and inability to implement encrypted calls, and achieves the effect of ensuring confidentiality and a concise method.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
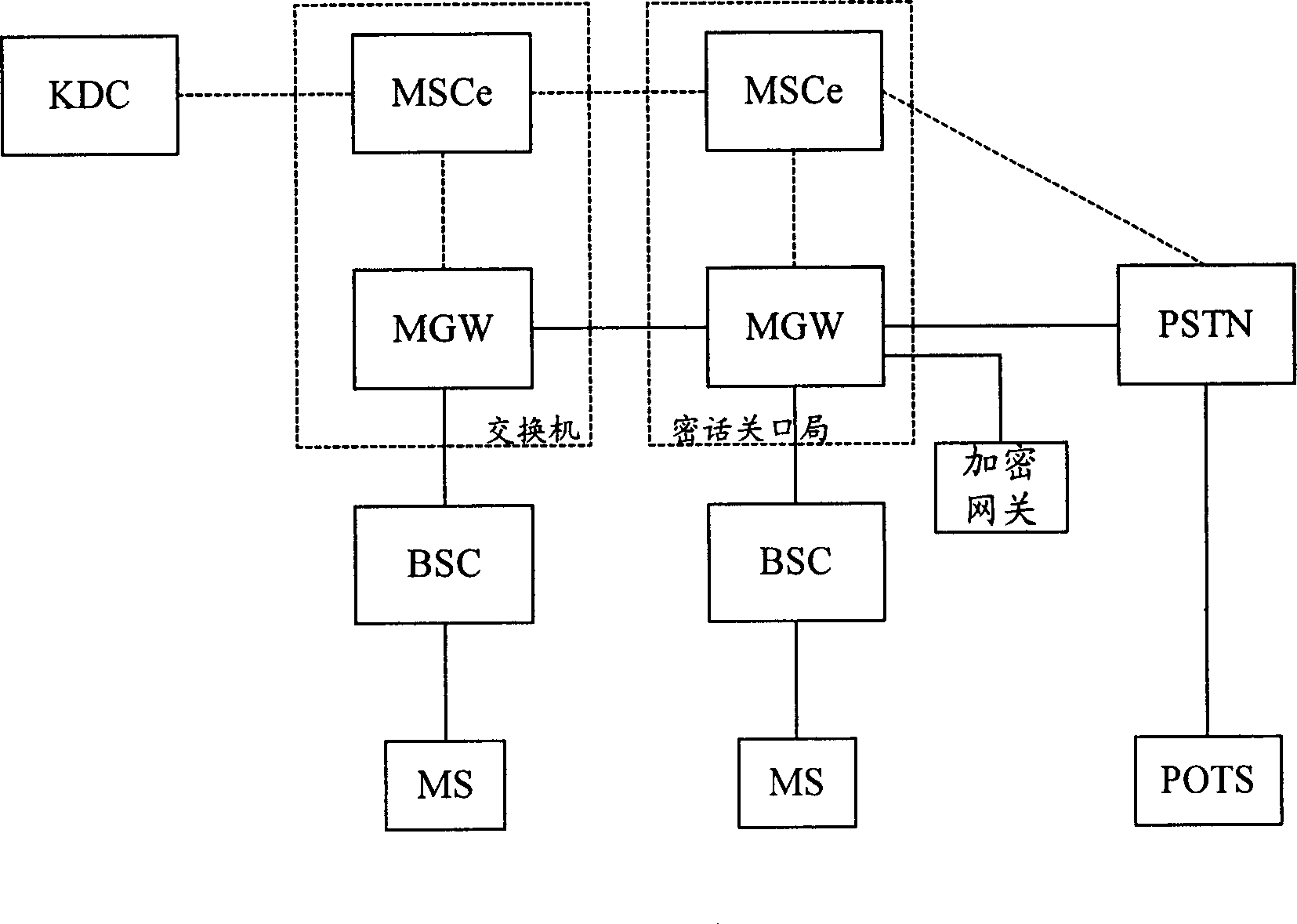
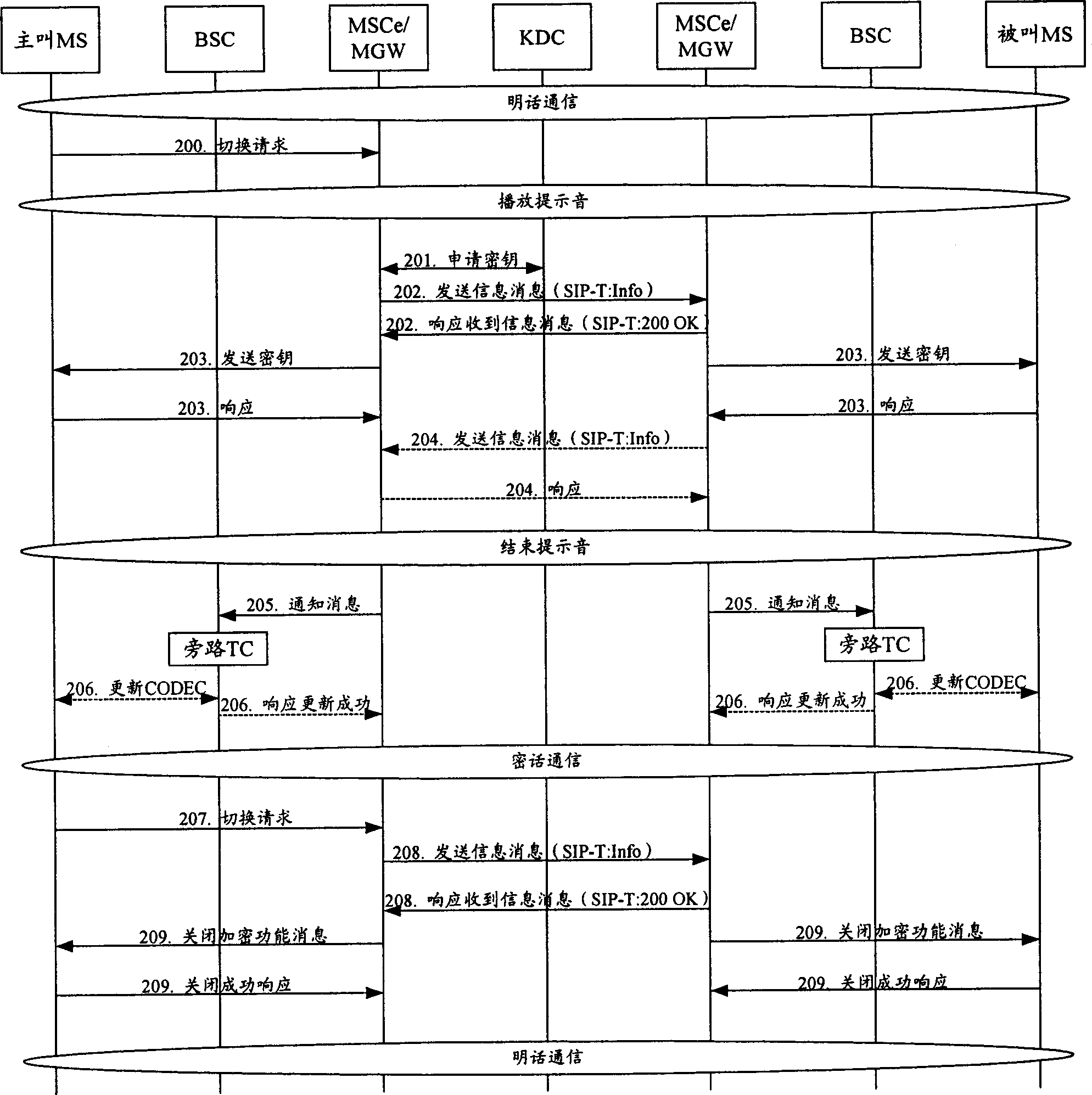
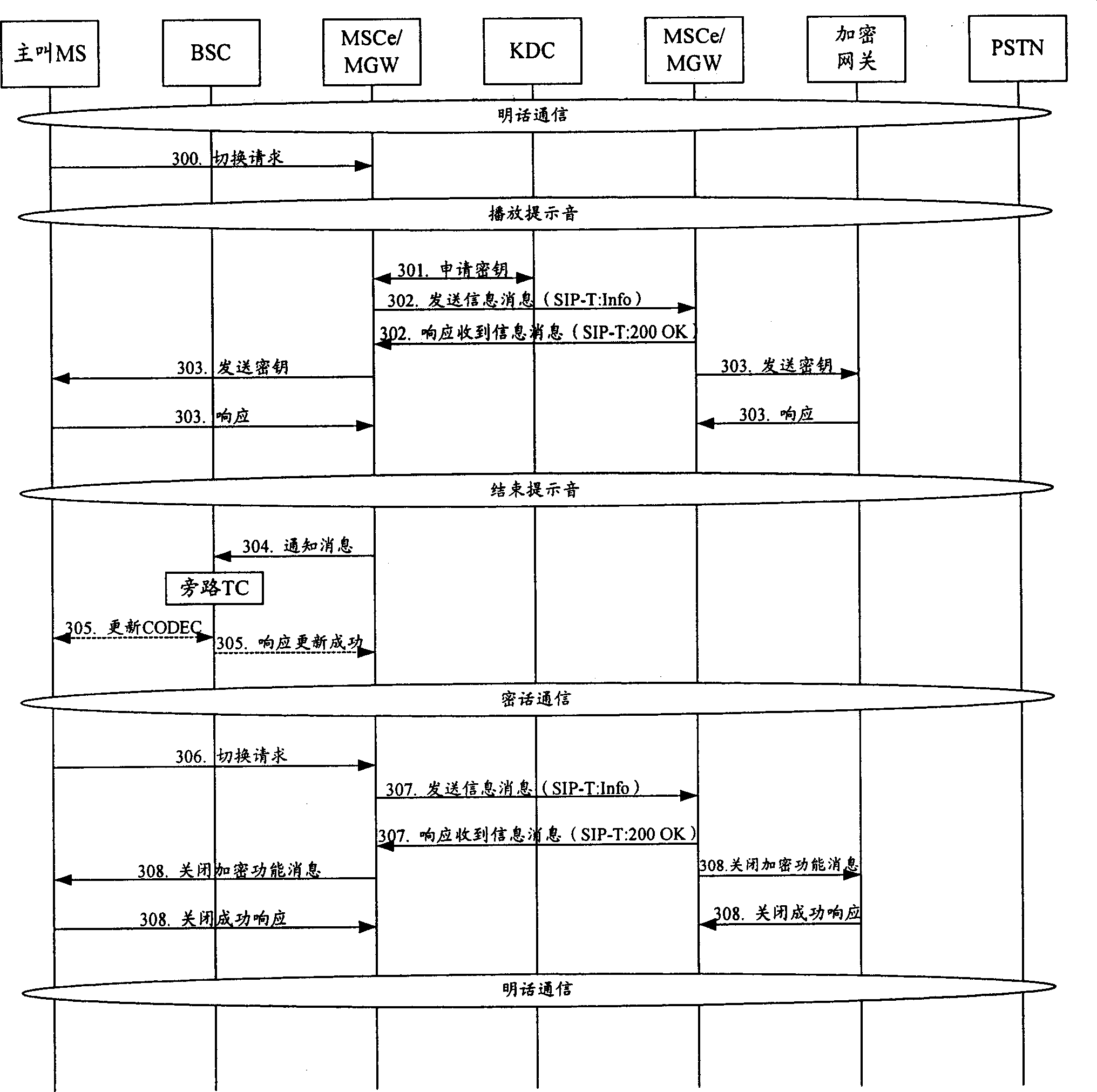
[0050] The core idea of the present invention is: using the existing end-to-end call flow, the calling party establishes a call and communicates normally. When both parties in the call need encrypted conversations, one party in the call initiates a switching request to the switch in the network control center where it is located. After receiving the switching request, the network control center judges whether the current call is clear or encrypted. After the control center applies for the key of both parties from the key distribution center and sends the applied key to the two parties in the call, the two parties in the call start the voice encryption function and enter the encrypted call; if the current call is an encrypted call, the network control center will Cancel the encrypted call and notify the two parties in the call. After receiving the notification of canceling the encrypted call, both parties will turn off the voice encryption function and enter the plain call.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com