Data processing method and device and electronic equipment
A data processing and data technology, applied in the computer field, can solve problems such as hidden dangers of data security, data leakage, and low data efficiency, and achieve the effect of reducing consumption and performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
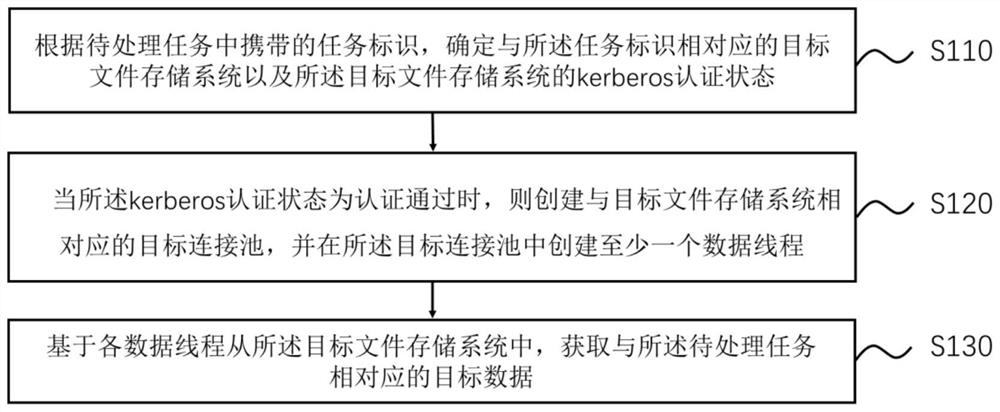
[0028] figure 1 This is a schematic flowchart of a data processing method provided in Embodiment 1 of the present invention. This embodiment is applicable to determining whether a task needs to be processed based on the kerberos authentication status of the file storage system corresponding to the task to be processed when a task to be processed is detected Perform kerberos authentication on the target file storage system, and after completing the kerberos authentication, create a data thread between the application software and the target file storage system for data transmission, the method can be performed by a data processing device, and the device can It is implemented in the form of software and / or hardware, and the hardware may be an electronic device, such as a mobile terminal or a PC terminal.
[0029] like figure 1 As shown, the method includes:
[0030] S110. Determine, according to the task identifier carried in the task to be processed, a target file storage sys...
Embodiment 2
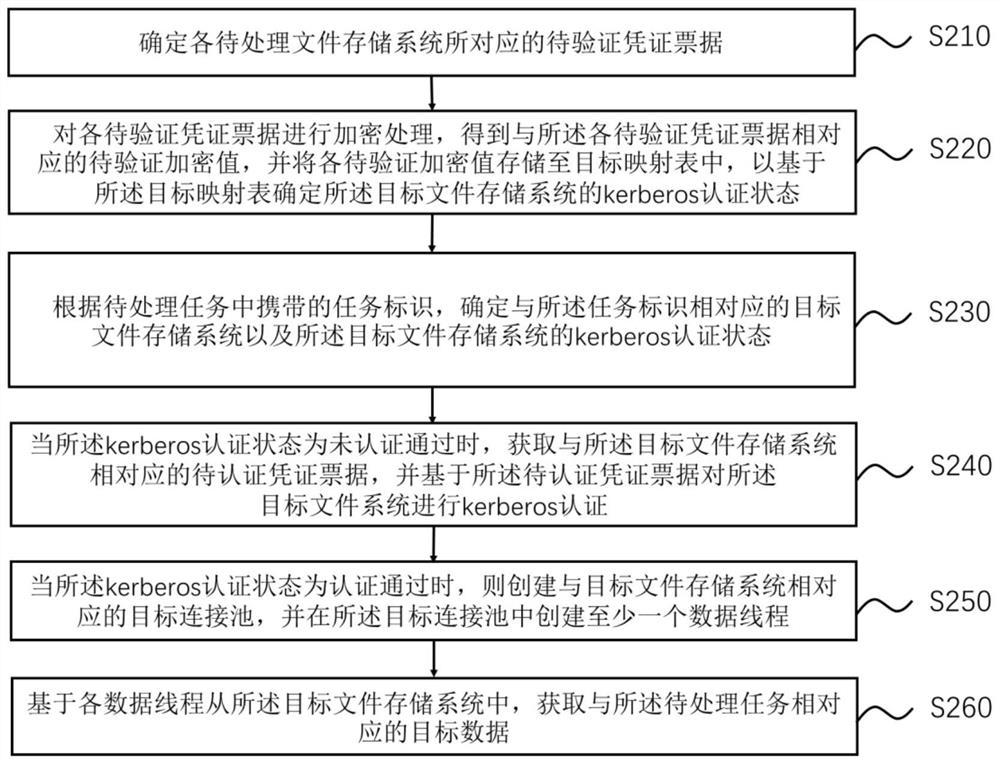
[0054] As an optional embodiment of the above-mentioned embodiment, figure 2 It is a schematic flowchart of a data processing method provided in Embodiment 2 of the present invention. Optionally, according to the task identifier carried in the to-be-processed task, the target file storage system corresponding to the task identifier and the target file storage system corresponding to the task identifier are determined. Before describing the kerberos authentication status of the target file storage system, perform kerberos authentication for each to-be-processed file storage system according to the pre-validated vouchers corresponding to each to-be-processed file system, and if the target file storage system fails the kerberos authentication , perform kerberos authentication on the target file storage system.
[0055] like figure 2 As shown, the method includes:
[0056] S210: Determine the to-be-verified voucher ticket corresponding to each to-be-processed file storage syst...
Embodiment 3
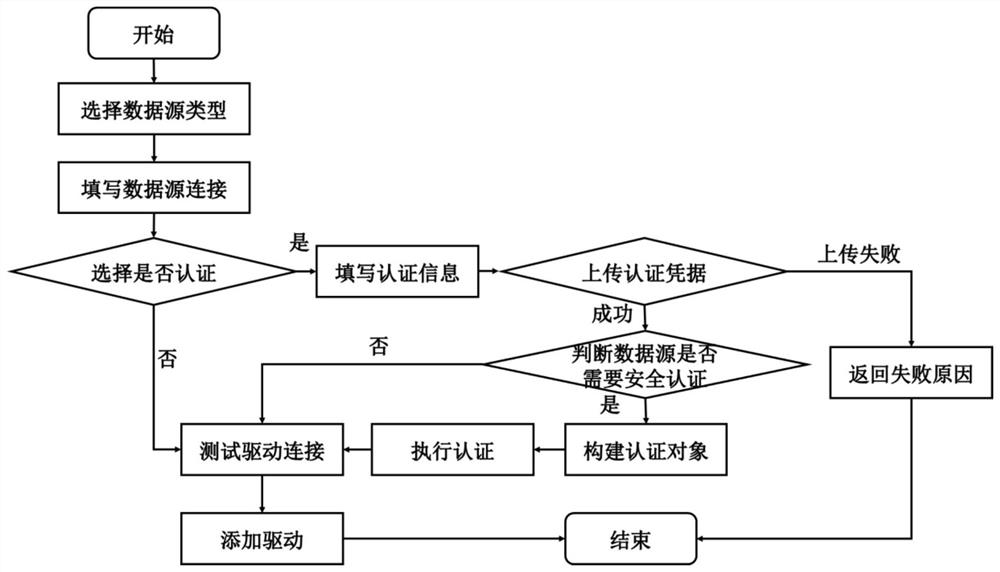
[0074] In a specific example, such as image 3 As shown, when the task to be processed is detected, the task identifier corresponding to the task to be processed is determined, the data type corresponding to the task to be processed is determined according to the task identifier, and then the data source connection corresponding to the task to be processed is filled in ( That is, the target file storage system), so that when the target file storage system needs to be processed, a data thread is established between the application software and the target file storage system, so as to perform data transmission based on the established data thread.
[0075] First, determine whether the target file storage system for data transmission needs authentication. When the kerberos authentication status of the target file storage system is passed, it is not necessary to perform kerberos authentication on the target file storage system again. Create data threads between file storage system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com